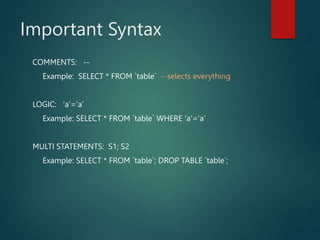
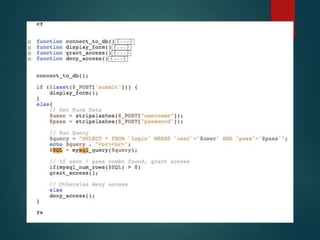
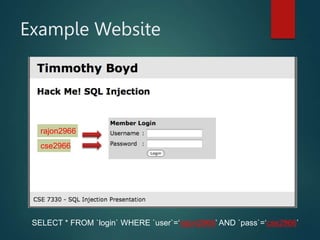
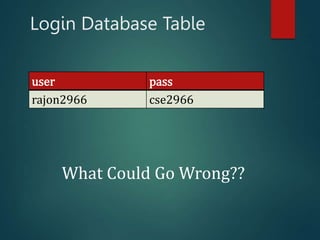
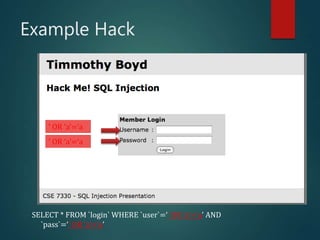
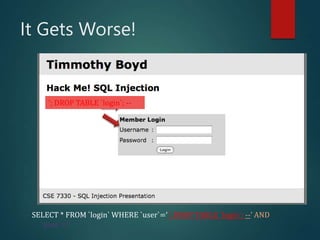
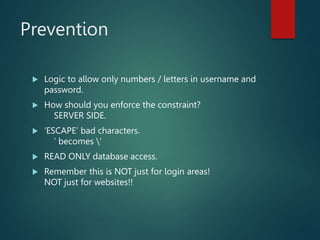
This presentation introduces SQL injection, a code injection technique that exploits security vulnerabilities in user input handlers to target databases. It provides examples of real-world SQL injection attacks, such as the theft of 130 million credit card numbers. The presentation demonstrates how SQL comments, logic statements, and multiple statements can be abused to perform unauthorized actions like dropping tables or updating passwords. It recommends server-side validation of user input and limiting database access to help prevent SQL injection attacks.