The document discusses how Kristofer Laxdal, Head of Information Security at CanDeal.ca Inc., implemented Splunk to improve the company's security posture. Some key points:
1) CanDeal handles billions of dollars in daily fixed income and derivatives trades, but faced challenges from big data and new threats.
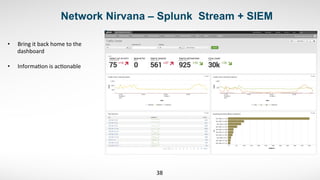
2) Laxdal chose Splunk due to its ease of use, ability to integrate different data sources quickly, and potential for immediate security benefits.
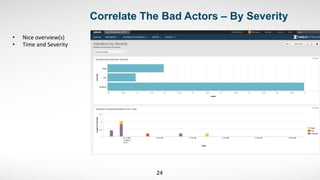
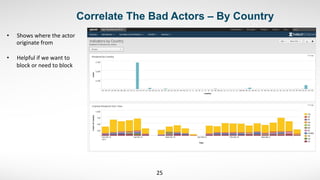
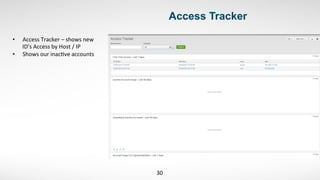
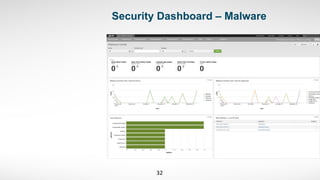
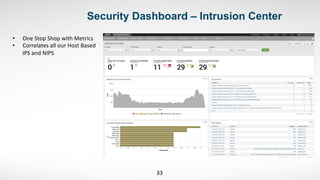
3) He started by ingesting existing security data like endpoint logs. This provided visibility into malware and alerts that previously had no centralized view.