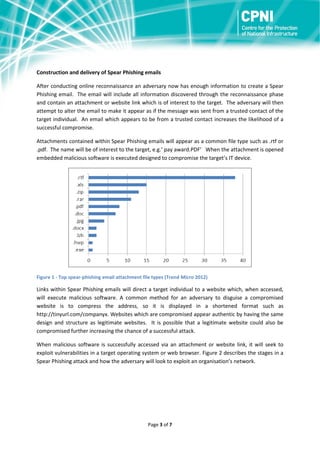
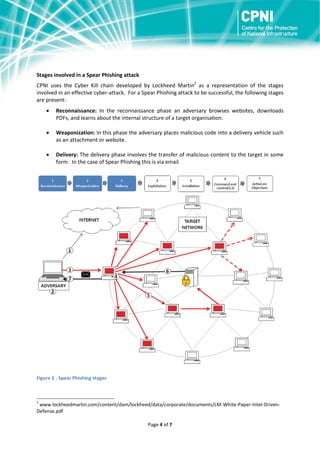
Spear phishing is a targeted form of phishing where adversaries conduct online research about individuals and organizations to craft personalized phishing emails. These emails often contain malicious attachments or links that install malware when opened. Spear phishing has a high success rate because targets are more likely to open emails that appear personalized. Organizations can reduce spear phishing risks through security awareness training for employees and technical defenses like firewalls, software patching, and limiting administrative privileges.