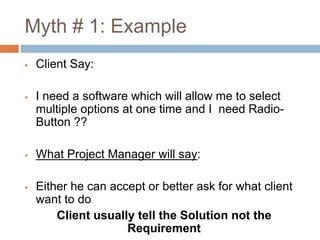
The document discusses several common software development myths. It is written by a group of 7 software engineers. The myths discussed include: 1) that clients know exactly what they want, 2) that requirements are fixed, 3) that quality can't be assessed until a program is running, 4) that adding more people fixes schedule slips, 5) that security is only a cryptography problem, 6) that a tester's only task is to find bugs, 7) that testing can't begin until development is fully complete, and 8) that network defenses alone can provide protection. The document aims to dispel these myths and provide more accurate perspectives.