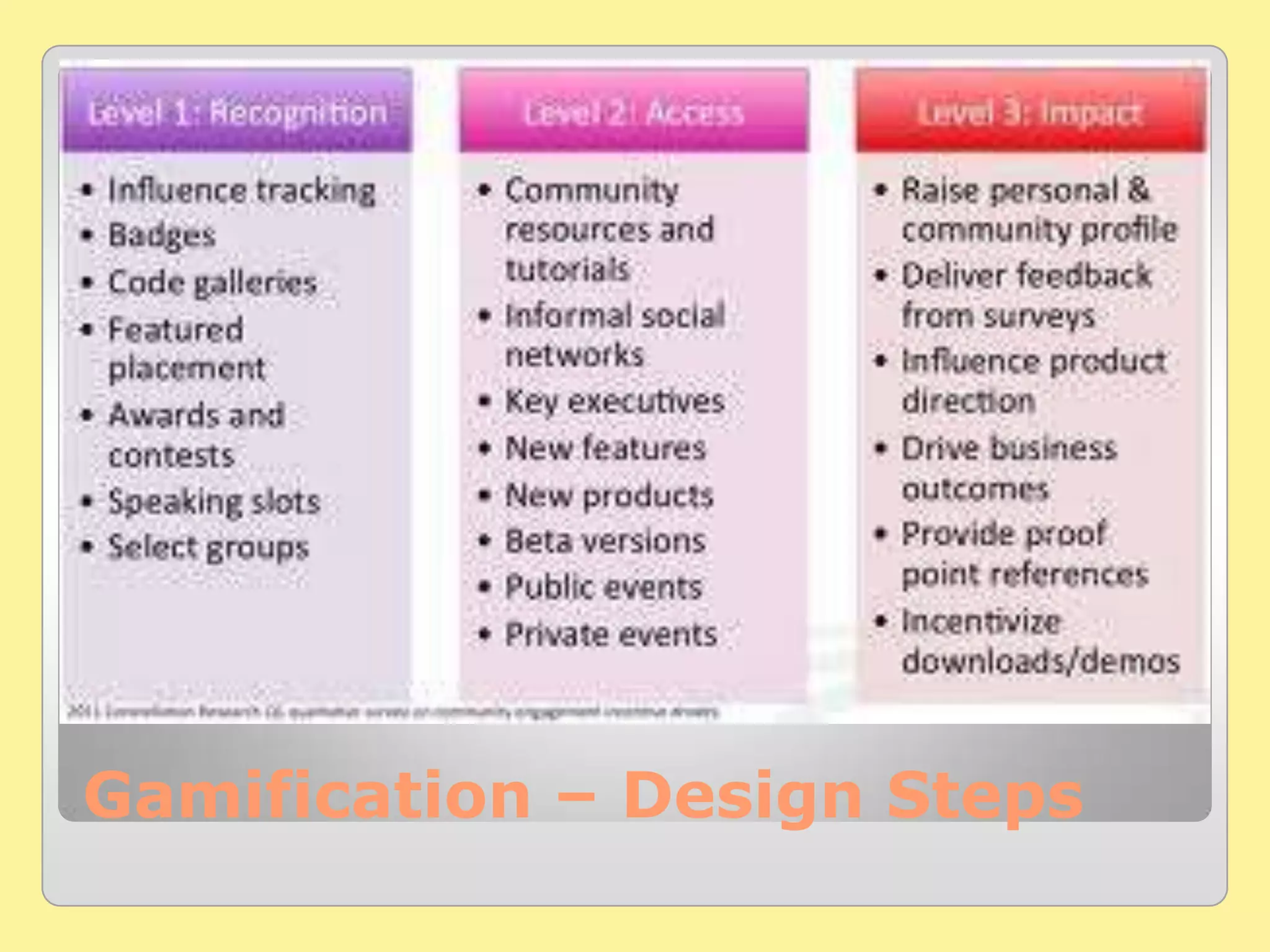
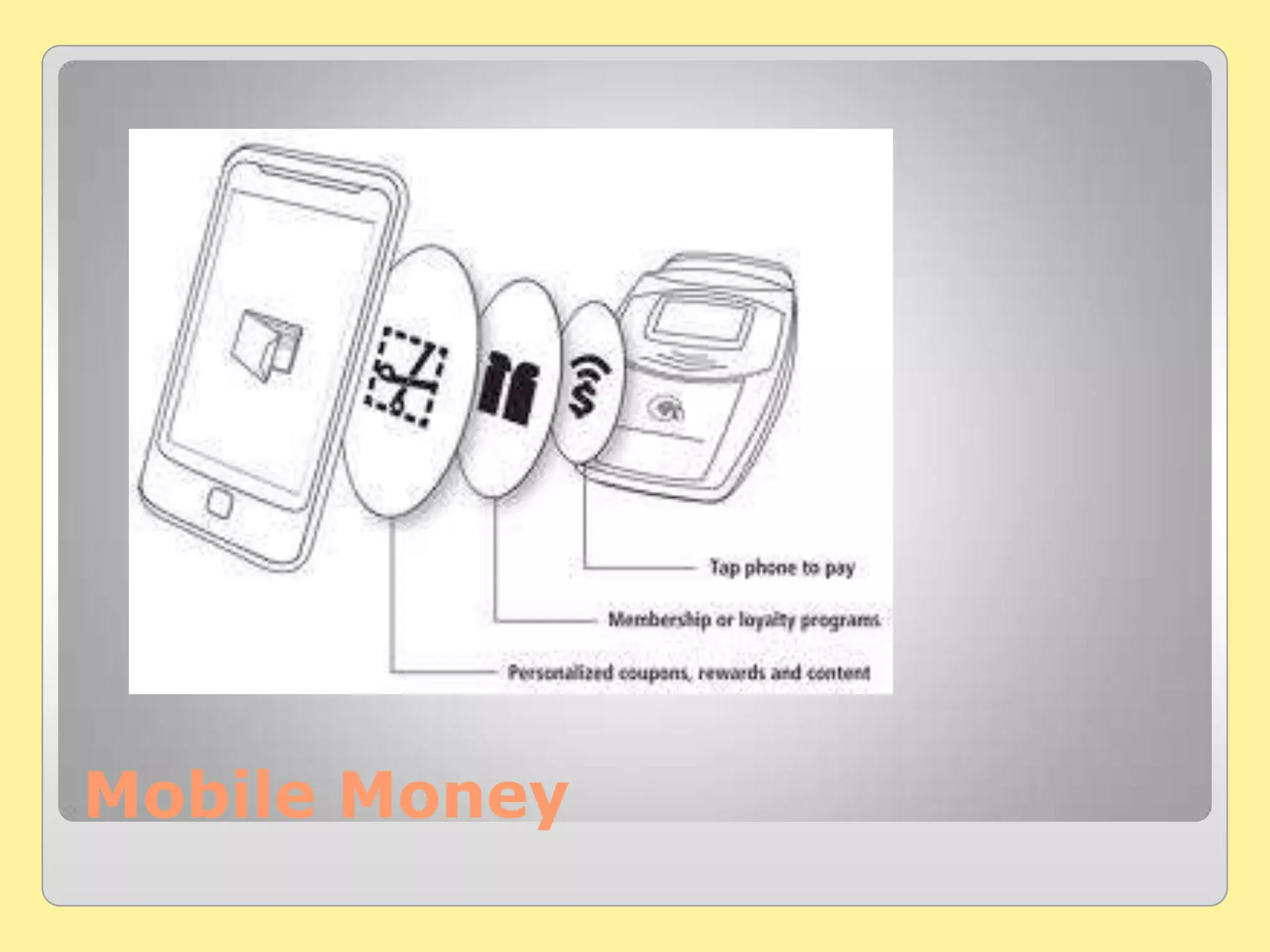
The document presents key software trends for 2013 and beyond, highlighting aspects such as gamification, mobile money, and mobile marketing. It discusses the regulation of free access to digital services and the importance of security implementations in protecting personal data. The author, Sanjiv Arora, offers IT consulting services and emphasizes the need for businesses to adapt to evolving technology trends.