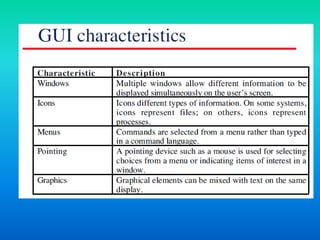
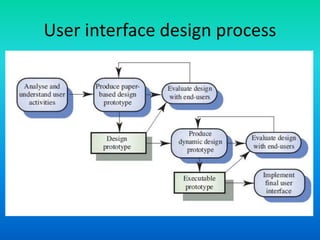
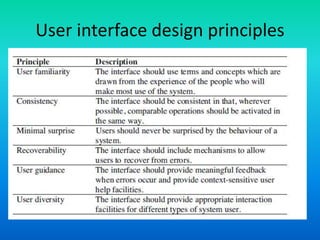
This document discusses user interface design for software systems. It notes that users often judge systems by their interfaces and poor interface design can lead to errors. Most business systems now use graphical user interfaces (GUIs) which are easy to learn and use. The document advocates for user-centered design where users' needs are paramount. It outlines the user interface design process and principles such as consistency, minimizing surprises, and supporting error recovery. Design principles also include making interfaces familiar to users and providing guidance for a diverse user base.