The document discusses a software birthmark method for detecting theft of JavaScript programs. It begins with an introduction to software theft, birthmarks, and JavaScript programs. It then outlines the related work in software birthmarks, describes the proposed system's methodology including heap profiling, graph generation, merging and detection. The conclusions state that the software birthmark system can find similarities between applications and distinguish them while resisting attacks. Future work aims to improve the graph selection and detection speed.


![Software
Birthmark for
Detecting
Theft of
JavaScript
Programs
Patel Swati
Jitendrakumar
Outline
Introduction
Literature
Survey
Methodology
Conclusions
and Future
work
Introduction
Software Theft
It is an unauthorized copy and use of computer software.
57 % Computer Users admit that they use pirated
software.
JavaScript programs and their theft
It is an interpreted computer programming language.
Techniques of avoiding Software Theft
• Software Watermarking :
An extra code known as watermark is included as a part
of a program to prove the ownership of the program.
• Code Obfuscation :
code obfuscation is the application of transformations to
the code, which changes the physical appearance of the
code, while preserving the black-box specifications of the
program.
Content of this slide cited from [?] [?] [?] [?] [?] [?]
October 24, 2013 SES’s R. C. Patel Institute of Technology, Shirpur, MS, India 3](https://image.slidesharecdn.com/rcpit-161227094348/85/Software-Birthmark-for-Detecting-Theft-of-JavaScript-Programs-3-320.jpg)
![Software
Birthmark for
Detecting
Theft of
JavaScript
Programs
Patel Swati
Jitendrakumar
Outline
Introduction
Literature
Survey
Methodology
Conclusions
and Future
work
Introduction contd...
Software Birthmark
A birthmark is a unique characteristic a program possesses
that can be used to identify the program.
To detect software theft,
1 The birthmark of the program under protection (the
plaintiff program) extracted.
2 The suspected program is searched against the birthmark.
3 If the birthmark of plaintiff program is found in the code of
suspected one, then it can be claimed as the suspected
program or part of it is a copy of the plaintiff program.
Content of this slide cited from [?]
October 24, 2013 SES’s R. C. Patel Institute of Technology, Shirpur, MS, India 4](https://image.slidesharecdn.com/rcpit-161227094348/85/Software-Birthmark-for-Detecting-Theft-of-JavaScript-Programs-4-320.jpg)
![Software
Birthmark for
Detecting
Theft of
JavaScript
Programs
Patel Swati
Jitendrakumar
Outline
Introduction
Literature
Survey
Methodology
Conclusions
and Future
work
Introduction contd...
Taxonomy of Software Birthmark
Static Birthmark - extracted from the syntactic structure
of a program.
Let p, q be two components of a program or program itself.
Let f be method for extracting the set of characteristics
from a program. Then f(p) is a static birthmark of p if:
1. f(p) is obtainable from p itself.
2. q is copy of p ⇒ f(p) = f(q).
Content of this slide cited from [?] [?]
October 24, 2013 SES’s R. C. Patel Institute of Technology, Shirpur, MS, India 5](https://image.slidesharecdn.com/rcpit-161227094348/85/Software-Birthmark-for-Detecting-Theft-of-JavaScript-Programs-5-320.jpg)
![Software
Birthmark for
Detecting
Theft of
JavaScript
Programs
Patel Swati
Jitendrakumar
Outline
Introduction
Literature
Survey
Methodology
Conclusions
and Future
work
Introduction contd...
Taxonomy of Software Birthmark contd...
Dynamic Birthmark - extracted from the dynamic
behavior of a program at run-time.
Let p,q be two components of a program or program itself.
Let I be the input to p and q. Let f(p,I) the set of
characteristics extracted from a program p with input I.
Then f(p,I) is a dynamic birthmark of p if:
1. f(p,I) is obtainable from p itself when executing p with
input I.
2. q is copy of p ⇒ f(p,I) = f(q,I).
Content of this slide cited from [?] [?]
October 24, 2013 SES’s R. C. Patel Institute of Technology, Shirpur, MS, India 6](https://image.slidesharecdn.com/rcpit-161227094348/85/Software-Birthmark-for-Detecting-Theft-of-JavaScript-Programs-6-320.jpg)
![Software
Birthmark for
Detecting
Theft of
JavaScript
Programs
Patel Swati
Jitendrakumar
Outline
Introduction
Literature
Survey
Methodology
Conclusions
and Future
work
Introduction contd...
Heap Graph based Birthmark
Content of this slide cited from [?]
October 24, 2013 SES’s R. C. Patel Institute of Technology, Shirpur, MS, India 7](https://image.slidesharecdn.com/rcpit-161227094348/85/Software-Birthmark-for-Detecting-Theft-of-JavaScript-Programs-7-320.jpg)
![Software
Birthmark for
Detecting
Theft of
JavaScript
Programs
Patel Swati
Jitendrakumar
Outline
Introduction
Literature
Survey
Methodology
Conclusions
and Future
work
Introduction contd...
The Threat Model
Content of this slide cited from [?]
October 24, 2013 SES’s R. C. Patel Institute of Technology, Shirpur, MS, India 8](https://image.slidesharecdn.com/rcpit-161227094348/85/Software-Birthmark-for-Detecting-Theft-of-JavaScript-Programs-8-320.jpg)
![Software
Birthmark for
Detecting
Theft of
JavaScript
Programs
Patel Swati
Jitendrakumar
Outline
Introduction
Literature
Survey
Methodology
Conclusions
and Future
work
Related Work
Year Author Work
2004 Myles et al. Whole program path birthmarks [?]
2007 Tamada et al. API calls based Birthmarks [?]
2007 Schuler et al. Birthmark for java [?]
2011 Chan et al. Birthmark on the runtime heap [?]
2011 Chan et al. Birthmark on heap memory analysis [?]
October 24, 2013 SES’s R. C. Patel Institute of Technology, Shirpur, MS, India 9](https://image.slidesharecdn.com/rcpit-161227094348/85/Software-Birthmark-for-Detecting-Theft-of-JavaScript-Programs-9-320.jpg)
![Software
Birthmark for
Detecting
Theft of
JavaScript
Programs
Patel Swati
Jitendrakumar
Outline
Introduction
Literature
Survey
Methodology
Conclusions
and Future
work
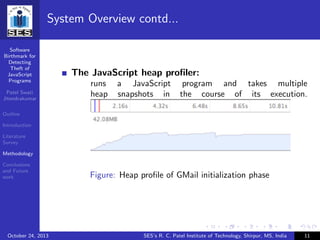
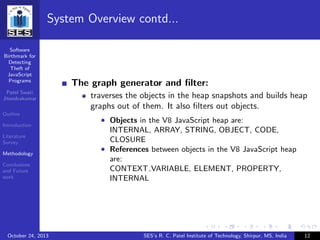
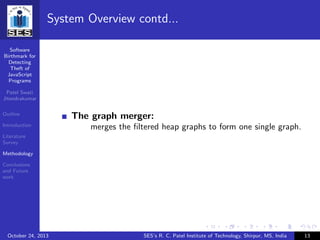
System Overview
Figure: System Overview
Content of this slide cited from [?]
October 24, 2013 SES’s R. C. Patel Institute of Technology, Shirpur, MS, India 10](https://image.slidesharecdn.com/rcpit-161227094348/85/Software-Birthmark-for-Detecting-Theft-of-JavaScript-Programs-10-320.jpg)



![Software
Birthmark for
Detecting
Theft of
JavaScript
Programs
Patel Swati
Jitendrakumar
Outline
Introduction
Literature
Survey
Methodology
Conclusions
and Future
work
“Ninth annual BSA global software 2011 piracy study,” 5 2012, [accessed on April 14,2013]. [Online].
Available: http://globalstudy.bsa.org/2011/
“Software theft,” [accessed on April 14,2013]. [Online]. Available:
http://www.javvin.com/softwareglossary/SoftwareTheft.html
“Software piracy,” [accessed on April 14,2013]. [Online]. Available:
http://www.fastiis.org/our services/enforcement/software theft/
C. Collberg and C. Thomborson, “Software watermarking:models and dynamic embeddings,”
Department of Computer Science, University of Auckland, Private Bag 92091, Auckland, New
Zealand, Tech. Rep., 2003.
H. I. A. Monden and K. Torii, “Watermarking java programs,” in International Symposium of Future
Software Technology, Nanjing, China, 1999.
C. T. C. Collberg and D. Low, “A taxonomy of obfuscating transformations,” University of Auckland,
Auckland, New Zealand, Tech. Rep. 148, 2003.
E. C. C. Collberg and M. Stepp, “Dynamic path-based software watermarking,” in Programming
Language Design and Implementation (PLDI 04), ACM, Ed., New York, 2004, pp. 107–118.
H. Tamada and A. Monden, “Design and evaluation of birthmarks for detecting theft of java
programs,” in IASTED International Conference of Software Engineering, 2004, pp. 569–575.
G. Myles and C. Collberg, “K-gram based software birthmarks,” in Symposium on Application
Computing (SAC 05), ACM, Ed., 2005, pp. 314–318.
October 24, 2013 SES’s R. C. Patel Institute of Technology, Shirpur, MS, India 16](https://image.slidesharecdn.com/rcpit-161227094348/85/Software-Birthmark-for-Detecting-Theft-of-JavaScript-Programs-17-320.jpg)

