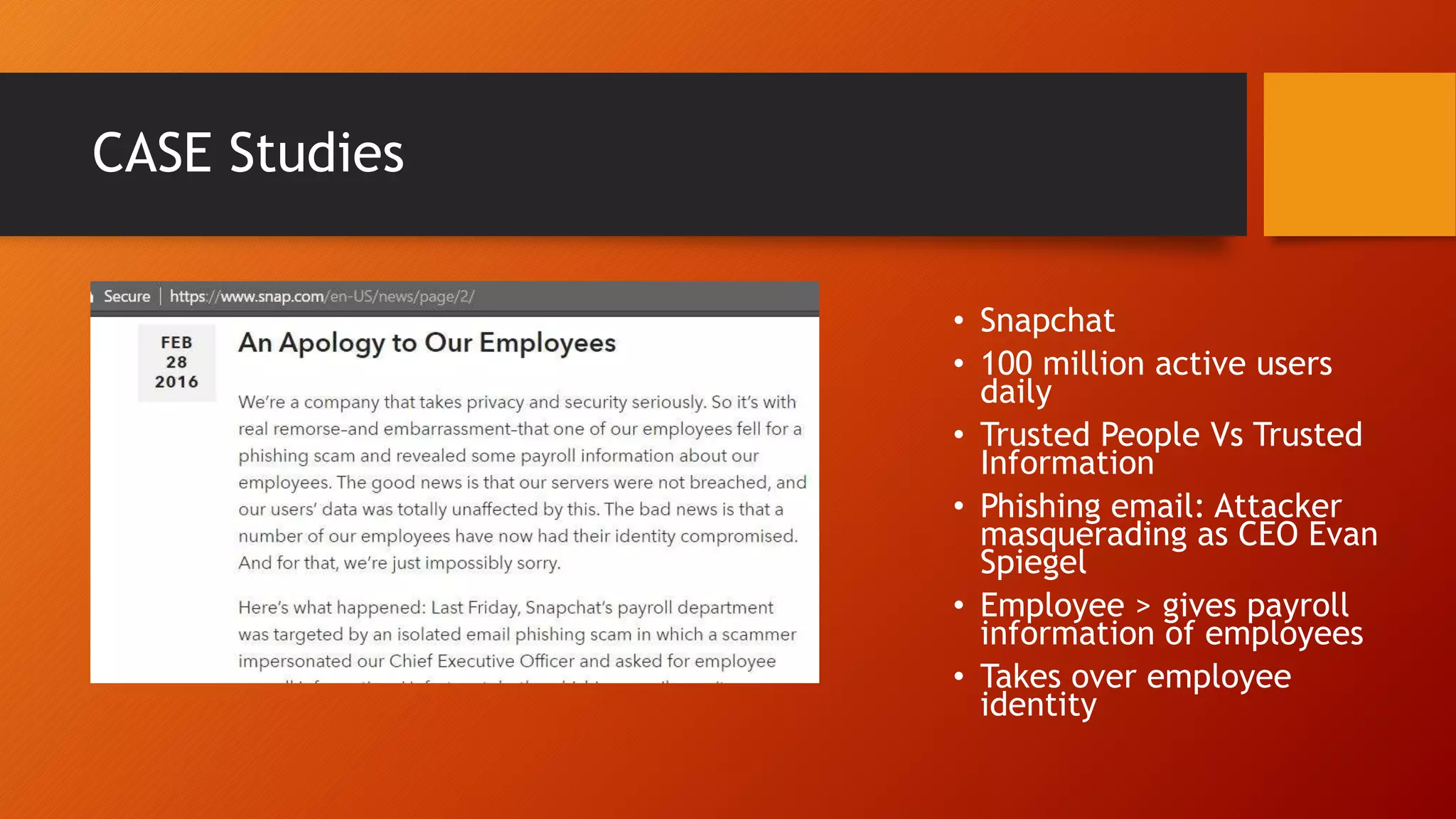
The document discusses social engineering techniques, emphasizing the psychological factors that differentiate humans from machines and the tactics employed in phishing and exploitation. It covers various methods of reconnaissance, tools used for social engineering, and case studies demonstrating the impact of such attacks on organizations. The document concludes with recommendations for defenses, including security awareness and improved technology measures.