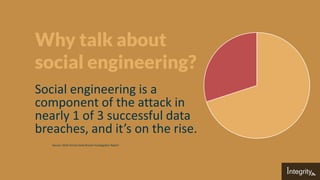
Social engineering exploits human behavior to manipulate individuals into providing confidential information, playing a significant role in nearly one-third of successful data breaches. Common attack methods include dumpster diving, pretexting, and phishing, with techniques that generally rely on deceptive practices to elicit responses. Effective defenses against these attacks include strong paper destruction processes, restricted access points, employee training, and regular assessments of organizational awareness and preparedness.