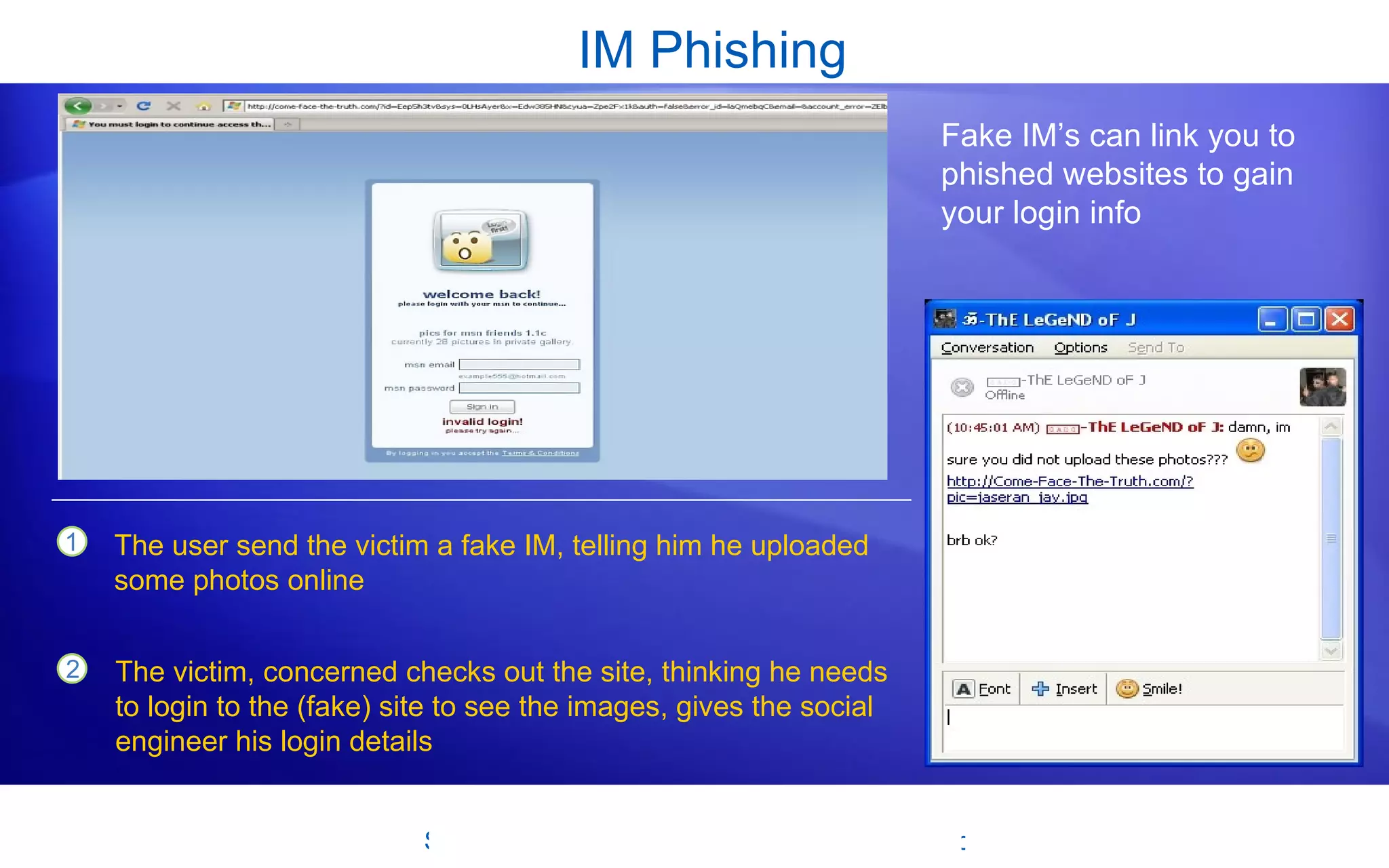
Social engineering and phishing scams manipulate users into providing sensitive information. Social engineers use deception through media like emails, websites, instant messages, or phone calls that appear legitimate but lead to fake sites seeking login or financial details. Users should be cautious of unsolicited messages and verify a site's authenticity by checking URLs and other details. Techniques like URL shorteners, phone number spoofing, and browser exploits can trick users, so vigilance is important when online or on calls. Resources are available to help learn about and mitigate these risks.