The document outlines a course calendar for a series of exams related to Service-Oriented Architecture (SOA) and its design patterns, focusing on topics such as Enterprise Service Bus (ESB), service brokers, data transformation, and reliable messaging. It includes detailed discussions on various design patterns, their problems, solutions, real-world applications, impacts, and relationships within SOA. Additionally, it emphasizes the importance of interoperability, message processing, and governance in complex service-oriented environments.





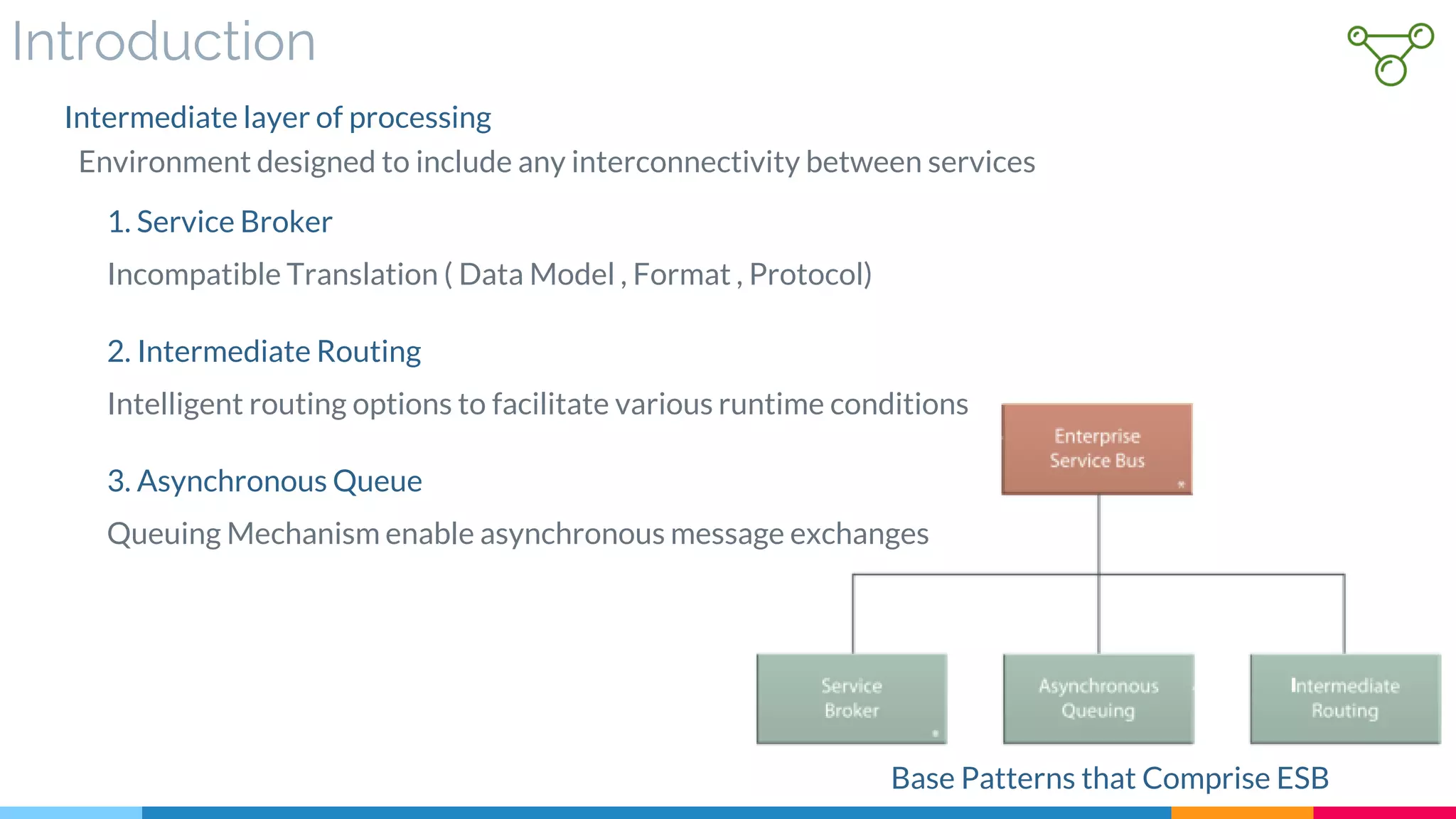
![1 Enterprise Service Bus
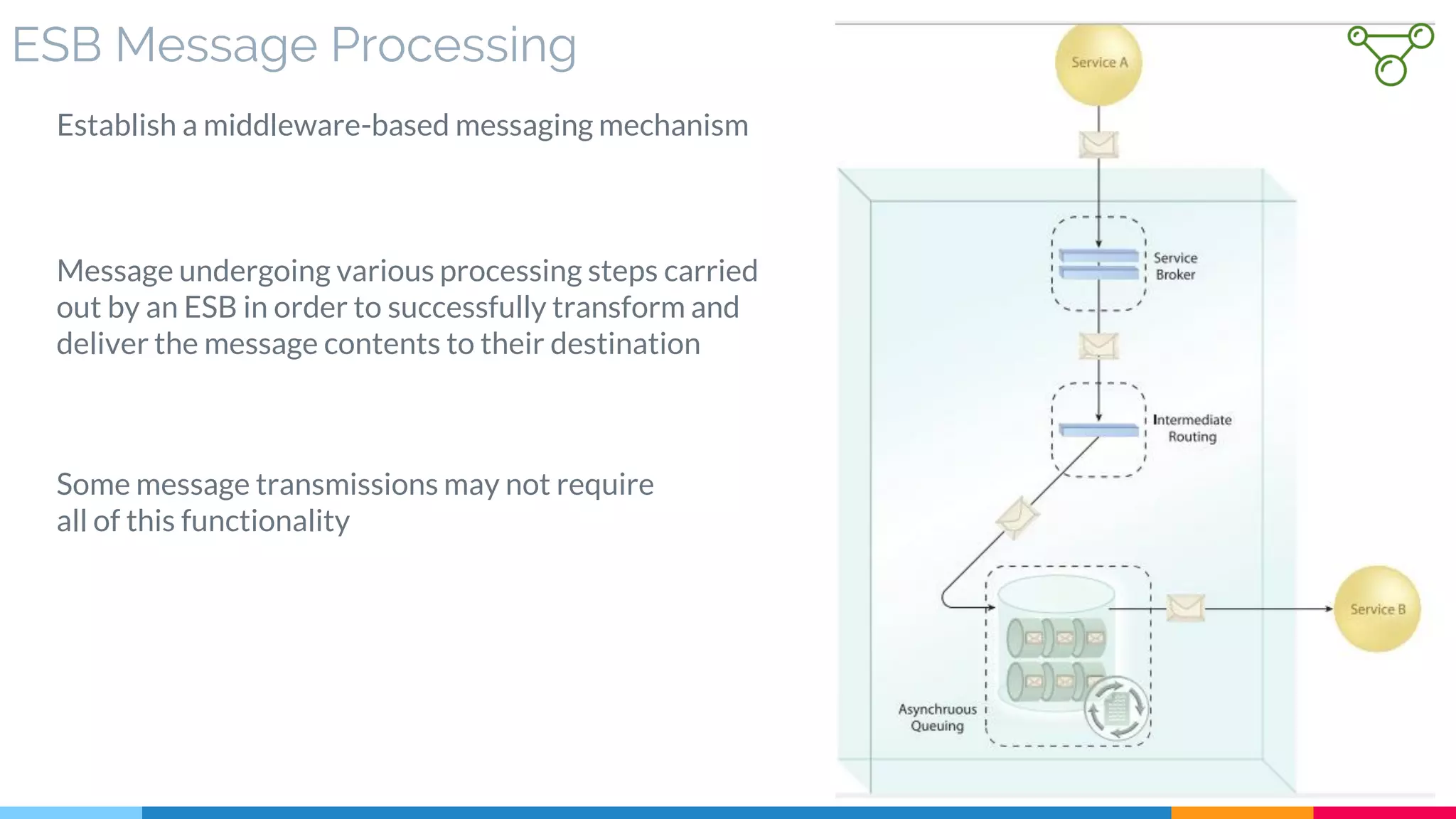
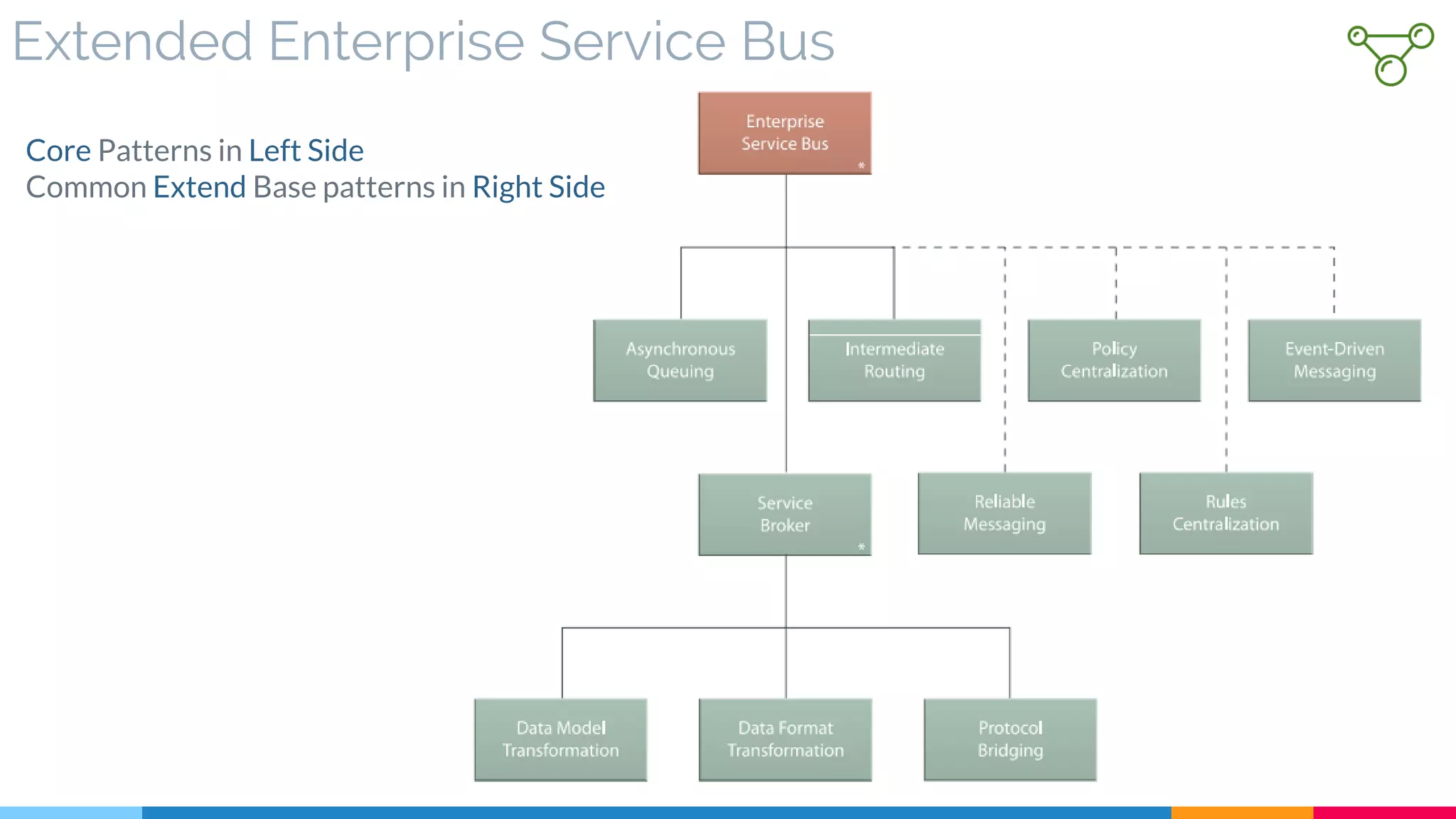
▷ Introduction
▷ ESB Message Processing
▷ Extended Enterprise Service Bus
[704]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-7-2048.jpg)
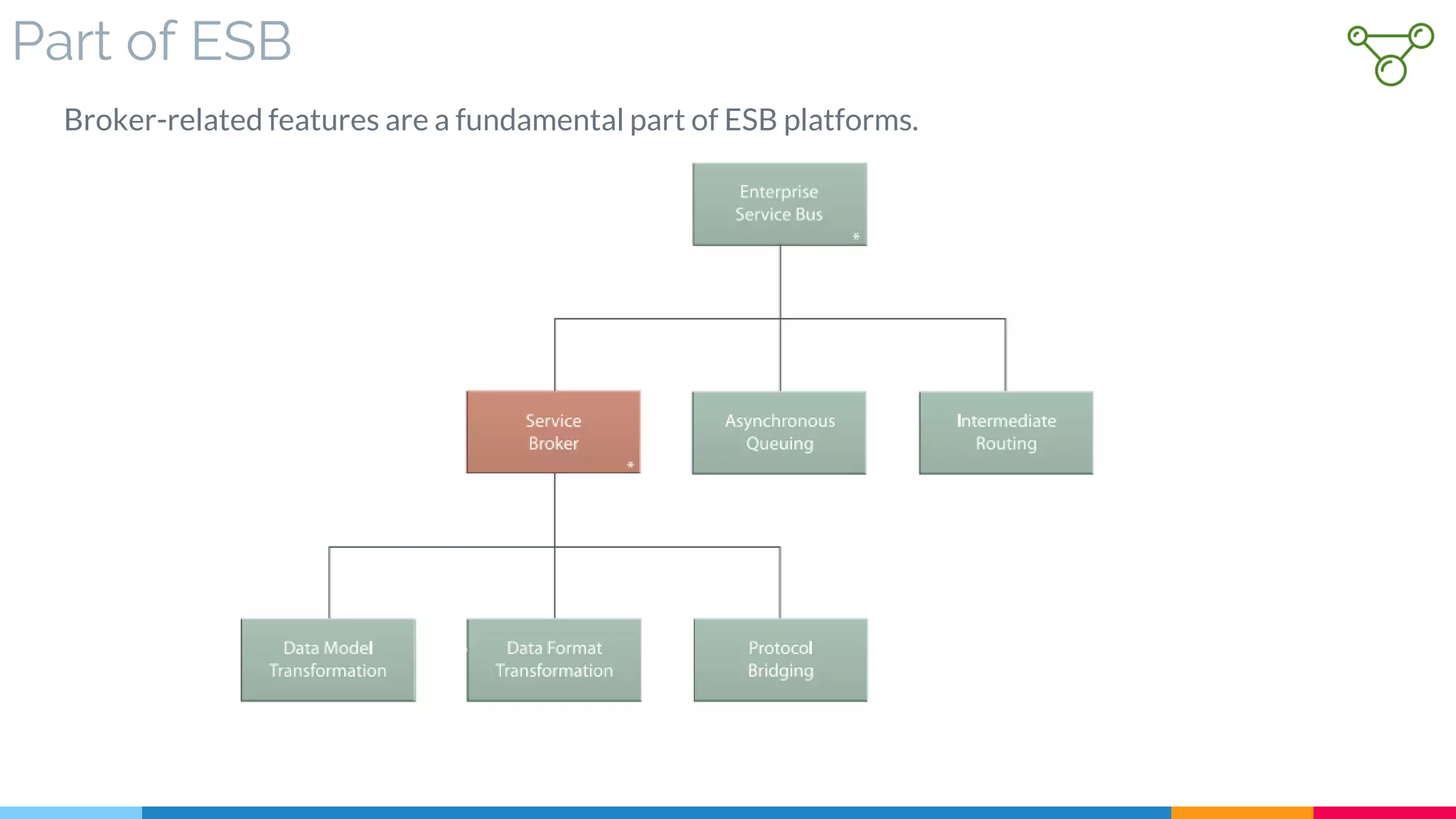
![2 Service Broker
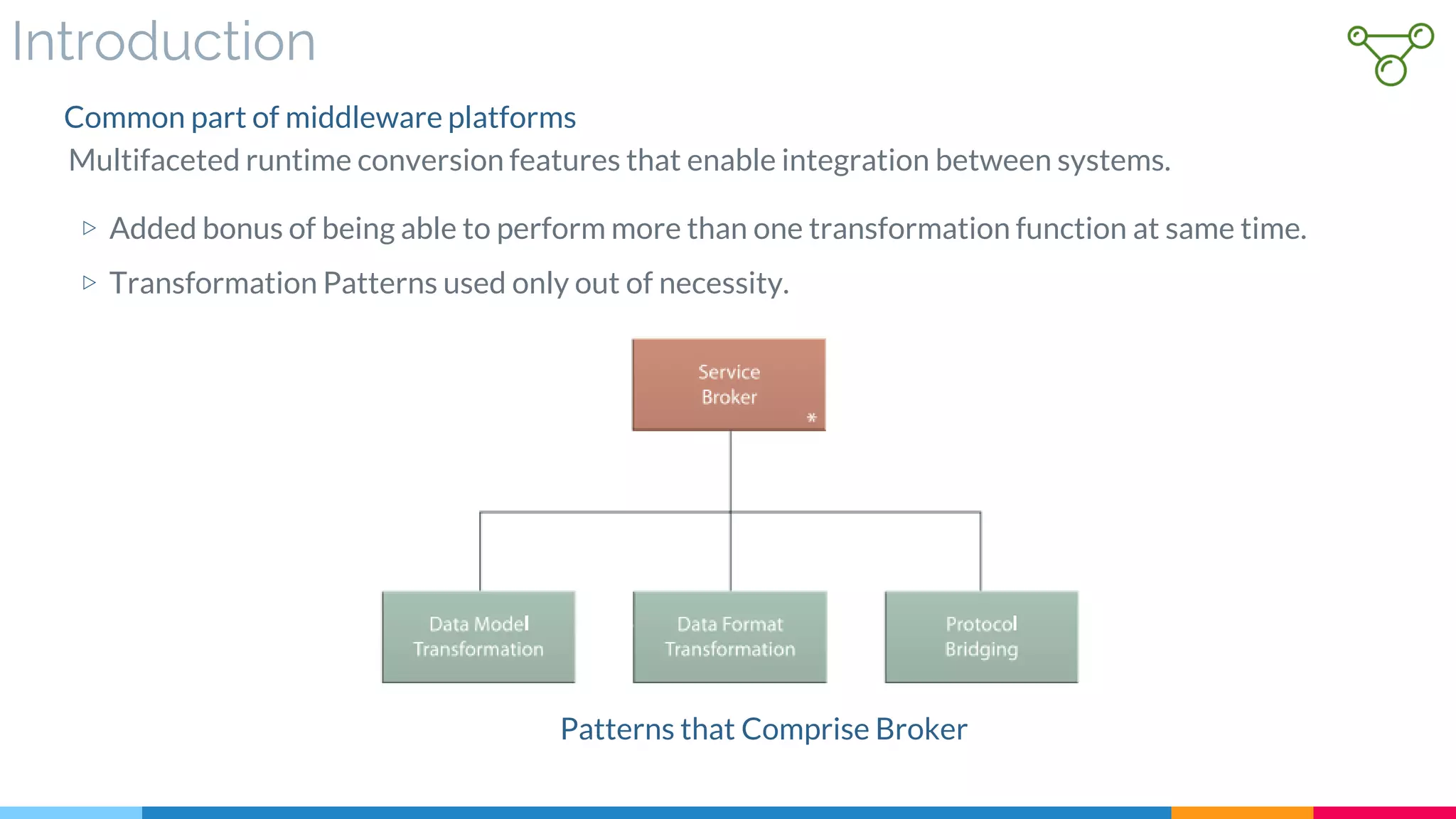
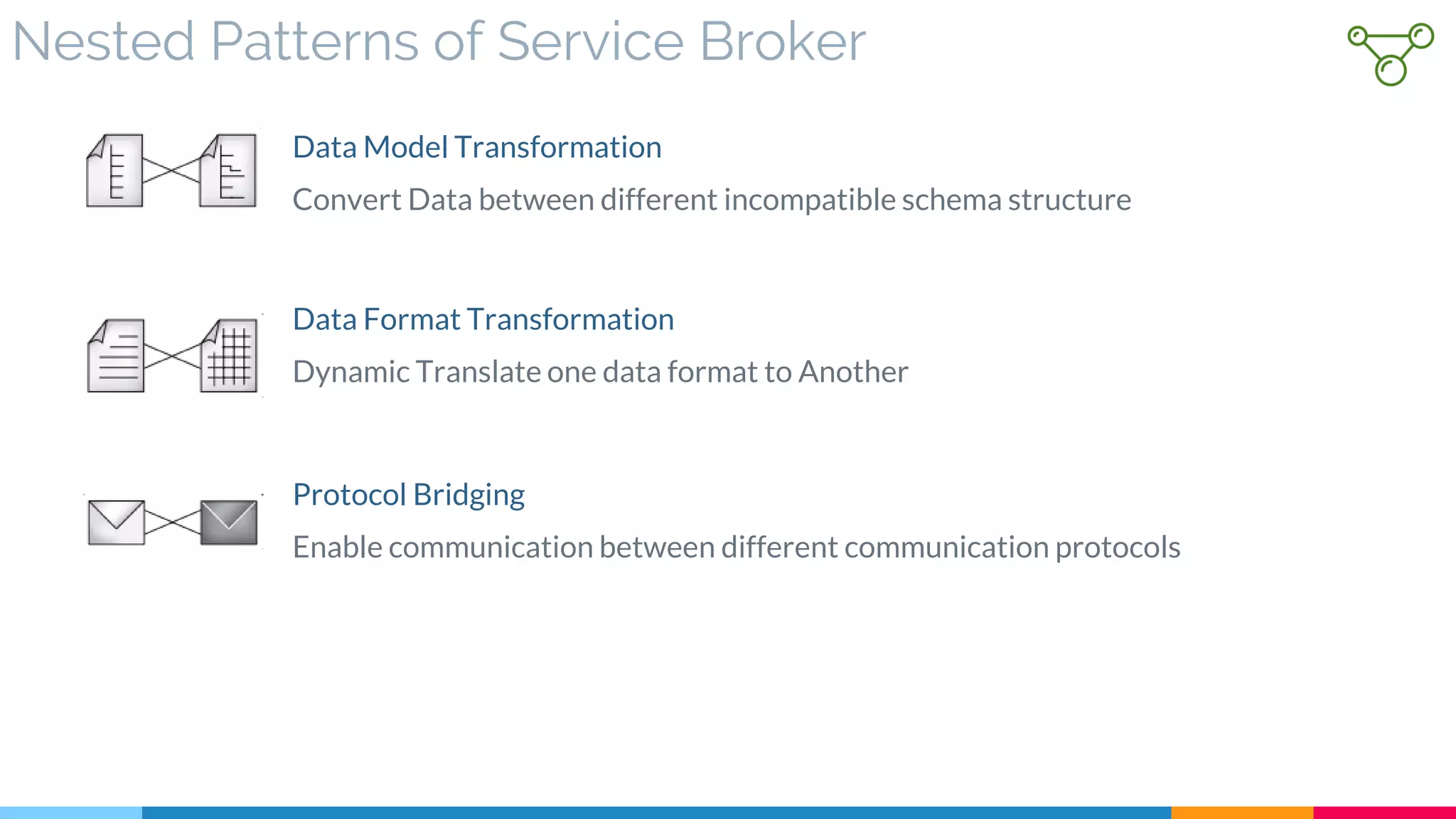
▷ Introduction
▷ Nested Patterns of Service Broker
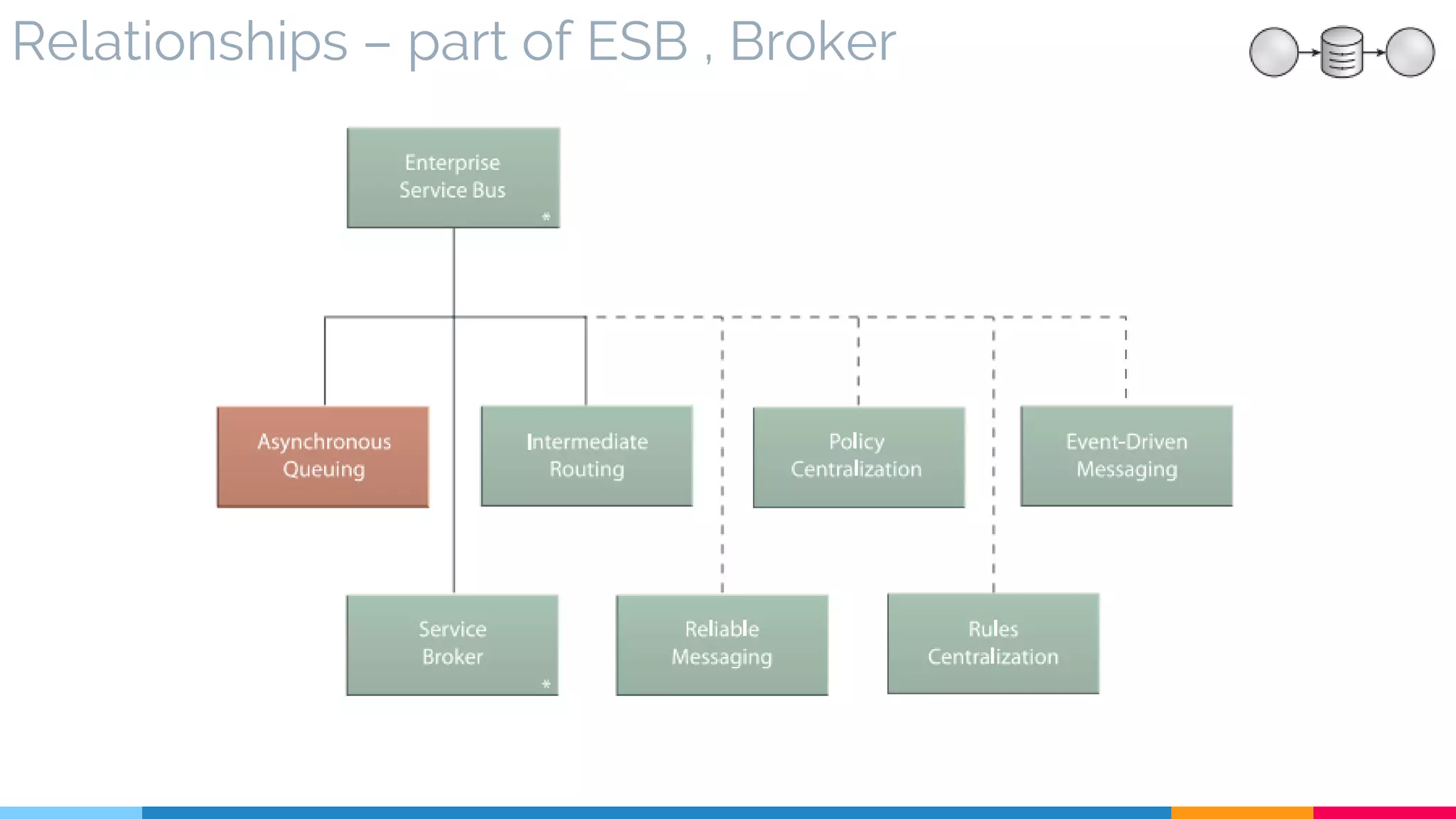
▷ Core Part of ESB
[707]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-11-2048.jpg)
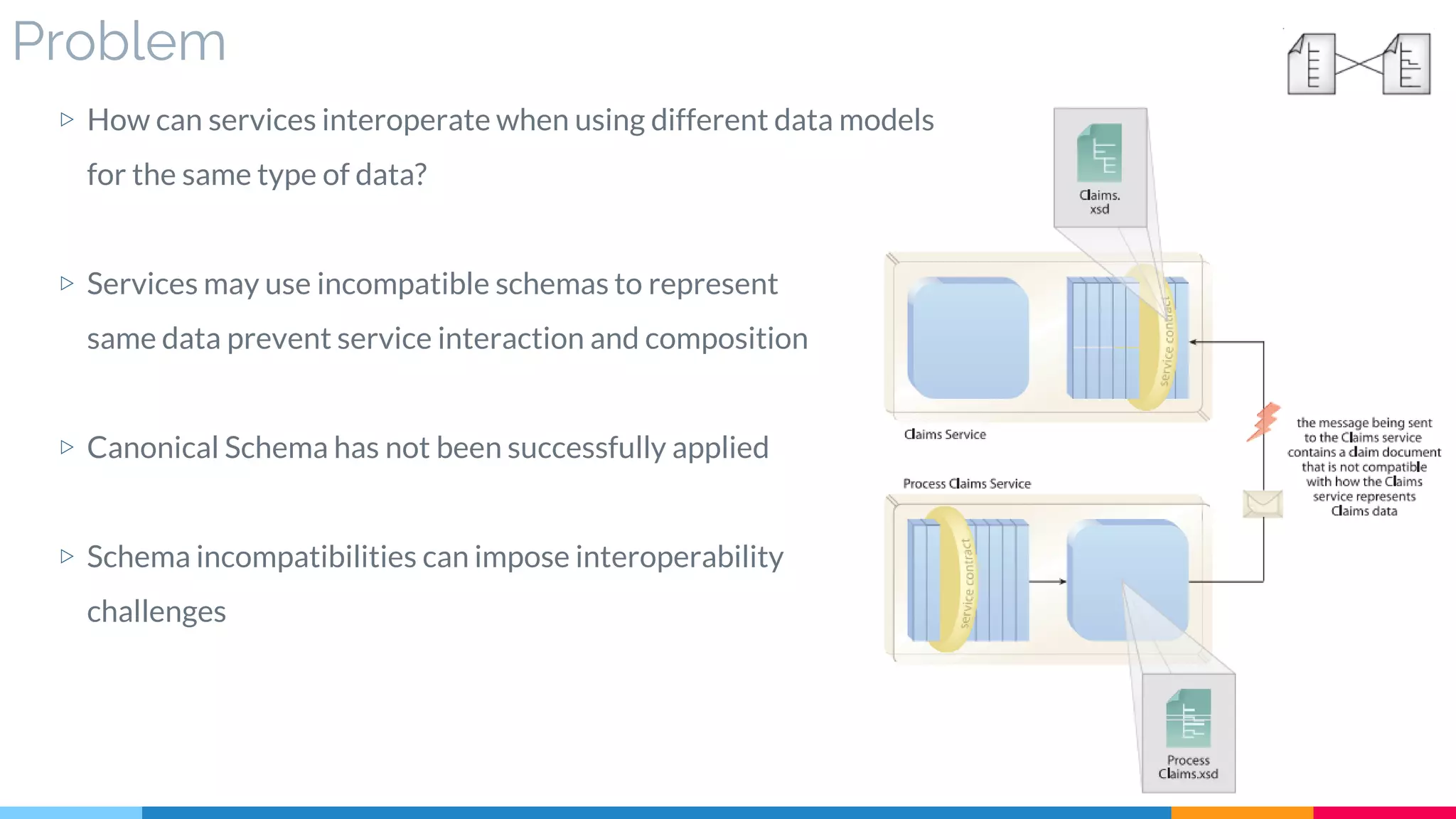
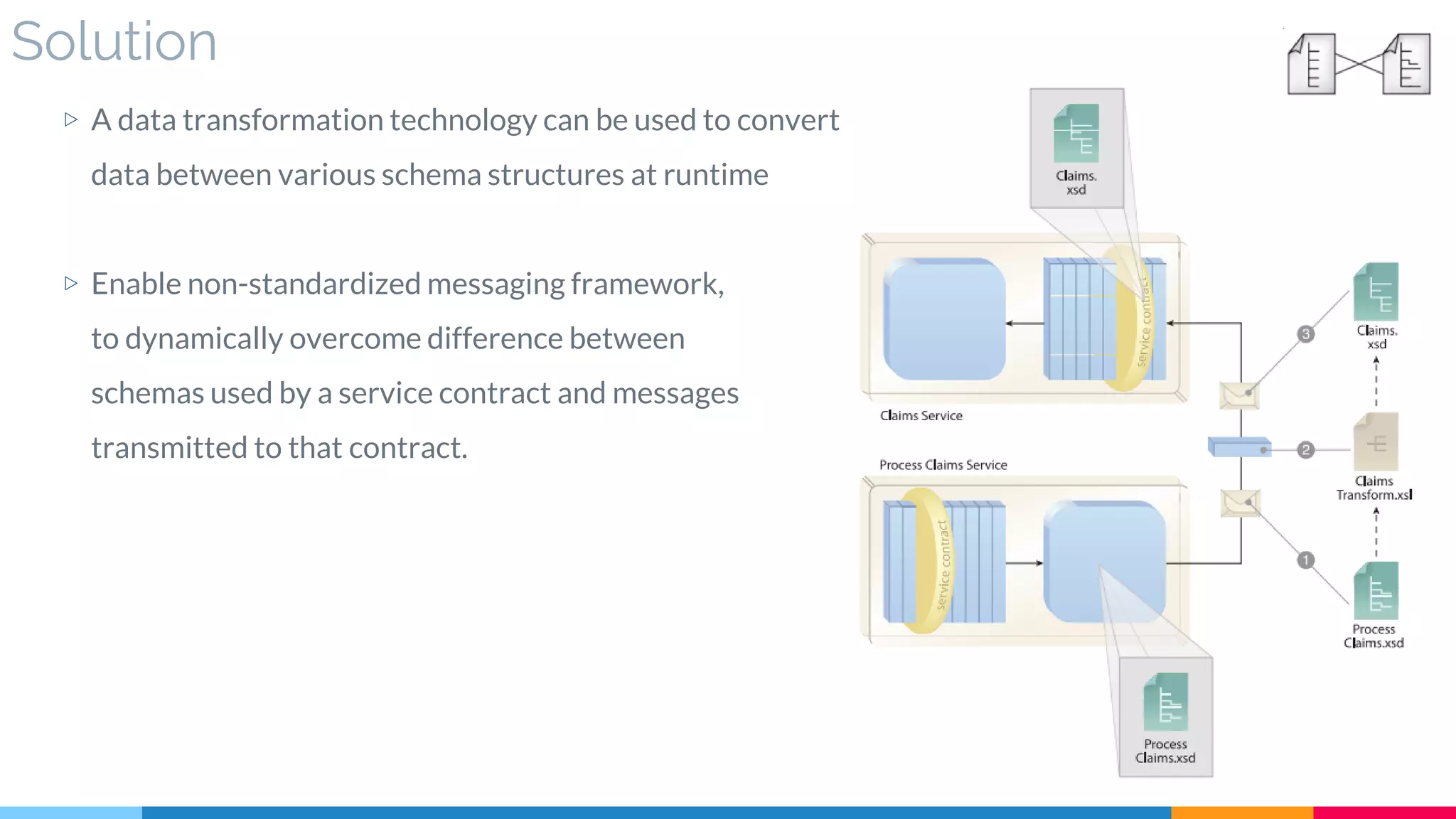
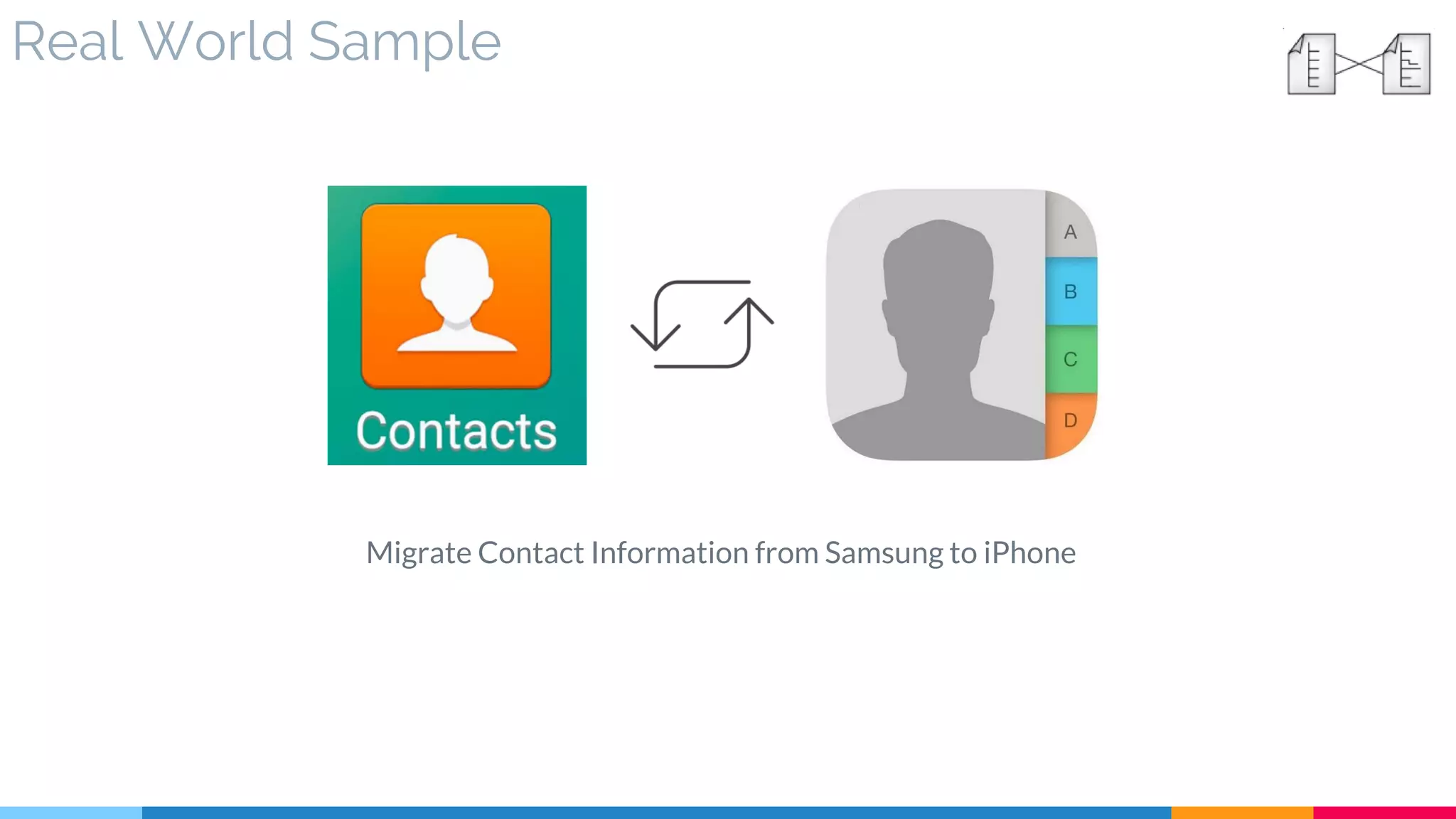
![3 Data Model Transformation
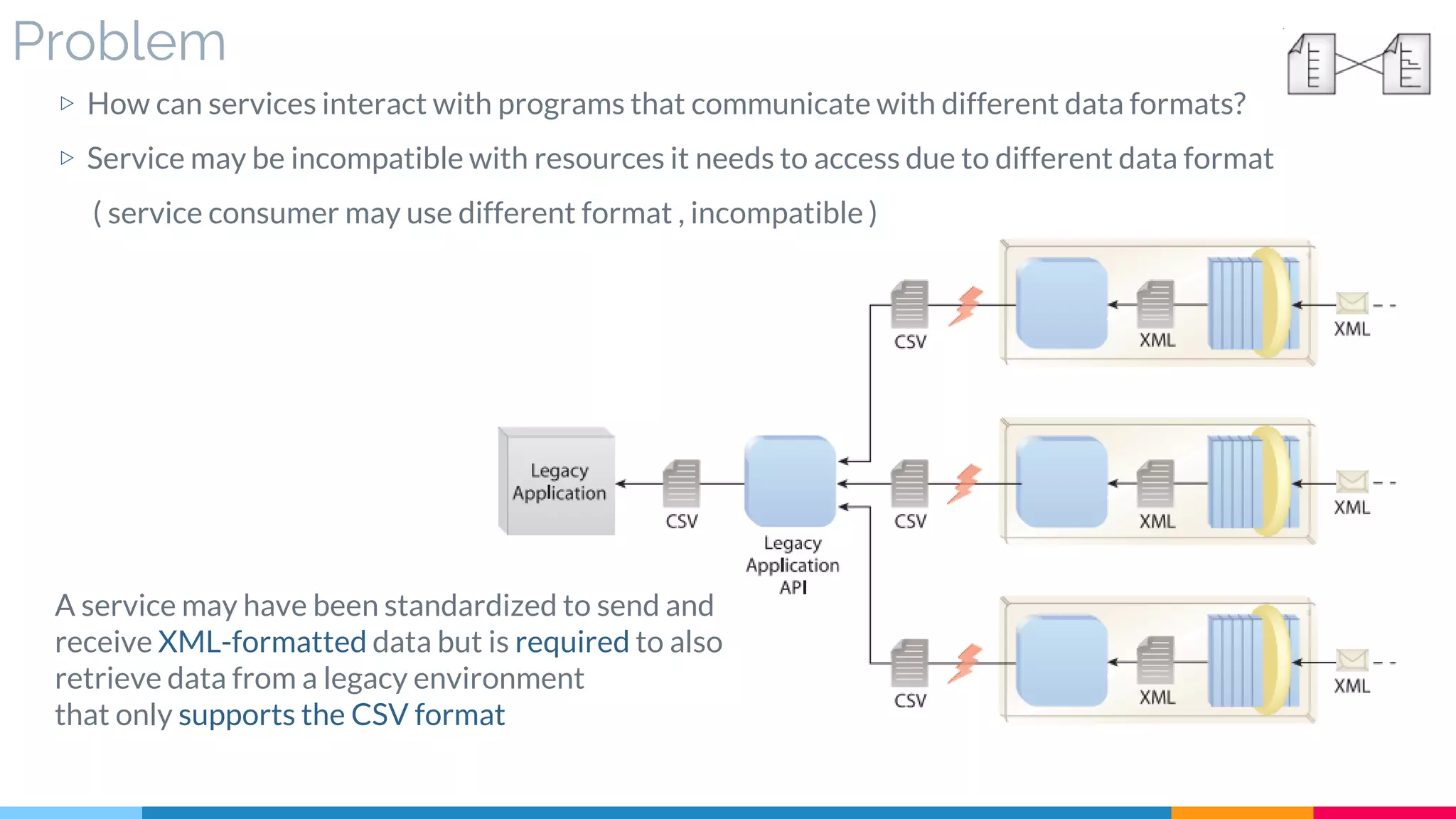
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
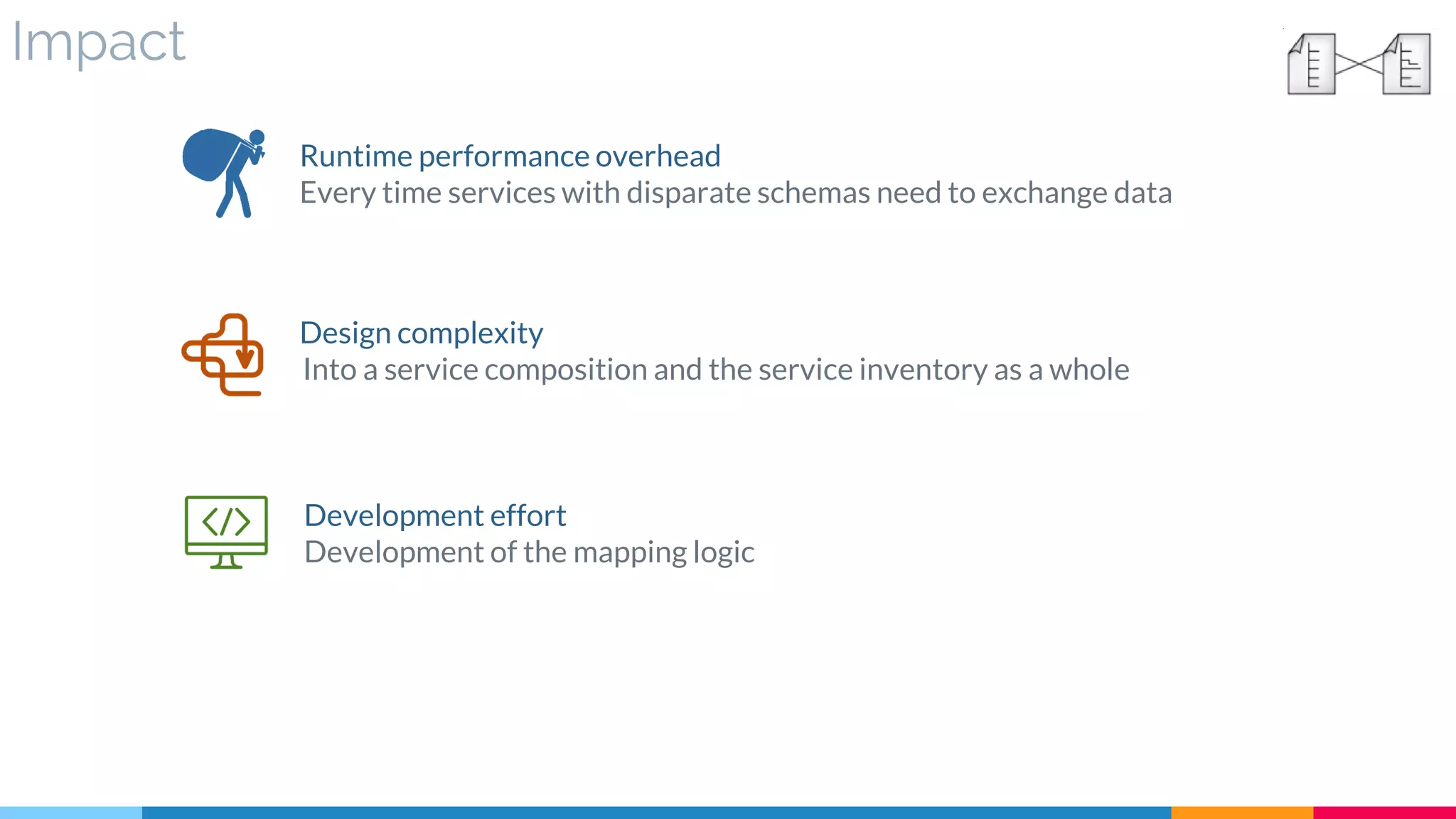
▷ Impact
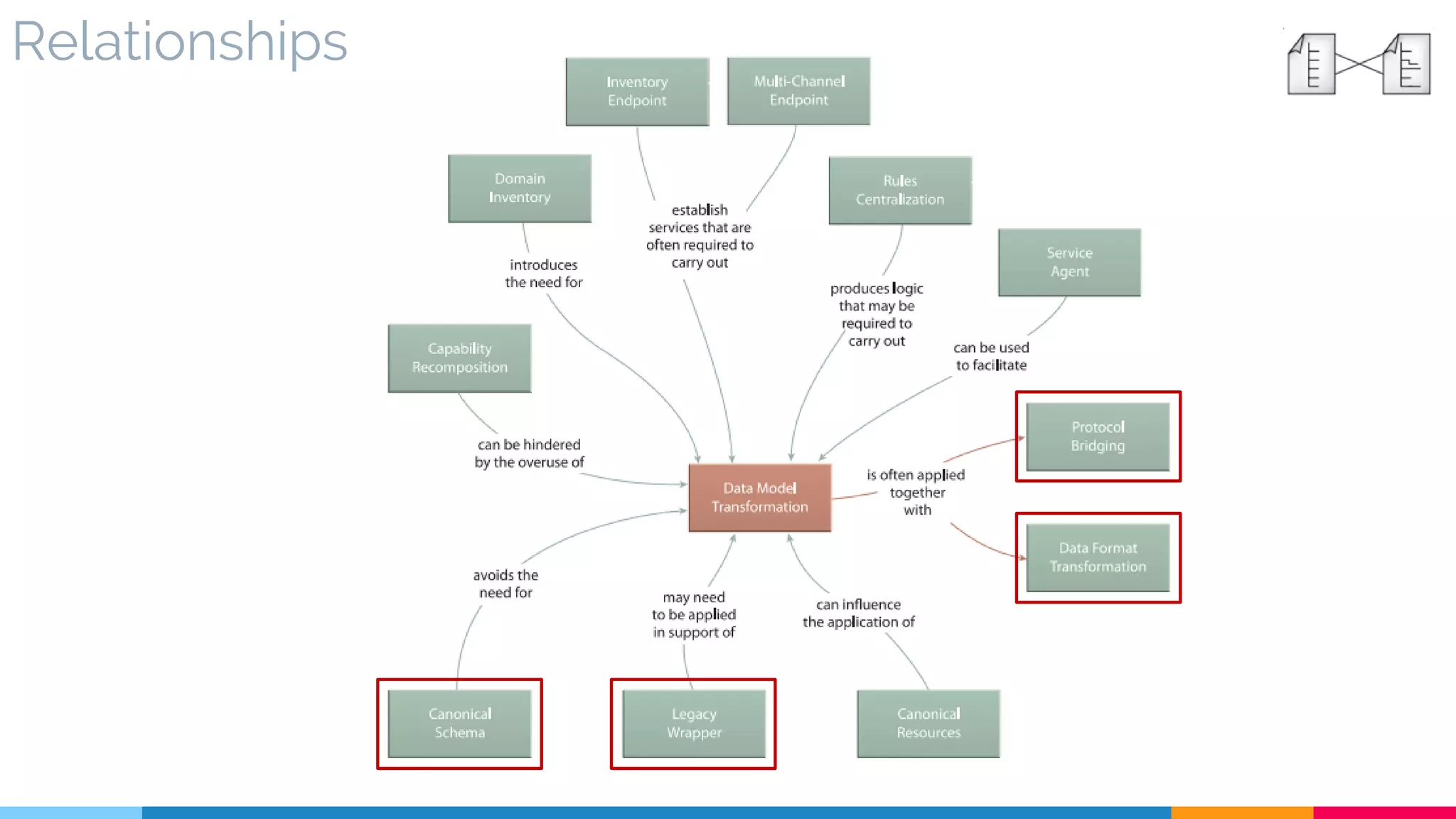
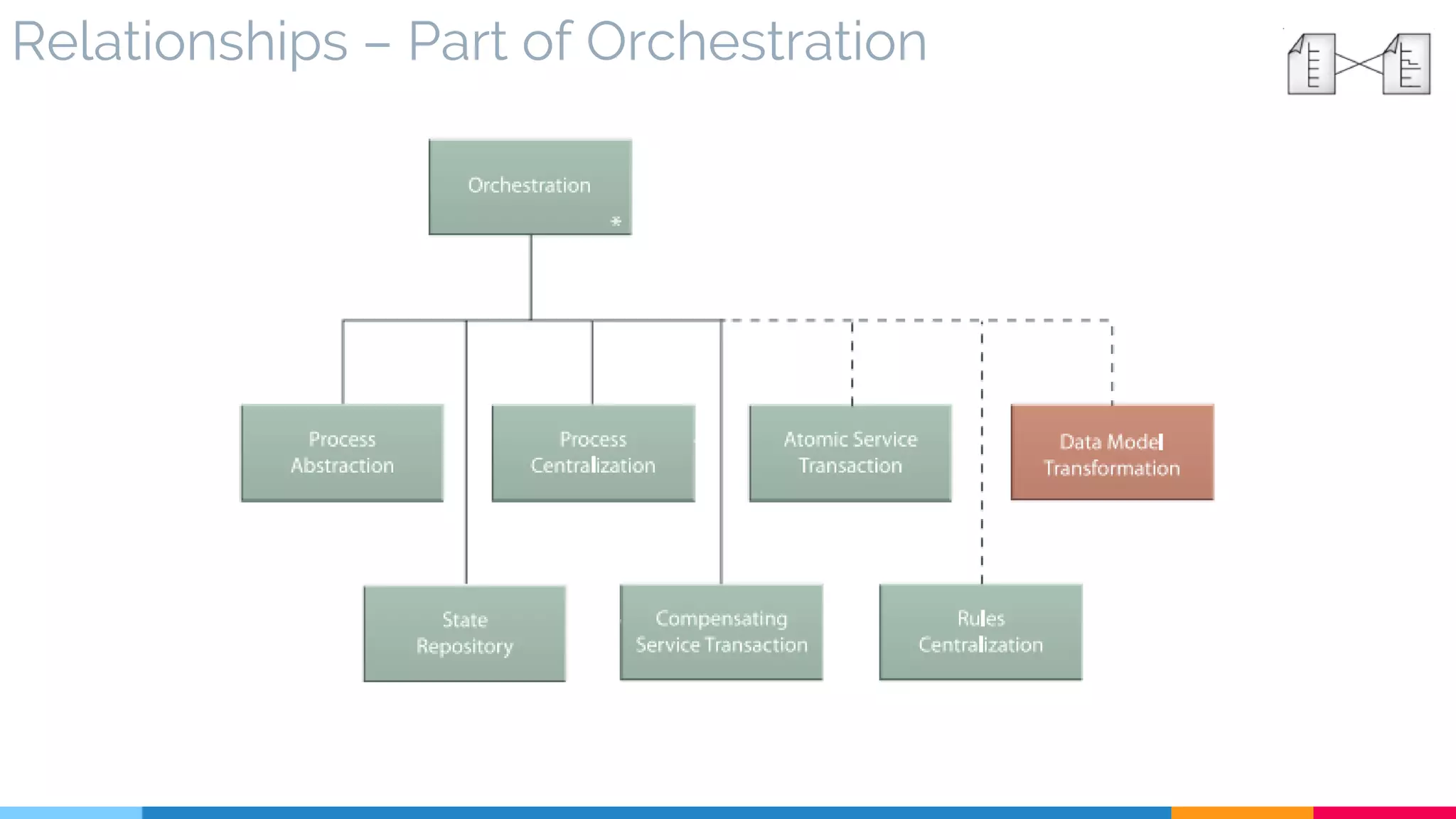
▷ Relationships
[671]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-15-2048.jpg)


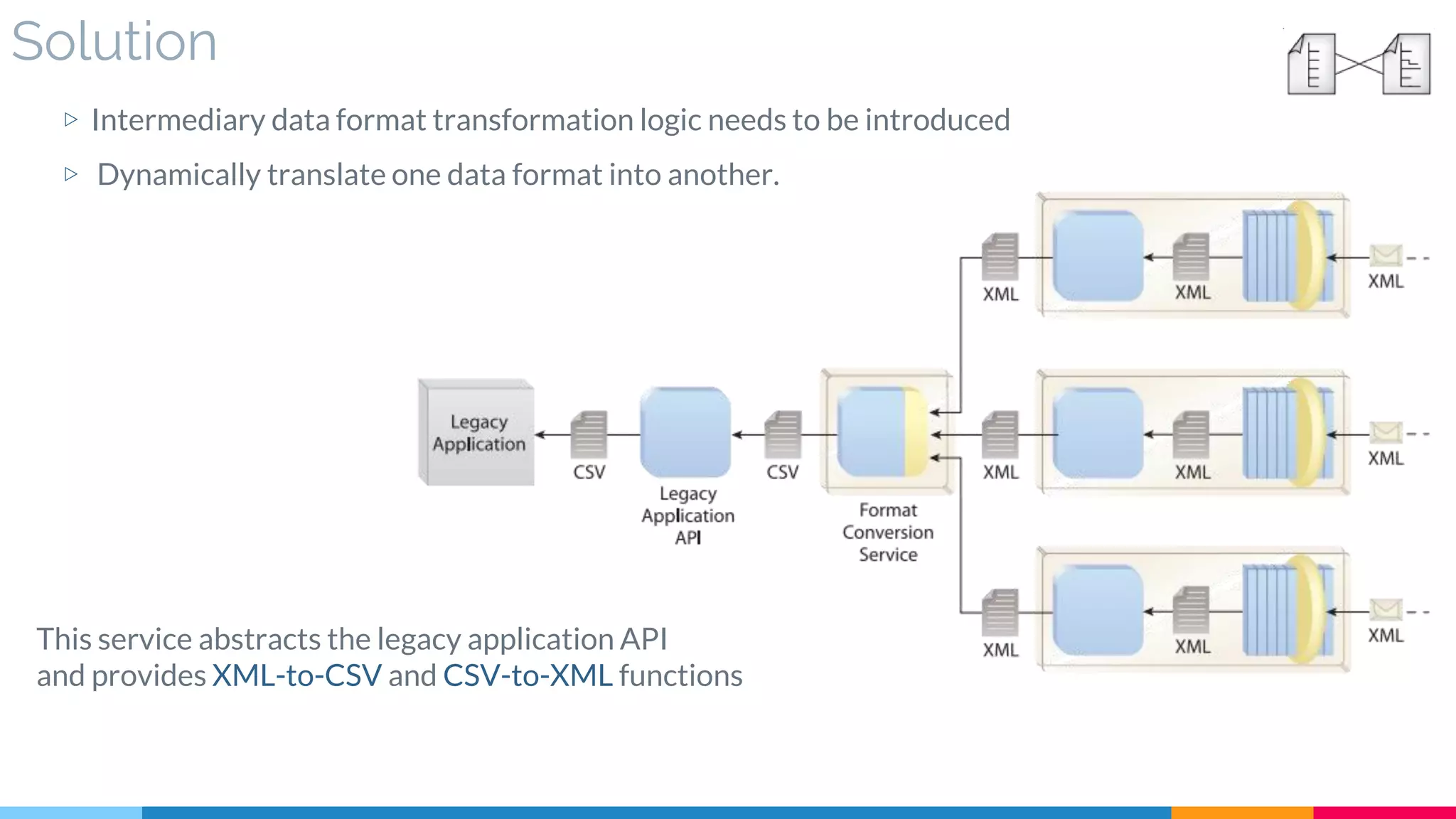
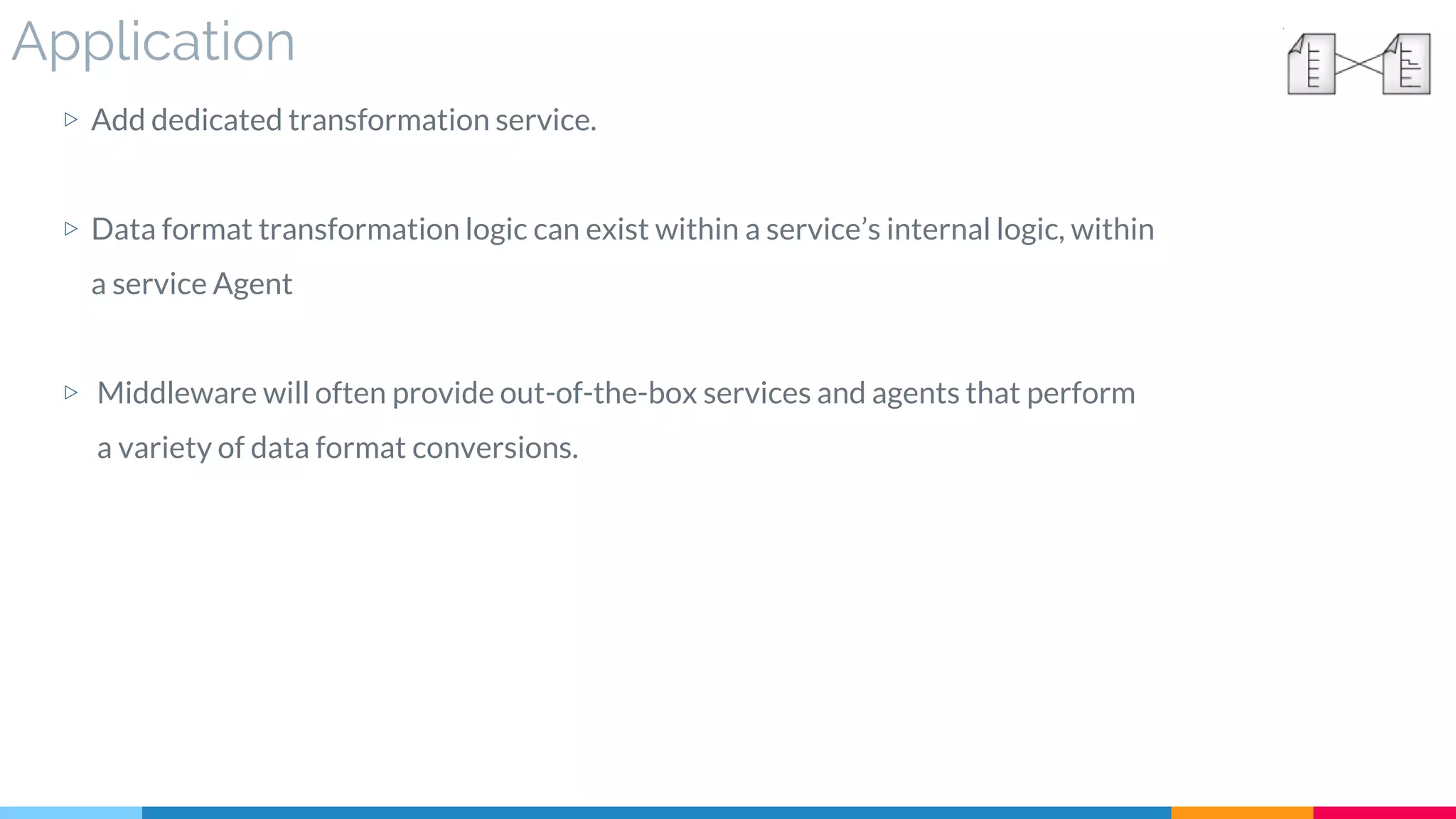
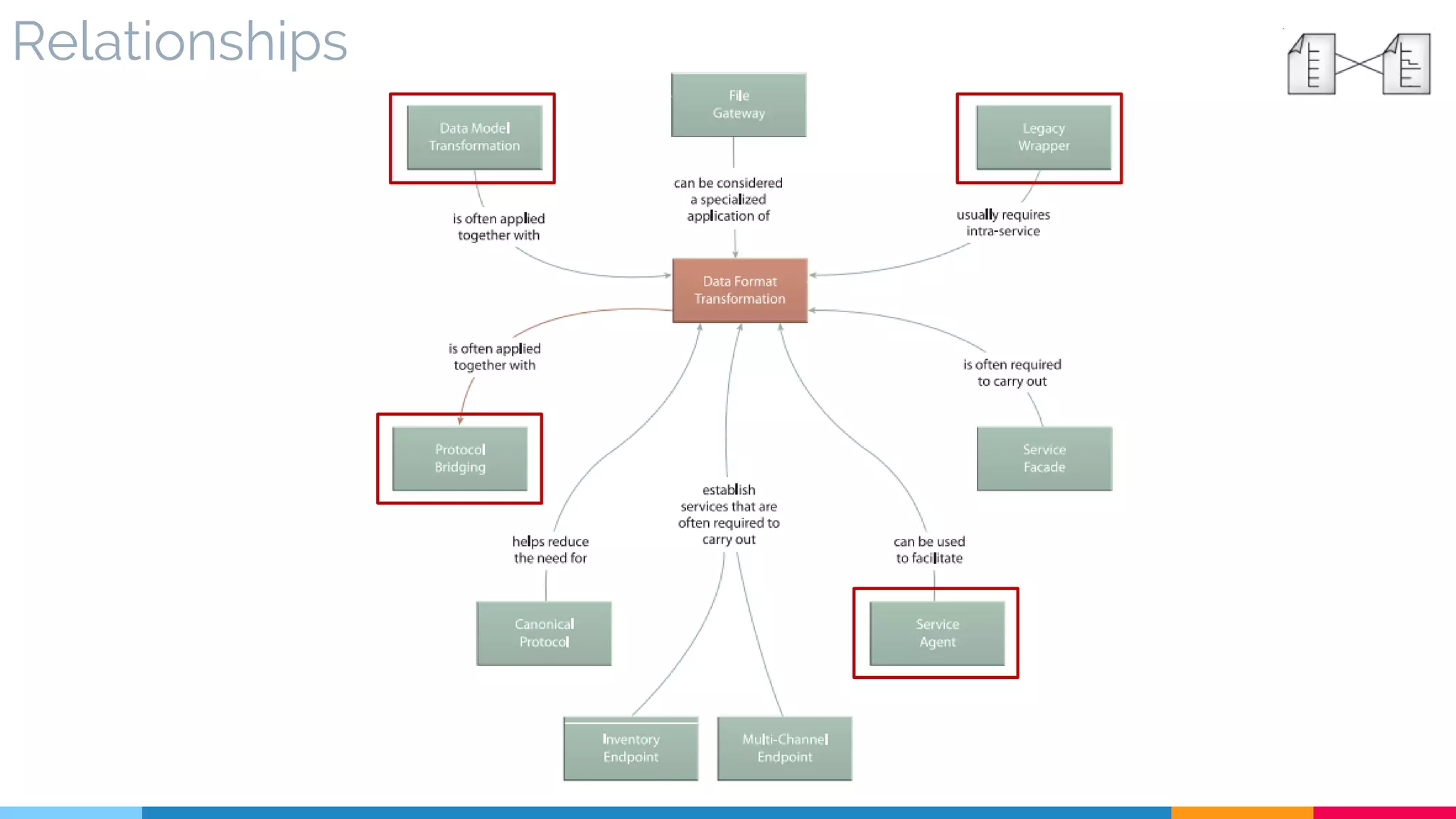
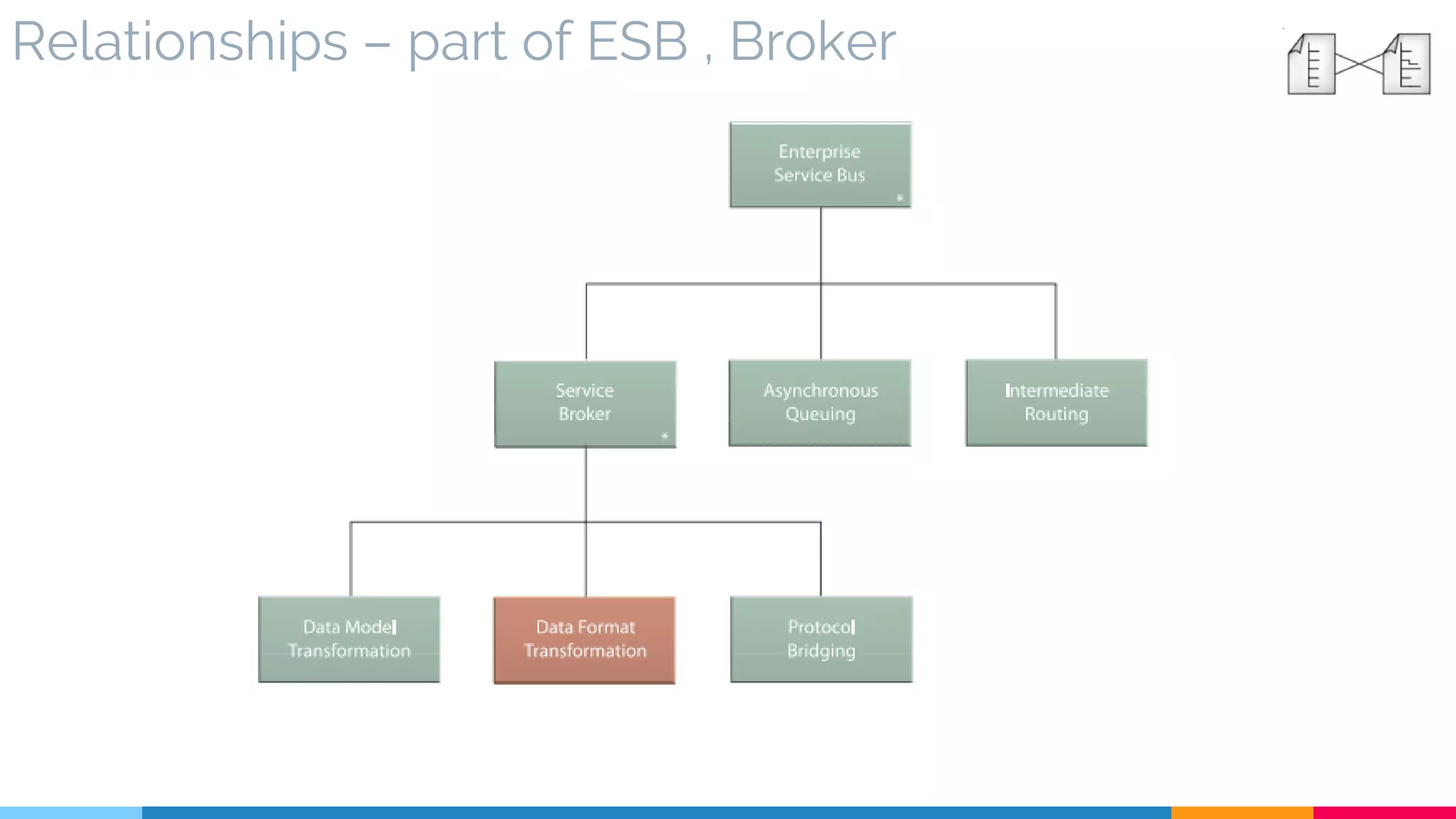
![4 Data Format Transformation
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[681]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-24-2048.jpg)


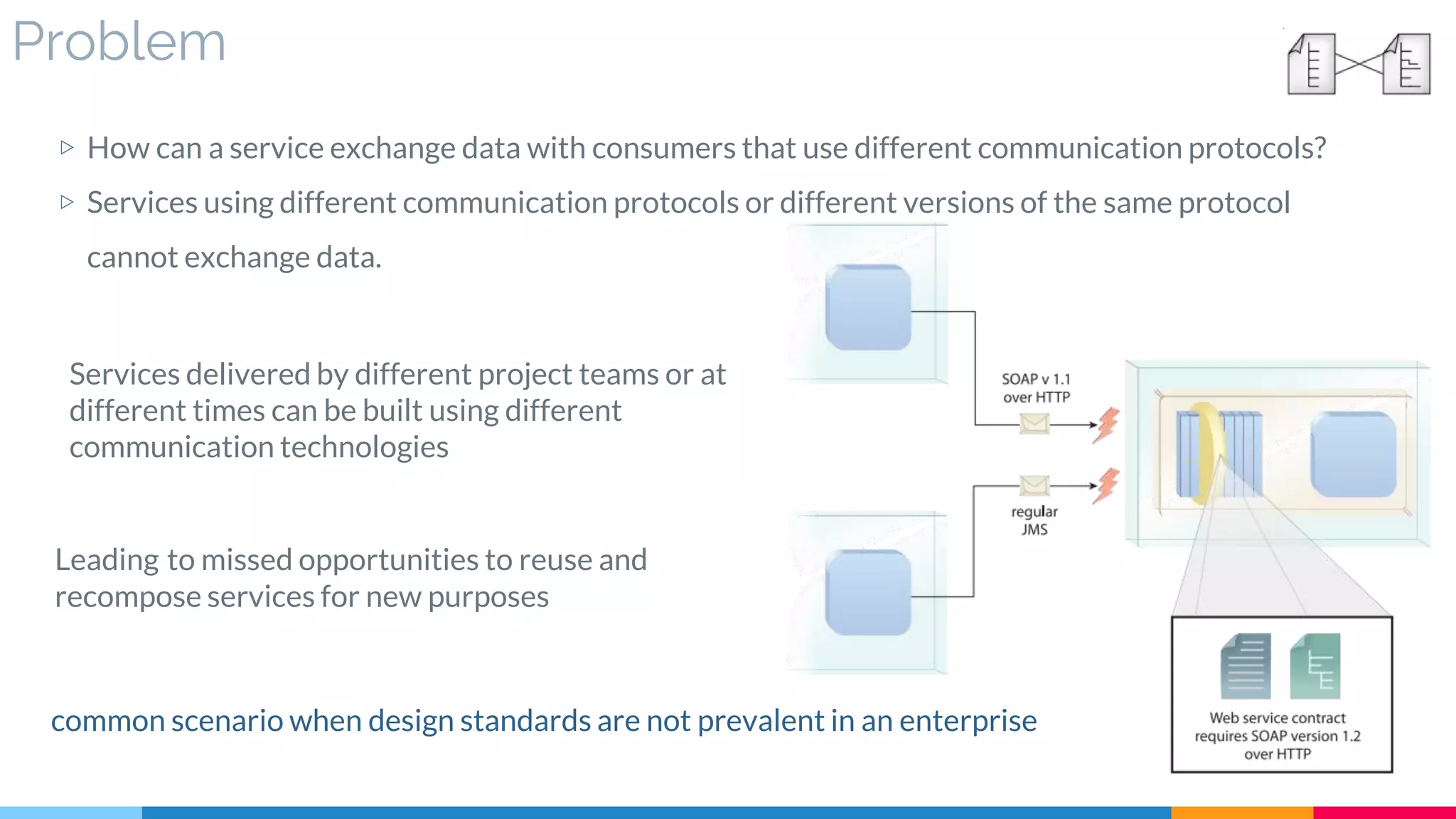
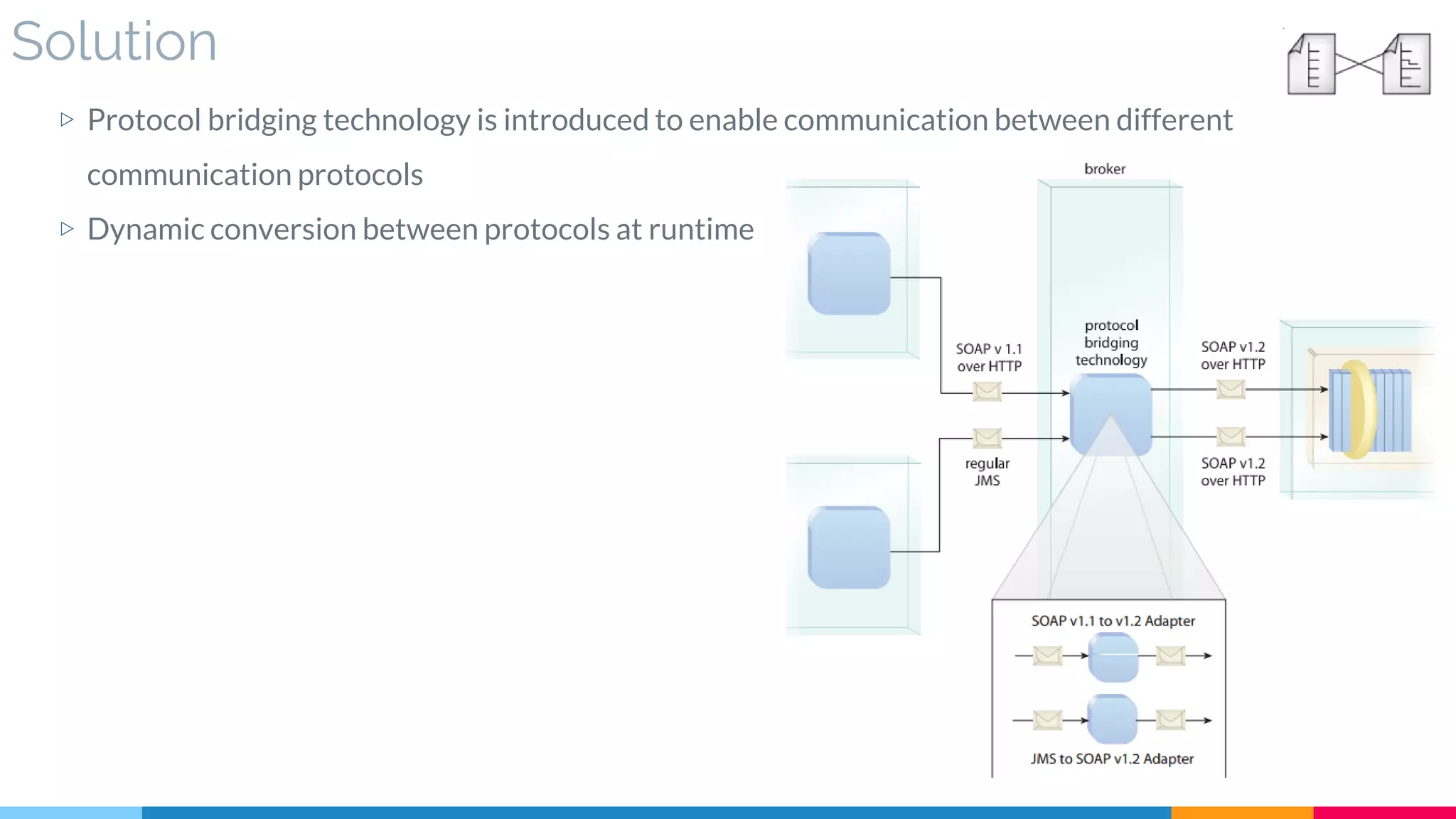
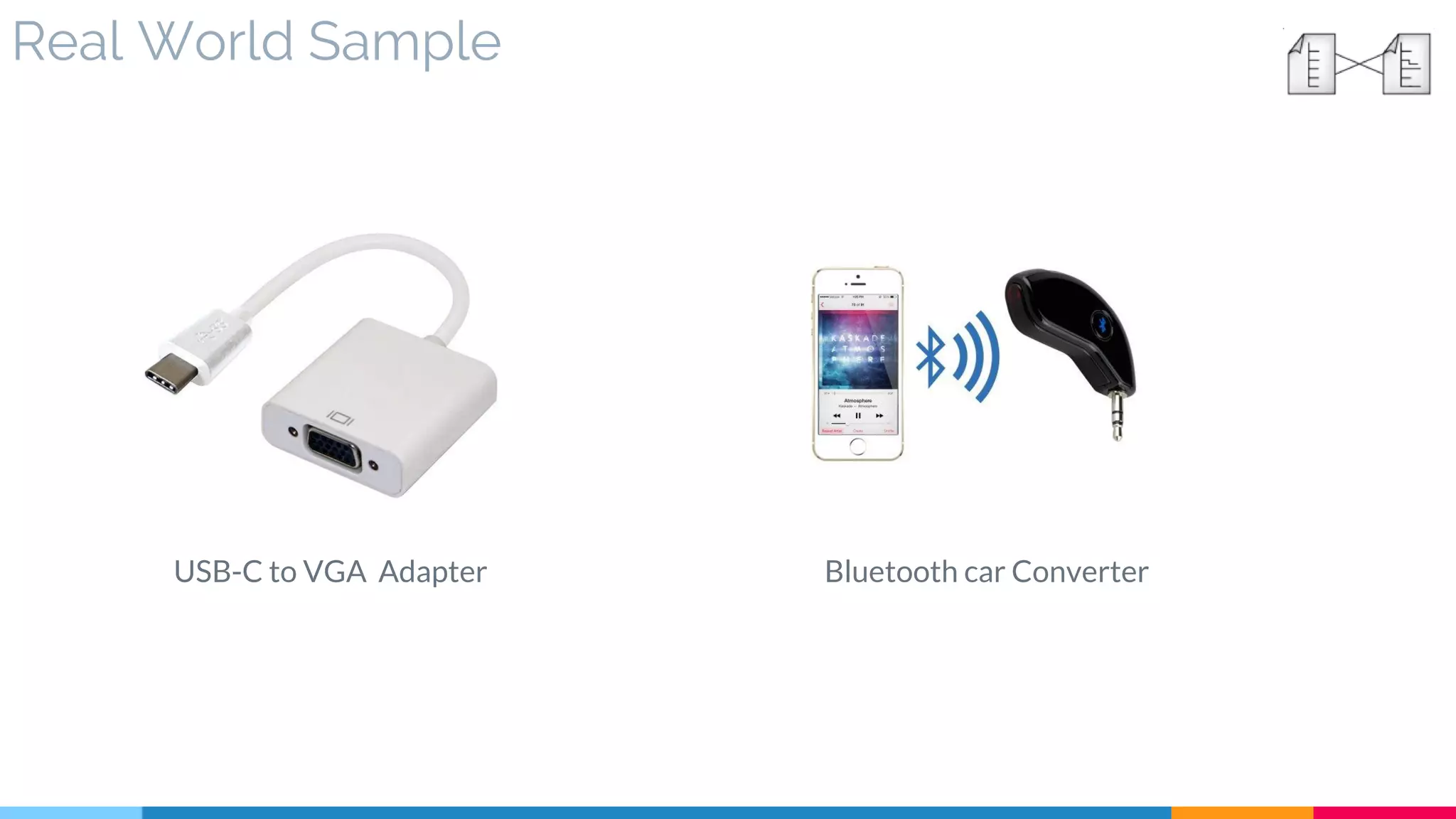
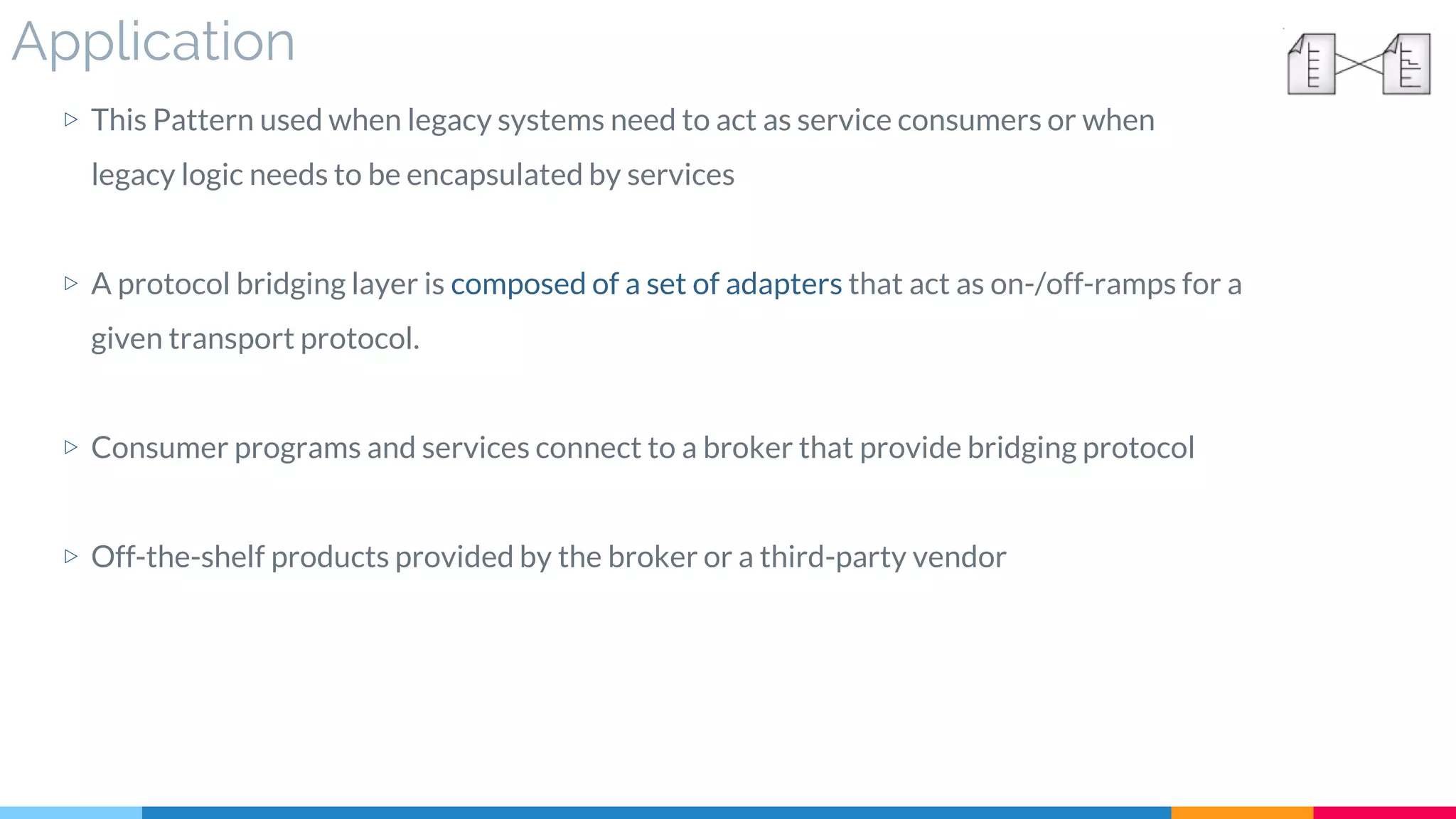
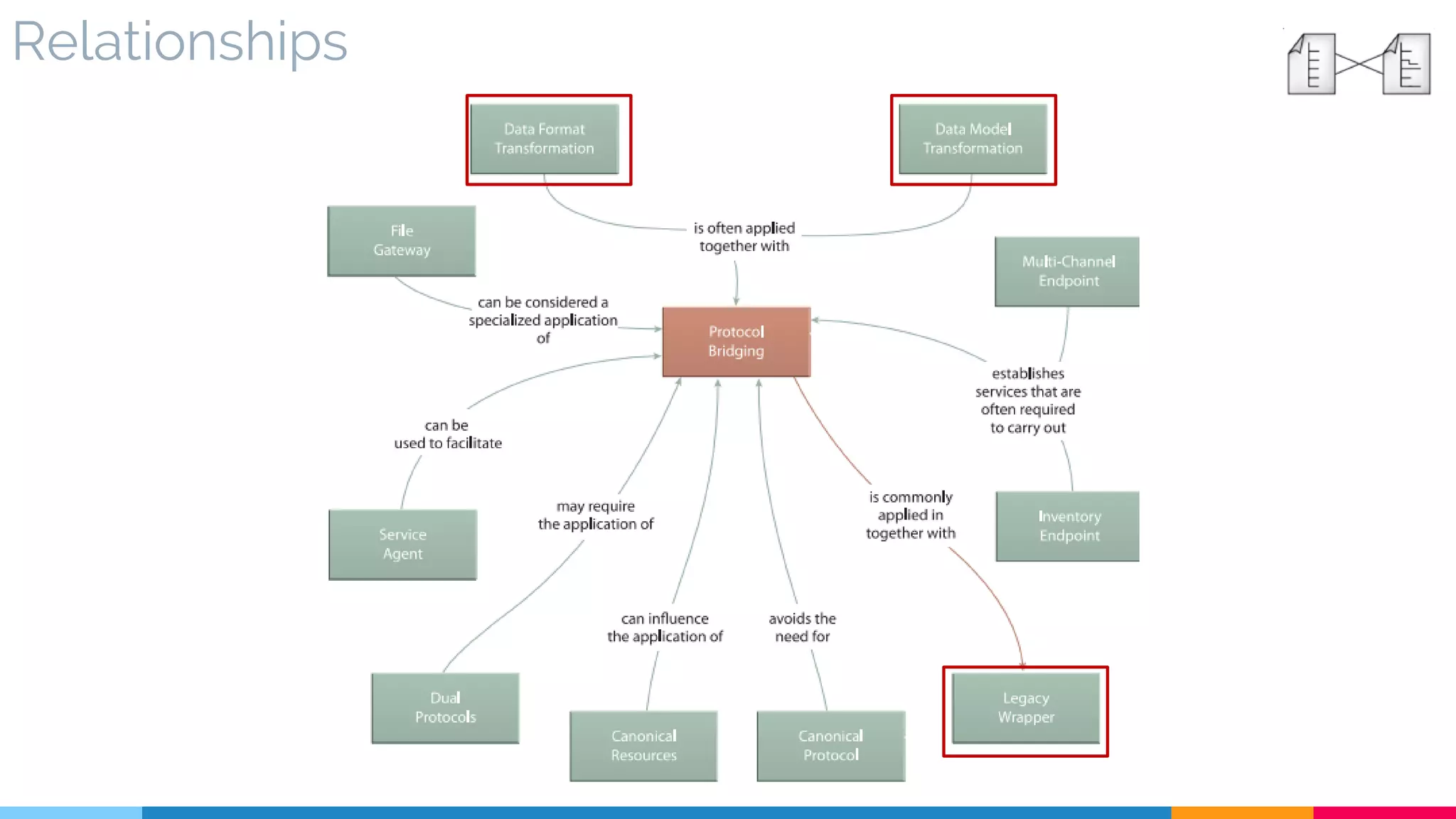
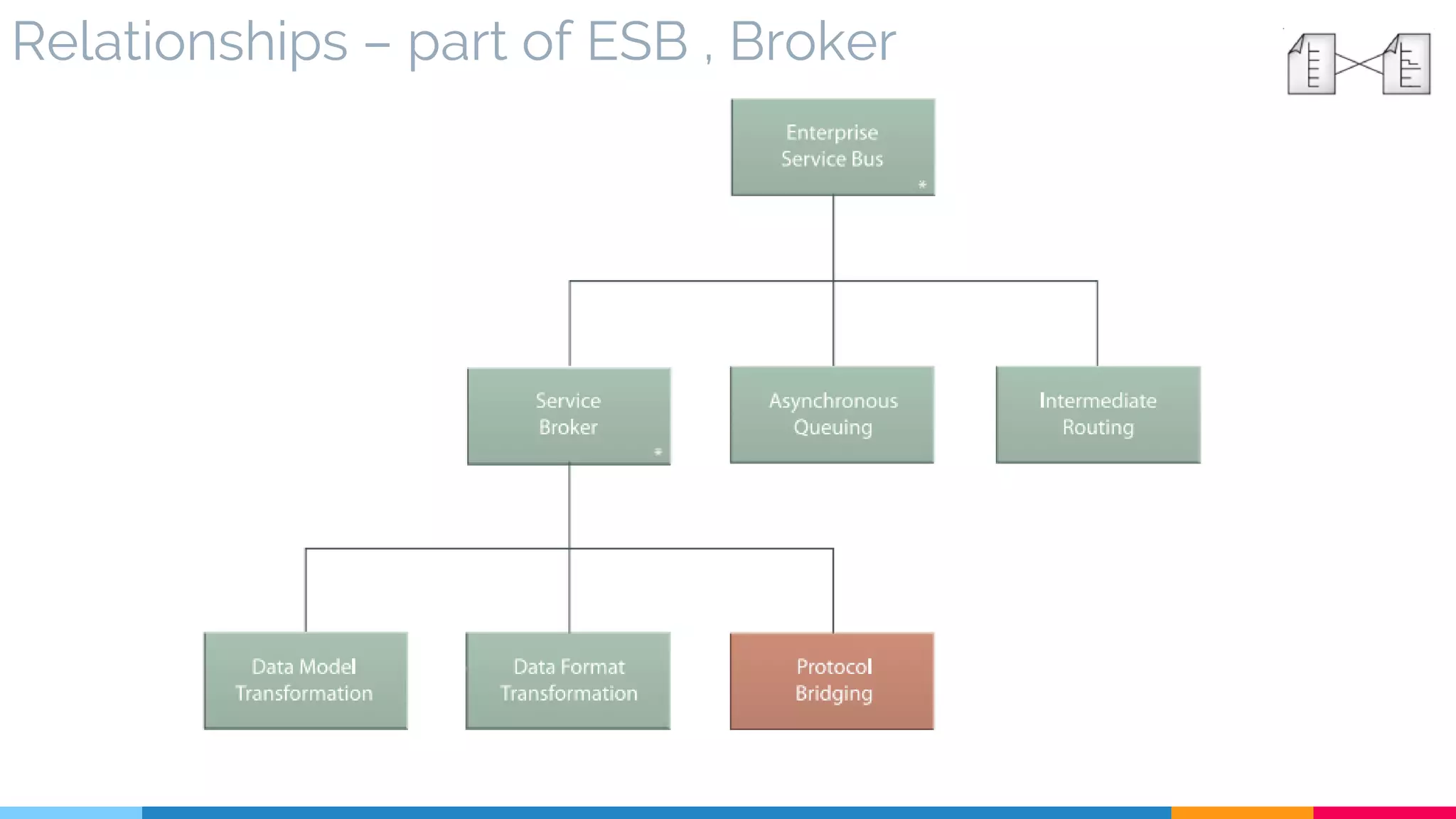
![5 Protocol Bridging
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[687]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-32-2048.jpg)

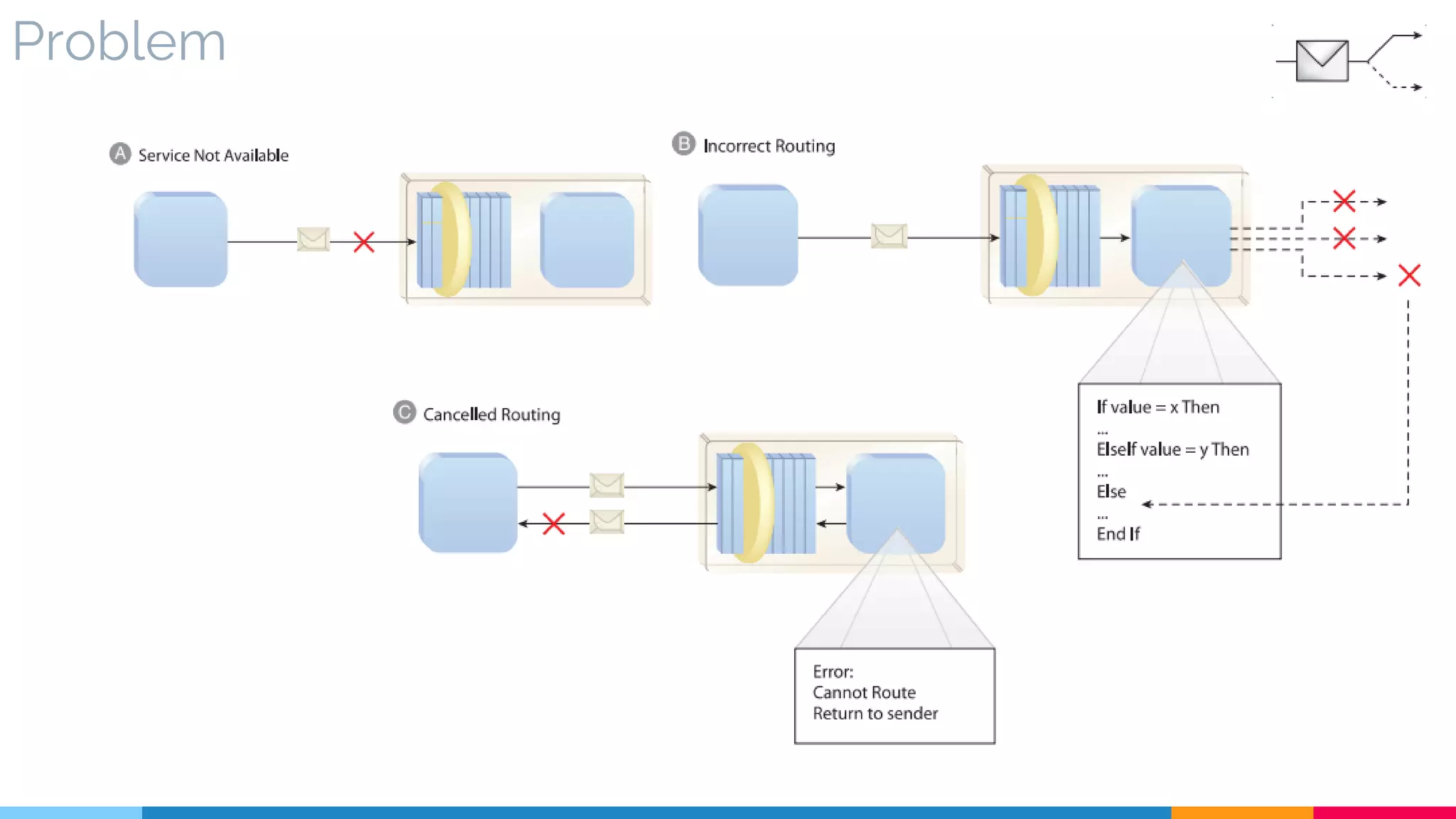
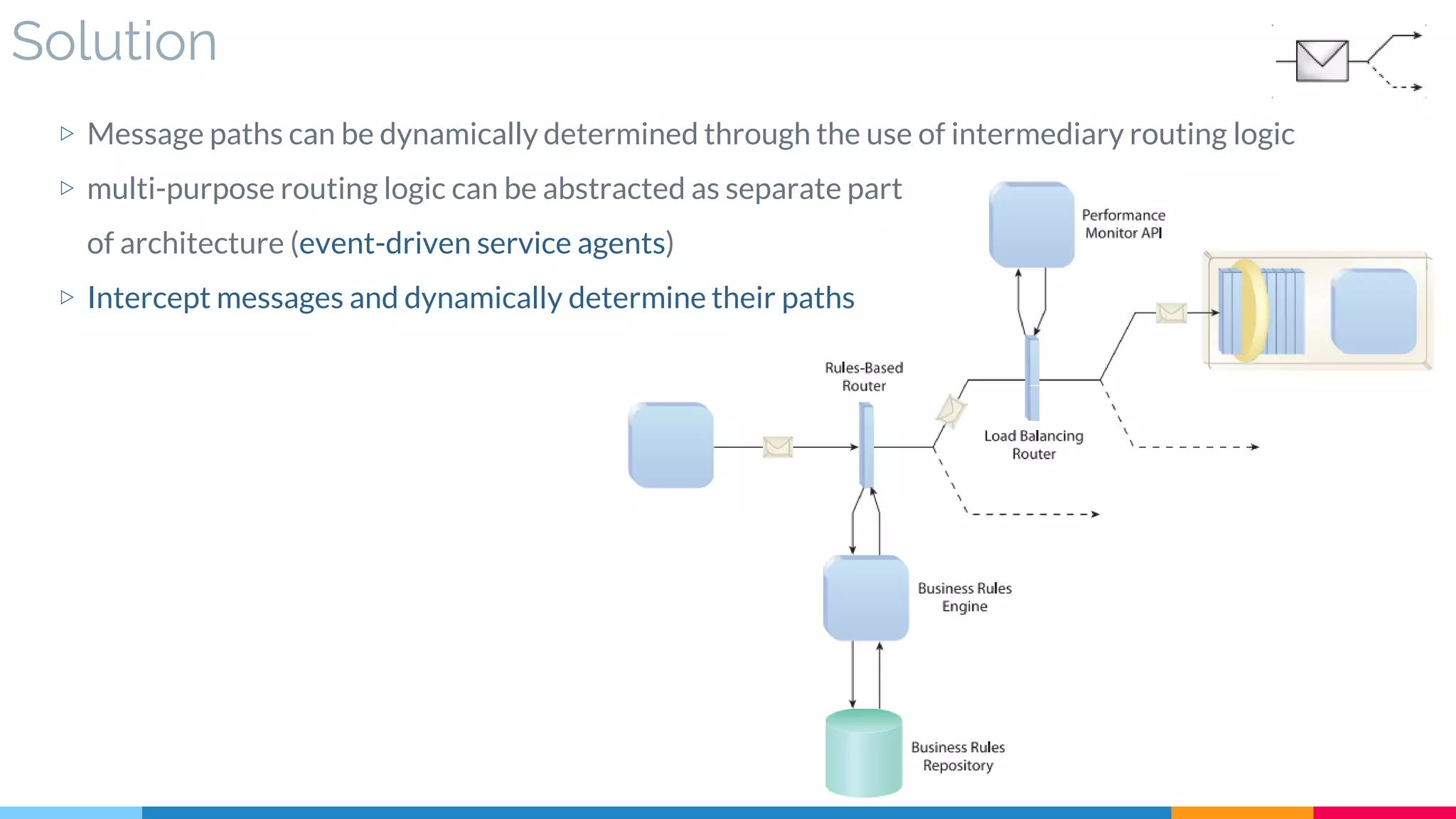
![6 Intermediate Routing
▷ Problem
▷ Solution
▷ Real World Sample
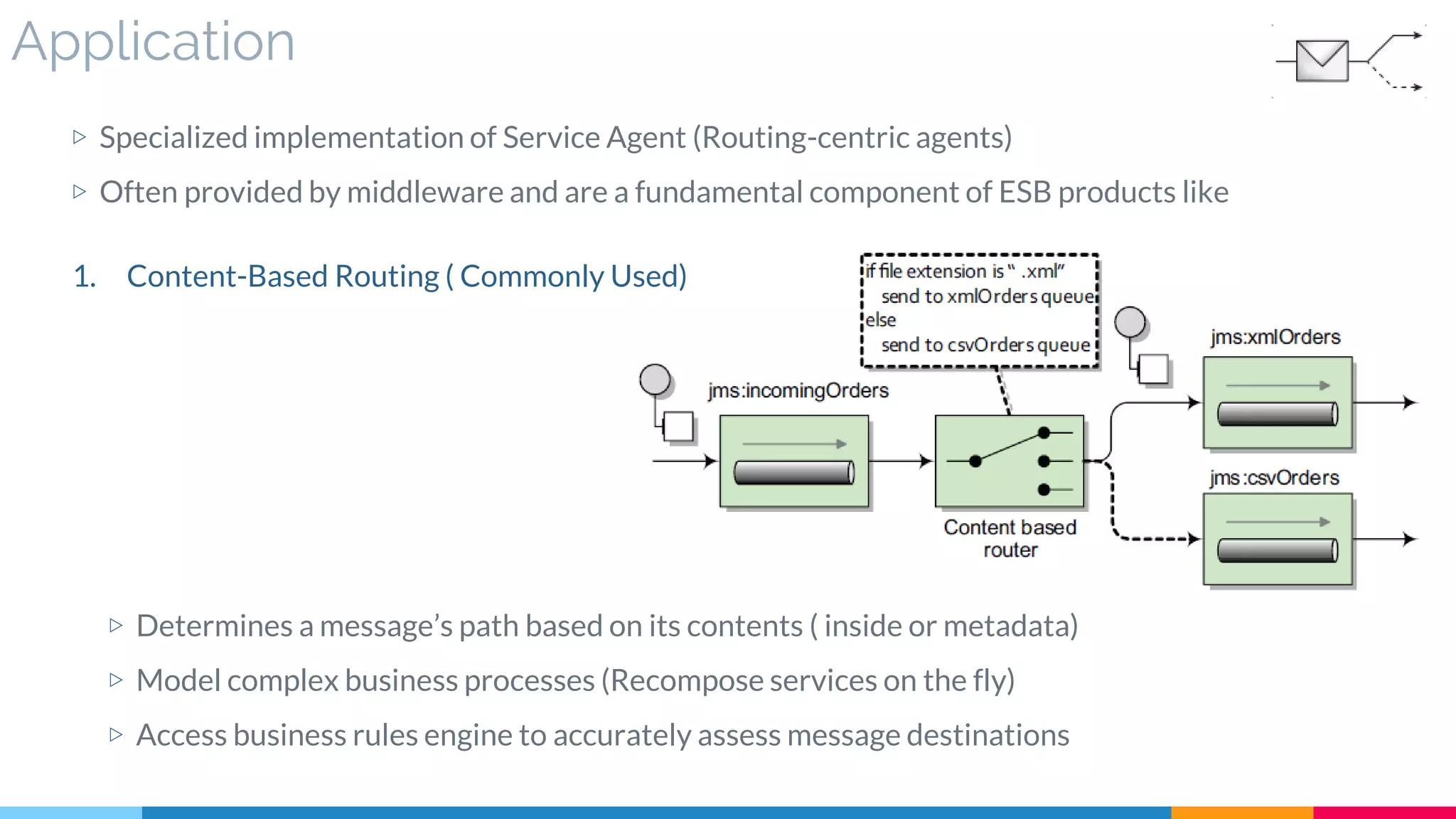
▷ Application
▷ Impact
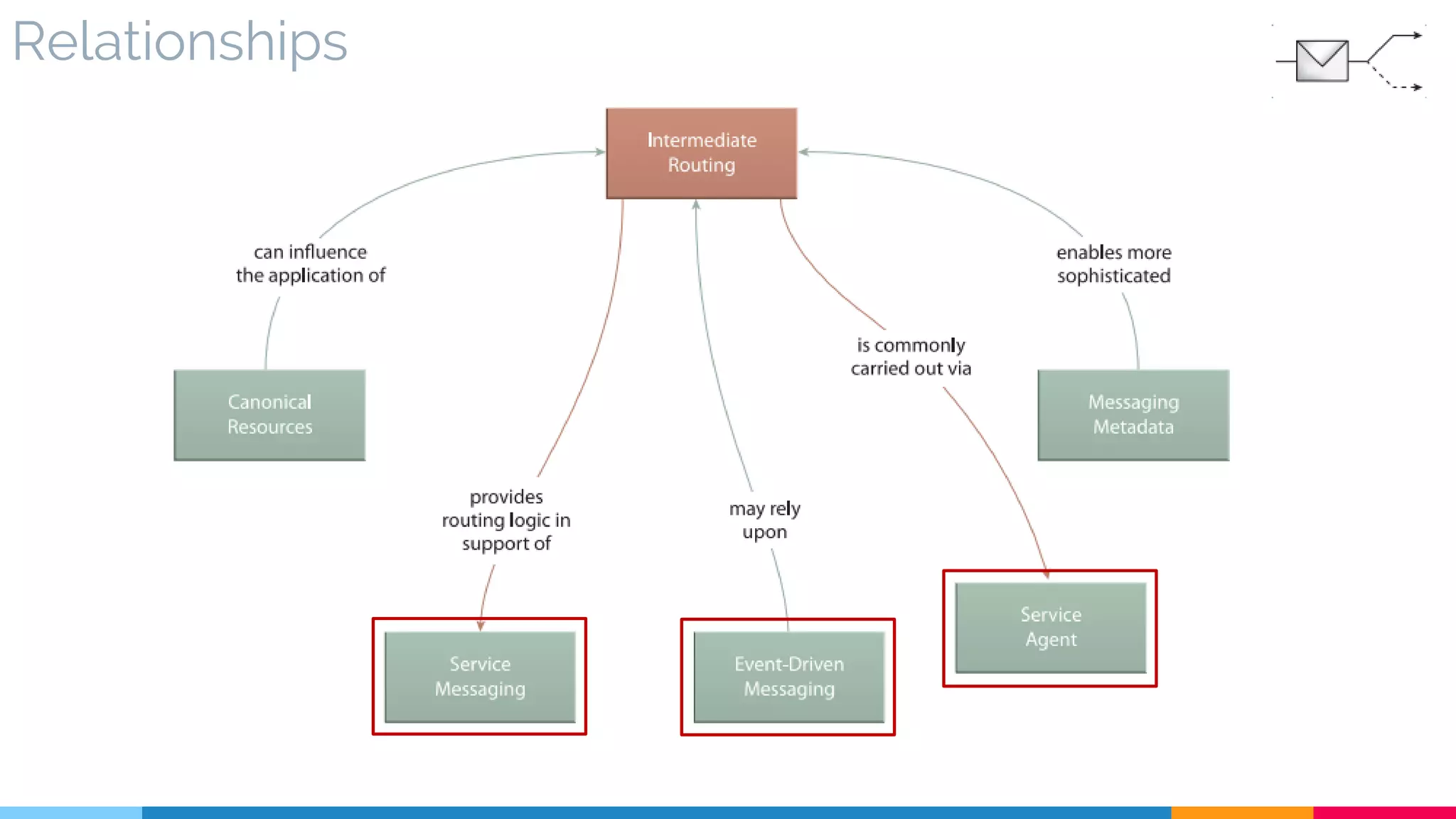
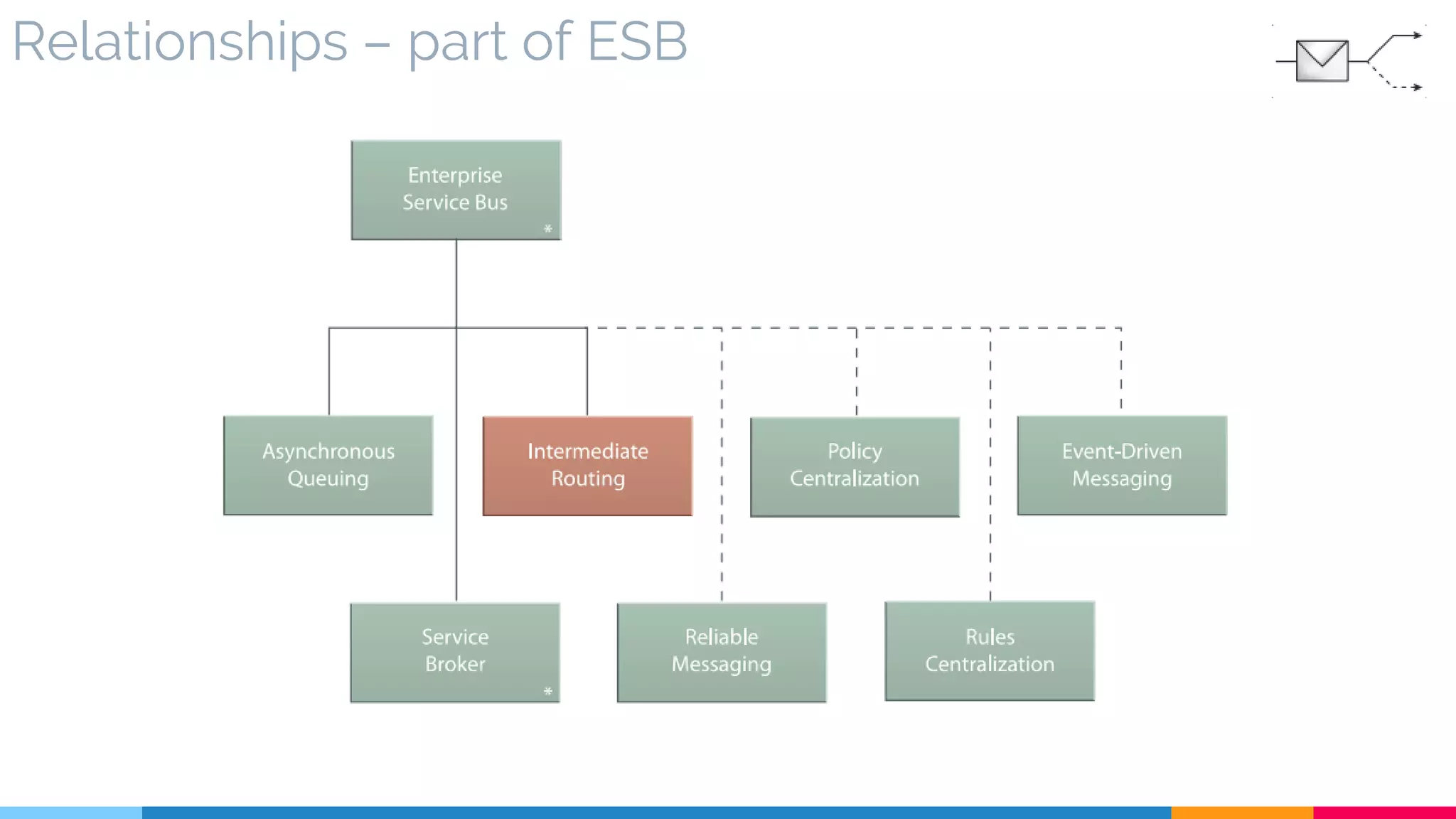
▷ Relationships
[549]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-40-2048.jpg)



![7 Asynchronous Queue
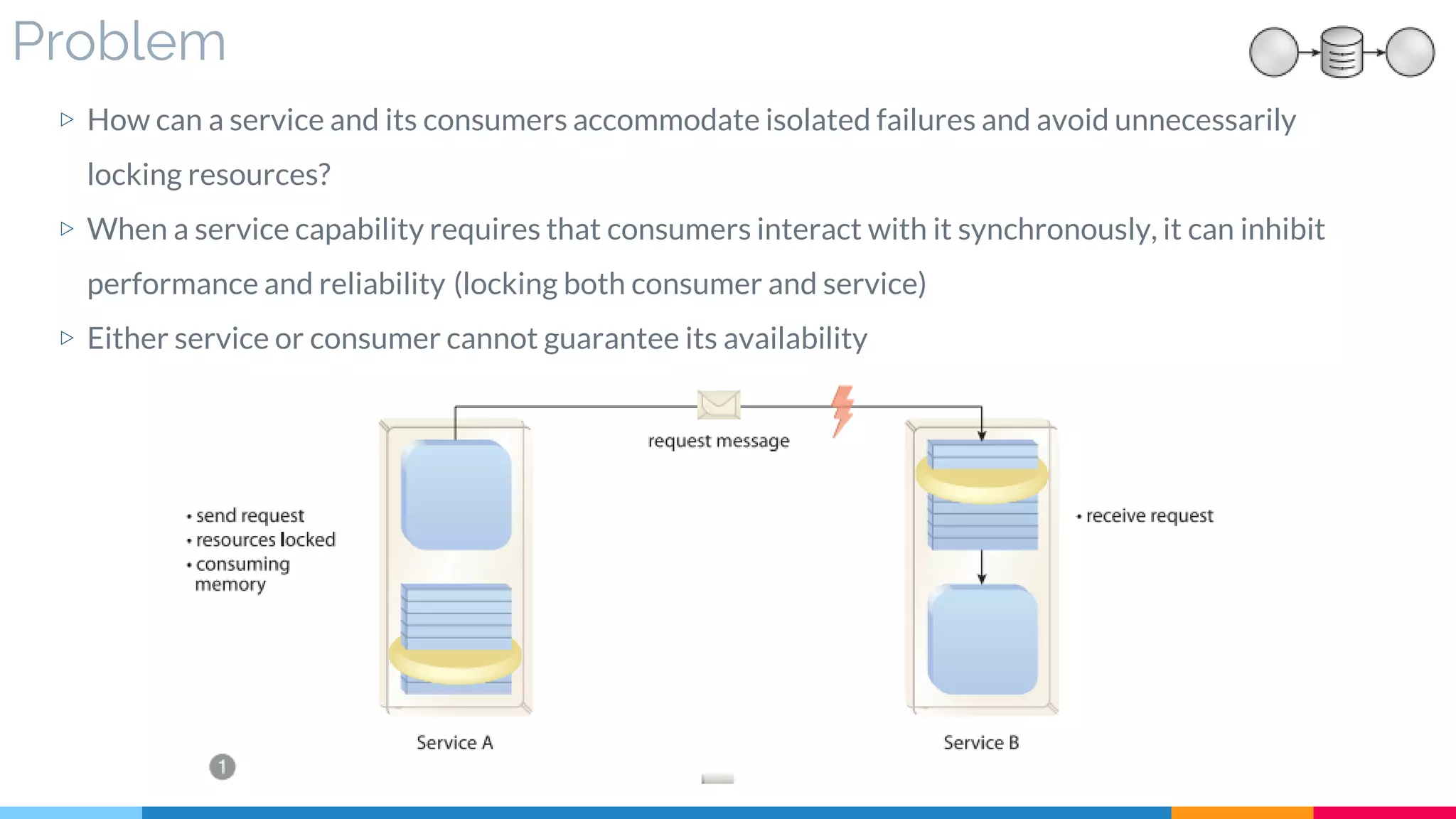
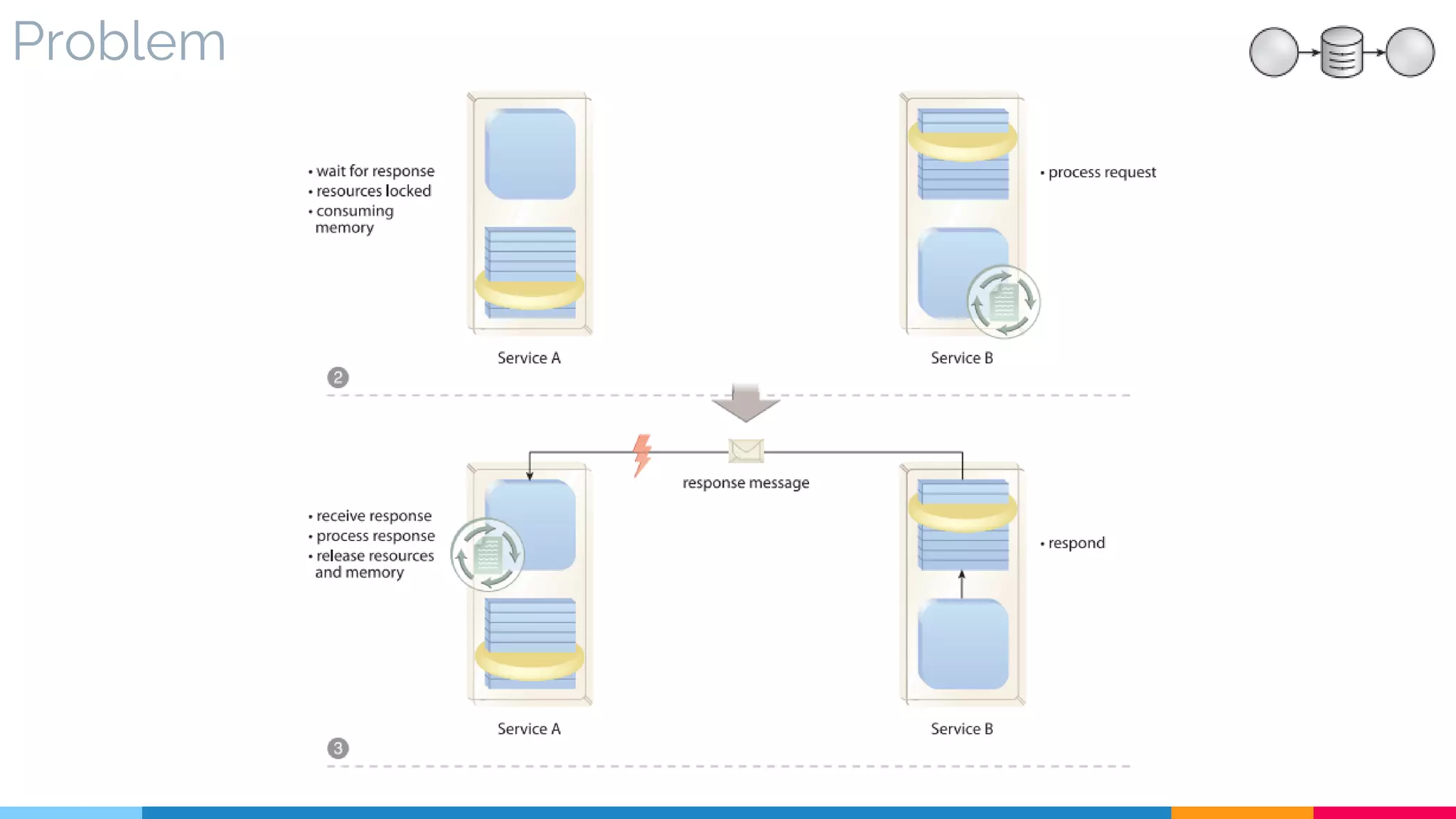
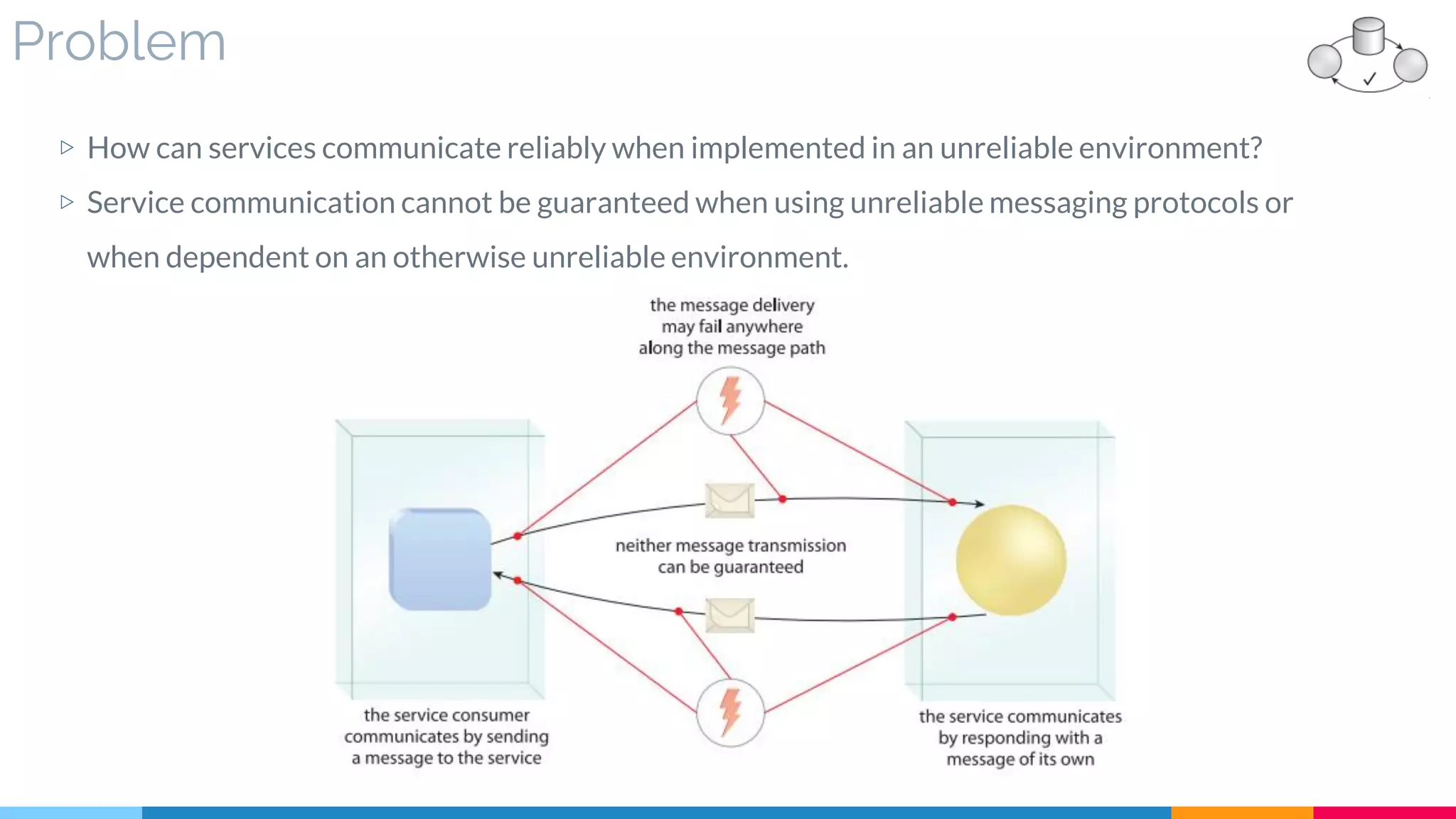
▷ Problem
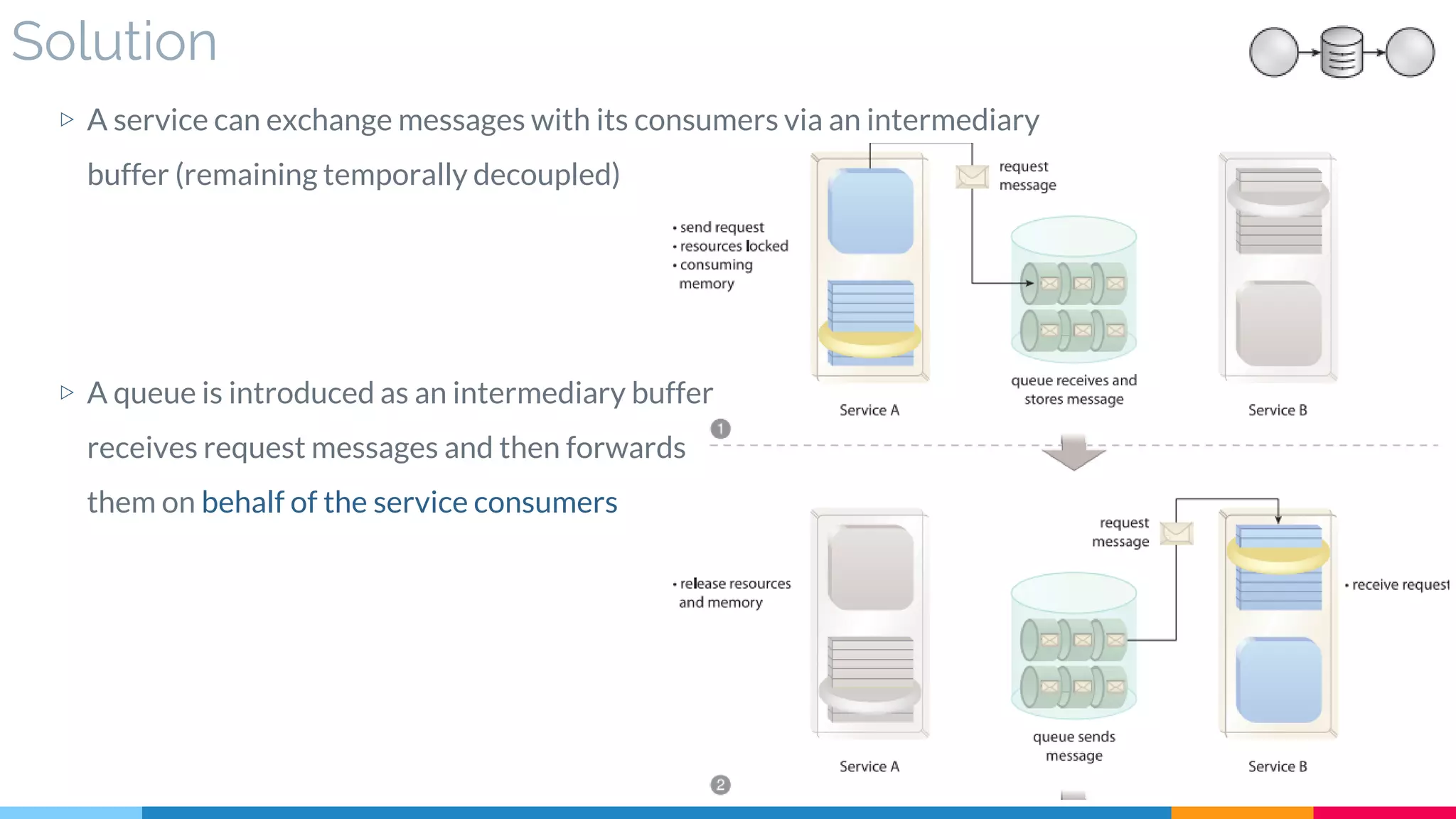
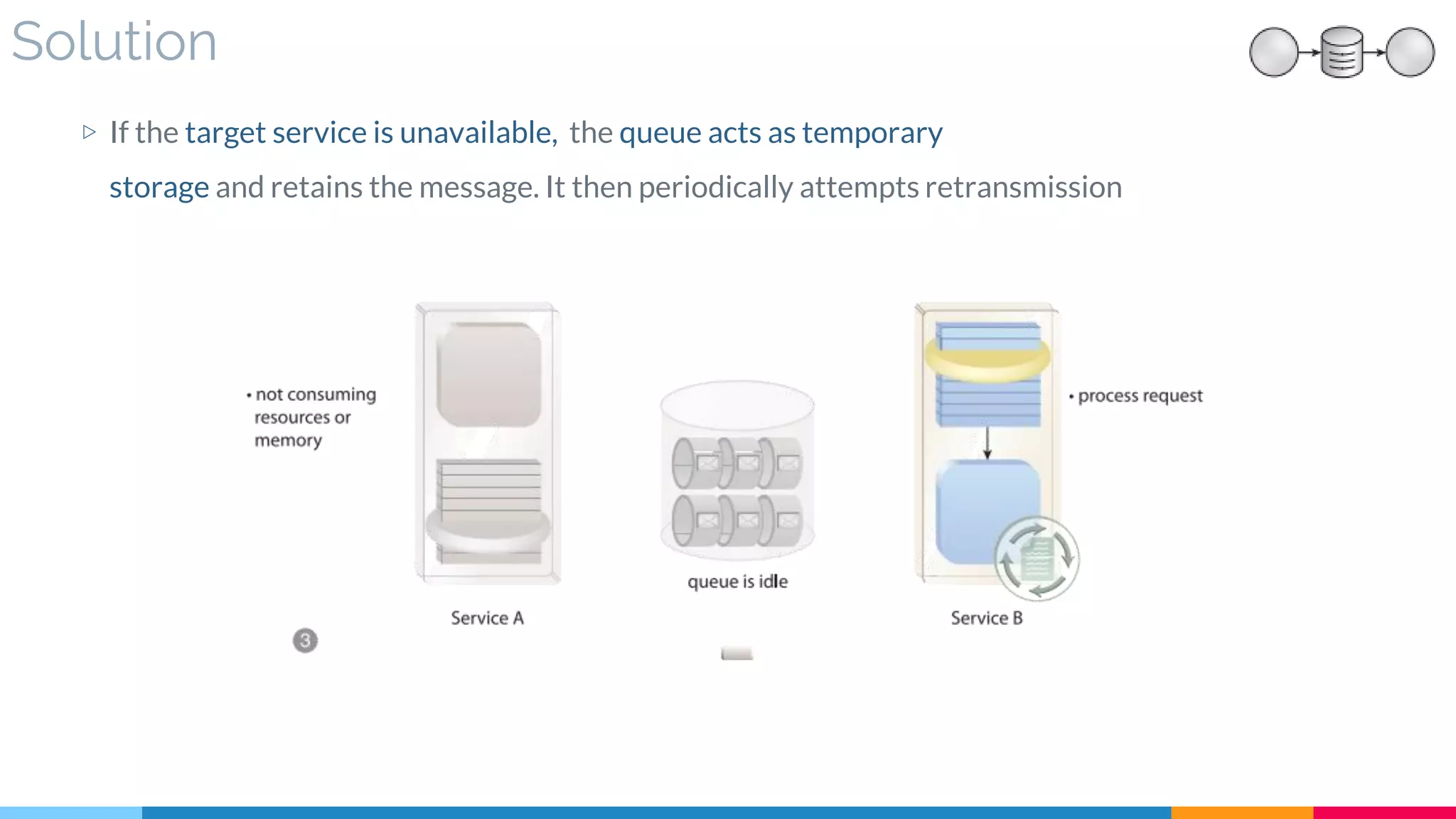
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
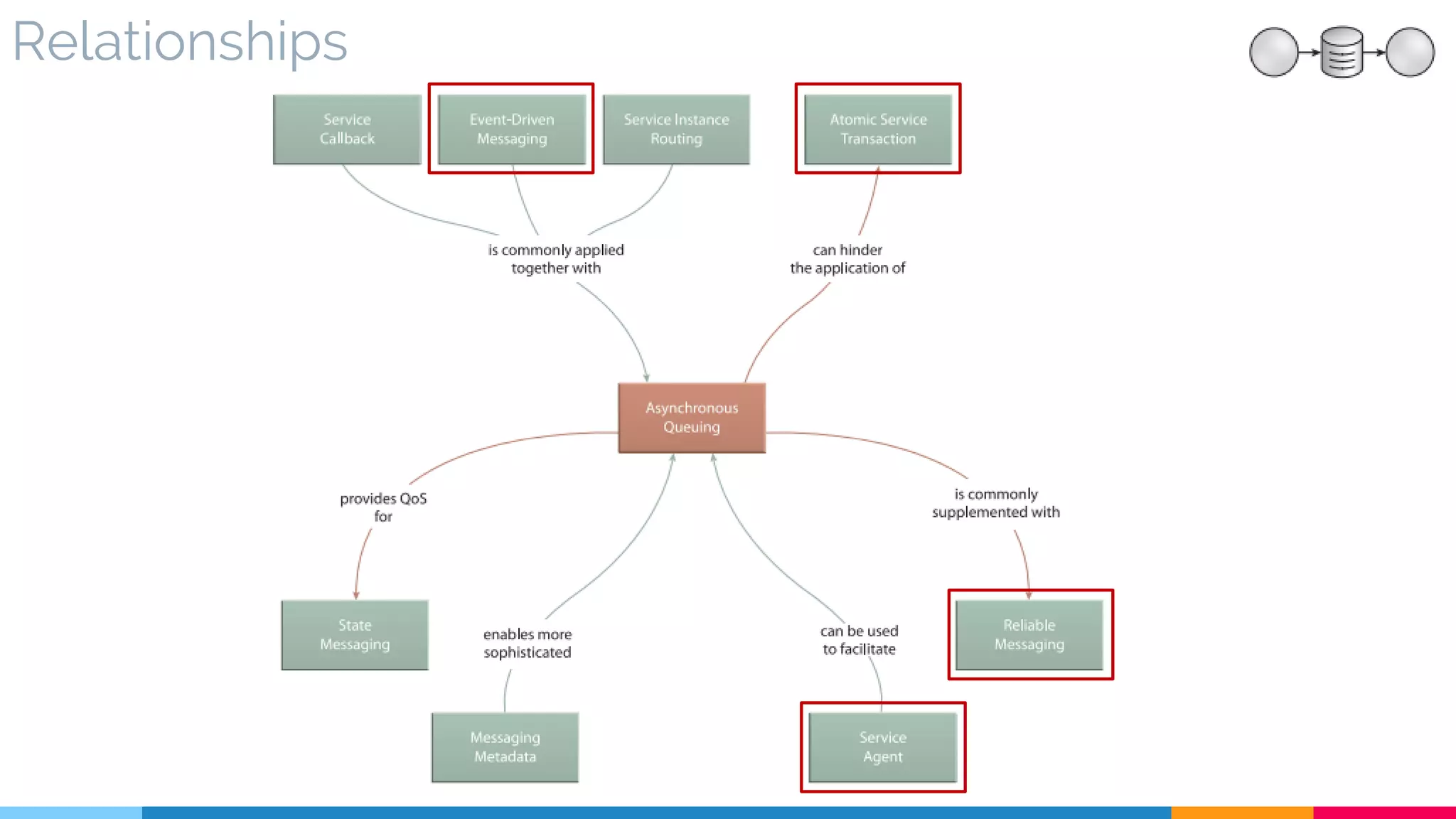
▷ Relationships
[582]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-50-2048.jpg)


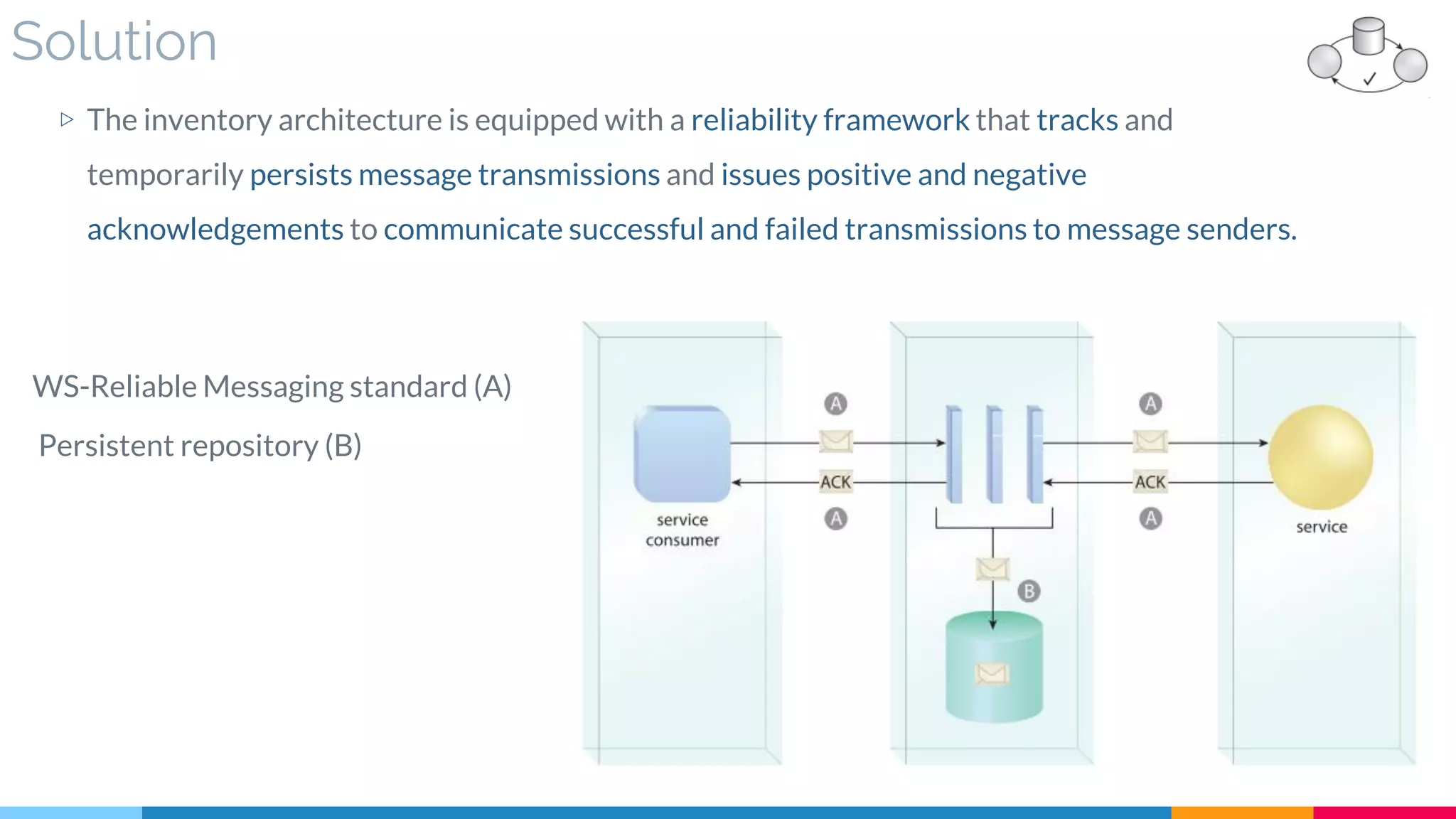
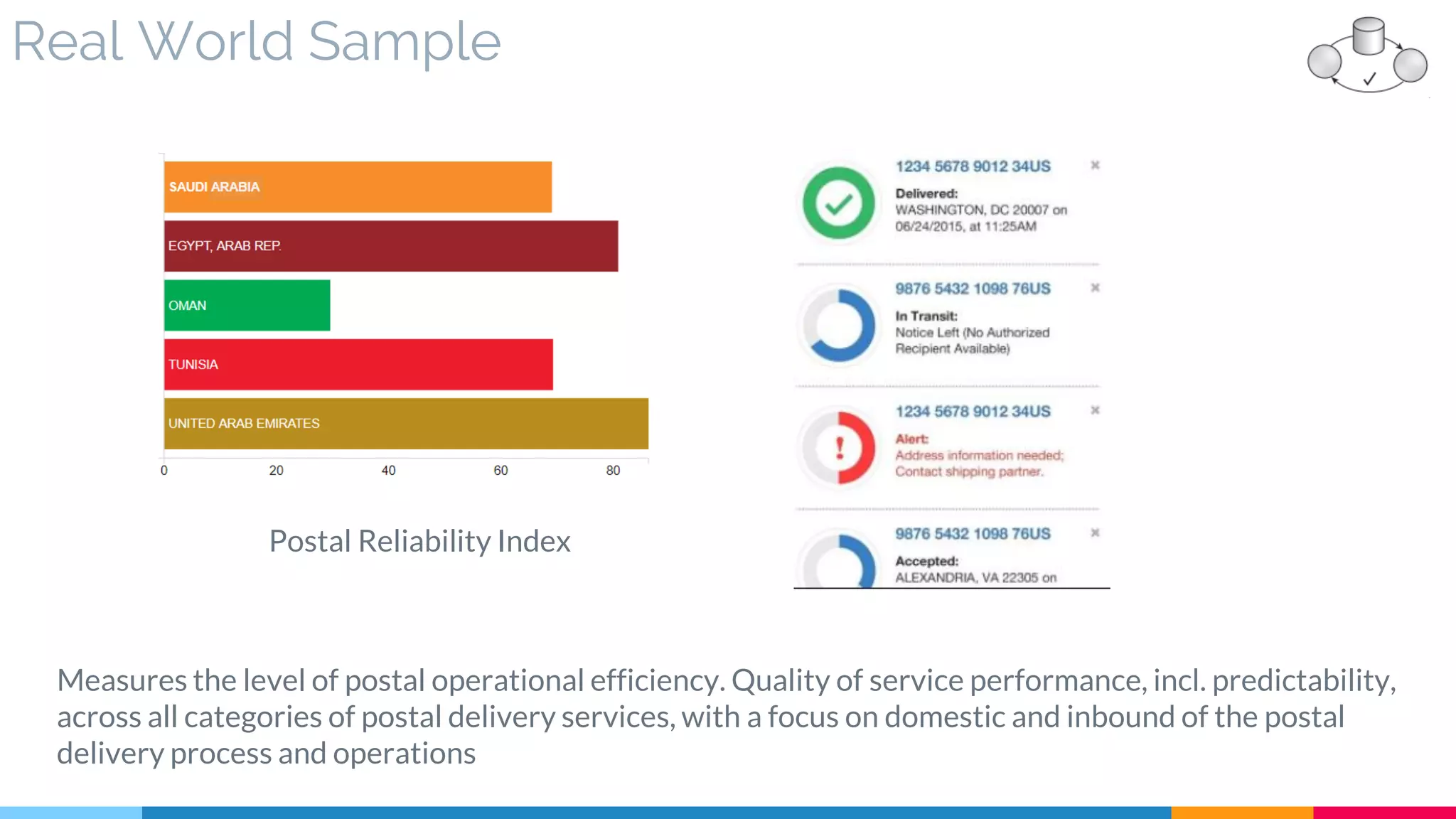
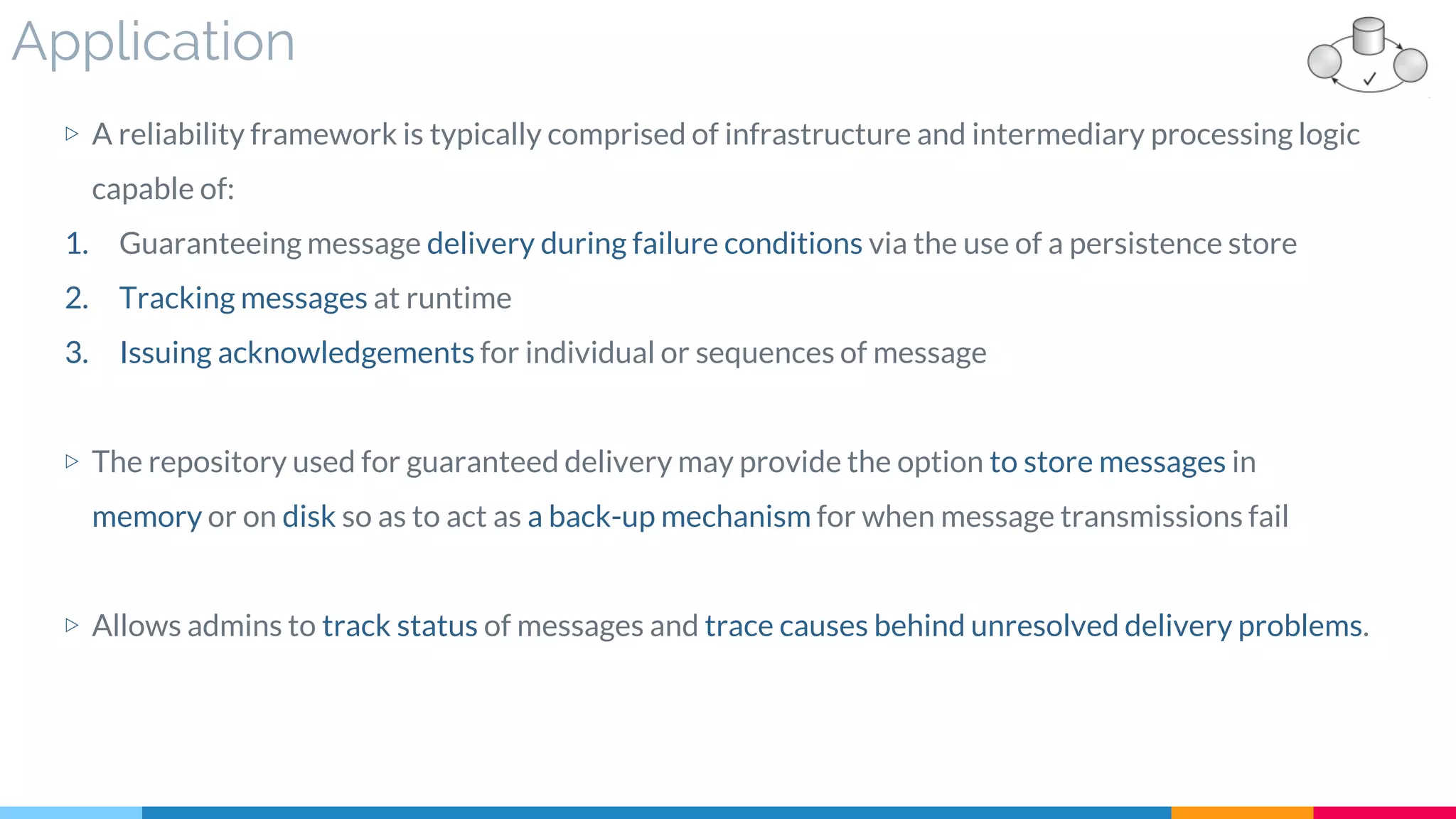
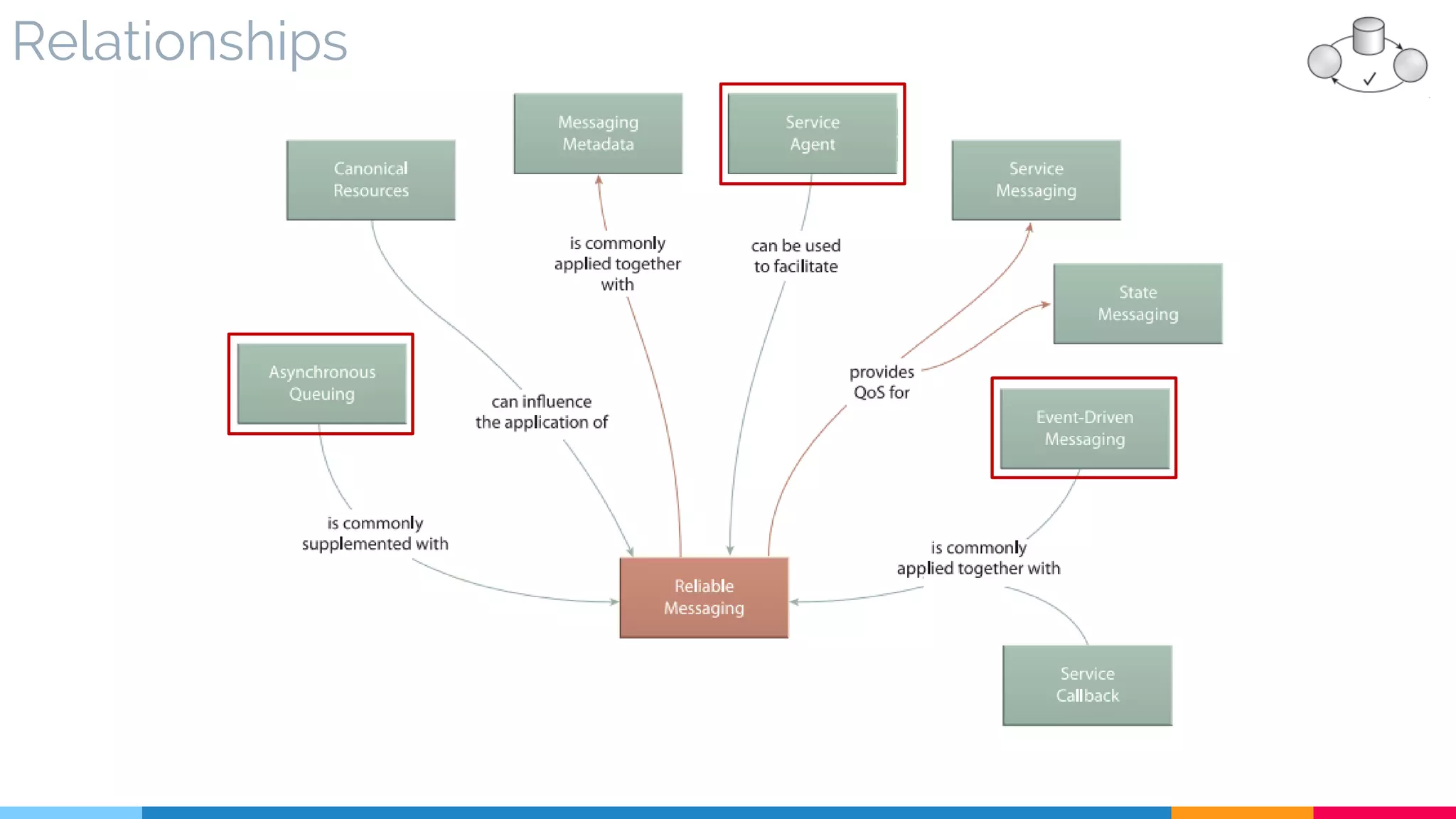
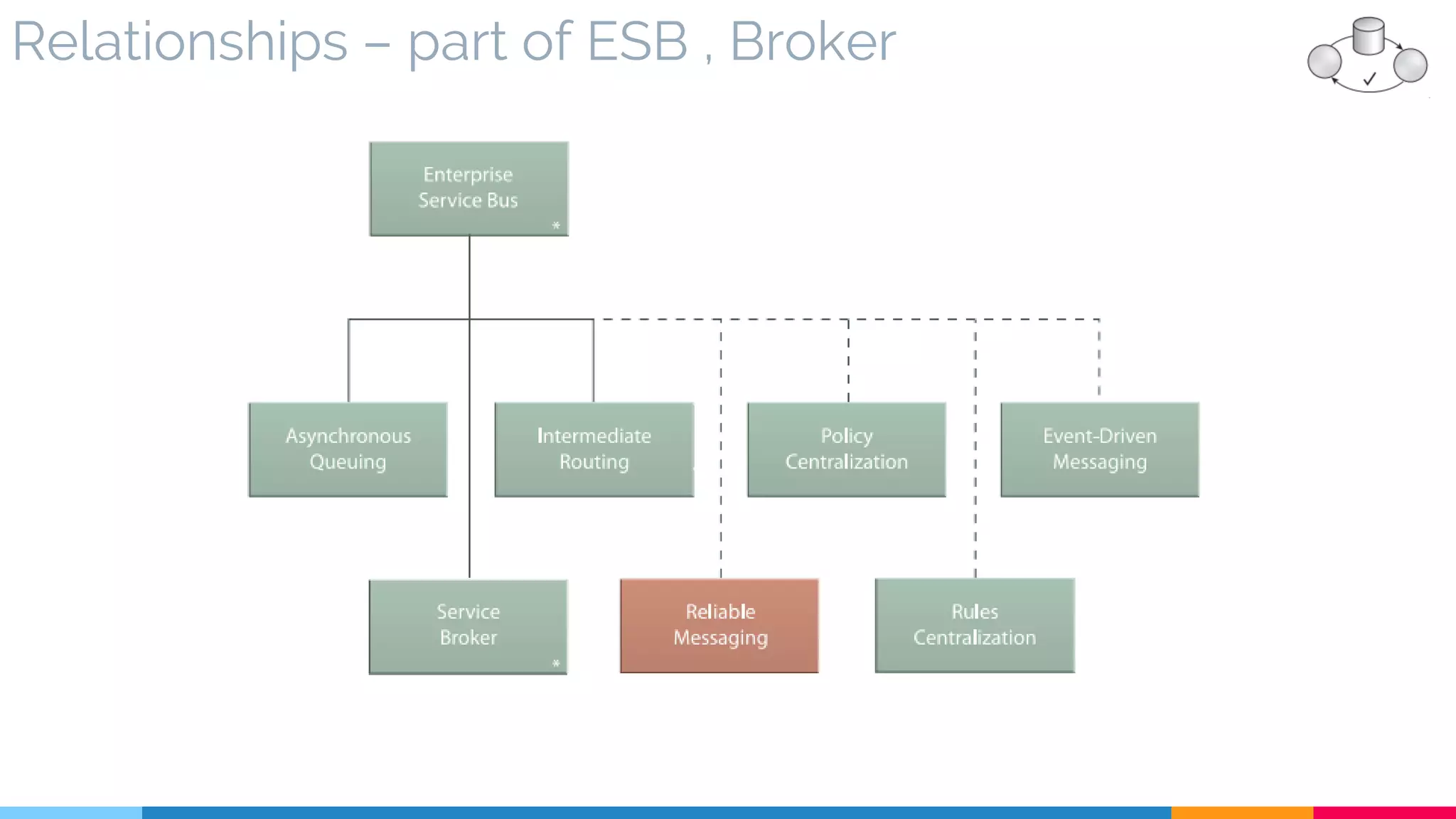
![8 Reliable Messaging
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
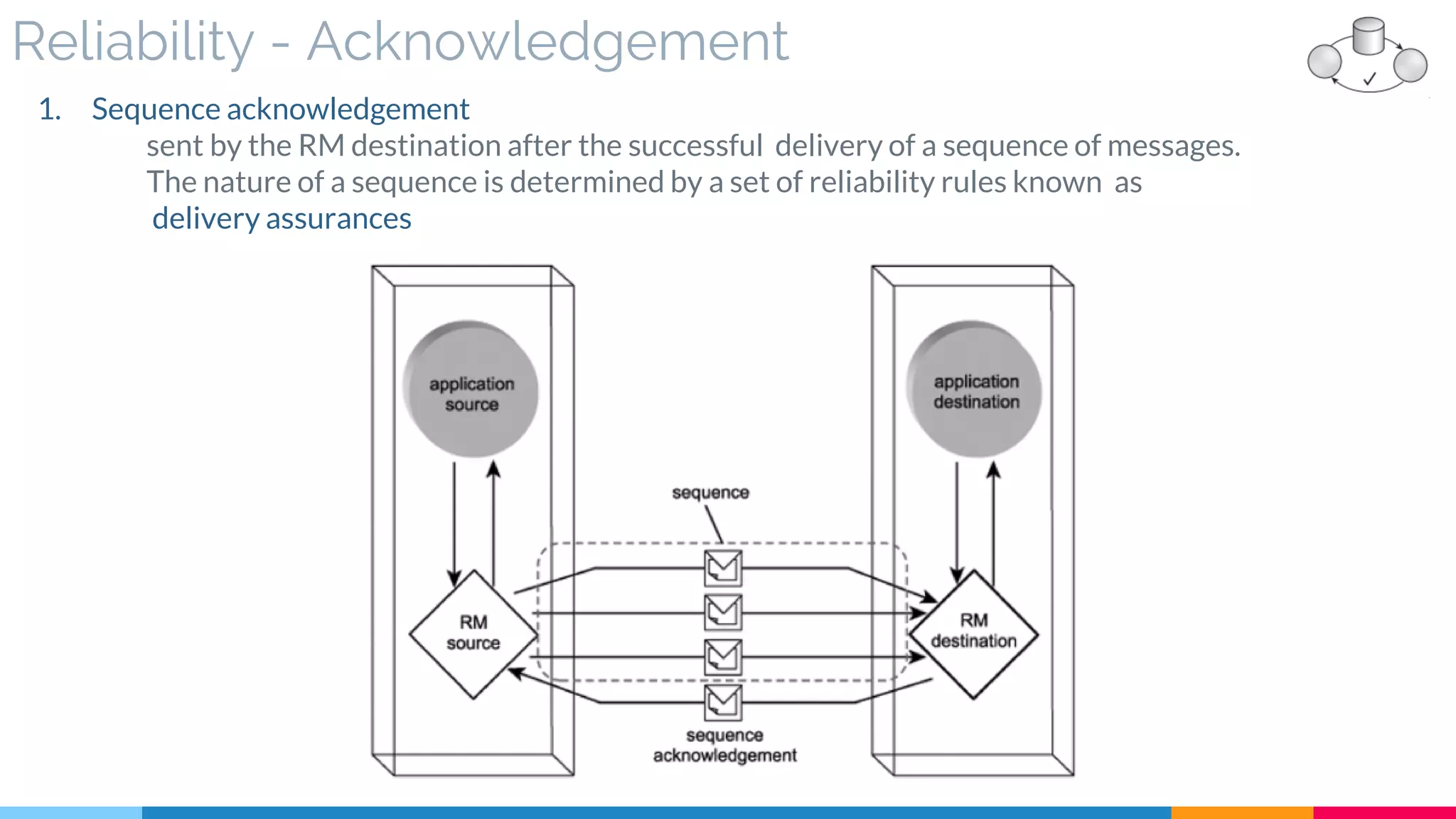
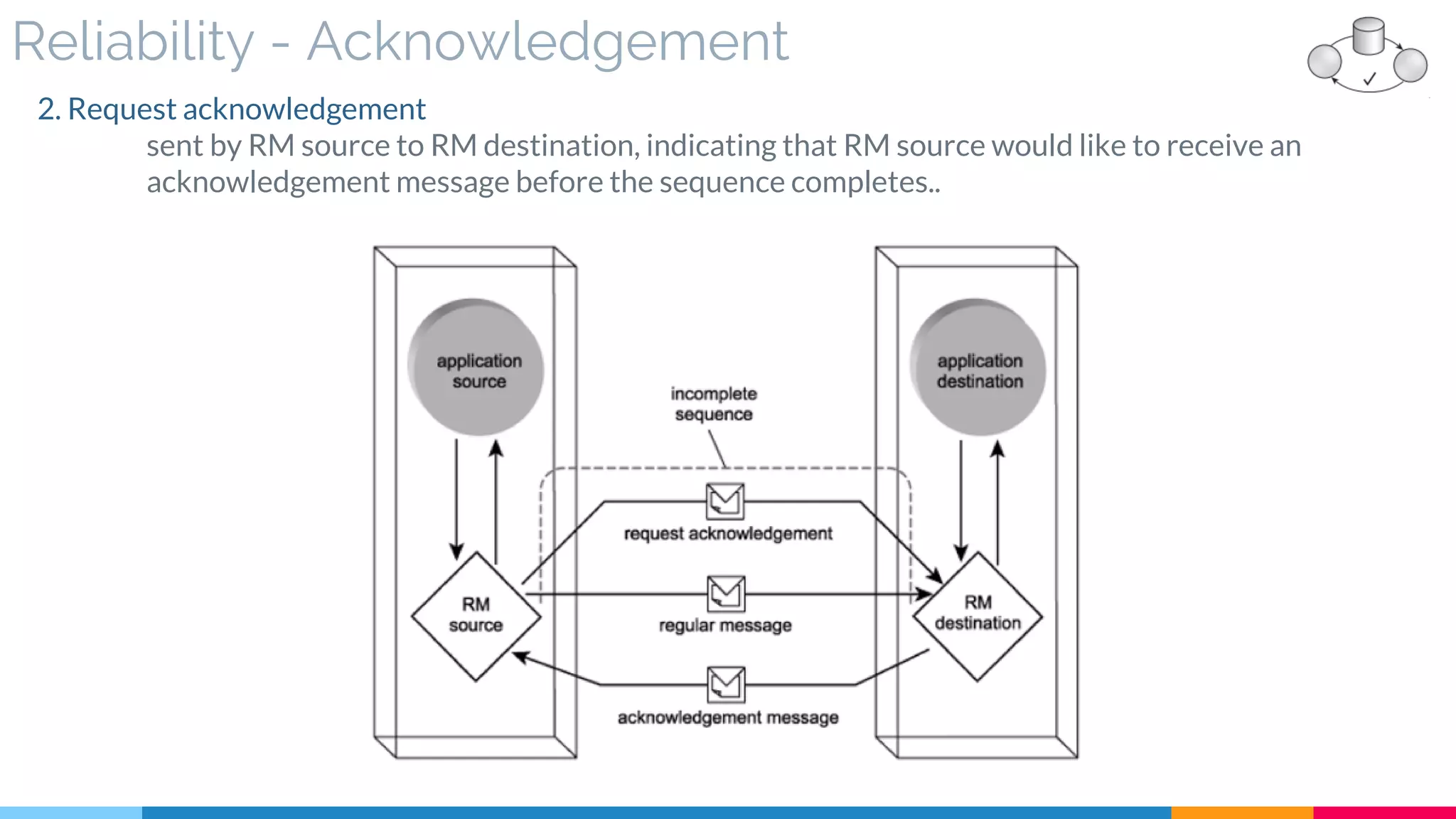
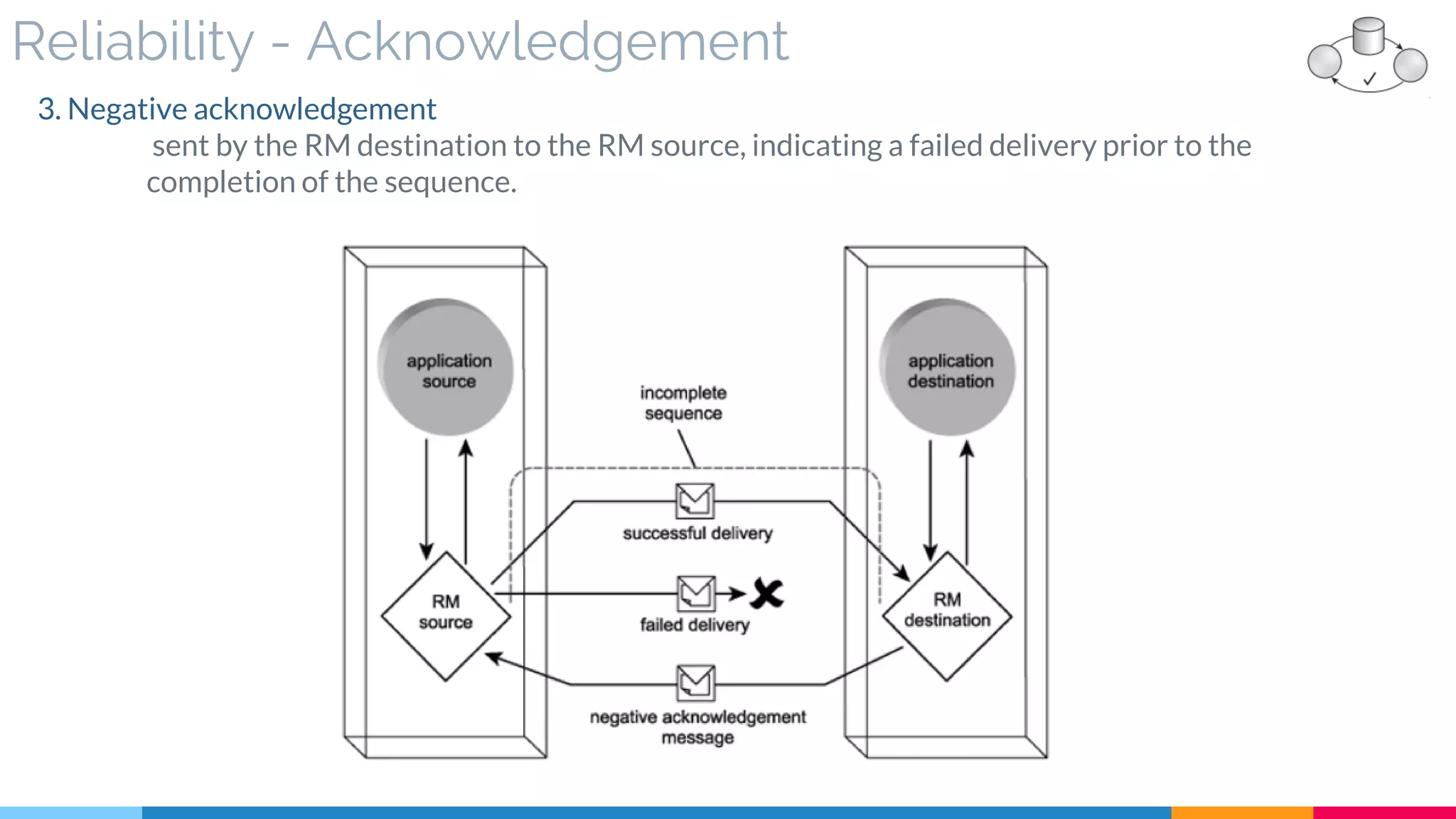
▷ Reliability (Acknowledgment – Assurance)
[592]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-60-2048.jpg)

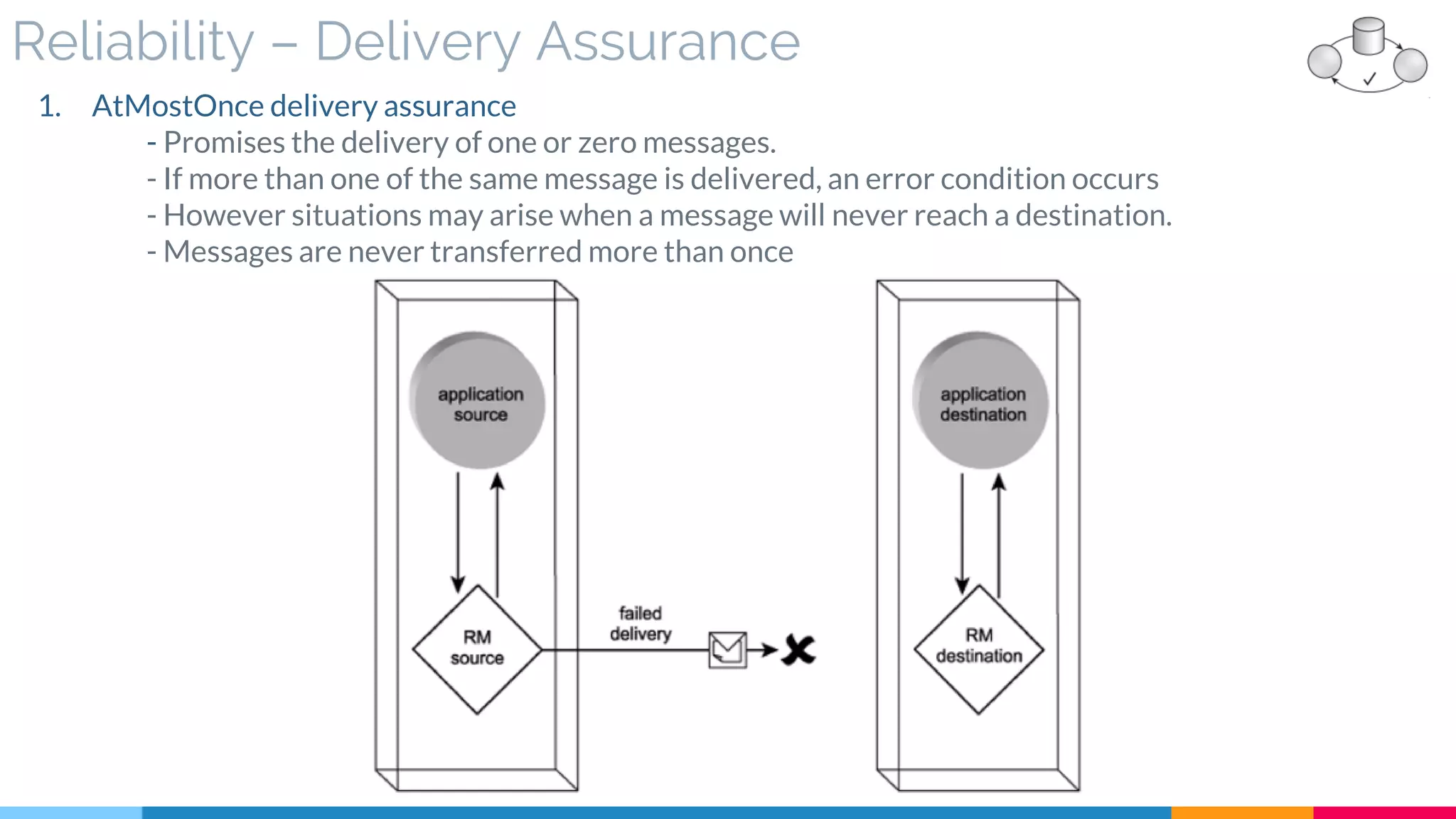
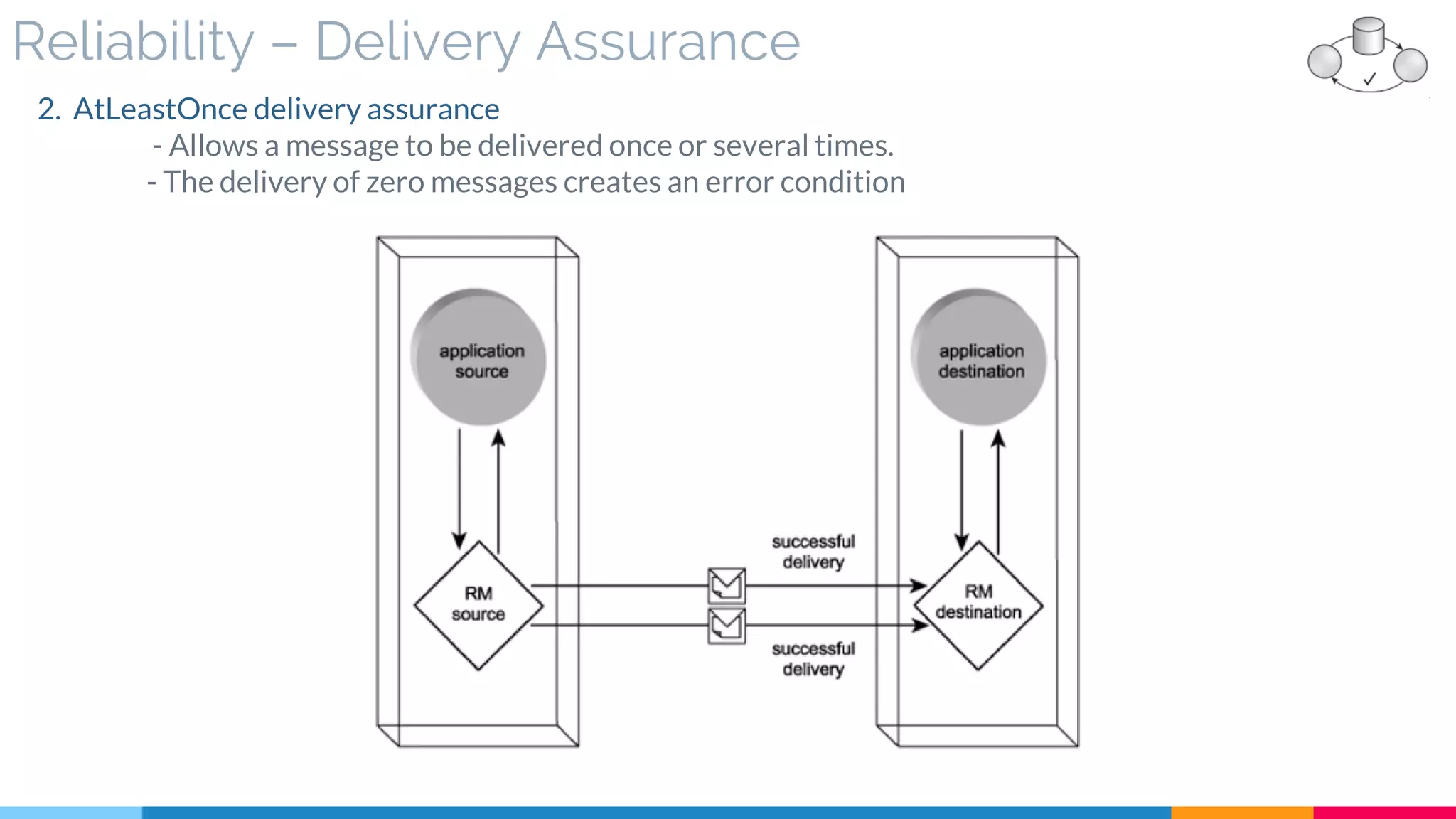
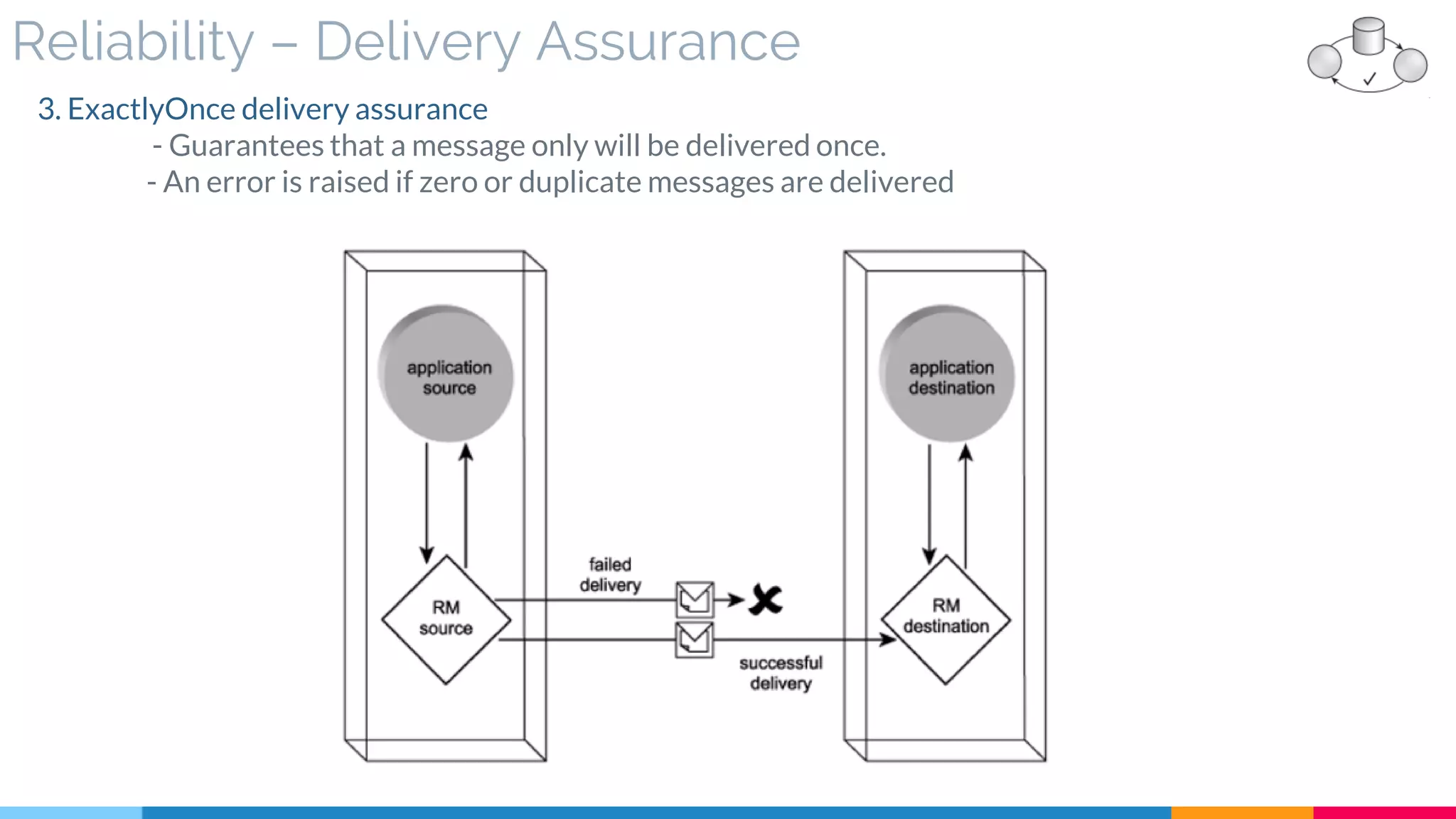
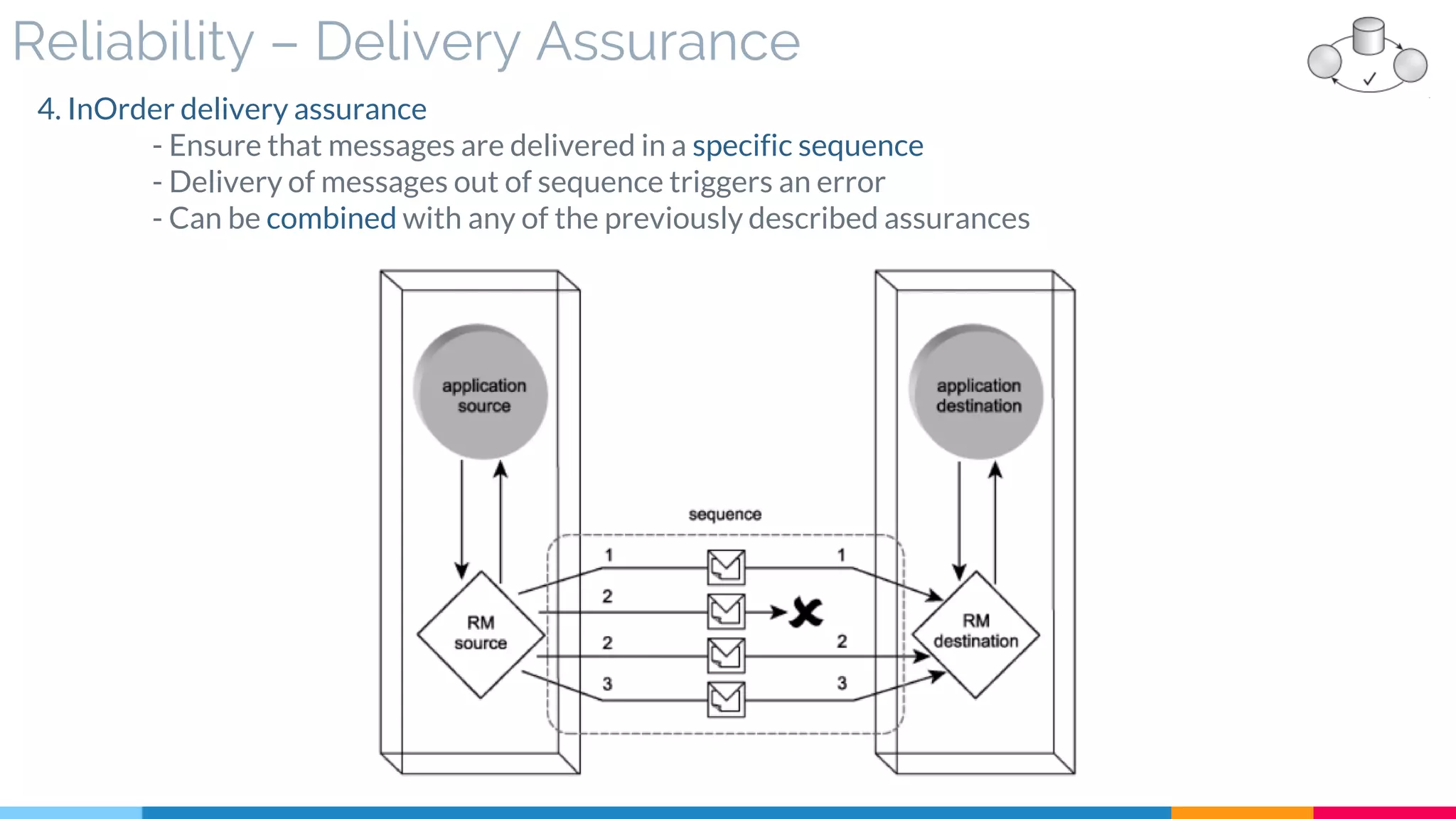
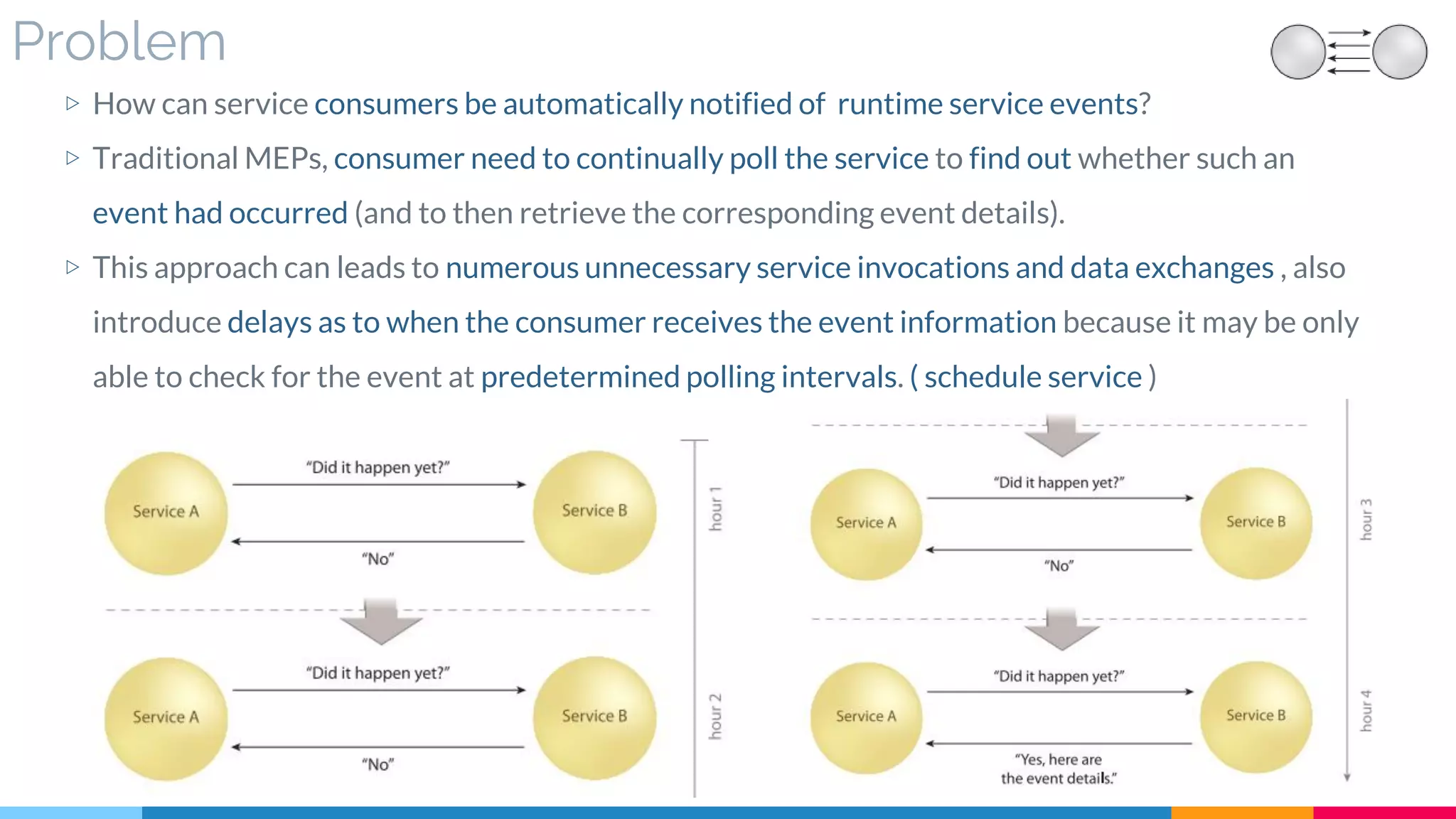
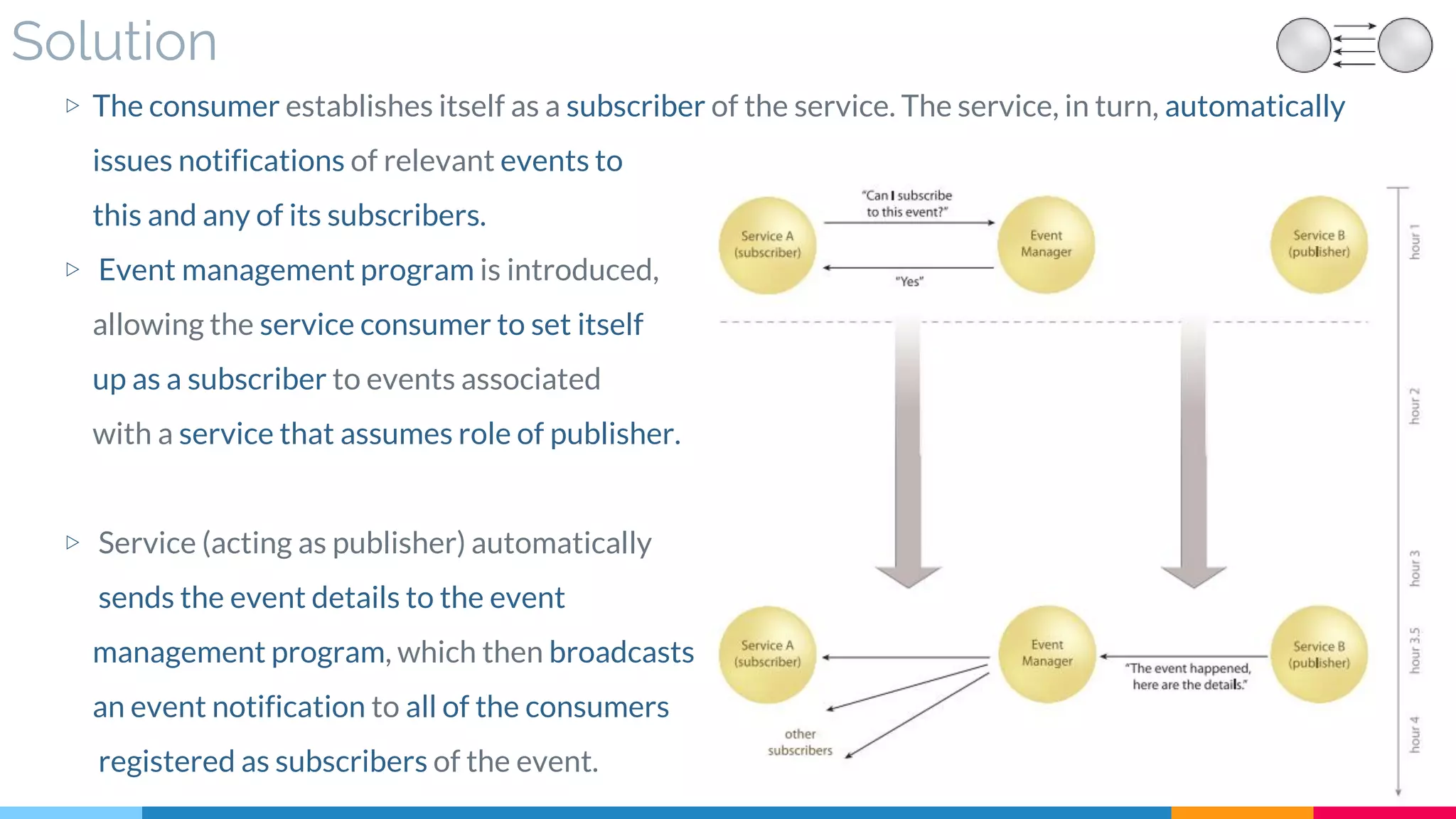
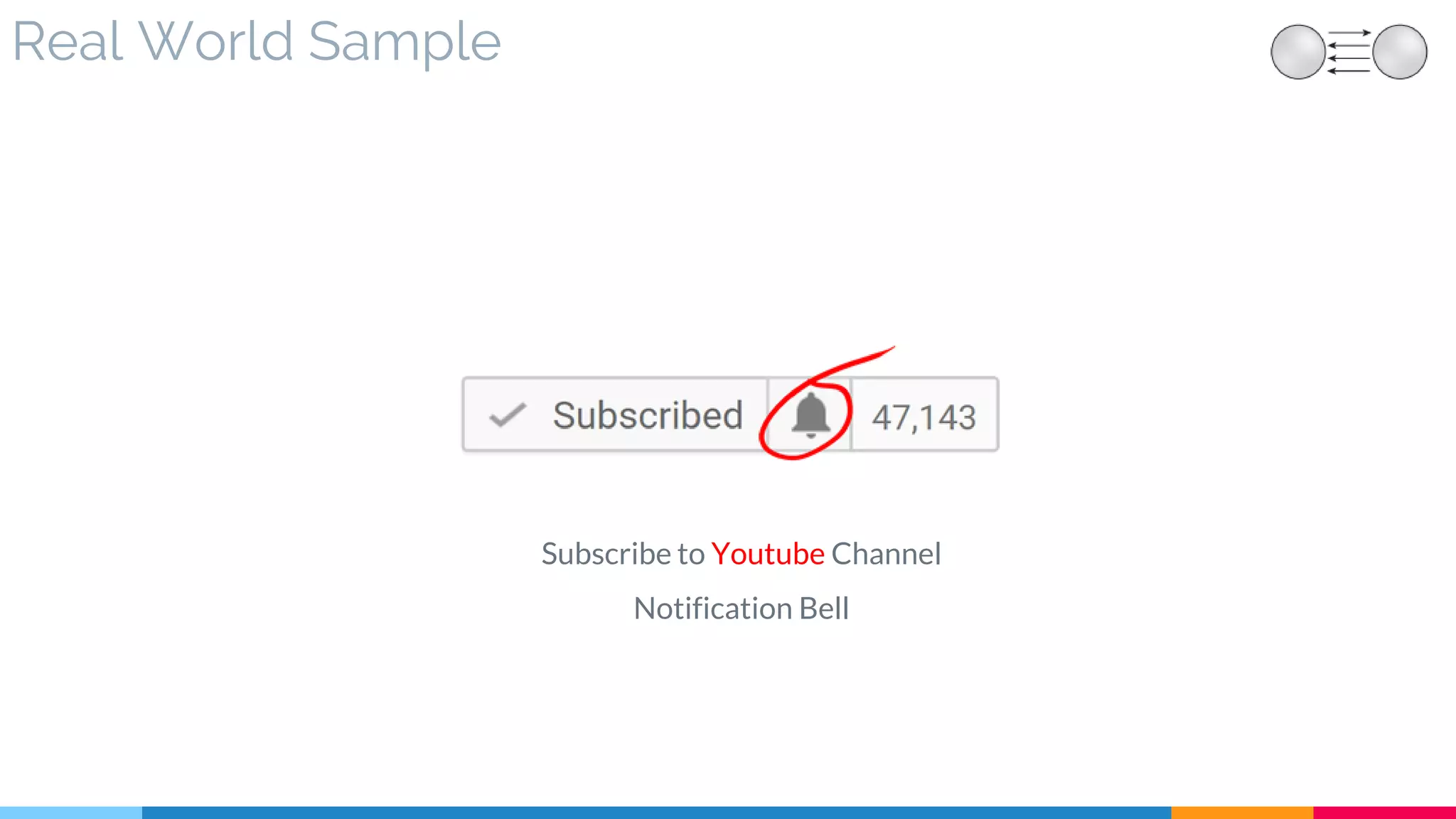
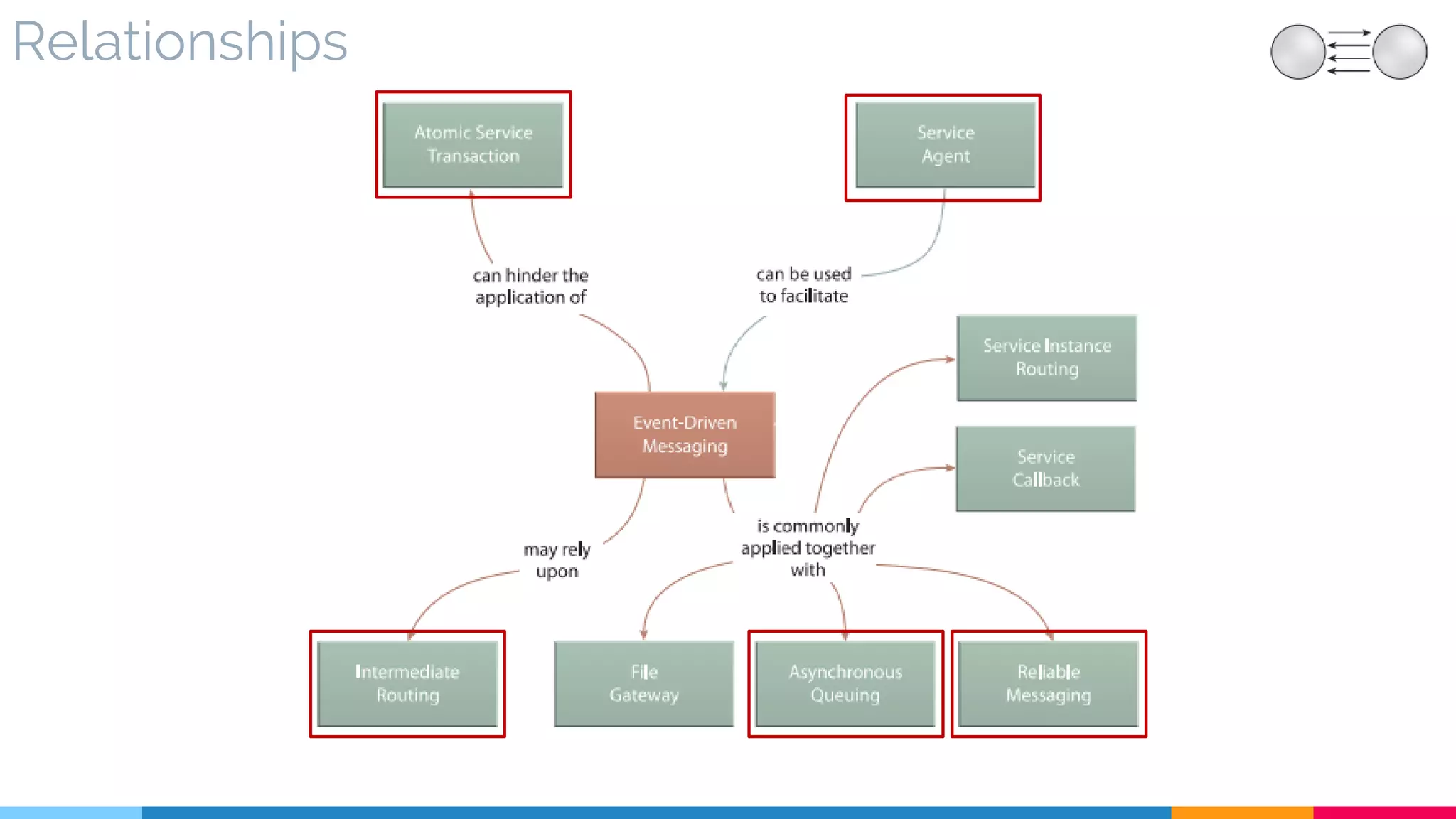
![9 Event-Driven Messaging
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[599]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-75-2048.jpg)


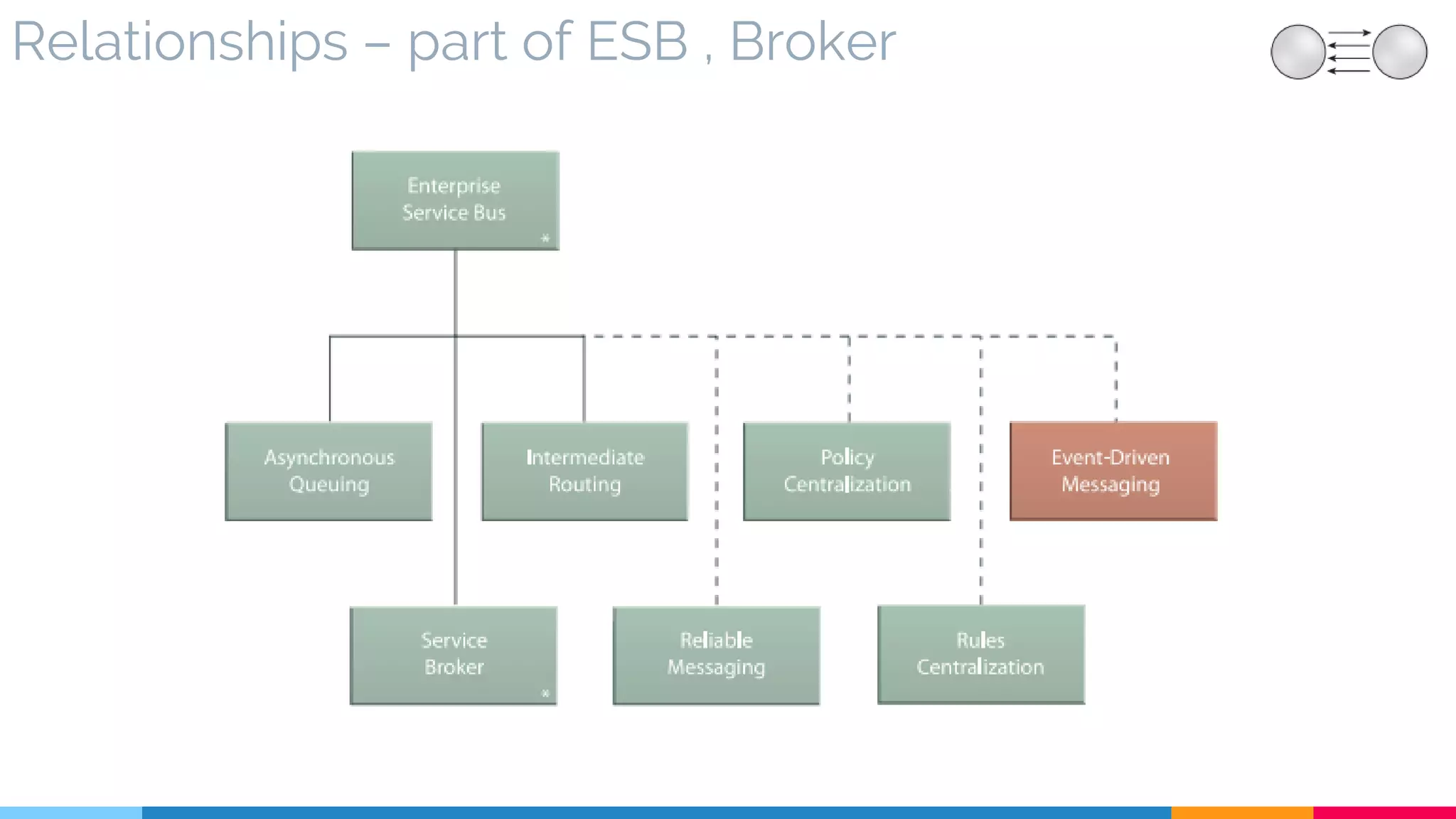
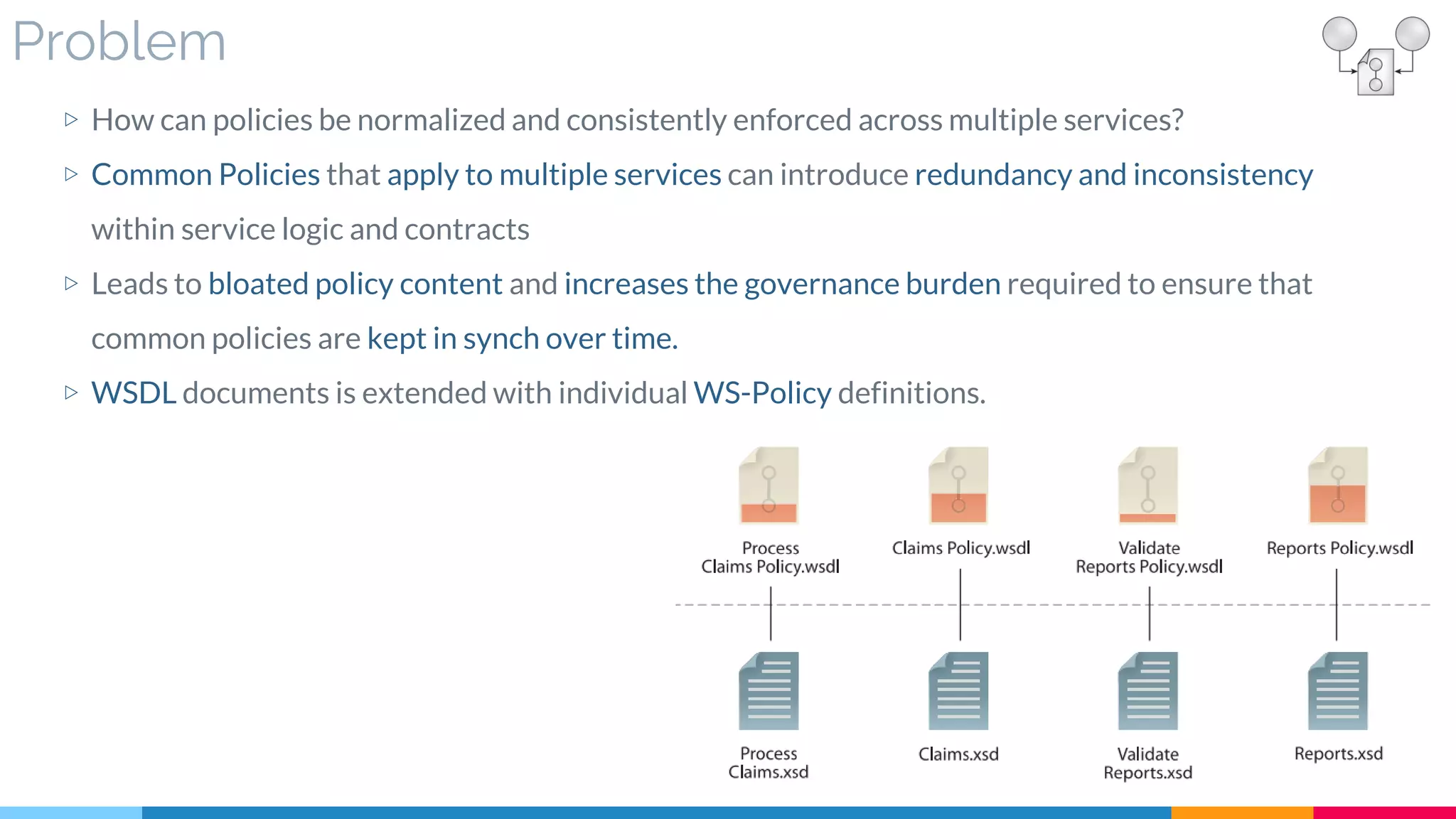
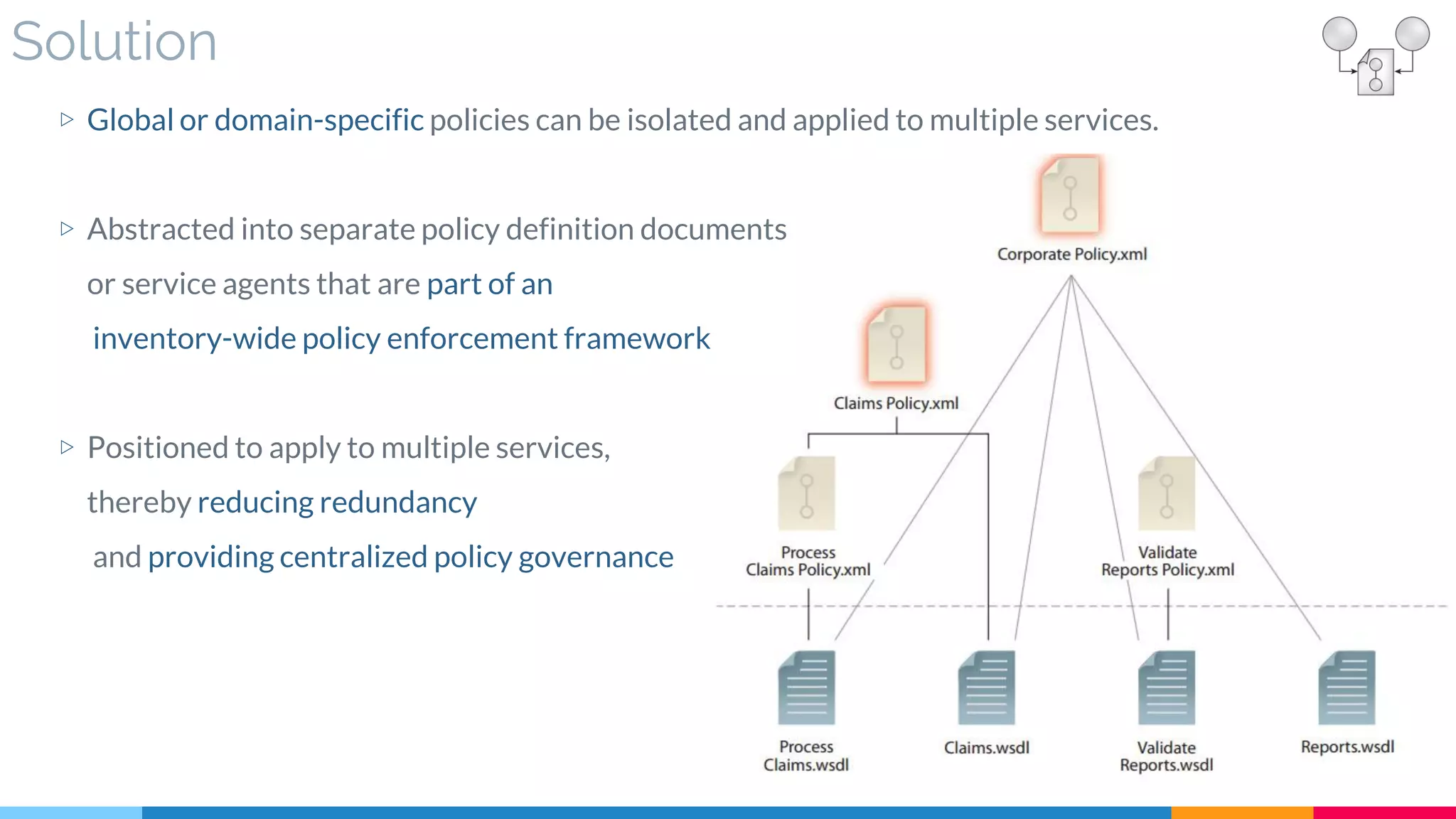
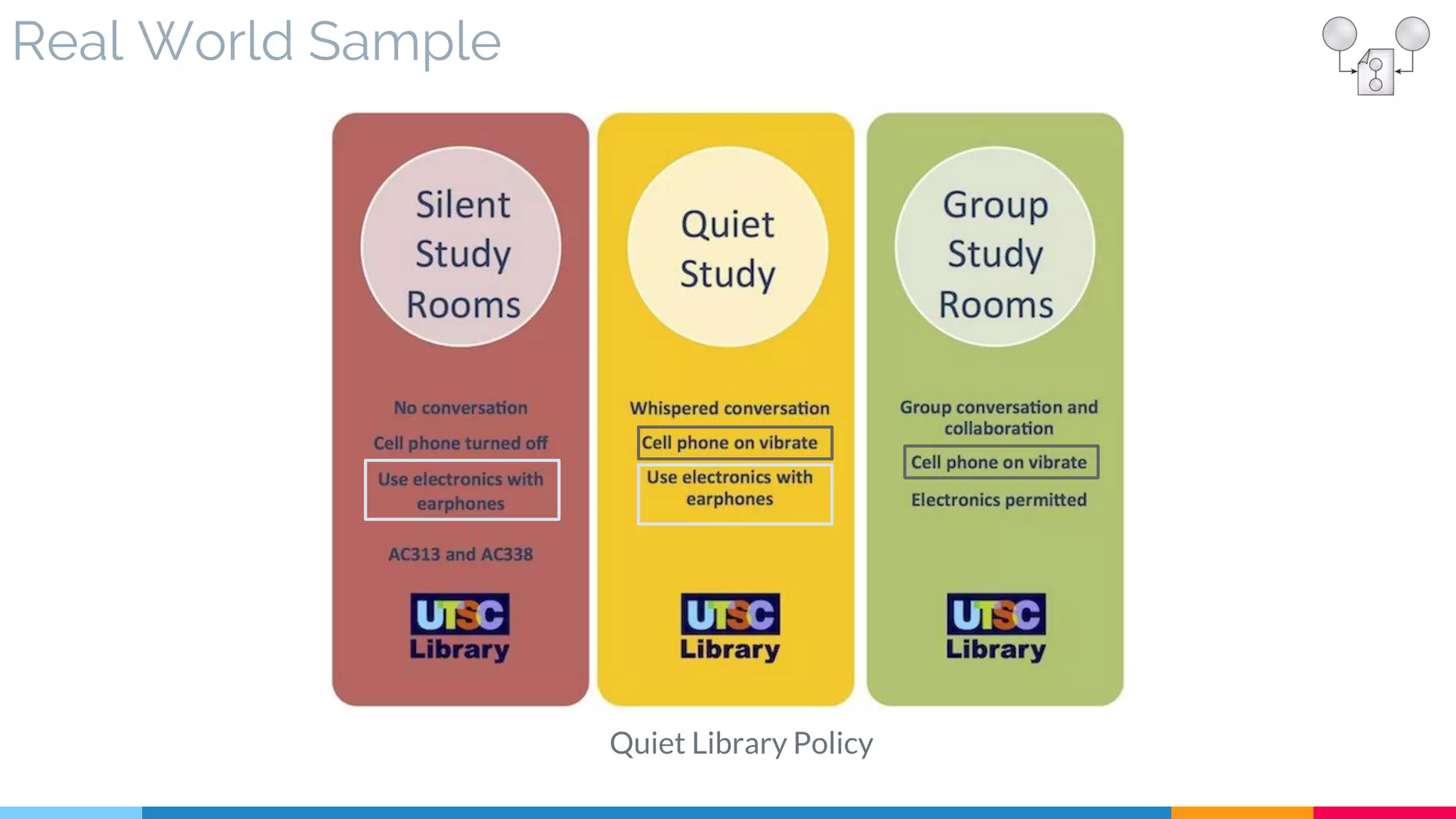
![10. Policy Centralization
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[207]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-83-2048.jpg)
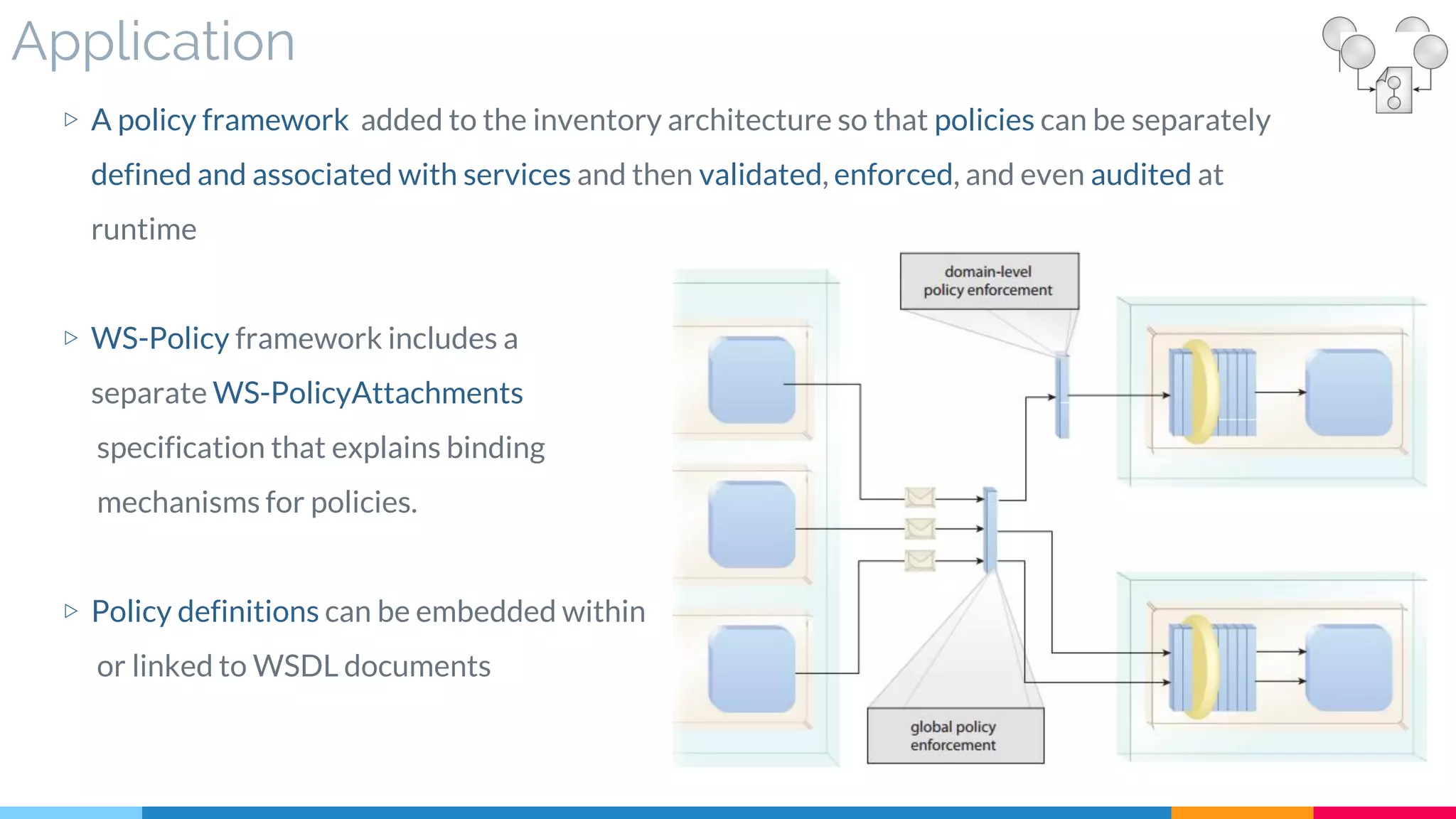

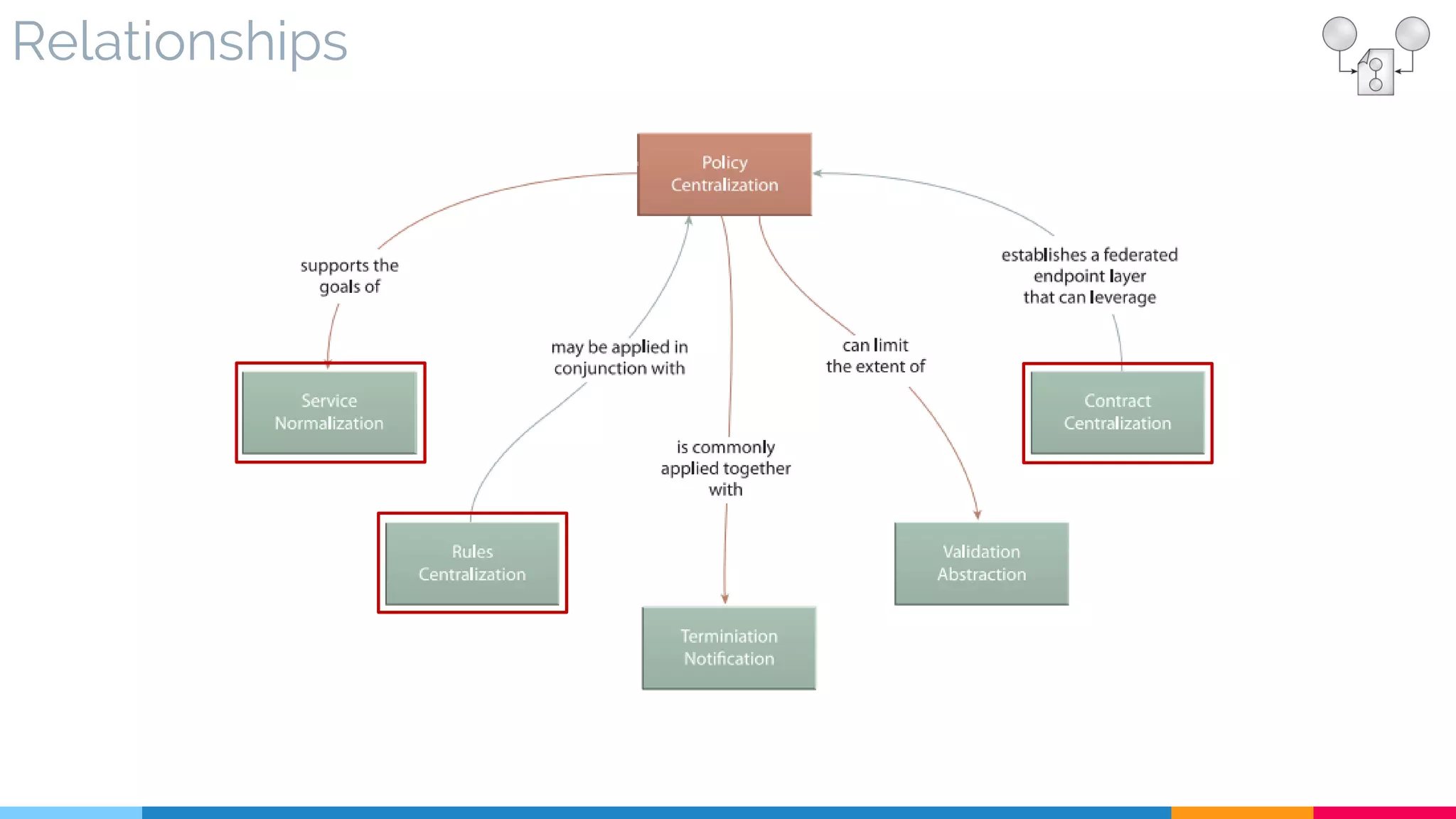
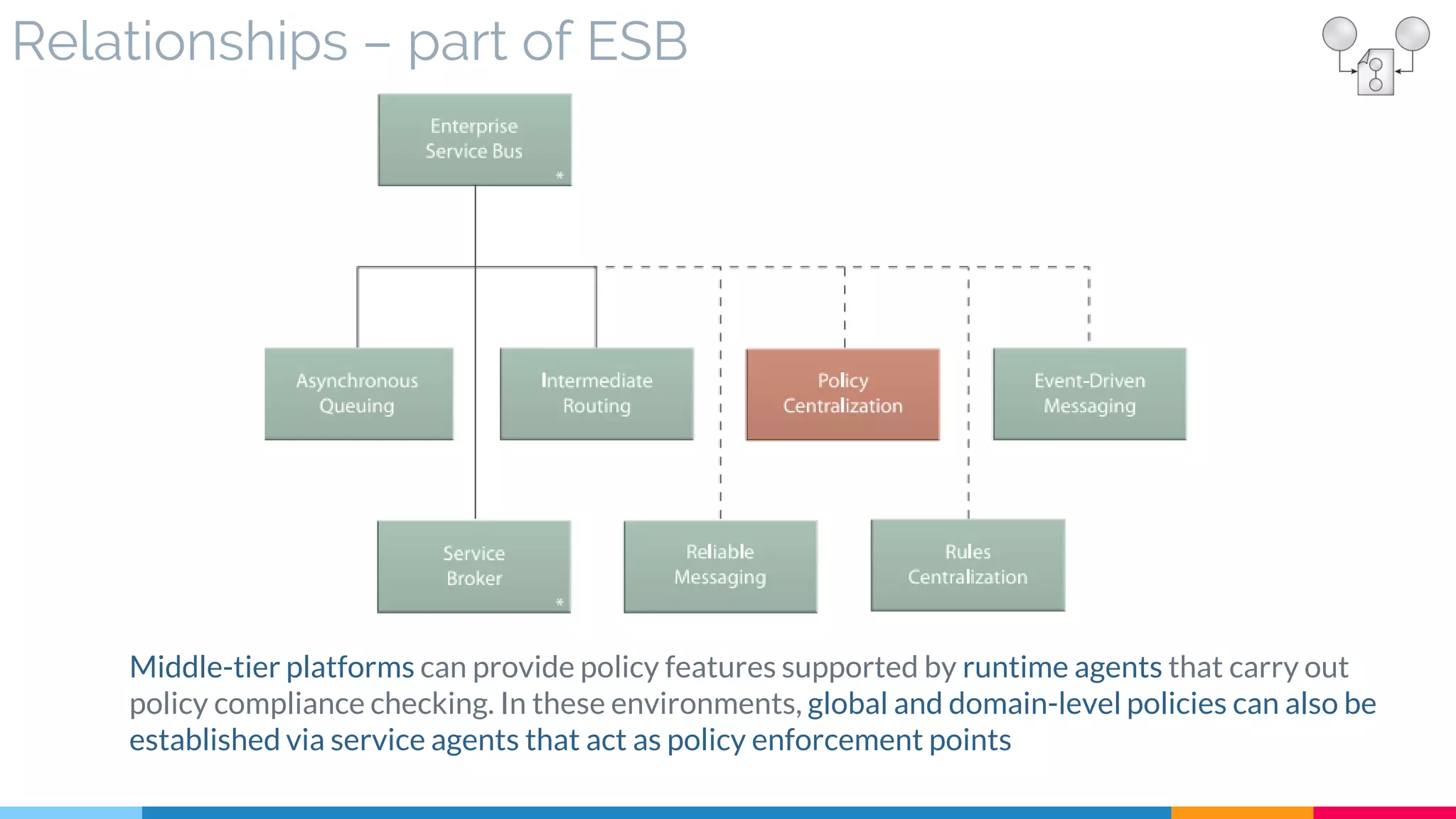
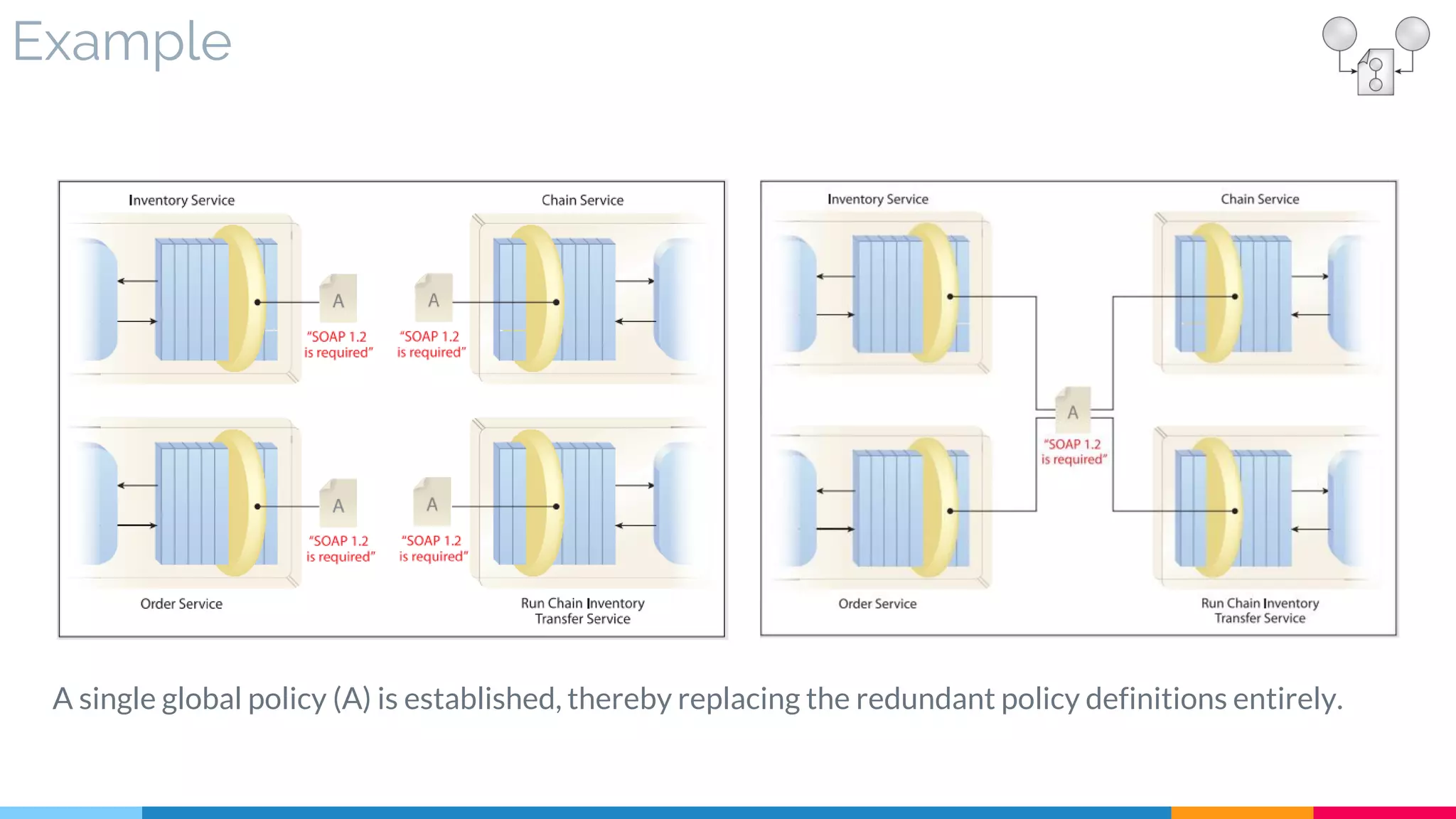
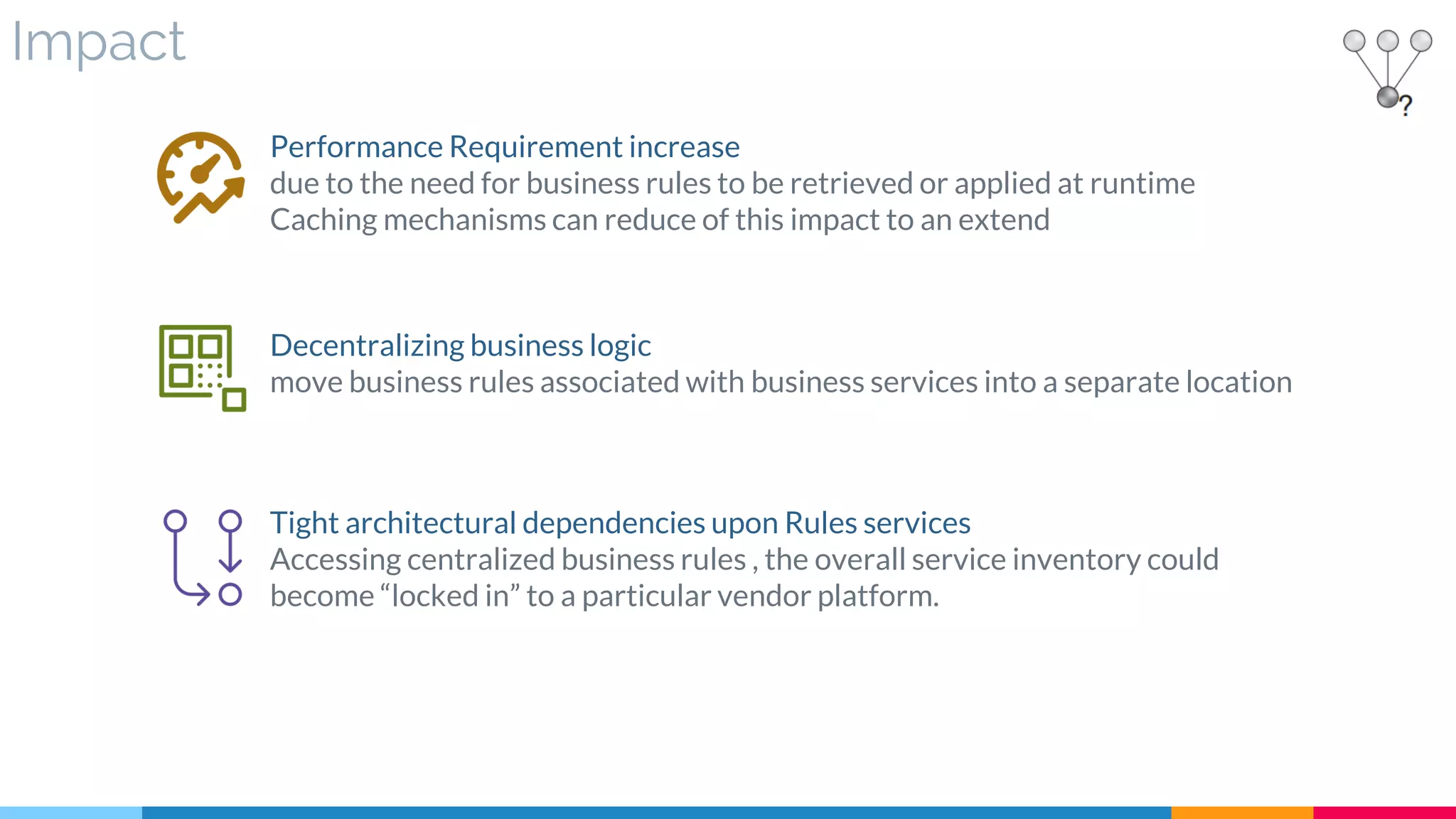
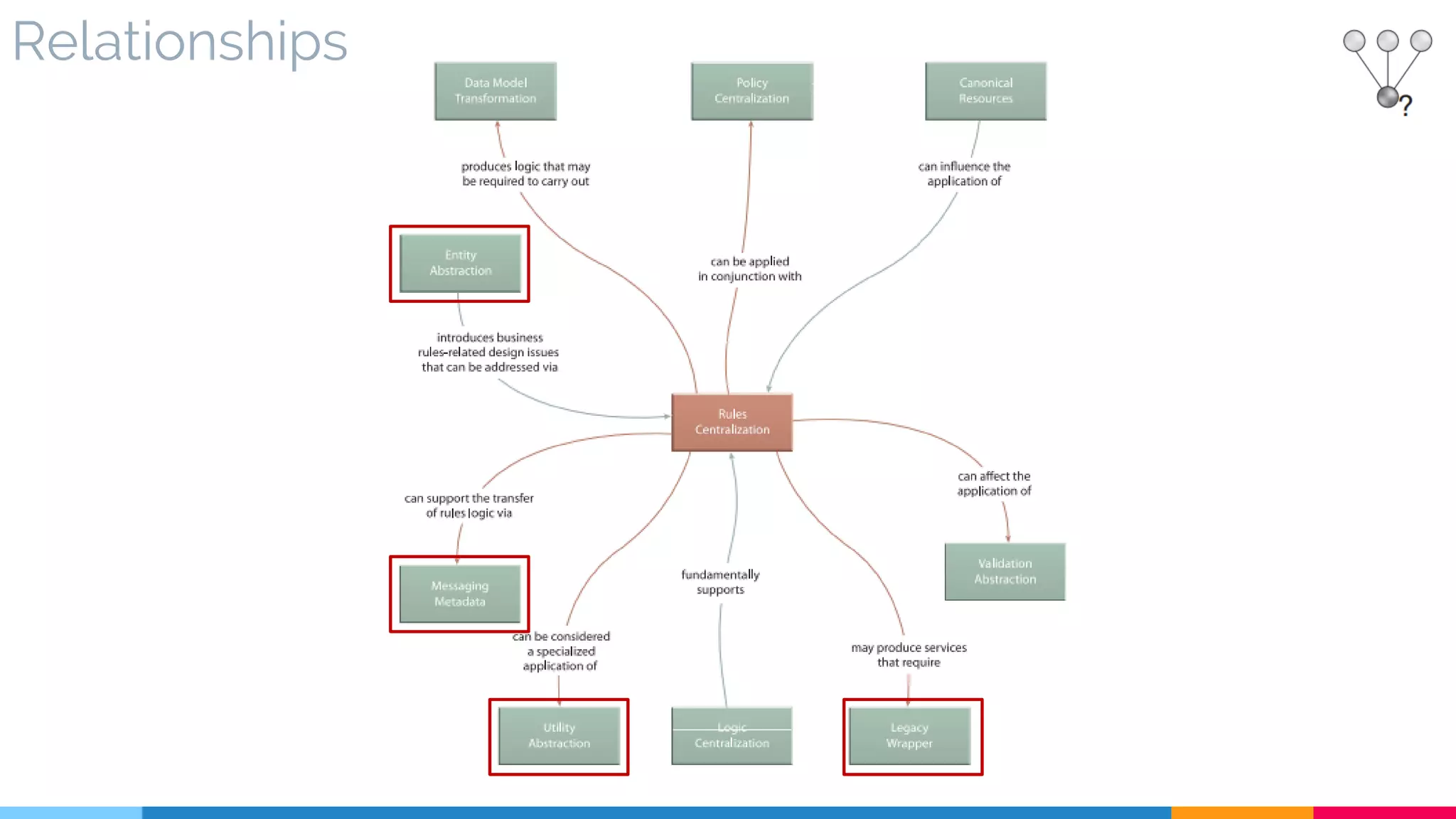
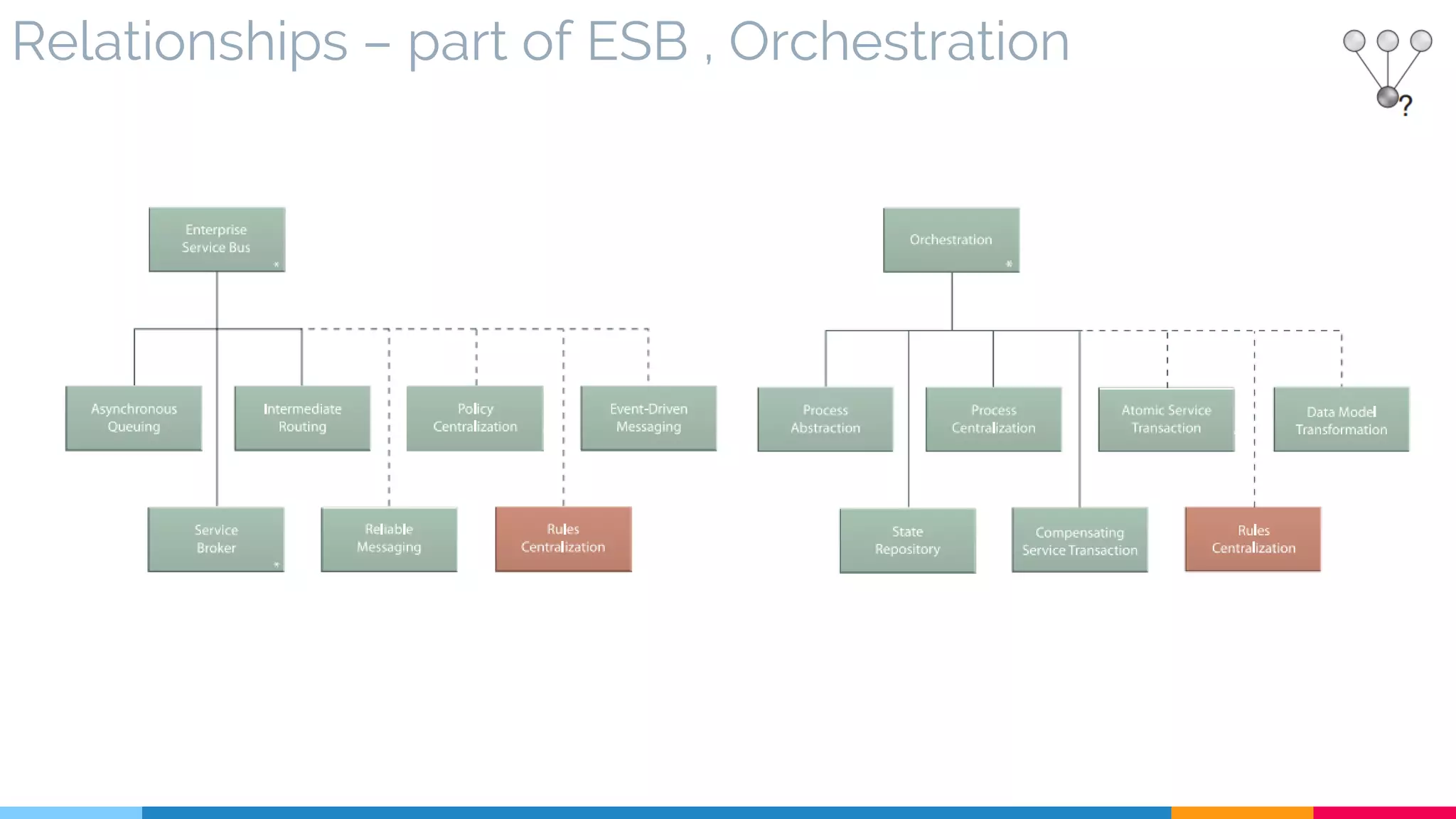
![11 Rules Centralization
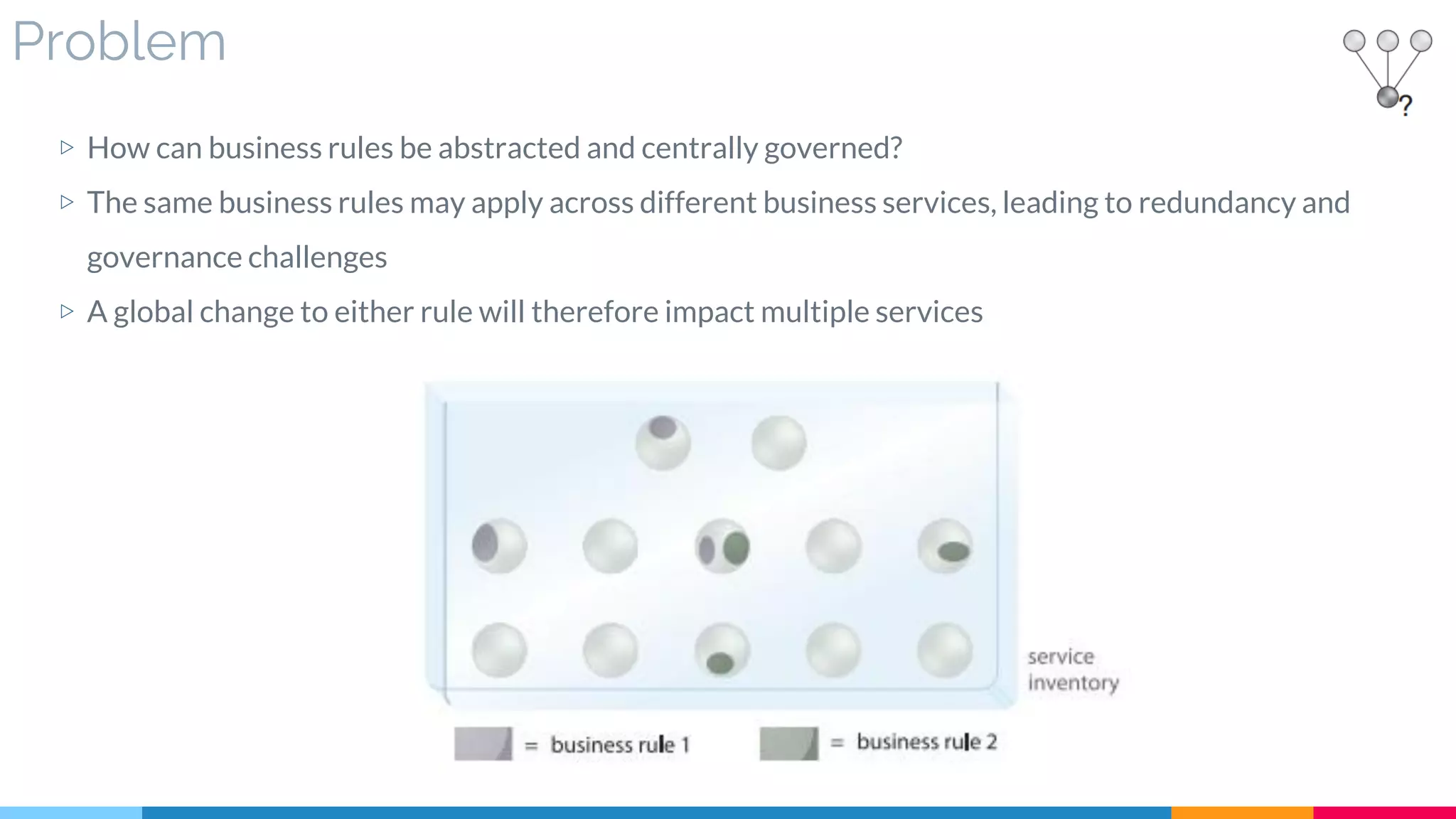
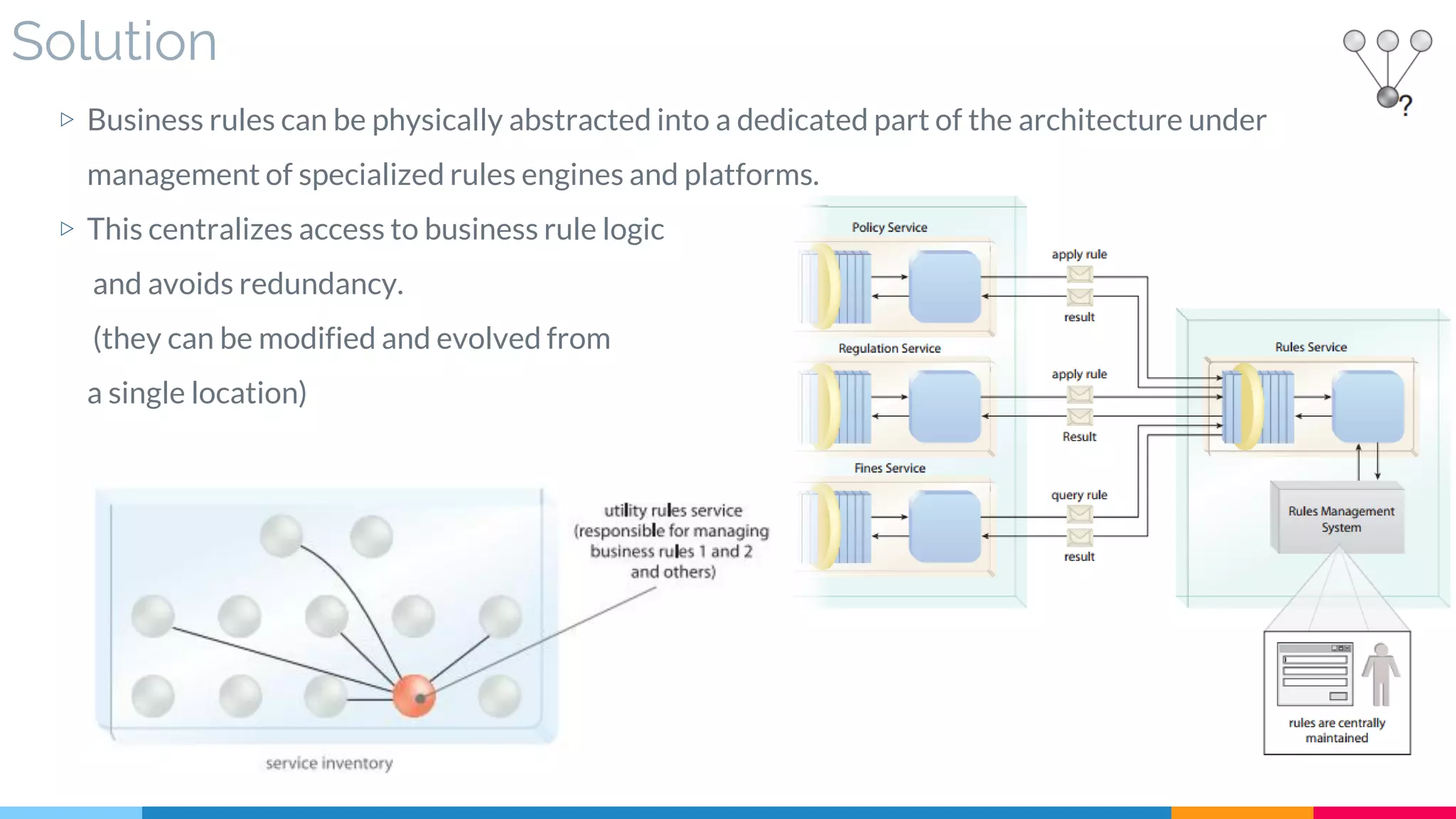
▷ Problem
▷ Solution
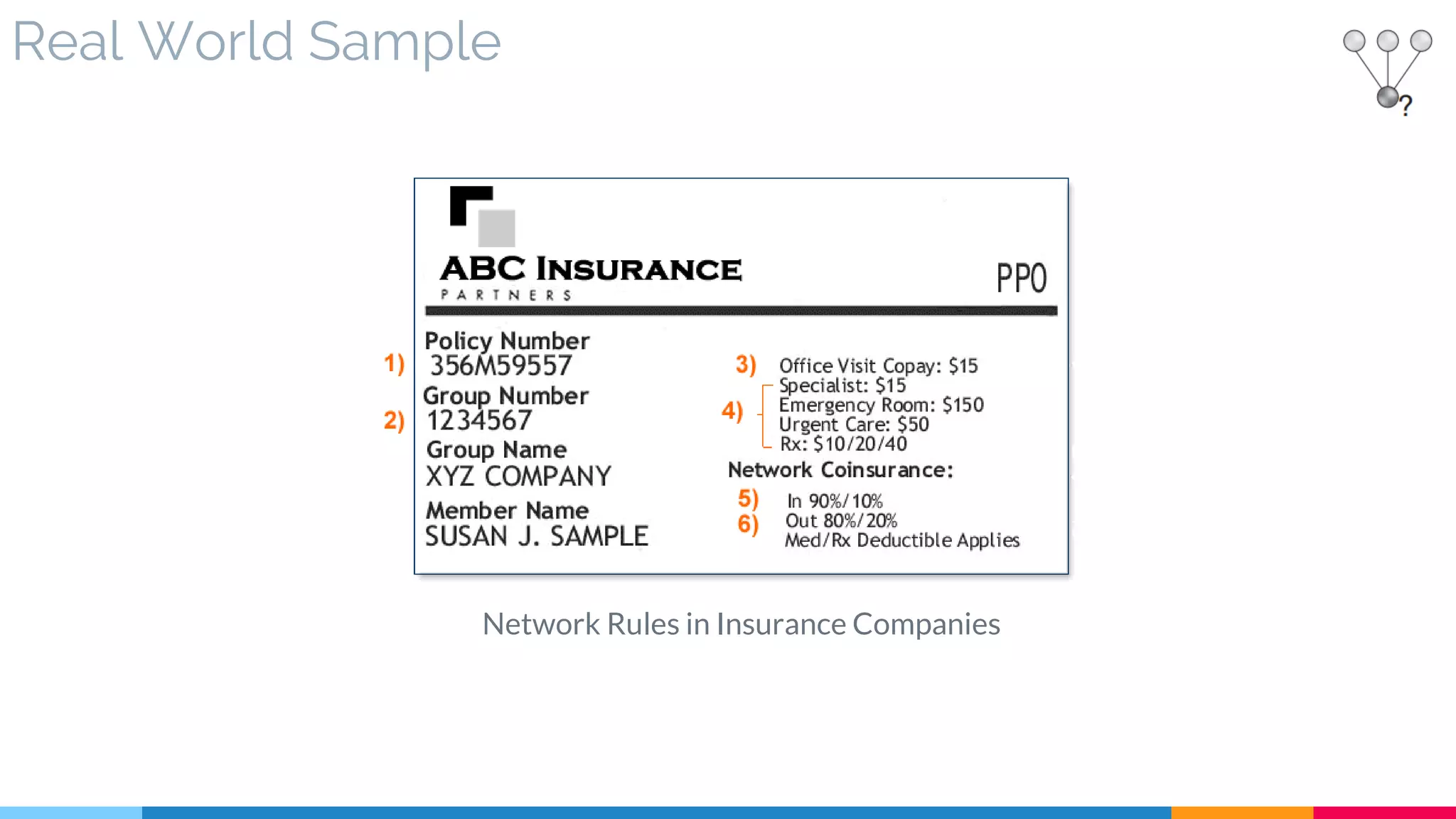
▷ Real World Sample
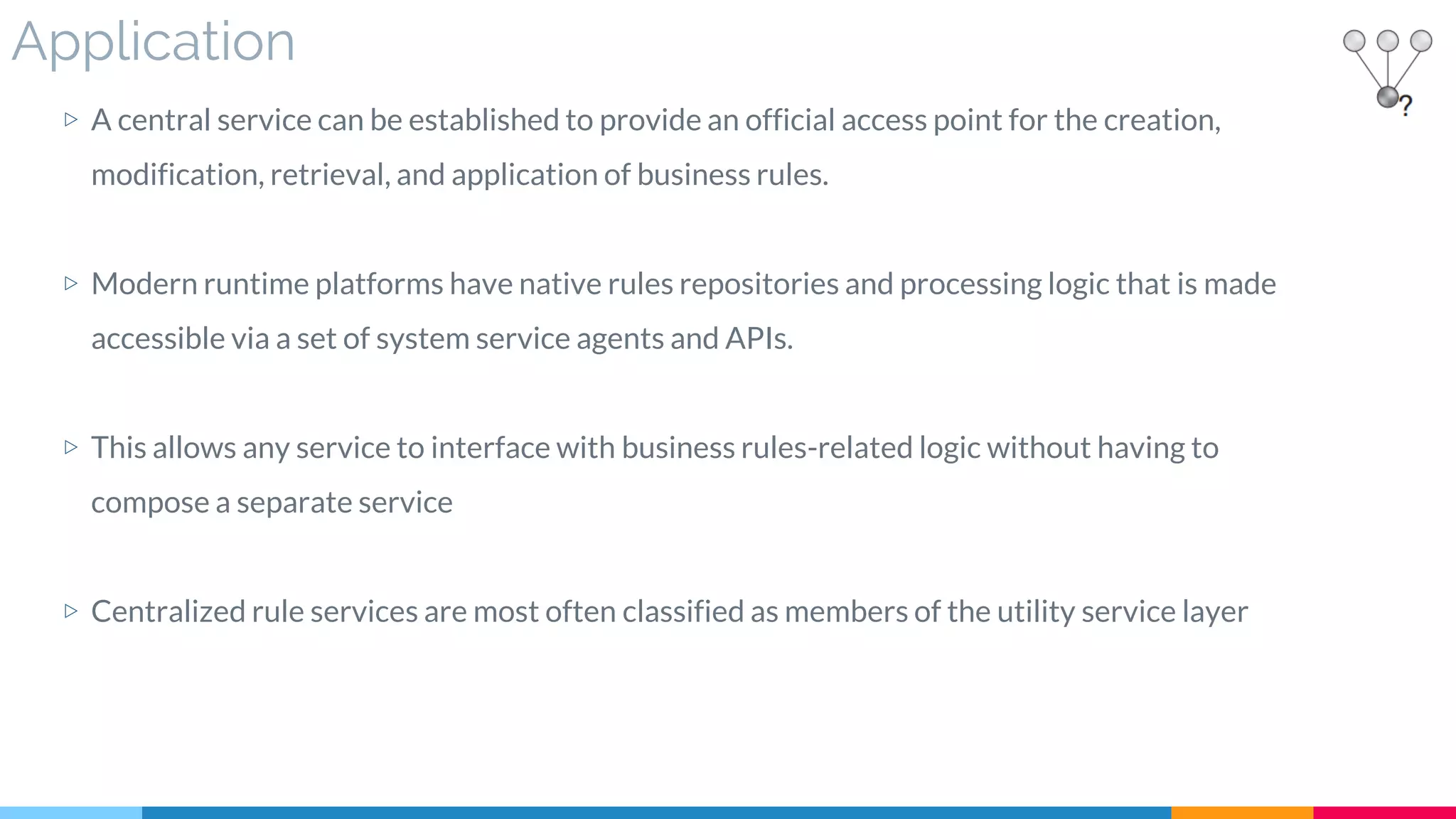
▷ Application
▷ Impact
▷ Relationships
[216]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-92-2048.jpg)

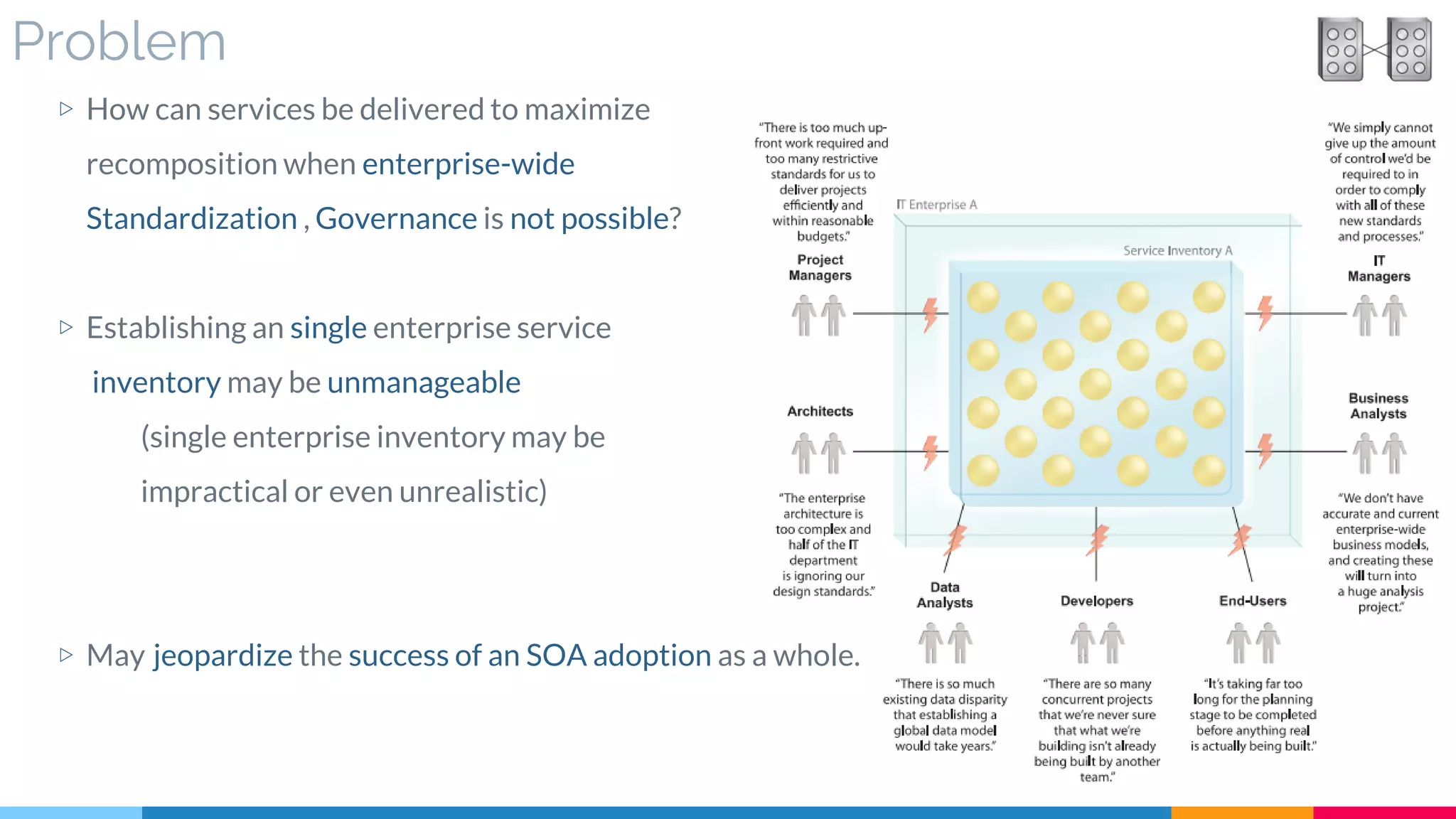
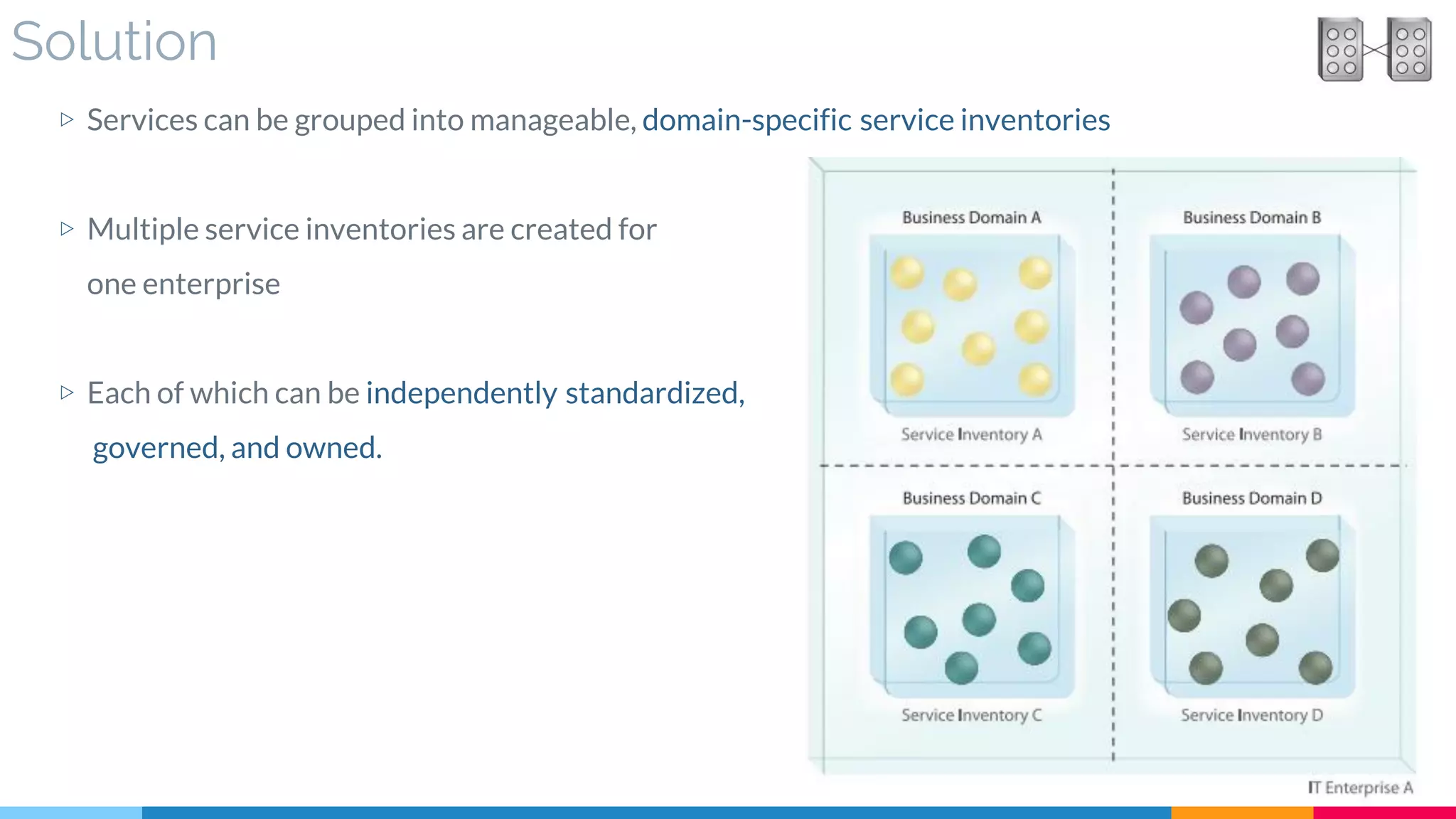
![12 Domain Inventory
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
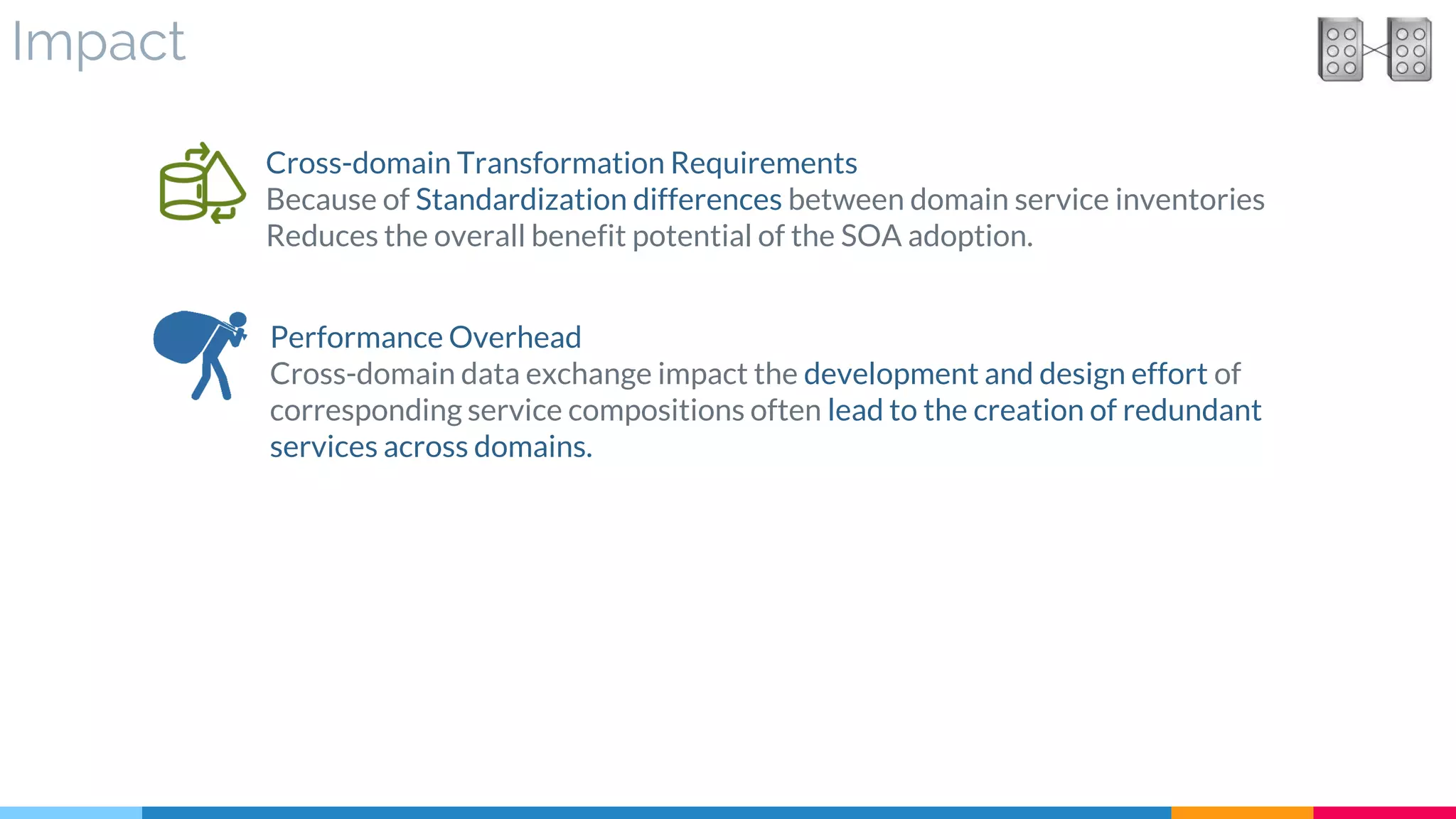
▷ Impact
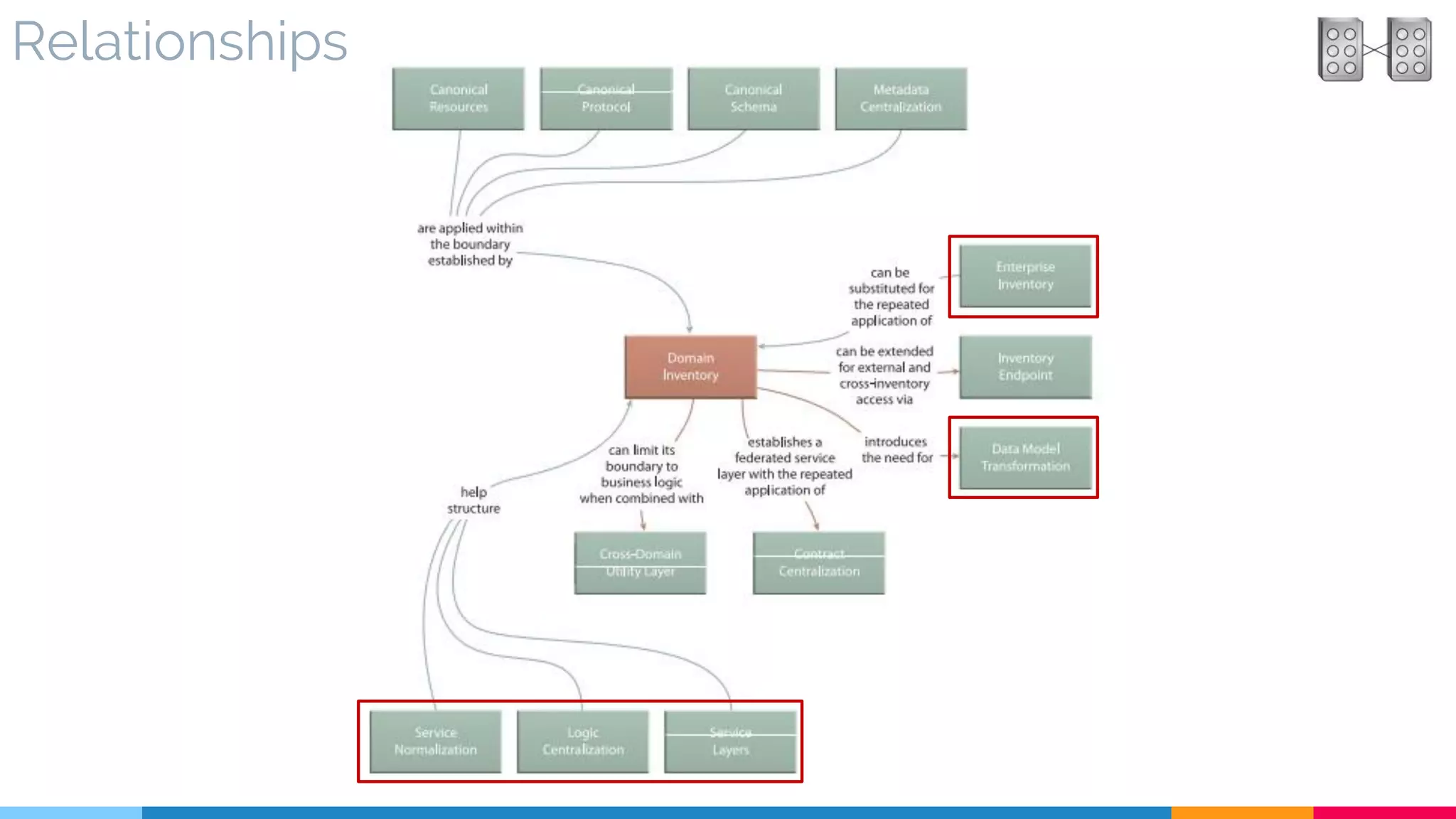
▷ Relationships
[123]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-101-2048.jpg)



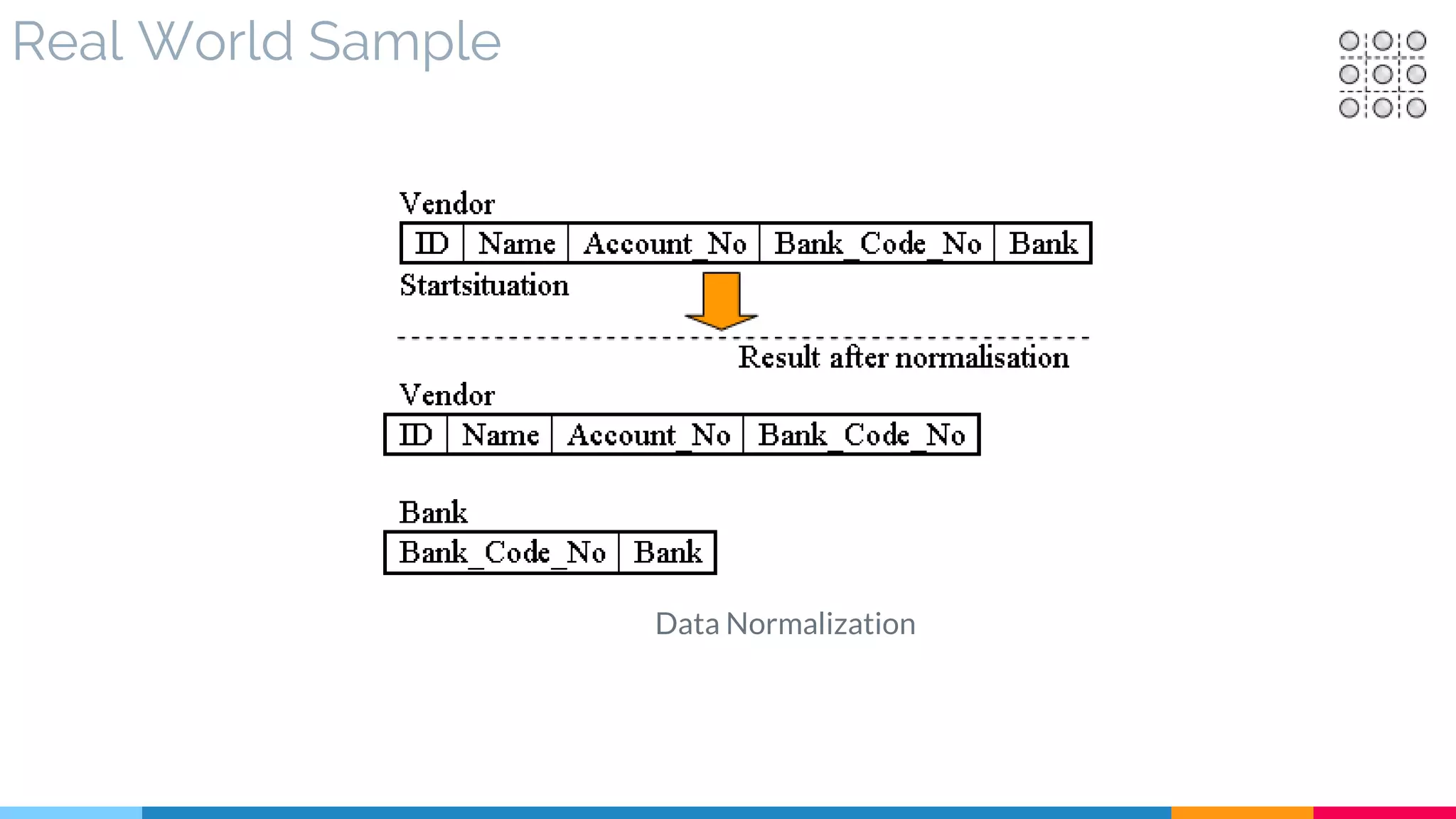
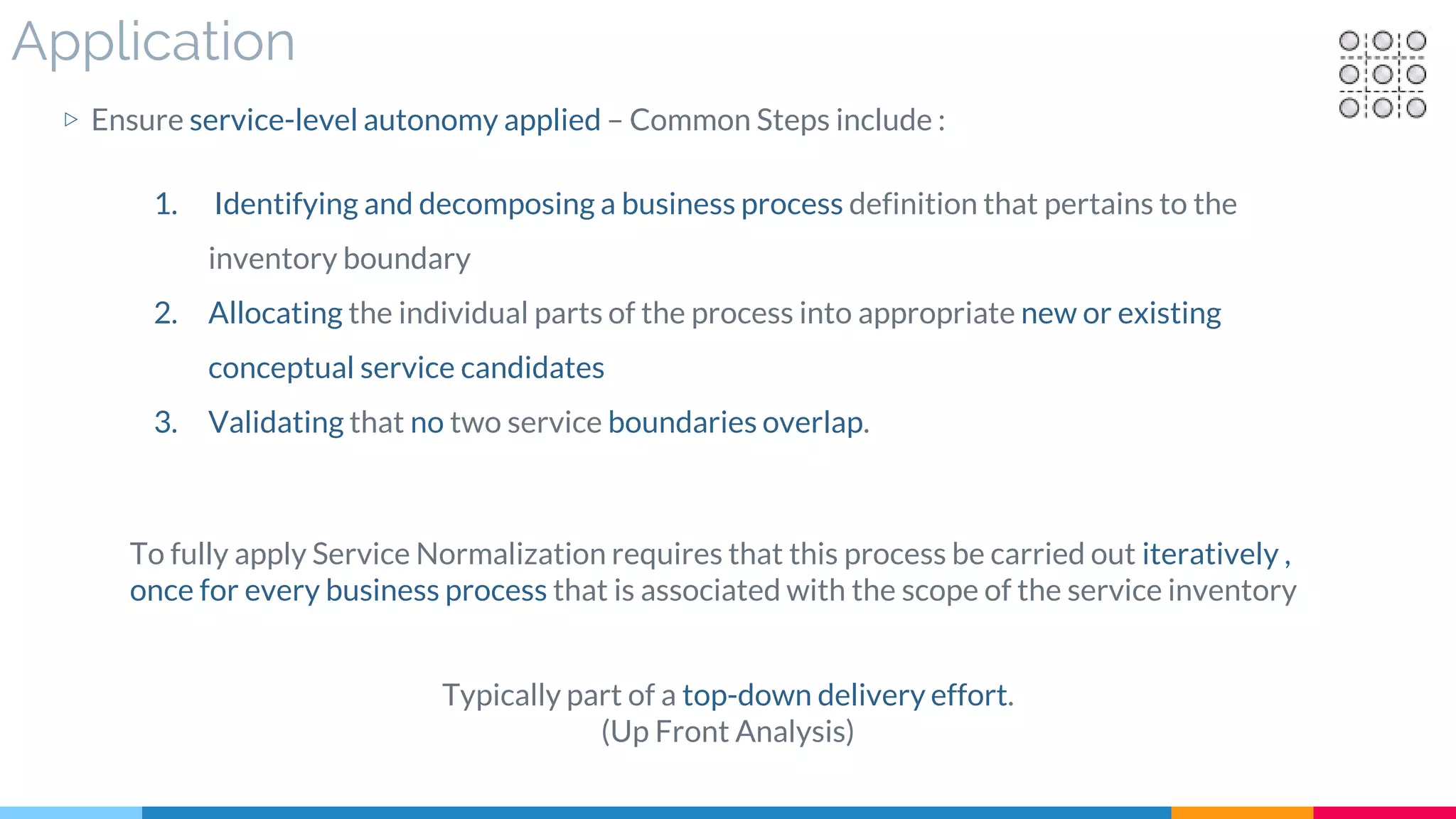
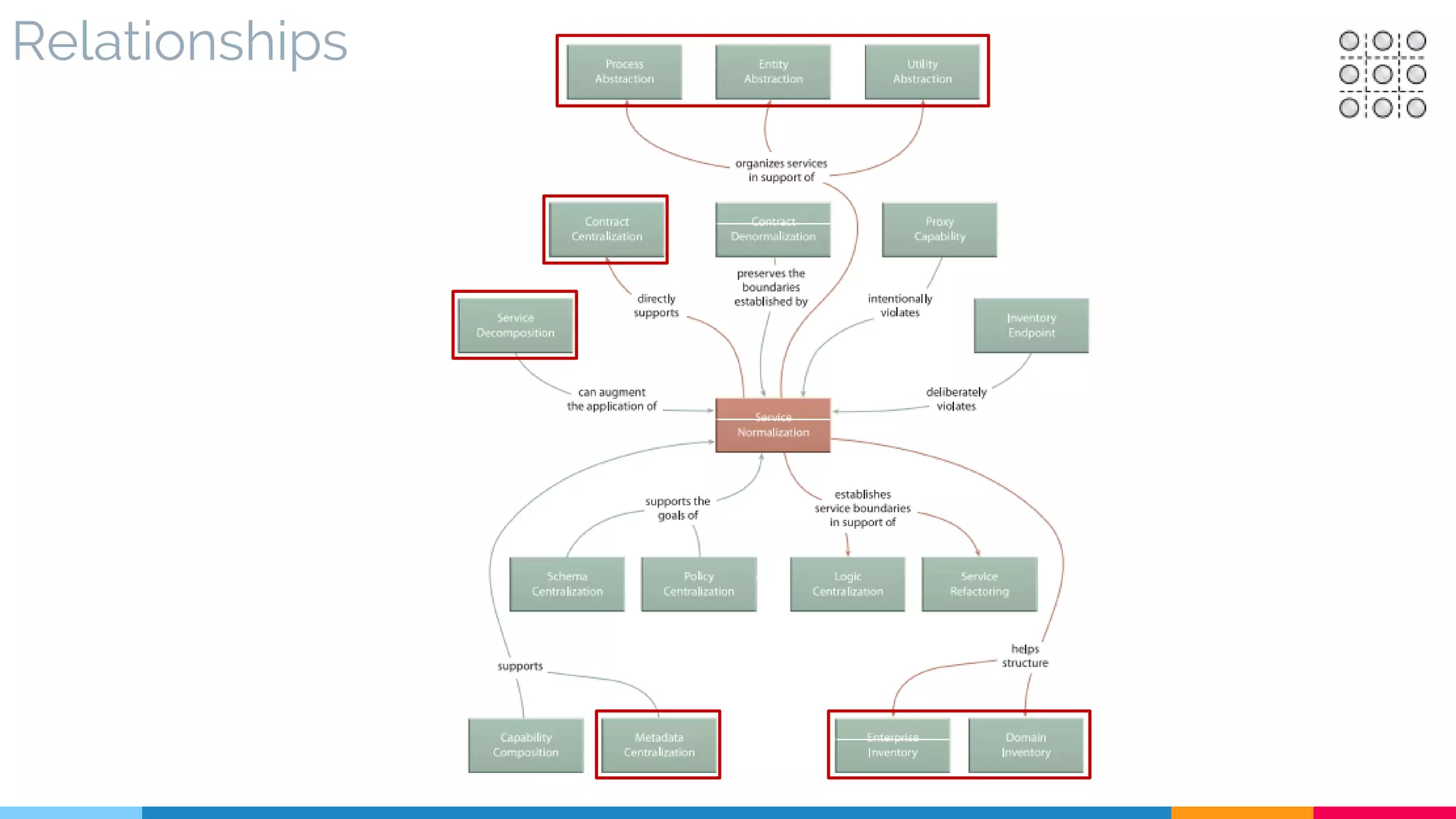
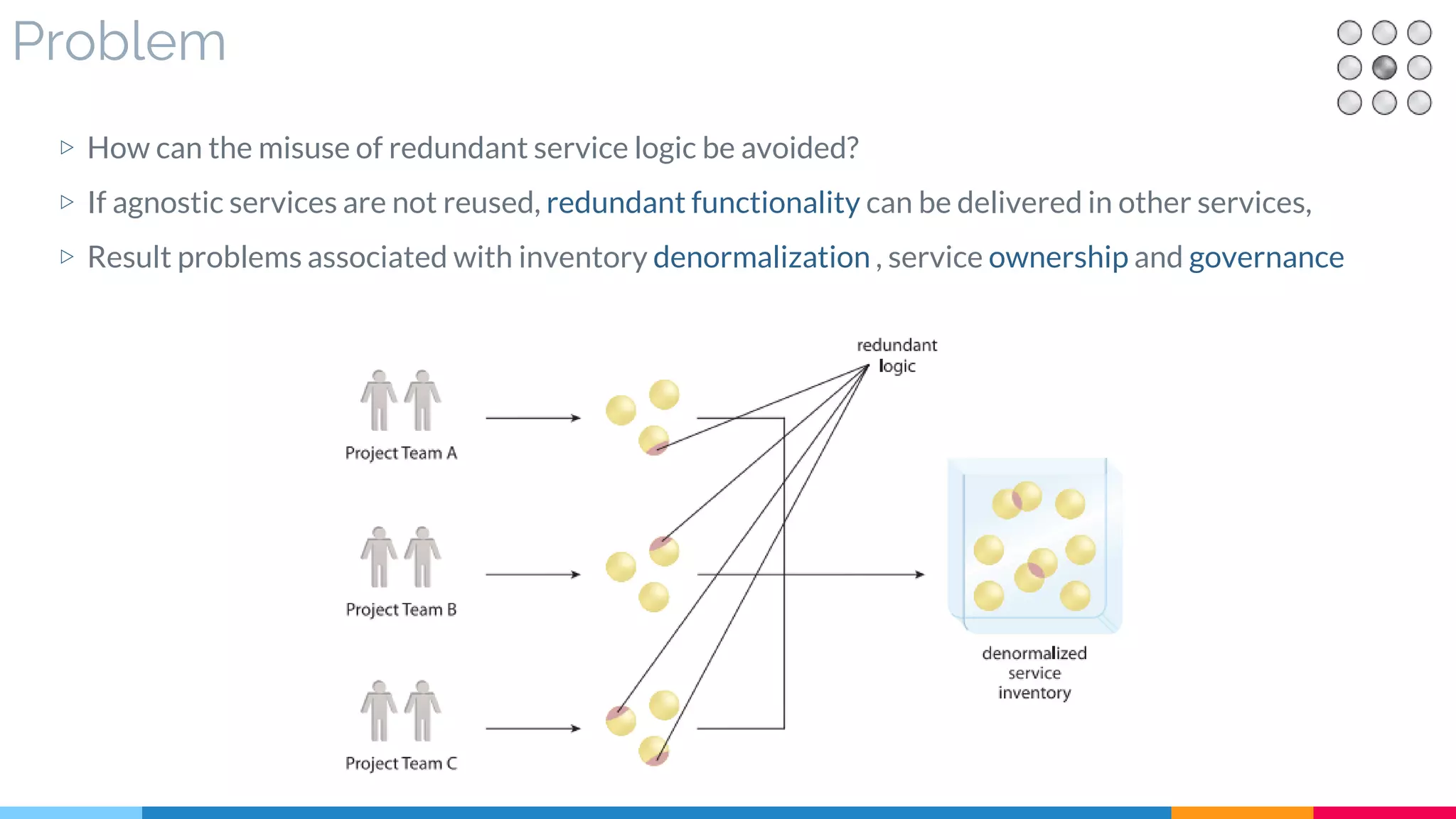
![13 Service Normalization
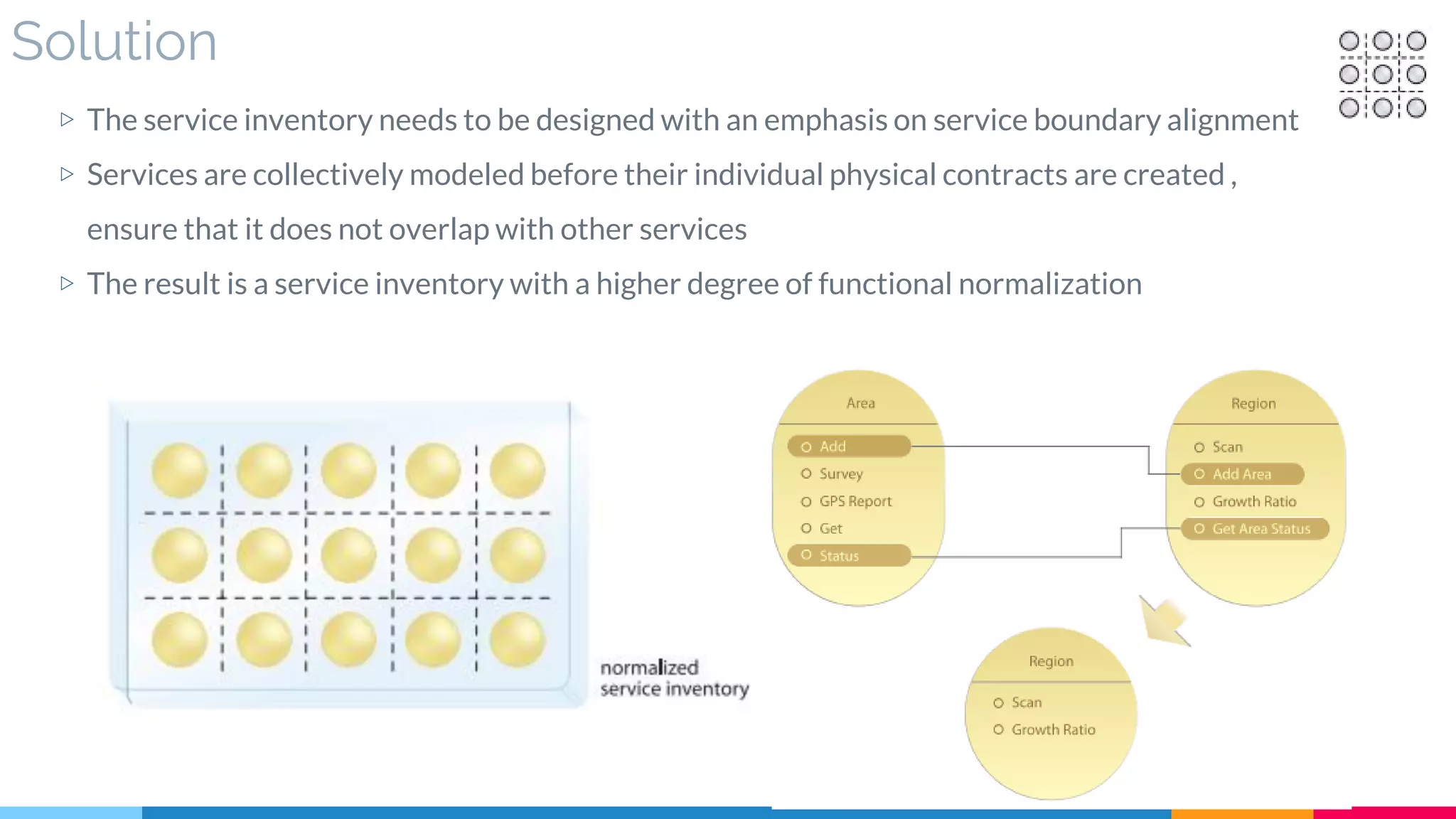
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[131]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-109-2048.jpg)


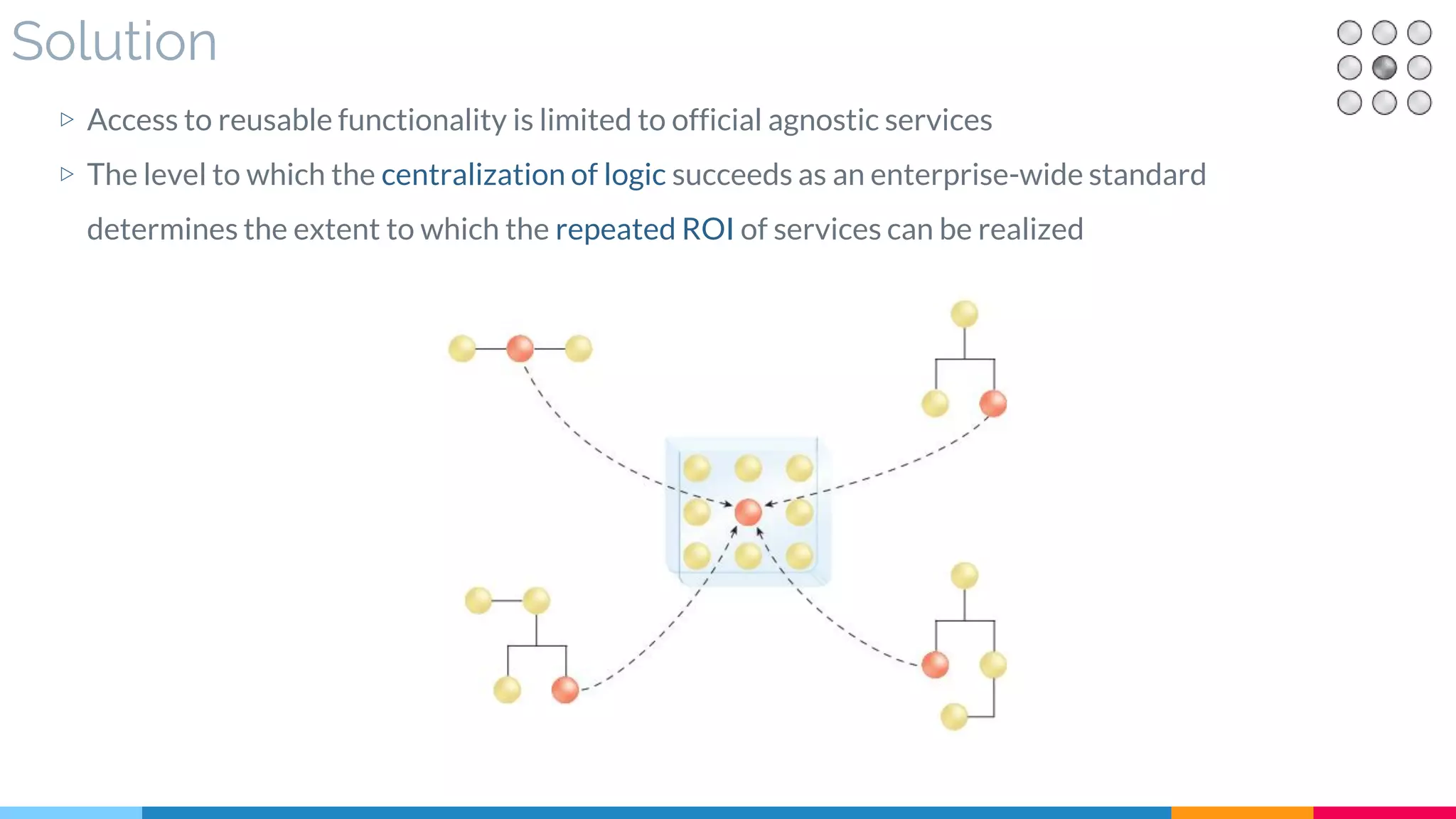
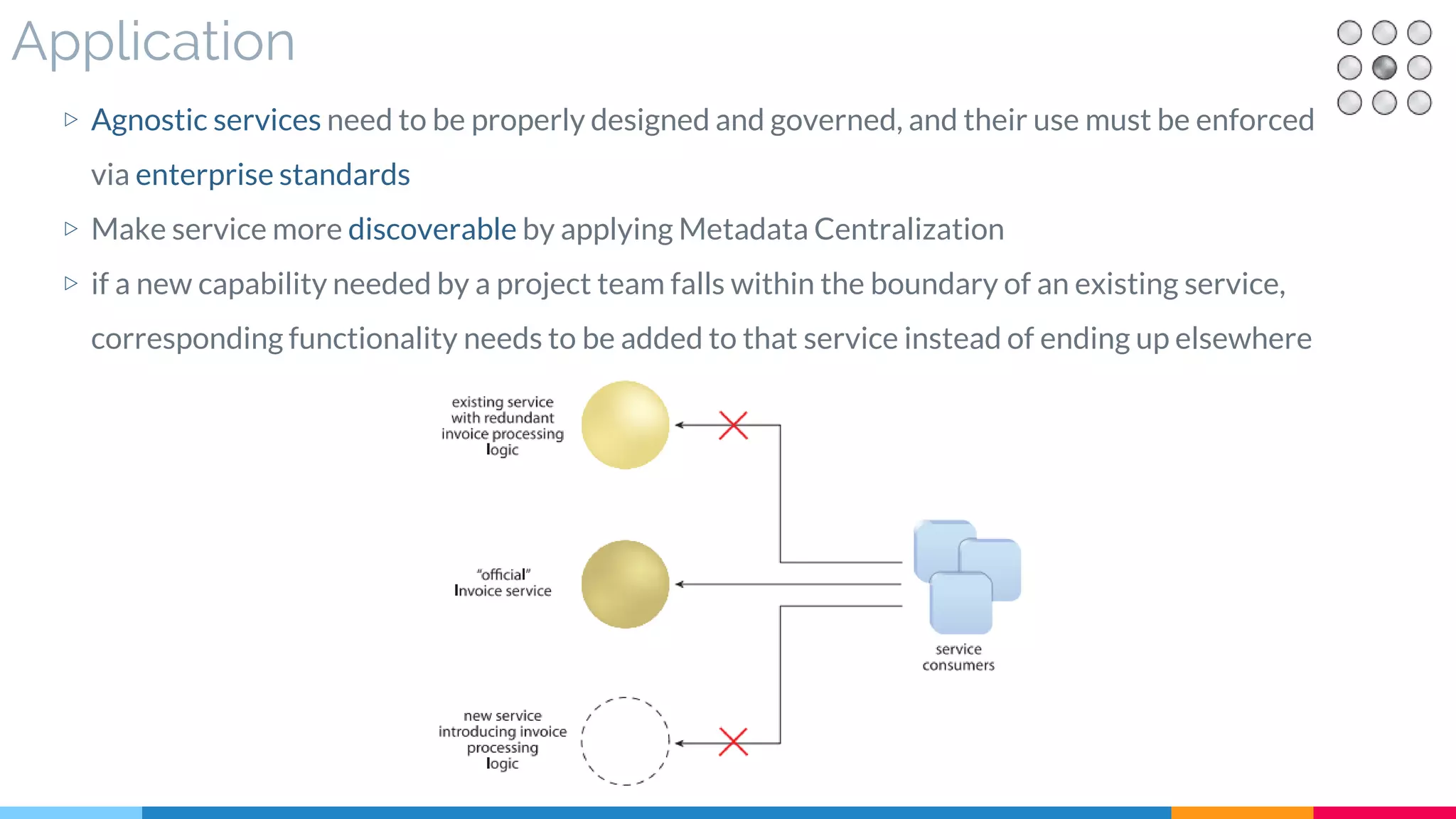
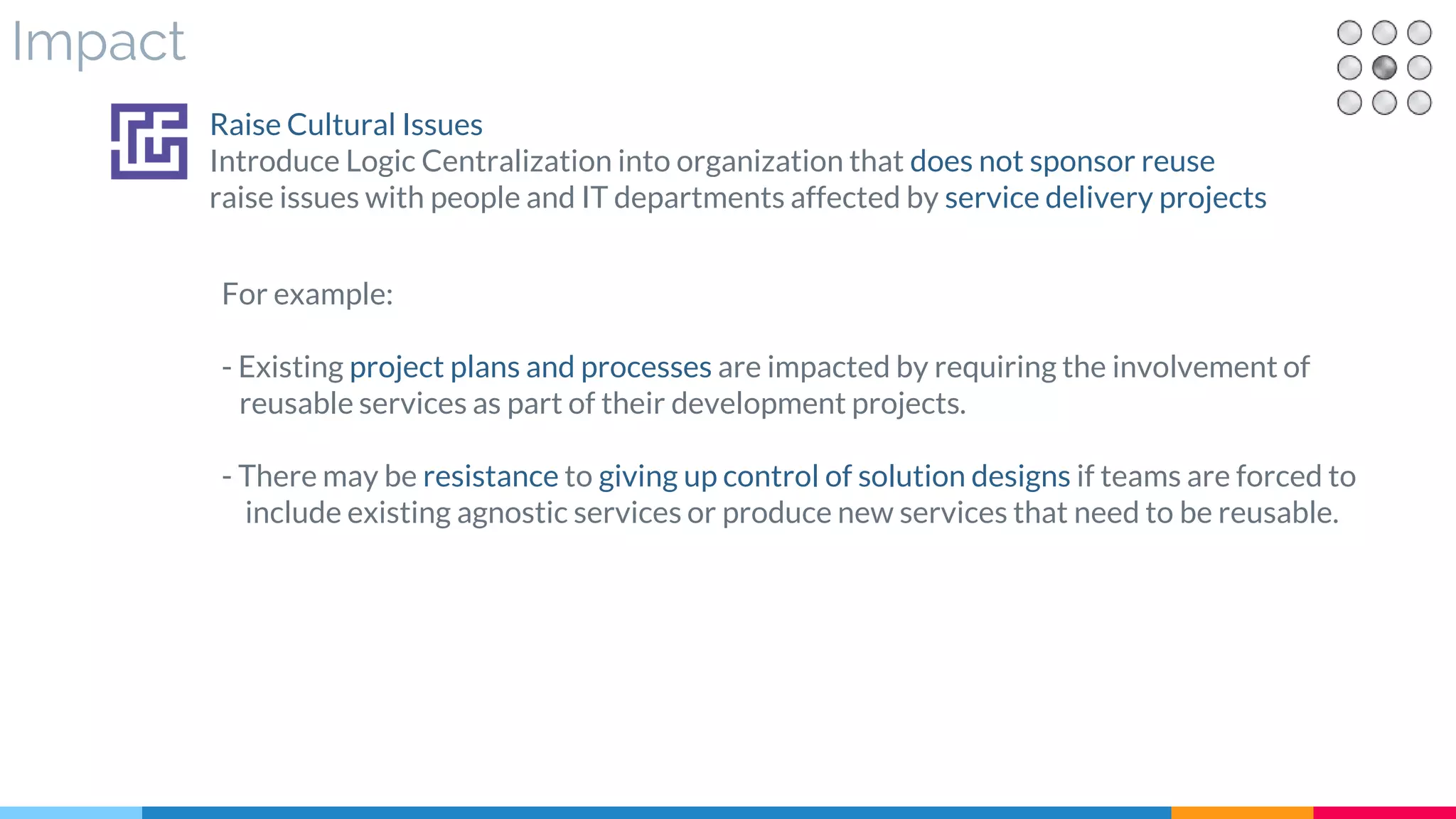
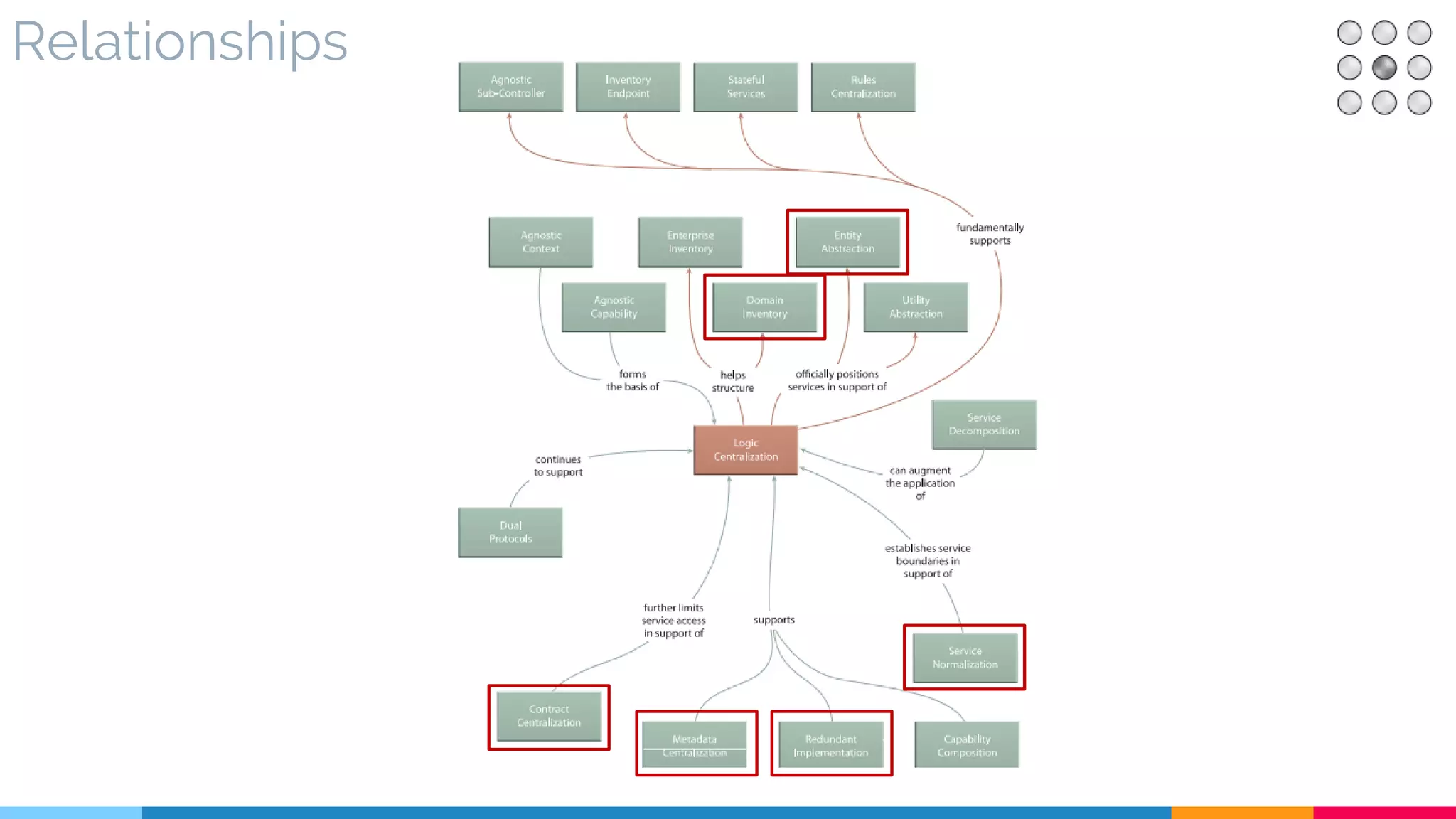
![14 Logic Centralization
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[136]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-116-2048.jpg)

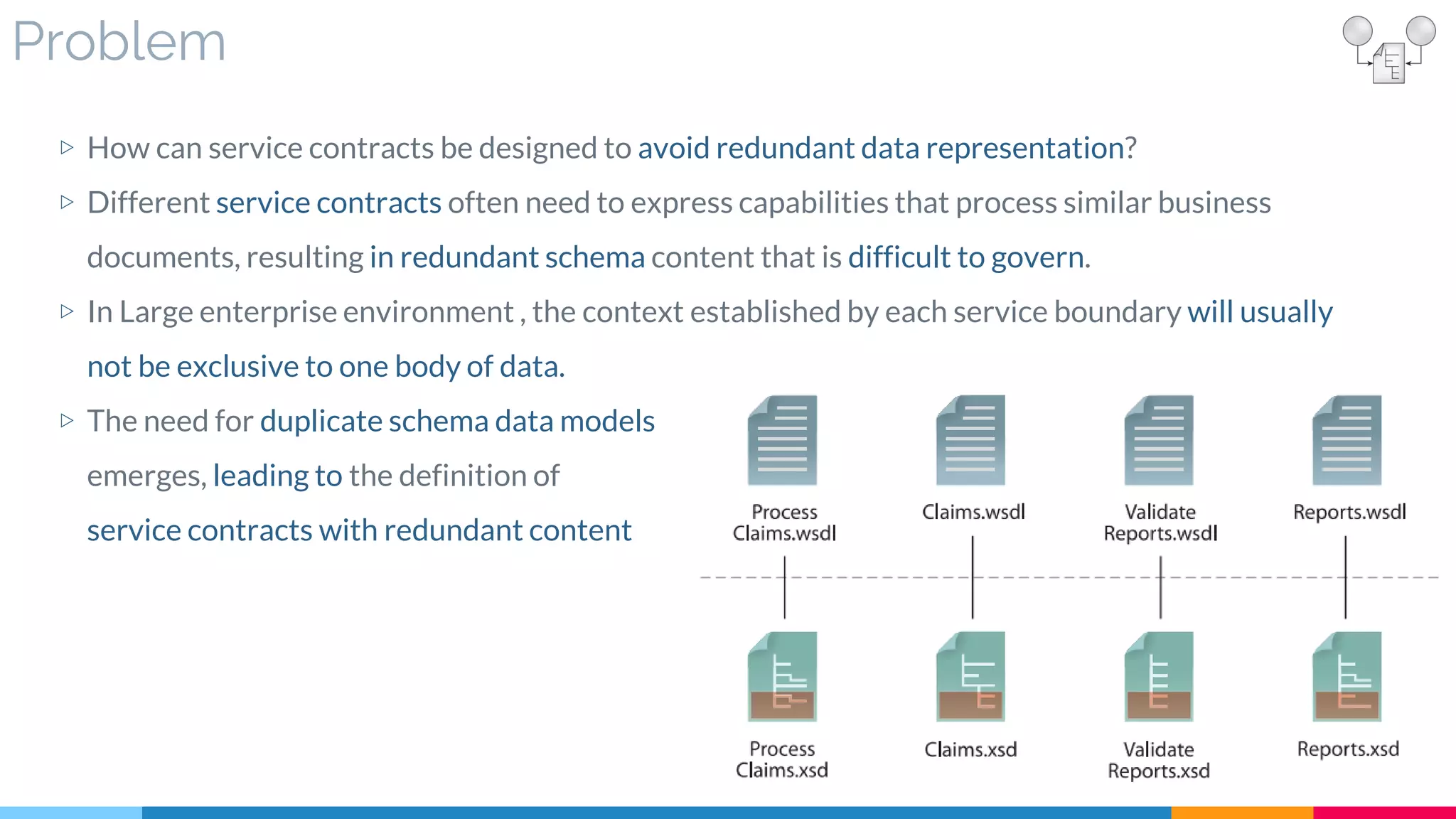
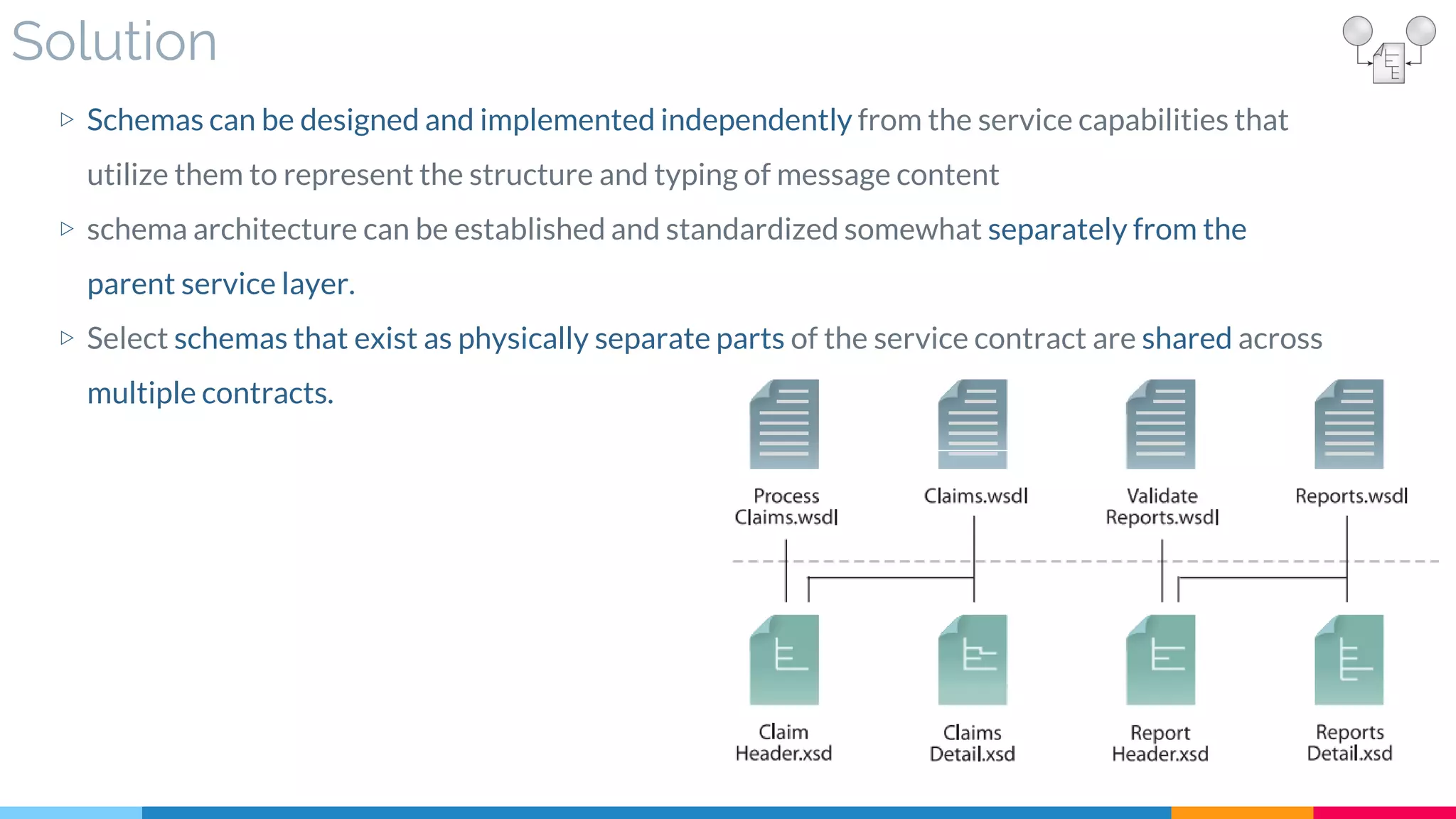
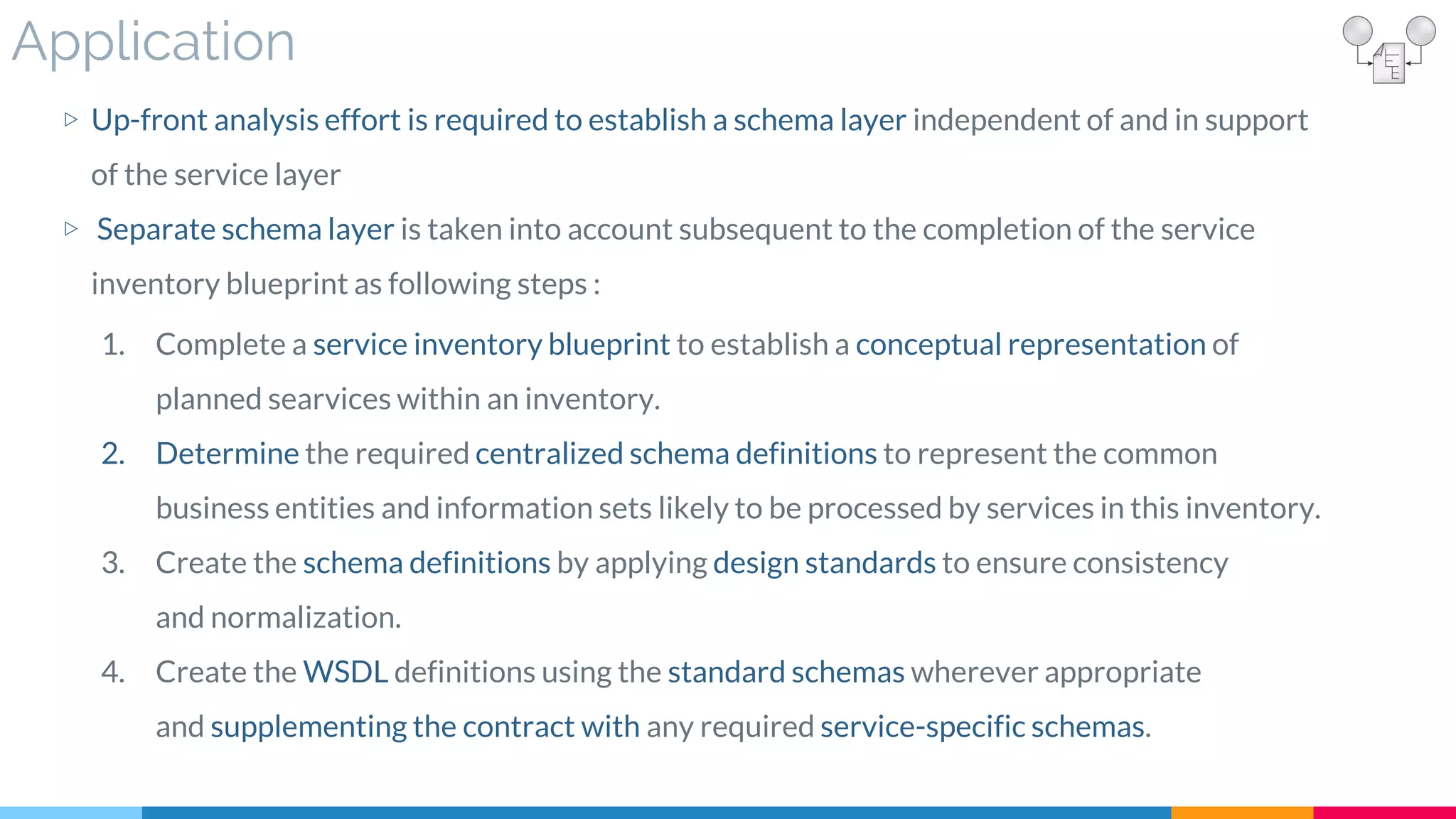
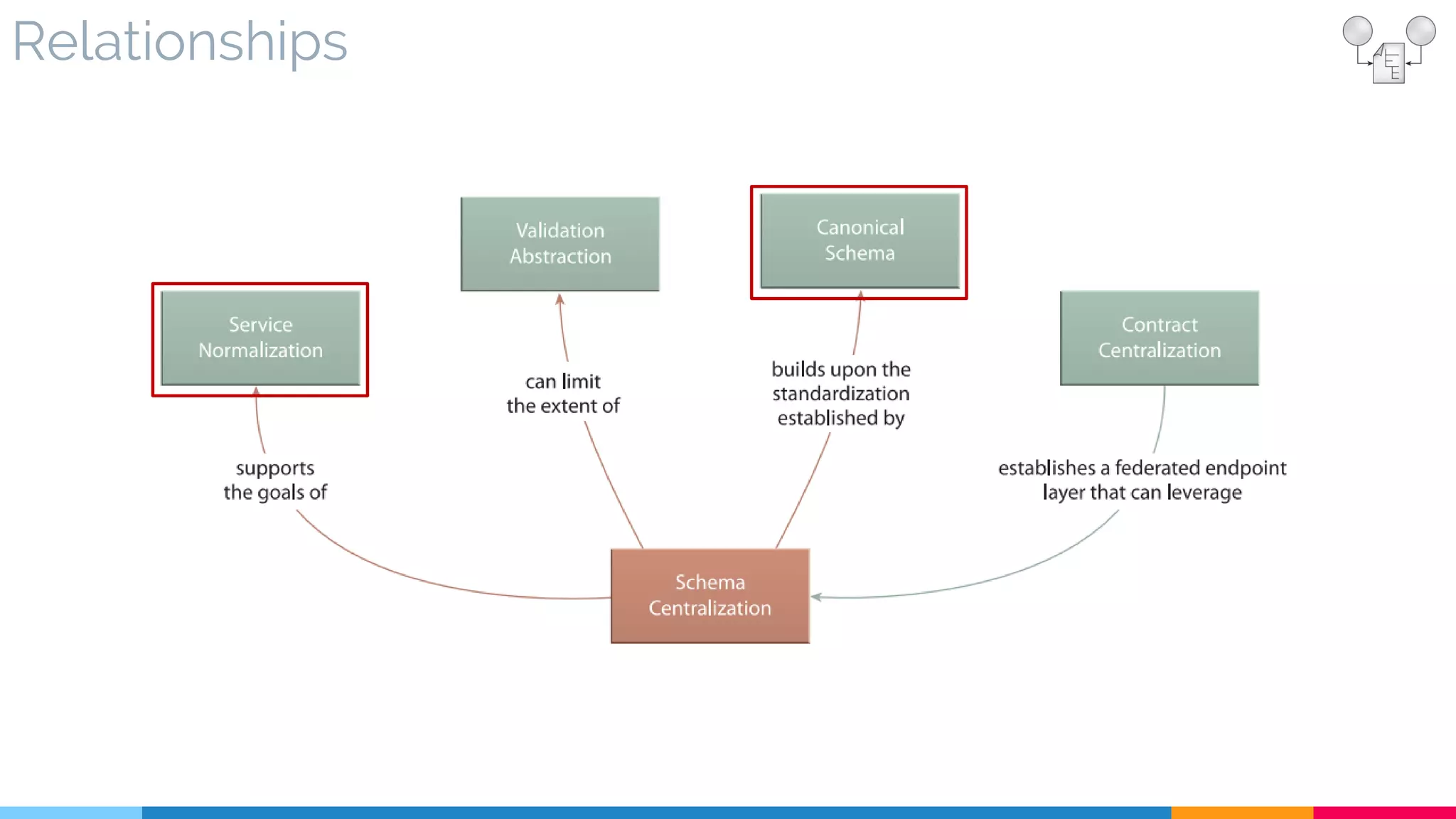
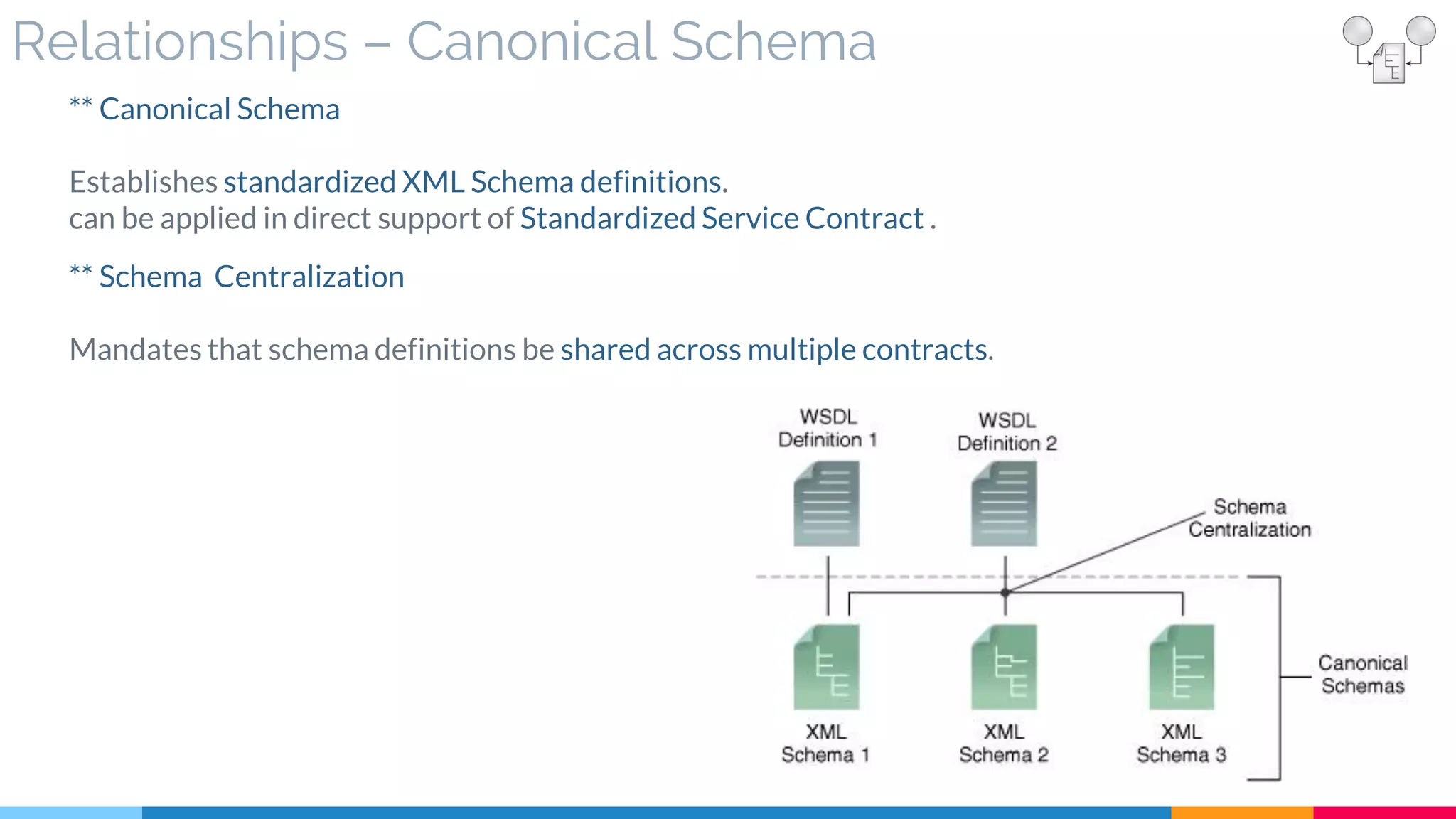
![15 Schema Centralization
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[200]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-123-2048.jpg)



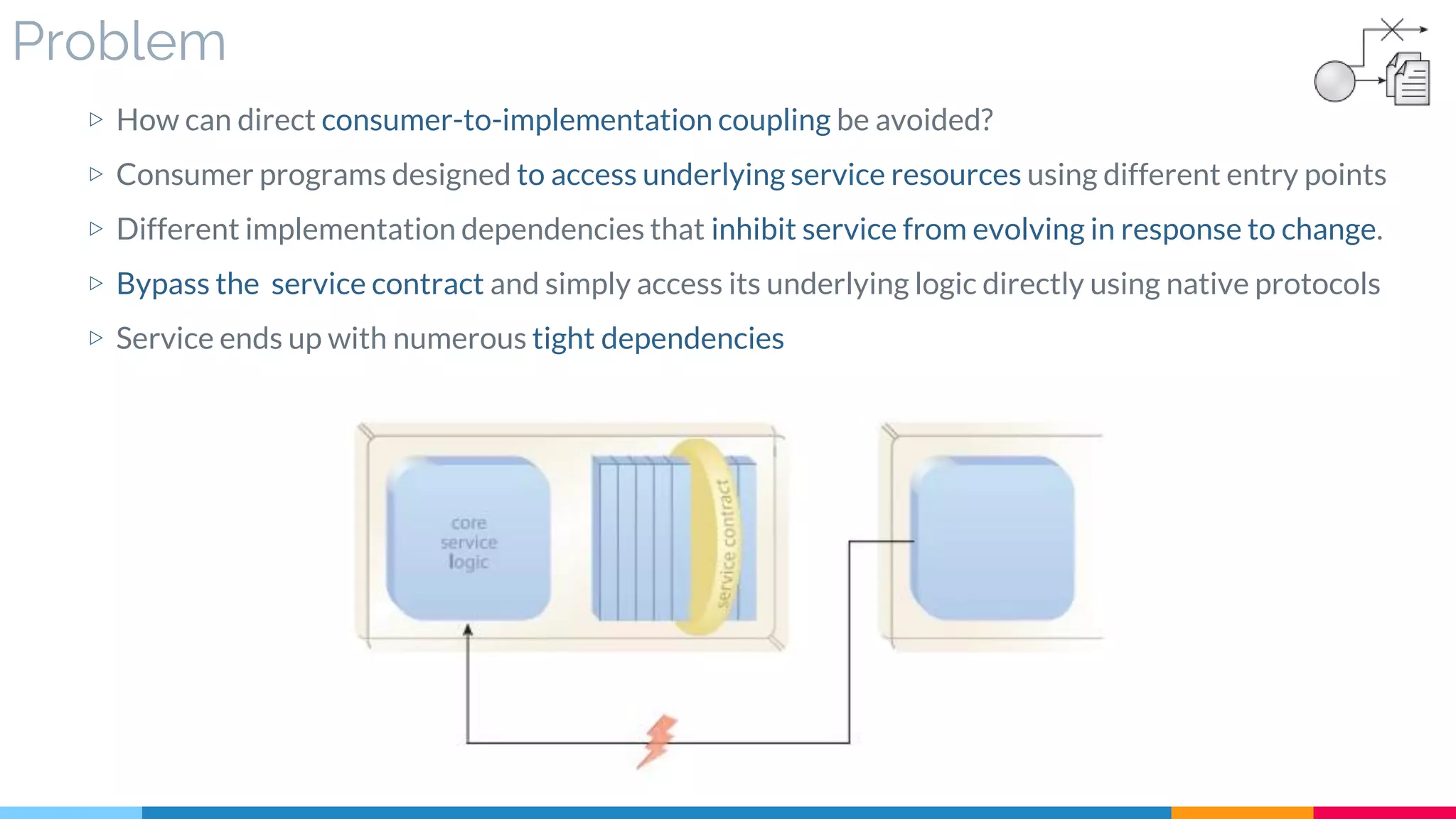
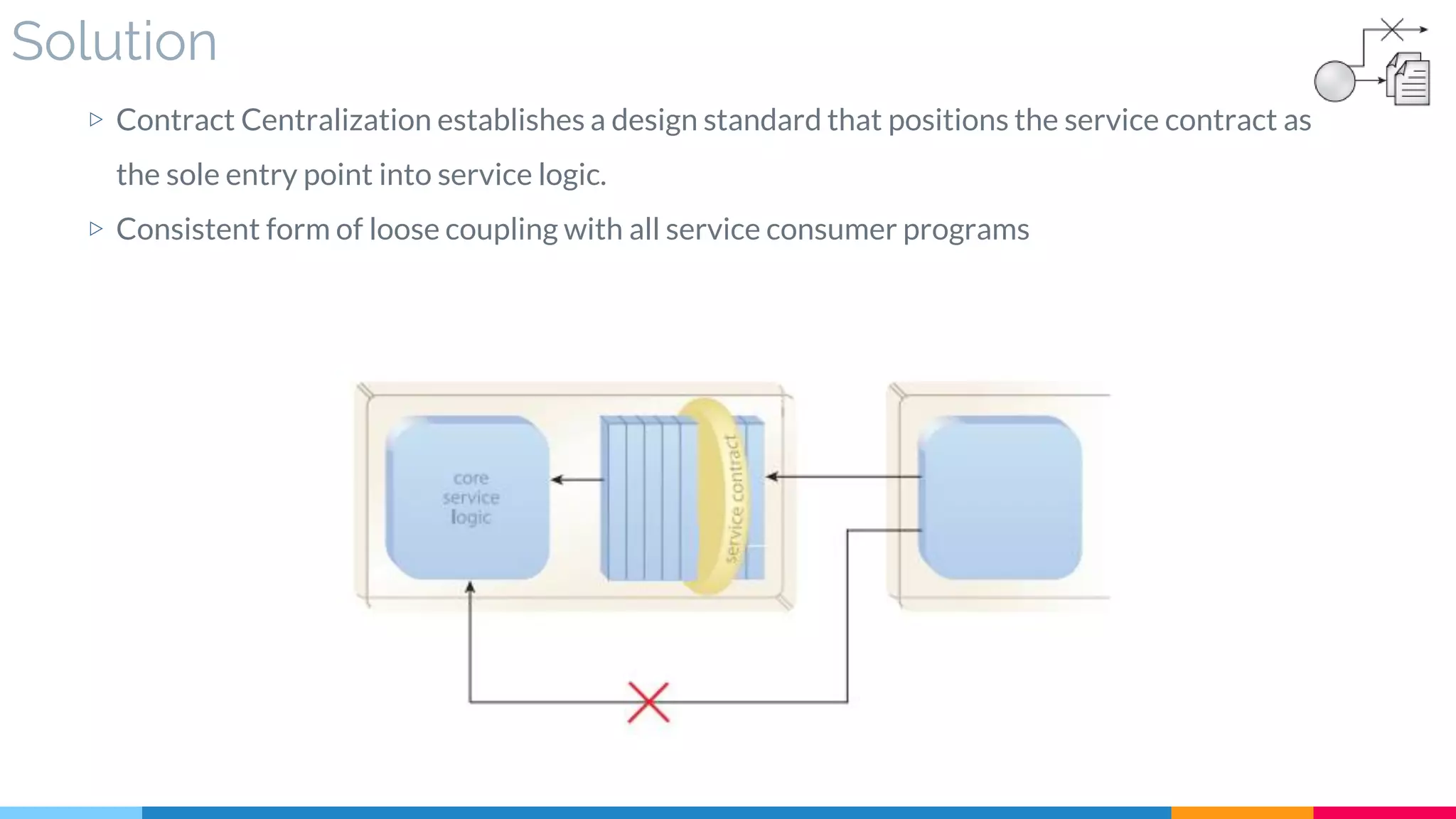
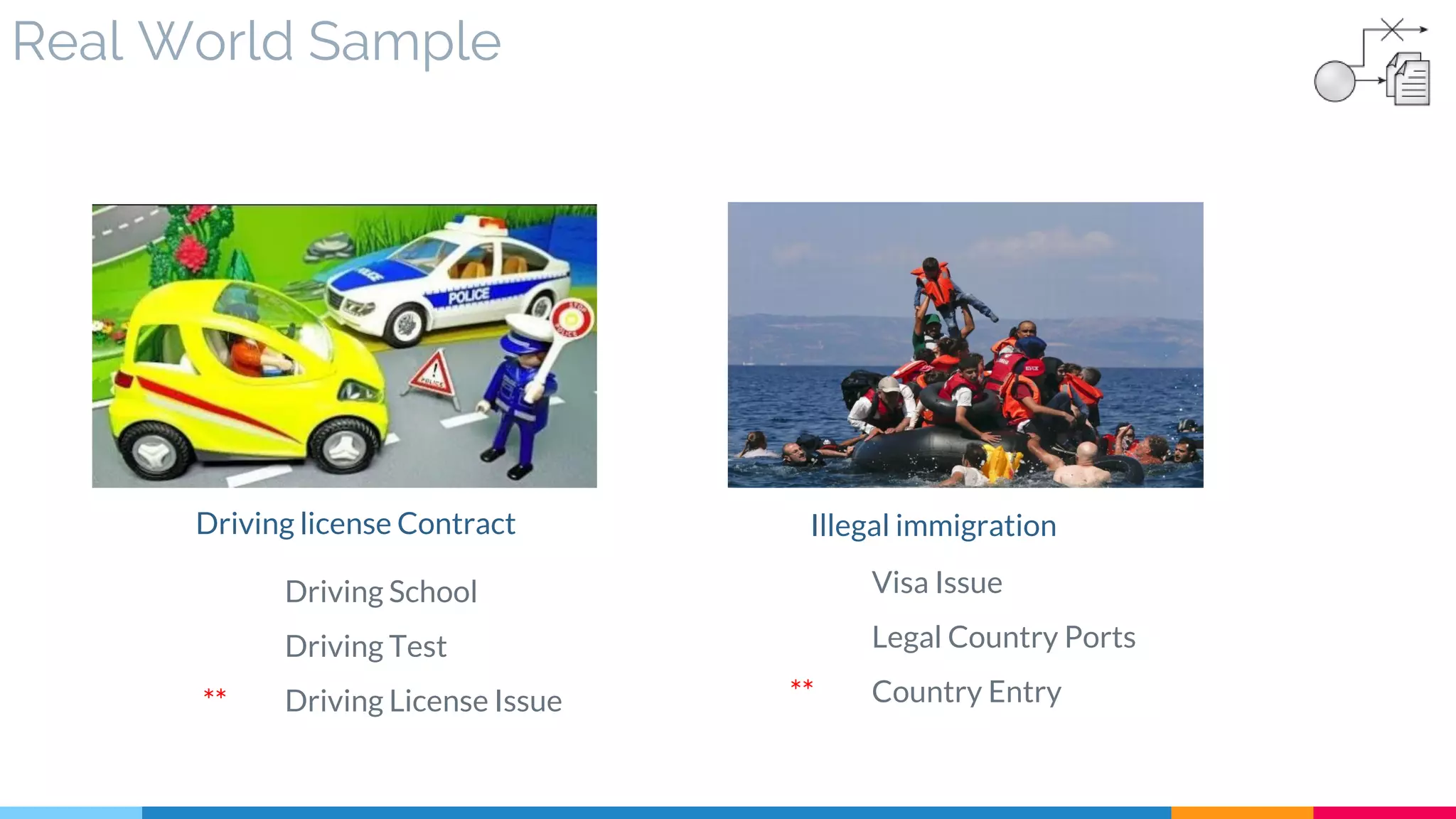
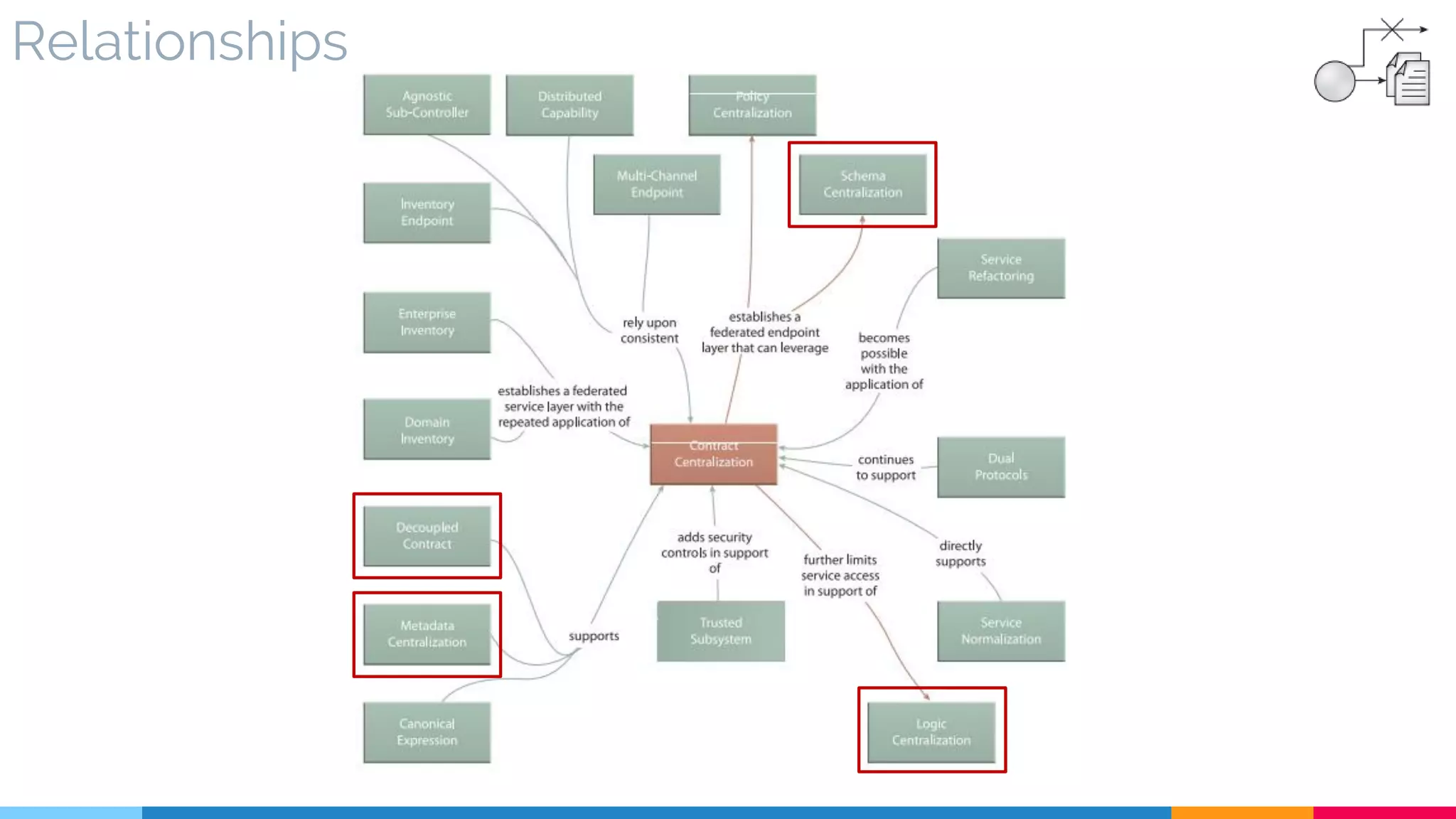
![16 Contract Centralization
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[409]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-132-2048.jpg)


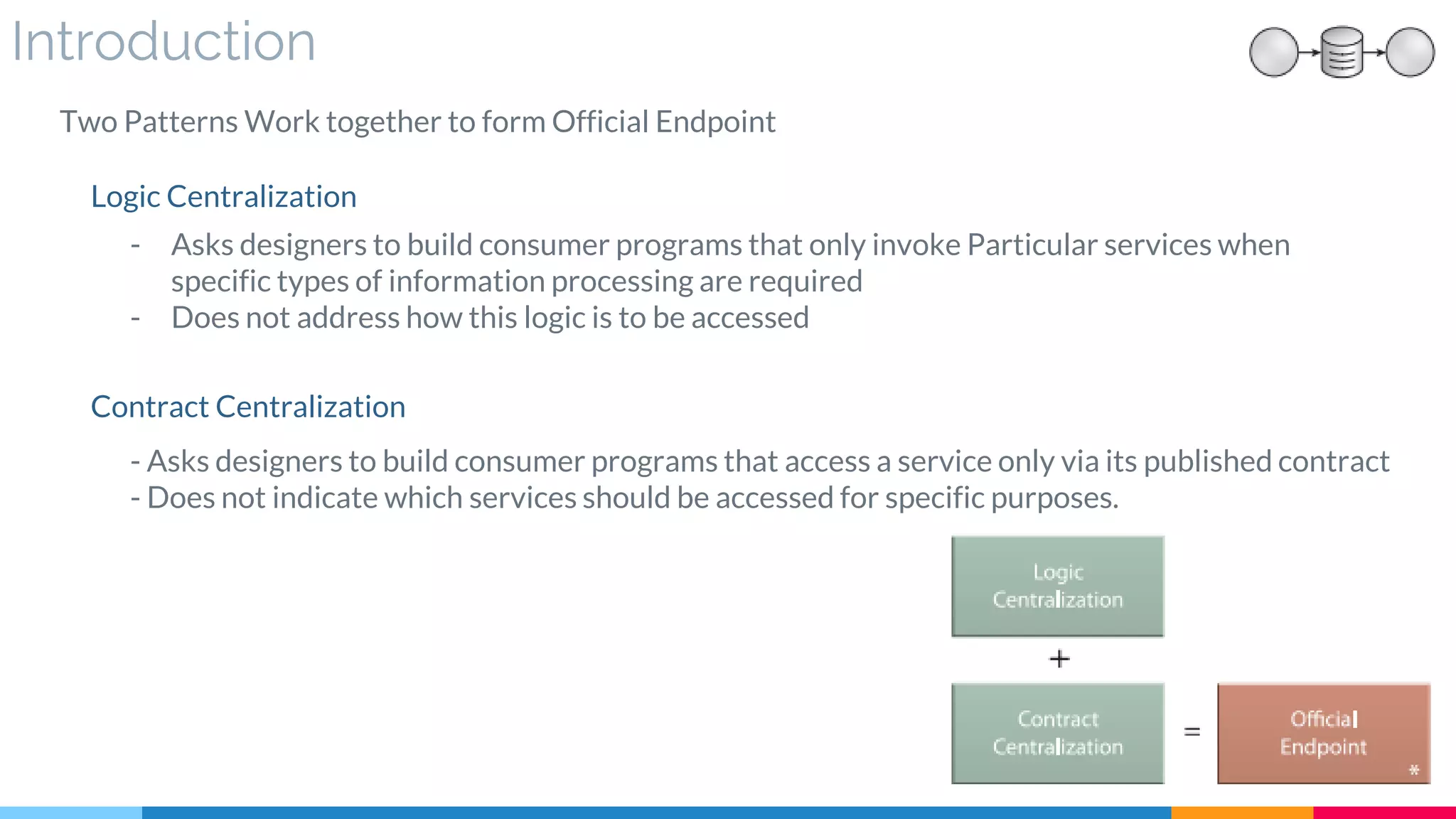
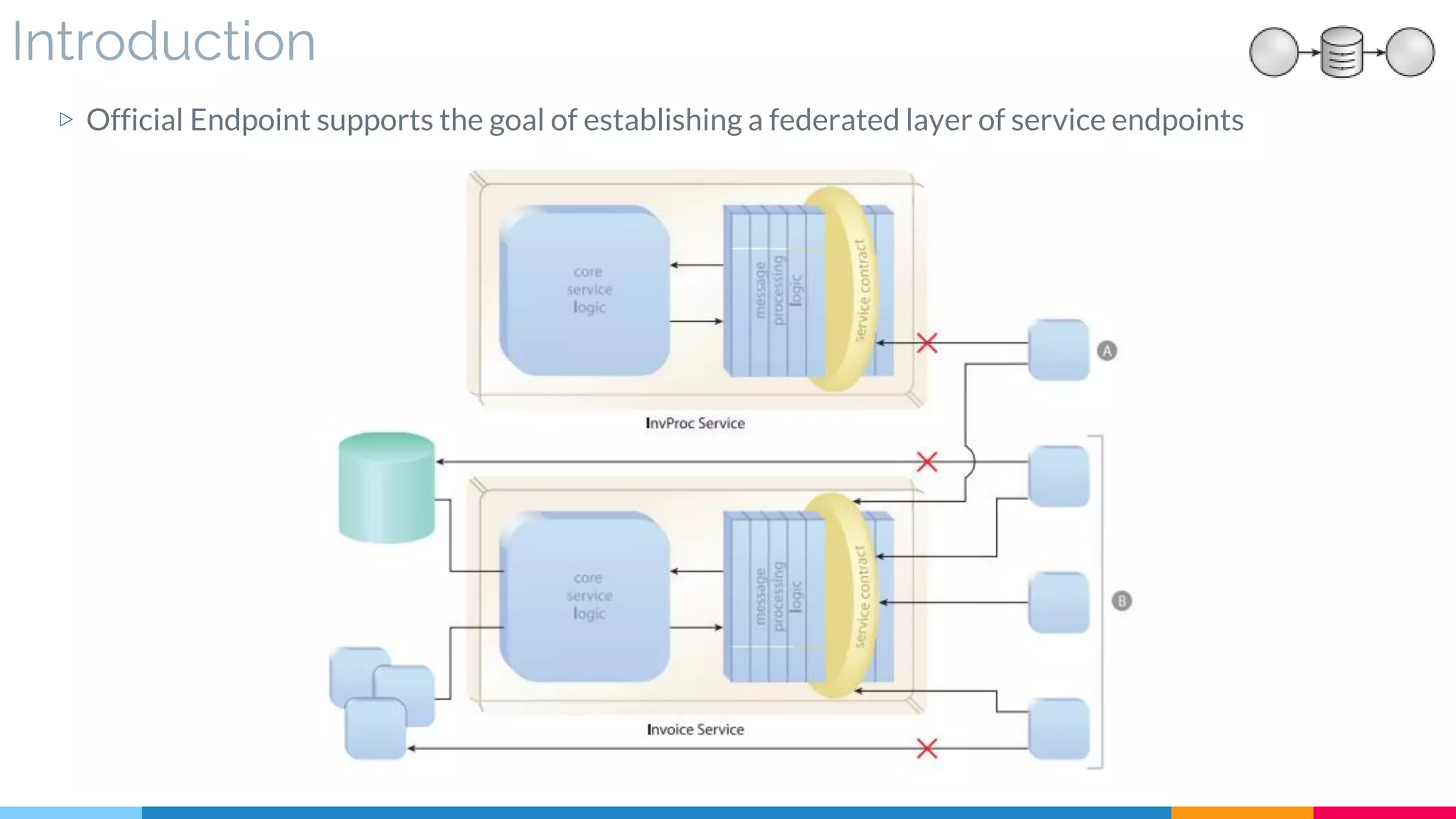
![17 Official Endpoint
▷ Introduction
[711]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-139-2048.jpg)
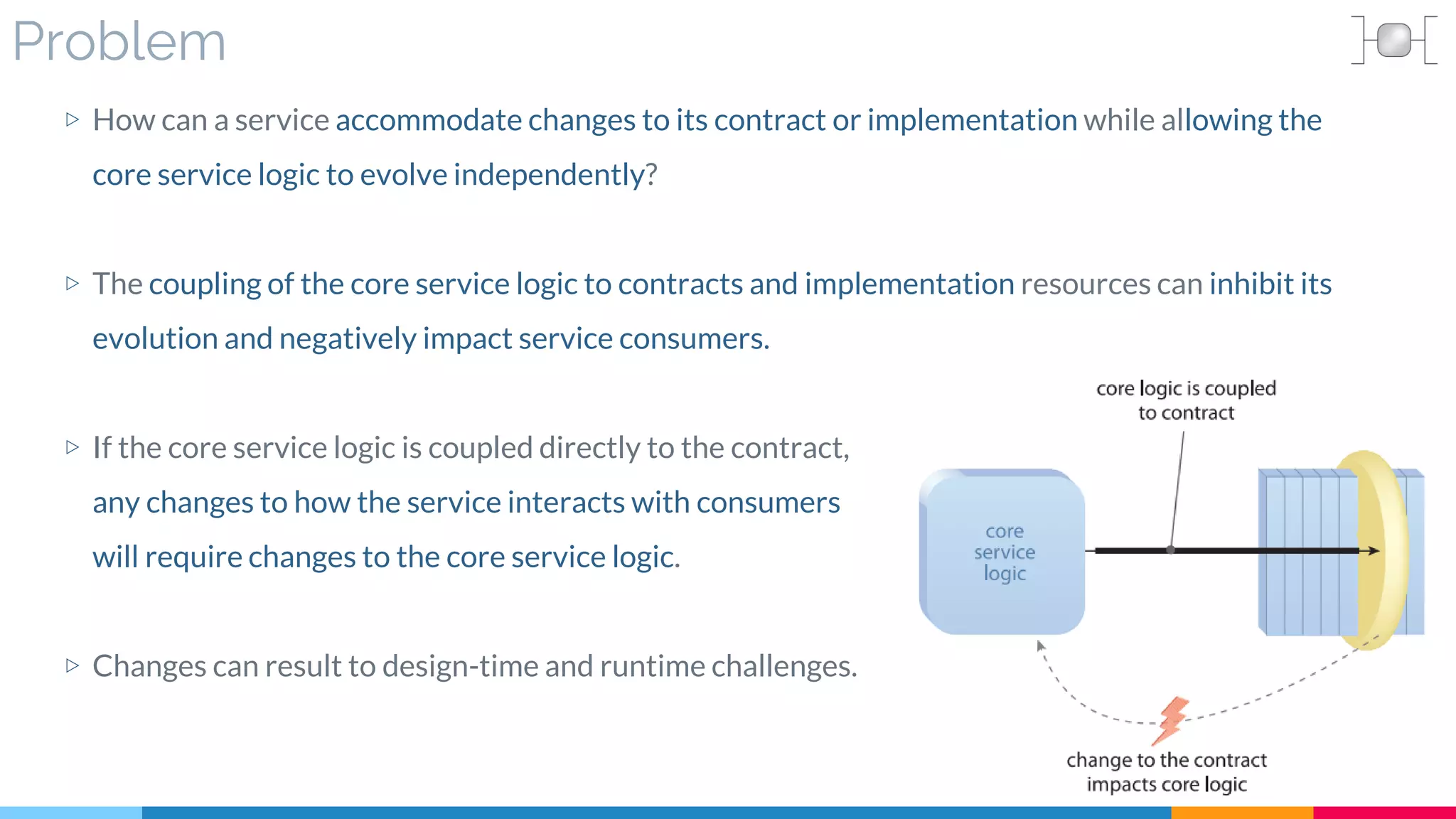
![18 Service Façade
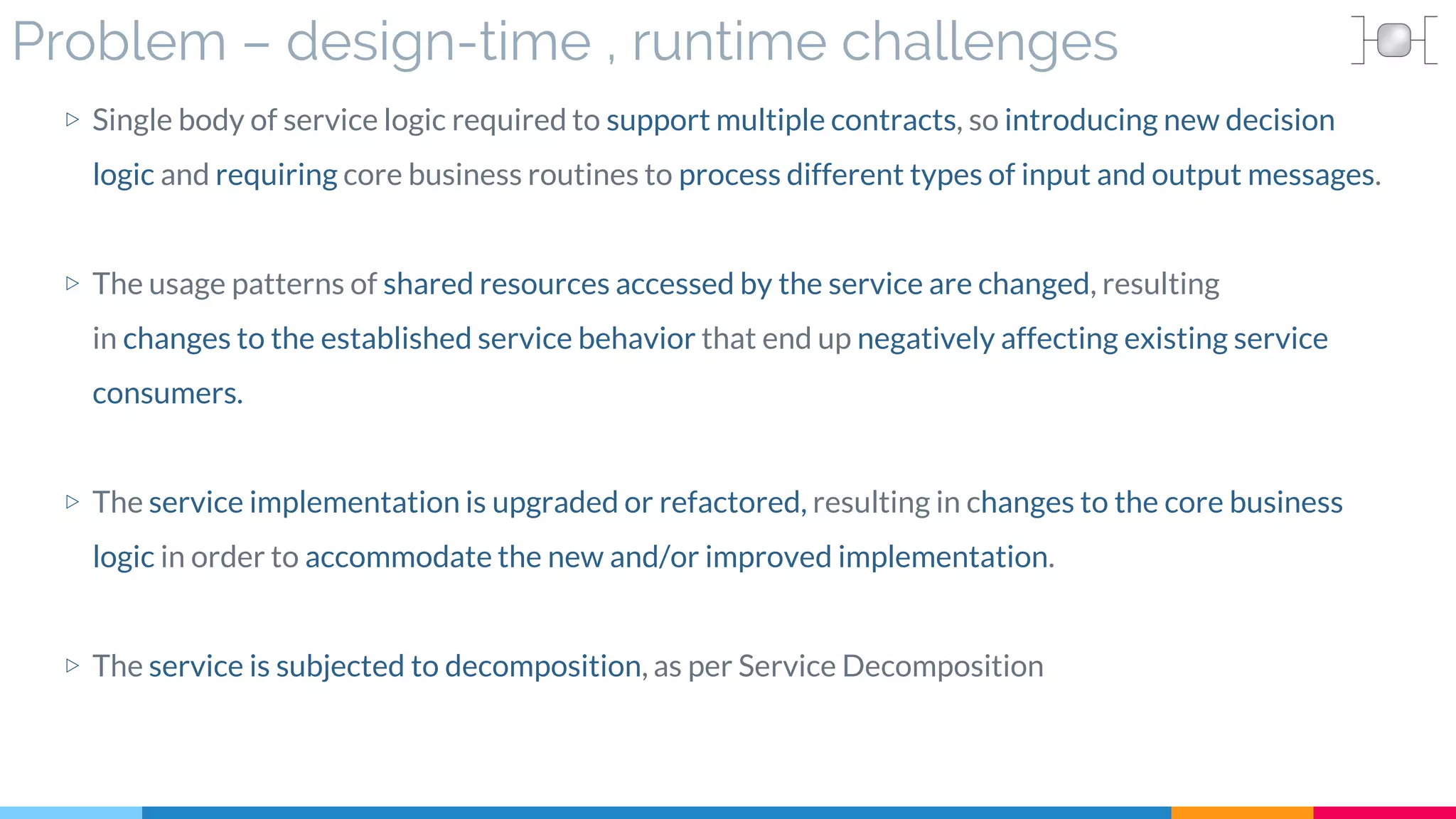
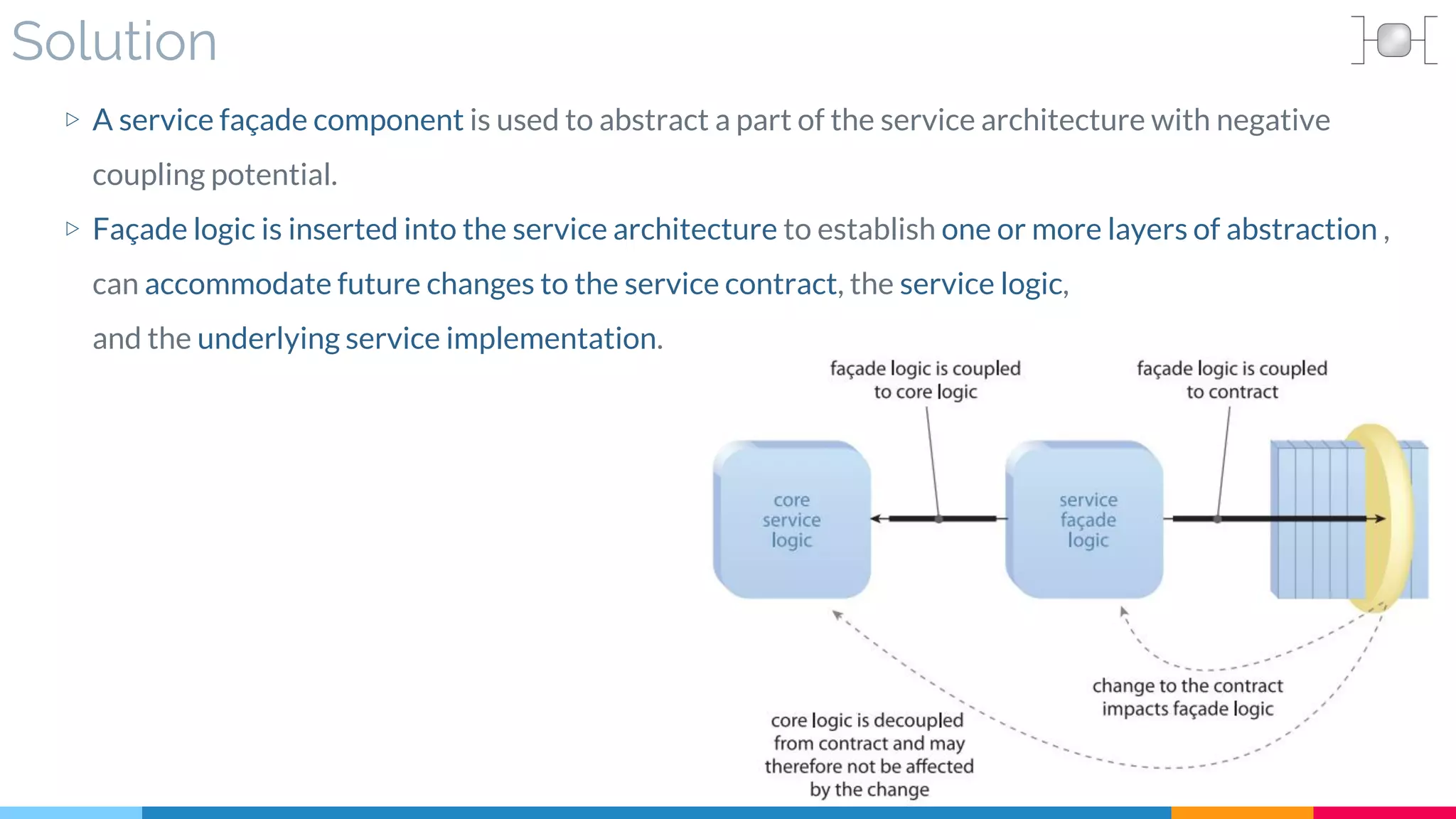
▷ Problem
▷ Solution
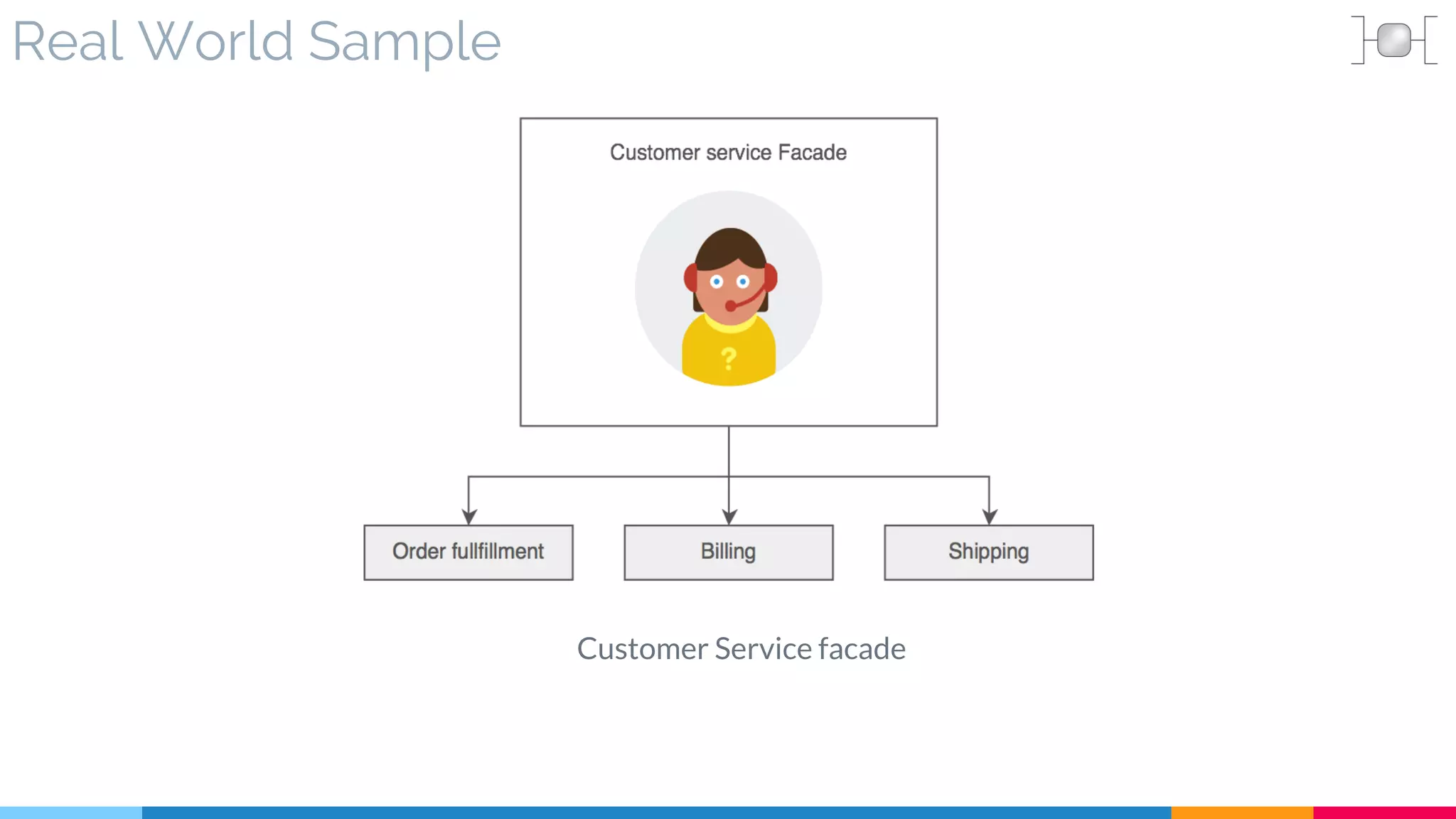
▷ Real World Sample
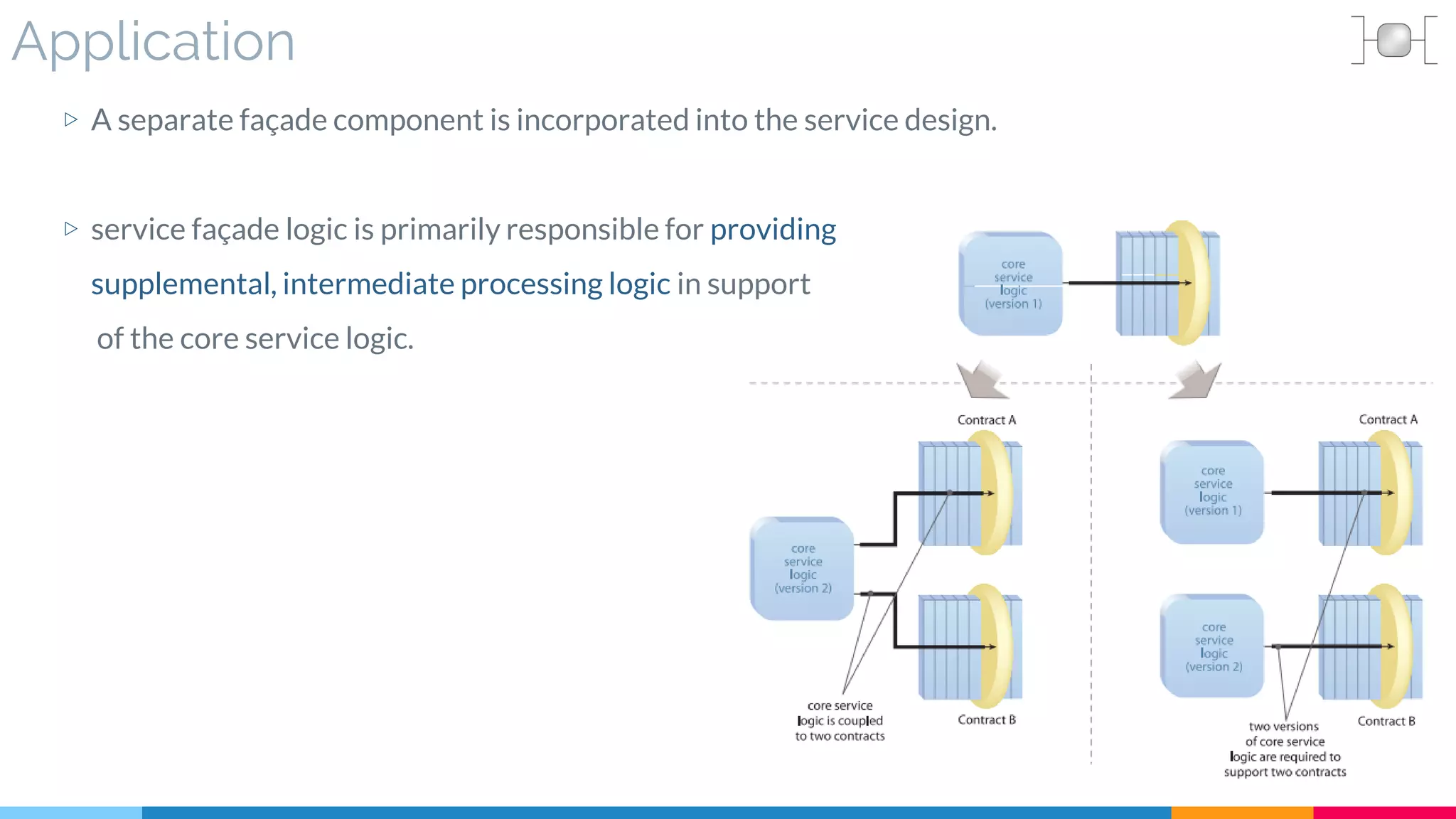
▷ Application
▷ Impact
▷ Relationships
[333]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-142-2048.jpg)


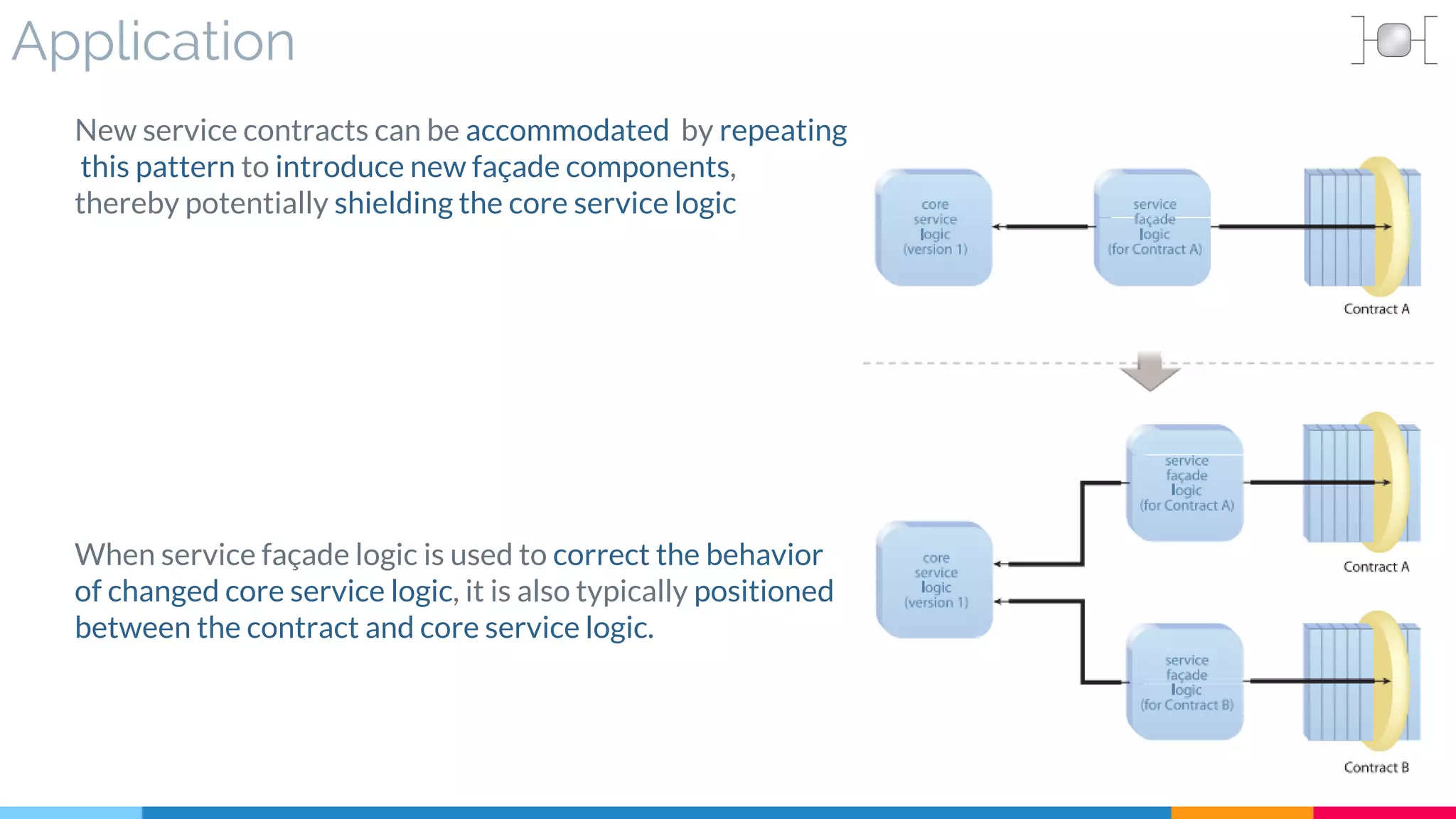
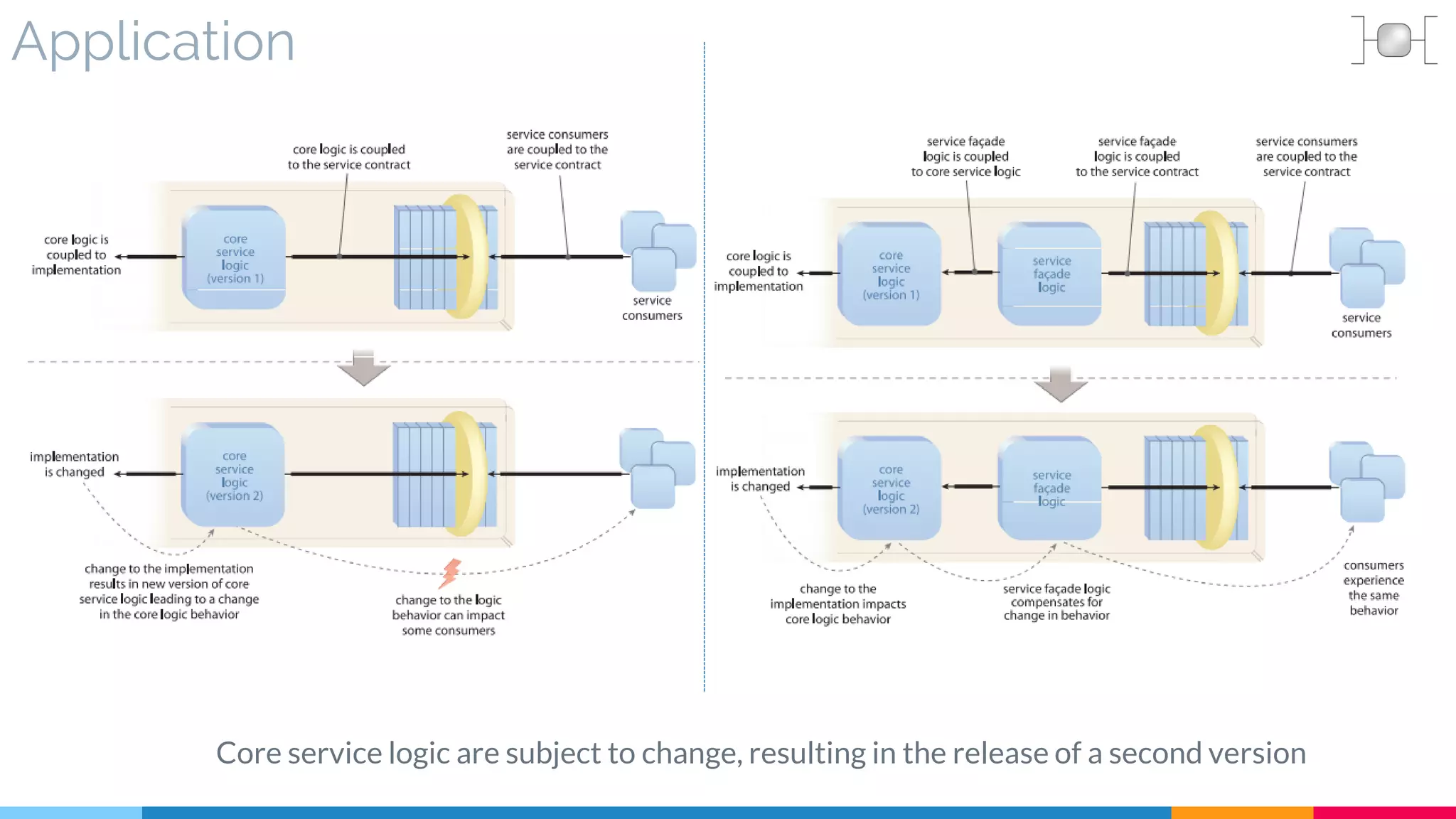
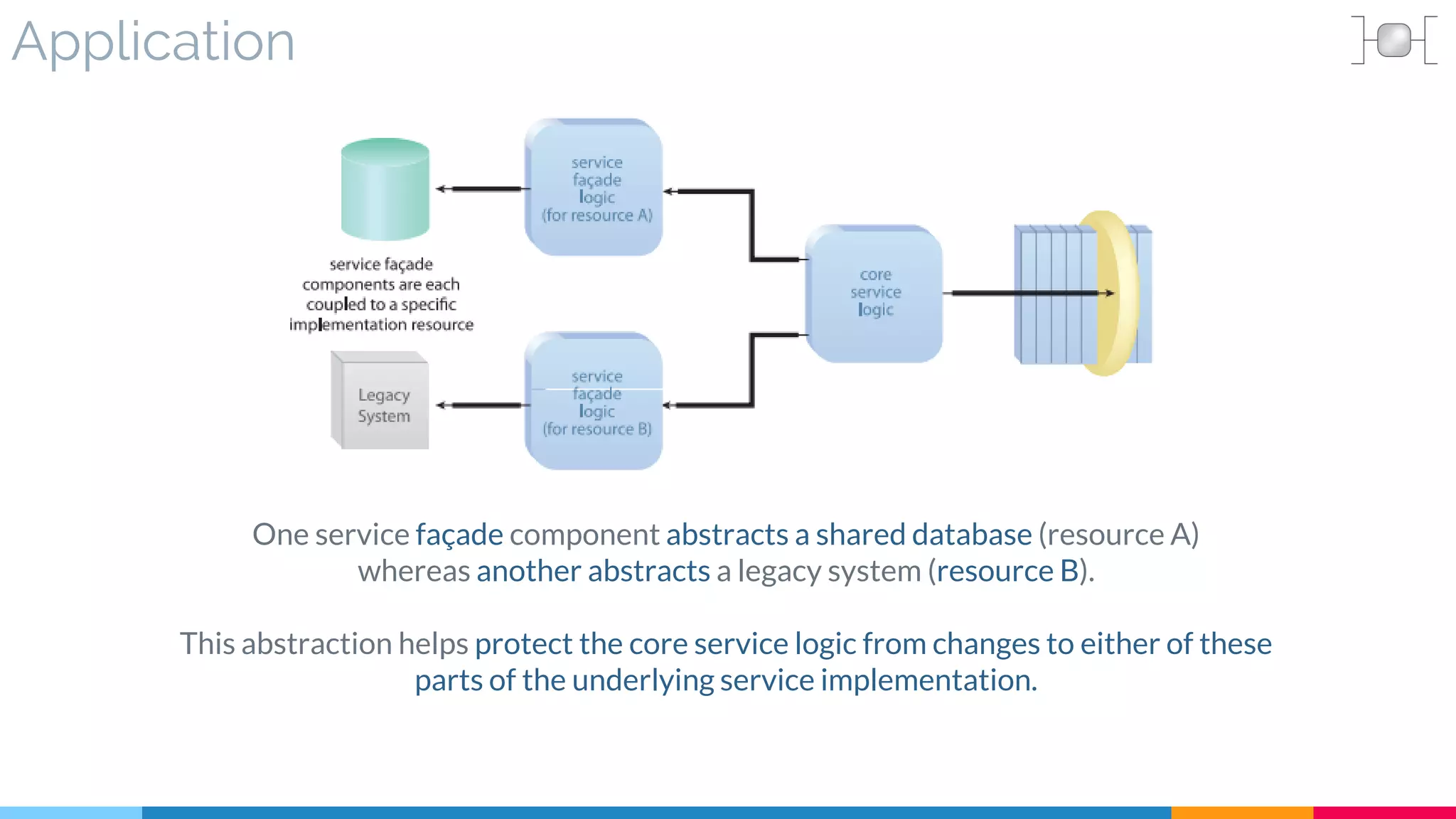

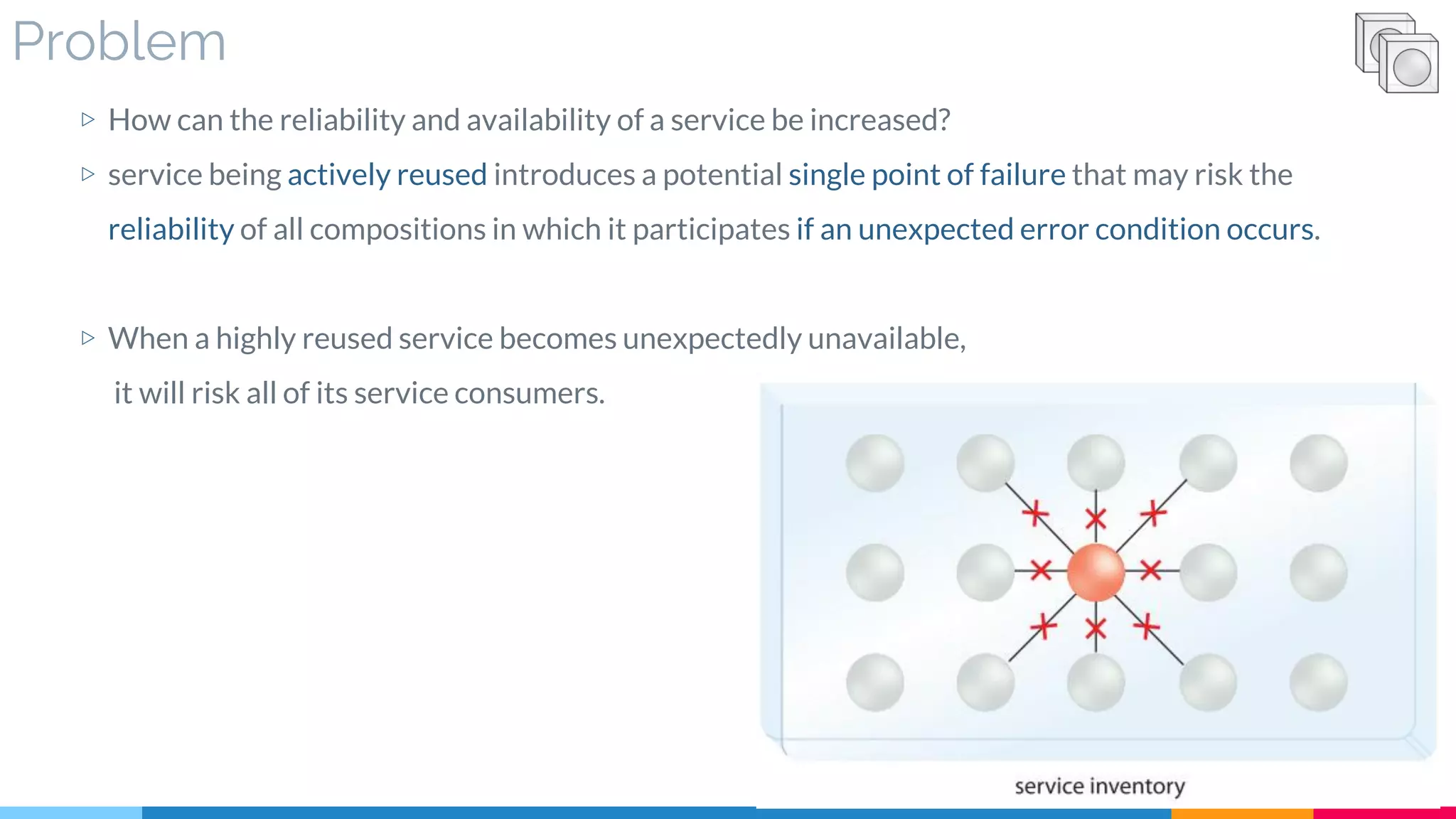
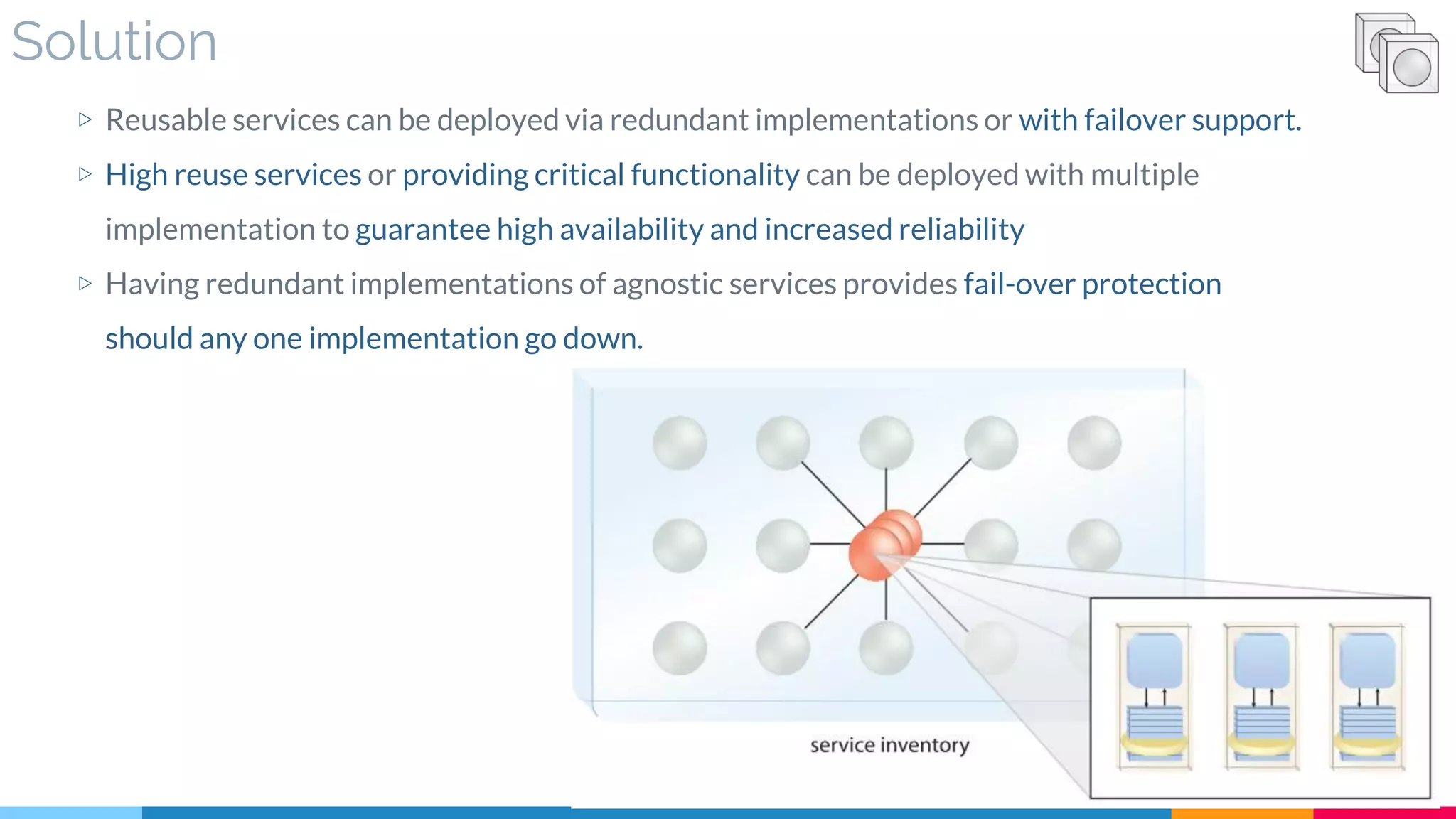
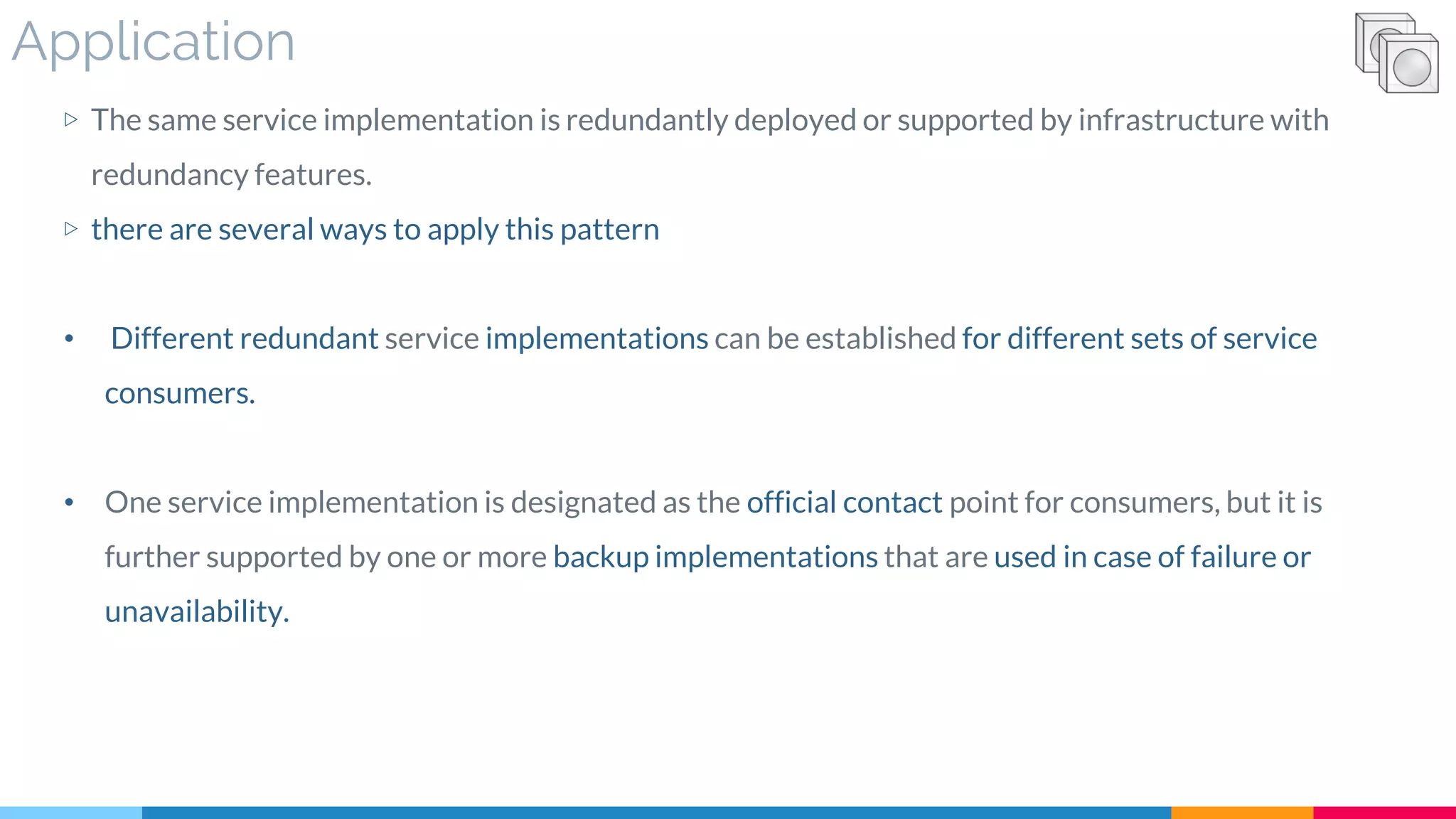
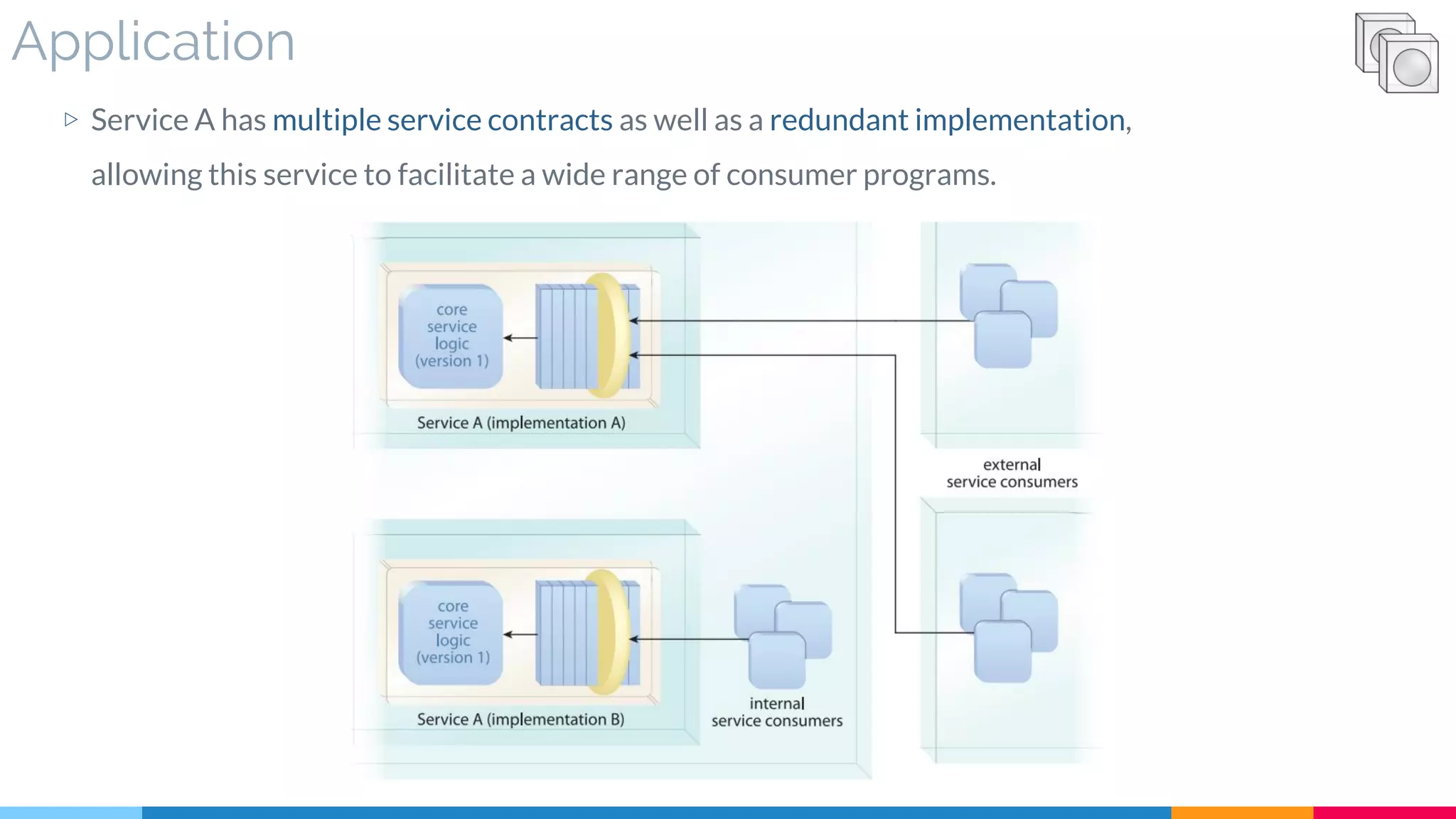
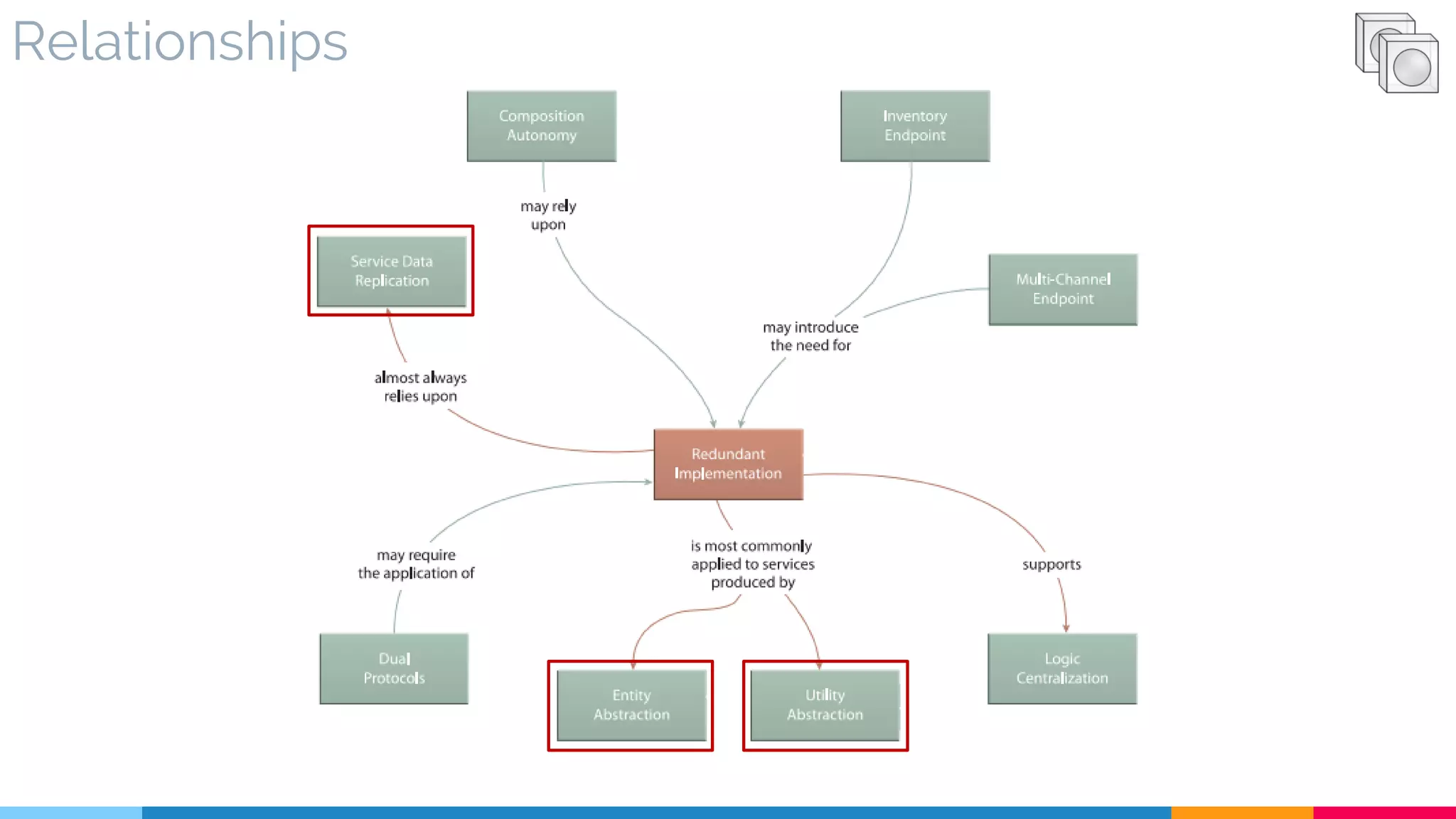
![19 Redundant Implementation
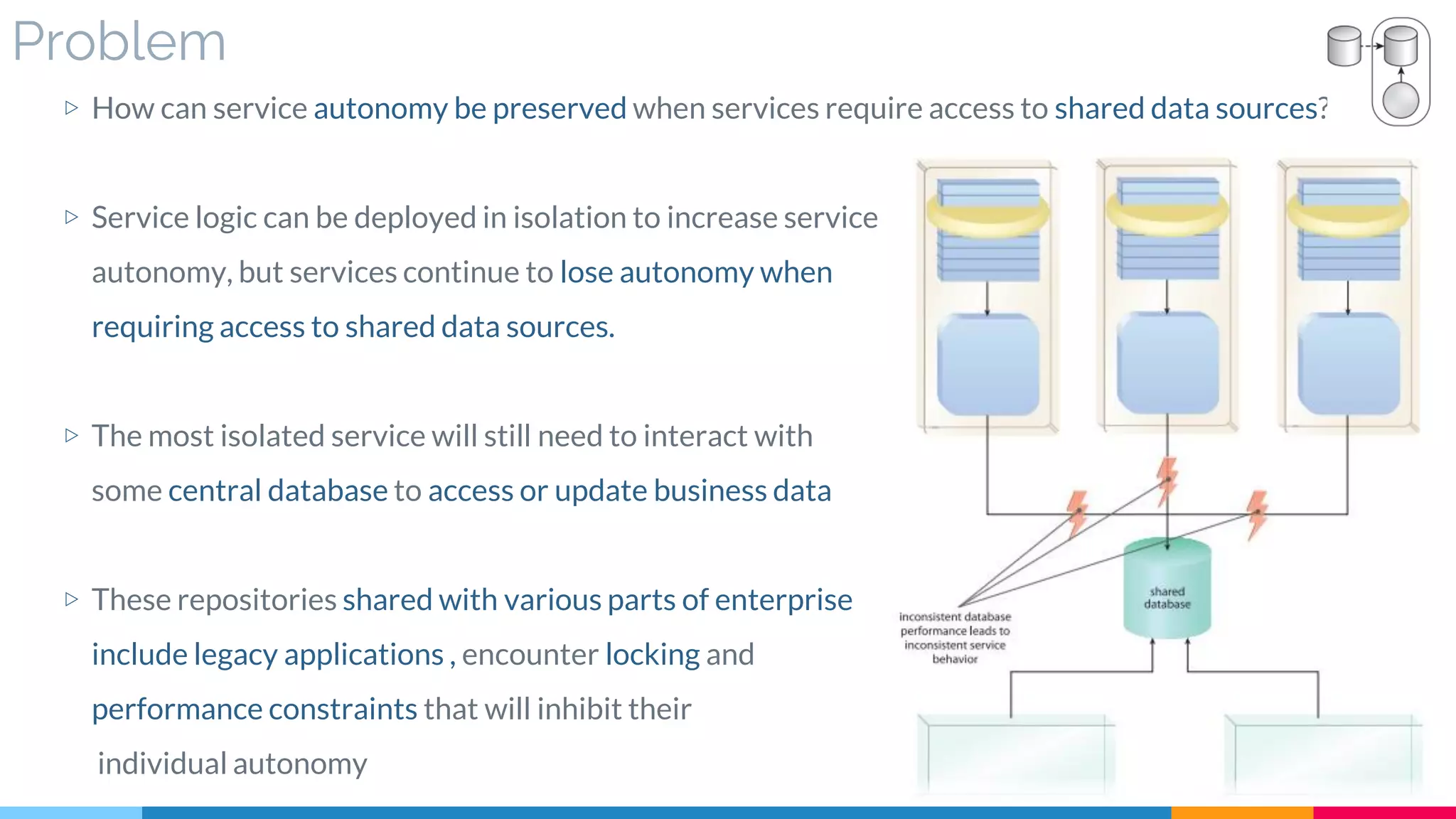
▷ Problem
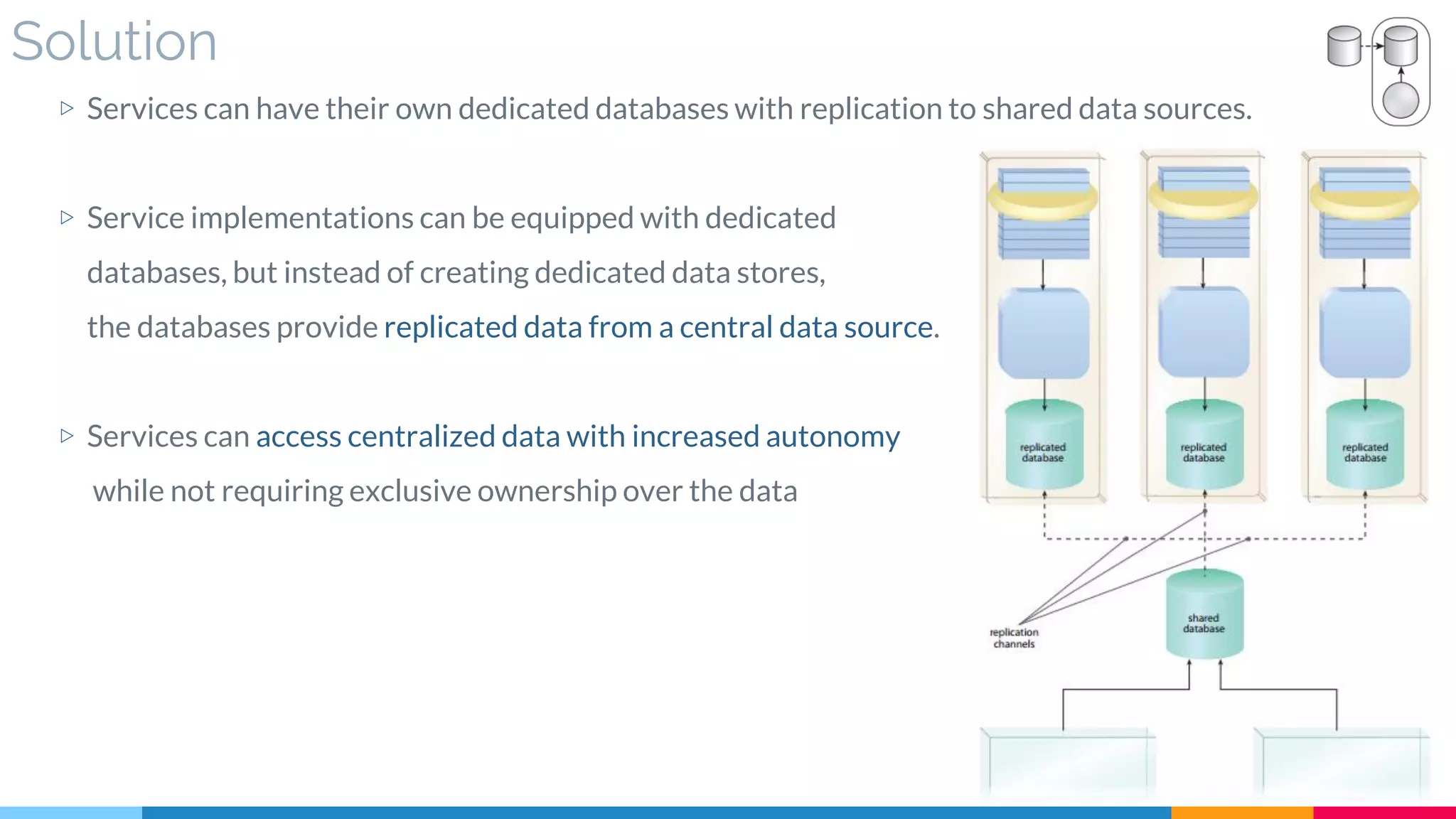
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[345]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-155-2048.jpg)


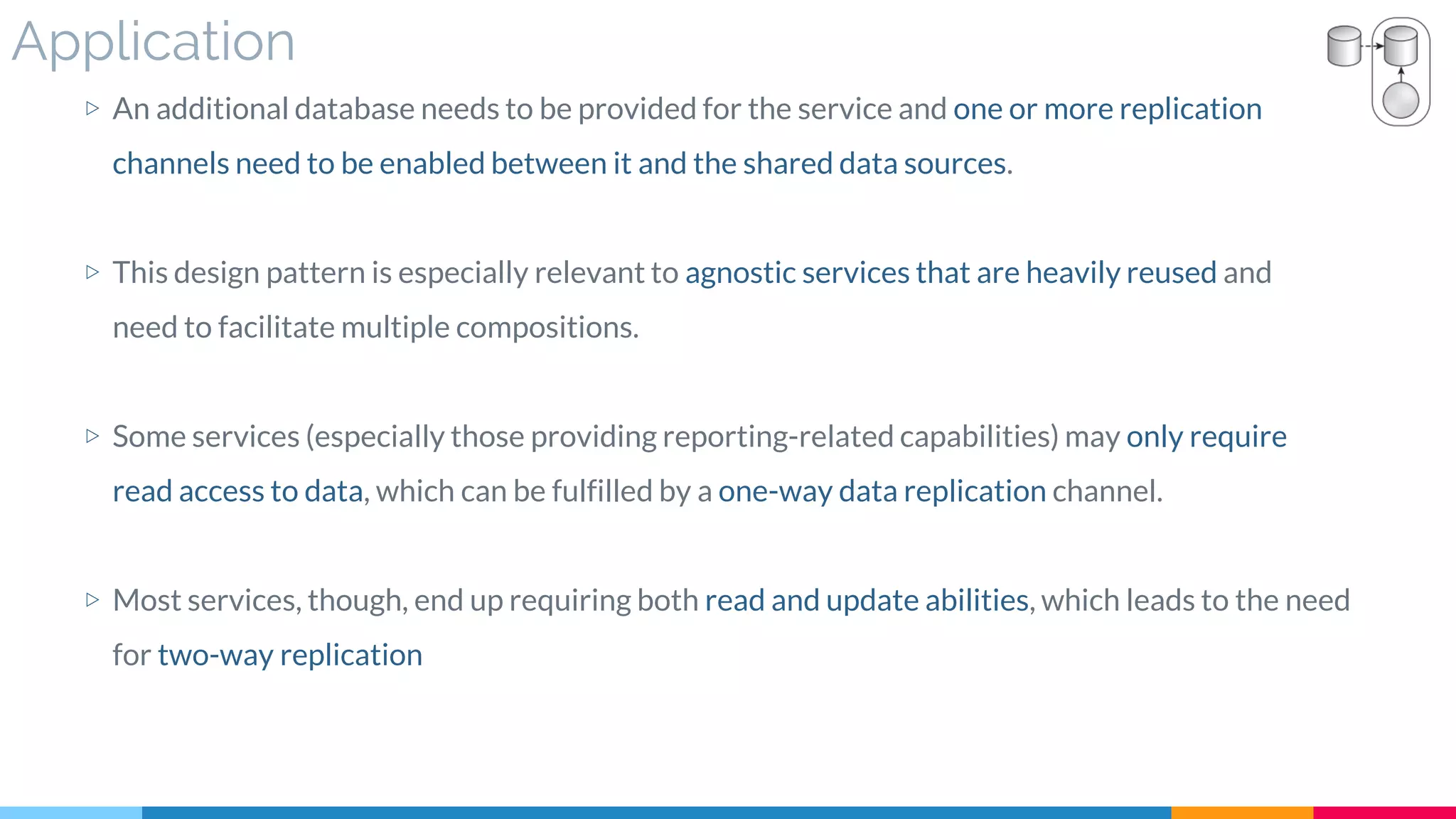
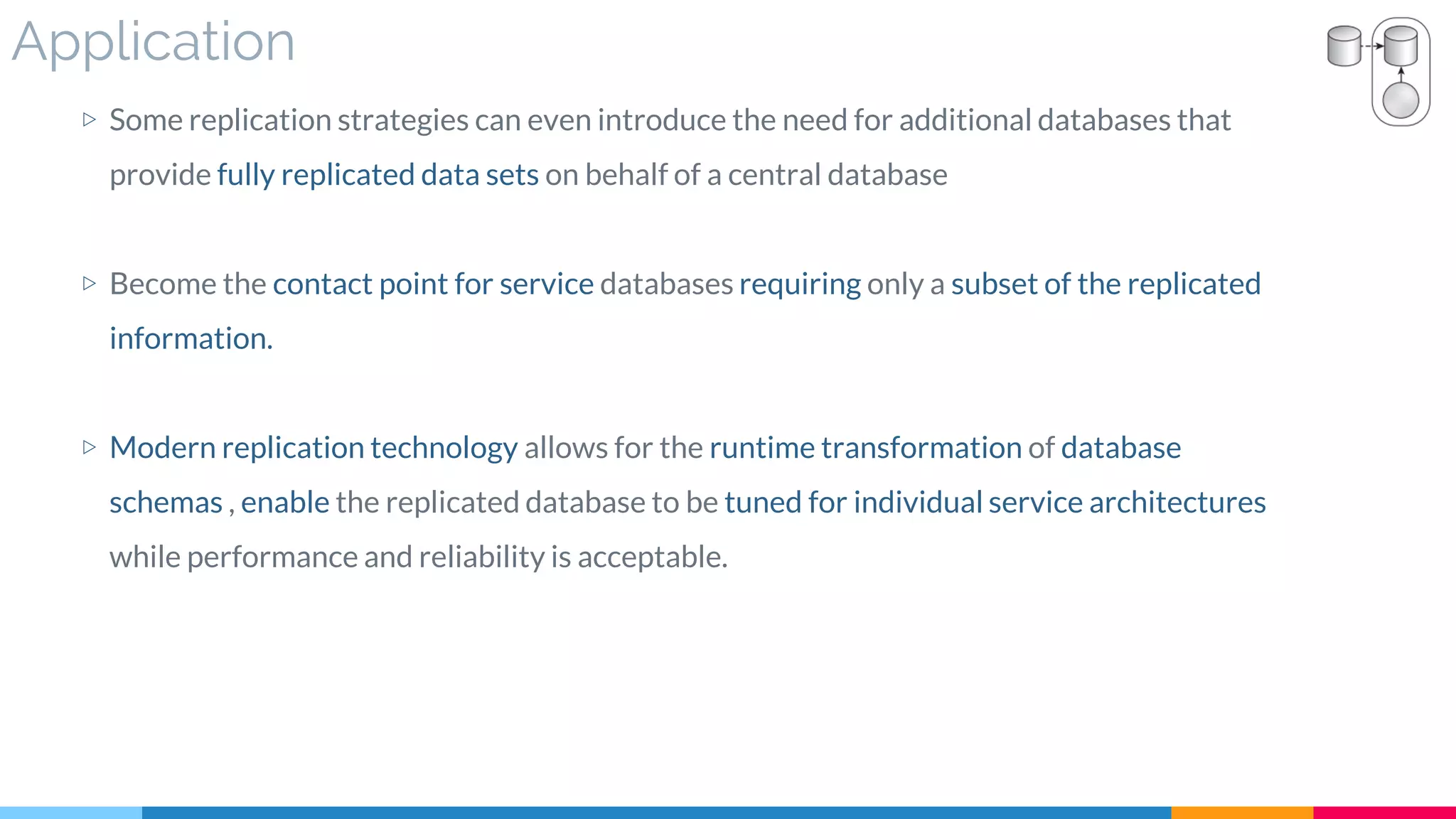
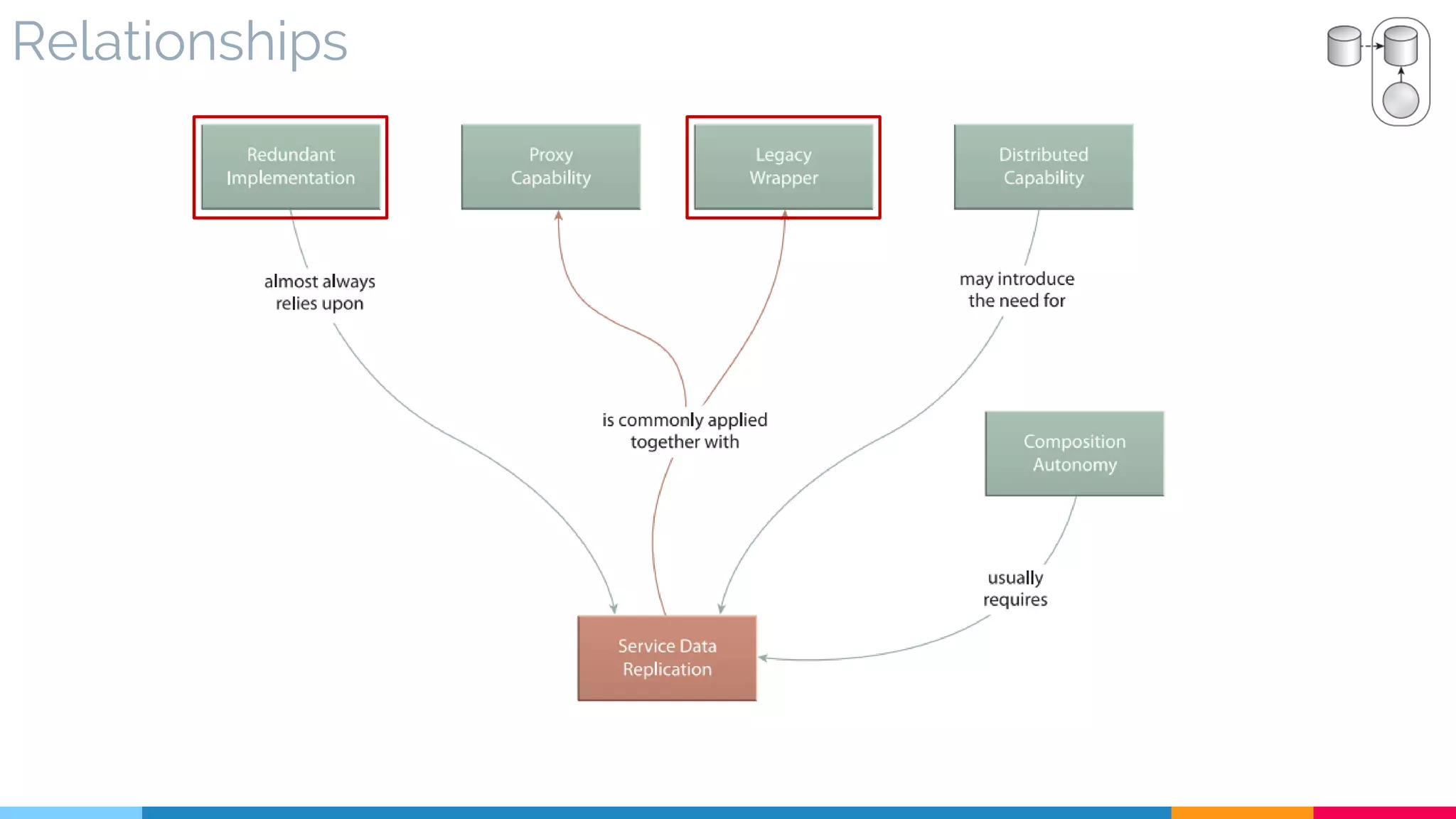
![20 Service Data Replication
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[350]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-163-2048.jpg)

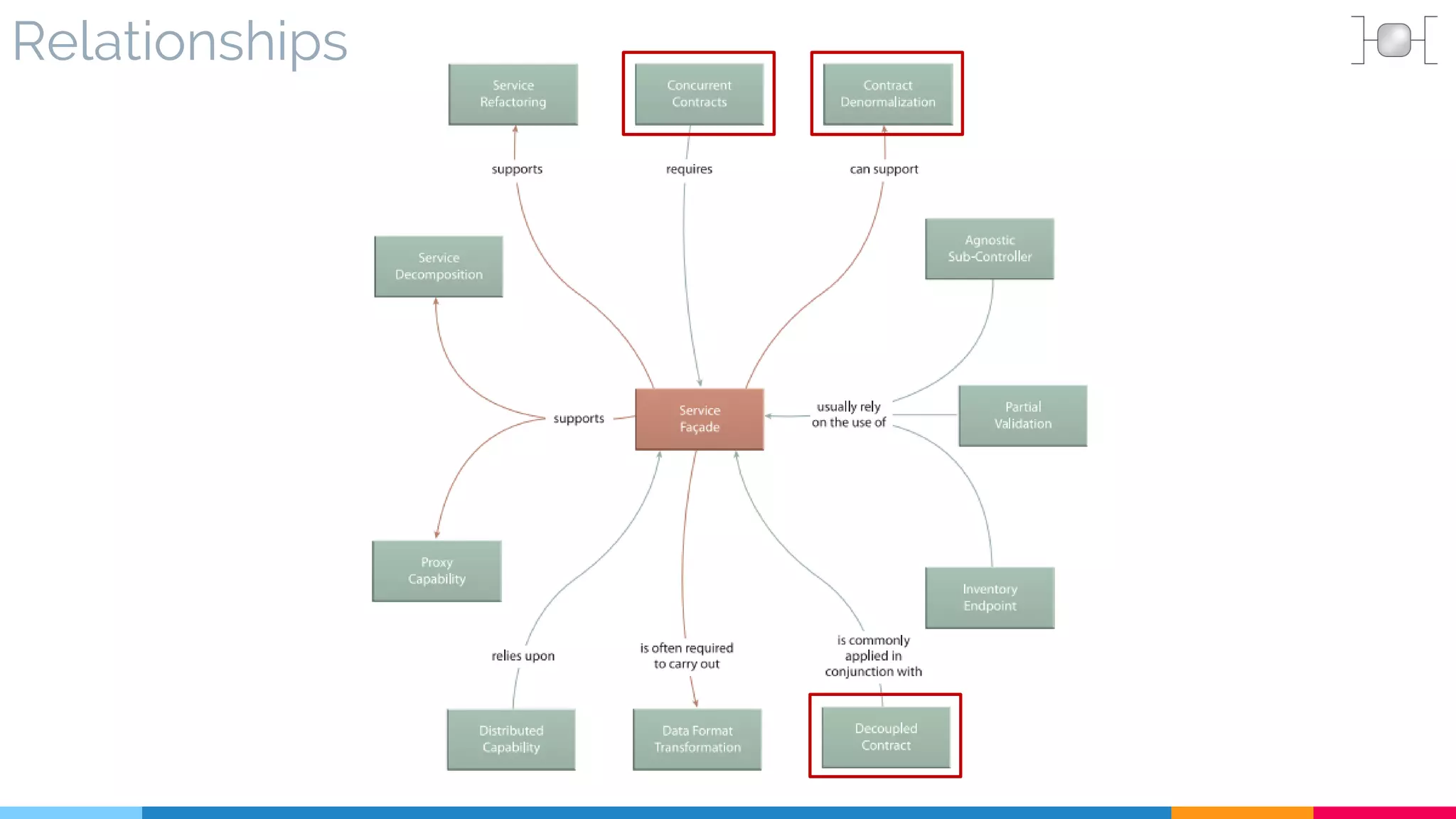
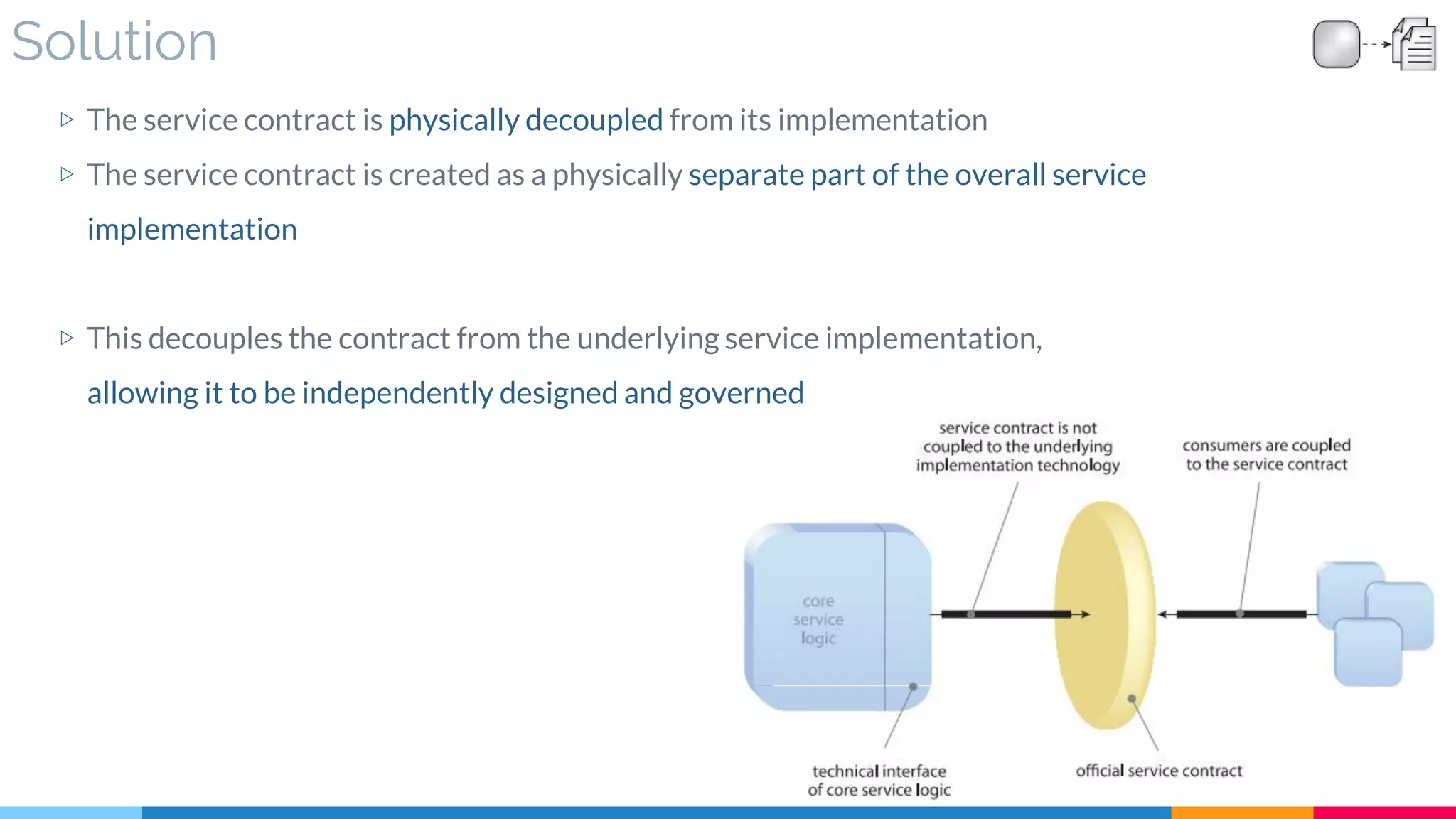
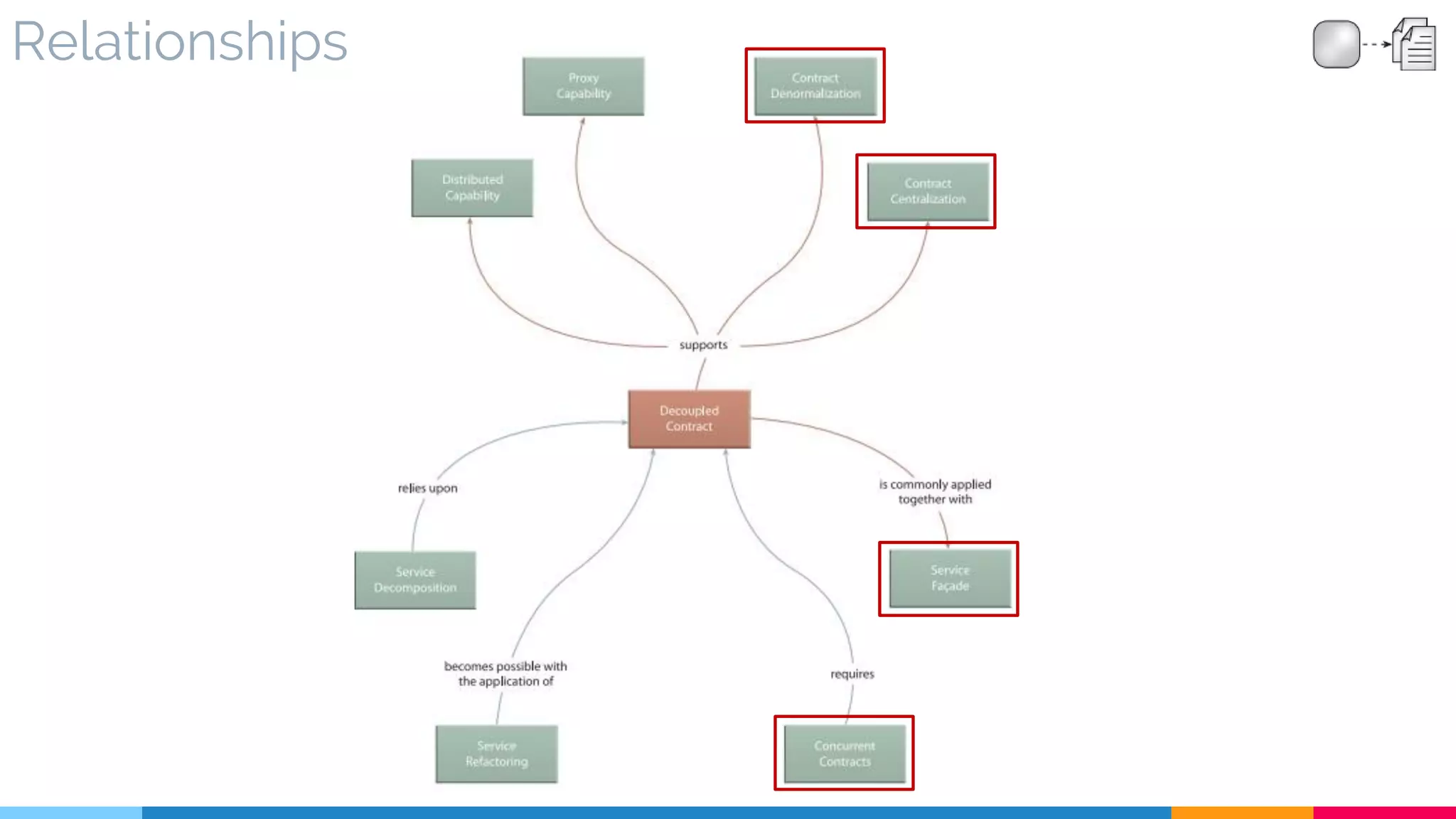
![21 Decoupled Contract
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[401]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-171-2048.jpg)

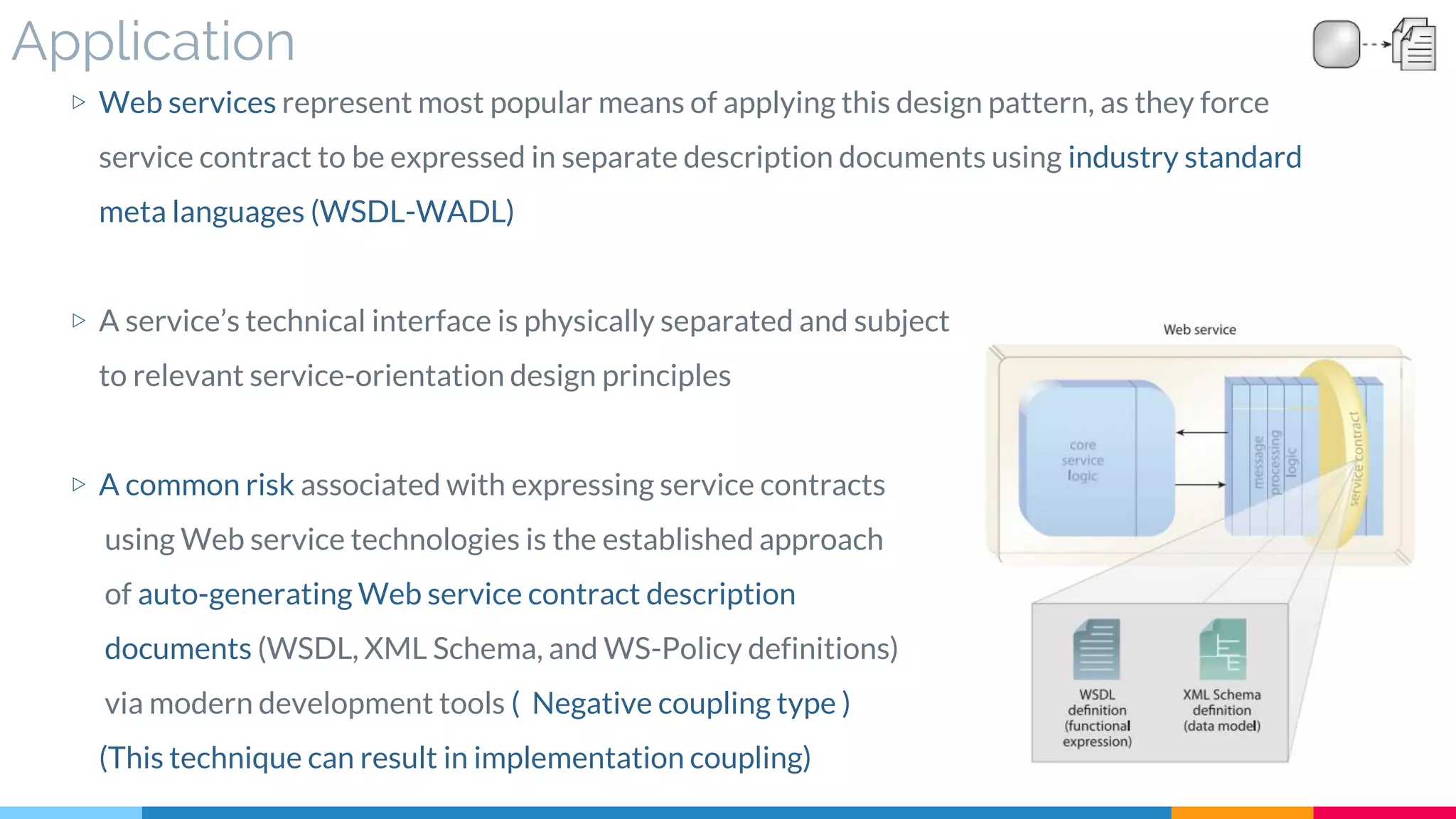
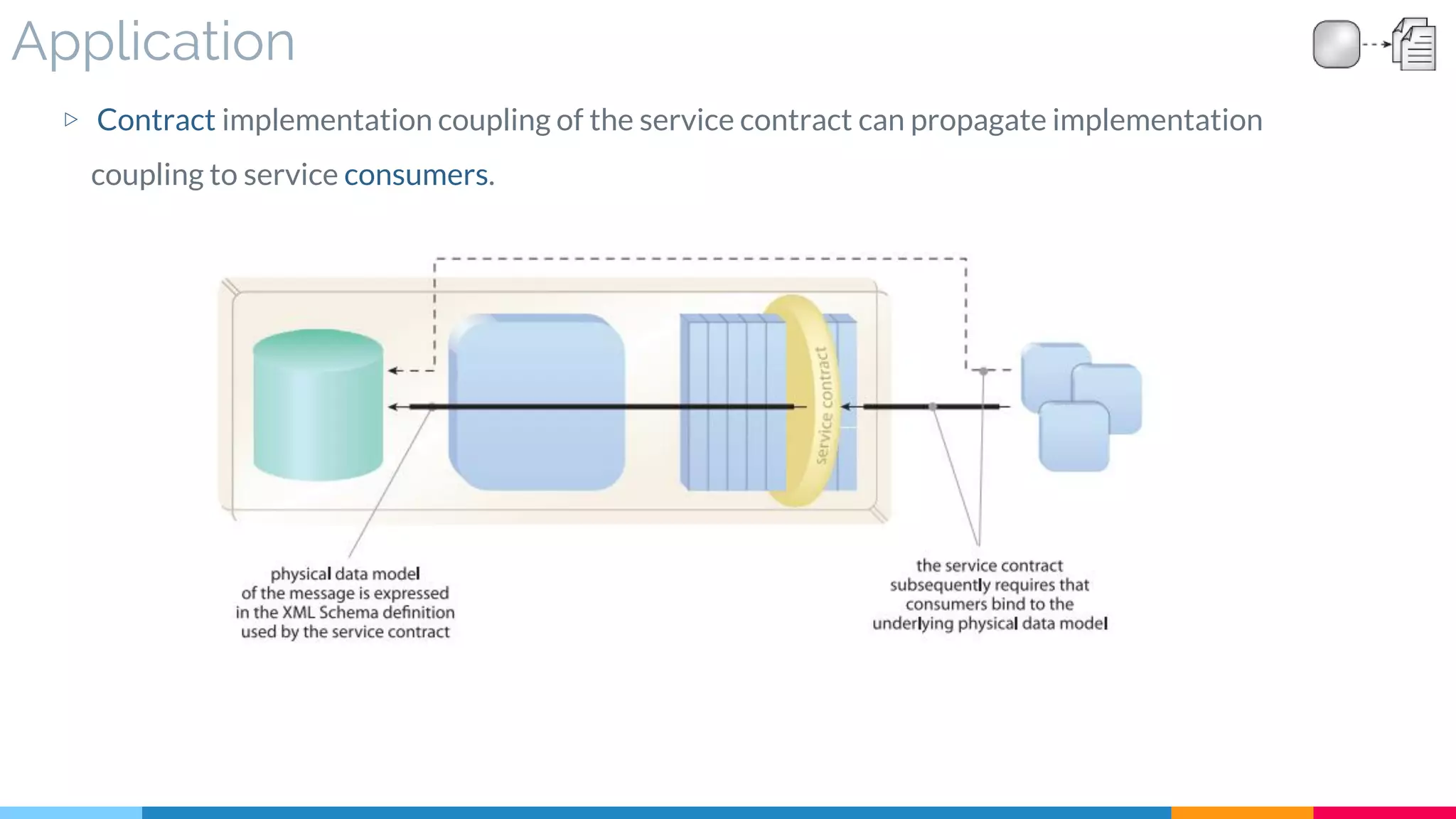
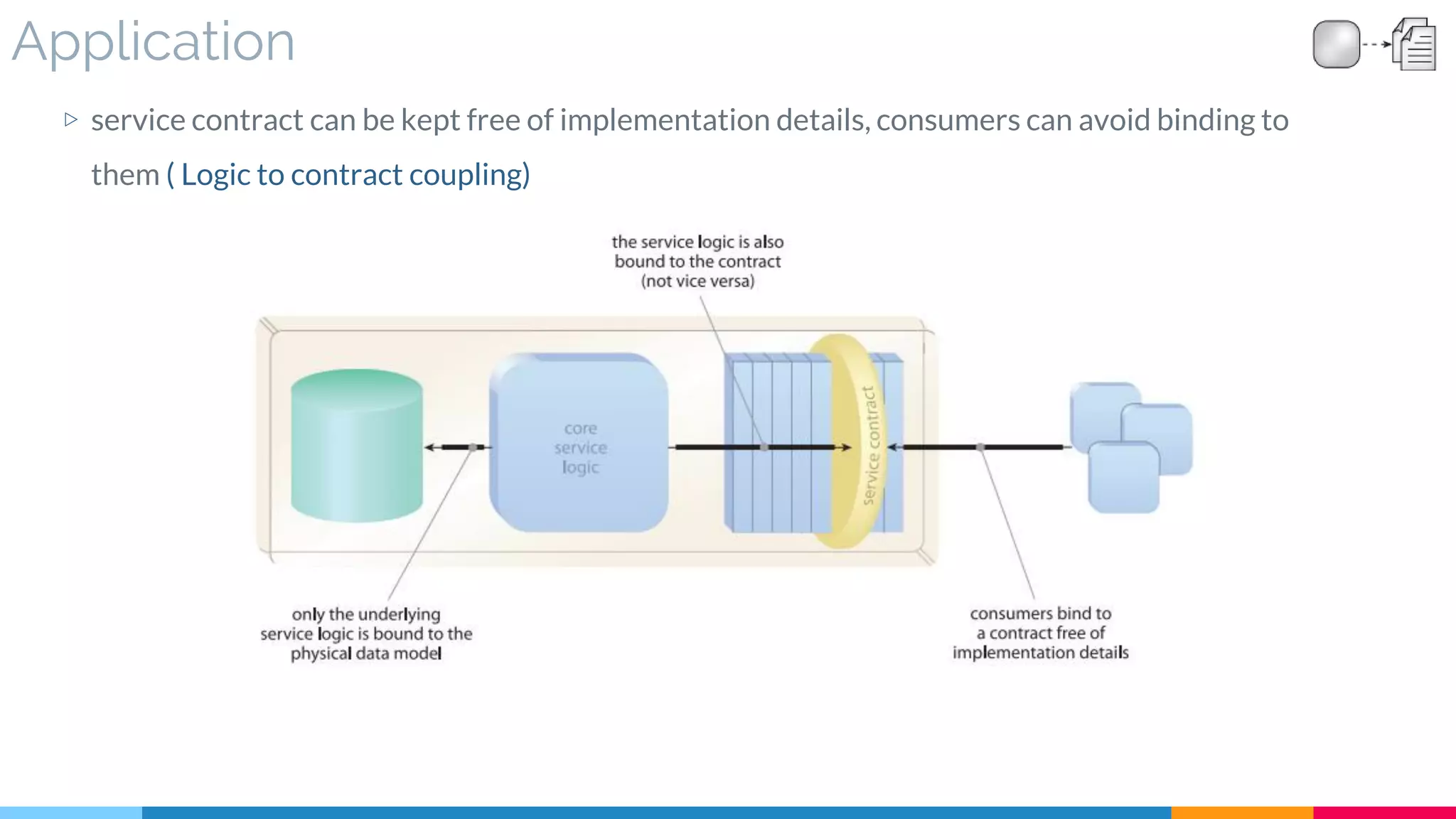

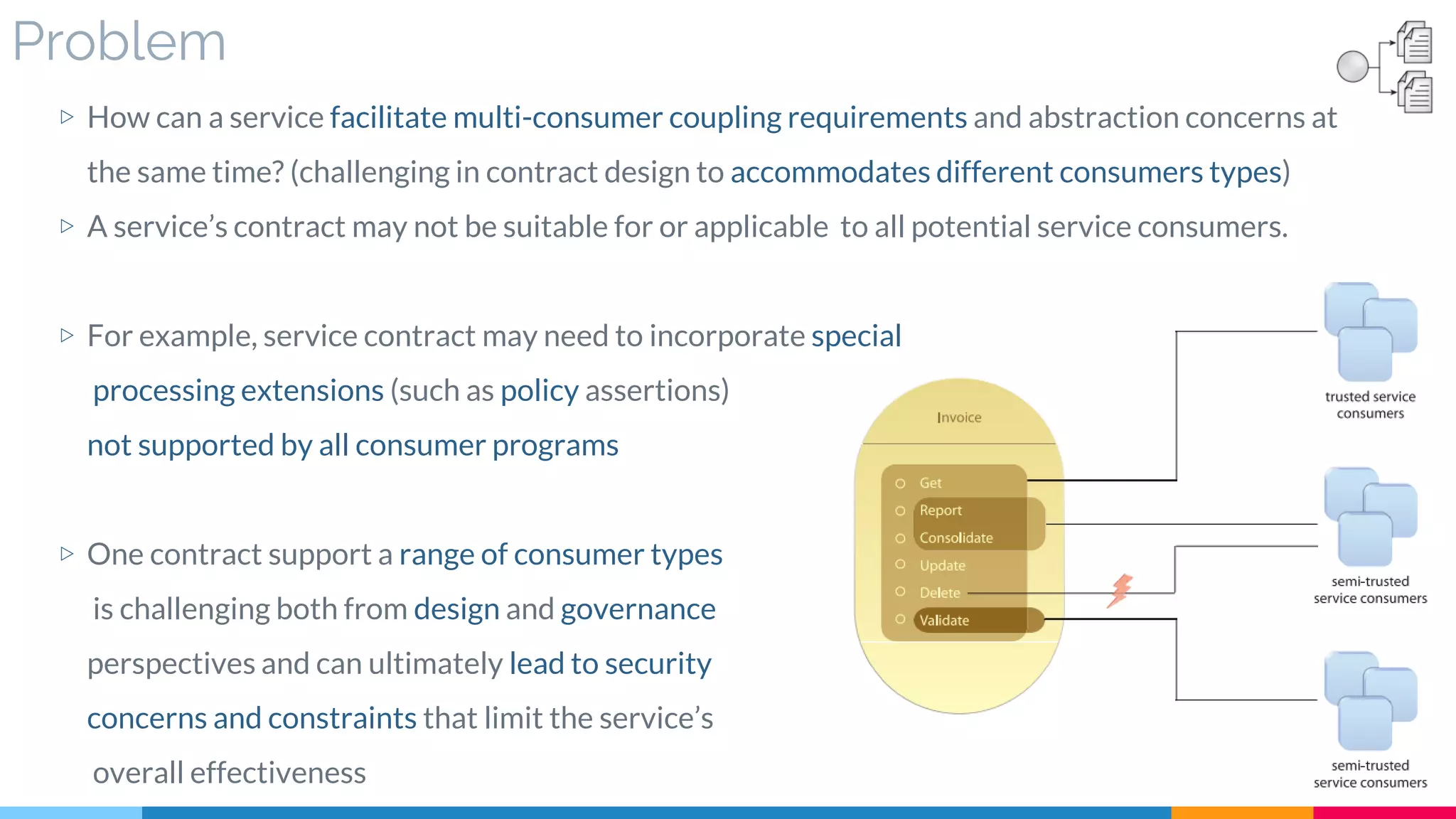
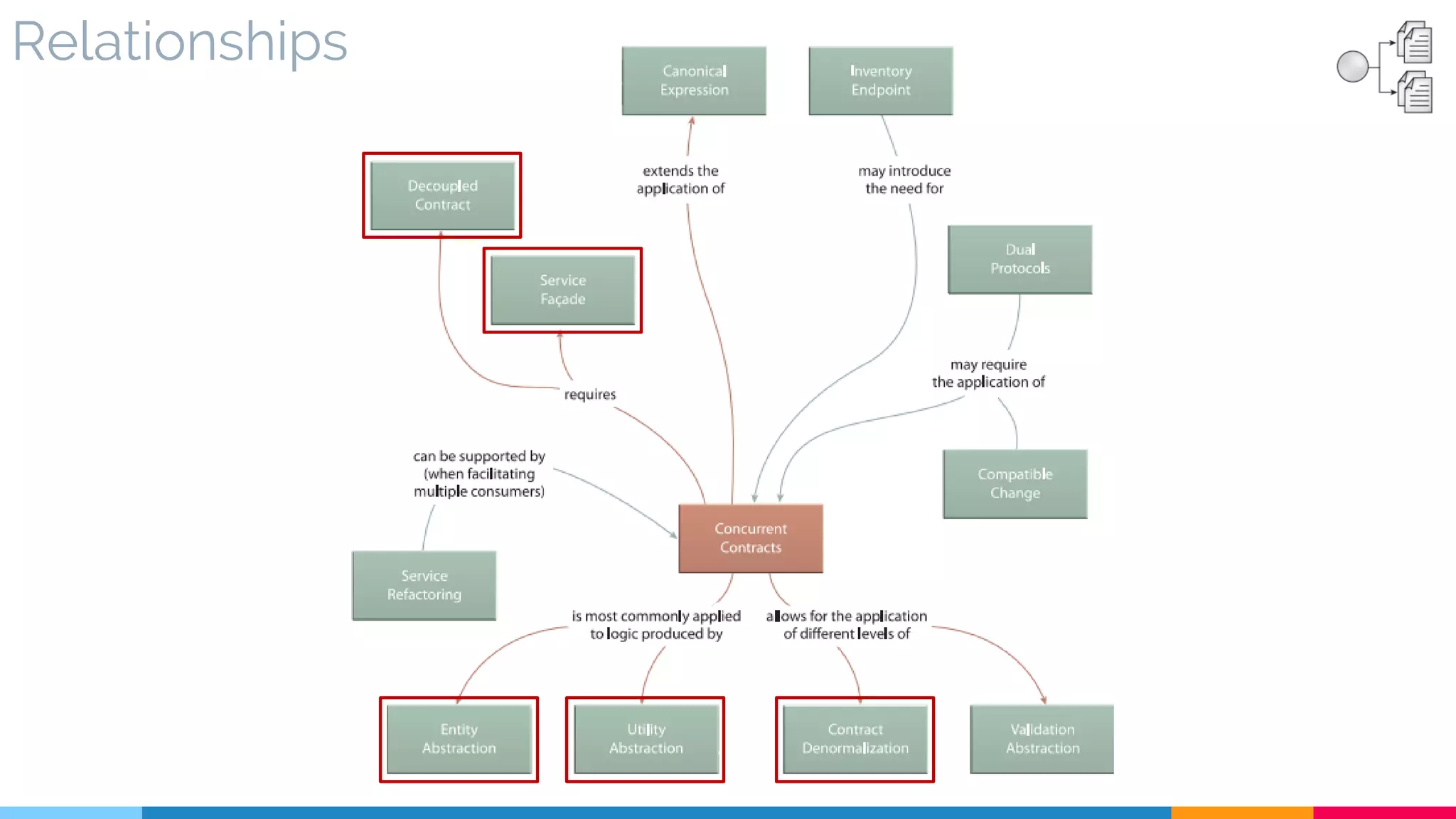
![22 Concurrent Contract
▷ Problem
▷ Solution
▷ Real World Sample
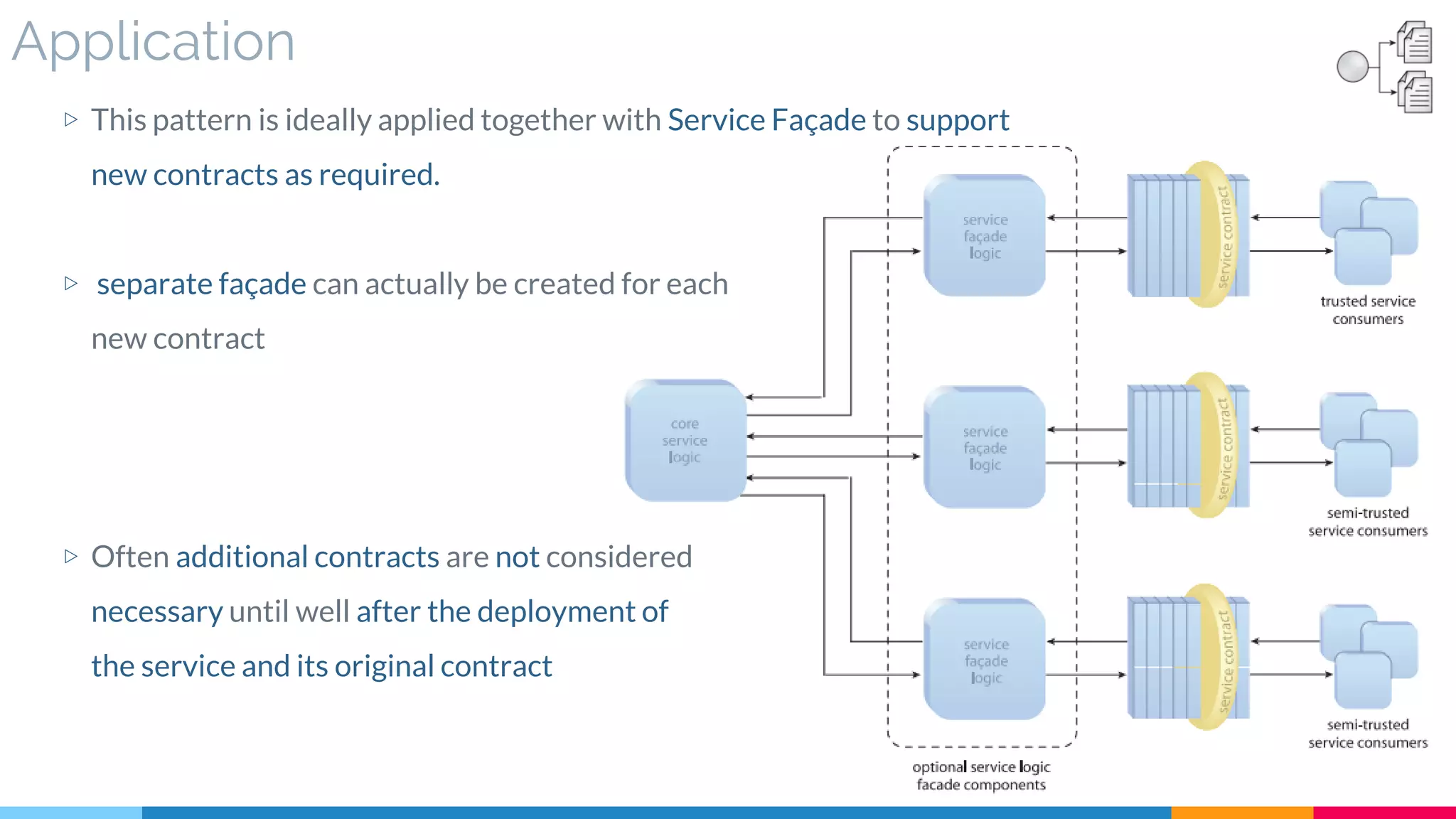
▷ Application
▷ Impact
▷ Relationships
[421]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-180-2048.jpg)
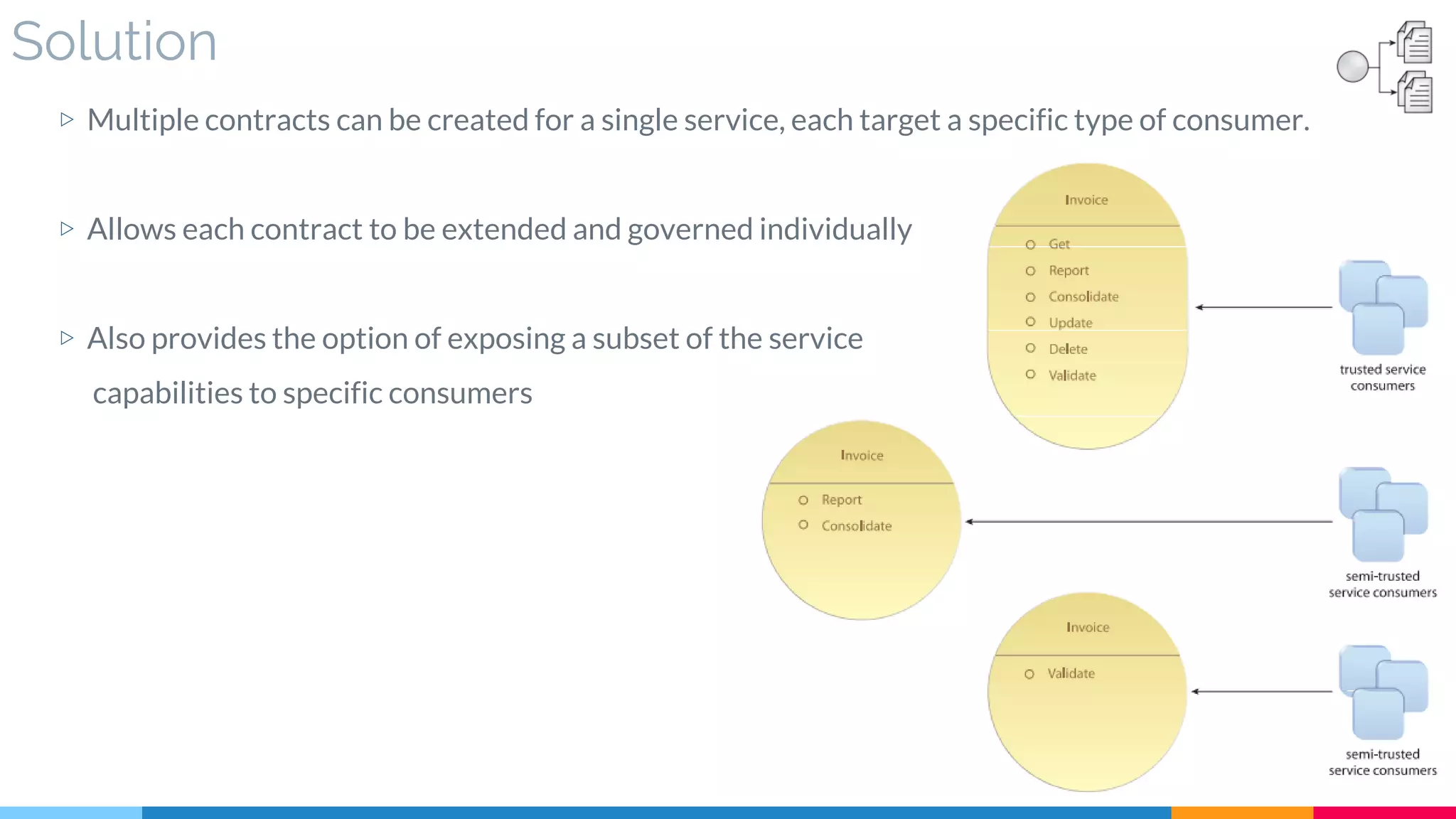
![Real World Sample
Concurrent Edition contract [ Same service provided by
multiple contracts to accommodate consumers concerns]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-183-2048.jpg)

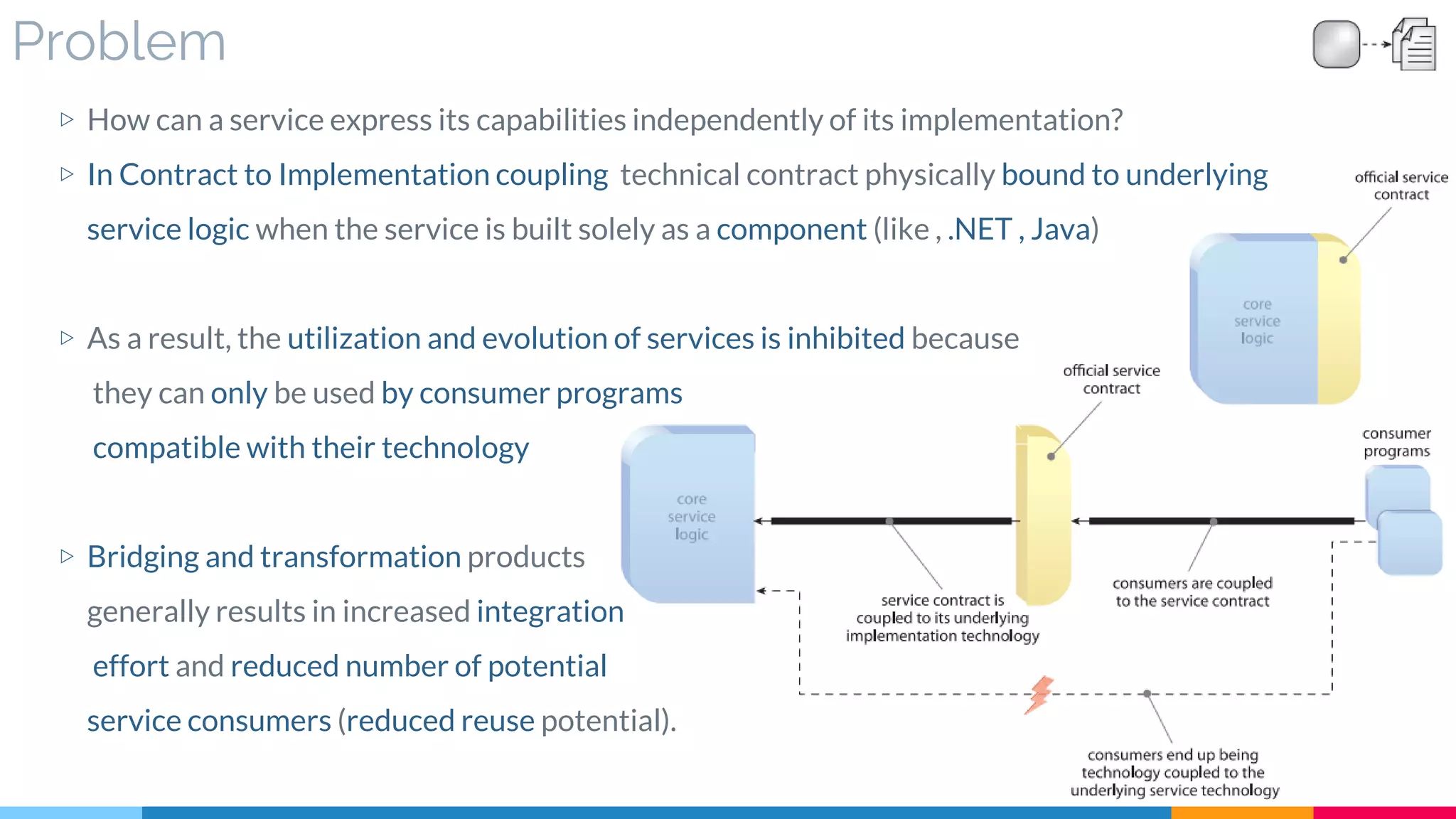
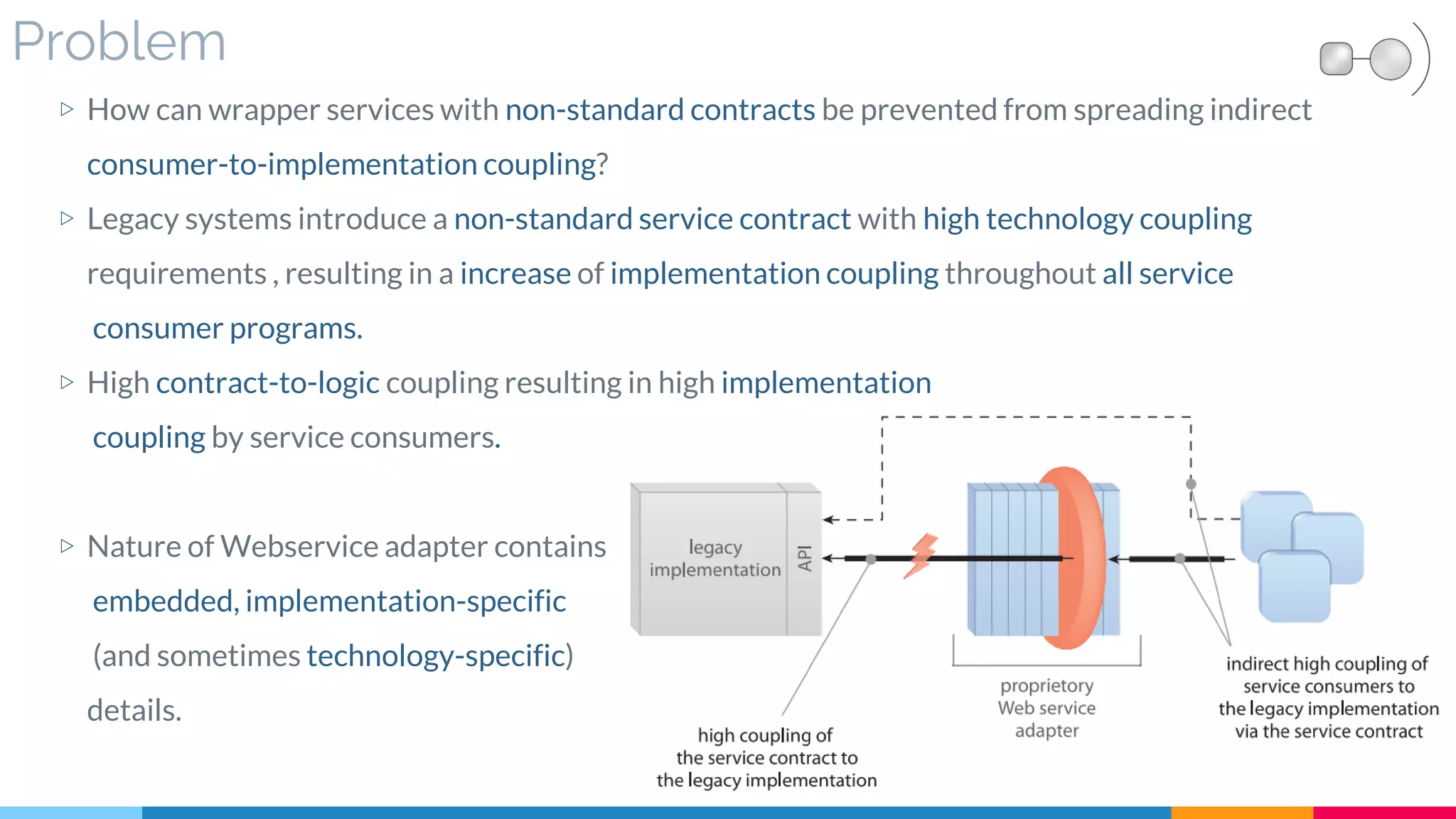
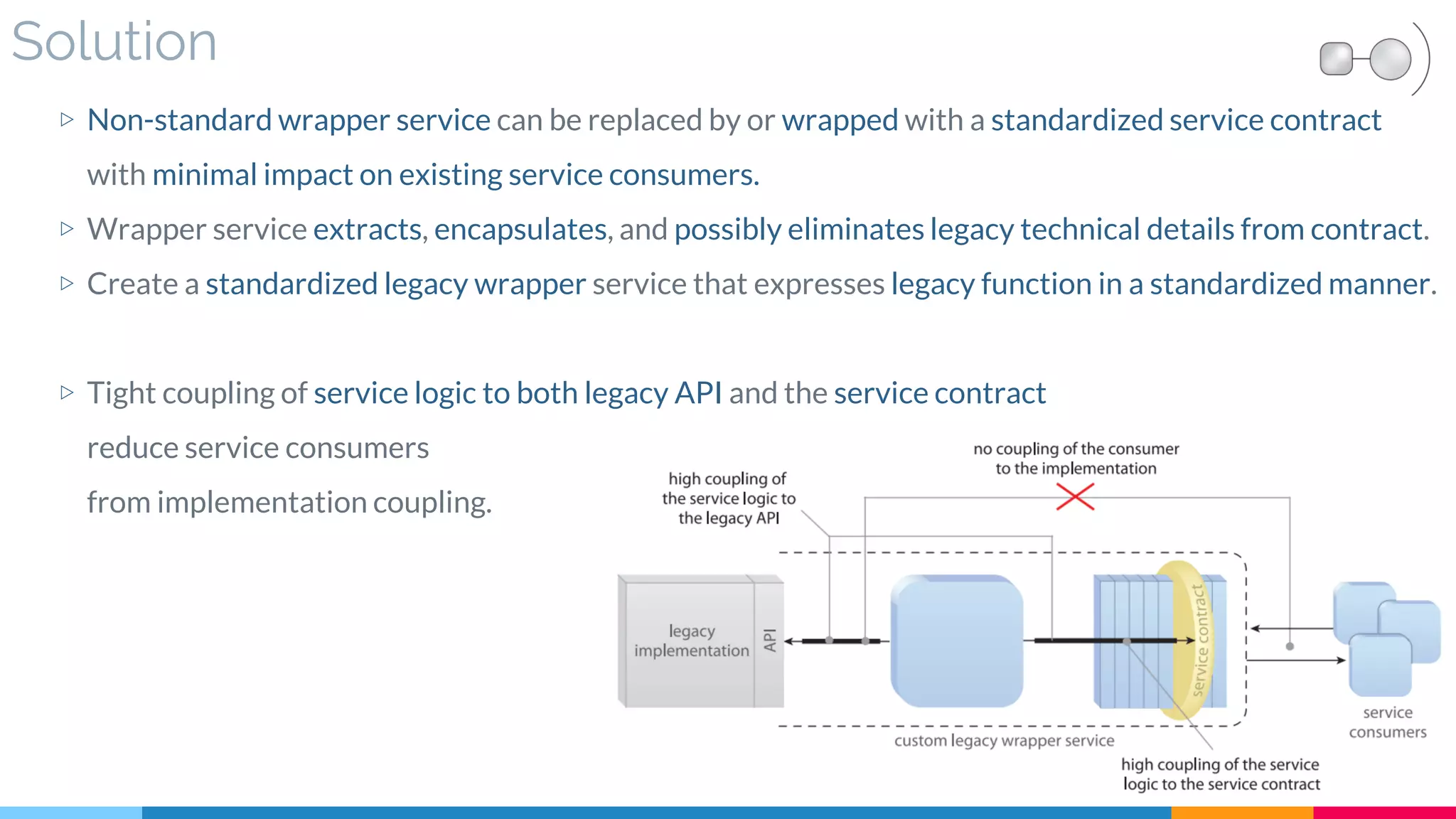
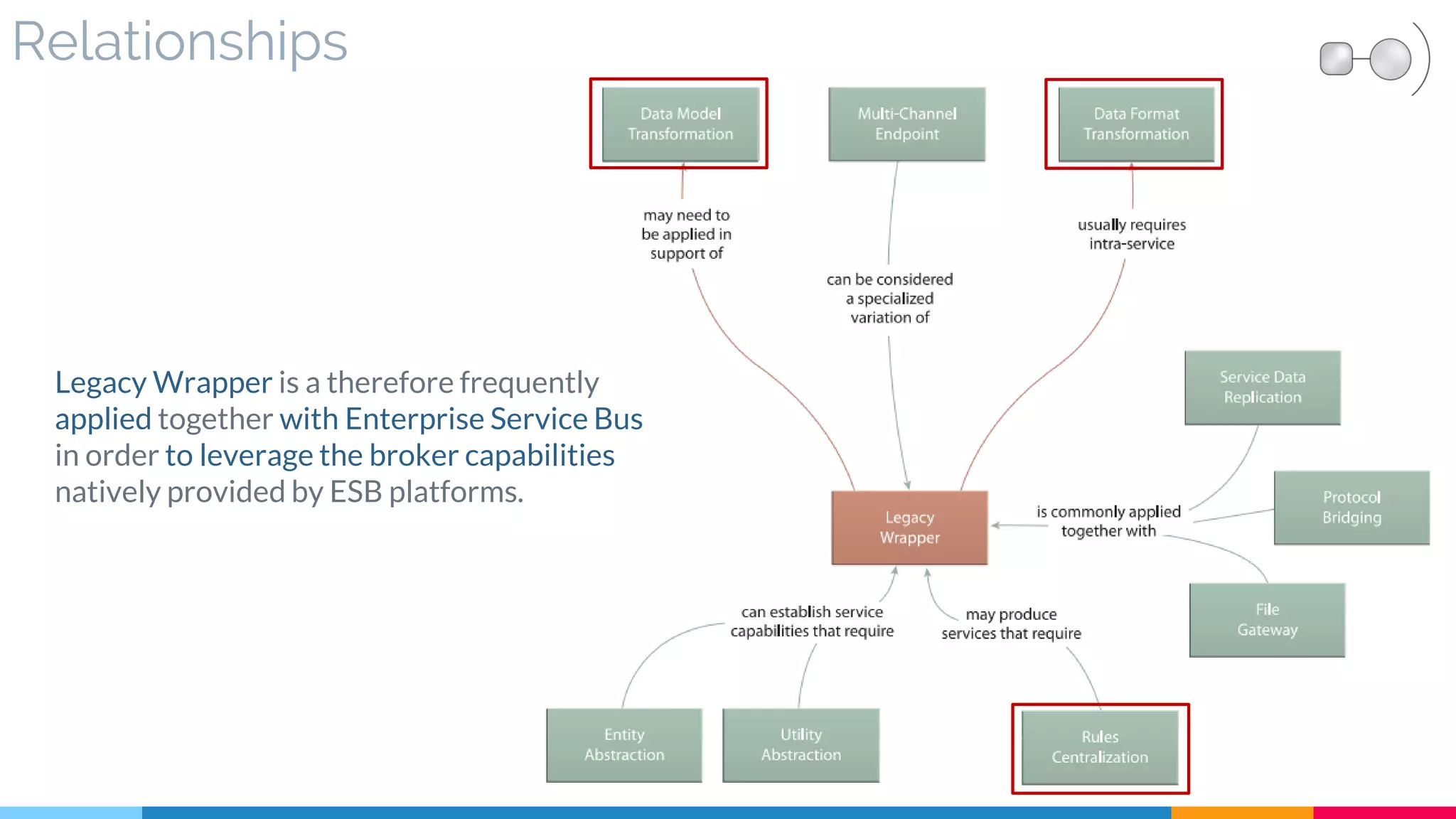
![23 Legacy Wrapper
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[441]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-187-2048.jpg)

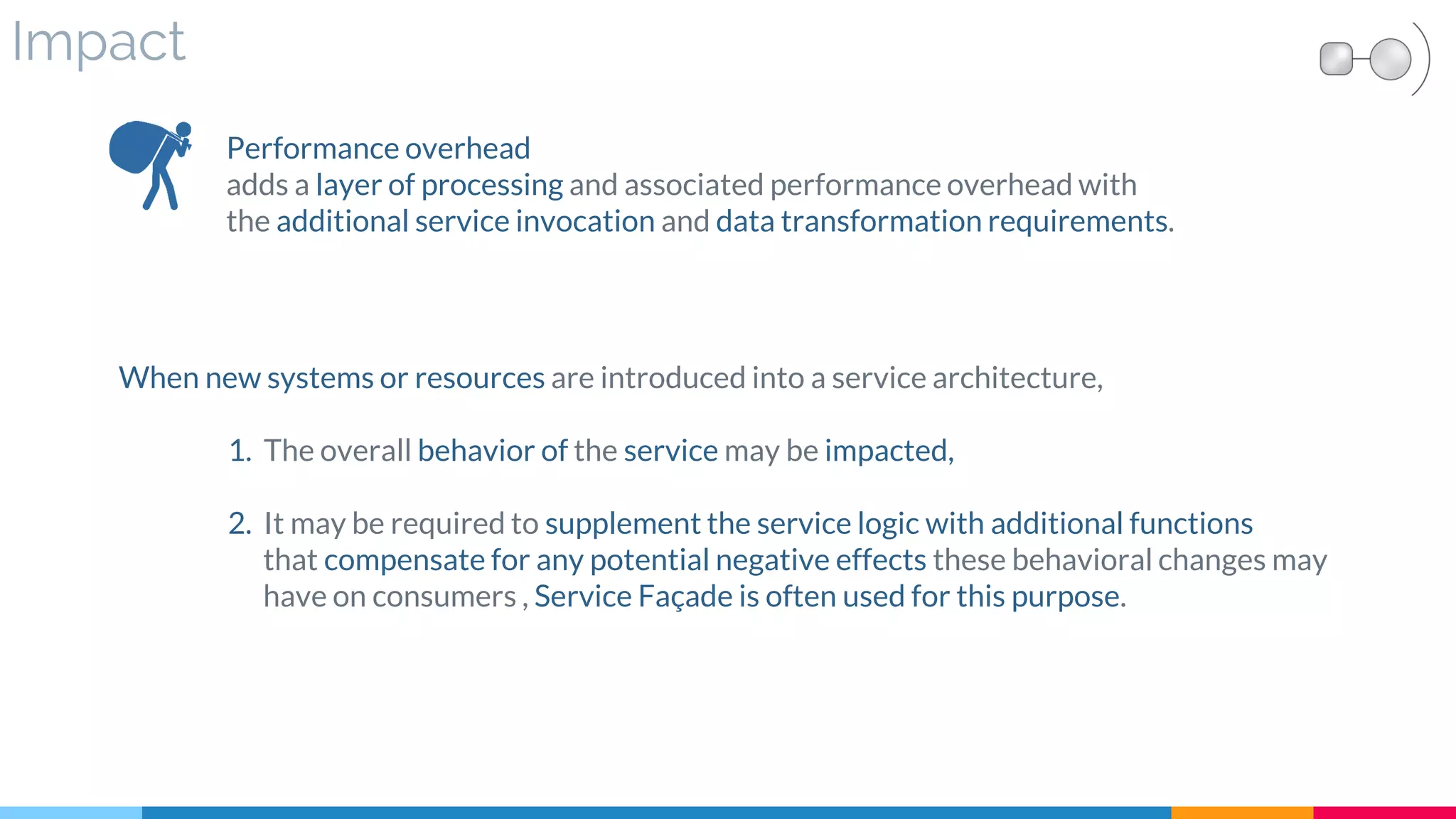
![Application
▷ Eliminating Technical Information:
1. Eliminate input and output data contain highly proprietary characteristics like
[error code can be replaced by SOAP Fault]
2. Usually result in Utility service
▷ Encapsulating Technical Information:
1. Replace legacy-specific data with standardized business data
2. Partition standardized business data from proprietary legacy data into body and header sections
3. Usually result in add the wrapper logic as an extension of a business service.](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-192-2048.jpg)
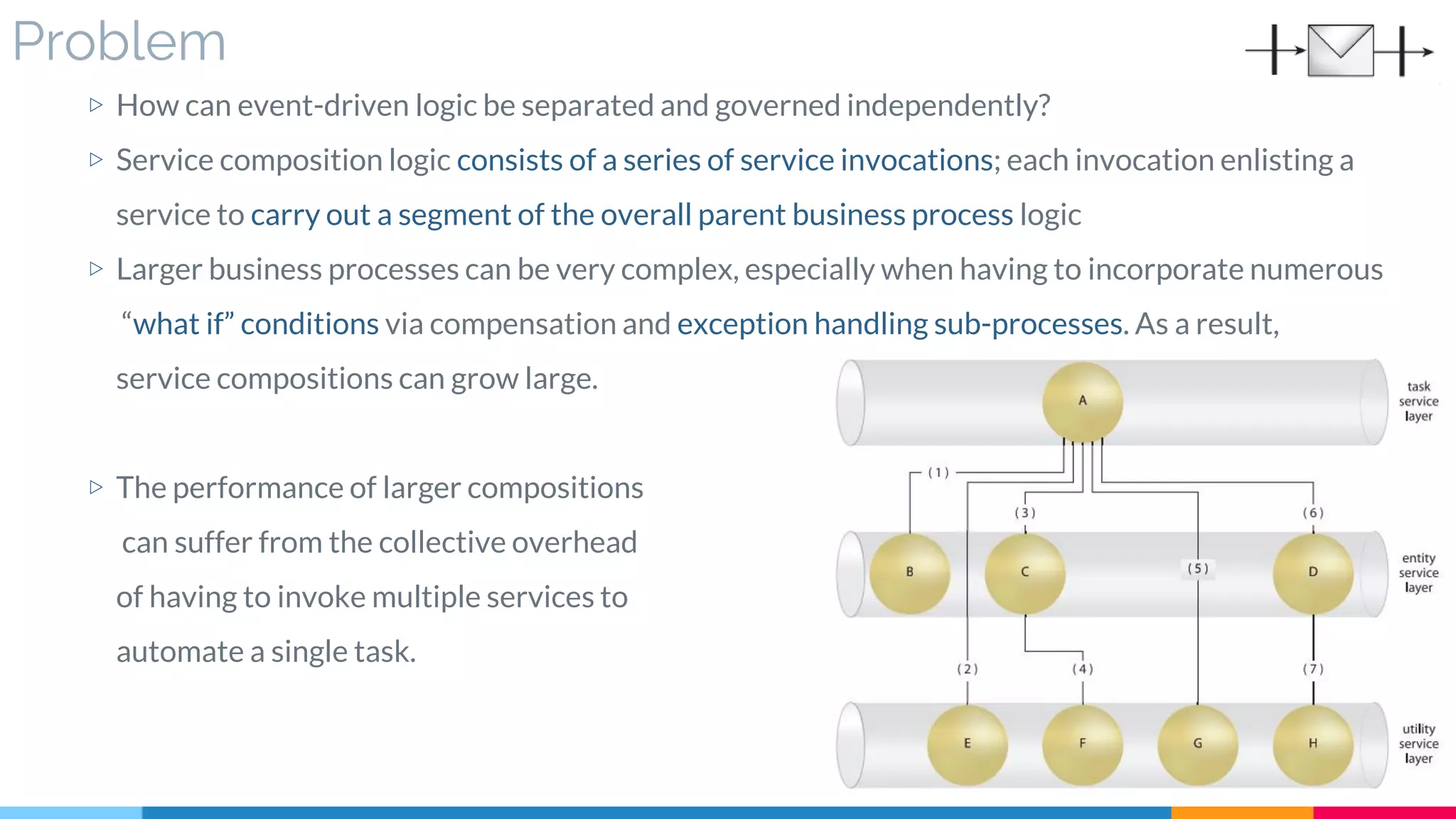
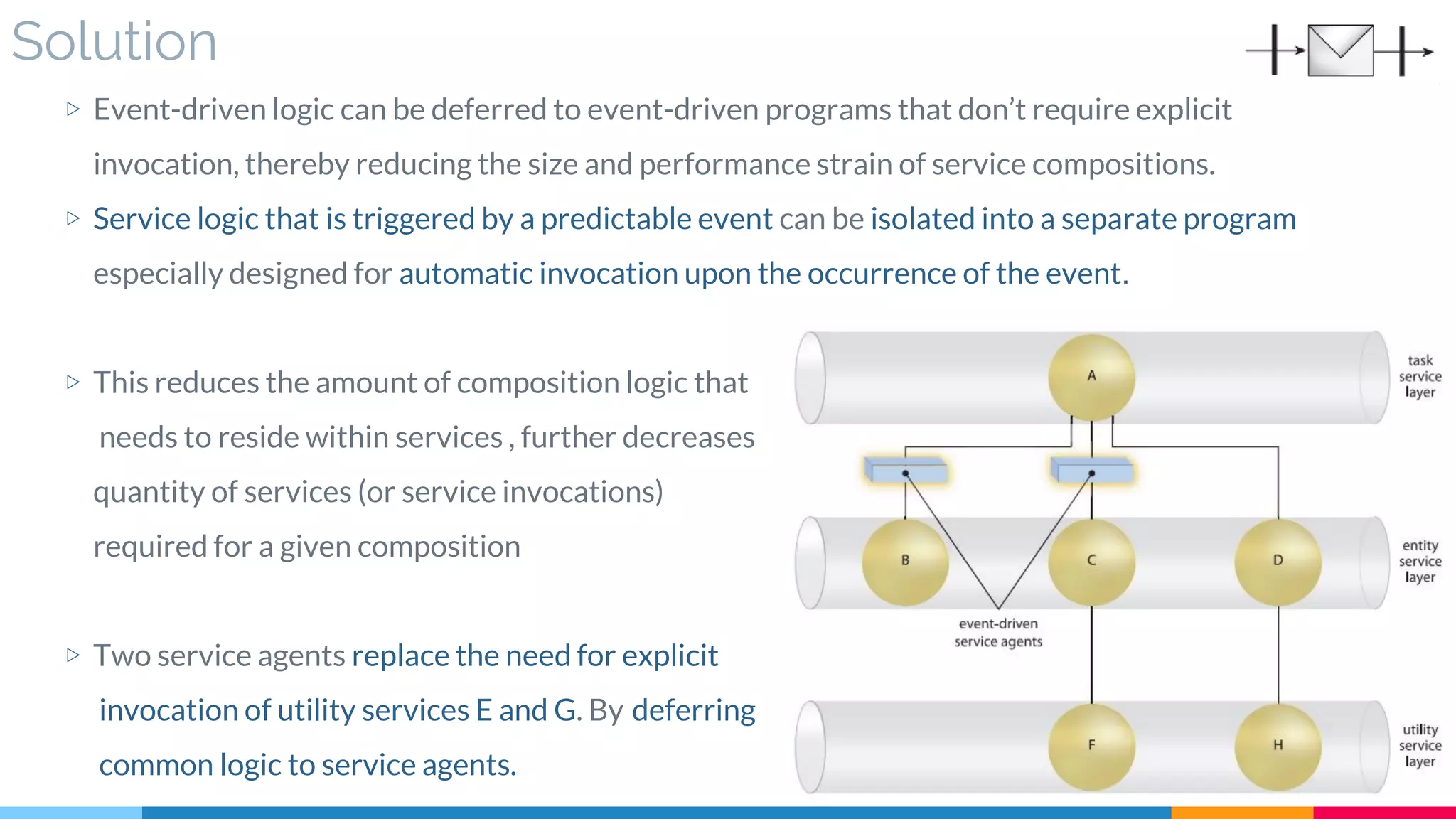
![24 Service Agent
▷ Problem
▷ Solution
▷ Real World Sample
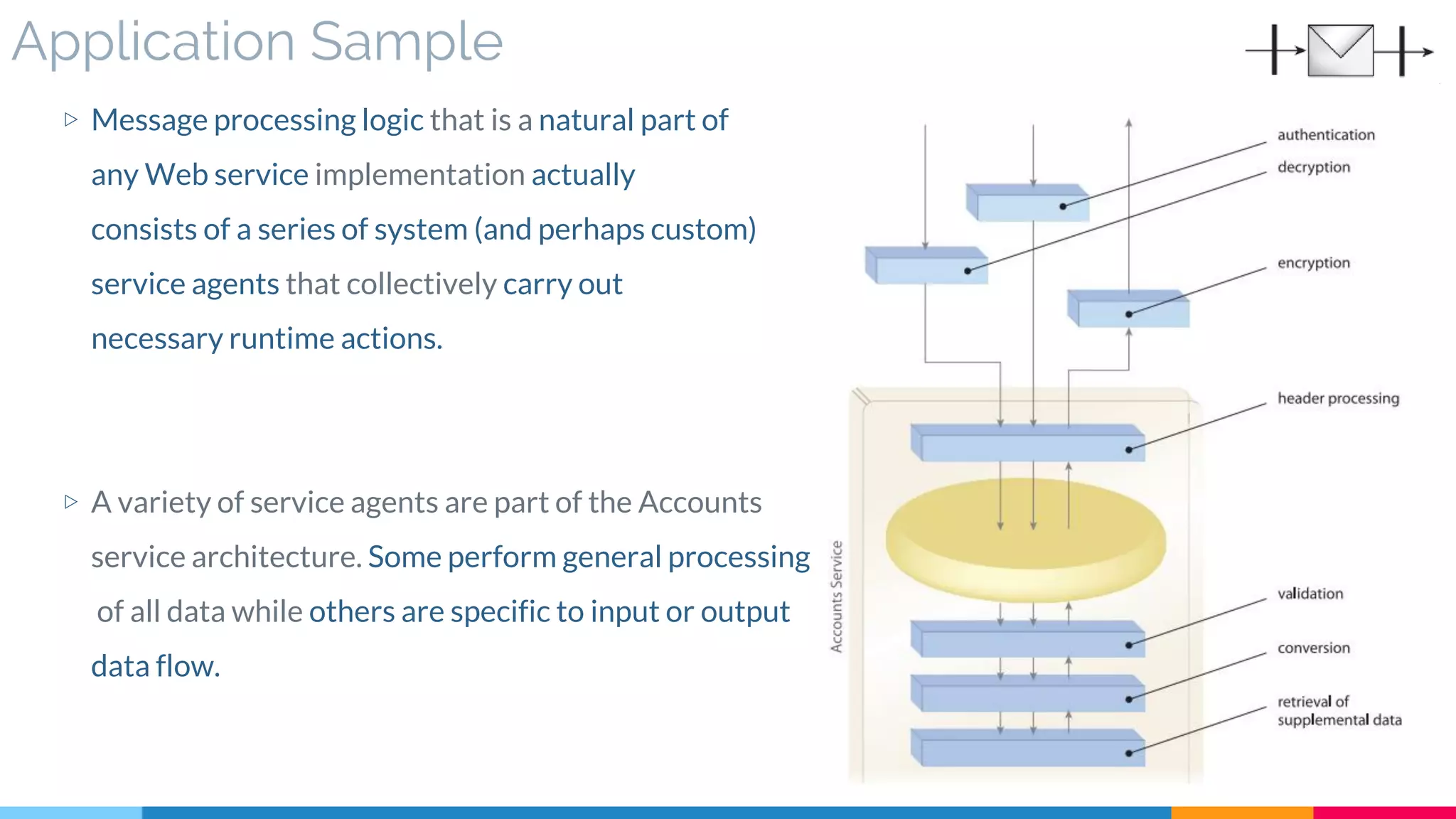
▷ Application
▷ Impact
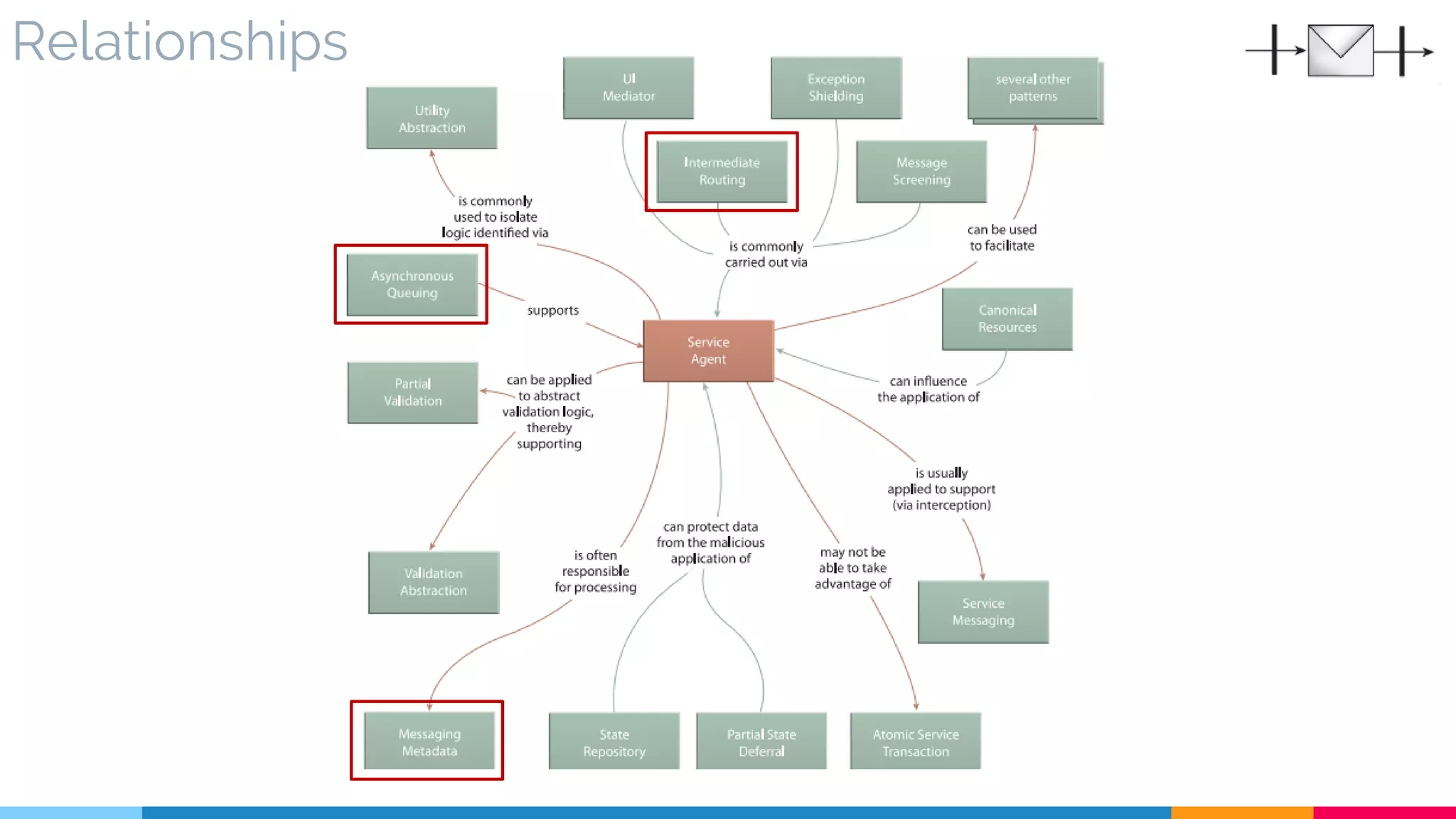
▷ Relationships
[543]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-195-2048.jpg)


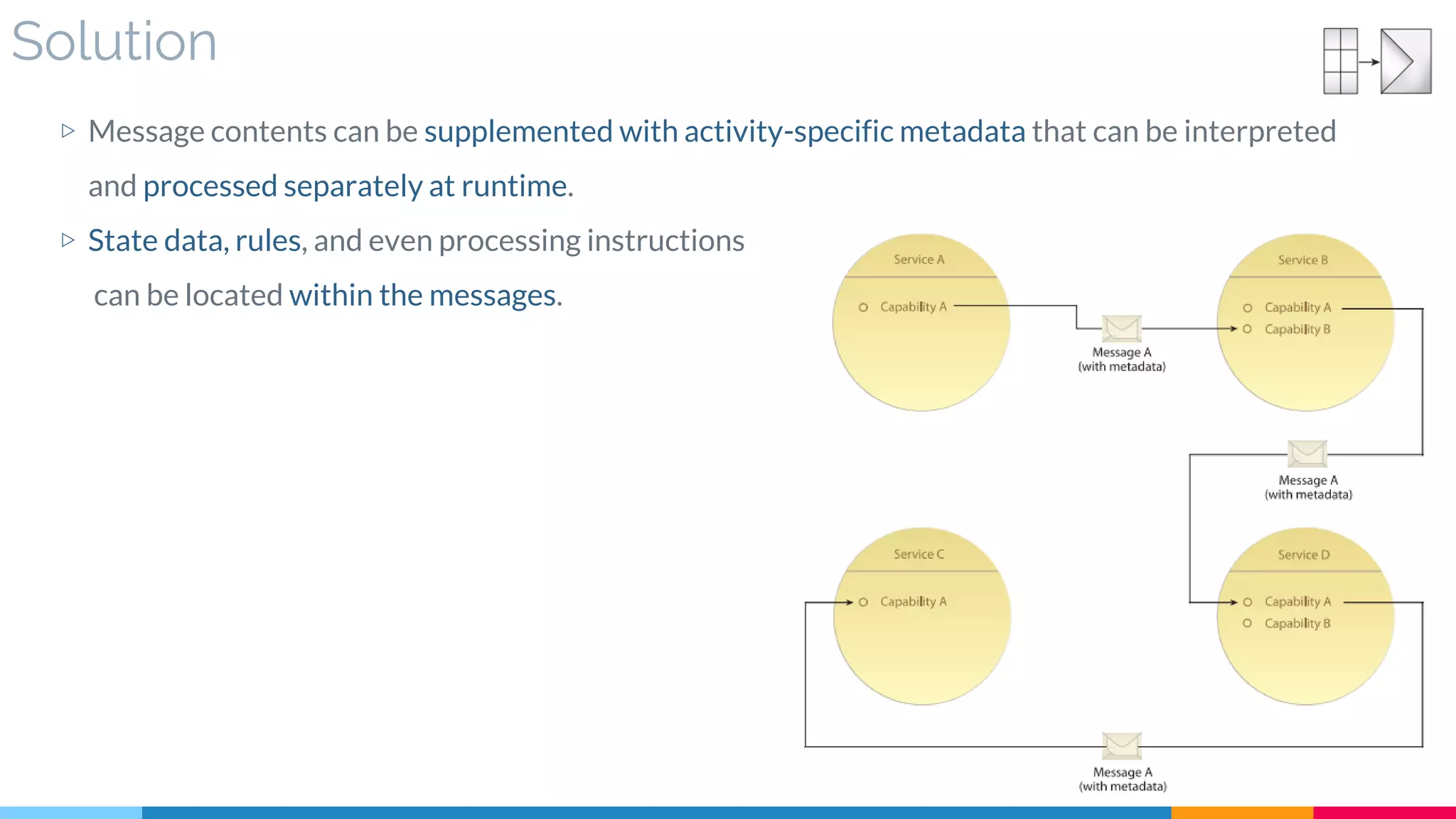
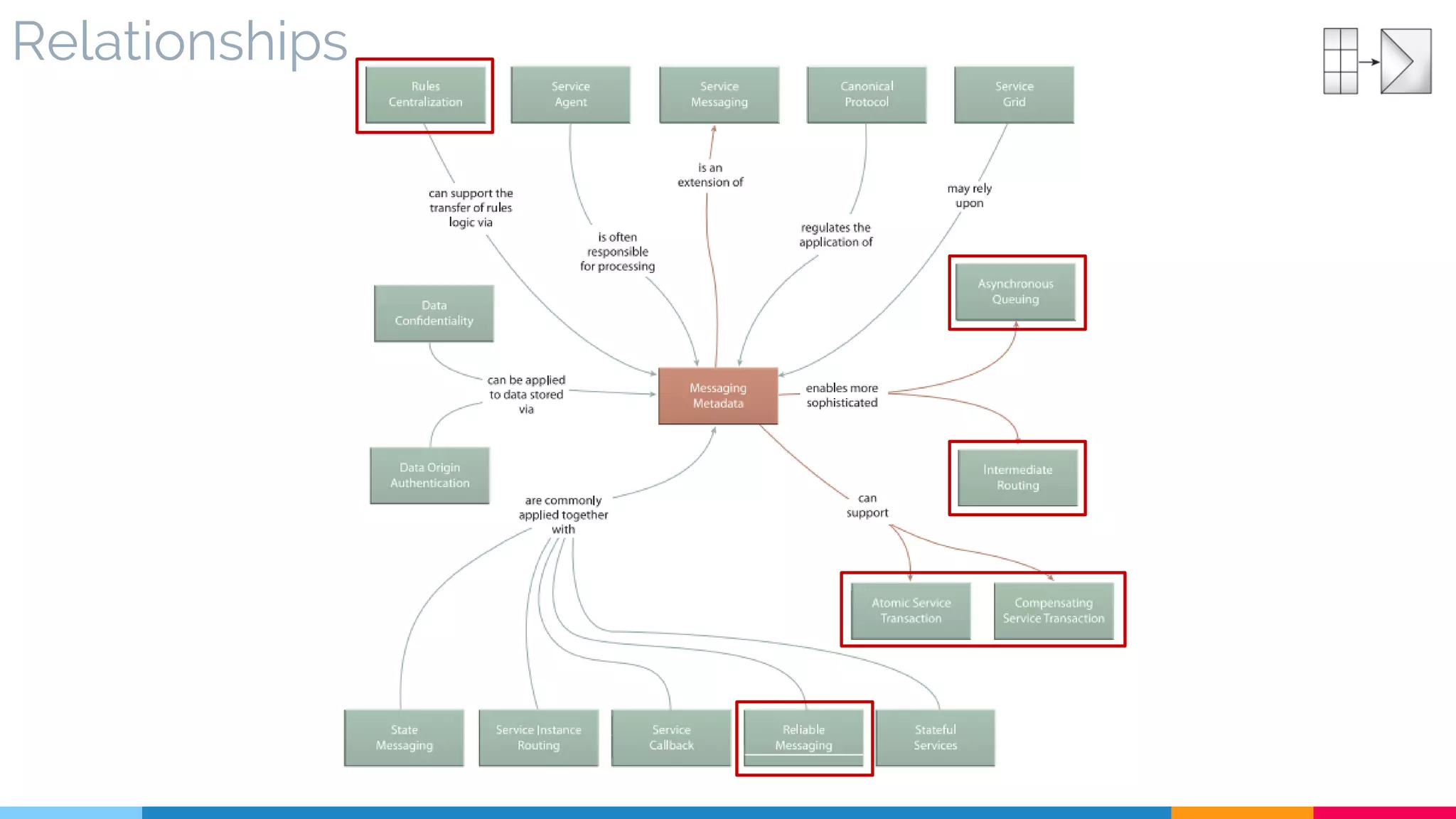
![25 Messaging Metadata
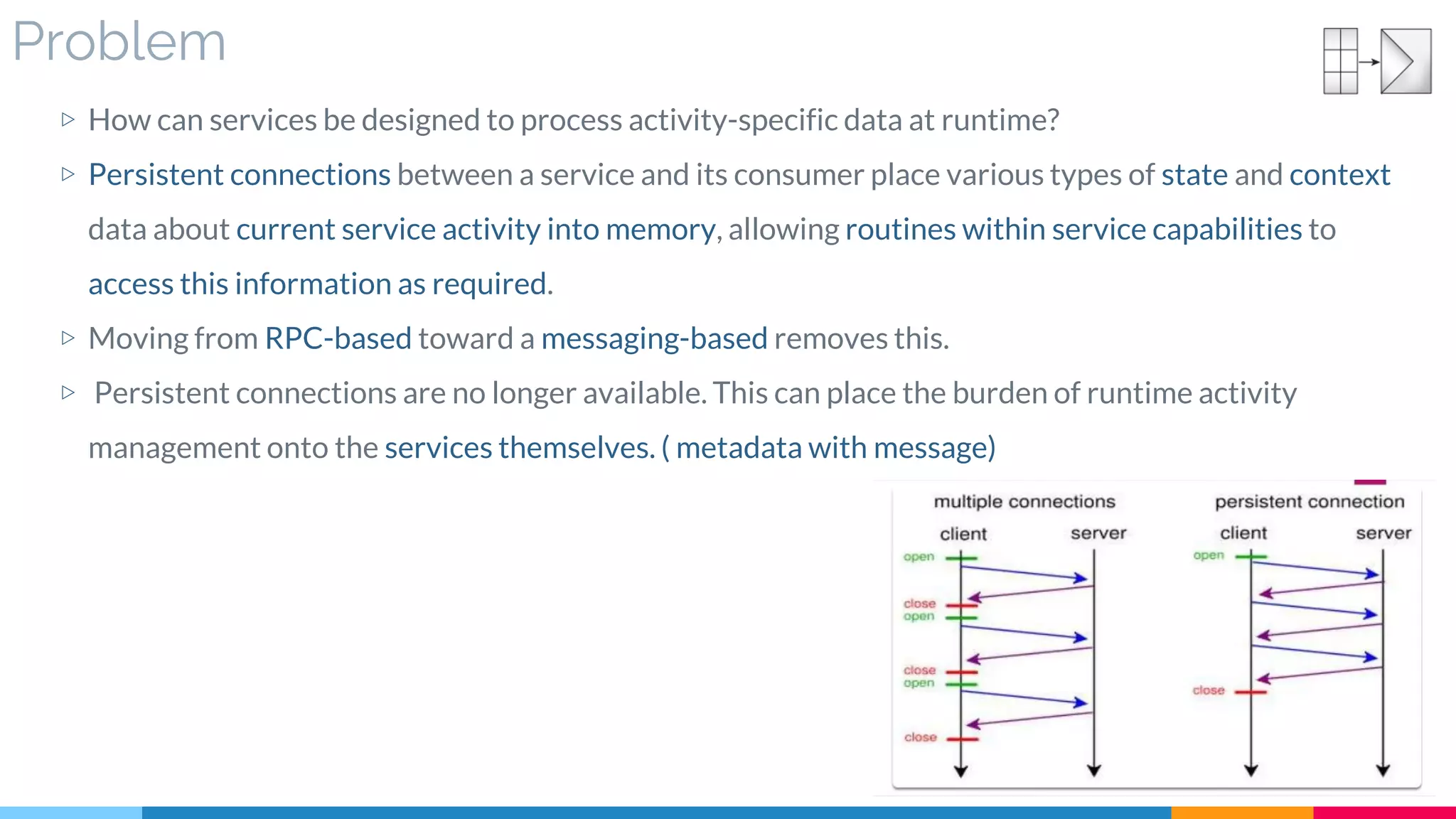
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[538]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-203-2048.jpg)




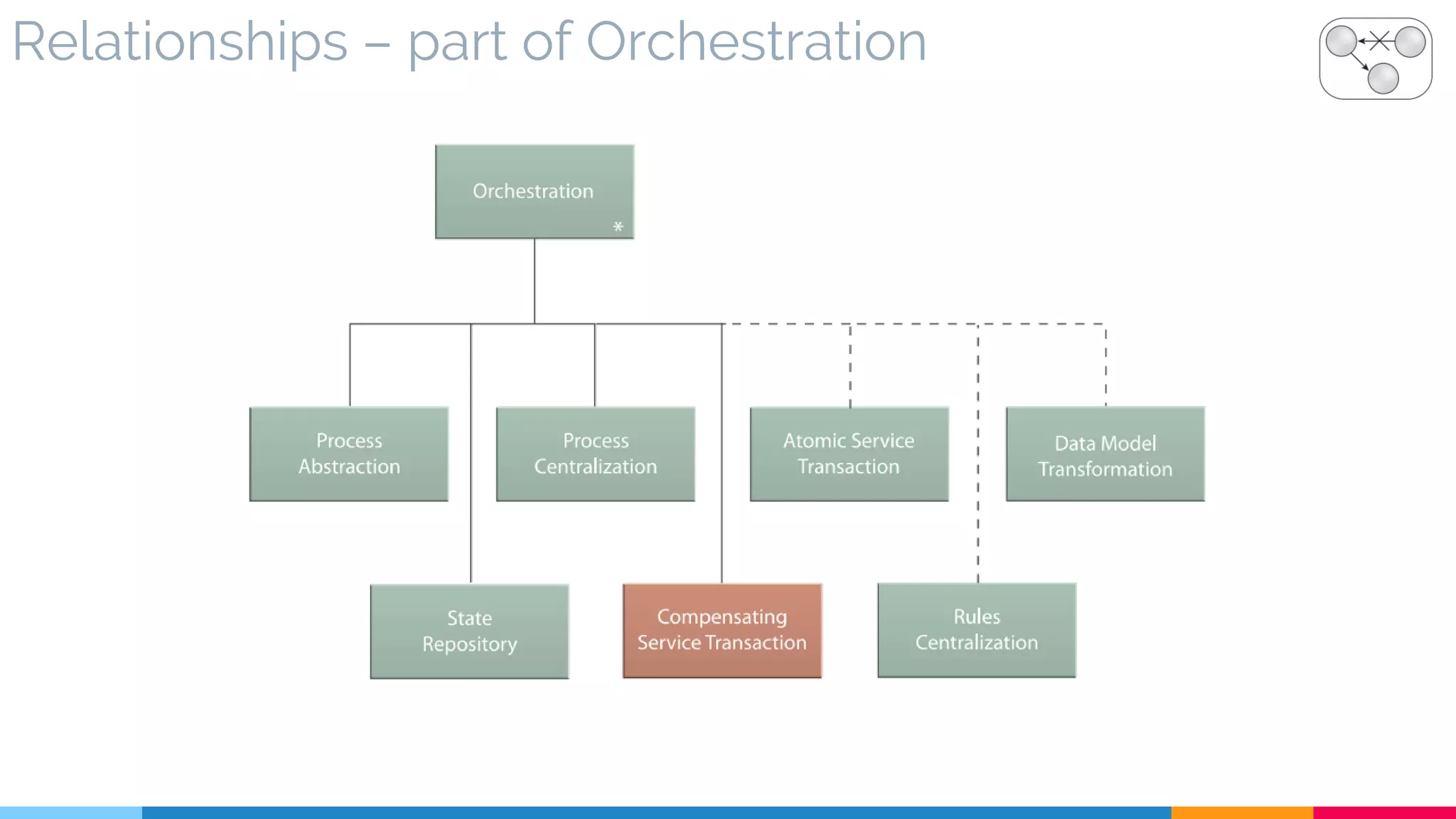
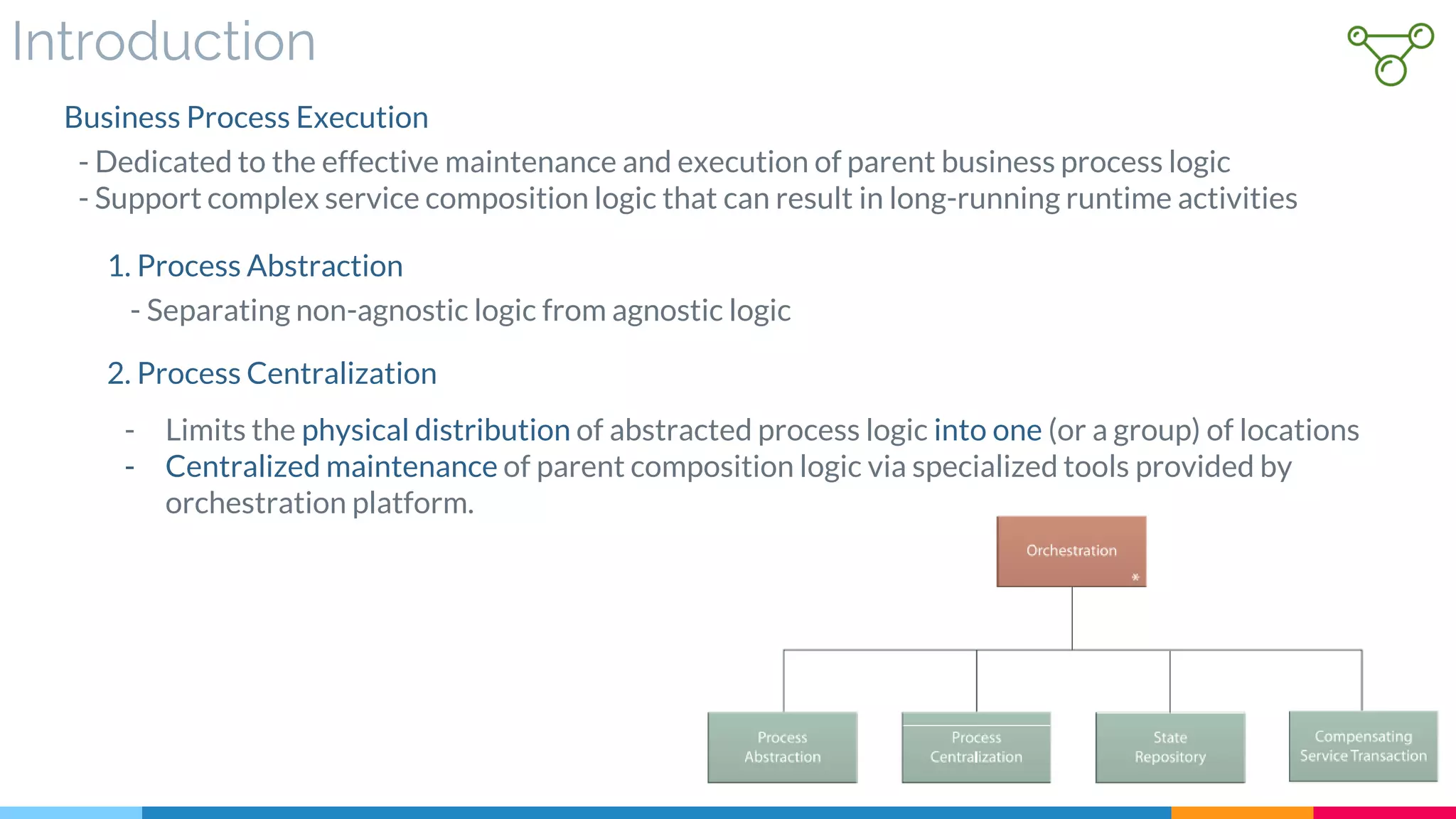
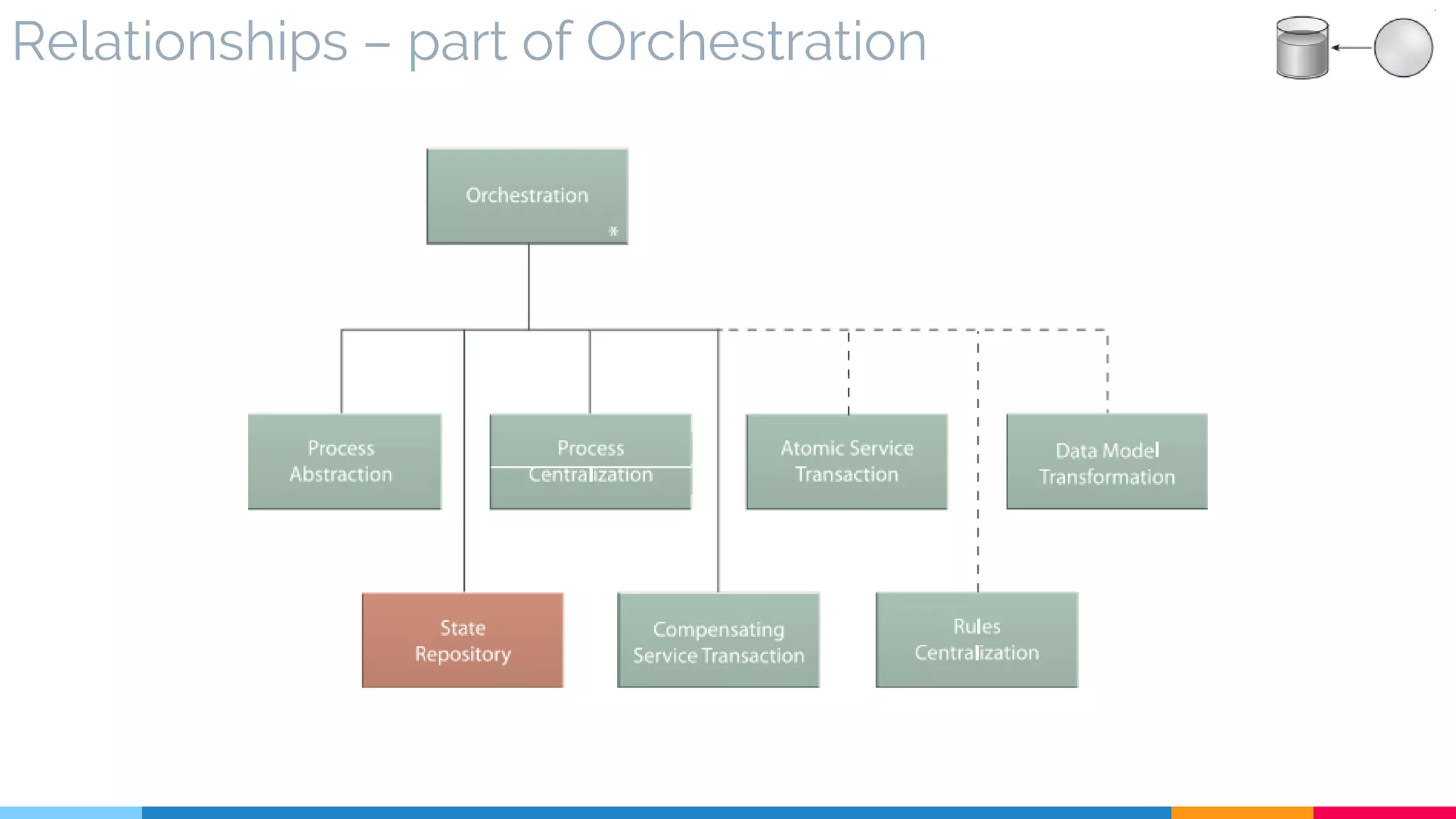
![26 Orchestration
▷ Introduction
▷ Orchestration Components
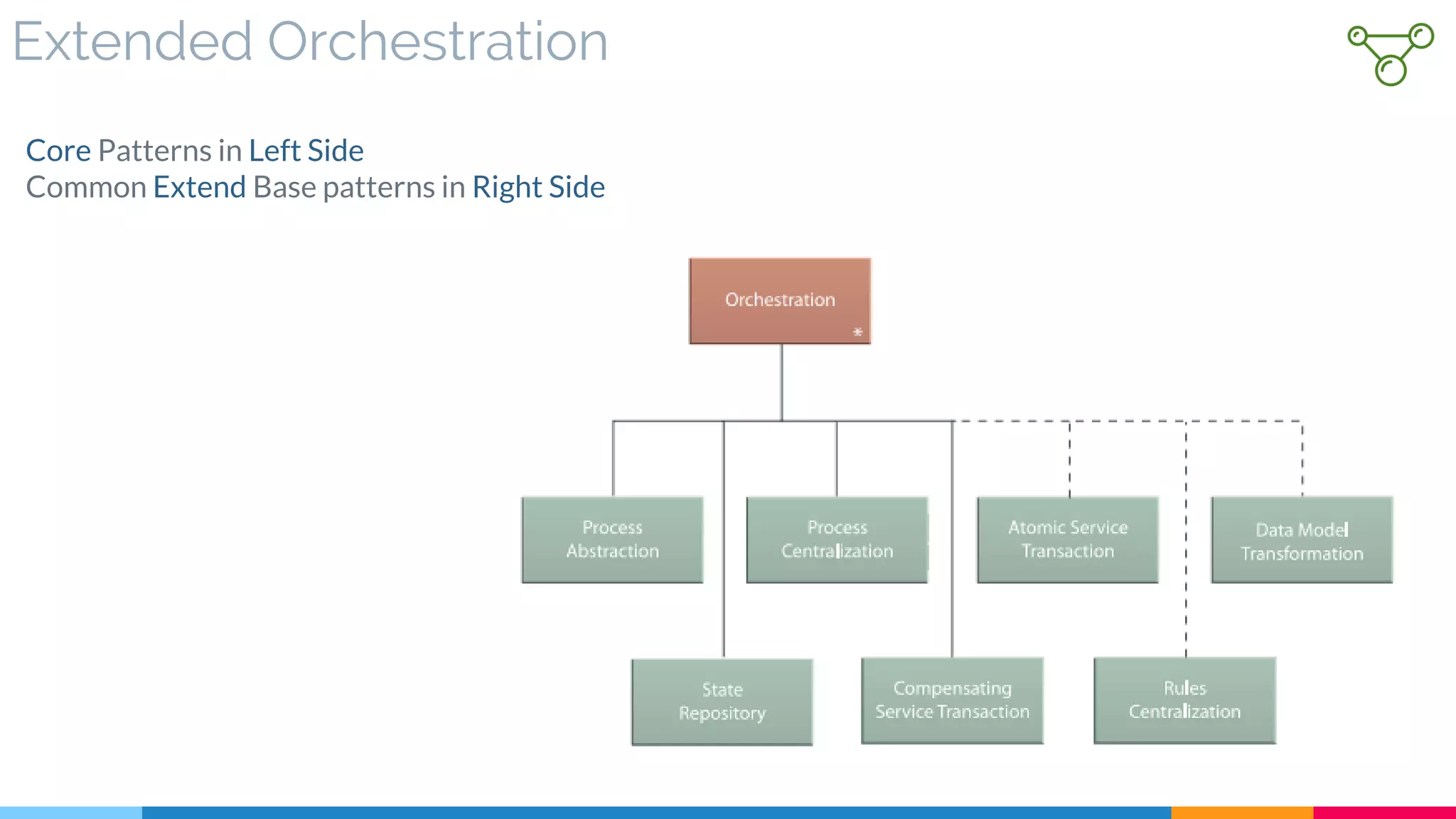
▷ Extended Orchestration
[701]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-211-2048.jpg)
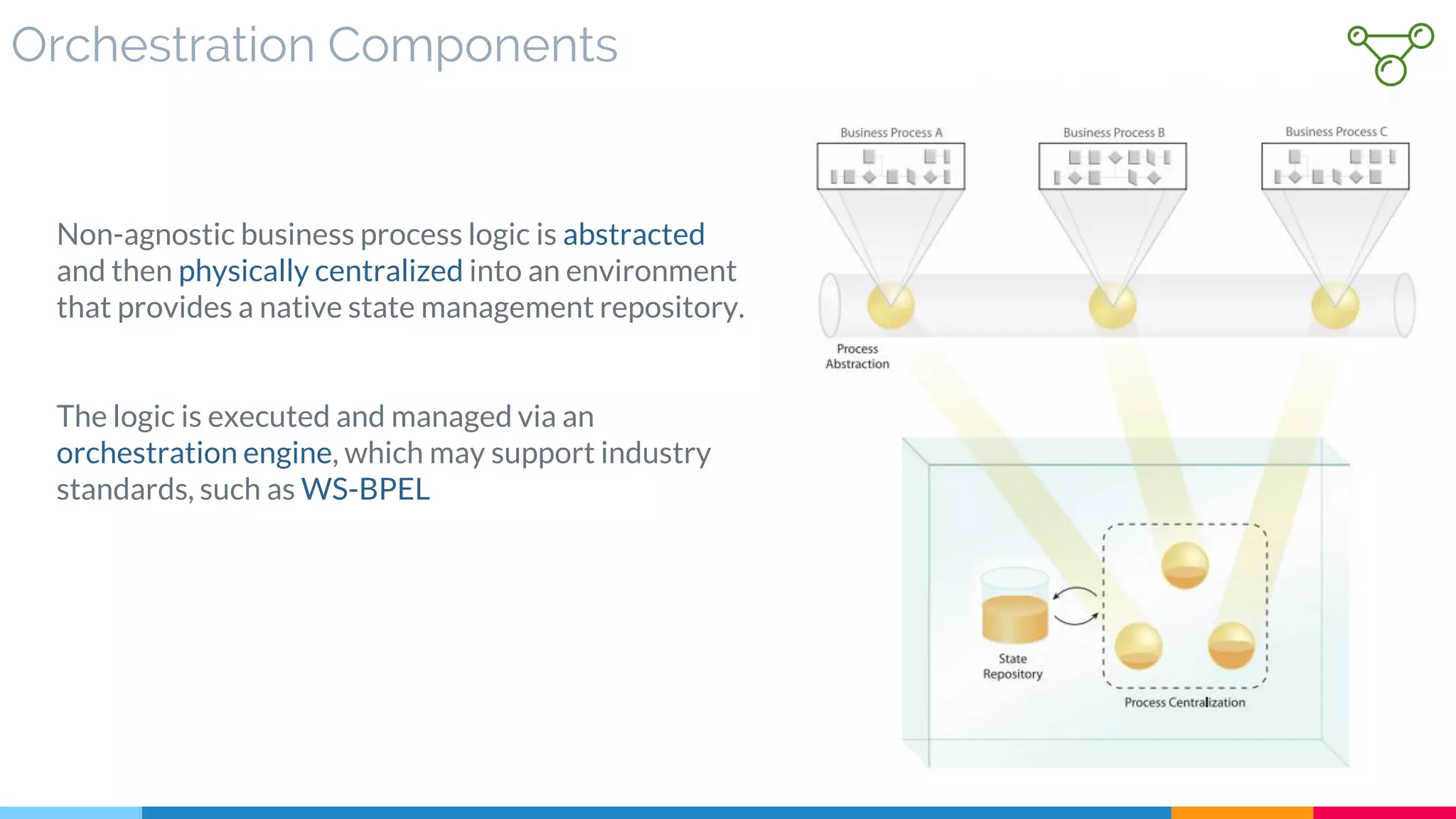
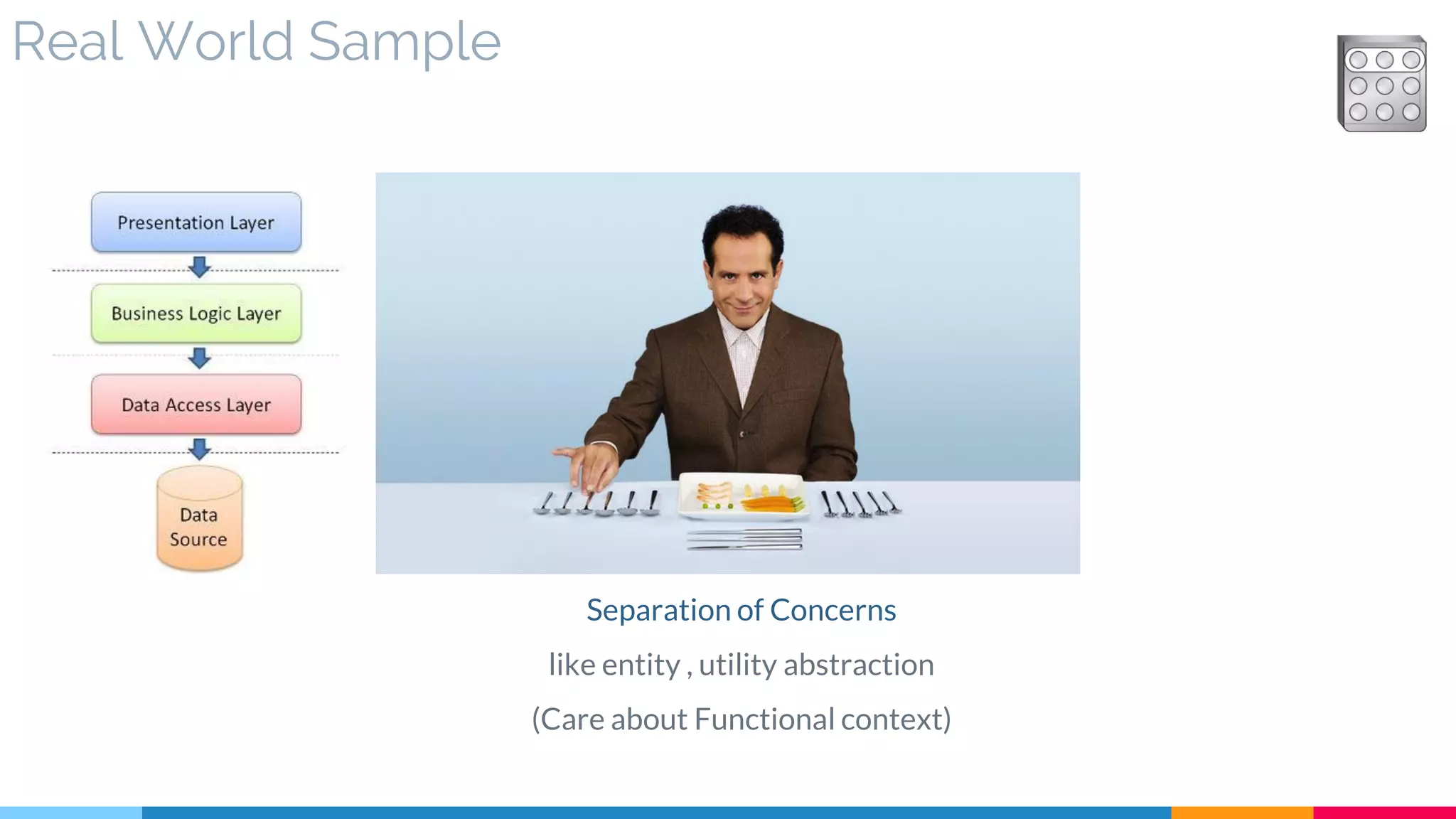
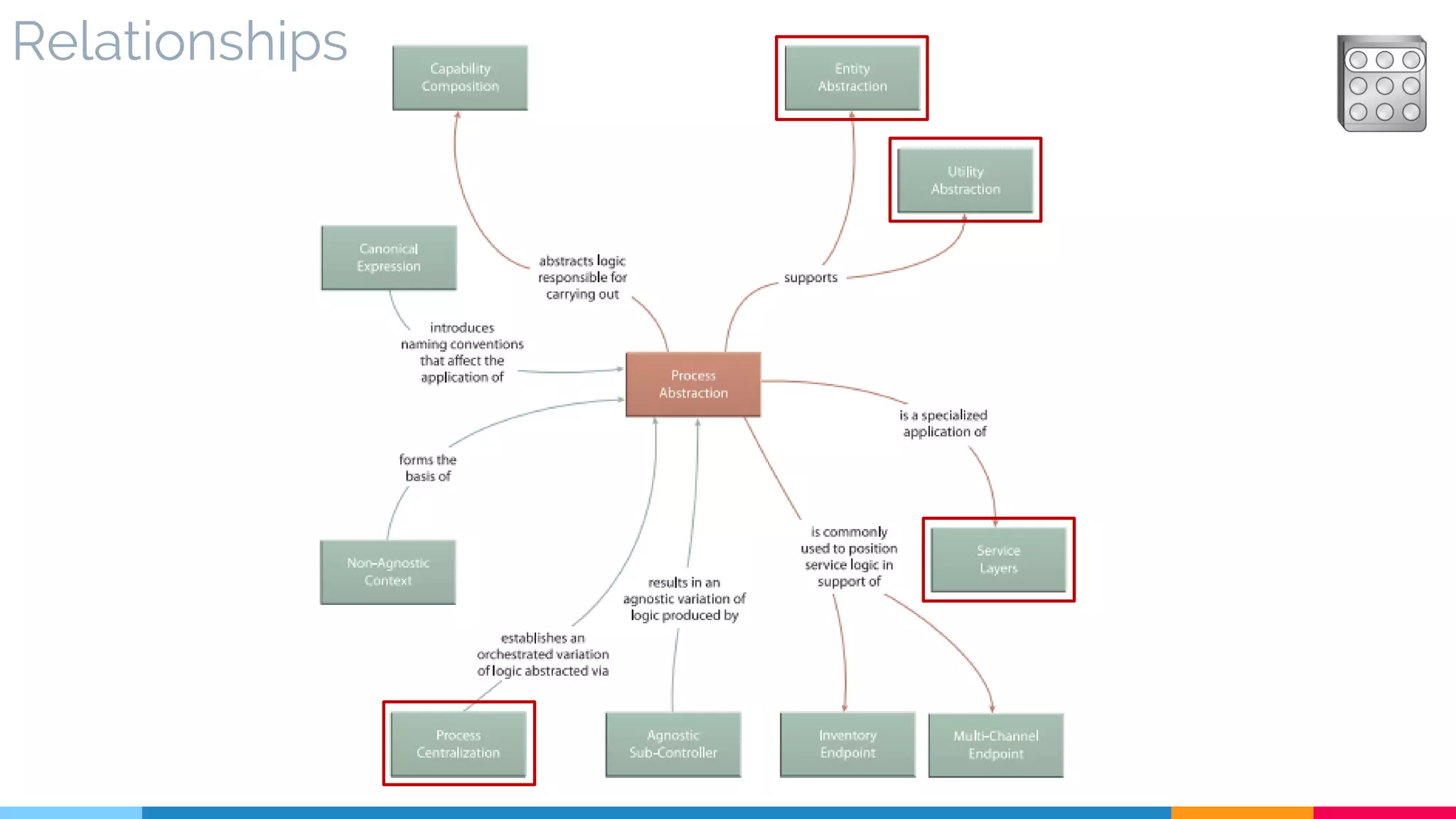
![27 Process Abstraction
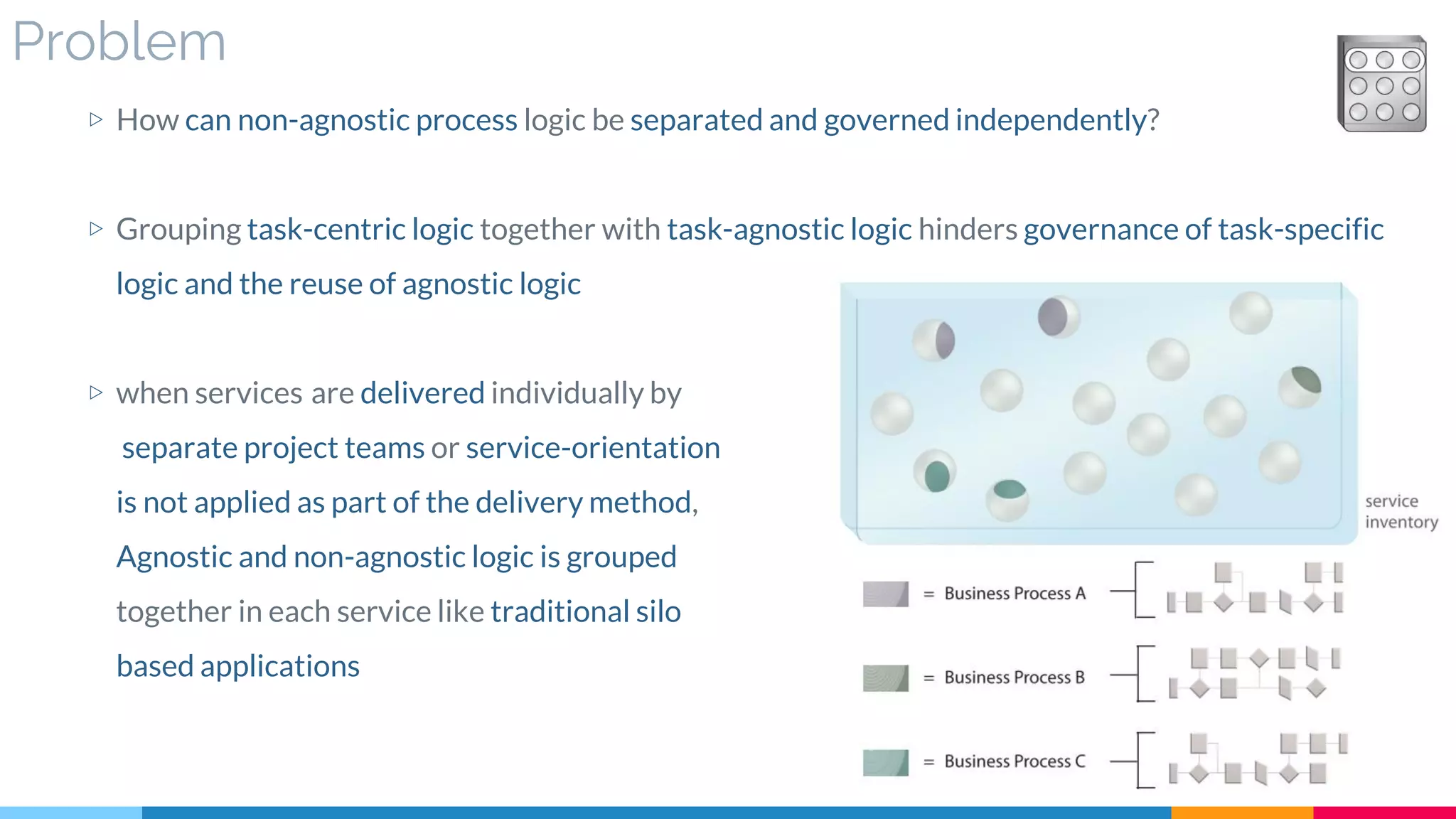
▷ Problem
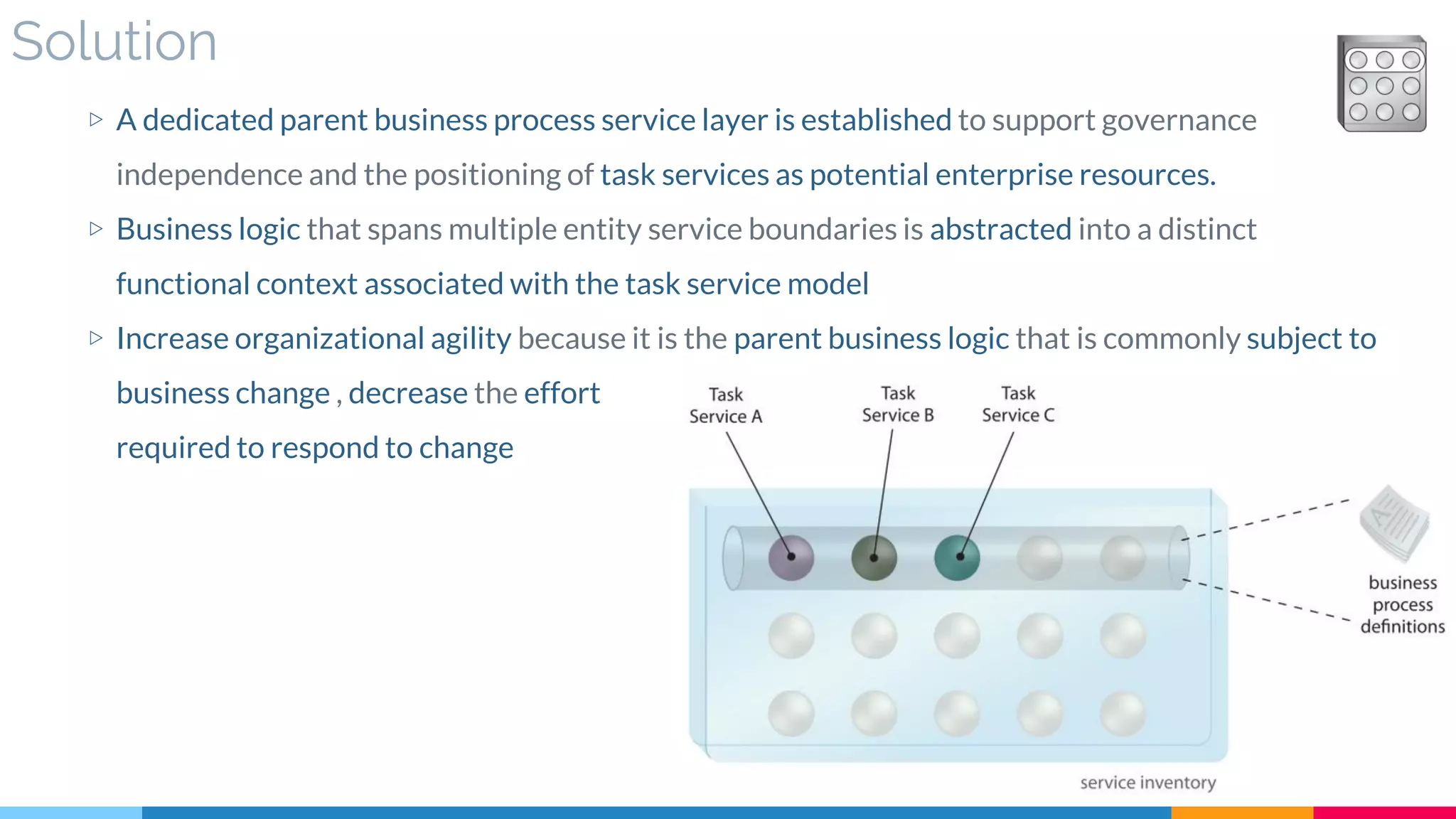
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[182]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-216-2048.jpg)



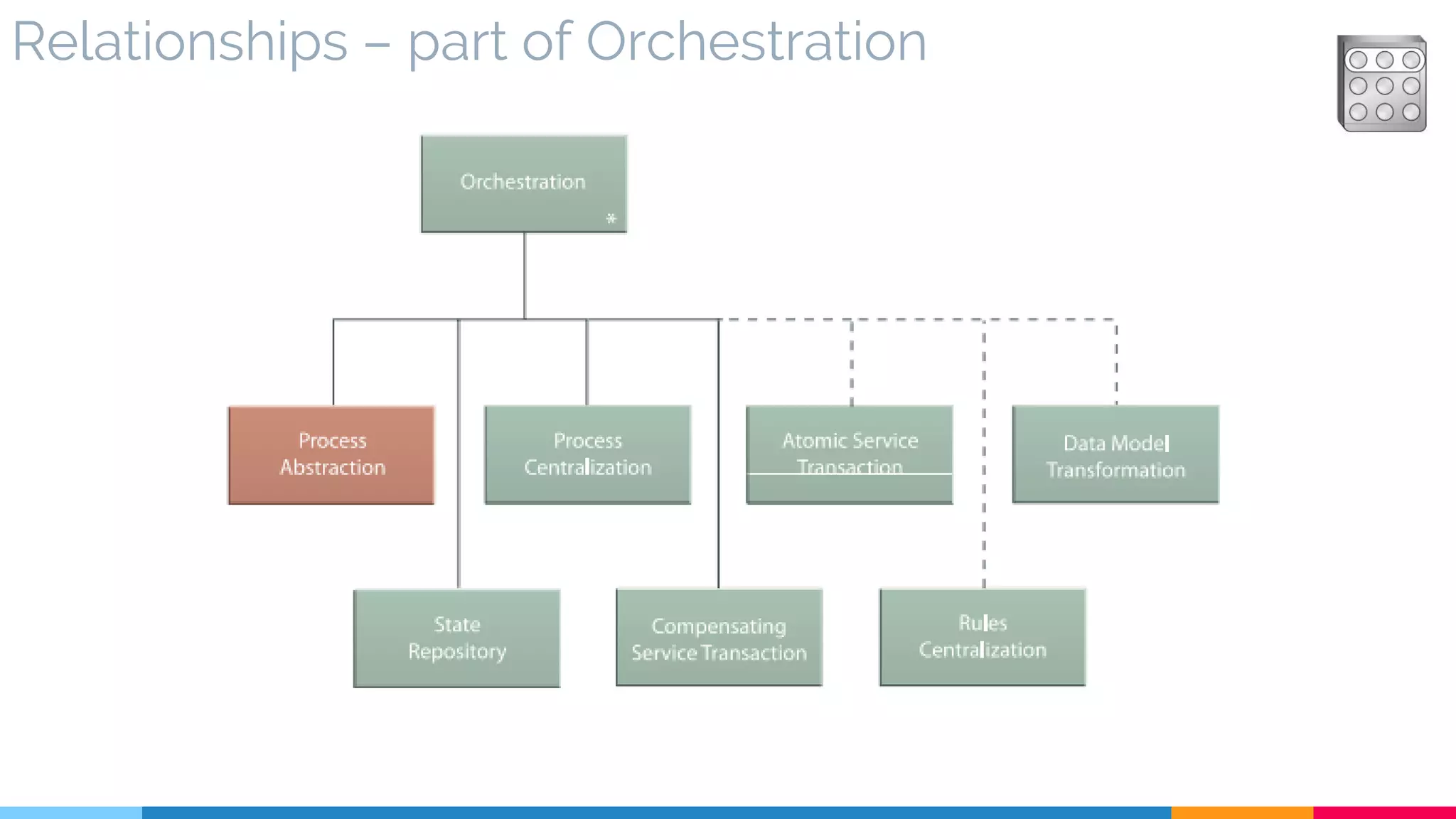
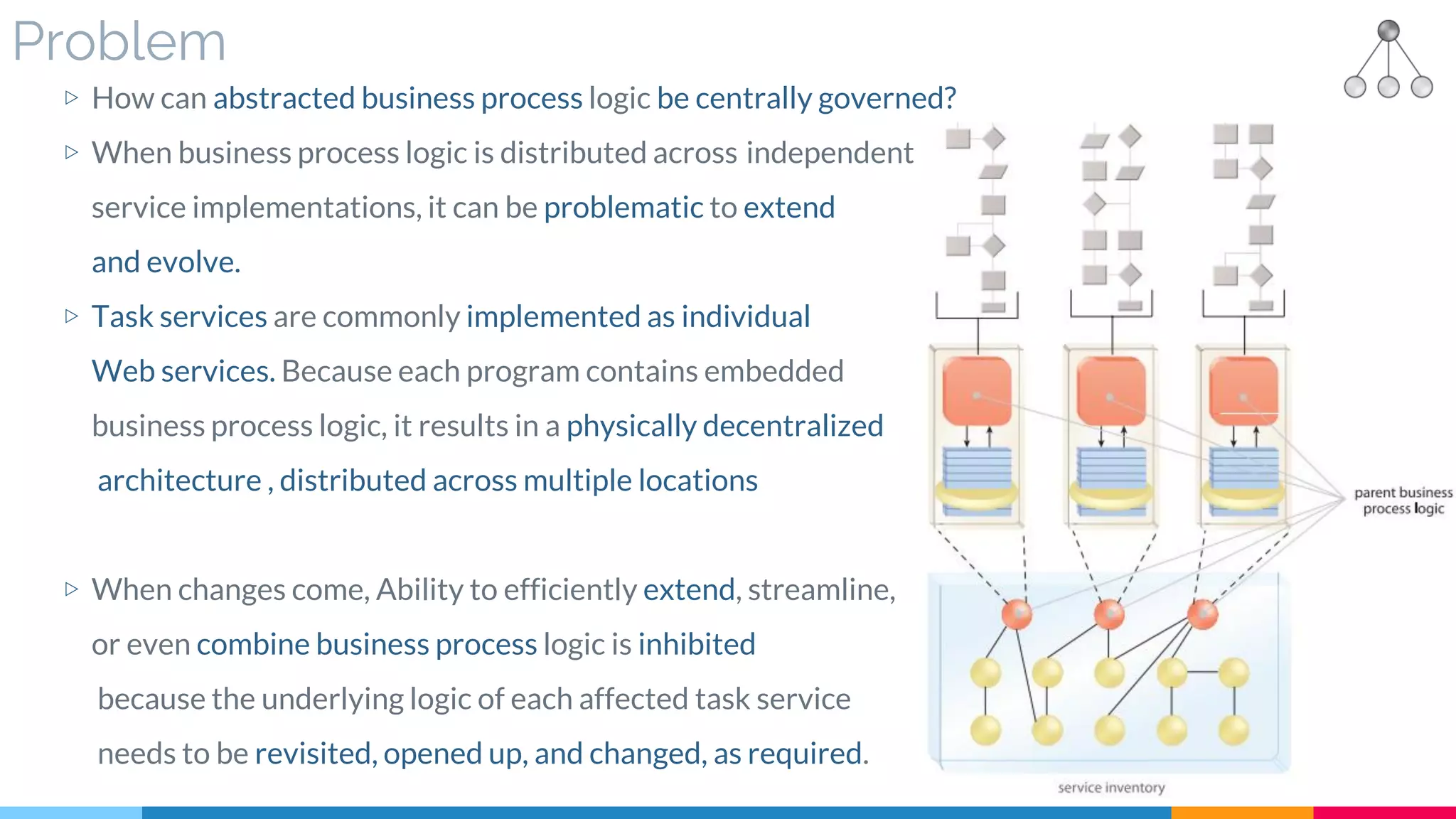
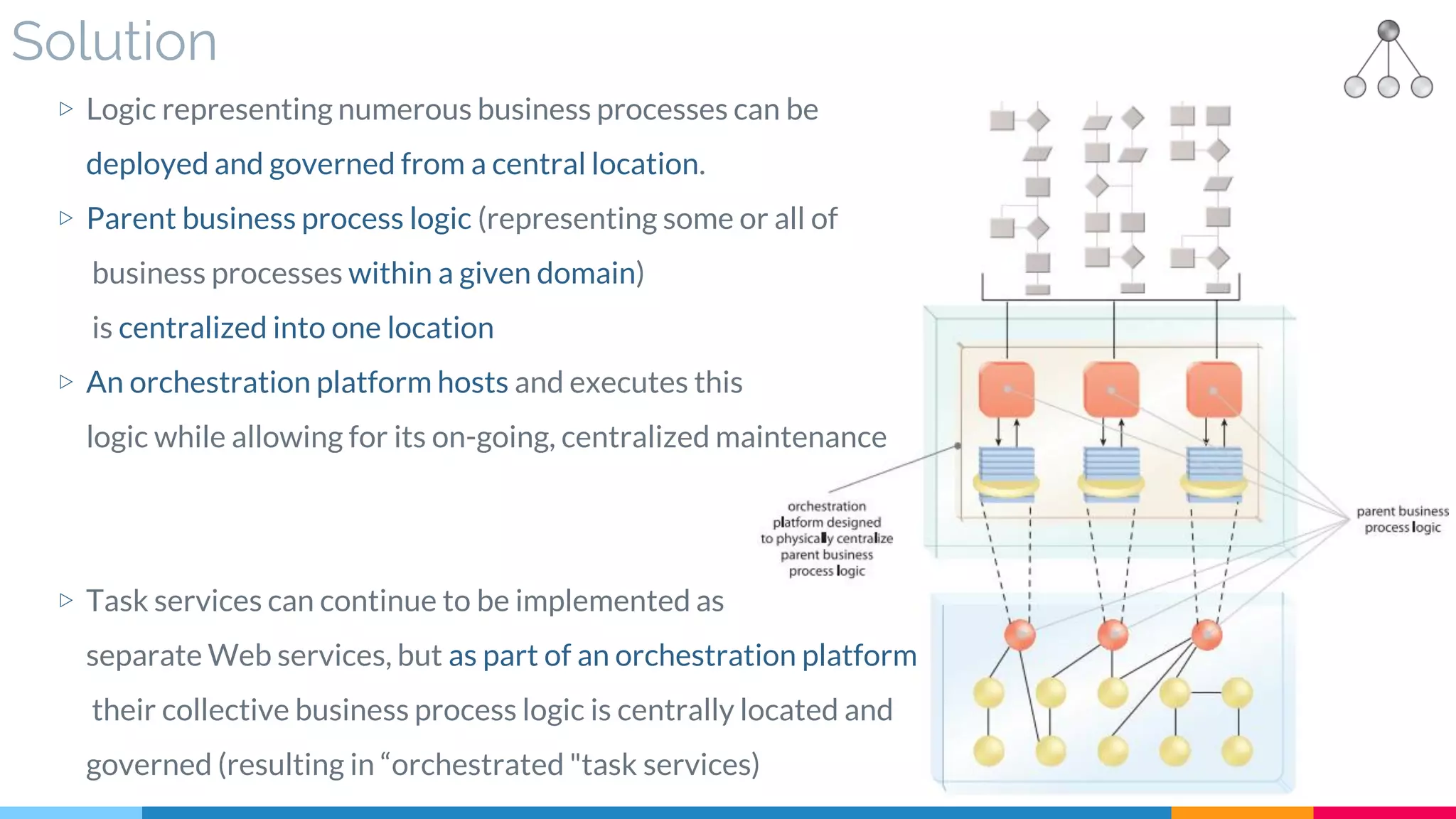
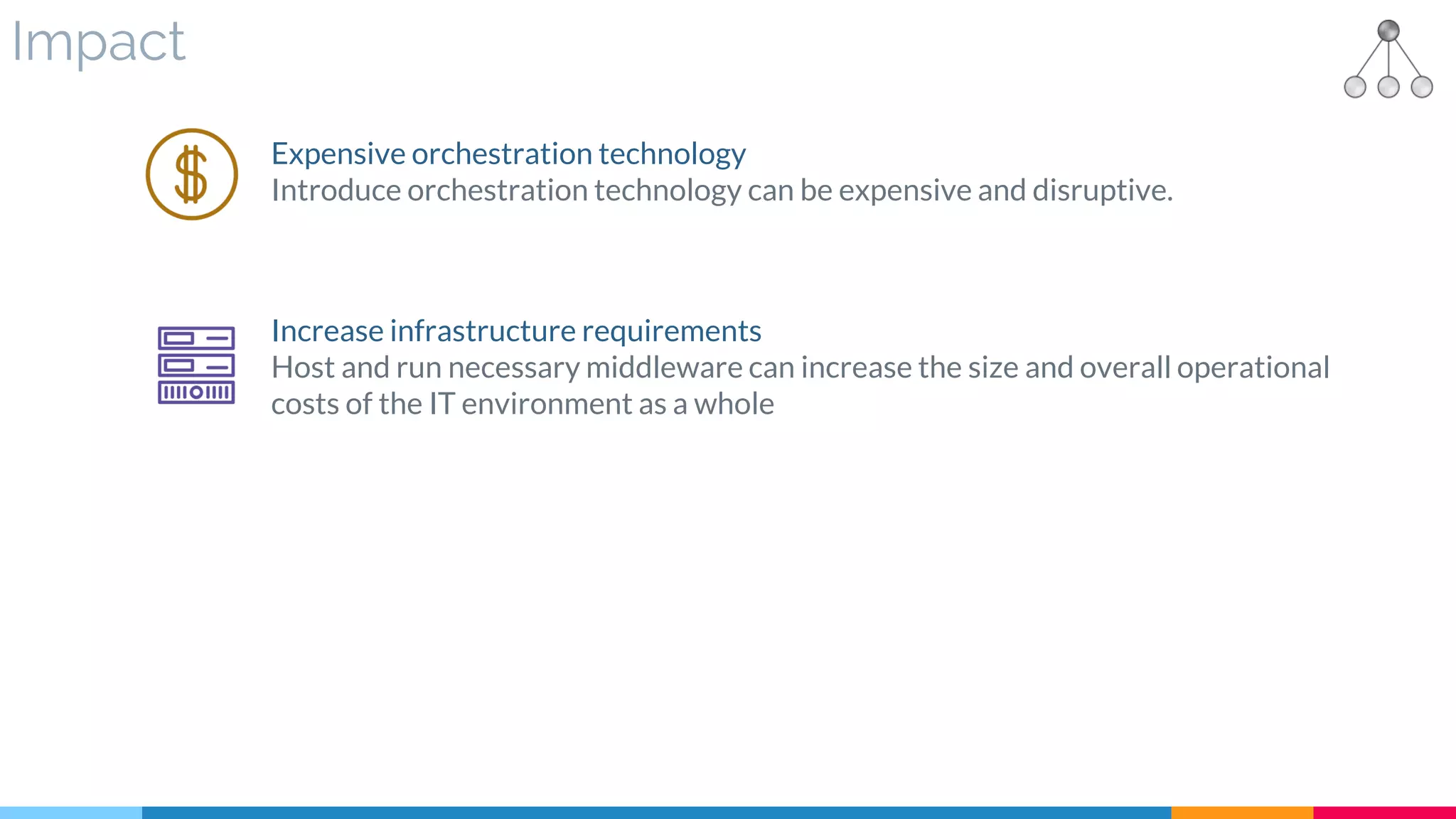
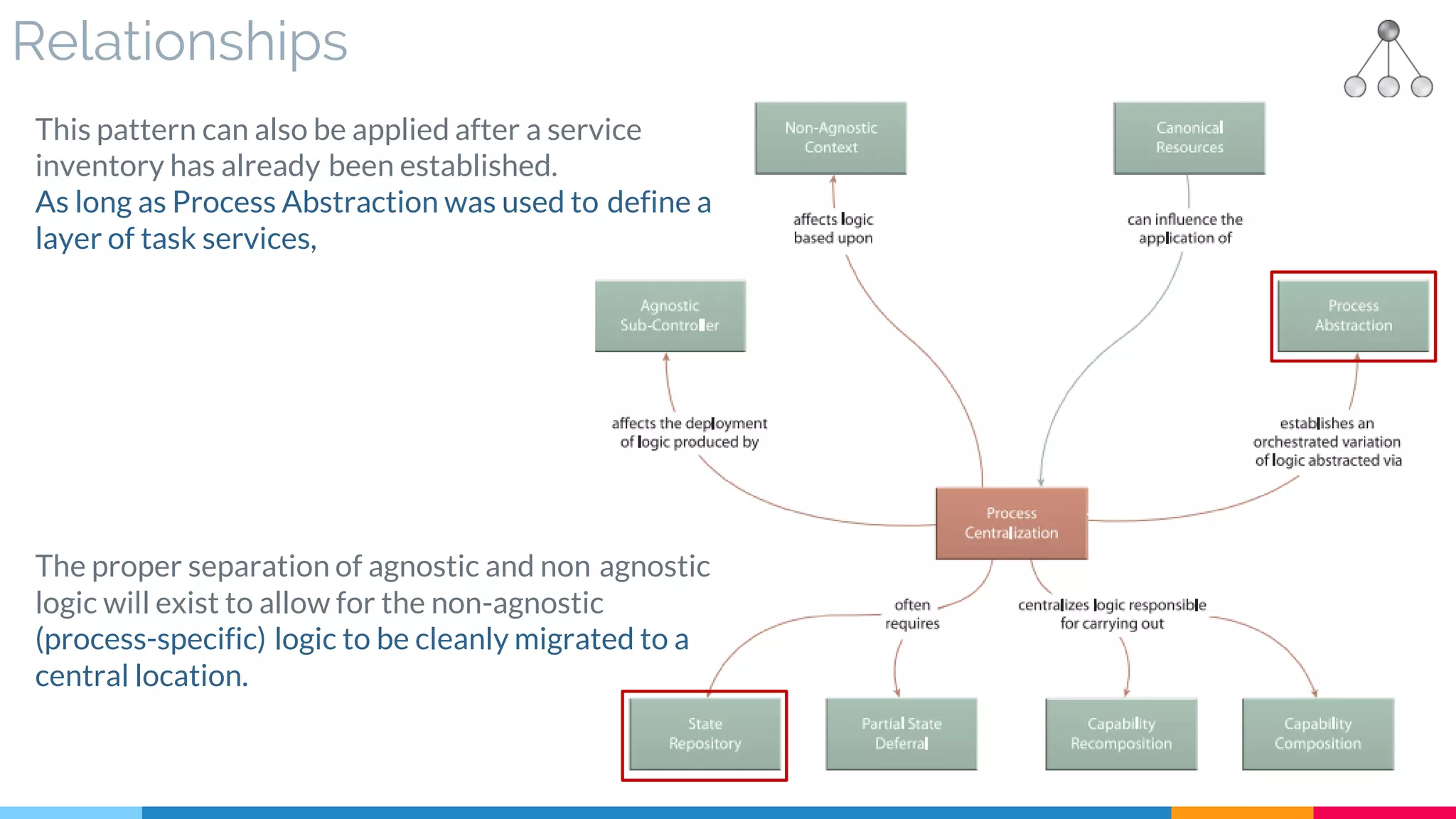
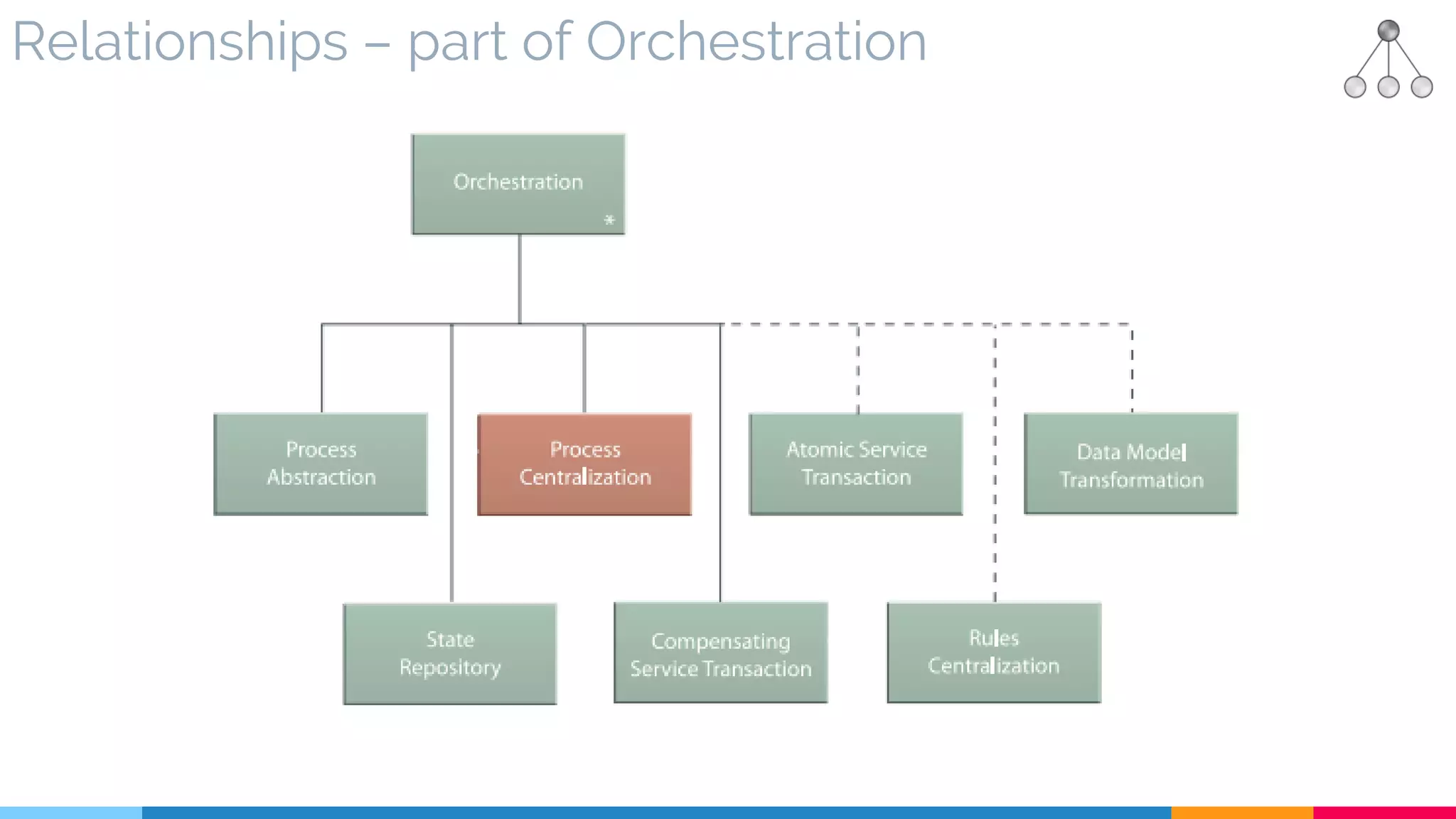
![28 Process Centralization
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[193]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-225-2048.jpg)


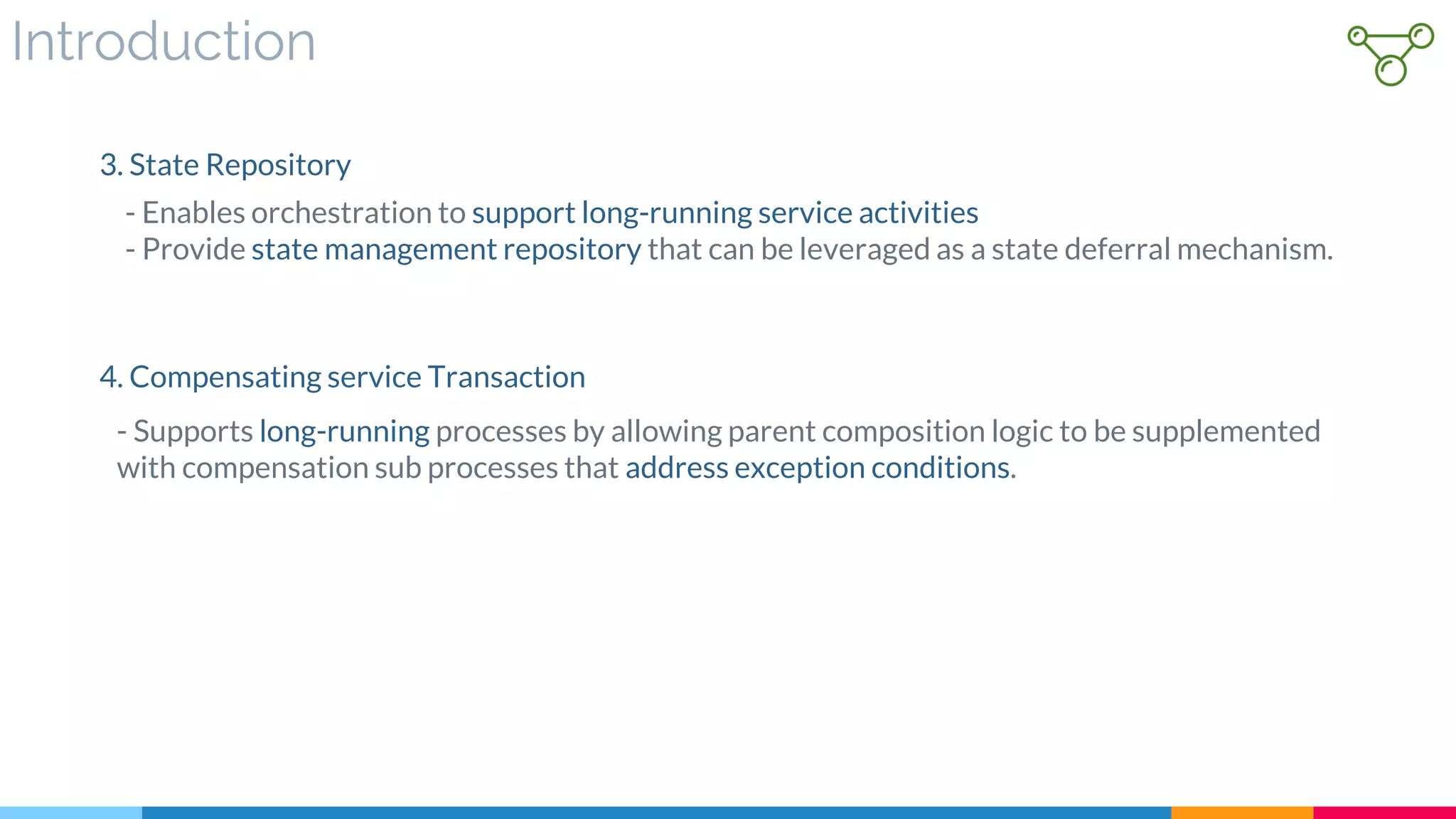
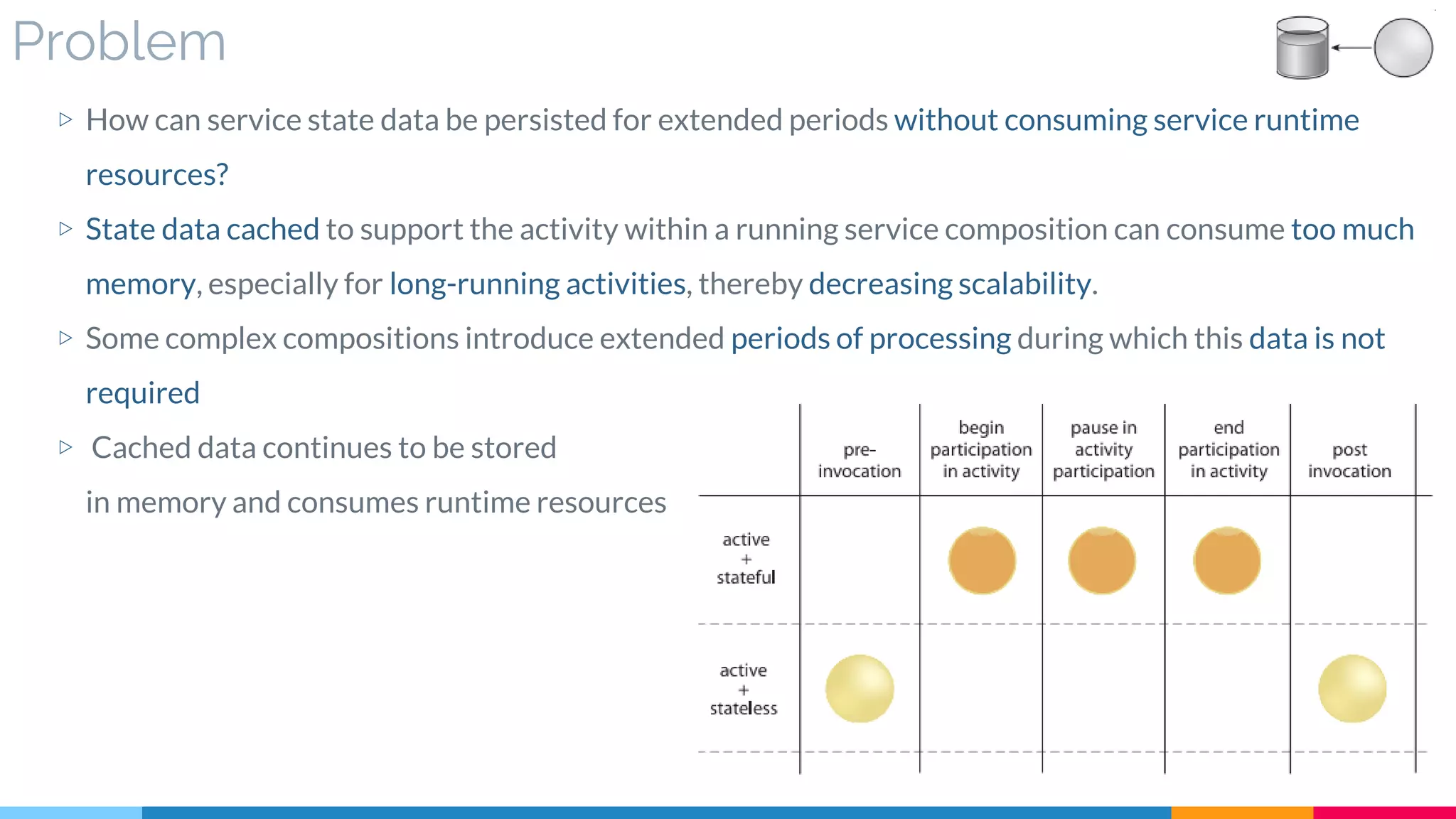
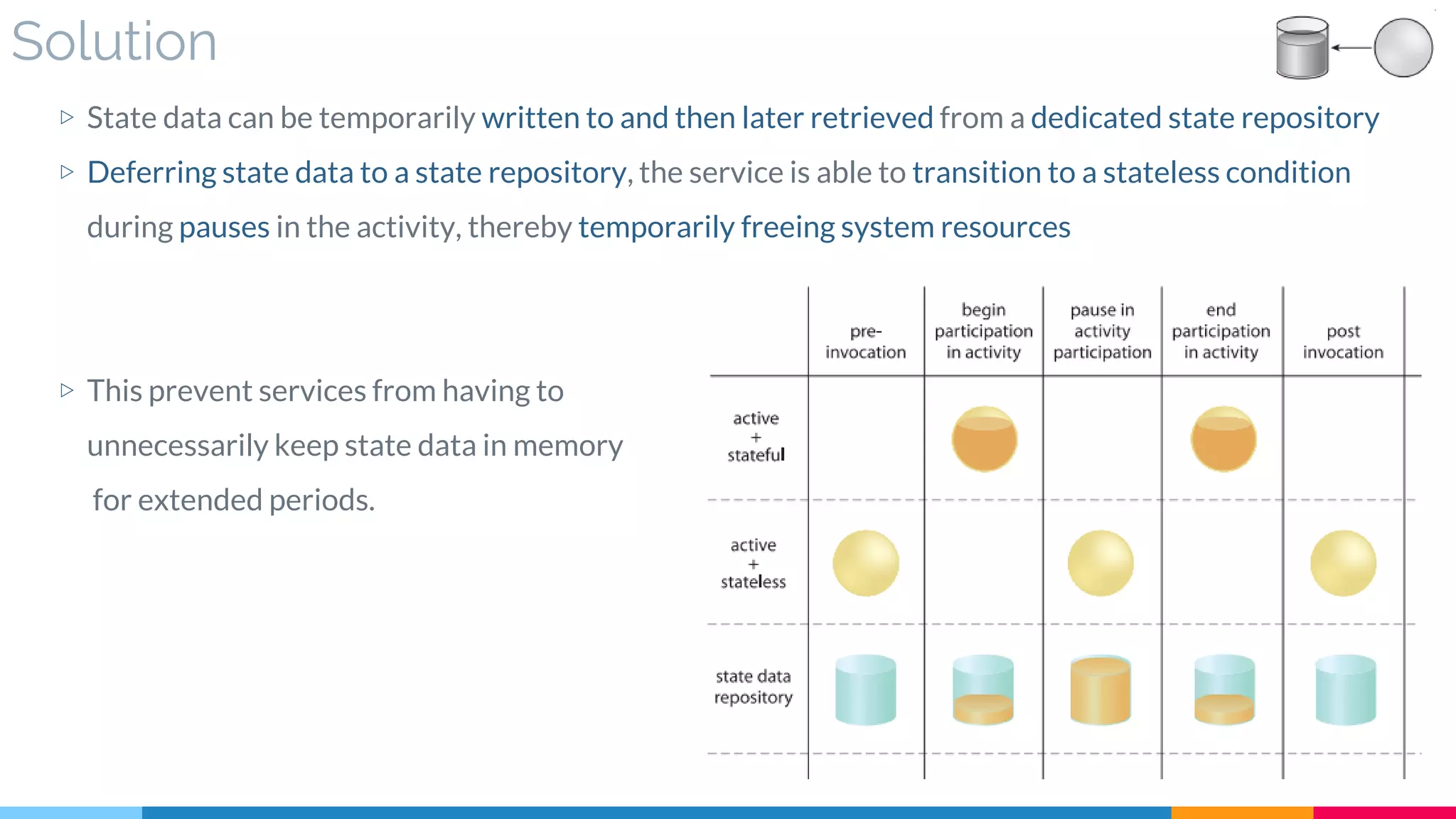
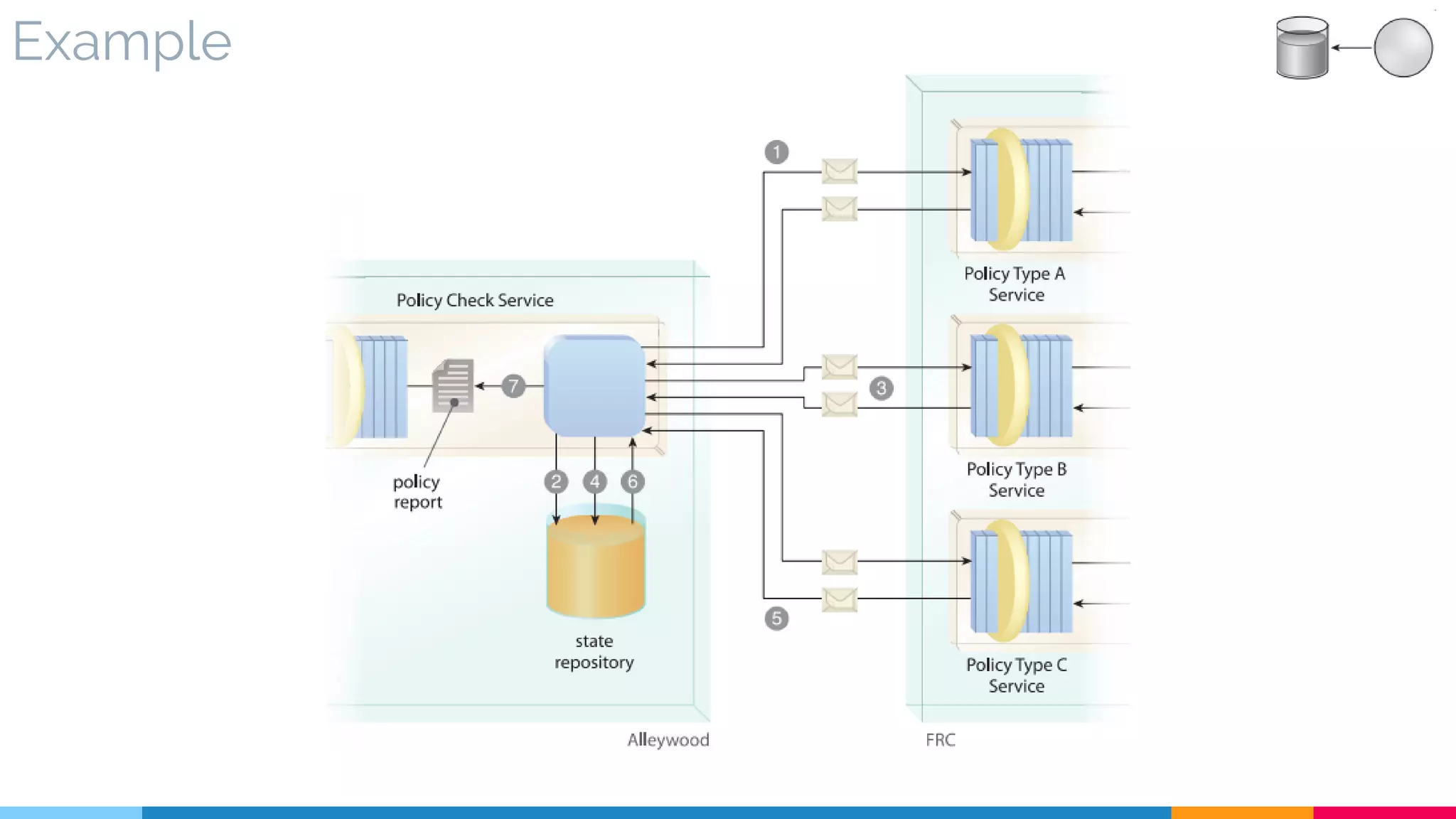
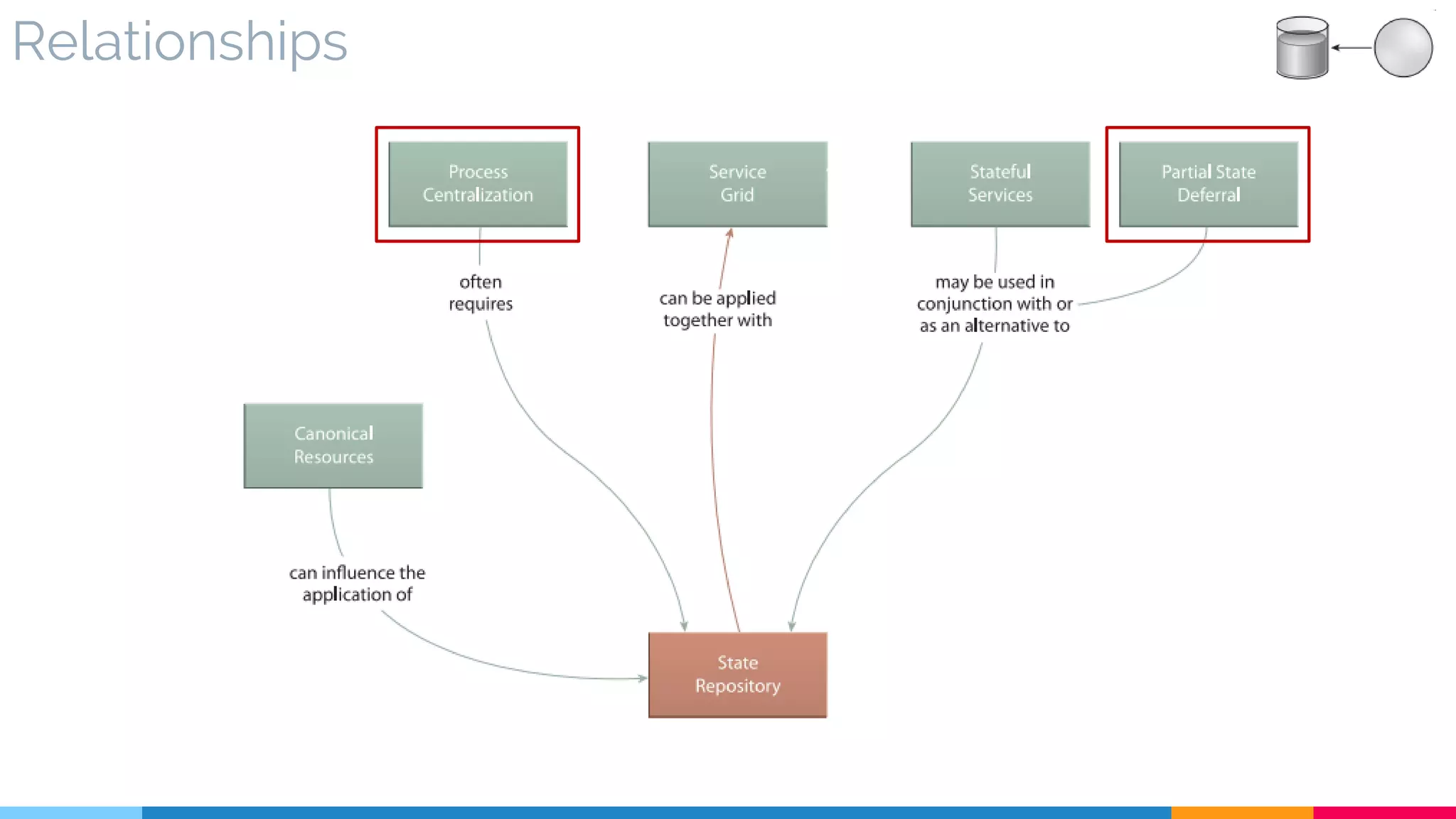
![29 State Repository
▷ Problem
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[242]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-233-2048.jpg)


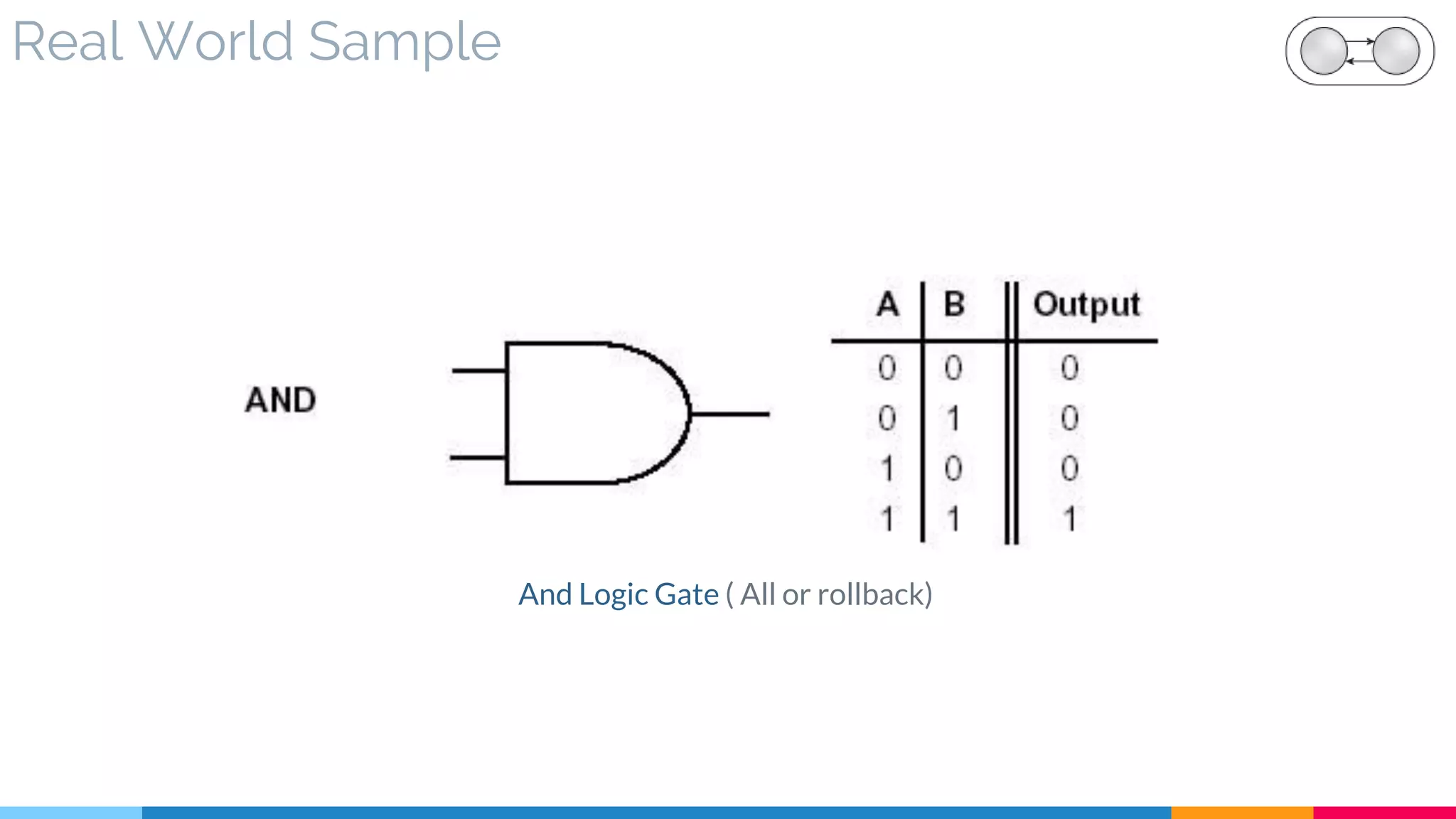
![30 Atomic Service Transaction
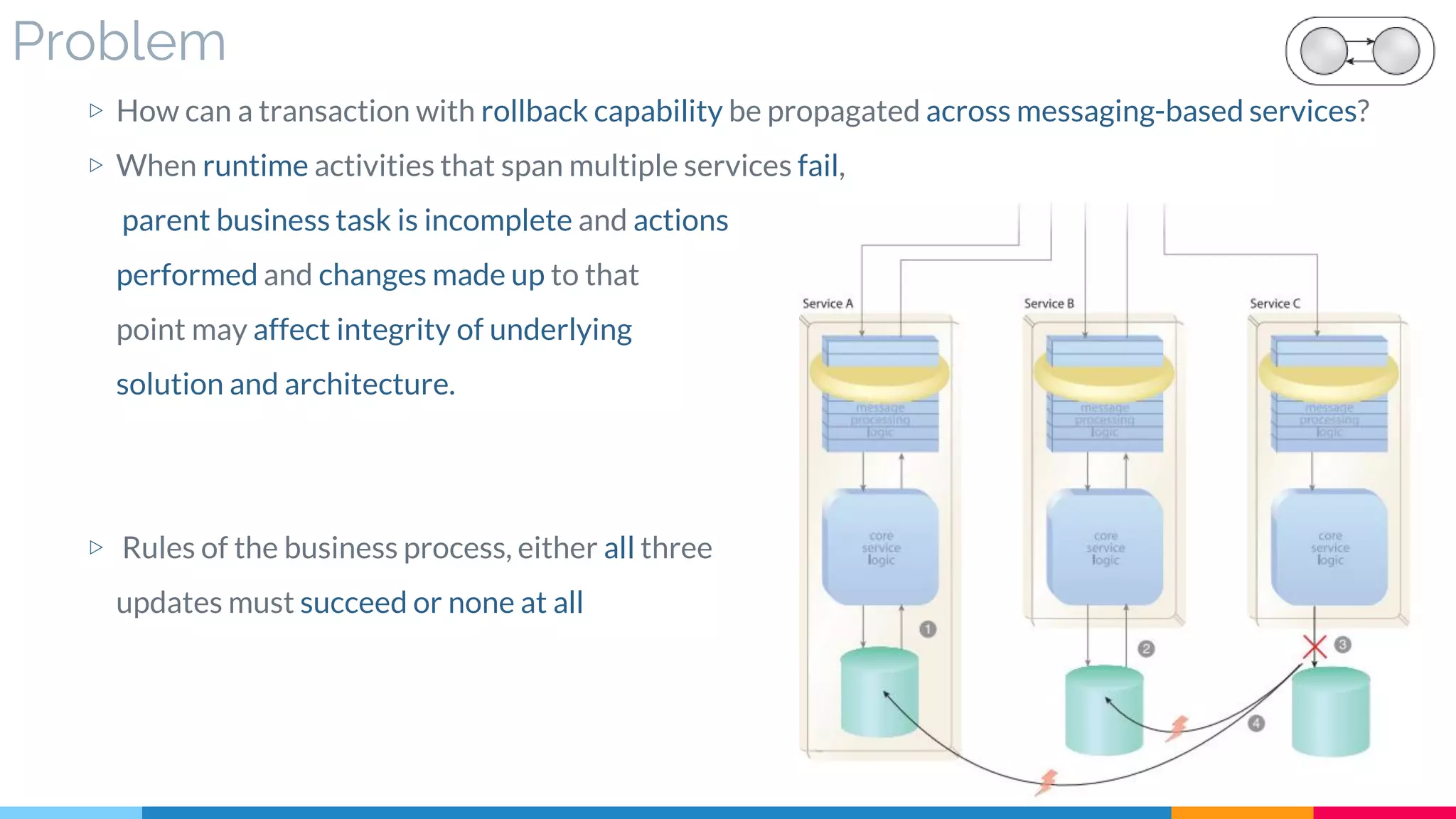
▷ Problem
▷ Solution
▷ Real World Sample
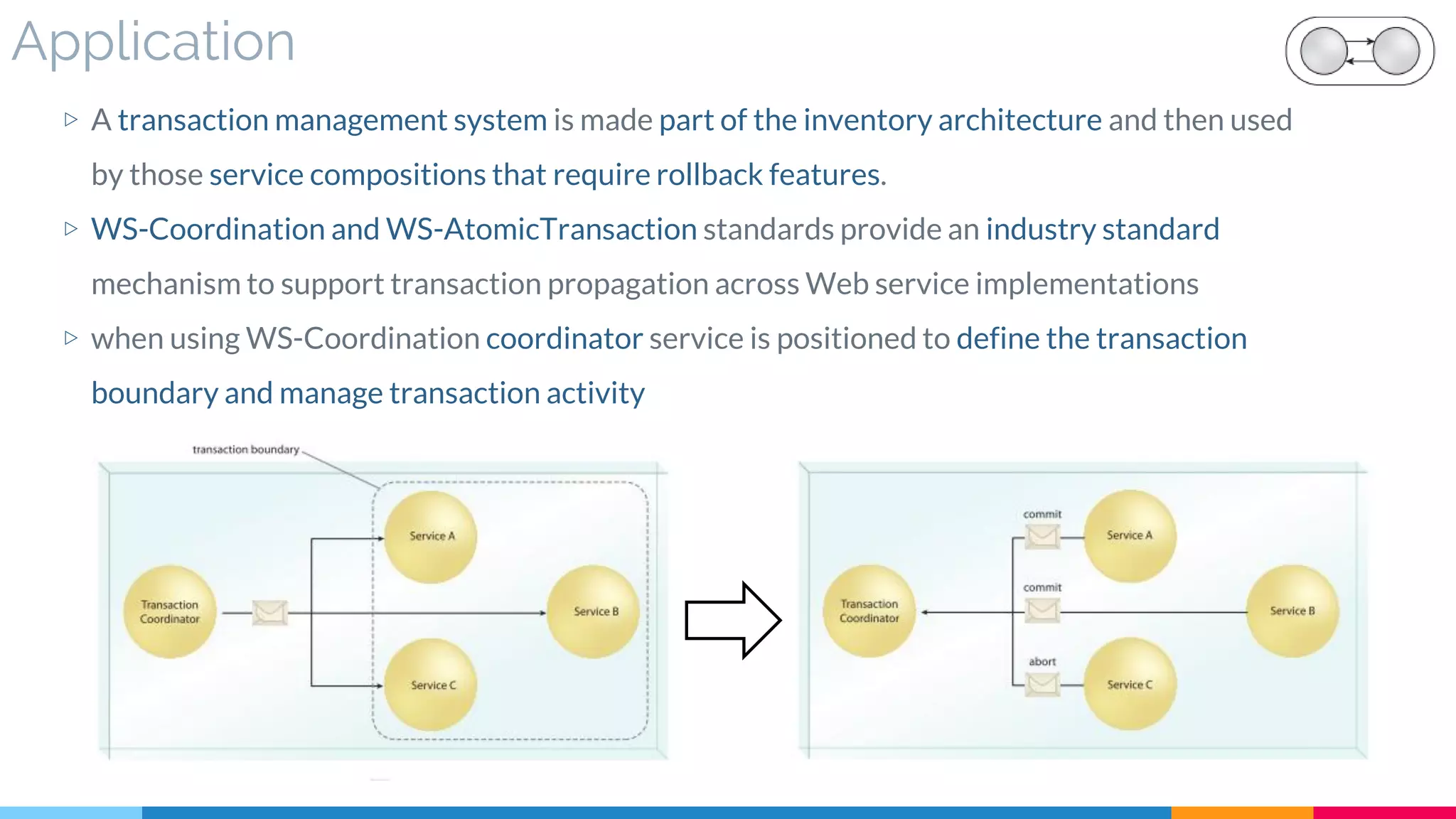
▷ Application
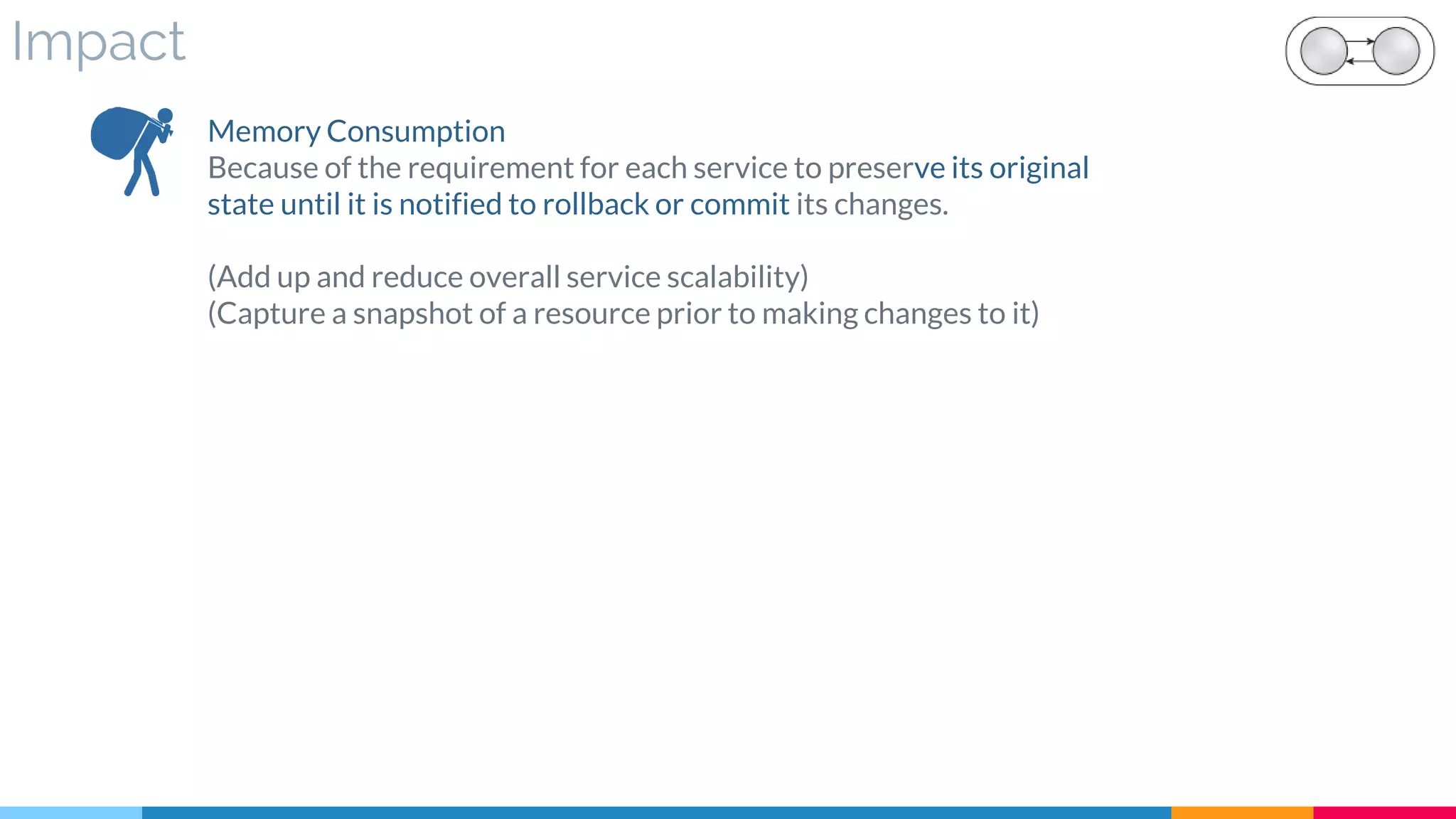
▷ Impact
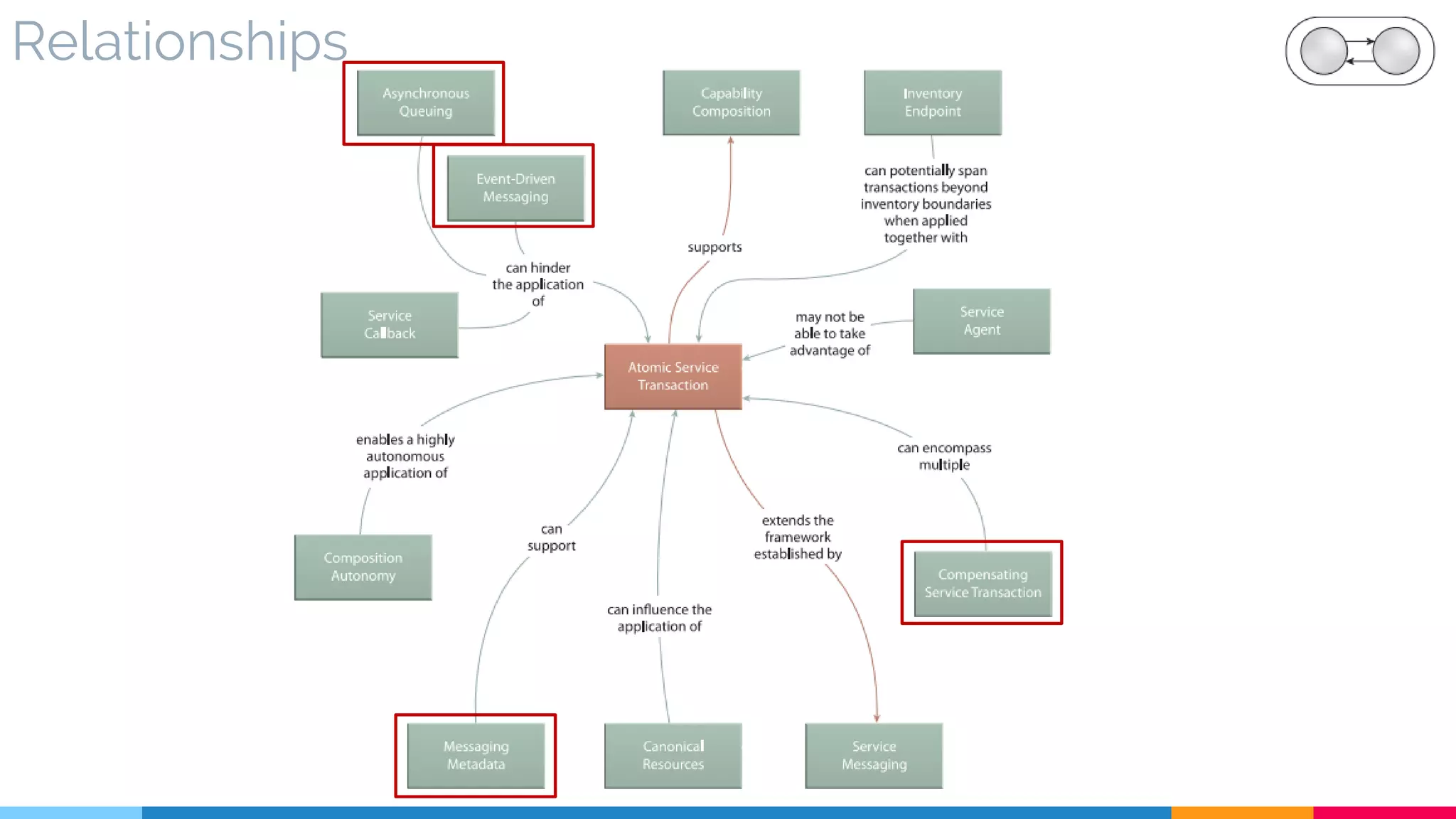
▷ Relationships
[623]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-242-2048.jpg)
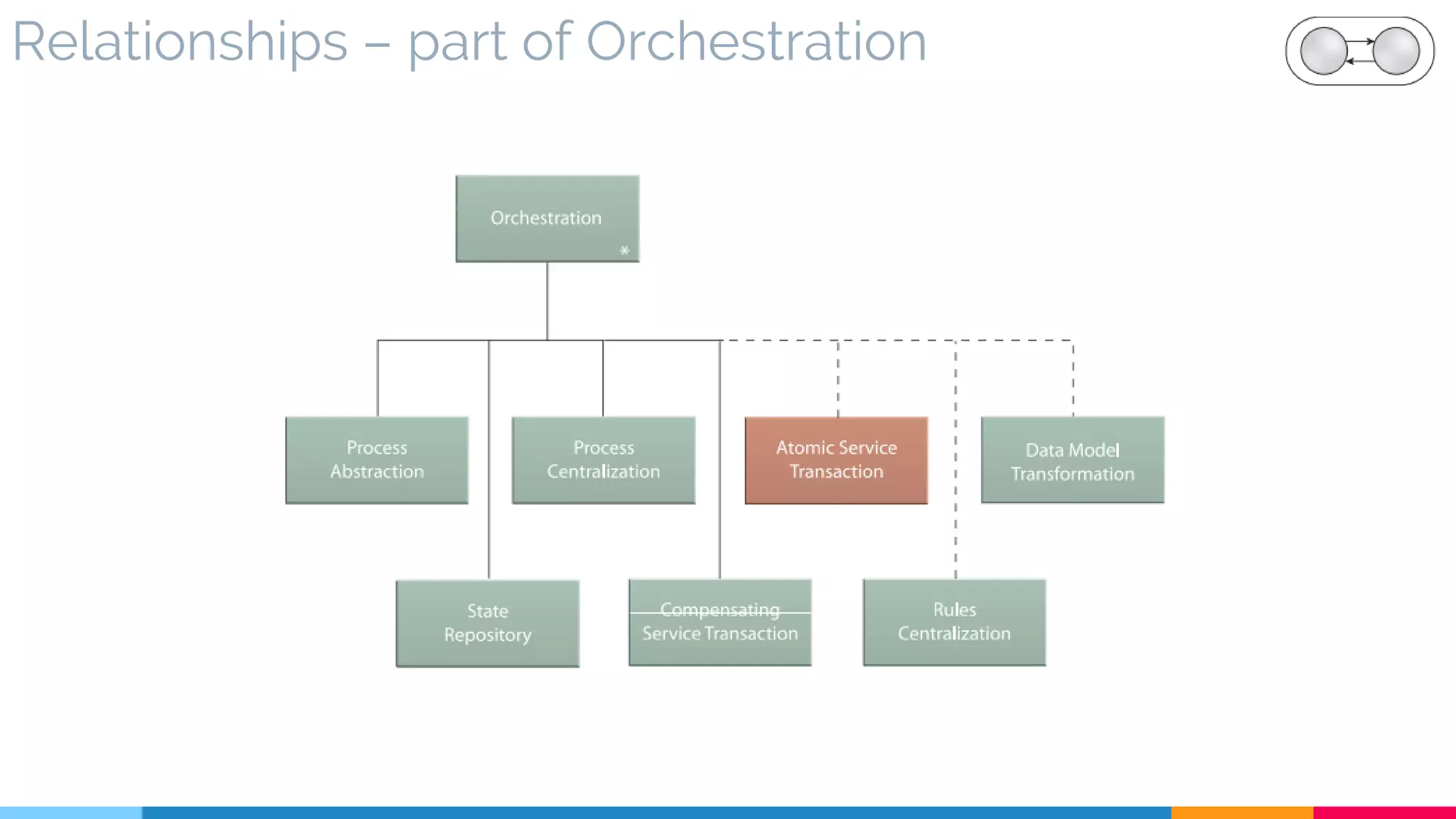
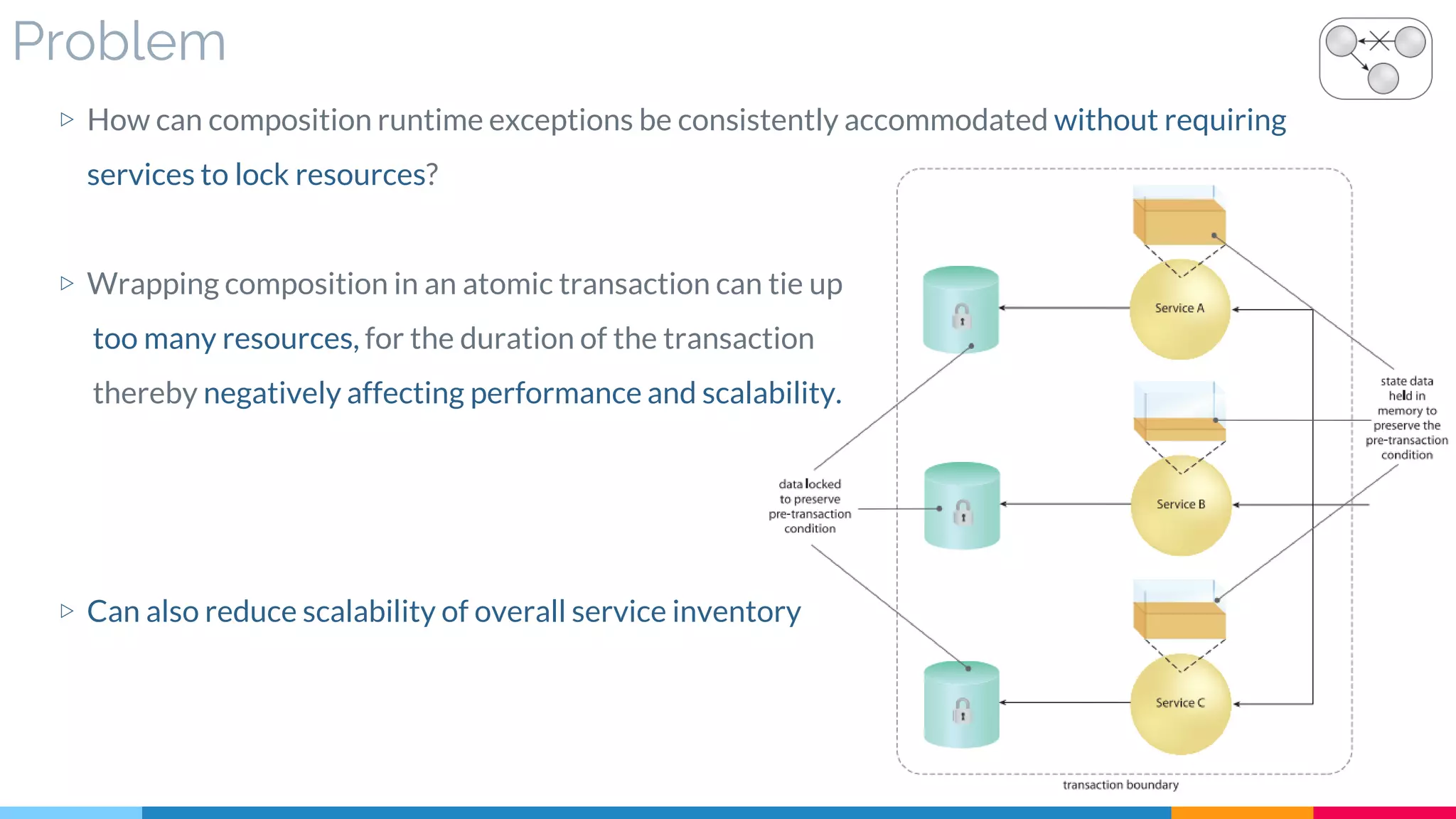
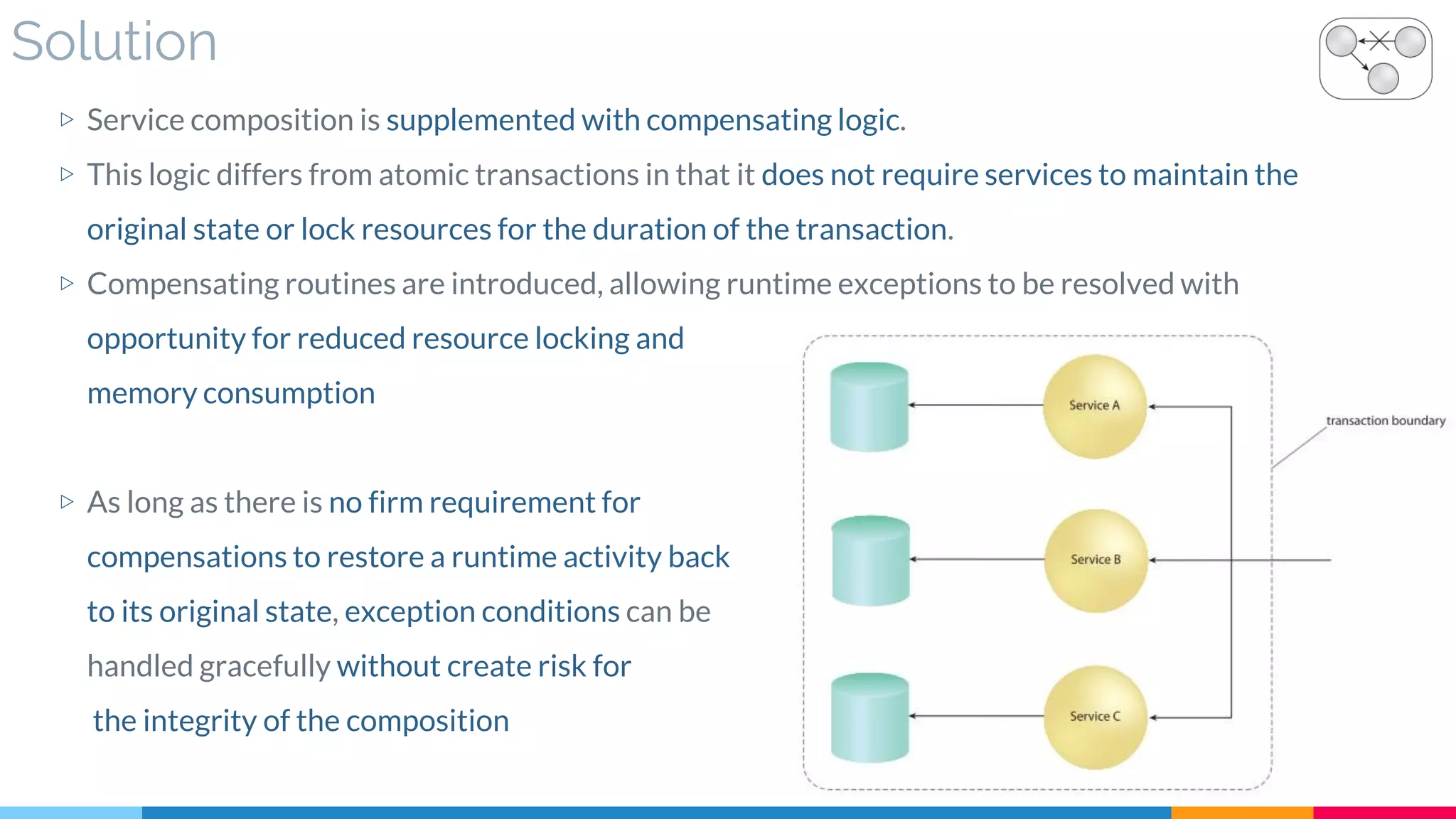
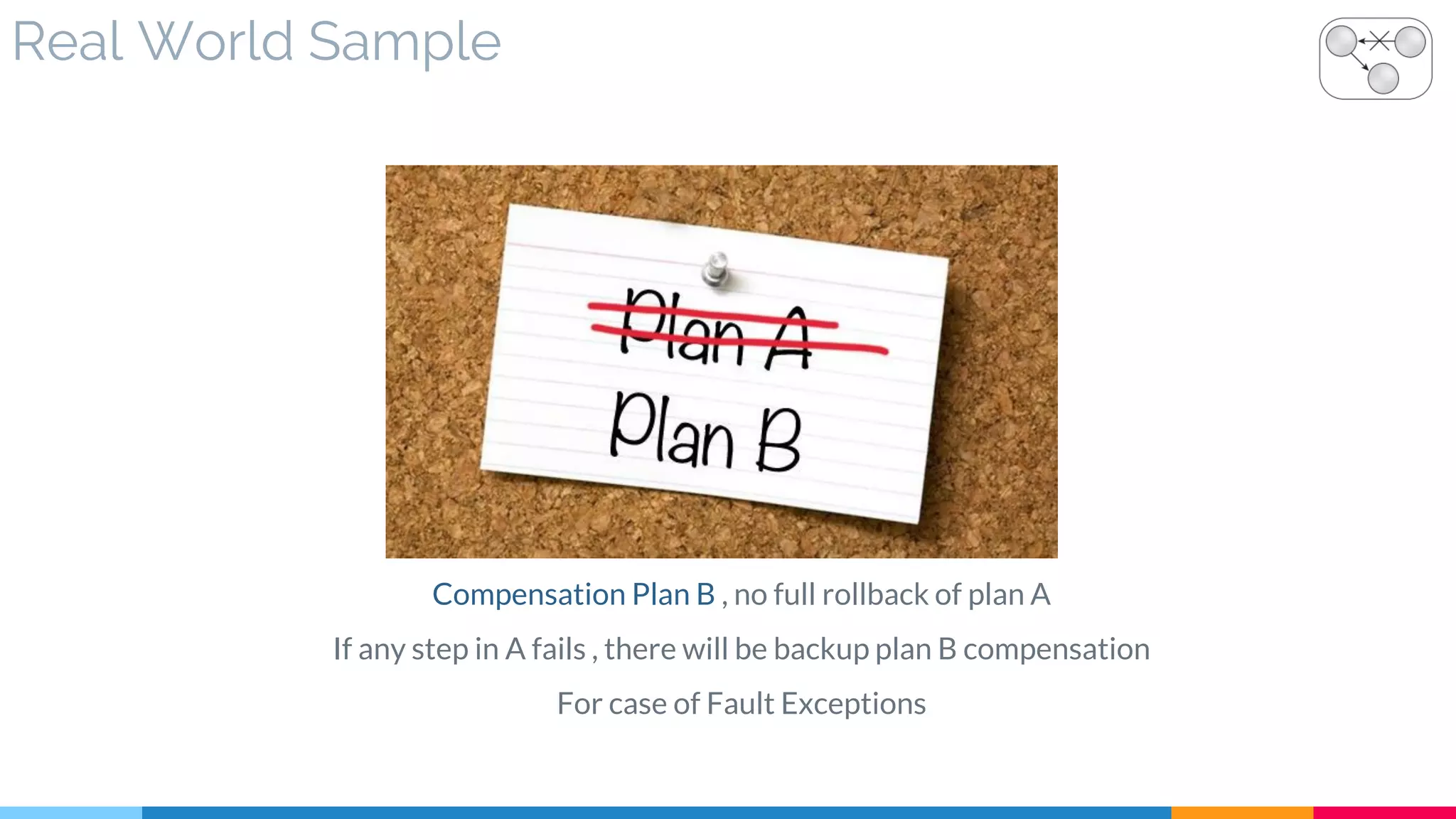
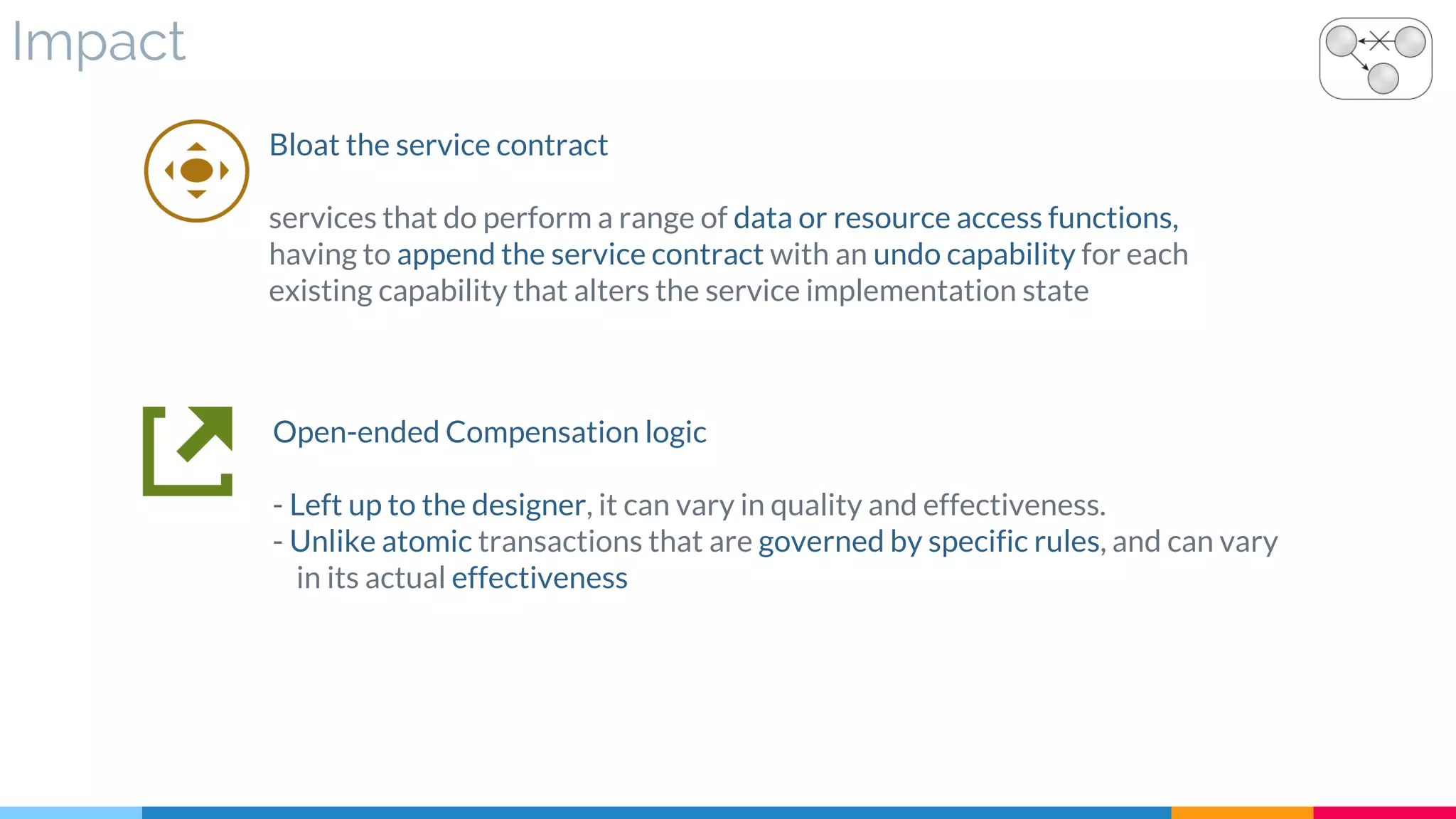
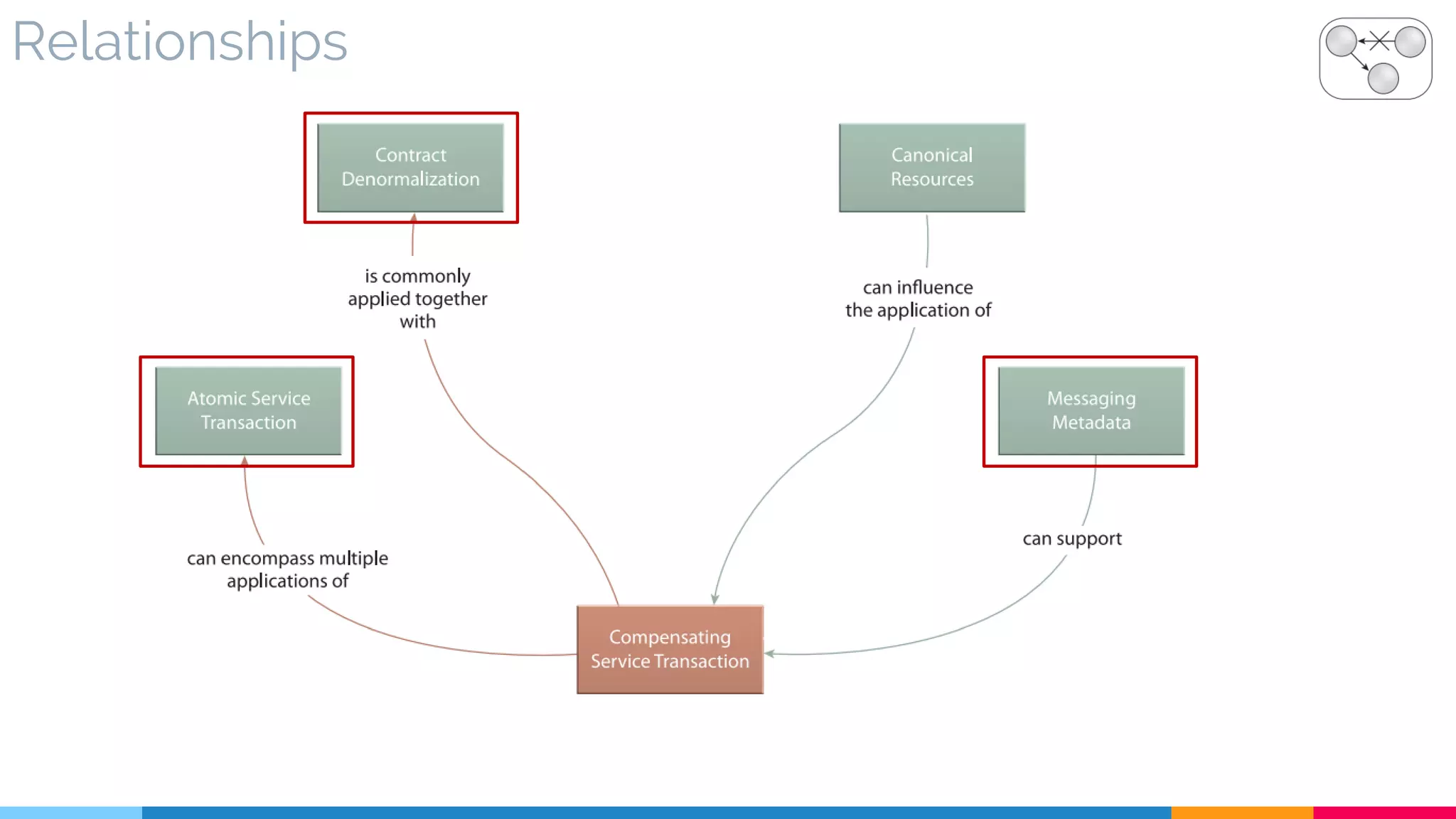
![31 Compensating Service Transaction
▷ Problem
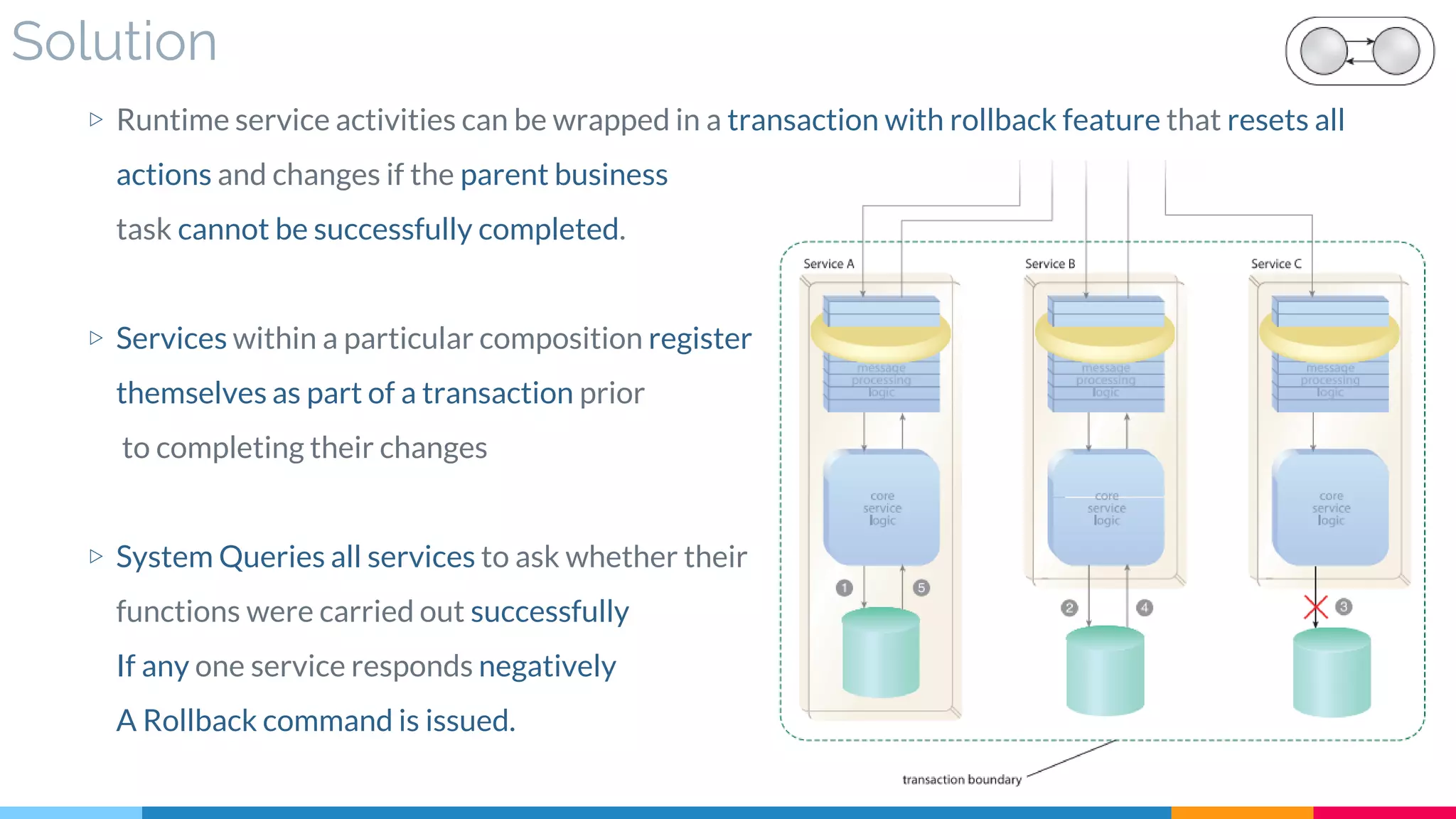
▷ Solution
▷ Real World Sample
▷ Application
▷ Impact
▷ Relationships
[631]](https://image.slidesharecdn.com/soadesignpatterns-180205103858/75/SOA-Design-Patterns-250-2048.jpg)