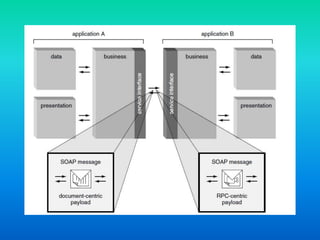
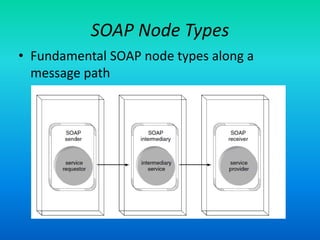
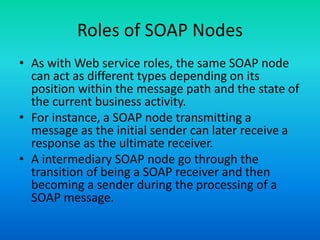
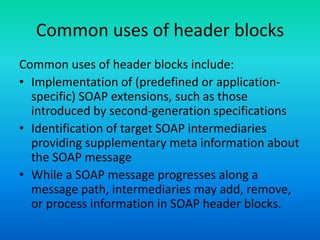
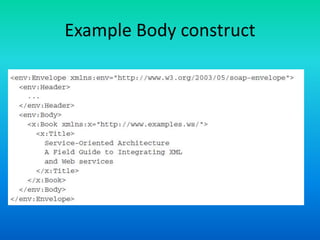
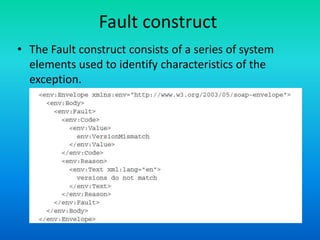
The document discusses the Simple Object Access Protocol (SOAP), detailing its role as a messaging format for XML web services and its evolution into a core component of service-oriented architecture. It explains the structure of SOAP messages, including the mandatory envelope, body, and optional header sections, as well as the roles of SOAP nodes in transmitting and processing messages. Additionally, it highlights common uses of SOAP header blocks and the handling of exceptions within the body construct.