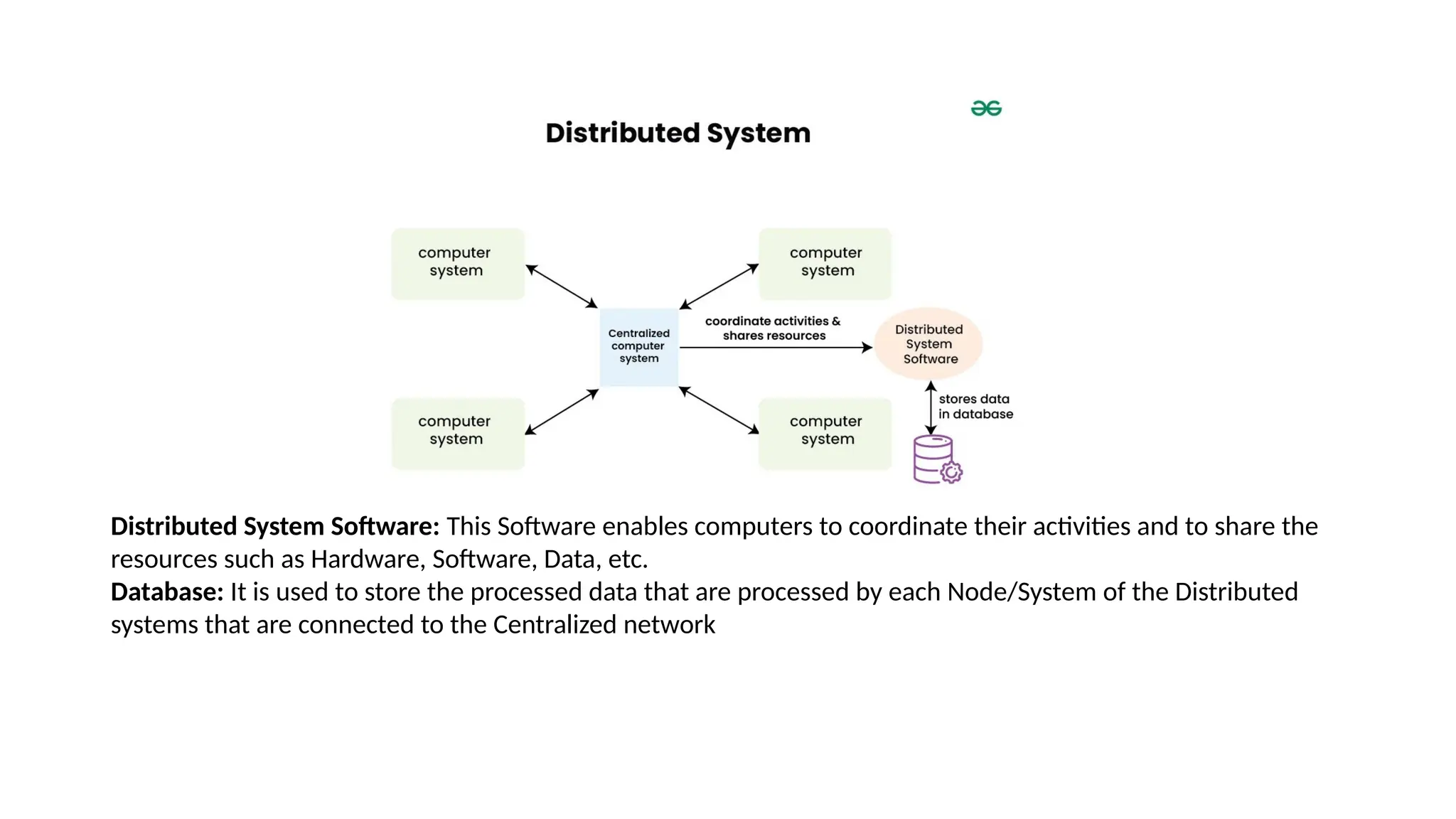
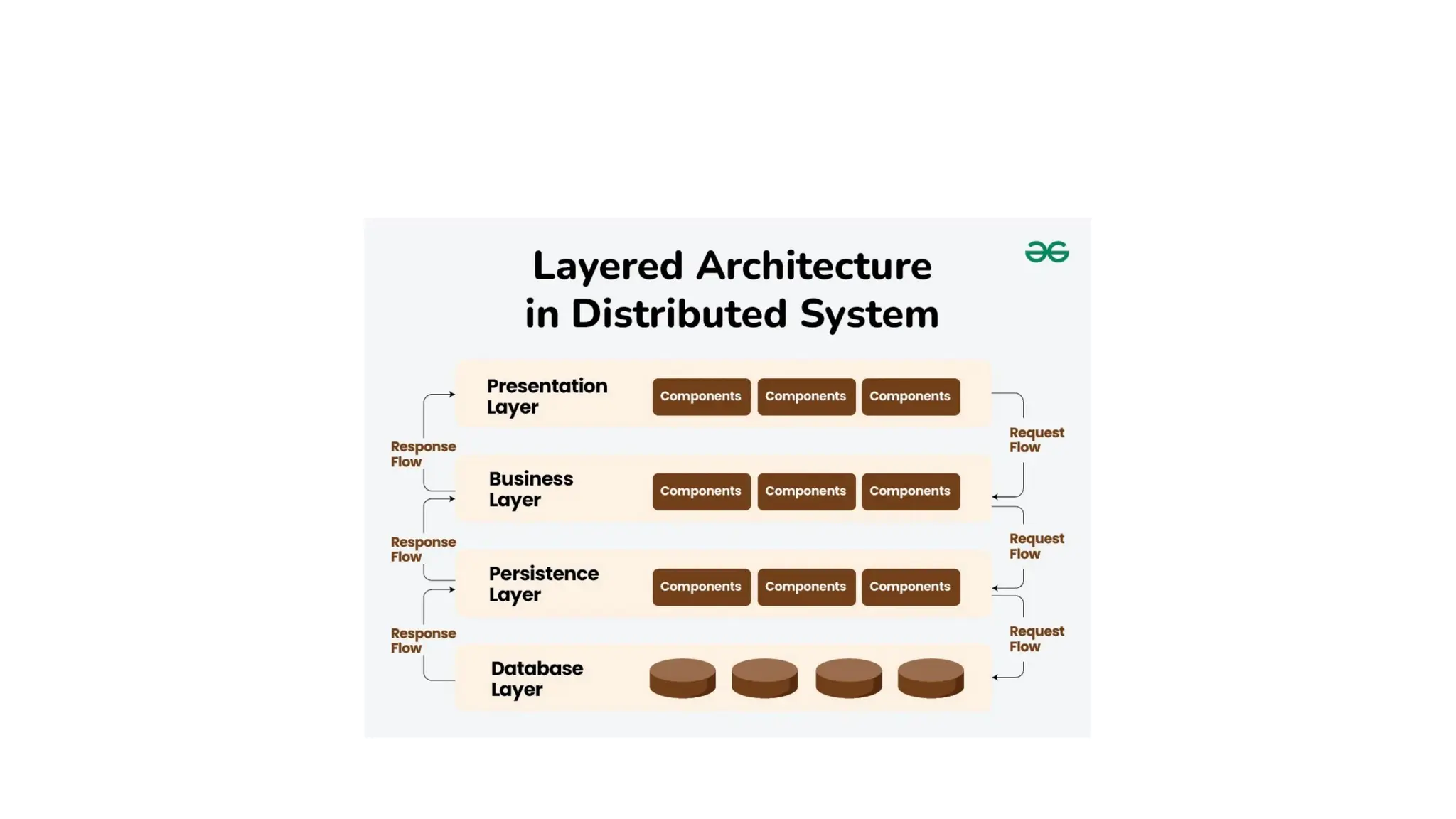
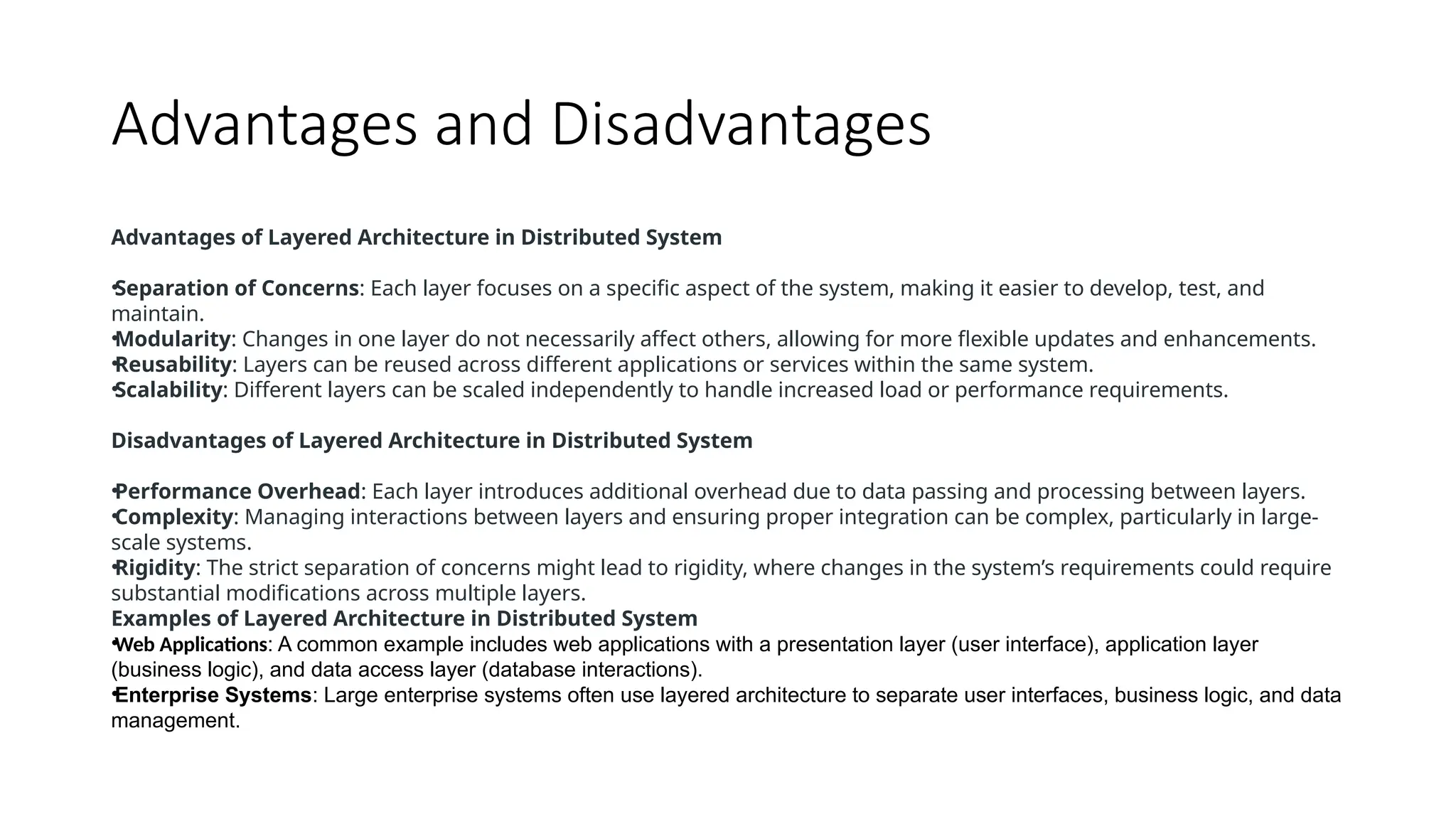
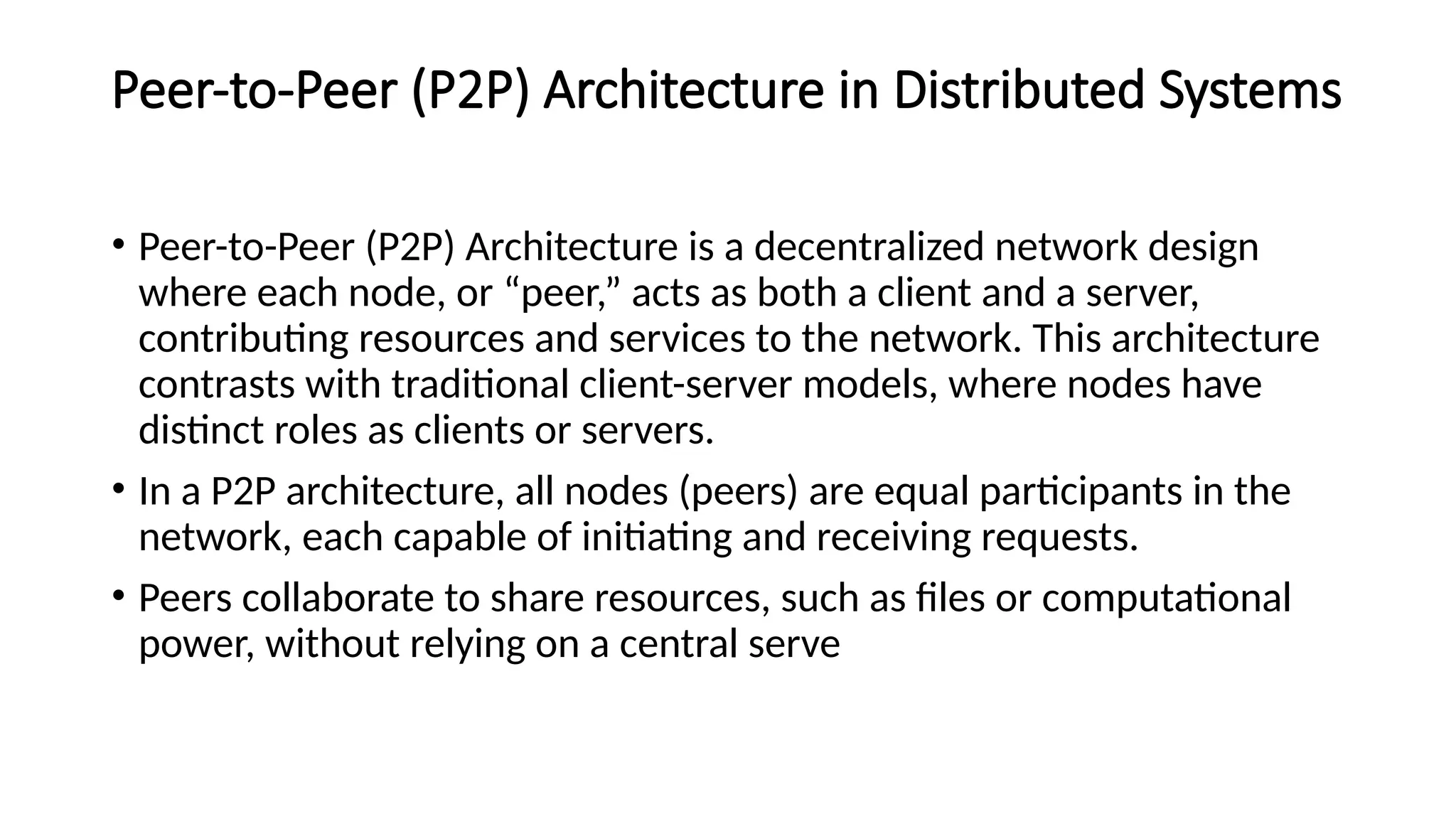
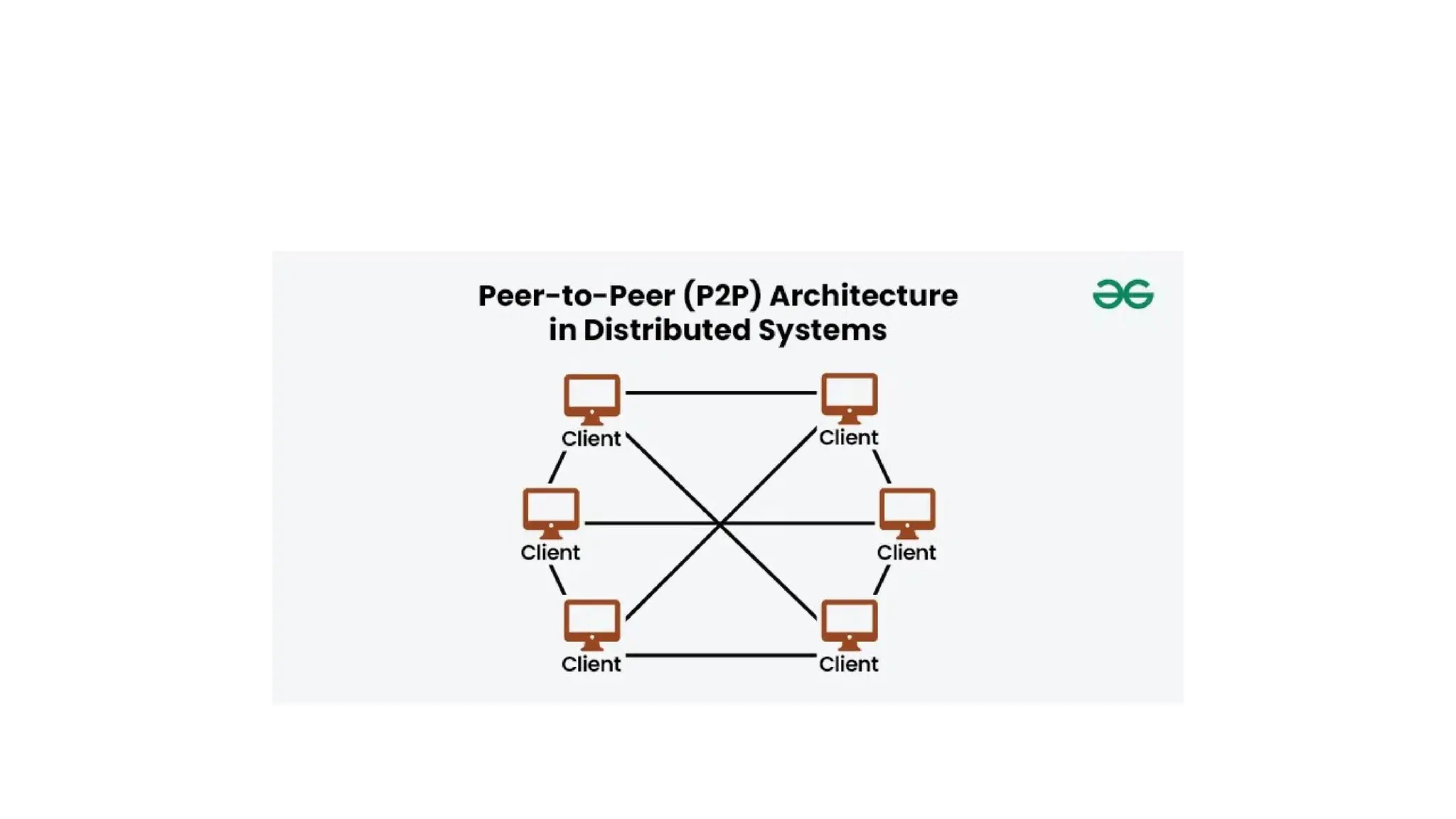
The document discusses the design issues and characteristics of distributed systems, highlighting aspects such as scalability, reliability, availability, consistency, and security. It explores various architectural styles including client-server, peer-to-peer, and microservices, along with communication issues and data management strategies within these systems. Additionally, it outlines the advantages and disadvantages of distributed systems and their software components, emphasizing the need for effective resource sharing and fault tolerance.