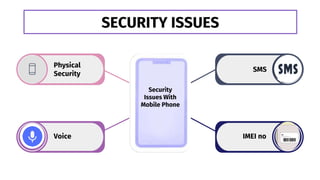
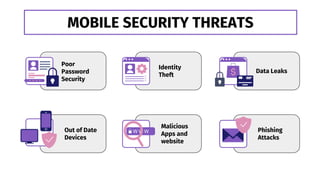
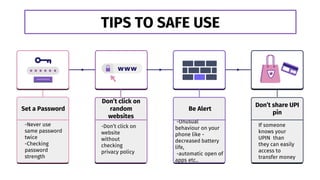
This document provides information about mobile security. It discusses introduction to mobile security, security issues, types of mobile threats including application, web and network based threats. It also discusses physical threats to mobile devices. The document lists tips for safe mobile use including setting passwords, not sharing UPI pins, being alert for unusual phone behavior, and not clicking random websites. It concludes by emphasizing the importance of mobile security awareness and training given the increasing cyber threats and sharing knowledge can help ensure safer mobile use.