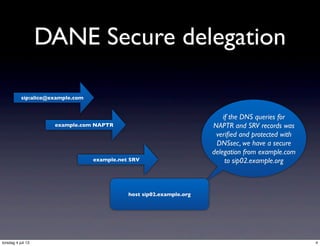
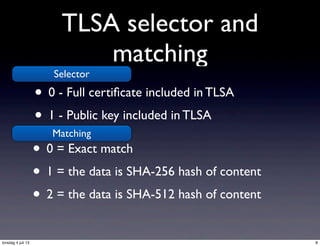
This document discusses the setup of SIP and DNS-based TLS using DANE, covering key concepts such as secure delegation, TLSA records, and certificate validation. It emphasizes the importance of DNSSEC for secure delegation and outlines fallback logic for SRV servers and compatibility with non-SRV clients. Various TLSA record usages and matching rules are detailed to ensure proper certificate verification and secure connections.