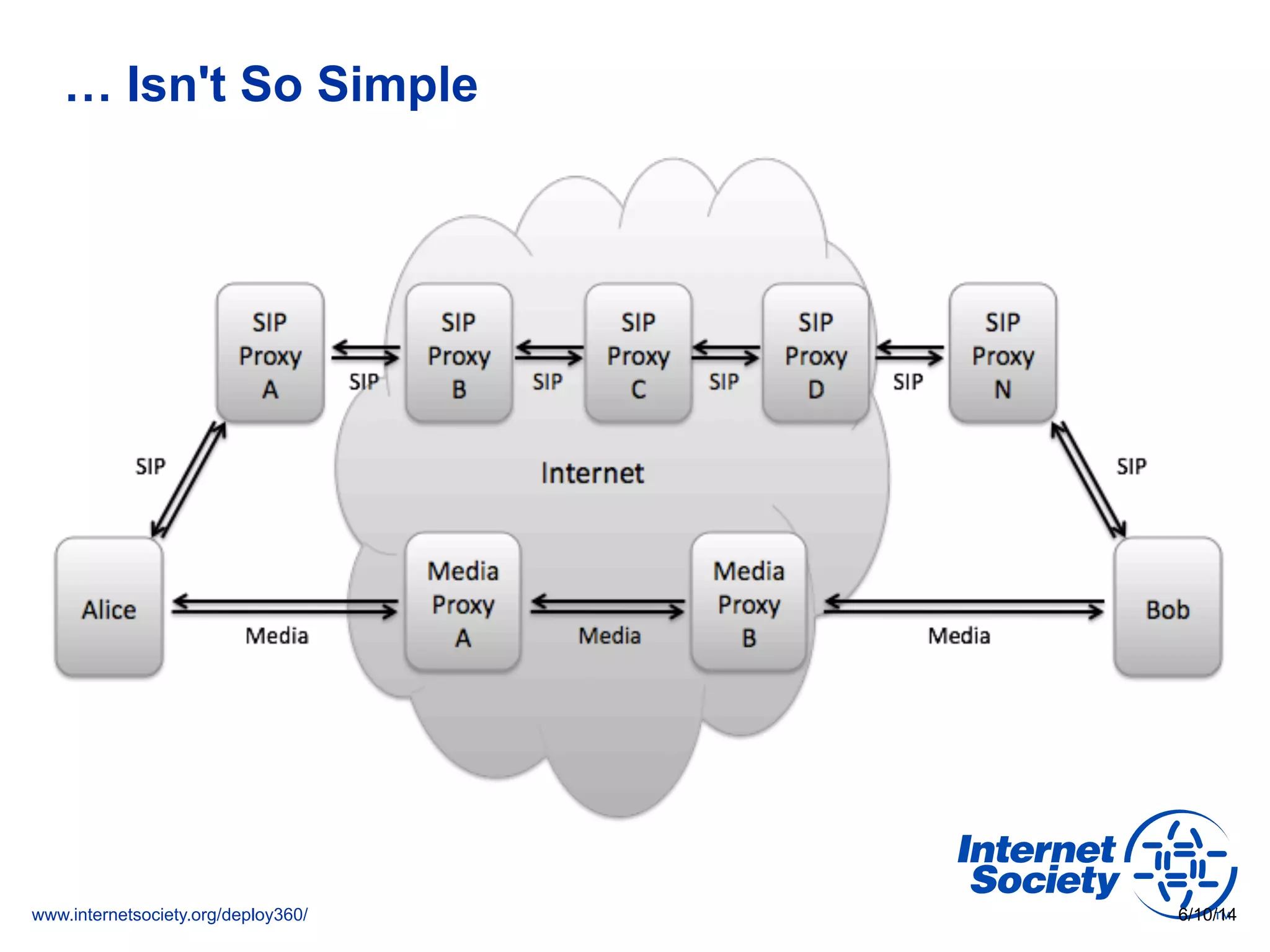
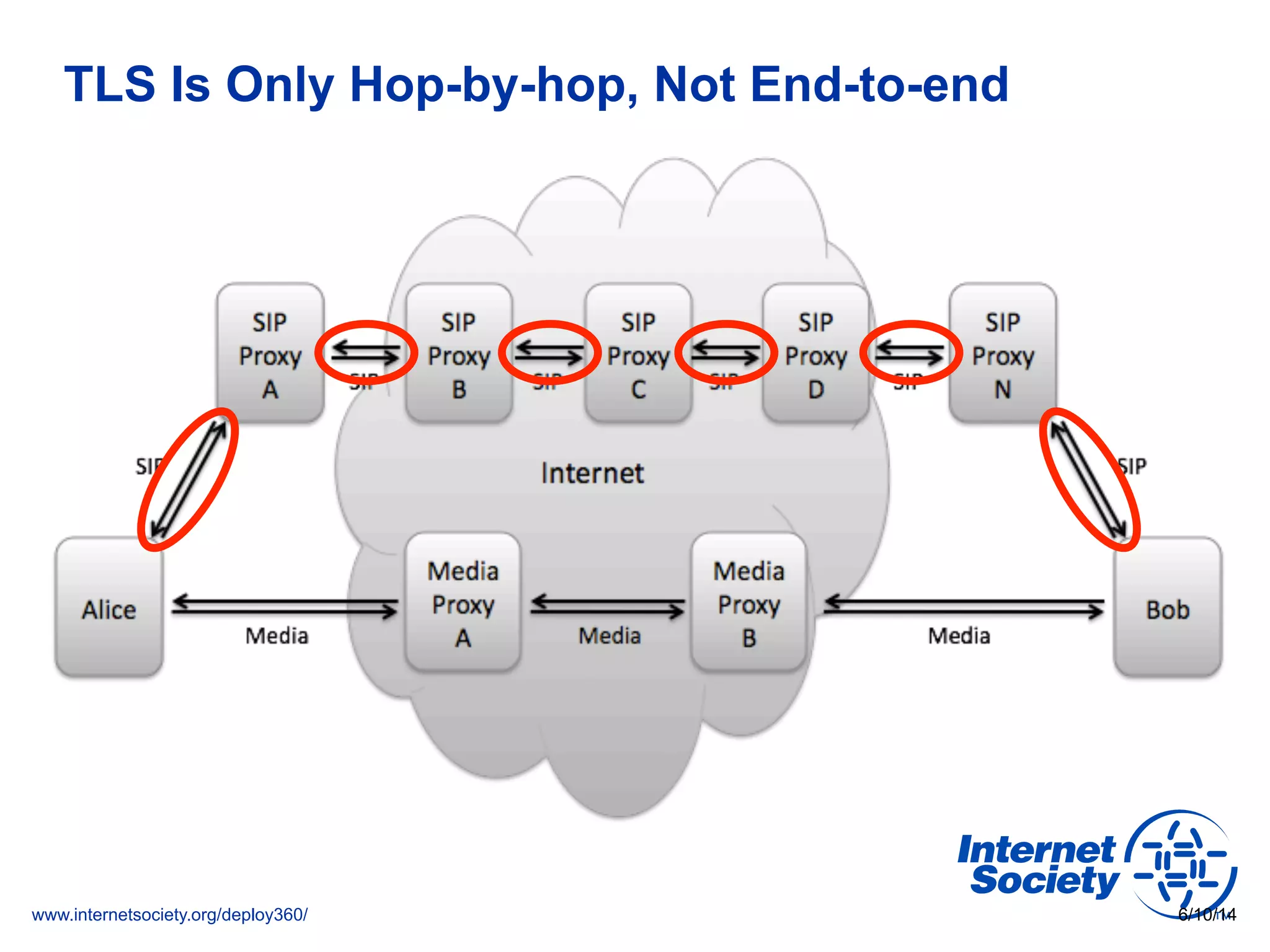
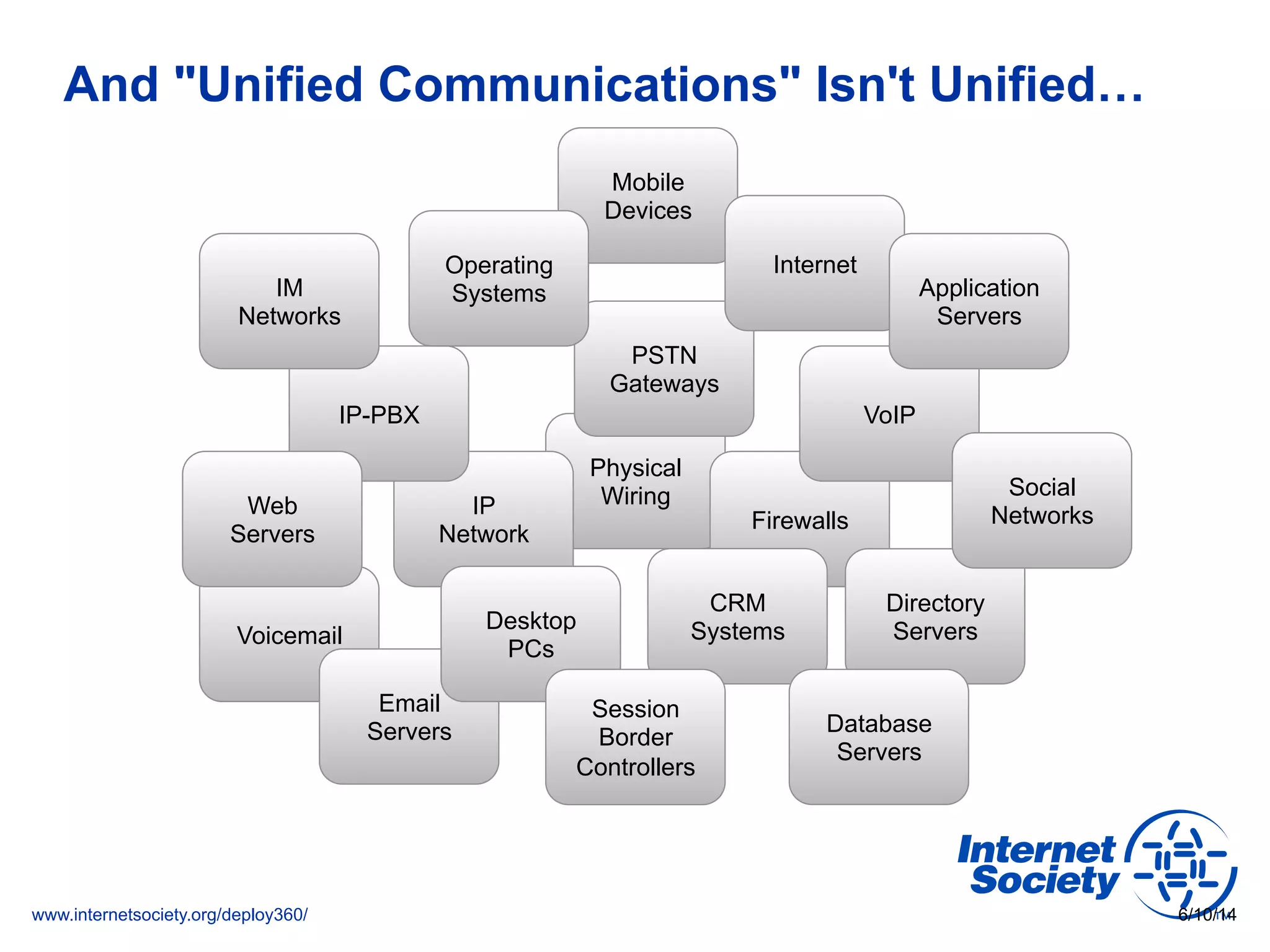
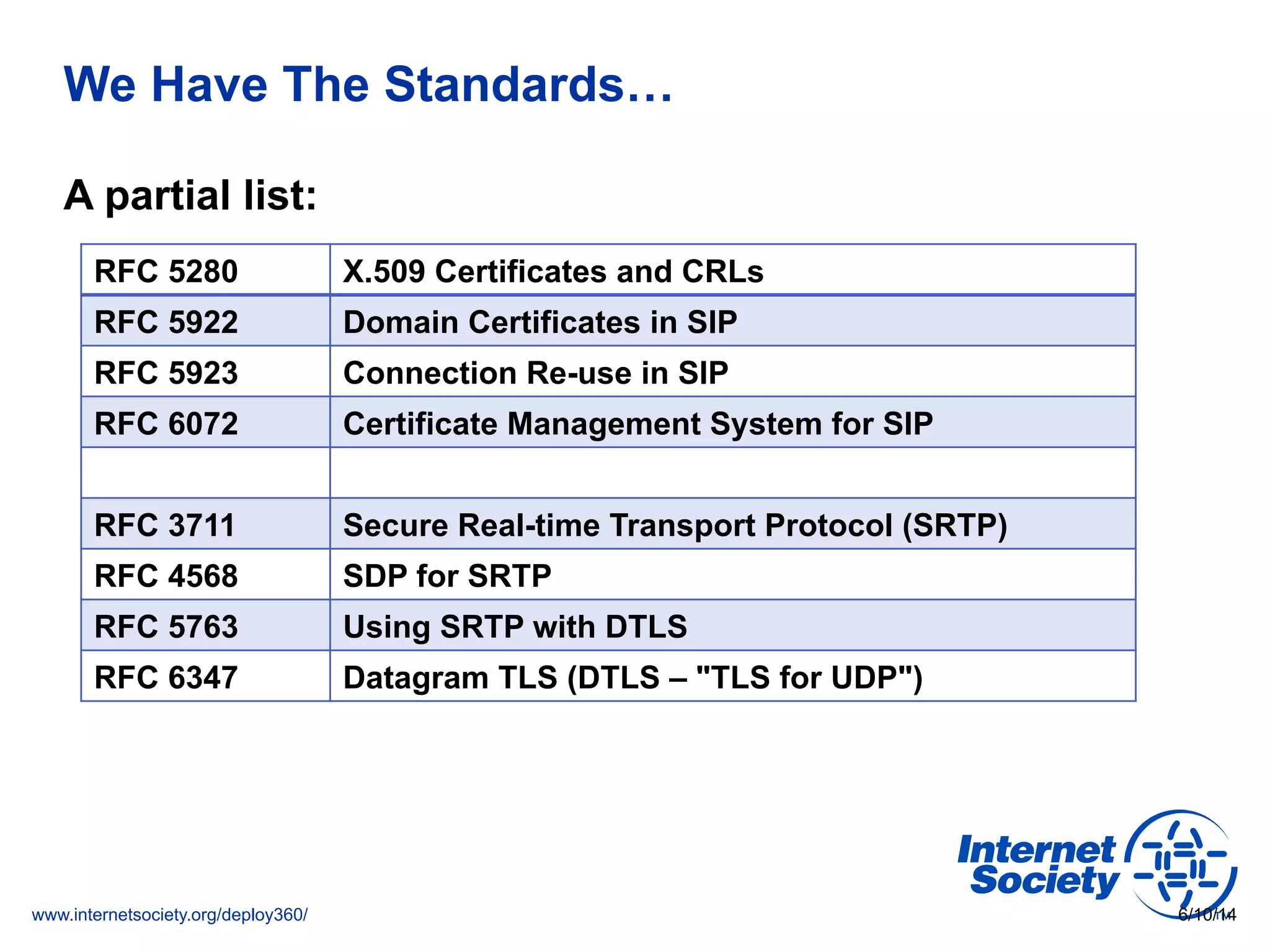
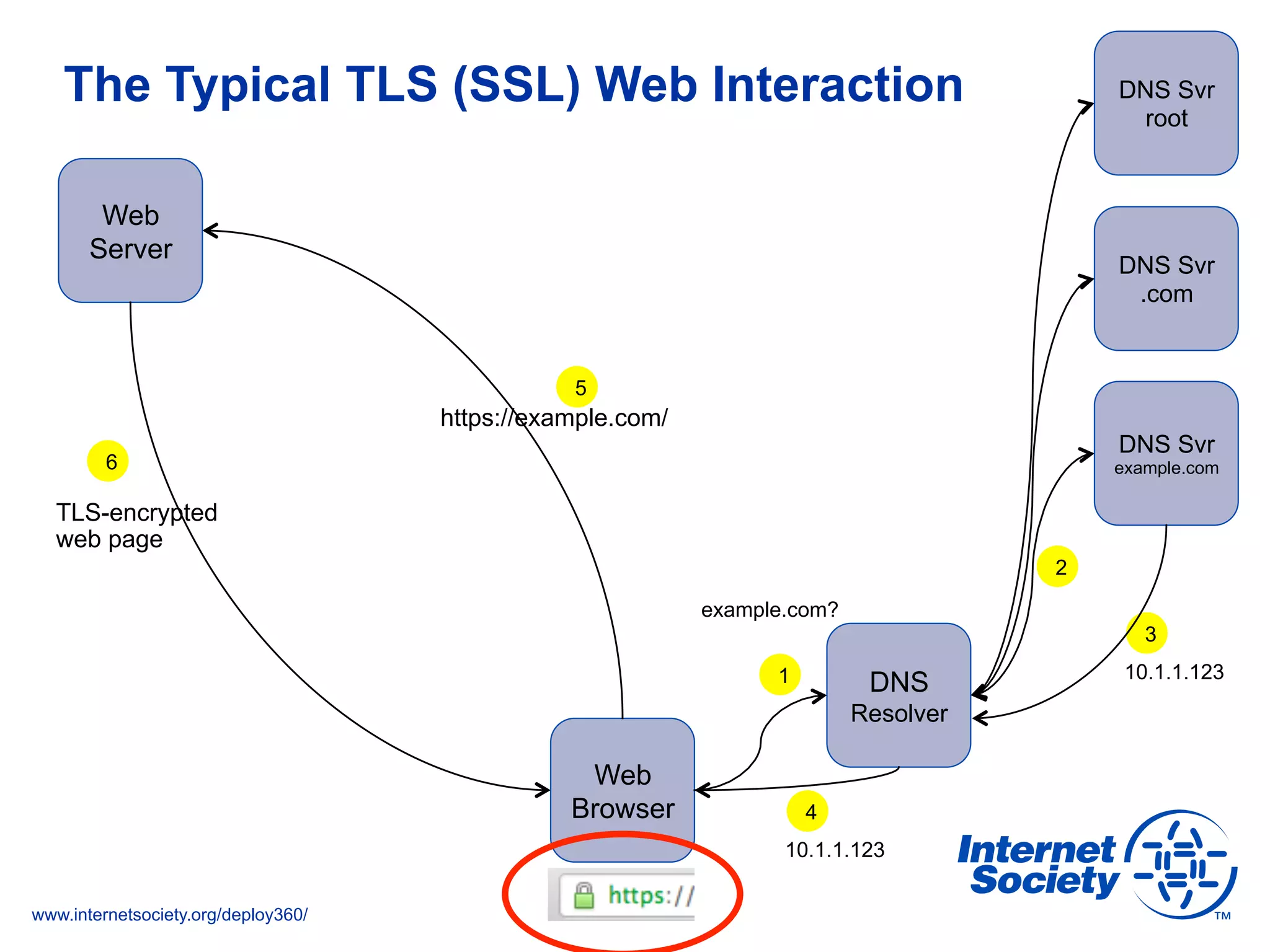
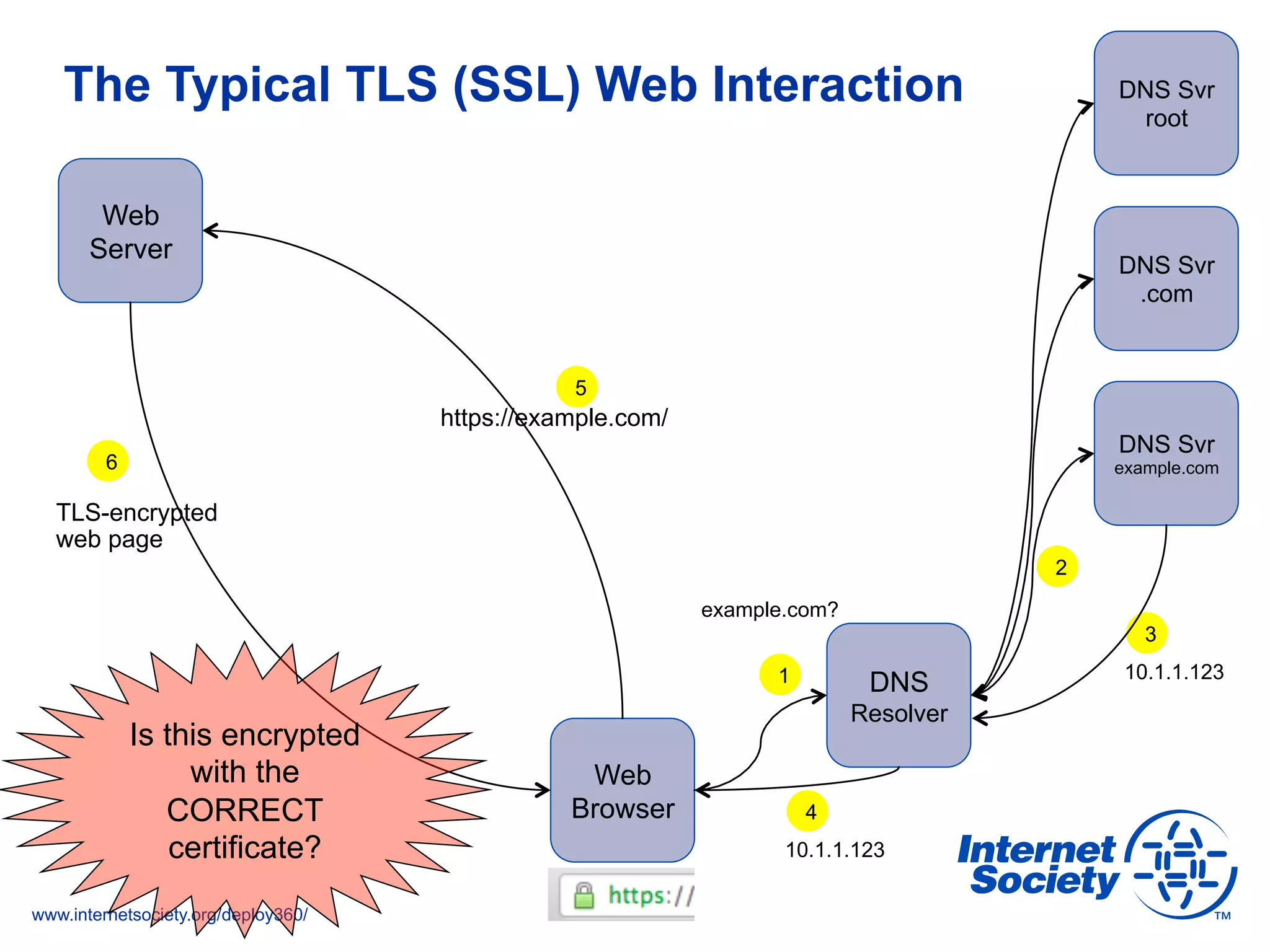
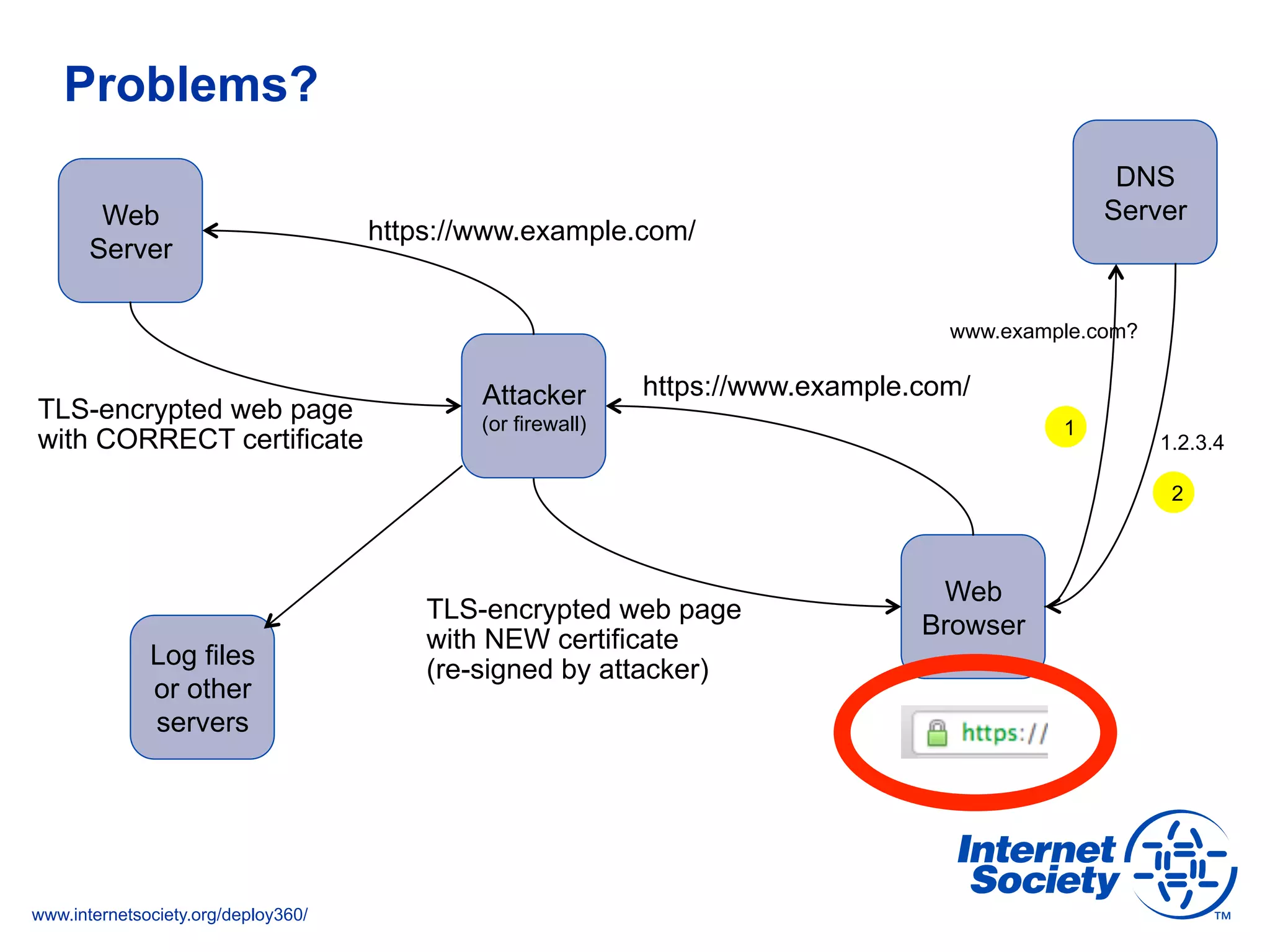
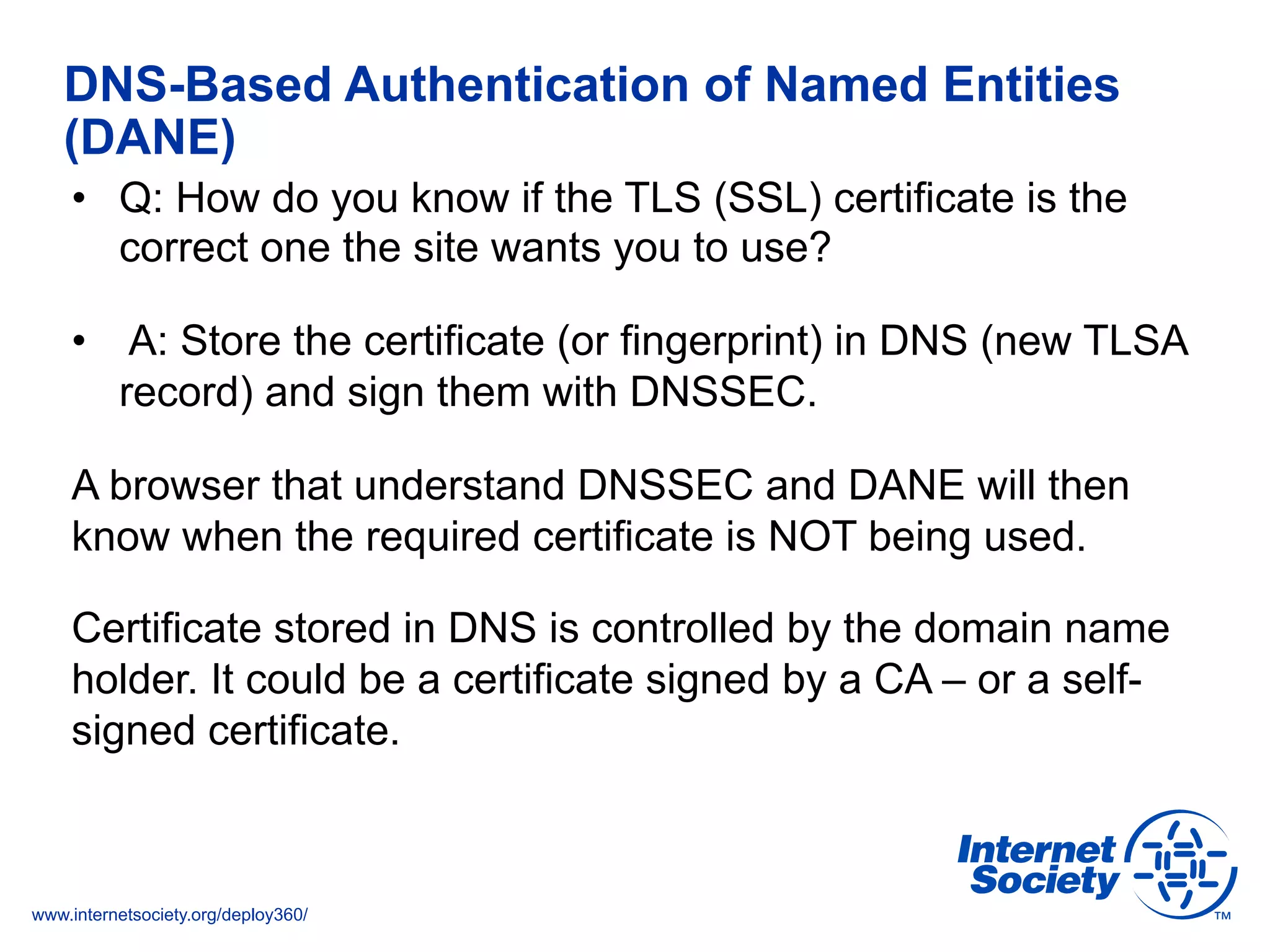
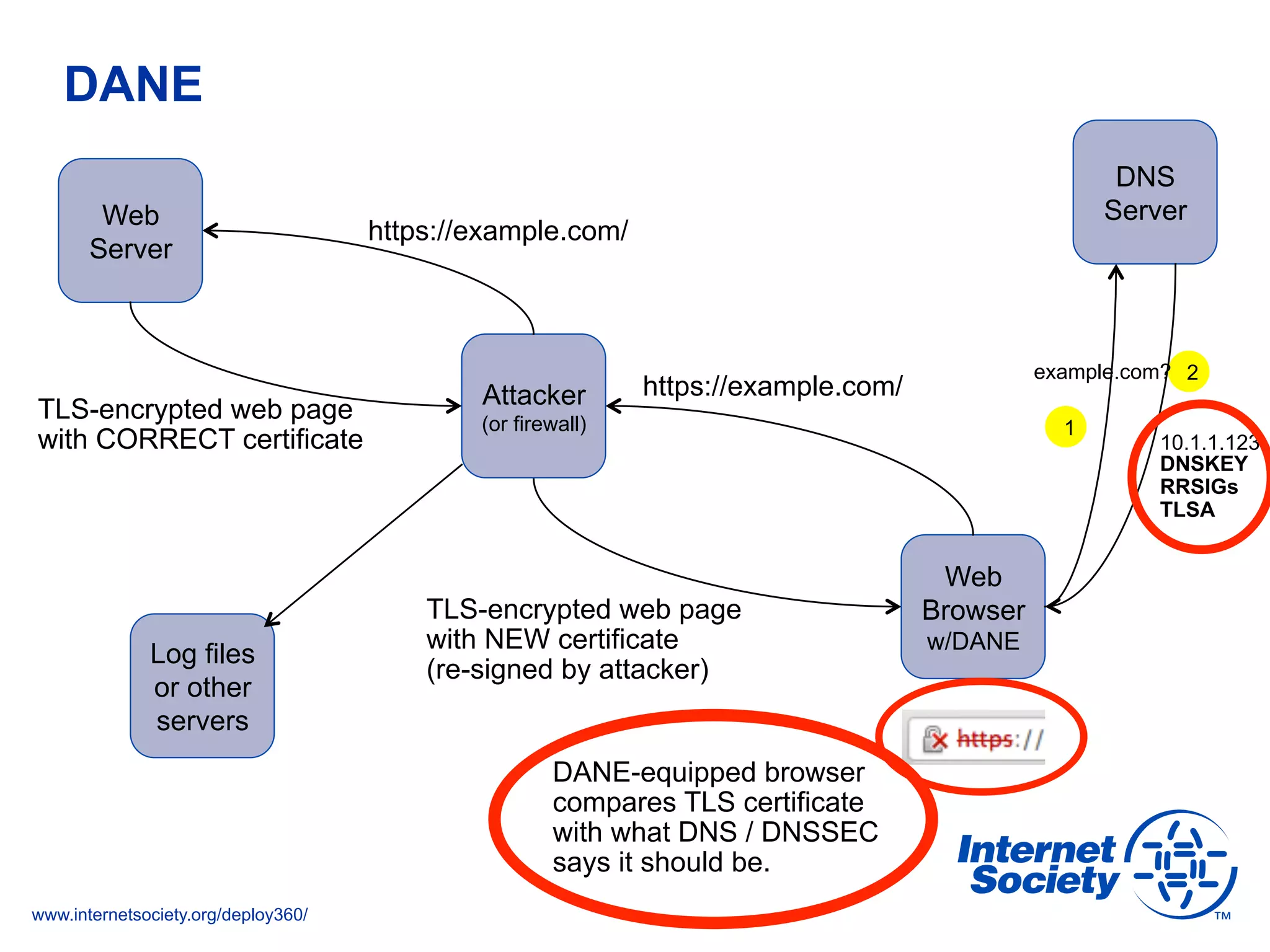
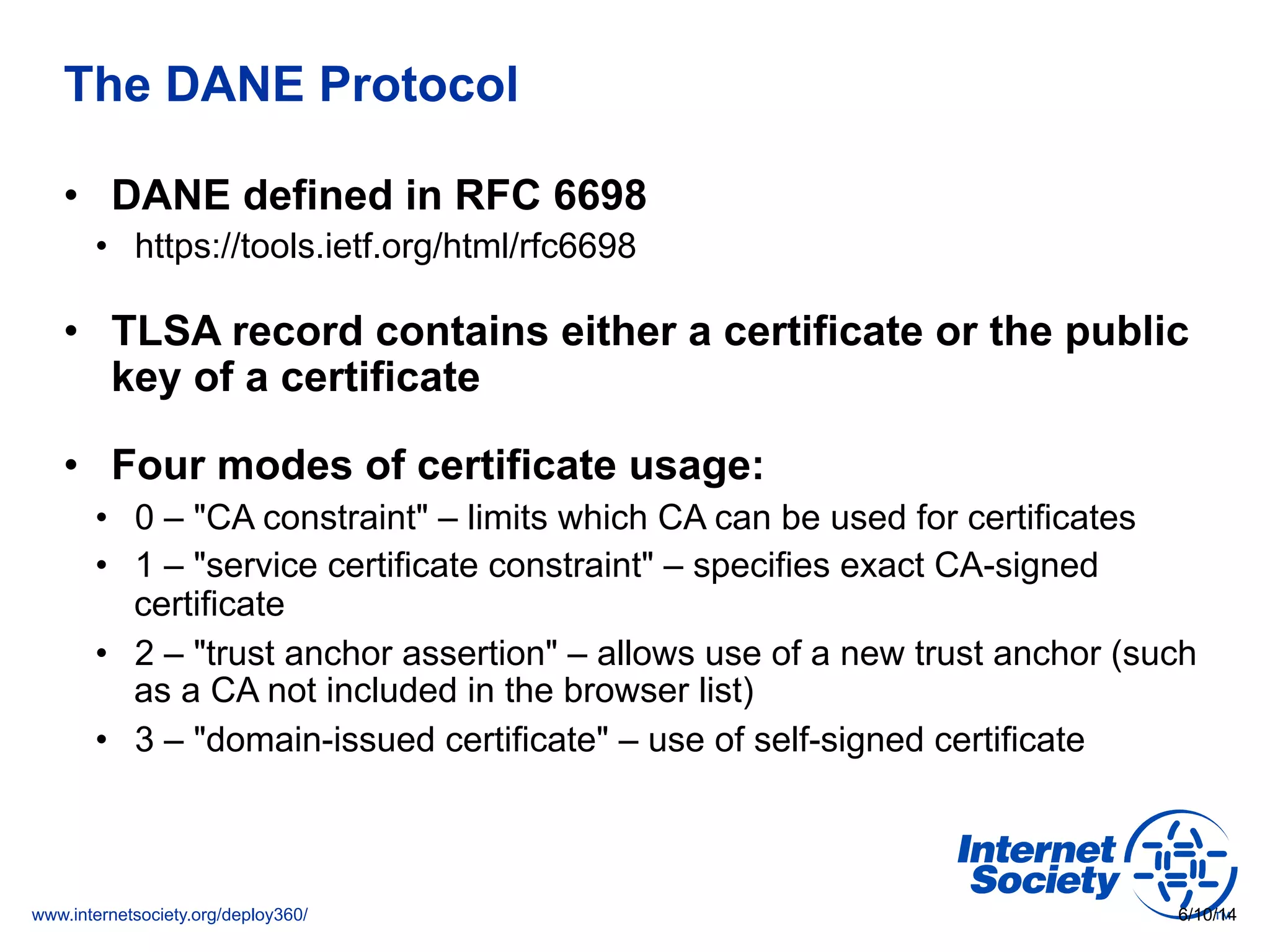
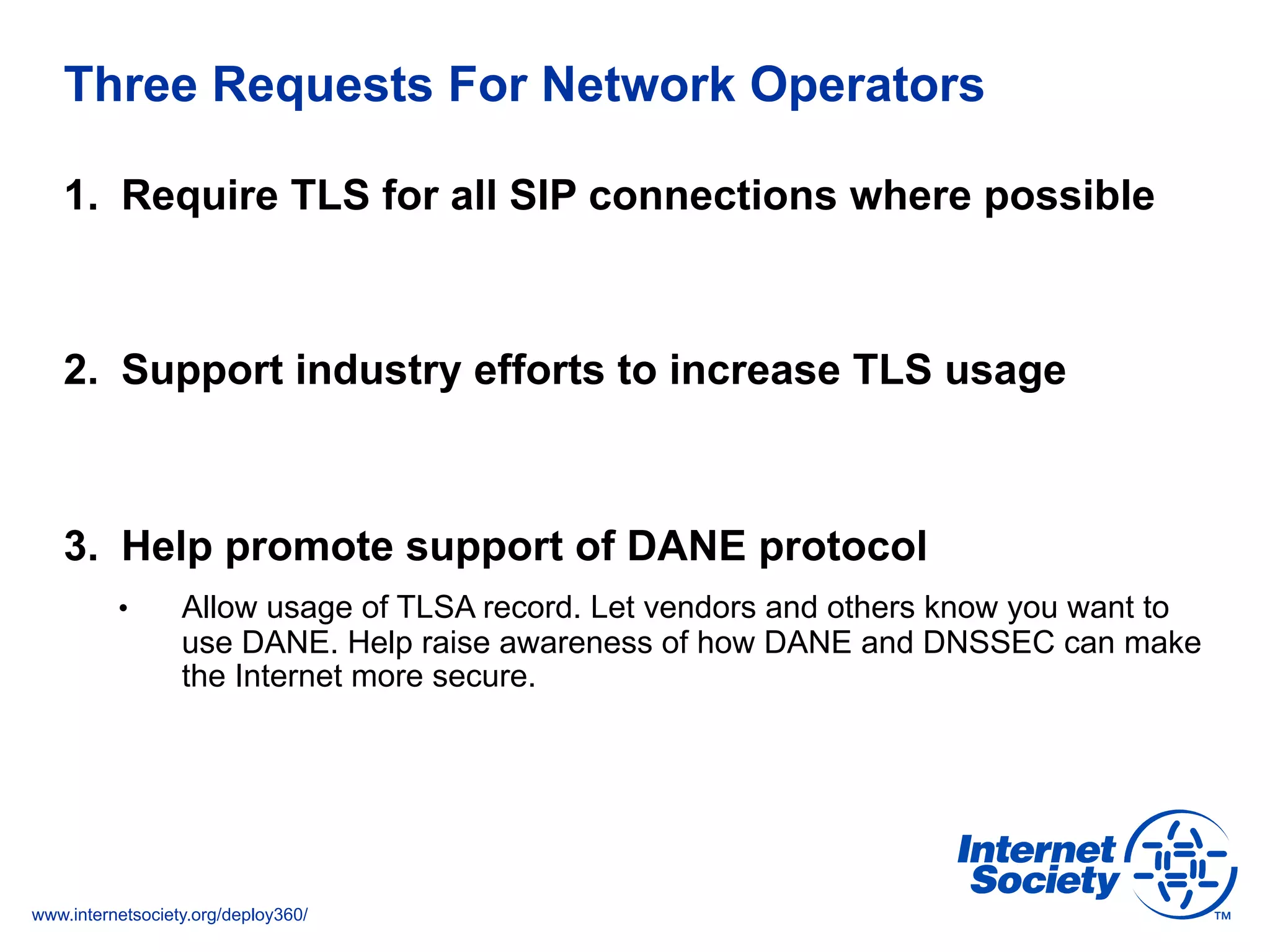
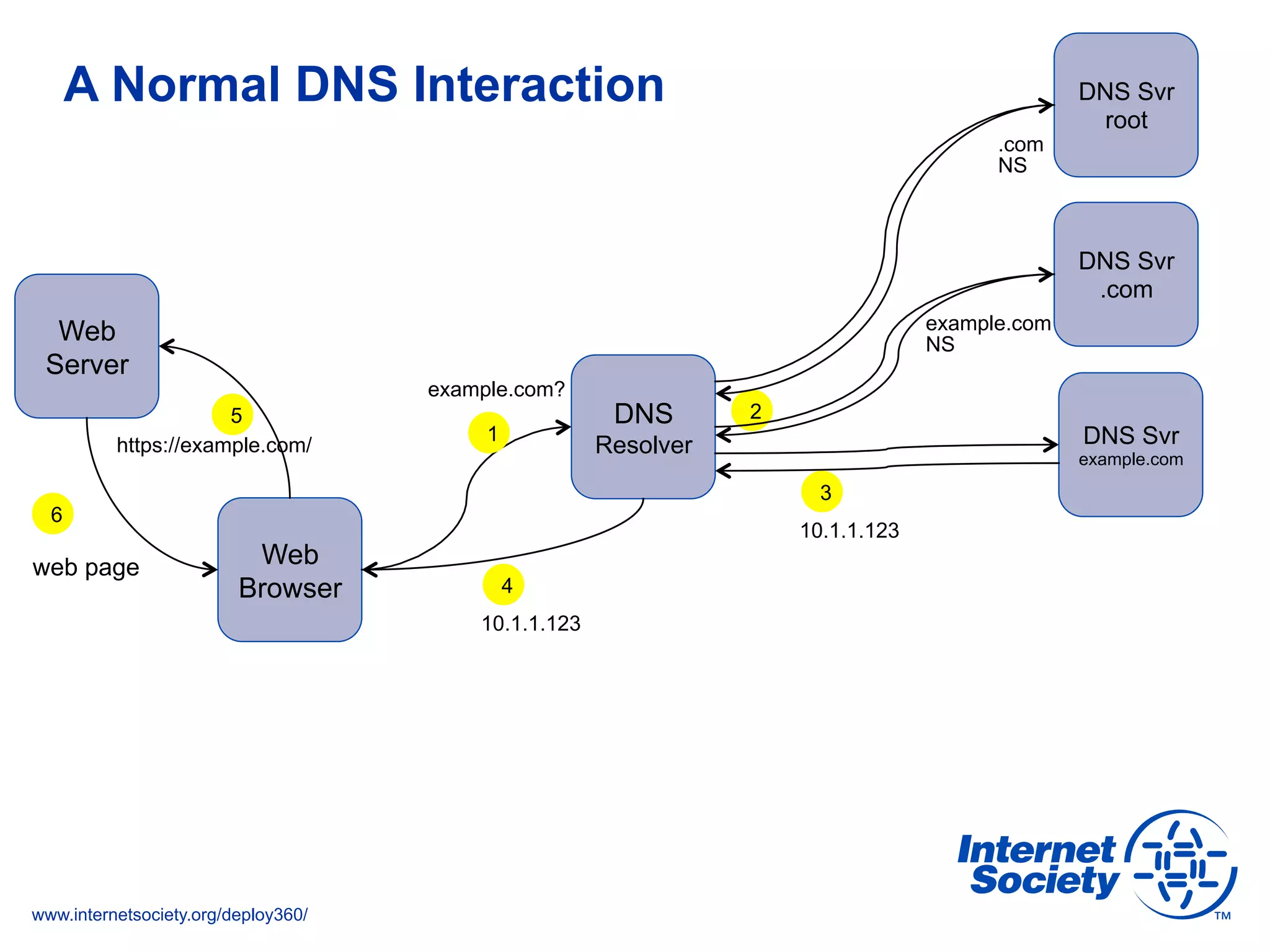
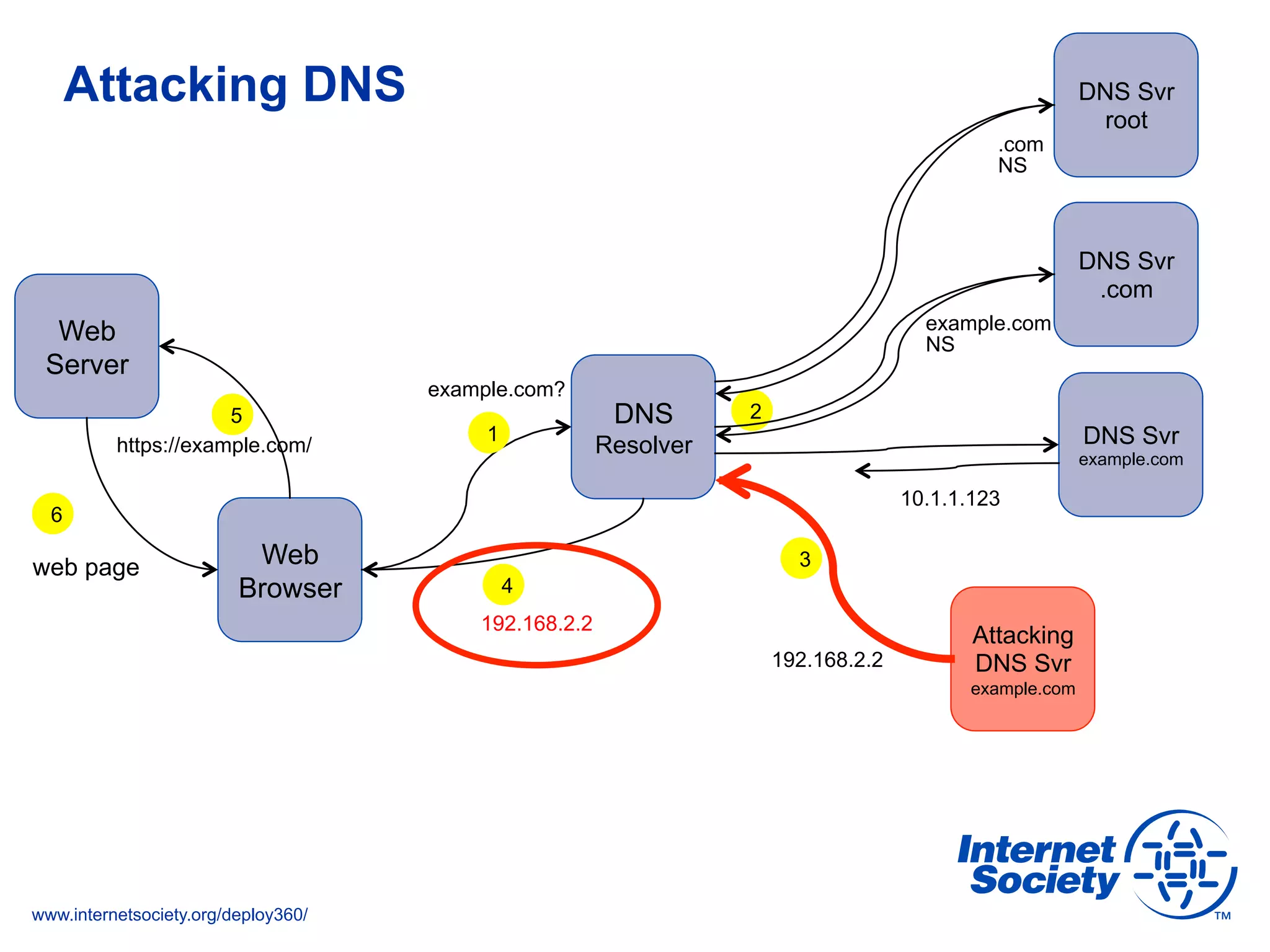
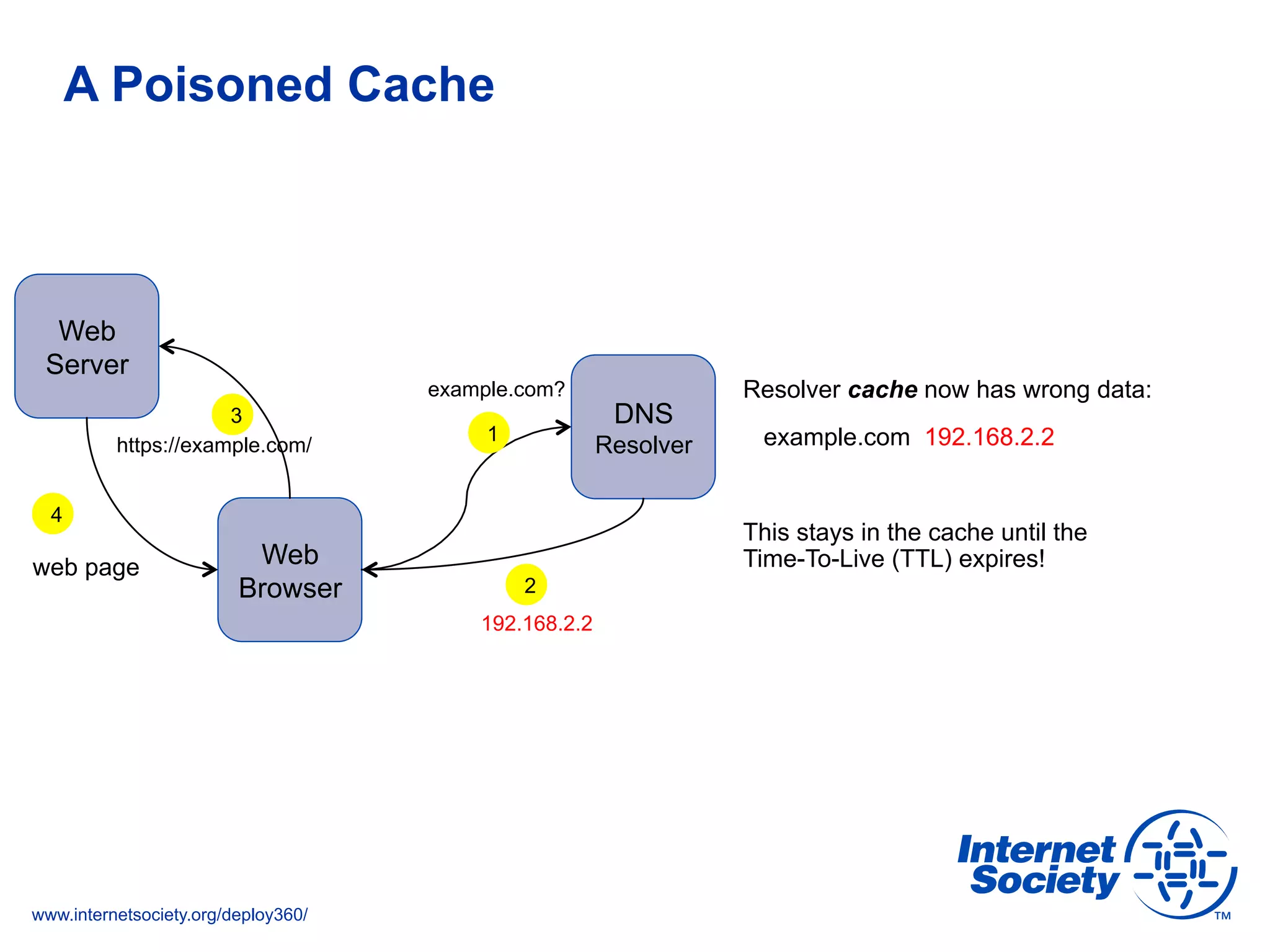
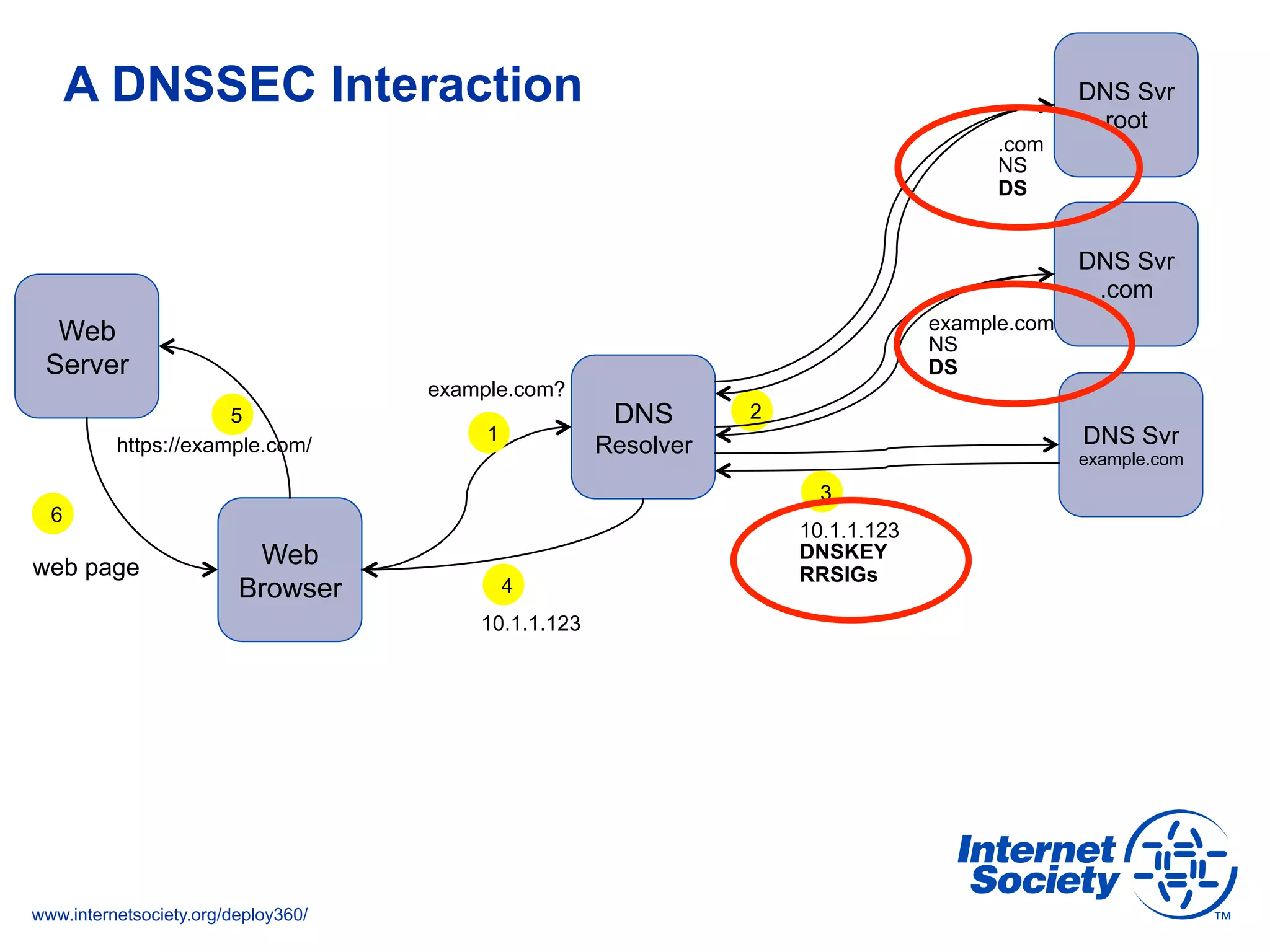
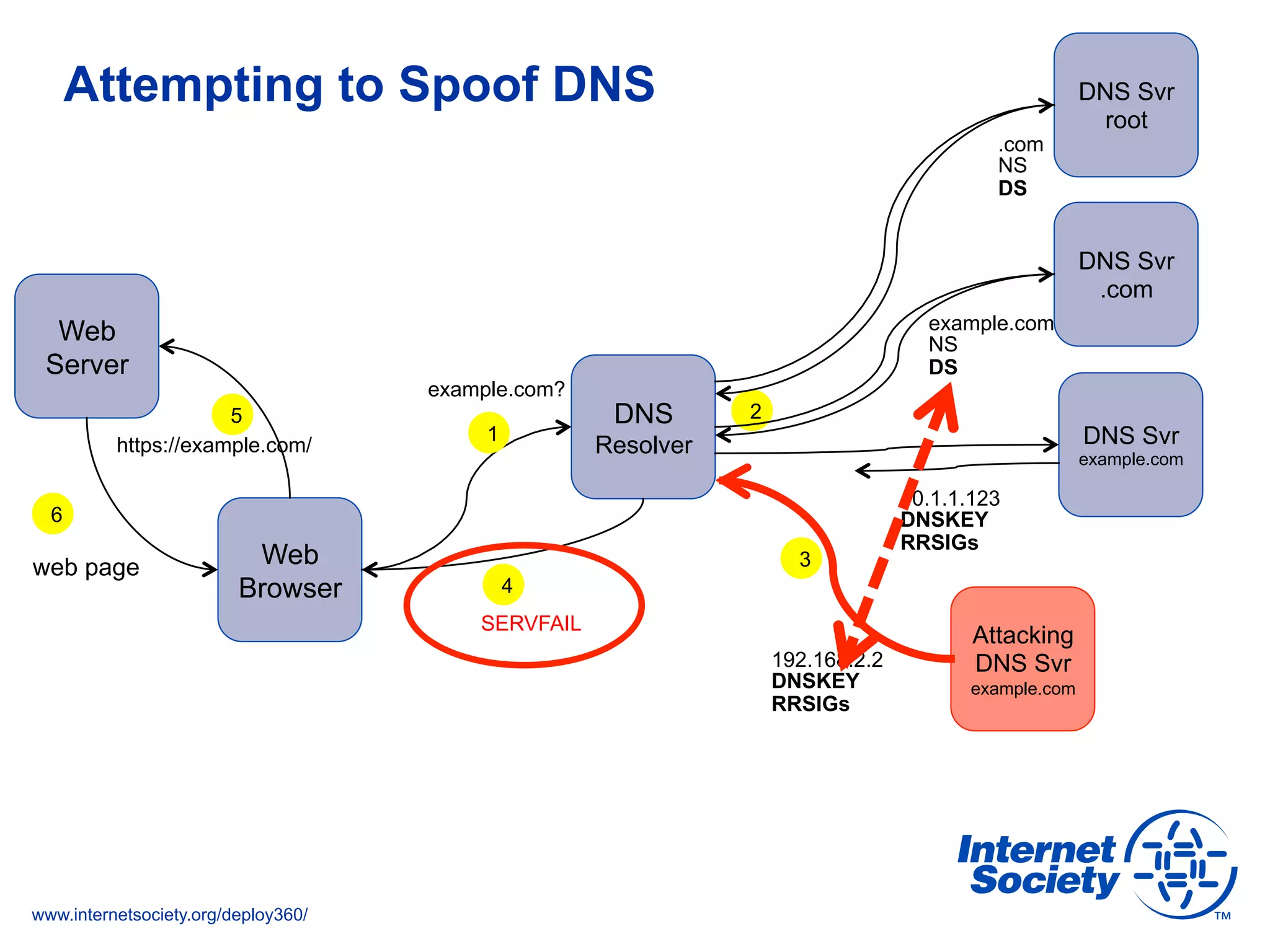
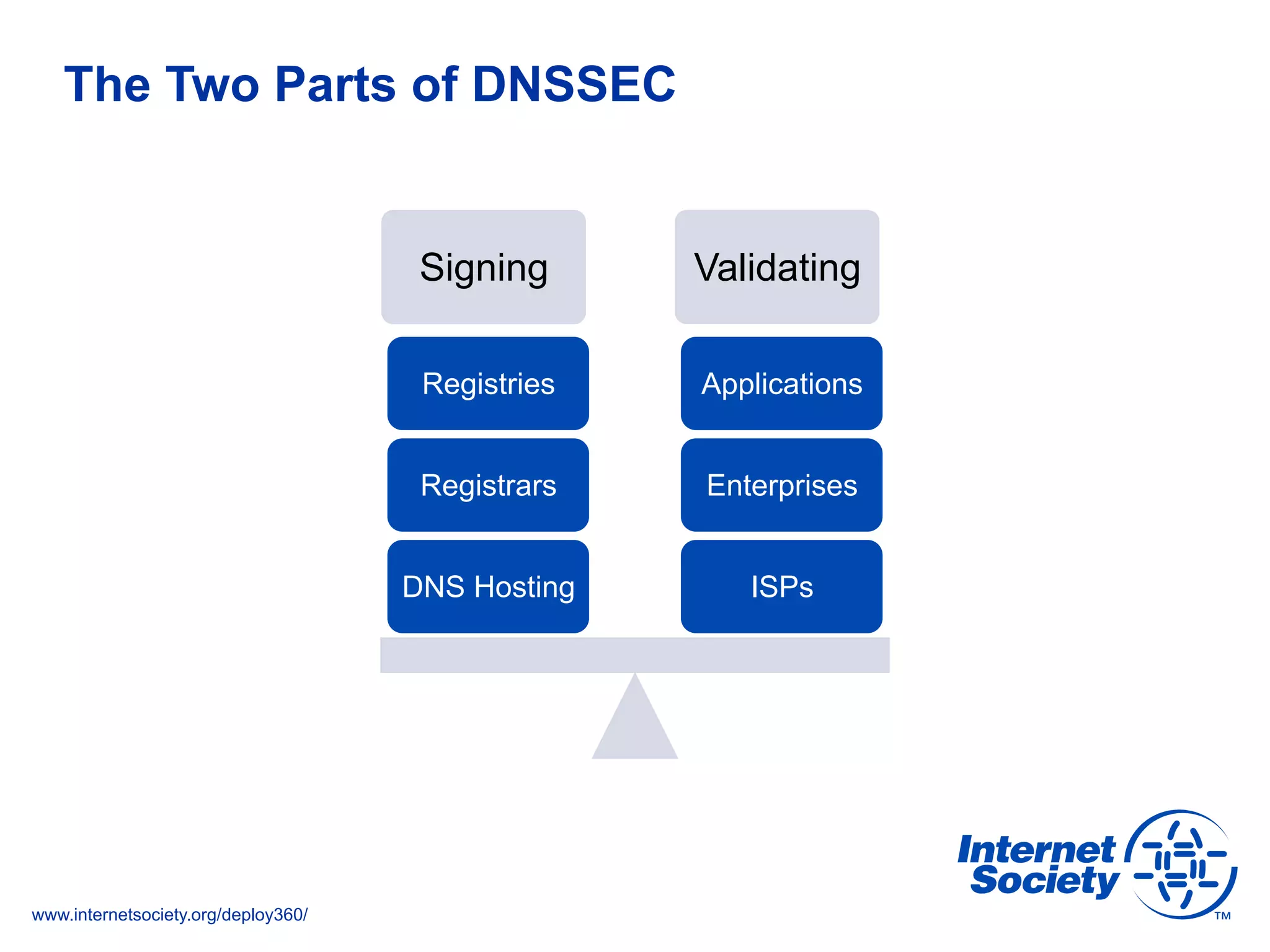
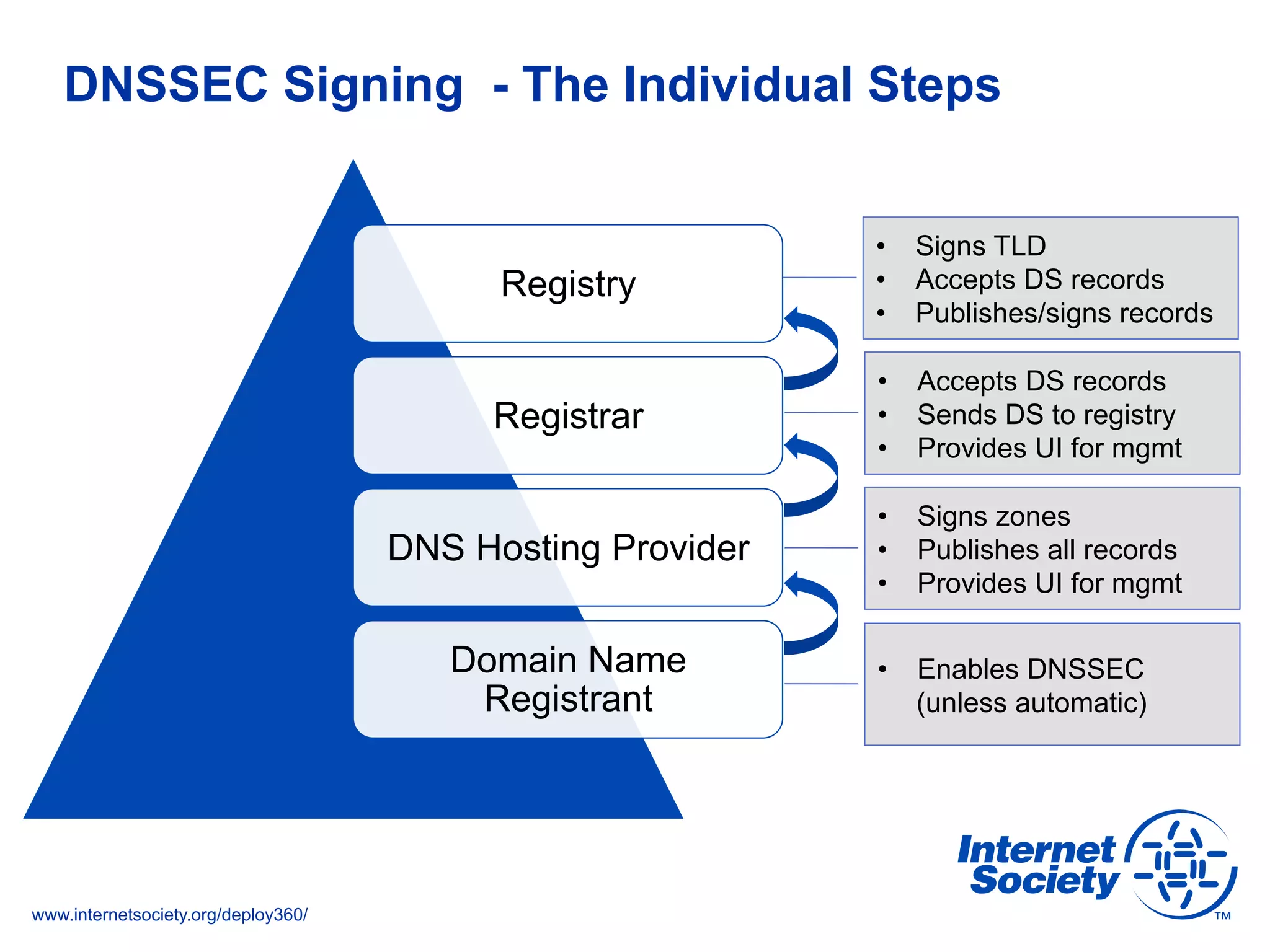
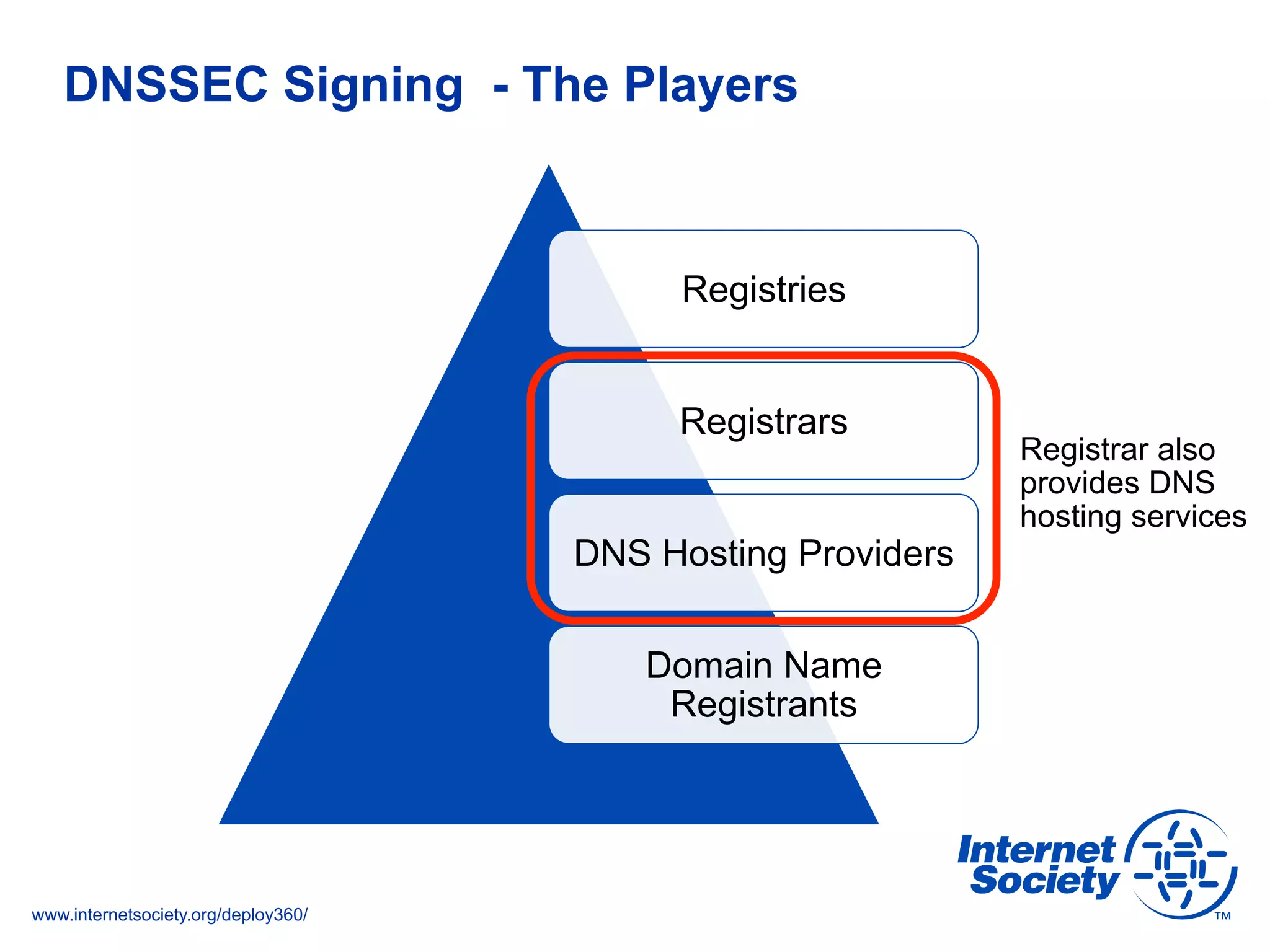
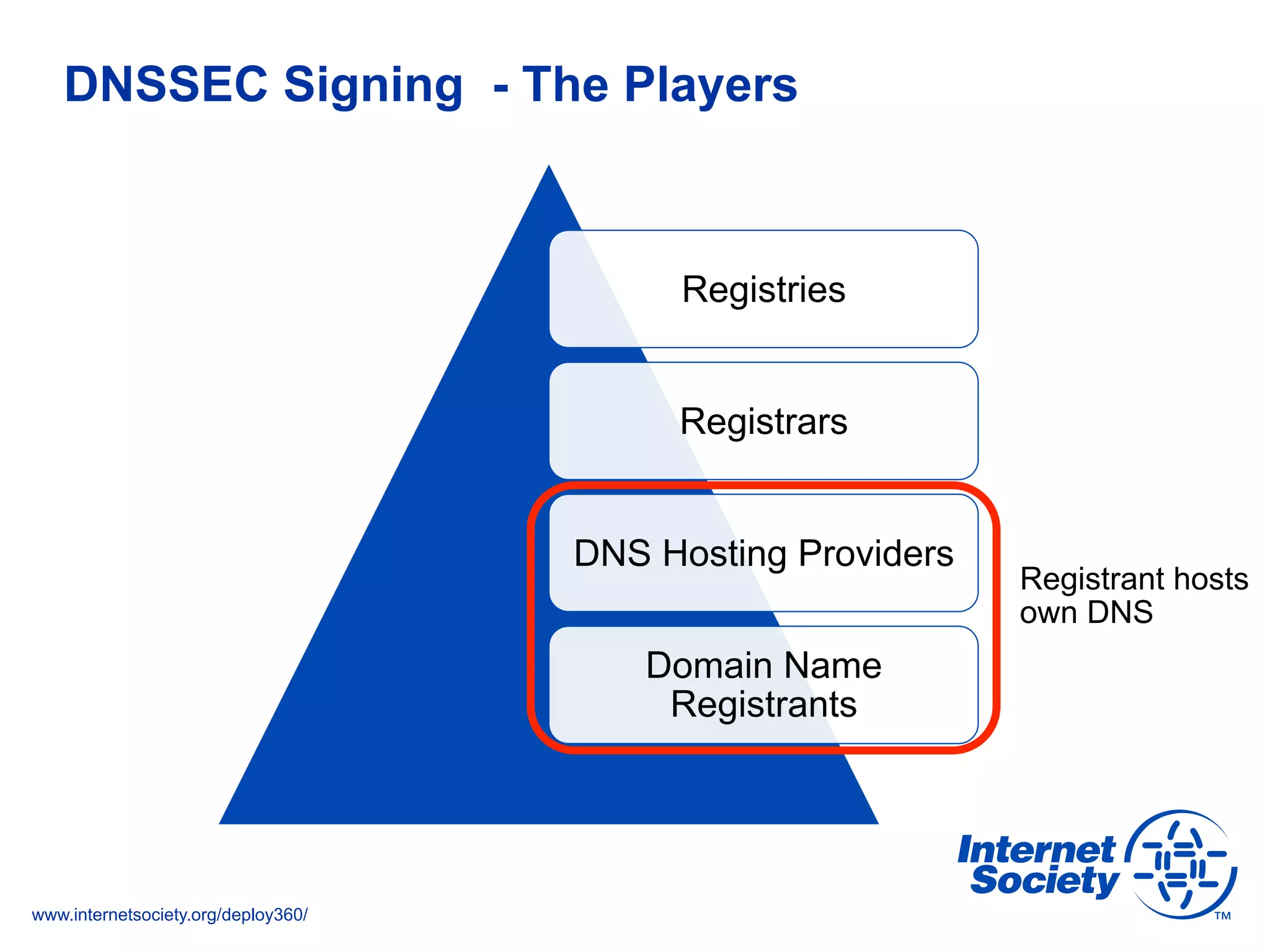
The document addresses the need for increased usage of Transport Layer Security (TLS) in SIP-based communications, discussing the challenges and barriers to its adoption. It highlights the Internet Society's Deploy360 program, which provides resources and guidance for implementing protocols like TLS to enhance security in real-time applications. Additionally, it outlines the benefits of DNS-based Authentication of Named Entities (DANE) in supporting TLS, encouraging SIP operators to adopt these technologies for improved security.