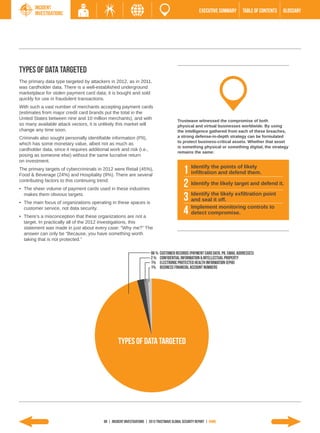
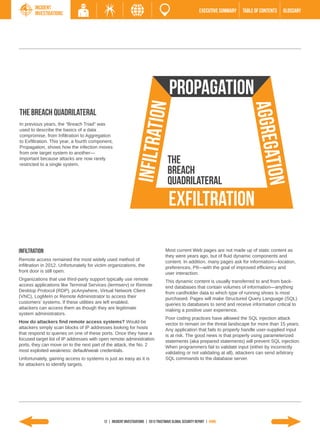
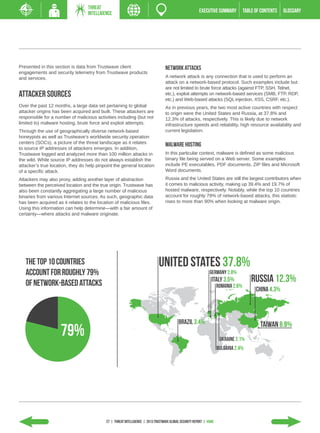
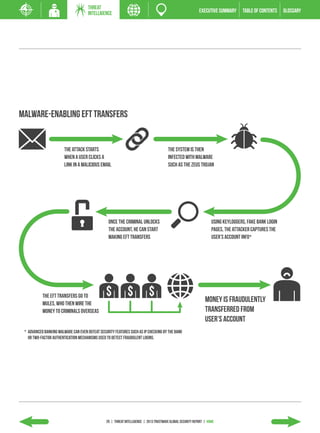
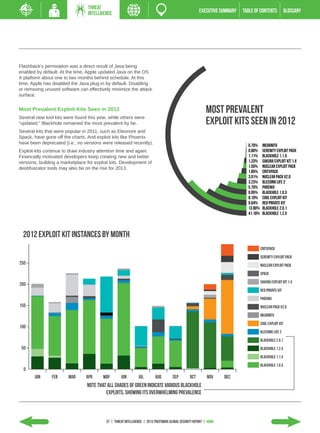
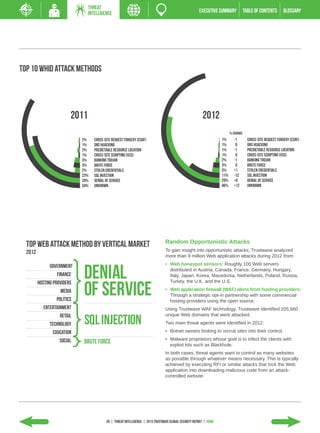
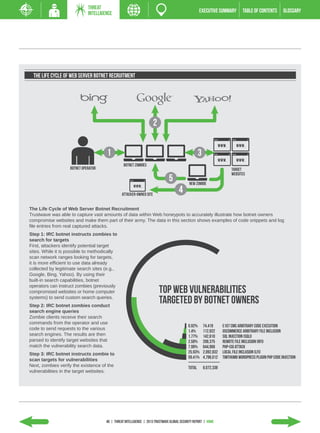
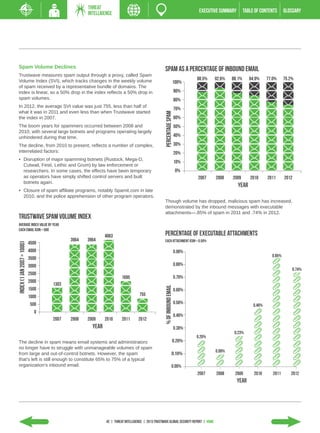
The 2013 Global Security Report from Trustwave analyzes security incident data from 2012. Key findings include:
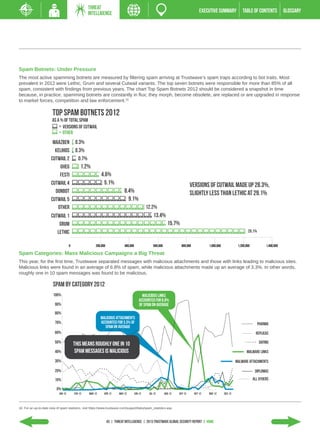
- Retail businesses faced the highest percentage of attacks due to sensitive customer data.
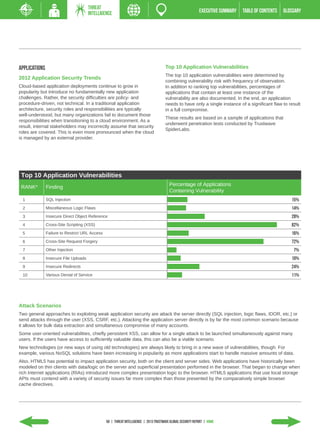
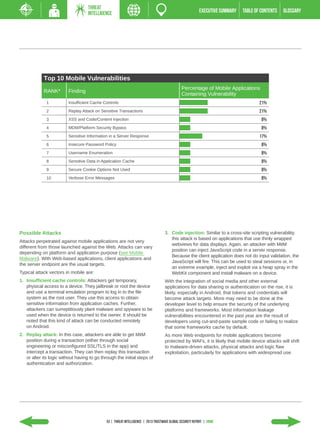
- Web applications surpassed other attack vectors, with e-commerce sites being the most targeted asset.
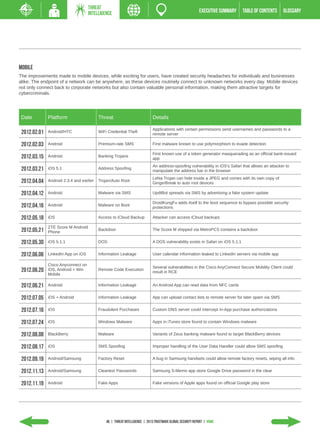
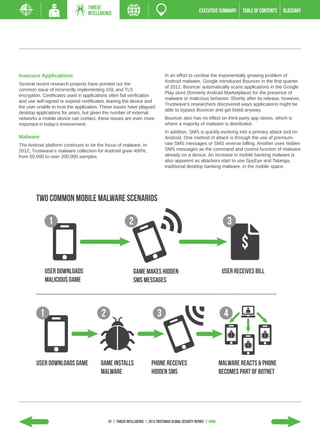
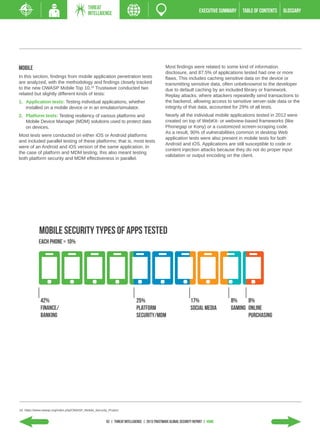
- Mobile malware targeting Android devices exploded, growing 400% in 2012.
- Outsourcing IT operations introduced additional security risks for many organizations.
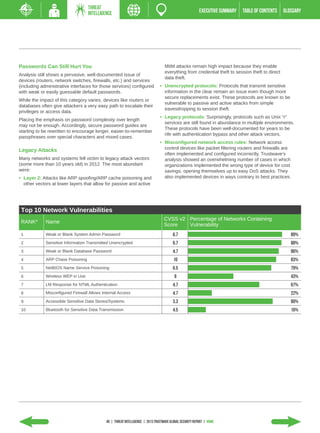
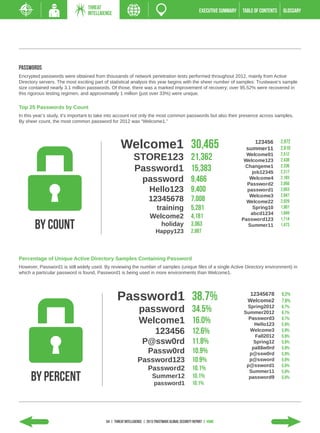
- On average, breaches took over 200 days for organizations to detect, with some going undetected for years.