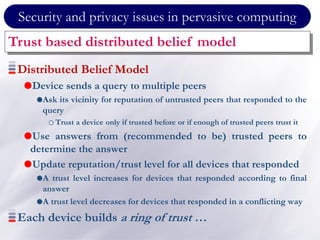
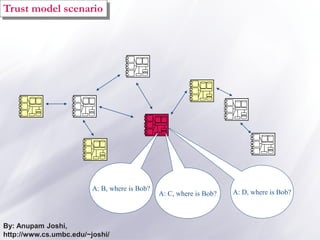
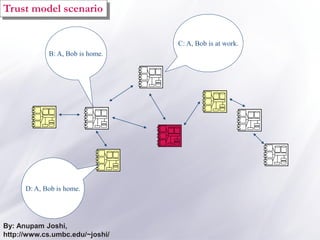
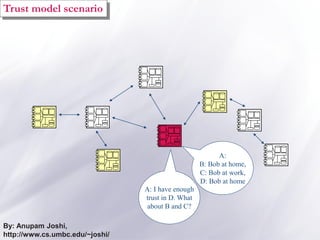
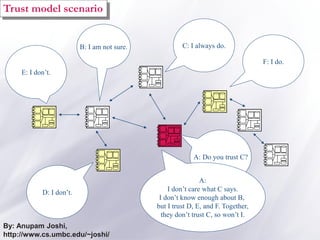
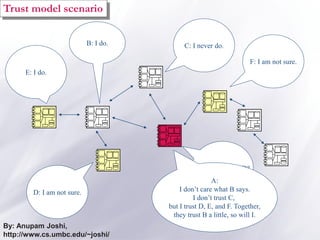
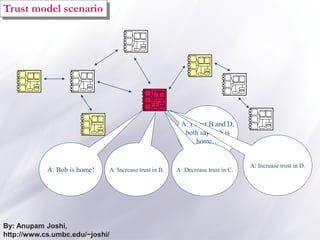
The document discusses the importance of security and privacy in pervasive computing, emphasizing the need for confidentiality, integrity, non-repudiation, and availability in this context. It highlights the challenges posed by the vulnerabilities of wireless networks, the risks of unauthorized access, and the complexities of trust between devices in an interconnected environment. Trust-based models are proposed as a solution to enhance security and facilitate collaboration among smart artifacts, although they also face issues regarding the reliability of information and sources.