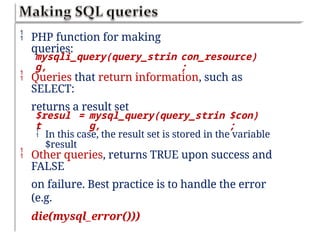
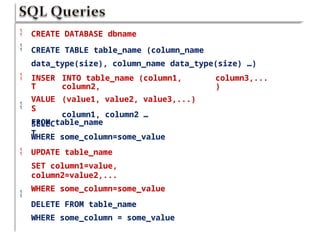
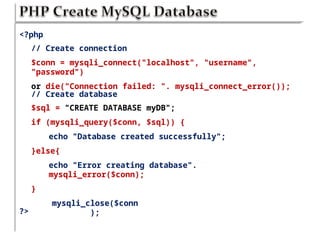
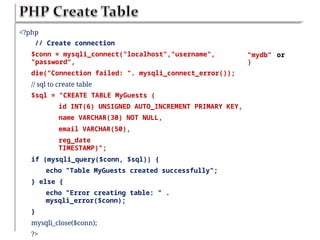
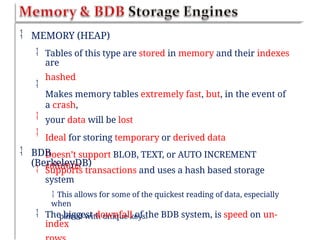
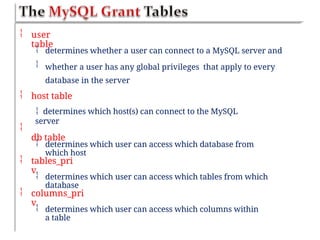
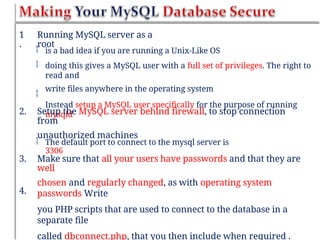
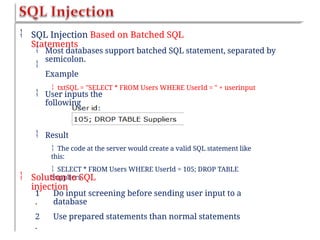
Chapter six discusses the concepts and technologies related to database-driven websites, particularly focusing on PHP and MySQL. It covers various aspects including the MySQL privilege system, optimization methods for database queries, web security considerations, and the implementation of dynamic web pages that interact with a database. Key technical information includes the advantages of different database systems, examples of application structures, and best practices for database operations and security.









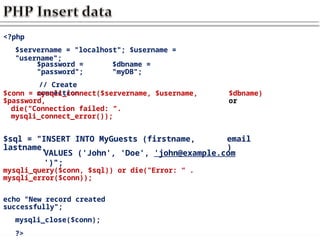
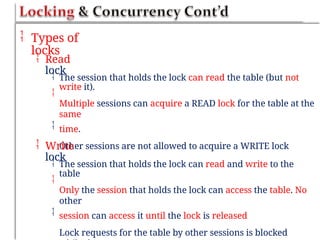
![ The PHP function num_rows() is used to check if there
are
more than zero rows returned
The function fetch_assoc() puts all the
results
associative array that we can loop
through
Example
$result = mysqli_query(query,
$con);
into
an
if (mysqli_num_rows($result) >
0) {
while ($row
=
mysqli_fetch_assoc($result
))
$row['column_1_name'];
$row['column_2_name'];
{
$col
1
$col
2
//
and
=
=
so
forth...
}
}](https://image.slidesharecdn.com/chapter6dbdrivenwebsites-241220194239-2f88c87b/85/CHAPTER-six-DataBase-Driven-Websites-pptx-21-320.jpg)
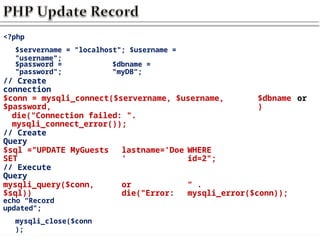
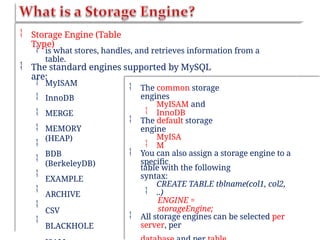
![<?php
$servername = "localhost"; $username =
"username";
$password =
"password";
$dbname =
"myDB";
$conn = mysqli_connect($servername, $username, $password,
$dbname) or
die("Connection failed: ".
mysqli_connect_error());
$sql = "SELECT id, fname, lname FROM
MyGuests";
mysqli_query($conn, $sql)) or die("Error: “ .
mysqli_error($conn));
if (mysqli_num_rows($result) > 0) {
while($row = mysqli_fetch_assoc($result)) {
echo "id:". $row["id"]. "Name:".
$row[“fname"].”
}
} else {
echo "0 results";}
mysqli_close($conn);
“.
$row["lname"]."<br>";](https://image.slidesharecdn.com/chapter6dbdrivenwebsites-241220194239-2f88c87b/85/CHAPTER-six-DataBase-Driven-Websites-pptx-22-320.jpg)











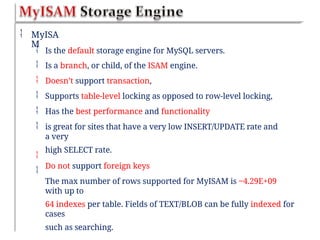





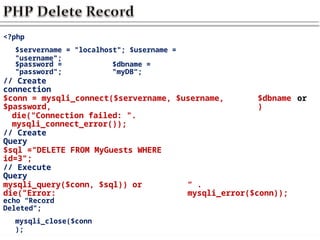
![ Secure Hash
Algorithm
String sha1(String str [, bool
raw_output])
Returns pseudo random 40-character
string
If raw_output is set
true
It returns random 20-character string of binary
data
The password cannot be decrypted back
If(sha1($password)==lajsdf0asdfj323j8258hasd
f93q)
Example
Select count(*) from authorized_users where
name=$username
and password=sha1($password)
The password column should have
varchar(40)](https://image.slidesharecdn.com/chapter6dbdrivenwebsites-241220194239-2f88c87b/85/CHAPTER-six-DataBase-Driven-Websites-pptx-47-320.jpg)




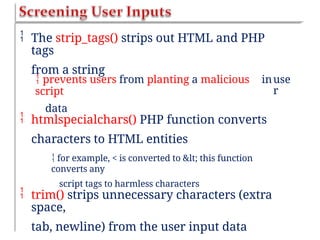
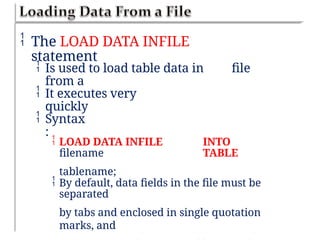
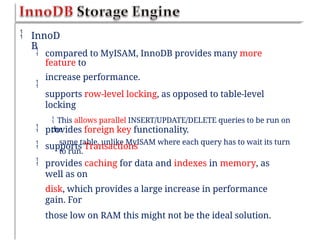
![<?php
$name = $email = $gender = $comment =
$website = "";
if ($_SERVER["REQUEST_METHOD"] ==
"POST")
$name = test_input($_POST["name"]);
$email = test_input($_POST["email"]);
$website = test_input($_POST["website"]);
$gender = test_input($_POST["gender"]);
}
{
function
test_input($data) {
$dat
a
$dat
a
$dat
a
=
=
=
trim($data);
stripslashes($data);
htmlspecialchars($dat
a);
return
$data;
}
?](https://image.slidesharecdn.com/chapter6dbdrivenwebsites-241220194239-2f88c87b/85/CHAPTER-six-DataBase-Driven-Websites-pptx-54-320.jpg)