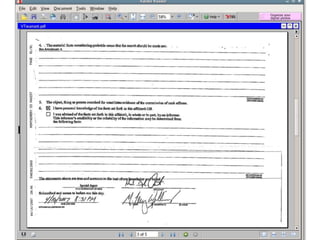
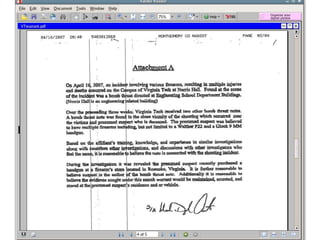
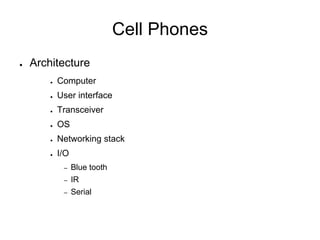
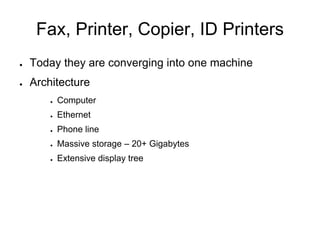
This document provides guidance on properly seizing electronic evidence from a crime scene. It emphasizes the importance of planning, documenting every step with photos and logs, and separating hardware from networks to preserve volatile data. Key steps include: securing the location, photographing everything in detail before collection, using tags and logs to maintain a chain of custody, and being aware of potential legal liabilities from disrupting business data. The goal is to collect all potential digital evidence while ensuring its integrity and admissibility in court.