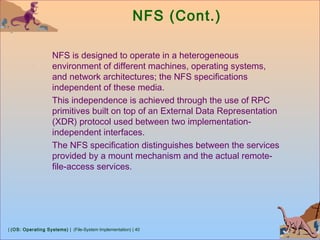
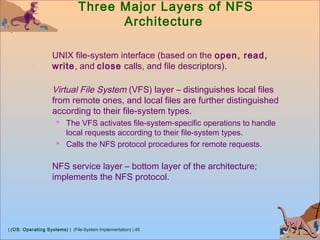
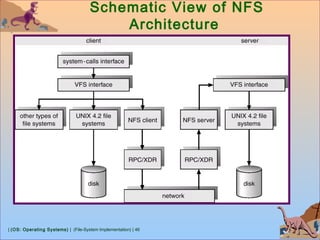
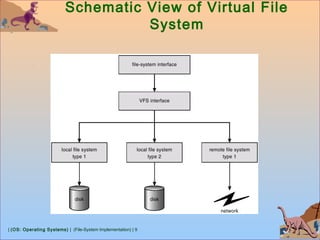
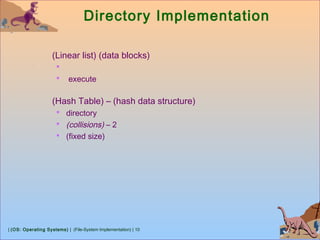
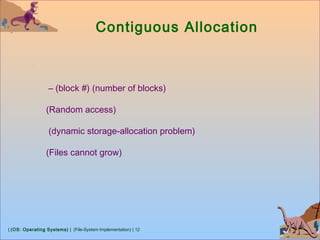
This document discusses various aspects of file system implementation in operating systems. It covers file system structures, directory implementation methods, allocation techniques like contiguous, linked and indexed allocation, free space management using bitmaps and linked lists, performance optimization using caching, and recovery methods like journaling. It also describes network file systems like NFS, which allow remote access to files across networked machines in a transparent manner using client-server architecture and remote procedure calls.


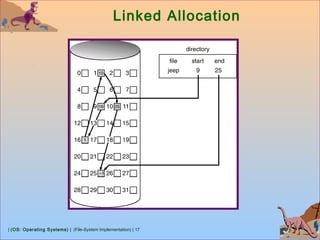
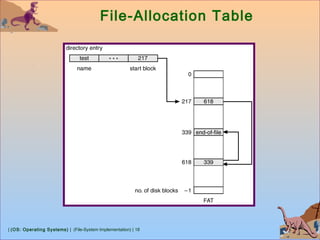
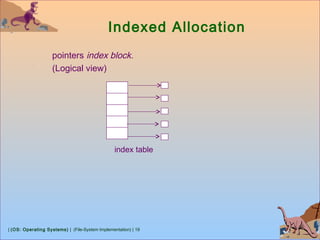
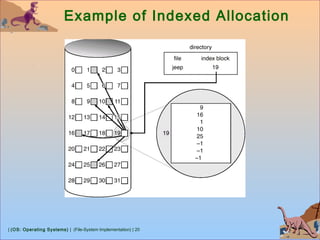
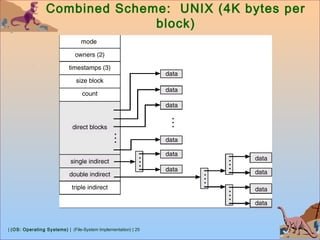
![| (OS: Operating Systems) | (File-System Implementation) | 26
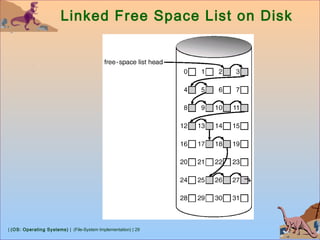
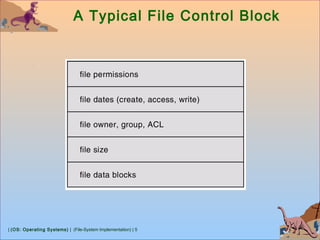
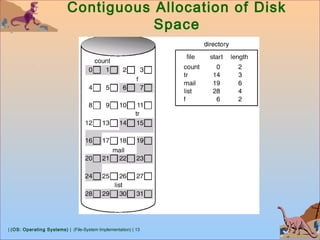
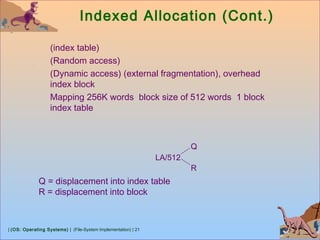
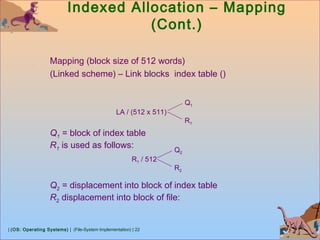
Free-Space Management
Bit vector (n blocks)
…
0 1 2 n-1
bit[i] =
0 ⇒ block[i] free
1 ⇒ block[i] occupied
Block number calculation
(number of bits per word) *
(number of 0-value words) +
offset of first 1 bit](https://image.slidesharecdn.com/8-1-osfilesystemimplementation-181119120154/85/8-1-os-file-system-implementation-26-320.jpg)
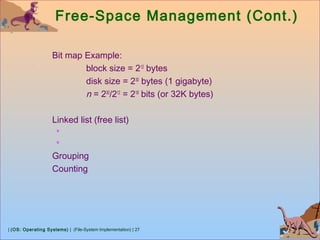
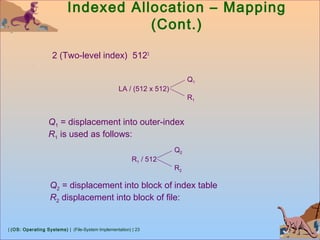
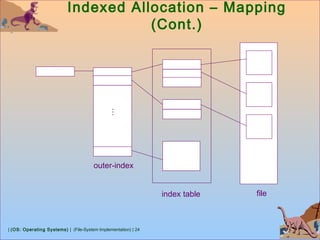
![| (OS: Operating Systems) | (File-System Implementation) | 28
Free-Space Management (Cont.)
(protect)
Pointer (free list)
Bit map
block[i] bit[i] = 1 bit[i] = 0
Solution:
Set bit[i] = 1 in disk.
Allocate block[i]
Set bit[i] = 1 in memory](https://image.slidesharecdn.com/8-1-osfilesystemimplementation-181119120154/85/8-1-os-file-system-implementation-28-320.jpg)