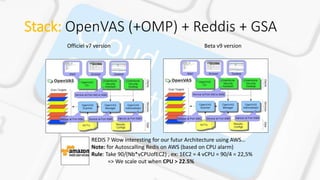
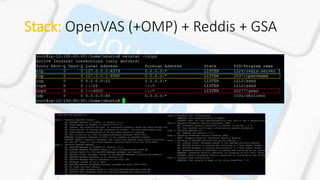
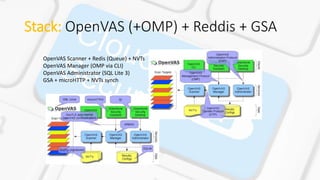
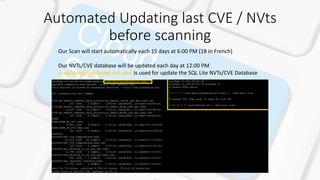
The document describes VAaaS, an automated vulnerability assessment service for AWS clouds using OpenVAS. It outlines the key components including OpenVAS, Redis, and the Greenbone Security Assistant (GSA). It also provides steps for setting up an automated scanning lab in AWS, including starting/stopping EC2 instances, updating vulnerabilities databases, and performing full automated scans of a VPC using OpenVAS commands to parse IP lists and generate reports. The goal is to build a fully automated vulnerability assessment of EC2 instances in an AWS VPC.




![Setup LAB (1/3)
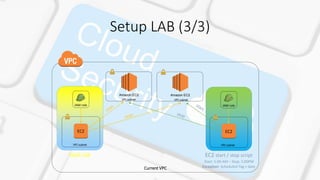
Our current VPC is not a PRODUCTION environment which means our ressources are not not setup for
running at night: Billing Optimization !
- We have a dedicated EC2 Instance running with a dedicated role which contains a crontab BASH
script for:
- Starting all VPC EC2 instance at 5:00 AM (or value in Schedule-Tag)
- Stopping all VPC EC2 instance at 5:00 PM (or value in Schedule-Tag)
ex: if Schedule-Tag = [1-5] [5-17]: Monday to Wednesday, 5:AM to 5:00PM (17h00 French)
[1-5] [NA-NA]: Monday to Wednesday, ALL TIME RUNNING
Exception: if Schedule-Exception present:
format: YEAR-MONTH-DAY HOUR 2016-12-13 18 : 2016-12-16 18
=> Let this EC2 instance running from 2016-12-13 6:00 PM to 2016-12-16 6:00 PM
- We have a dedicated EC2 instance running with our LAB environment with a full IAM permission
role -> t2.2xlarge](https://image.slidesharecdn.com/vaaas-170316181036/85/VAaaS-11-320.jpg)
![Setup LAB (2/3)
EC2 Start/Stop Role
Policy attached:
{
"Statement": [
{
"Action": [
"ec2:DescribeInstances",
"ec2:StartInstances",
"ec2:StopInstances",
"ec2:CreateTags"
],
"Effect": "Allow",
"Resource": "*"
}
]
}
{
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:*",
],
"Resource": "*"
}
]
}
EC2 LAB Role
Policy attached:](https://image.slidesharecdn.com/vaaas-170316181036/85/VAaaS-12-320.jpg)




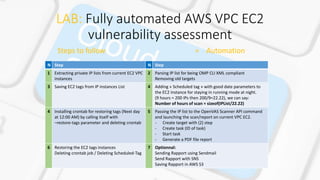
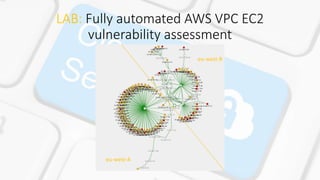
![LAB: Fully automated AWS VPC EC2
vulnerability assessment
Steps to follow = Automation
N Step N Step
1 aws ec2 describe-instances --instance-ids --query
Reservations[].Instances[].PrivateIpAddress > $target
+ Custom code
2 Custom code
3 aws ec2 describe-tags --filters "Name=resource-
type,Values=instance" --output json > $file
+ Custom code
4 aws ec2 describe-instances --instance-ids --query
'Reservations[].Instances[].[InstanceId]' --filters Name=instance-
state-name,Values=running
&
aws ec2 create-tags --resources $name --tags Key="Schedule-
Exception",Value="$TagToDelete“
+ Custom code
4 Custom code (--restore-tag) parameter 5 Custom code
6 aws ec2 delete-tags --resources $name --tags
Key="Schedule-Exception",Value="$TagsToDel“
+ Custom code
7 Custom code](https://image.slidesharecdn.com/vaaas-170316181036/85/VAaaS-20-320.jpg)