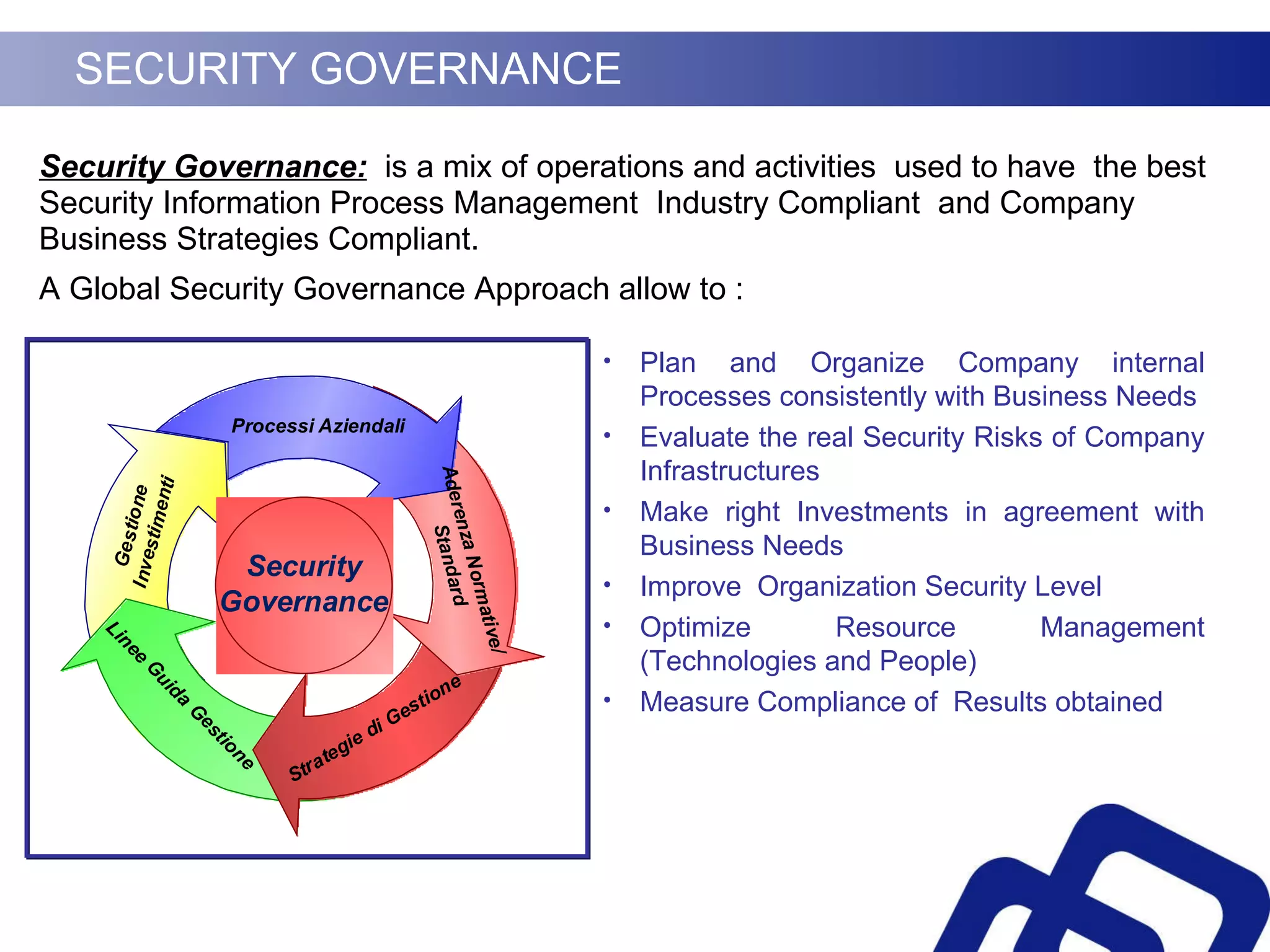
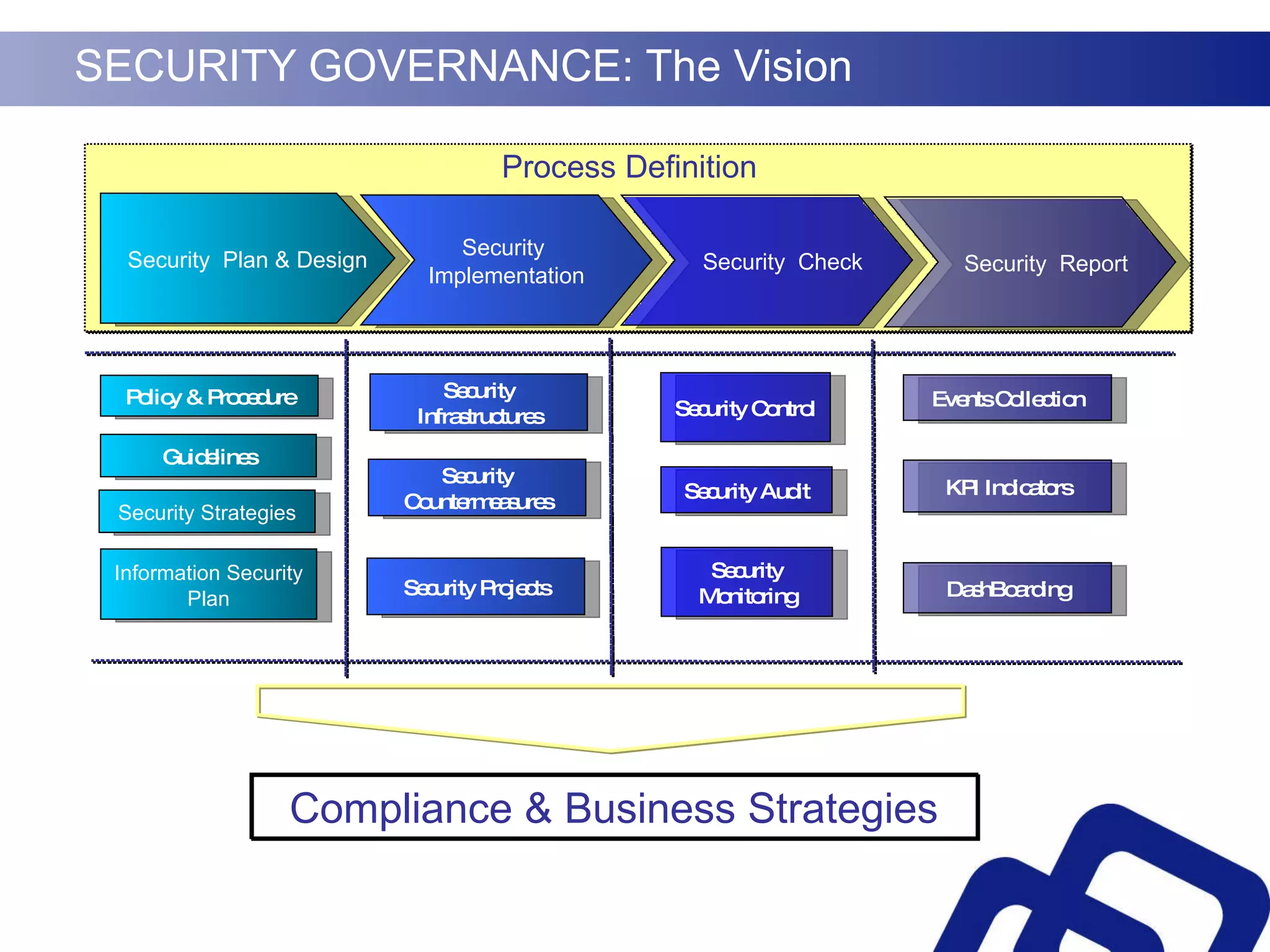
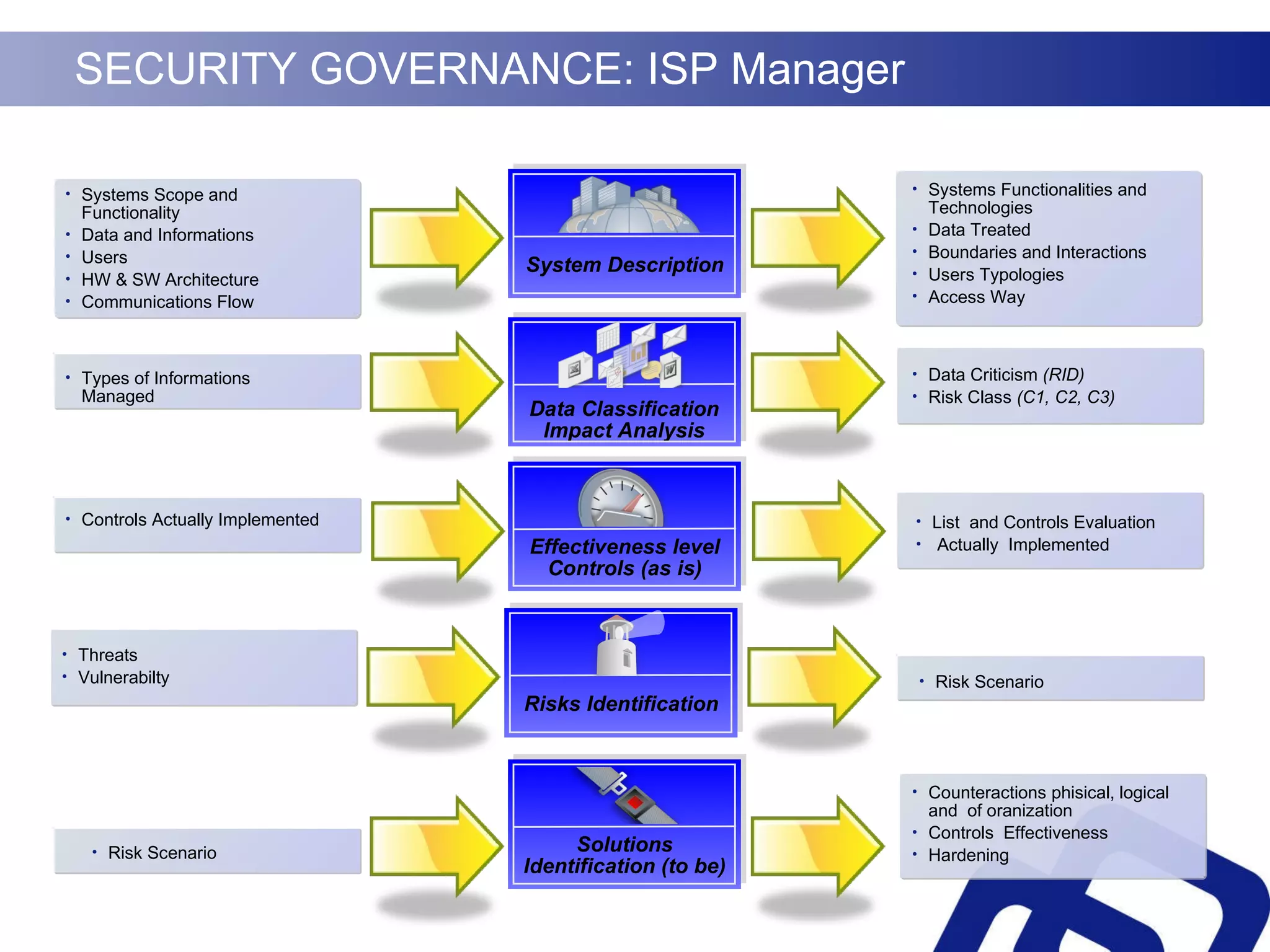
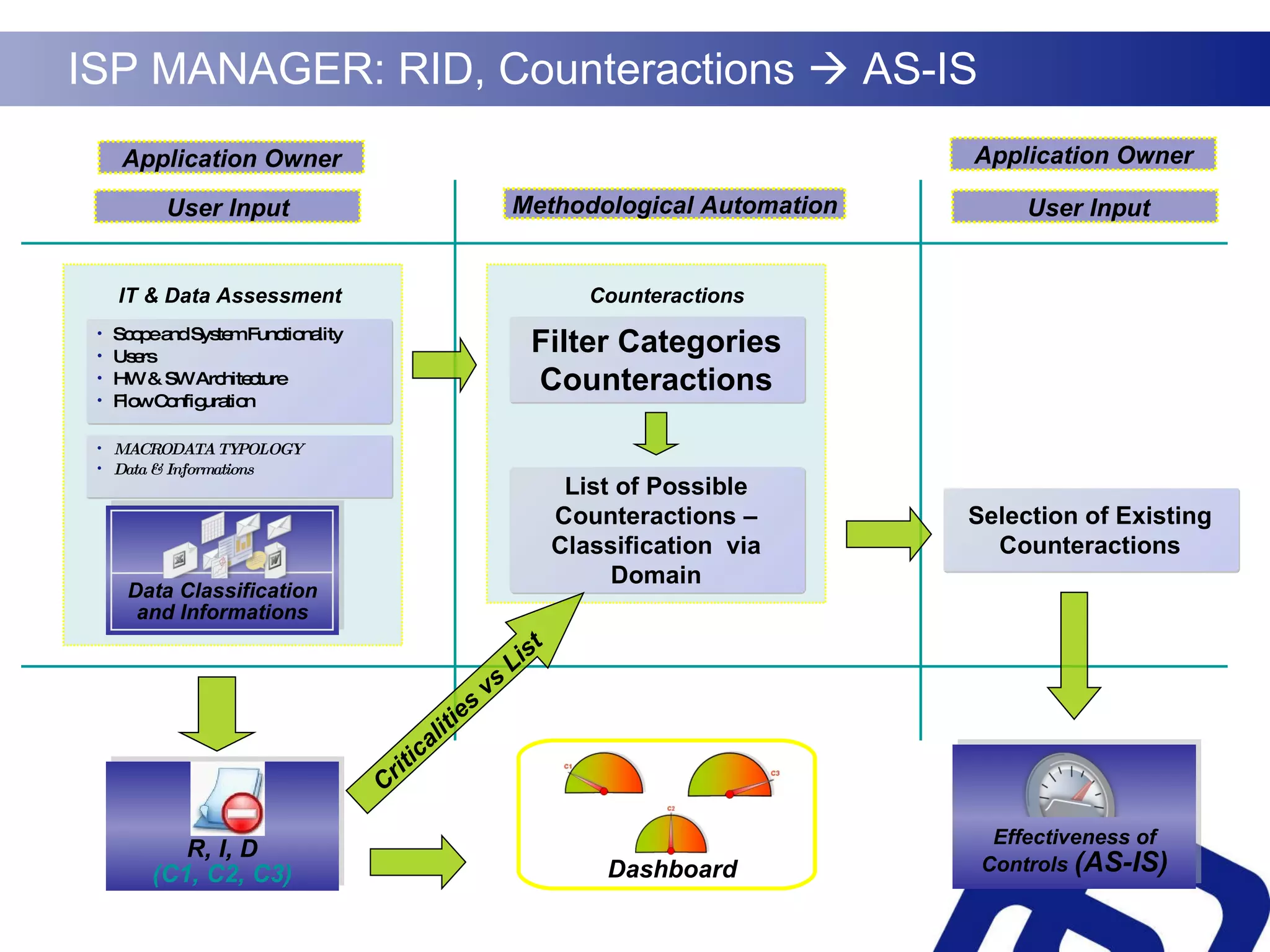
Security governance involves three key elements:
1) Evaluating an organization's security risks and ensuring investments in security controls align with business needs.
2) Improving the organization's overall security level and optimizing resource management of security technologies and personnel.
3) Measuring compliance of security practices with industry standards and business strategies.



![Roma, 22 settembre 2009 Maurizio Milazzo Business Development [email_address] Thank You Security Governance as IT Governance Internal Process](https://image.slidesharecdn.com/security-governanceispeng-100107065038-phpapp01/75/Security-Governance-Isp-Eng-9-2048.jpg)