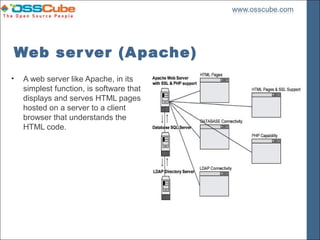
This document outlines the security measures necessary for setting up an Apache web server, detailing its functions, security assumptions, and prerequisites. It emphasizes the importance of hardening the operating system, implementing a chroot jail, and configuring PHP securely to prevent attacks such as SQL injection and cross-site scripting. The document also covers the installation steps for various modules and the need for proper user authentication and access management.








![Step – 1 - Installation
Decompress TAR balls and keep in one directory i.e. /var/tmp
Copy
• [root@localhost]/# cp apache_version.tar.gz /var/tmp
• [root@localhost]/# cp mod_ssl-version-version.tar.gz /var/tmp
• [root@localhost]/# cp mod_perl-version.tar.gz /var/tmp
• [root@localhost]/# cp php-version.tar.gz /var/tmp
• [root@localhost]/# cd /var/tmp/
Decompress
• [root@localhost]/tmp# tar xzpf apache_version.tar.gz
• [root@localhost]/tmp# tar xzpf mod_ssl-version-version.tar.gz
• [root@localhost]/tmp# tar xzpf mod_perl-version.tar.gz
• [root@localhost]/tmp# tar xzpf php-version.tar.gz](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-12-320.jpg)
![Mod_SSL –
• [root@localhost]/# cd mod_ssl-version-version
• [root@localhost]/# CC="egcs" CFLAGS="-O9 -funroll-loops -ffast-math
-malign-double -mcpu=pentiumpro -march=pentiumpro -fomit-frame-pointer
-fno-exceptions" ./configure --with-apache=../apache_1.3.37 --with-
crt=/etc/ssl/certs/server.crt --with-key=/etc/ssl/private/server.key
*CC – C Compiler
**egcs – Enhanced GNU Compiler System
***CFLAGS – O2 (i386), O3 (i586), O9 (i686) Optimization Option](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-13-320.jpg)
![PHP 4
• [root@localhost]# cd apache_1.3.37
Configure -
• [root@localhost]# CC="egcs" OPTIM="-O9 -funroll-loops -ffast-math -malign-double
-mcpu=pentiumpro -march=pentiumpro -fomit-frame-pointer -fno-exceptions" CFLAGS="-
DDYNAMIC_MODULE_LIMIT=0"
• ./configure
• --prefix=/home/httpd
• --bindir=/usr/bin
• --sbindir=/usr/sbin
• --libexecdir=/usr/lib/apache
• --includedir=/usr/include/apache
• --sysconfdir=/etc/httpd/conf
• --localstatedir=/var
• --runtimedir=/var/run
• --logfiledir=/var/log/httpd
• --datadir=/home/httpd
• --proxycachedir=/var/cache/httpd
• --mandir=/usr/man](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-14-320.jpg)
![PHP4
This tells PHP4 to set itself up for this particular hardware setup with:
• Compile without debugging symbols.
• Enable safe mode by default.
• Include IMAP & POP support.
• Include LDAP directory support.
• Include PostgreSQL / MySQL database support.
• Include mm support to improve performance of Memory Library.
• Enable inline-optimization for better performance.
• Compile with memory limit support.
• Assume the C compiler uses GNU ld.
• 3. [root@deep ]/php-4.0# make && make install](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-15-320.jpg)
![Mod_PERL
• [root@localhost] cd ../mod_perl-version.version/
• [root@localhost] perl Makefile.PL EVERYTHING=1
APACHE_SRC=../apache_1.3.37/src USE_APACI=1 PREP_HTTPD=1
DO_HTTPD=1
• 3. [root@localhost]/mod_perl-version.version# make && make install](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-16-320.jpg)
![Apache
• 1. [root@localhost]/apache1.3.37# SSL_BASE=SYSTEM EAPI_MM=SYSTEM CC="egcs"
OPTIM="-O9 -funroll-loops -ffast-math -malign-double -mcpu=pentiumpro -march=pentiumpro
-fomit-frame-pointer -fno-exceptions" CFLAGS="-DDYNAMIC_MODULE_LIMIT=0"
• ./configure
• --prefix=/home/httpd
• --bindir=/usr/bin
• --sbindir=/usr/sbin
• --libexecdir=/usr/lib/apache
• --includedir=/usr/include/apache
• --sysconfdir=/etc/httpd/conf
• --localstatedir=/var
• --runtimedir=/var/run
• --logfiledir=/var/log/httpd
• --datadir=/home/httpd
• --proxycachedir=/var/cache/httpd
• --mandir=/usr/man
• --add-module=src/modules/experimental/mod_mmap_static.c
• --add-module=src/modules/standard/mod_auth_db.c](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-17-320.jpg)
![• --enable-module=ssl
• --enable-rule=SSL_SDBM
• --disable-rule=SSL_COMPAT
• --activate-module=src/modules/php4/libphp4.a
• --enable-module=php4
• --activate-module=src/modules/perl/libperl.a
• --enable-module=perl
• --disable-module=status
• --disable-module=userdir
• --disable-module=negotiation
• --disable-module=autoindex
• --disable-module=asis
• --disable-module=imap
• --disable-module=env
• --disable-module=actions
• 2. [root@localhost]/apache1.3.37# make && make install](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-18-320.jpg)


![Find Dependences
• [root@localhost]/# ldd /usr/sbin/httpd
• libpam.so.0 =>/lib/libpam.so.0 (0x40016000)
• libm.so.6 =>/lib/libm.so.6 (0x4001f000)
• libdl.so.2 =>/lib/libdl.so.2 (0x4003b000)
• libcrypt.so.1 =>/lib/libcrypt.so.1 (0x4003e000)
• libnsl.so.1 =>/lib/libnsl.so.1 (0x4006b000)
• libresolv.so.2 =>/lib/libresolv.so.2 (0x40081000)
• libdb.so.3 =>/lib/libdb.so.3 (0x40090000)
• libc.so.6 =>/lib/libc.so.6 (0x400cb000)
• /lib/ld-linux.so.2 =>/lib/ld-linux.so.2 (0x40000000)](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-23-320.jpg)
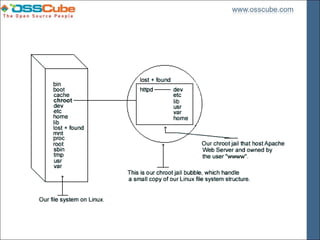
![Create Dir ector y Str uctur e (Similar in dependencies)
• [root@localhost ]/# mkdir /chroot/httpd
• [root@localhost ]/# mkdir /chroot/httpd/dev
• [root@localhost ]/# mkdir /chroot/httpd/lib
• [root@localhost ]/# mkdir /chroot/httpd/etc
• [root@localhost ]/# mkdir -p /chroot/httpd/usr/sbin
• [root@localhost ]/# mkdir -p /chroot/httpd/var/run
• [root@localhost ]/# mkdir -p /chroot/httpd/var/log/httpd
• [root@localhost ]/# chmod 750 /chroot/httpd/var/log/httpd/
• [root@localhost ]/# mkdir -p /chroot/httpd/home/httpd](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-24-320.jpg)
![Copy all found dependencies into created directory along with File Access
Permissions
(No other writable)
• [root@localhost ]/# cp -r /etc/ssl /chroot/httpd/etc/ � require only if you use mod_ssl
feature.
• [root@localhost ]/# chmod 600 /chroot/httpd/etc/ssl/certs/ca.crt � require only if you
use mod_ssl feature.
• [root@localhost ]/# chmod 600 /chroot/httpd//etc/ssl/certs/server.crt � require only if
you use mod_ssl feature.
• [root@localhost ]/# chmod 600 /chroot/httpd/etc/ssl/private/ca.key � require only if
you use mod_ssl feature.
• [root@localhost ]/# chmod 600 /chroot/httpd/etc/ssl/private/server.key � require only
if you use mod_ssl feature.](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-25-320.jpg)
![users authentication with .dbmpasswd password file
• To change the permissions on the dbmmanage program, use the following
command:
• [root@localhost ]/# chmod 750 /usr/bin/dbmmanage
• To create a username and password, use the following command:
• [root@deep ]/# /usr/bin/dbmmanage /etc/httpd/.dbmpasswd adduser username
• New password:
• Re-type new password:
• User username added with password encrypted to l4jrdAL9MH0K.](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-26-320.jpg)
![Now copy the passwd and group files inside the /chroot/httpd/etc chrooted directory and
remove all entries except for the user that apache runs as in both files passwd and
group.
• [root@localhost ]/# cp /etc/passwd /chroot/httpd/etc/
• [root@localhost ]/# cp /etc/group /chroot/httpd/etc/
Edit the passwd file, vi /chroot/httpd/etc/passwd and delete all entries except for the user
apache run as in our configuration, it's www:
• www:x:80:80::/home/www:/bin/bash
Edit the group file, vi /chroot/httpd/etc/group and delete all entries except the group
apache run as, in our configuration it,s www:
• www:x:80:
Then you will also need /etc/resolv.conf, /etc/nsswitch.conf and /etc/hosts files in your
chroot jail in same directory structure to resolve hosts name.](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-27-320.jpg)
![Step – 3: Securing CGI Applications
• Configuring PHP
• add the following lines to httpd.conf
• AddModule mod_php4.c
• AddType application/x-httpd-php .php
• AddType application/x-httpd-php .inc
• AddType application/x-httpd-php .class
• A few changes must also be made in the PHP configuration file
(/chroot/httpd/usr/local/lib/php.ini).
• Parameter Description
• safe_mode = On
• safe_mode_gid = Off
• open_basedir = directory[:...] (Only this dir. Accessible by Scipts)
• safe_mode_exec_dir = directory[:...] (Executable program refused to run by Apache)
• expose_php = Off (Do not show PHP Info)
• register_globals = Off
• display_errors = Off
• log_errors = On
• error_log = filename](https://image.slidesharecdn.com/securing-your-webserver-by-pradeep-sharma-1232704607813466-2/85/Securing-Your-Webserver-By-Pradeep-Sharma-28-320.jpg)