The document discusses the growth of cloud computing and its implications for finance, highlighting common myths related to security and data privacy. It emphasizes that the safety of data in the cloud depends on the security measures in place, regardless of whether the systems are managed in-house or by a vendor. Furthermore, it advises companies to rigorously evaluate cloud service providers based on their security standards and compliance capabilities.





![Business Drivers & Benefits
• Initial interest was with Workday, with cloud an eventual “bonus”
• The off-premise concept, including integration management was
intriguing
• Access to all traditional ERP applications, without traditional
ERP arrangement
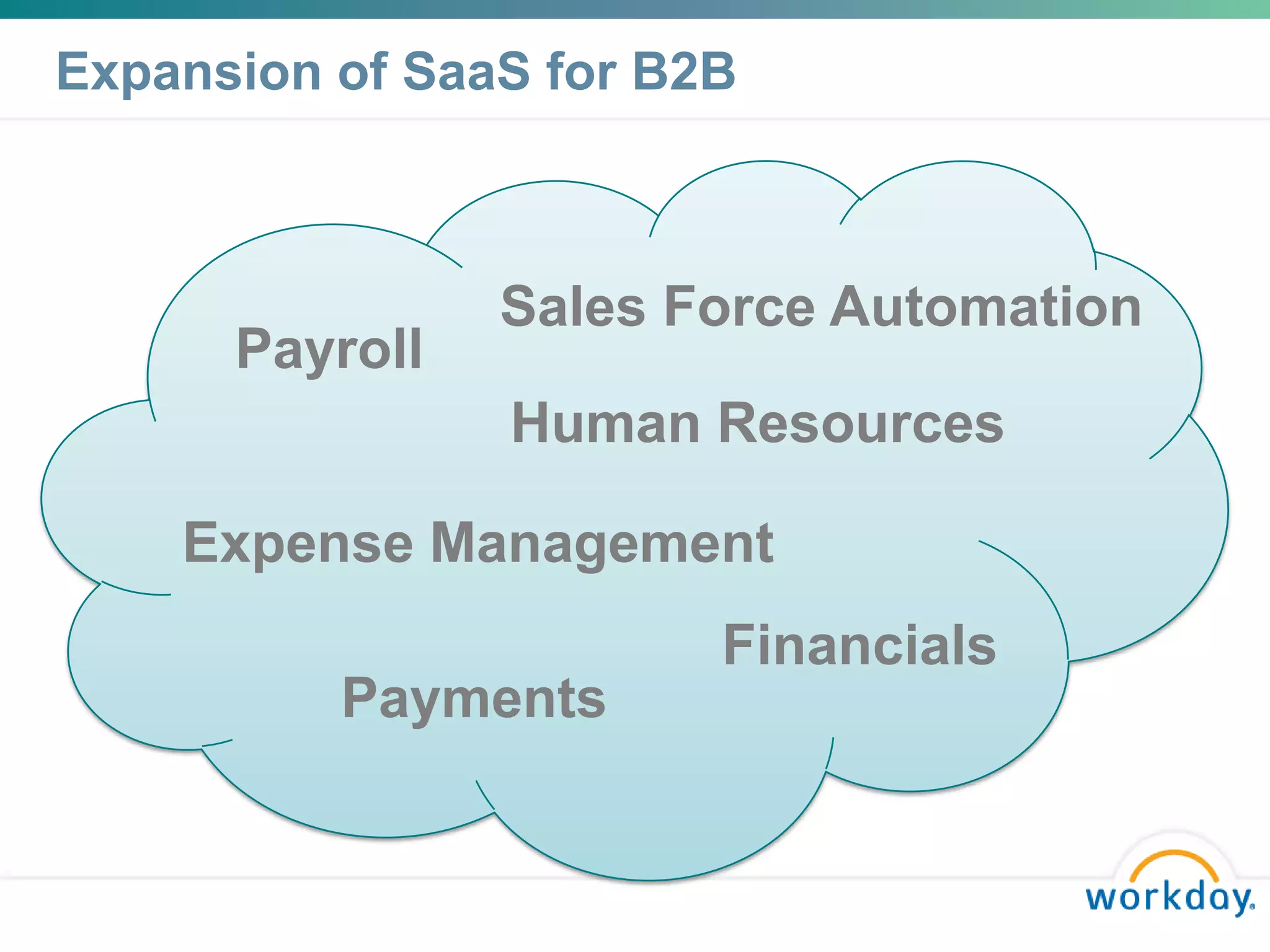
• Currently, Workday applications in the cloud:
- Human Capital Management, Expenses (reimbursement), Payroll [all live at least 2 years]
- Procurement, Supplier Accounts (AP), Banking [go live during 2012]
- Financials (GL), Customer Accounts (AR), Fixed Assets, Projects [go live during 2013]
• Cloud strategy supports our project requirements of:
- Increased efficiency (speed of system and business processes)
- Improved accuracy and reporting
- Lower overall cost
• Managing security and data privacy with third party vs. internal
- Ensure highest level of controls around cloud security (internal vs. external expertise)
- Cost – Benefit of internal controls maintenance internally vs. reliance on third party
- Zero tolerance for breach](https://image.slidesharecdn.com/slidedeckworkdaysponsoredwebcastwithcfopublishing041212-120501192307-phpapp01/75/Securing-the-Office-of-Finance-in-the-Cloud-Separating-Fact-from-Fiction-9-2048.jpg)



