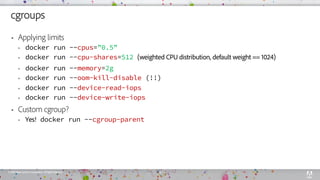
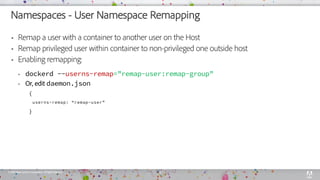
The document discusses container security mechanisms and strategies used in Docker, including control groups, namespaces, seccomp, and kernel capabilities. It emphasizes the importance of managing vulnerabilities, using trusted images, and enabling Docker content trust to enhance security. Additional tools and practices for vulnerability scanning and application-level security considerations within containers are also highlighted.













![©2018AdobeSystemsIncorporated. AllRightsReserved.
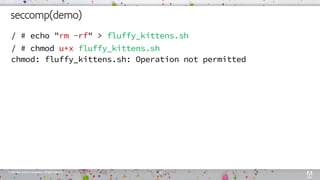
seccomp(demo)
cat seccomp-profile.json
{
"defaultAction": "SCMP_ACT_ALLOW",
"syscalls": [
{
"name": "chown",
"action": "SCMP_ACT_ERRNO"
},
{
"name": "chmod",
"action": "SCMP_ACT_ERRNO"
}
]
}
17](https://image.slidesharecdn.com/securingcontainers-180619035957/85/Securing-containers-17-320.jpg)