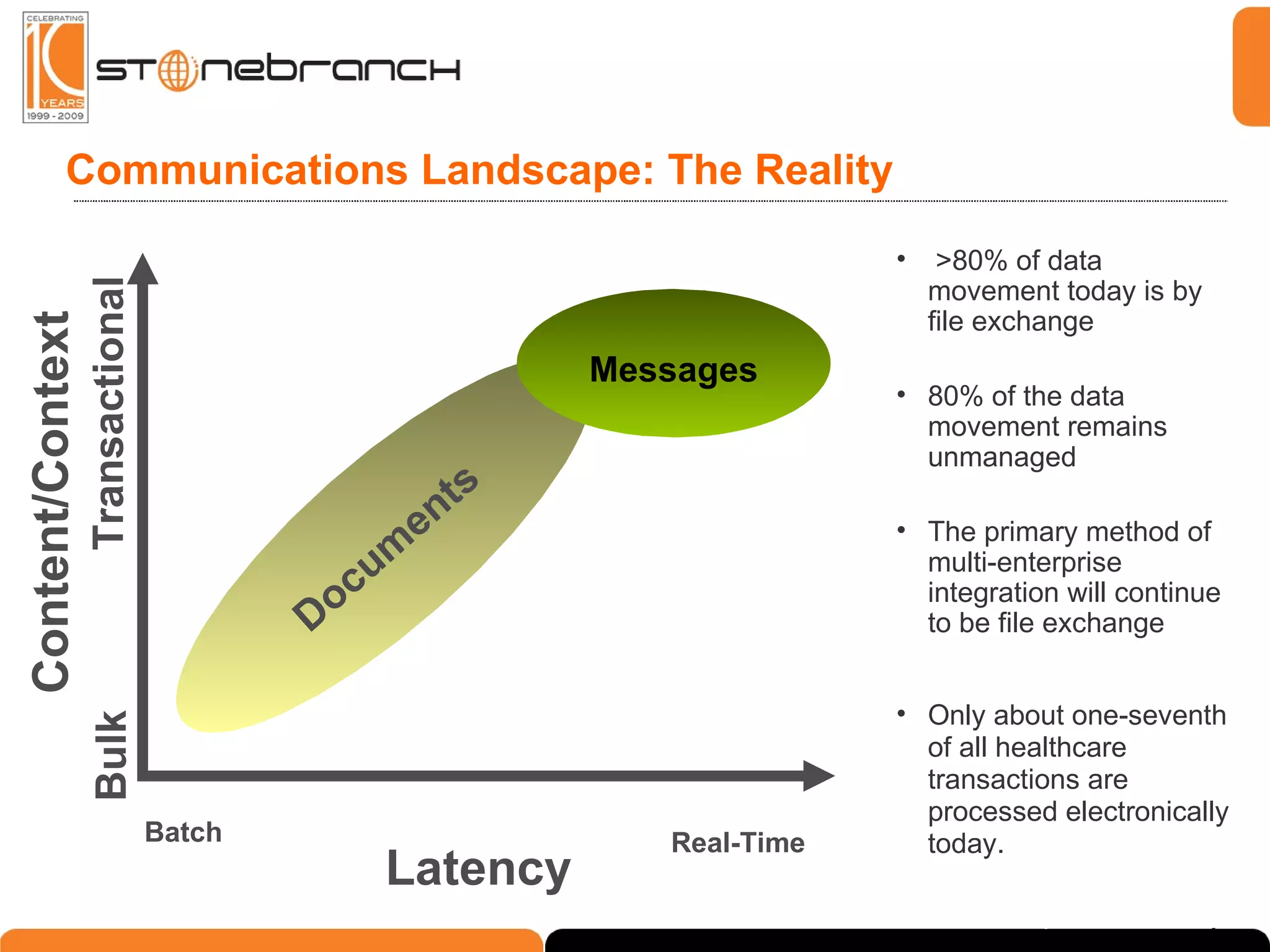
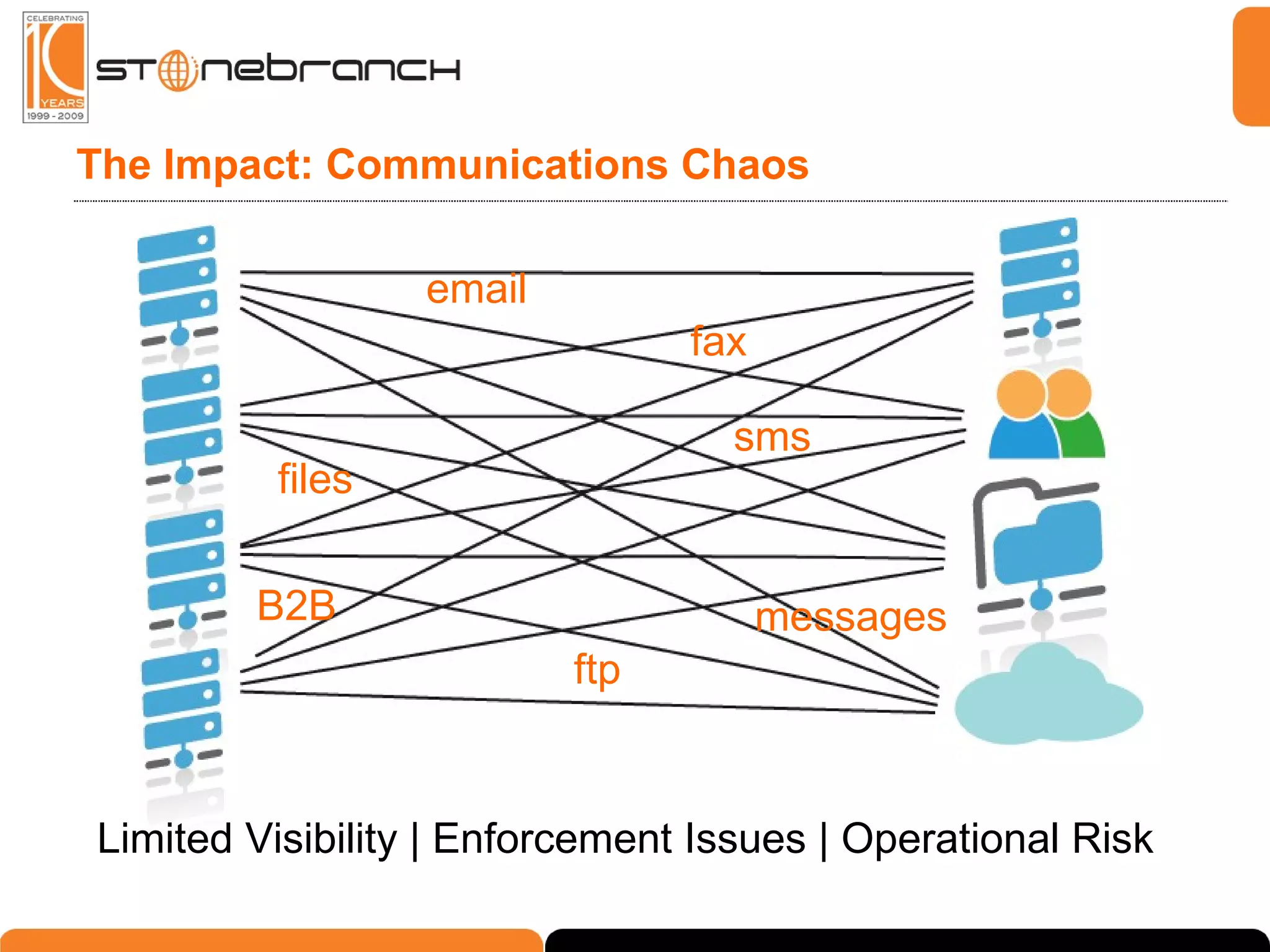
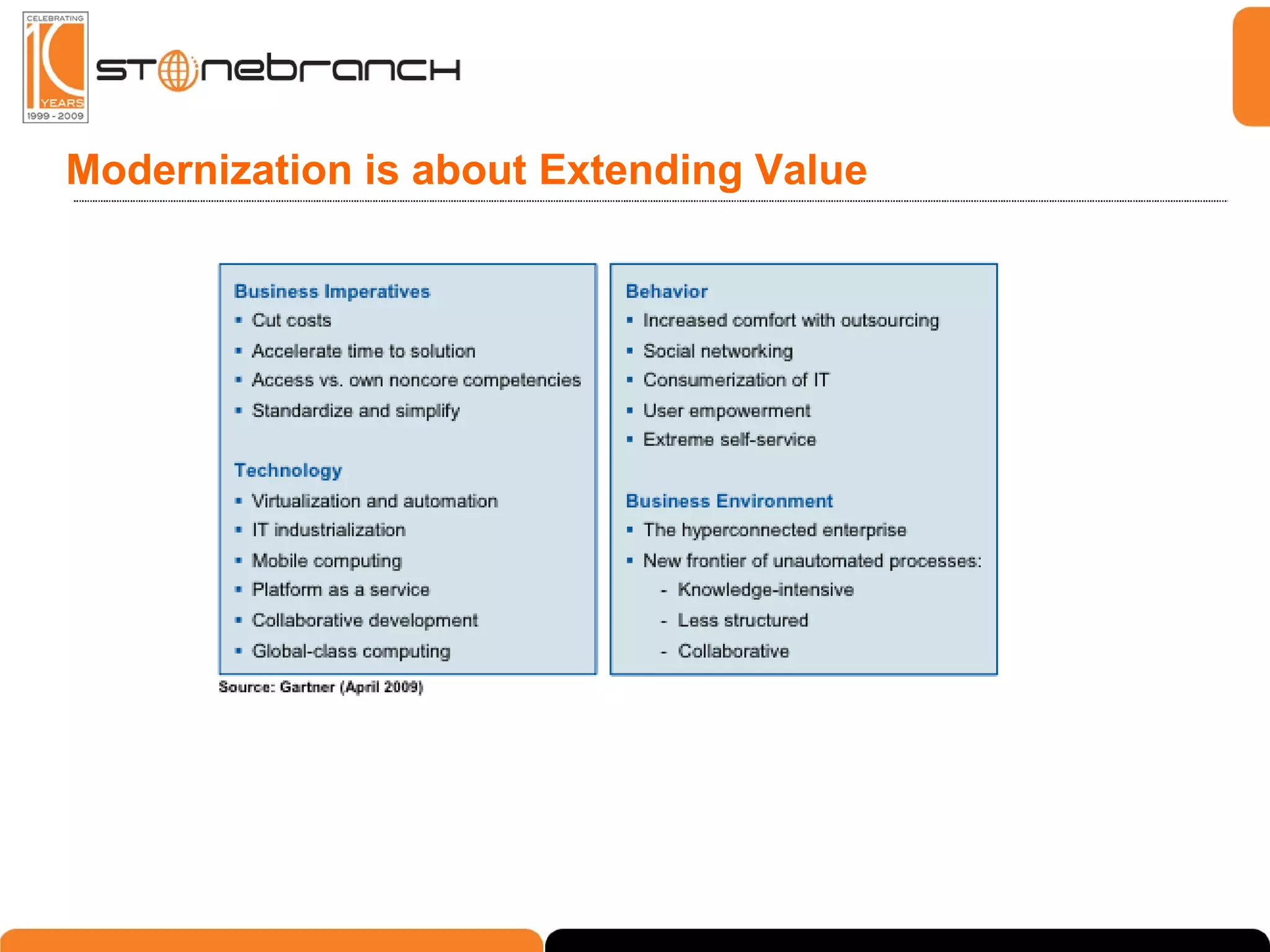
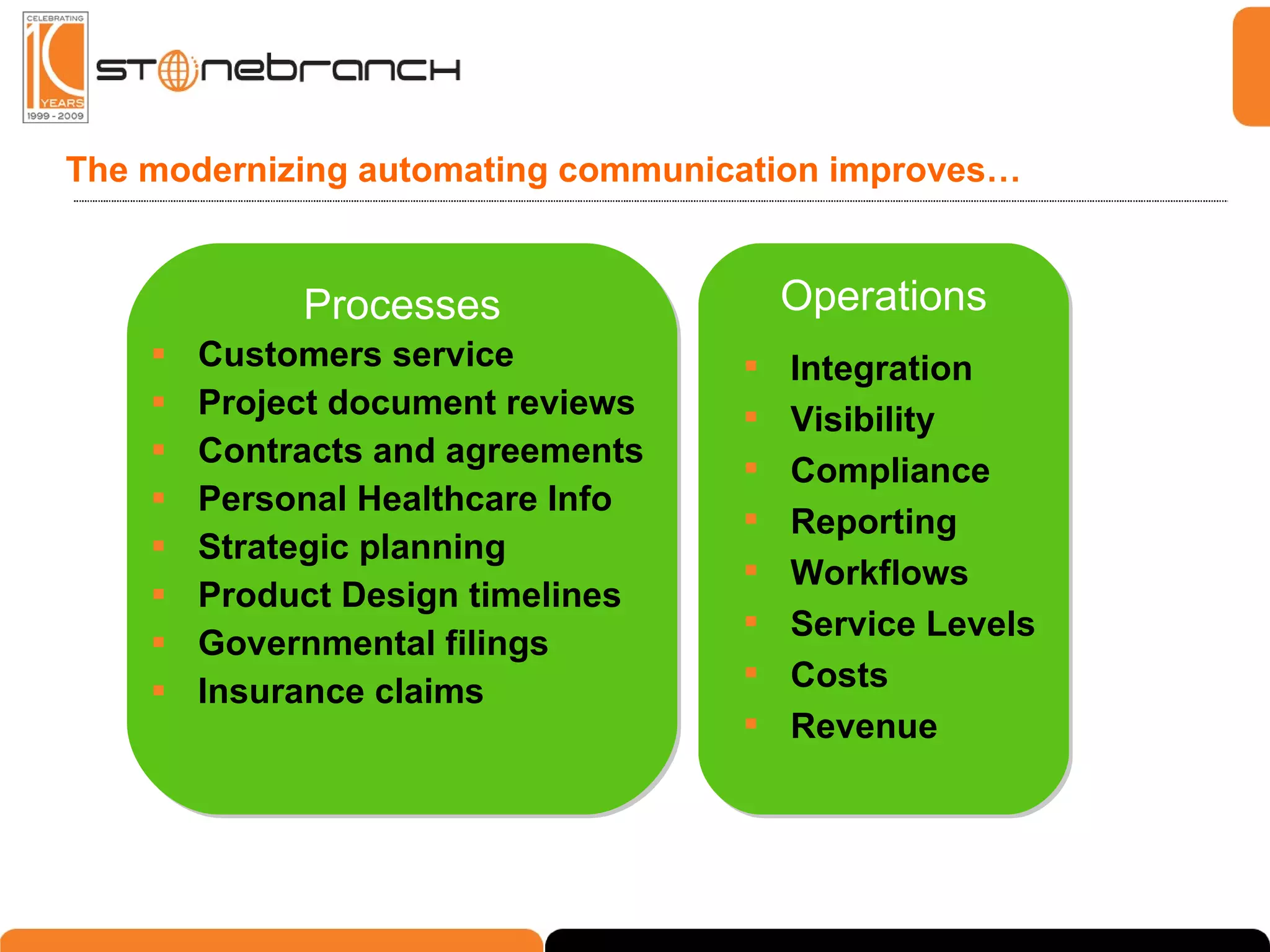
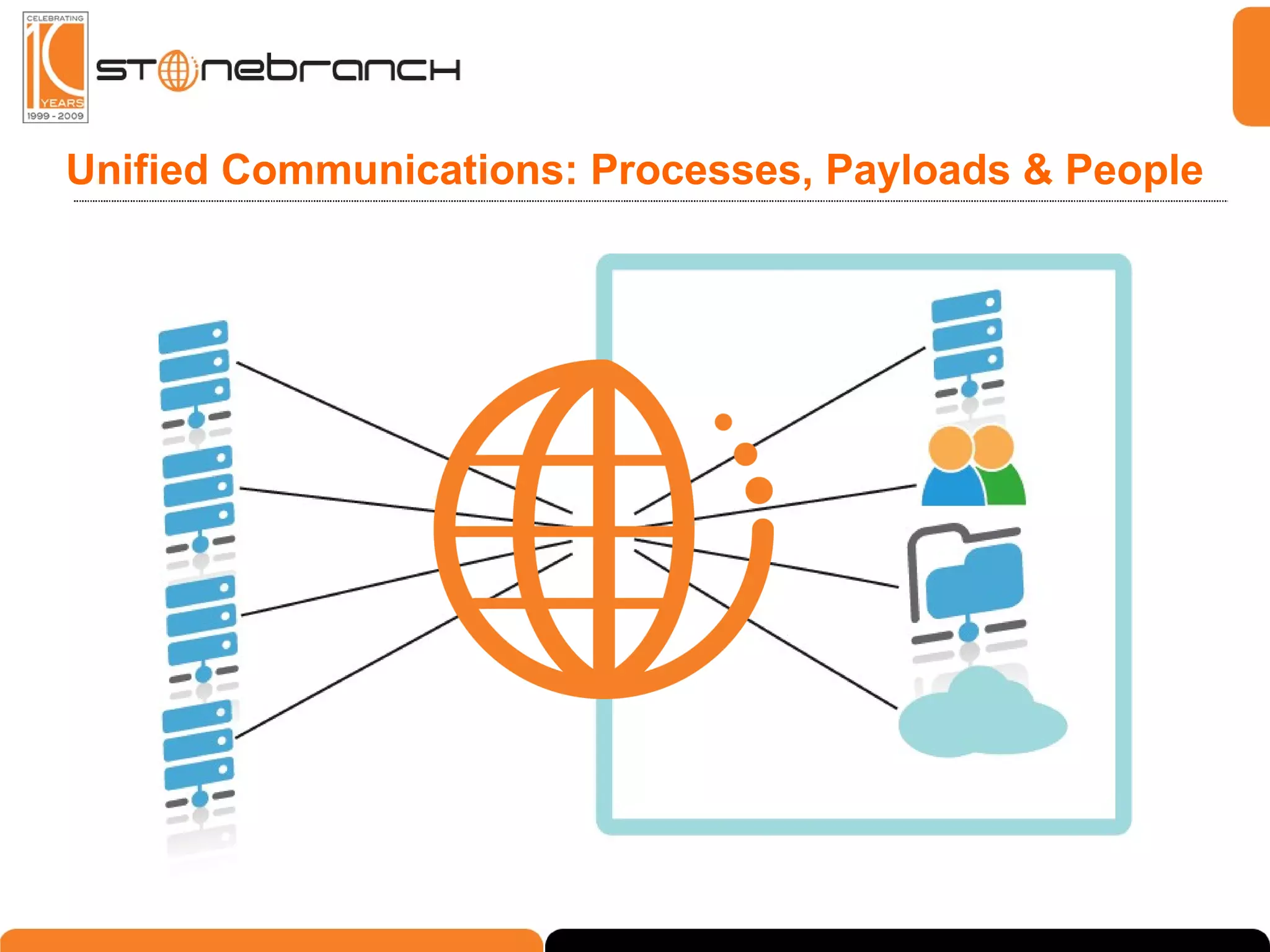
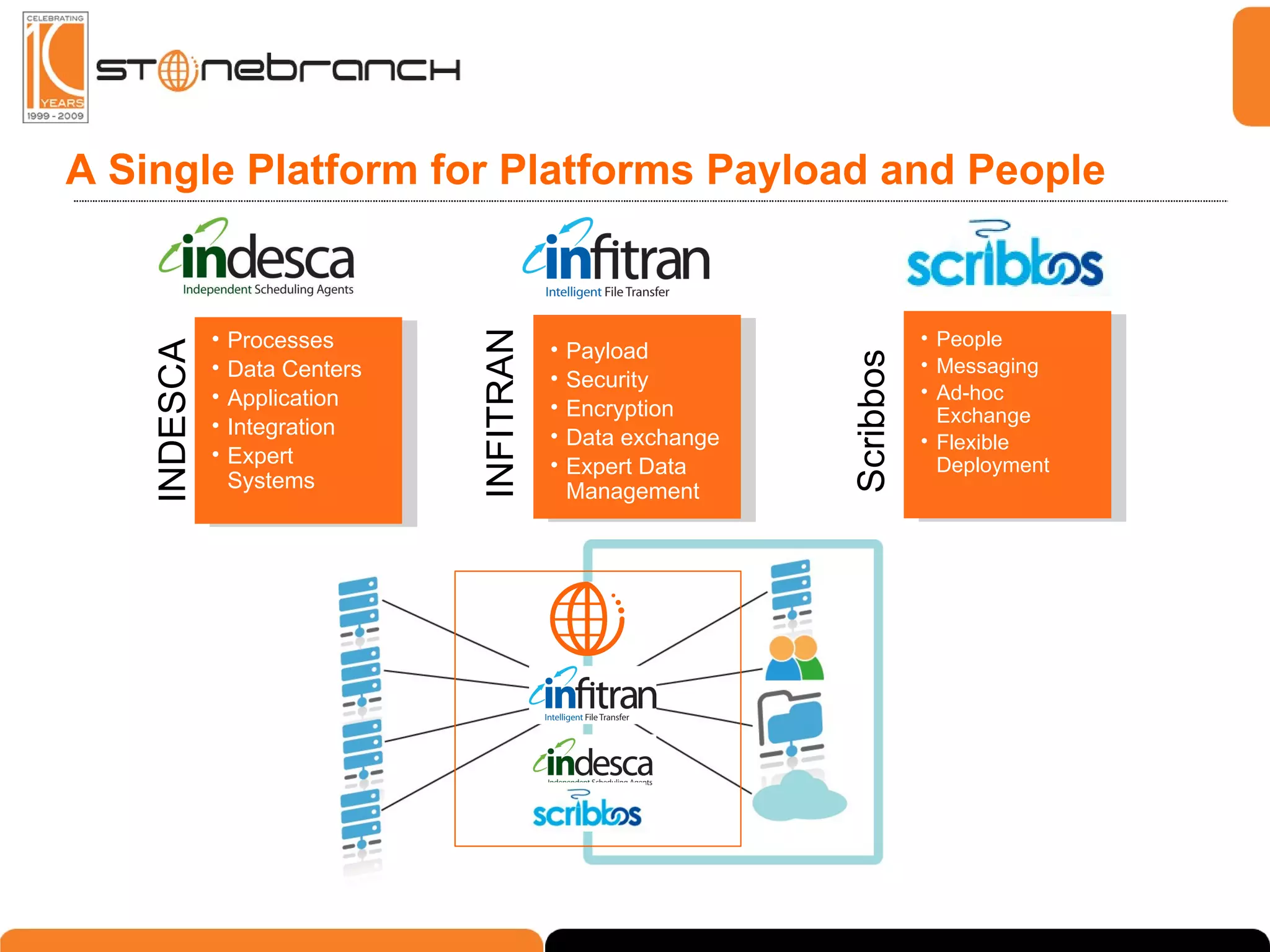
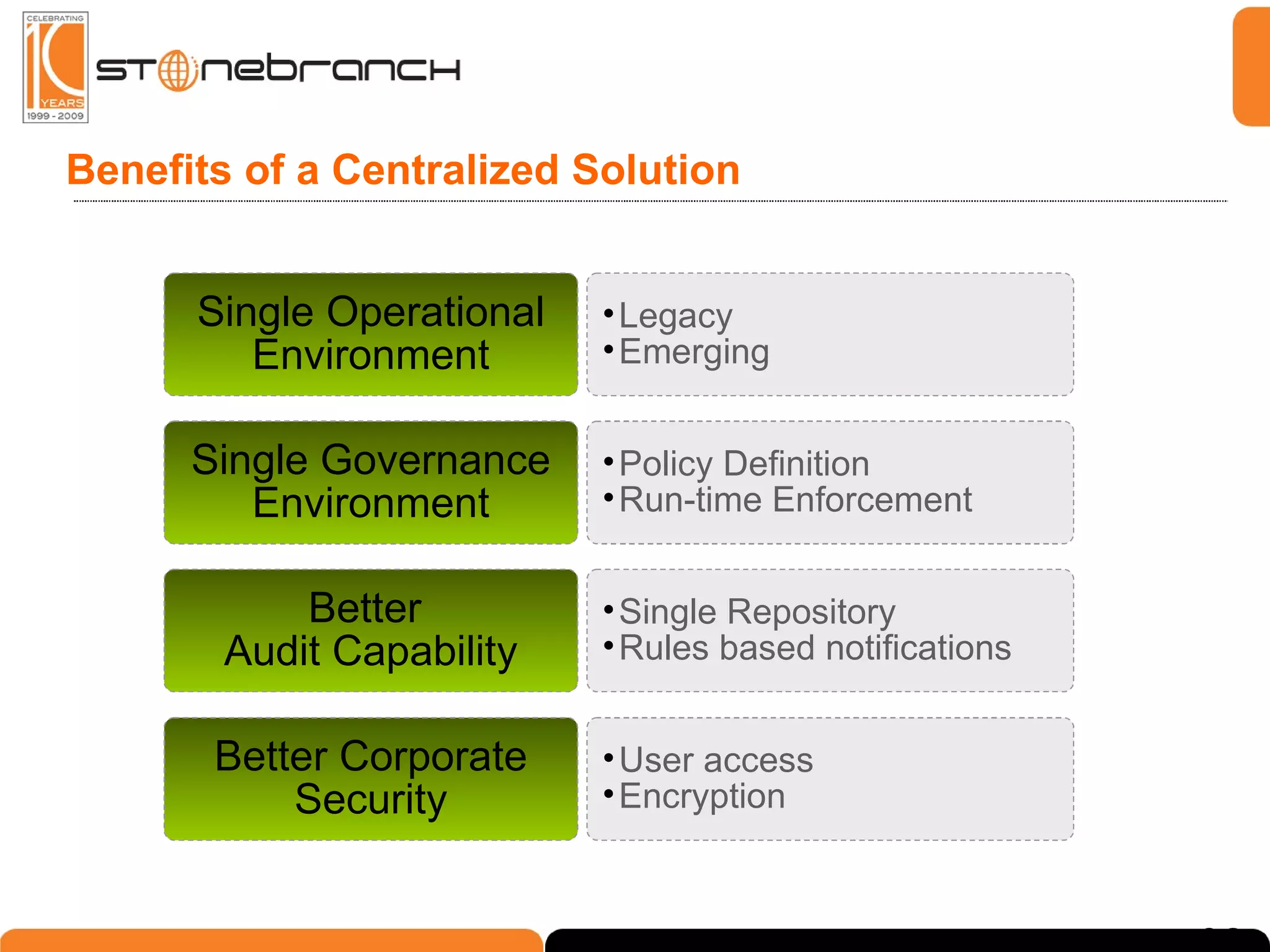
The document discusses the complexities and challenges in modern business and IT communication, emphasizing the need for secure file transfer and compliance in an evolving landscape. It highlights issues like operational risks, data breaches, and the necessity for modernization in IT communication practices to enhance business processes. Additionally, the text stresses the merging of business and IT compliance, advocating for centralized solutions to improve governance and security.