Secure Shell (SSH) and Domain Name Server (DNS)
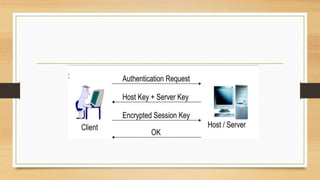
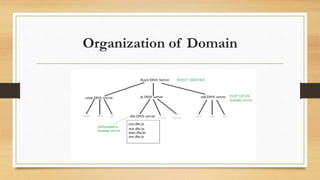
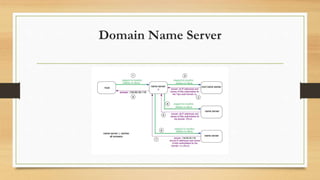
SSH provides strong encryption and authentication for remote login, command execution, and file transfer between machines. DNS is a distributed database that maps domain names to IP addresses through a hierarchy of name servers. It allows clients to find IP addresses for websites through queries to authoritative DNS servers. DNS organization involves storing records with domain names, IP addresses, and time-to-live information in a tree-like structure maintained across root, top-level, and authoritative name servers.