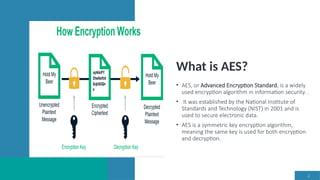
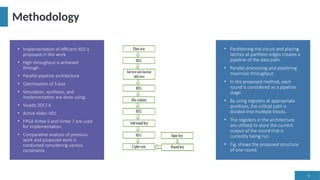
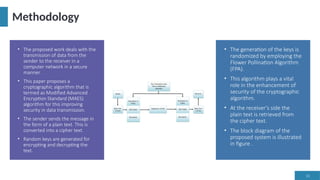
The document discusses the Advanced Encryption Standard (AES) and its application in securing cloud computing data. It highlights the efficiency, speed, and security features of AES, along with methodologies for implementing AES in various contexts, including selective encryption and modifications for enhanced data transmission. Overall, it concludes that AES and its variants provide robust solutions for data security challenges in cloud environments.