Embed presentation
Download to read offline

![Enterprise Security Risks
0
20
40
60
80
100
120
Sabotage
Fraud
IP Theft
[2] An Analysis of Technical Observations in Insider Theft of Intellectual Property Cases by
Michael Hanley, Tyler Dean, Will Schroeder, Matt Houy,Randall F. Trzeciak, Joji Montelibano in
CMU Technical Note CMU/SEI-2011-TN-006](https://image.slidesharecdn.com/satark-130525071142-phpapp01/75/Satark-2-2048.jpg)
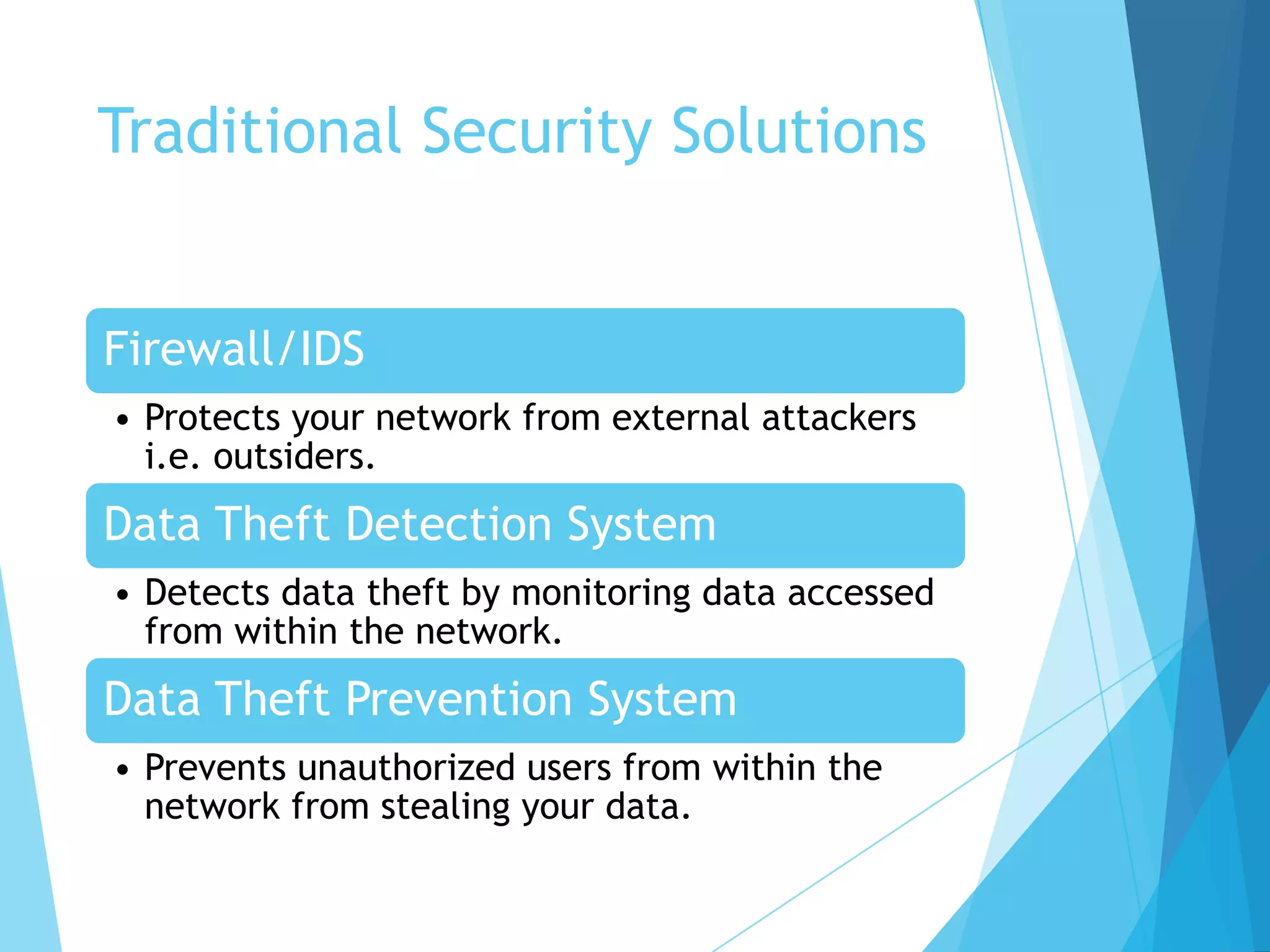



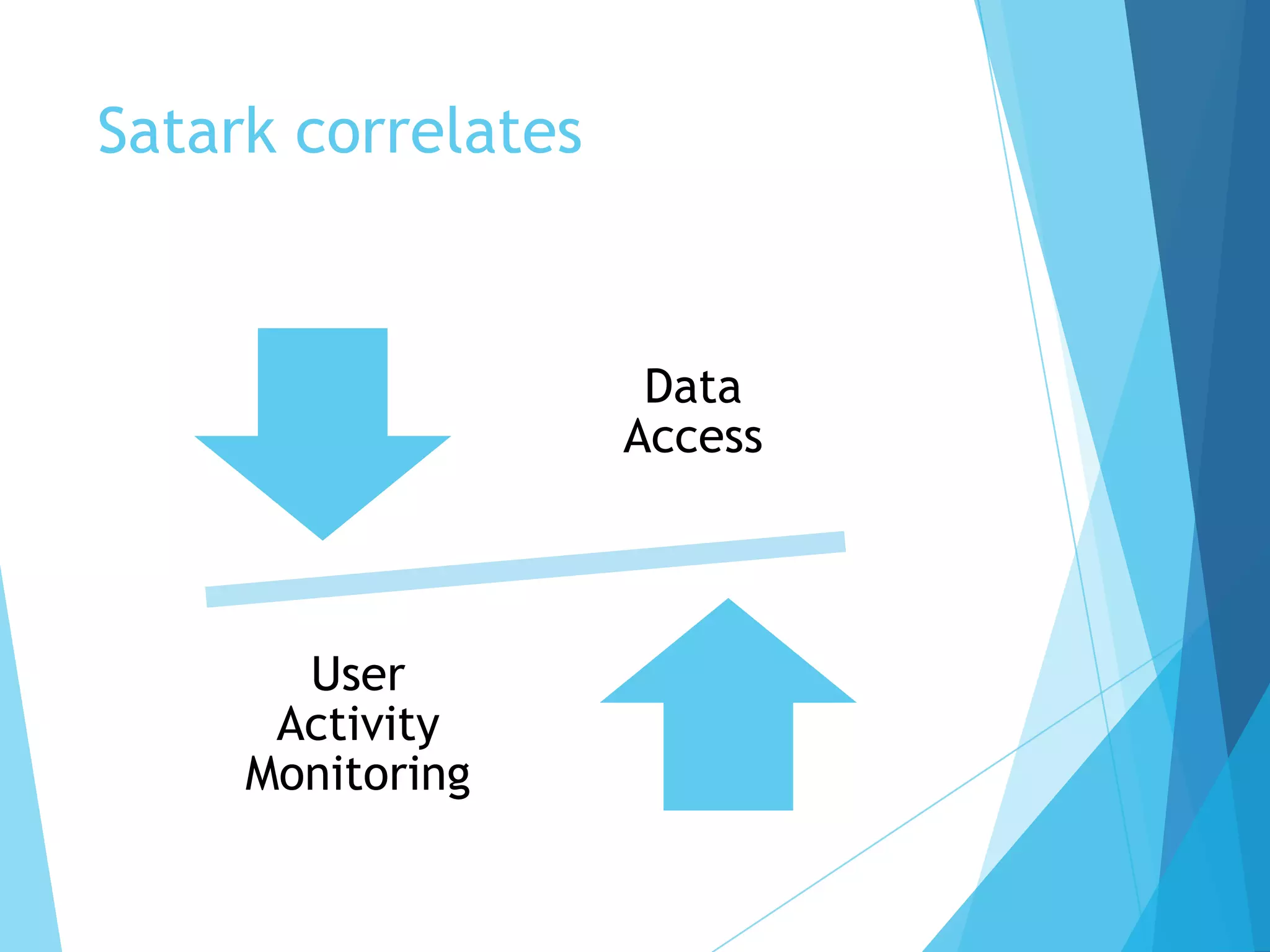
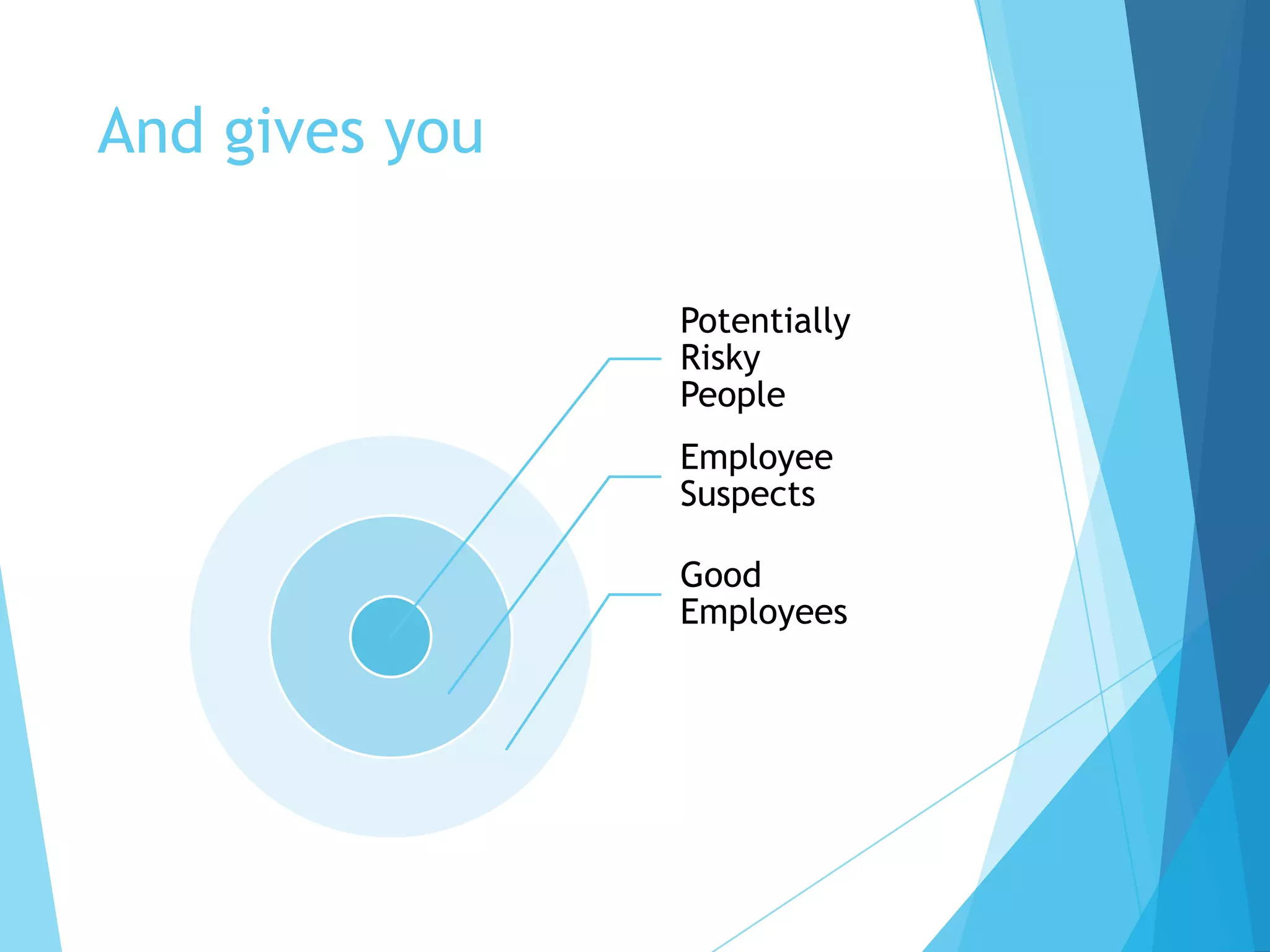



This document discusses cyber security solutions for enterprises and introduces Satark, a new insider threat detection system. Traditional solutions like firewalls and intrusion detection protect against external attackers but not insider threats. Insiders with access to critical information pose risks if they become disgruntled. Satark monitors user activity and data access to identify potentially risky employees before they can execute an attack, allowing threats to be caught early. It correlates this information anonymously while complying with relevant data protection acts.

![Enterprise Security Risks
0
20
40
60
80
100
120
Sabotage
Fraud
IP Theft
[2] An Analysis of Technical Observations in Insider Theft of Intellectual Property Cases by
Michael Hanley, Tyler Dean, Will Schroeder, Matt Houy,Randall F. Trzeciak, Joji Montelibano in
CMU Technical Note CMU/SEI-2011-TN-006](https://image.slidesharecdn.com/satark-130525071142-phpapp01/75/Satark-2-2048.jpg)







