Embed presentation


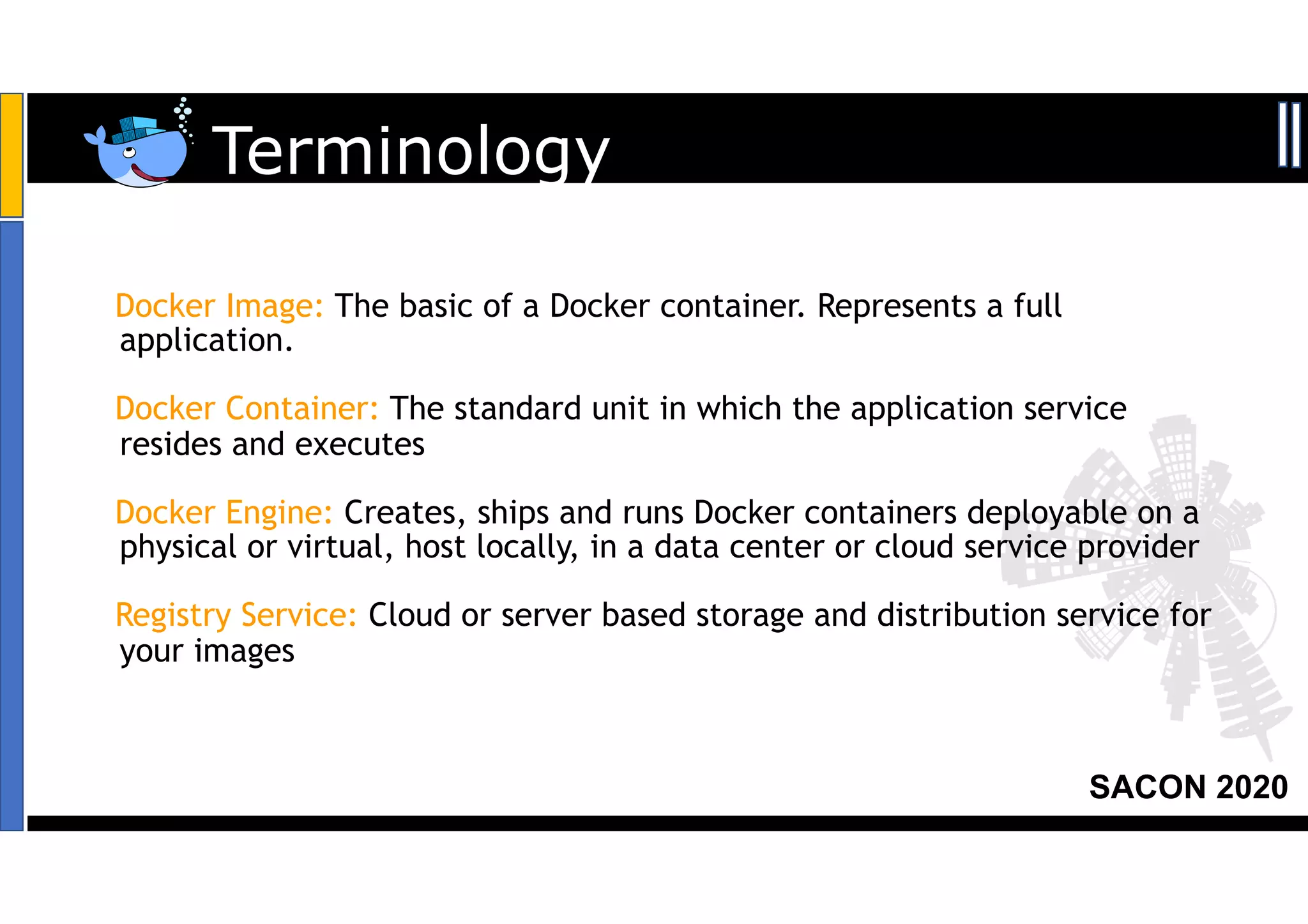
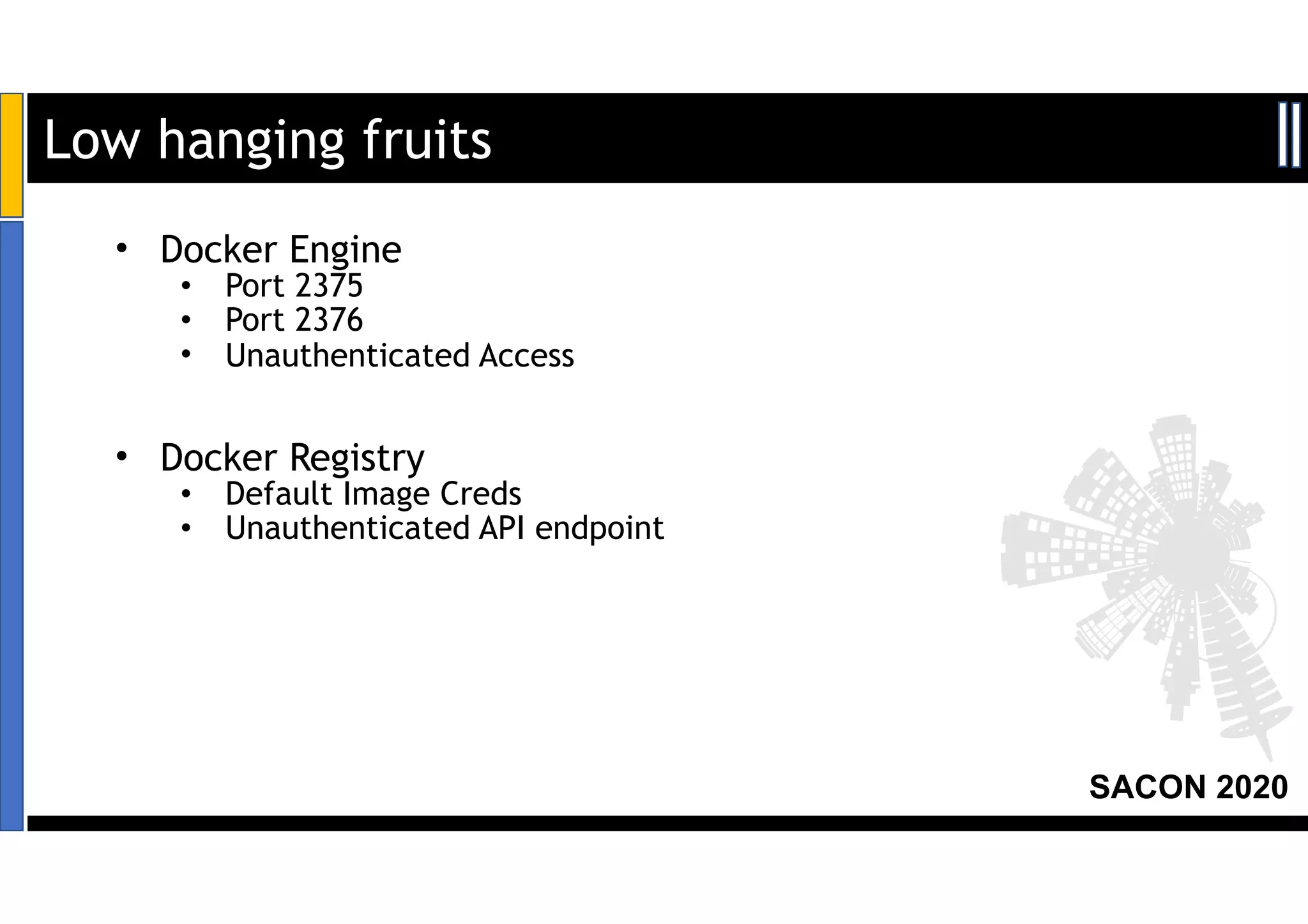
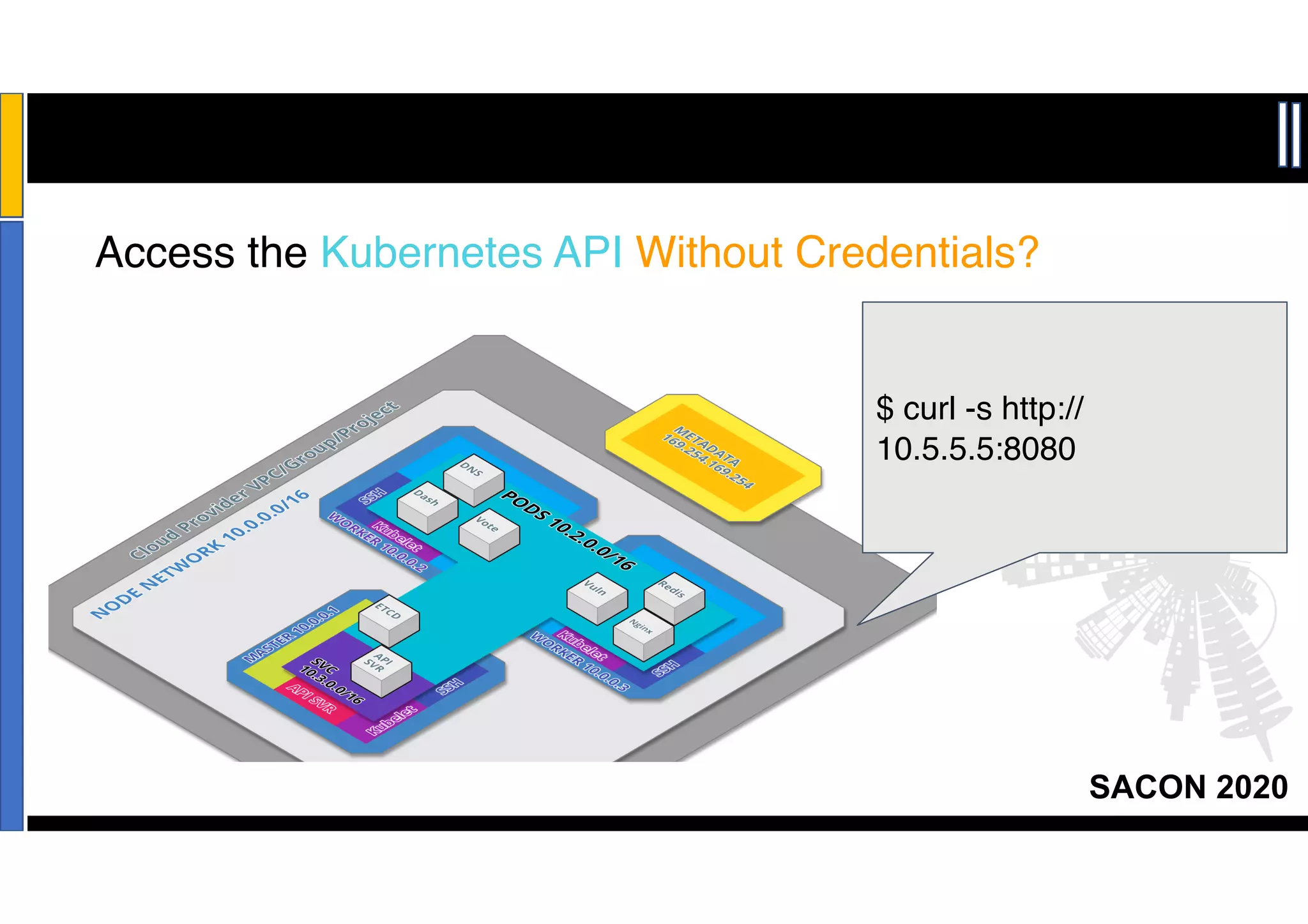
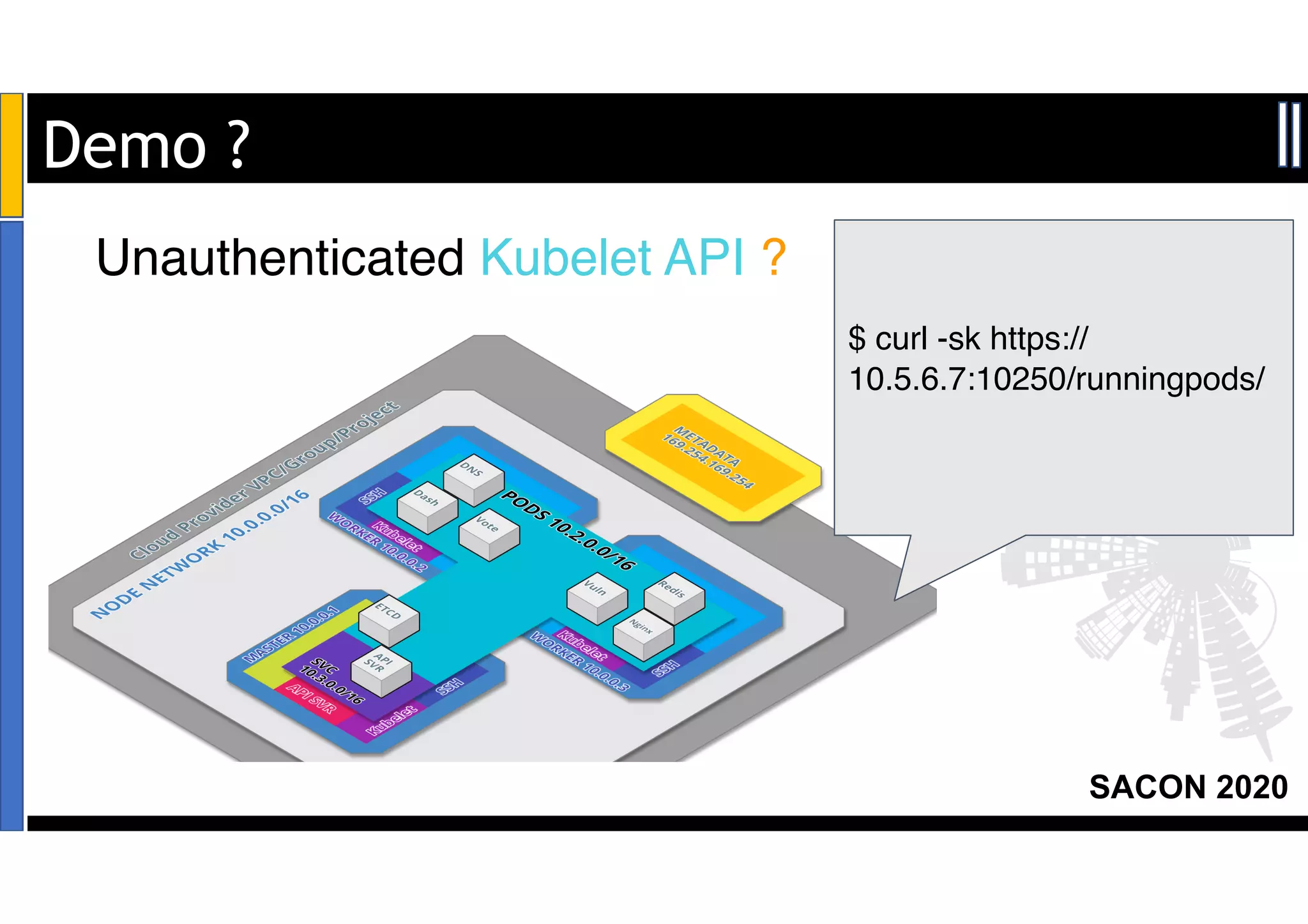
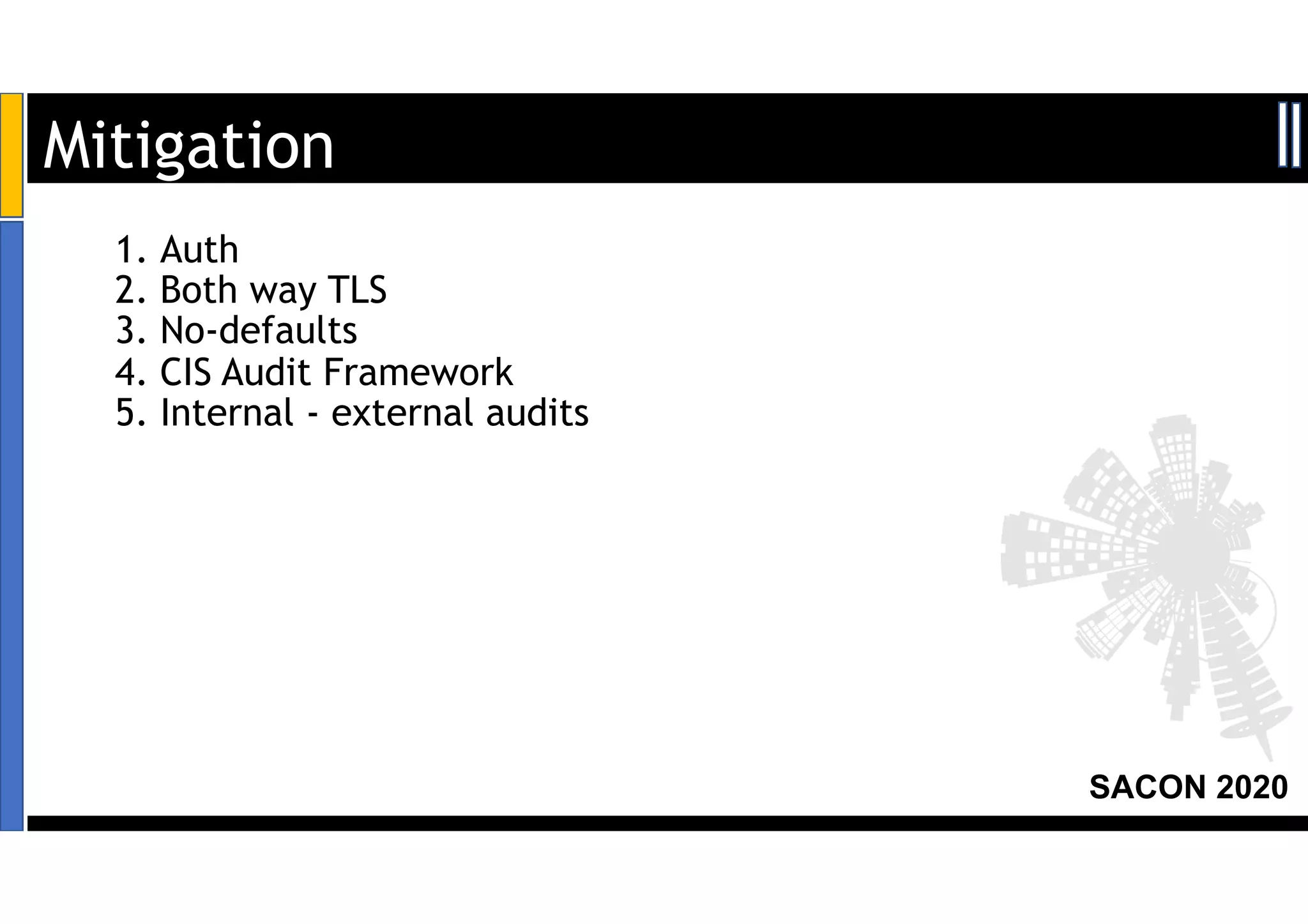
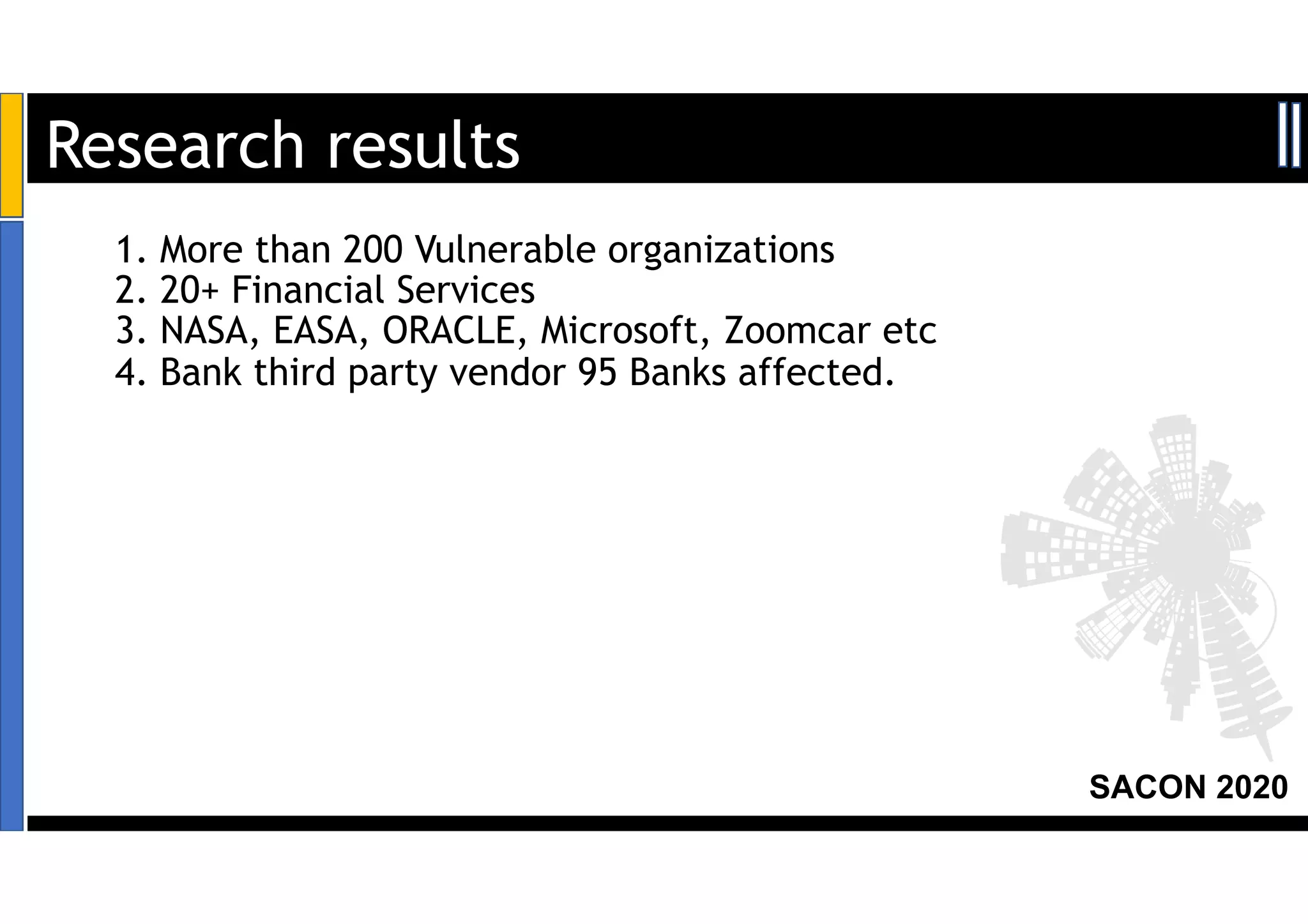

The SACON 2020 event focused on hacking and securing Kubernetes and Docker, featuring hands-on demonstrations by Apoorv Raj Saxena, a red team researcher. The agenda included discussions on Docker and Kubernetes insecurities, high-risk attacks, and mitigation methods to raise awareness among organizations. Key findings revealed vulnerabilities affecting over 200 organizations, including major financial services and technology companies.












