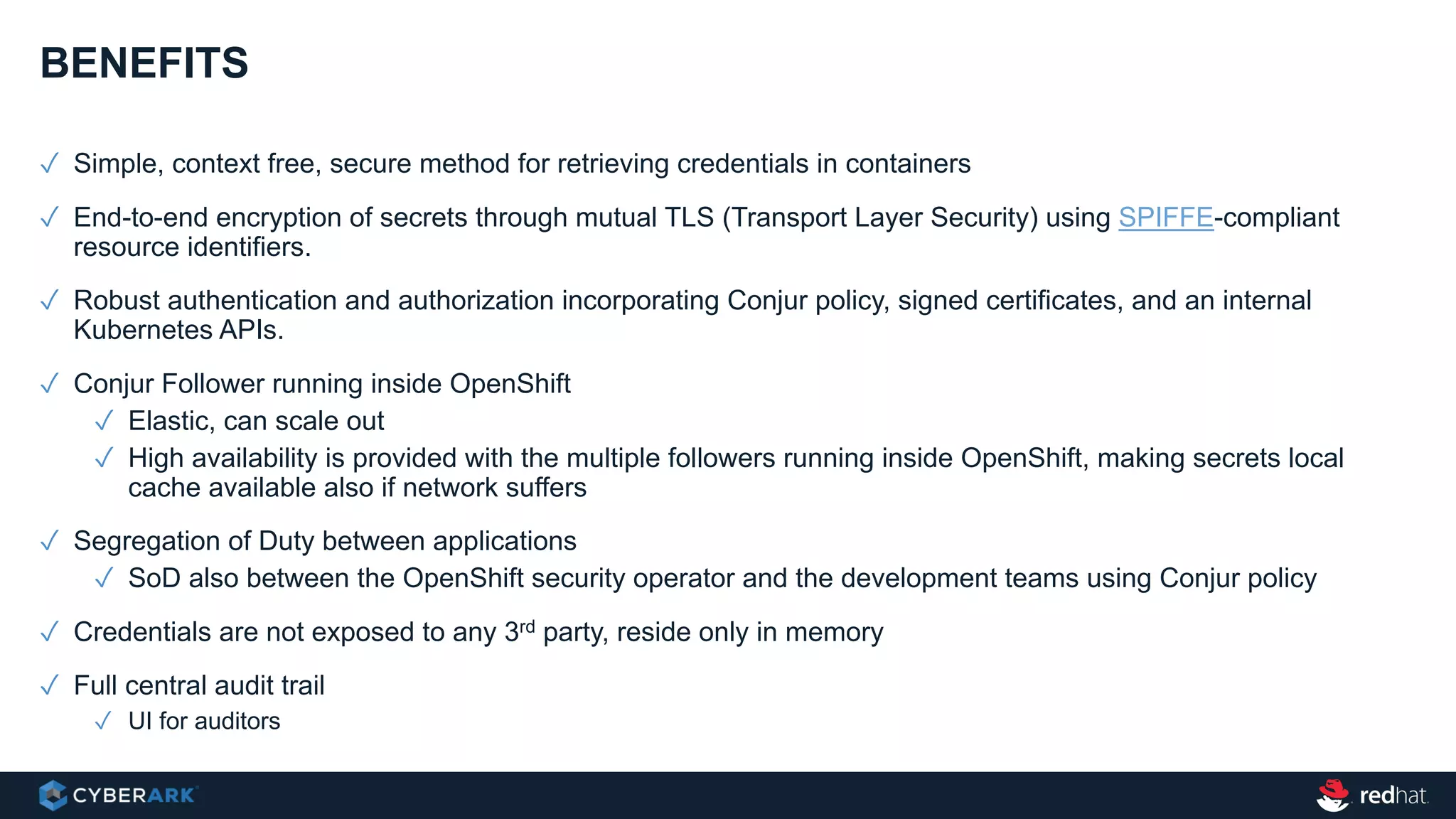
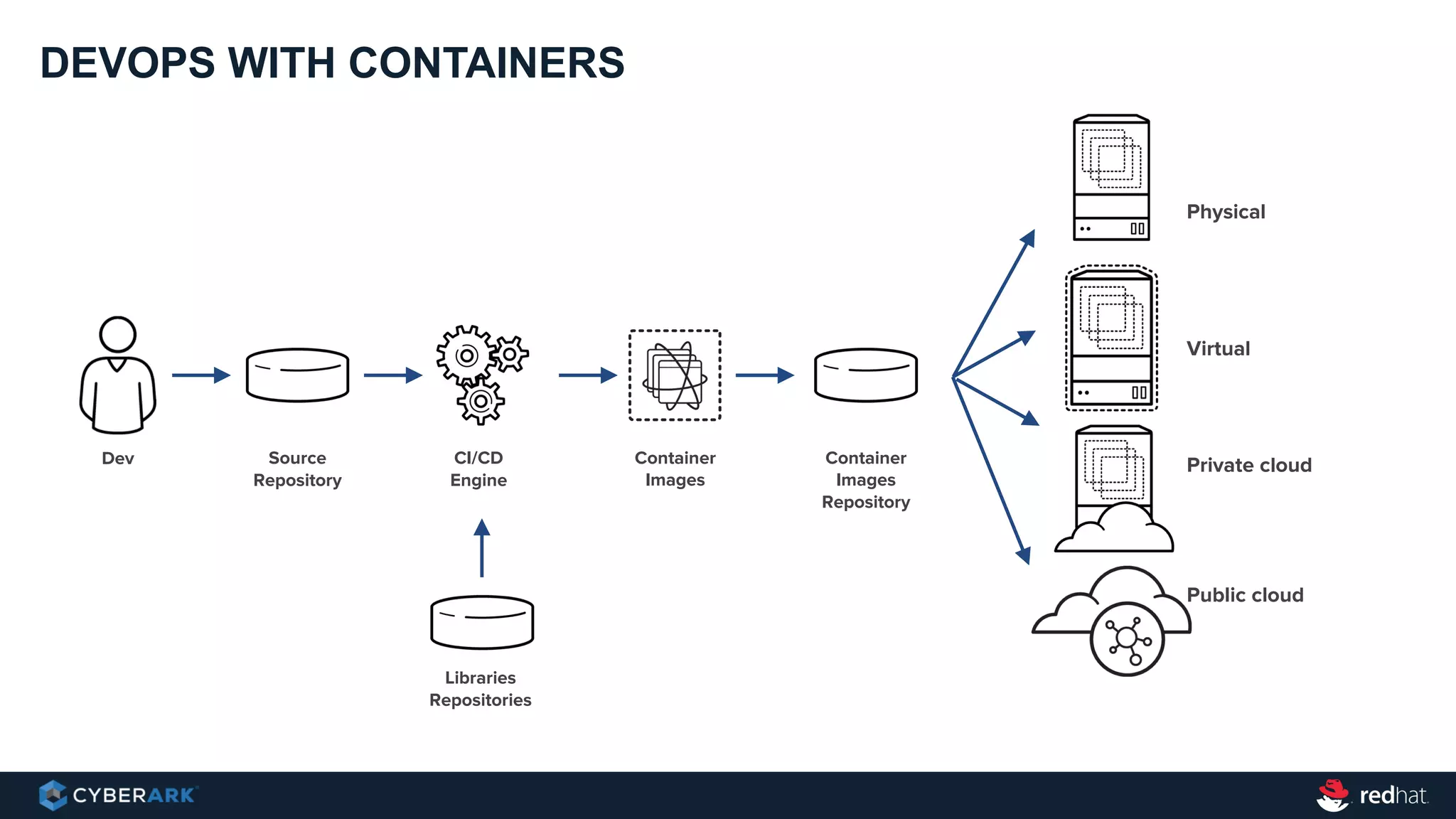
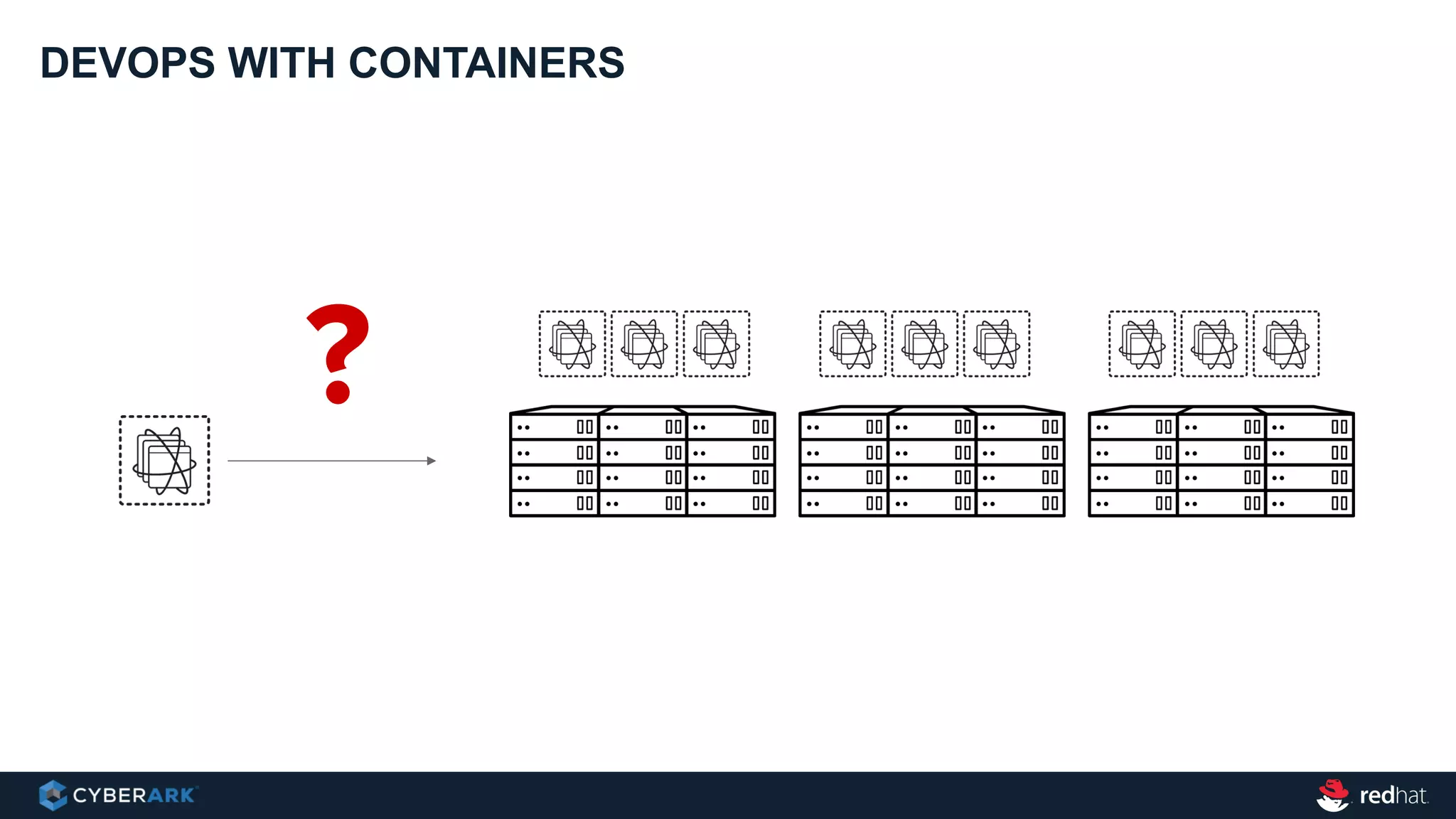
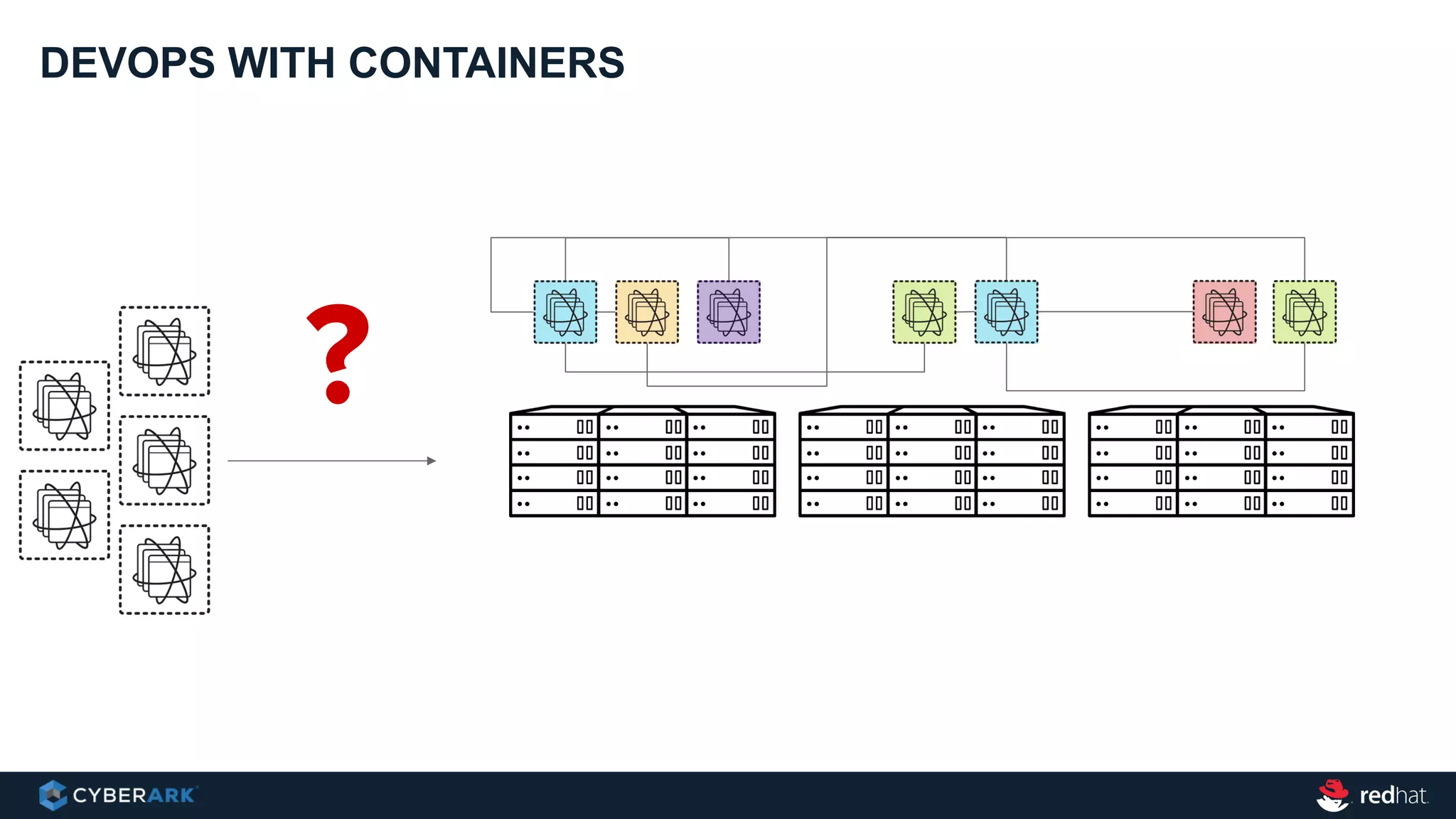
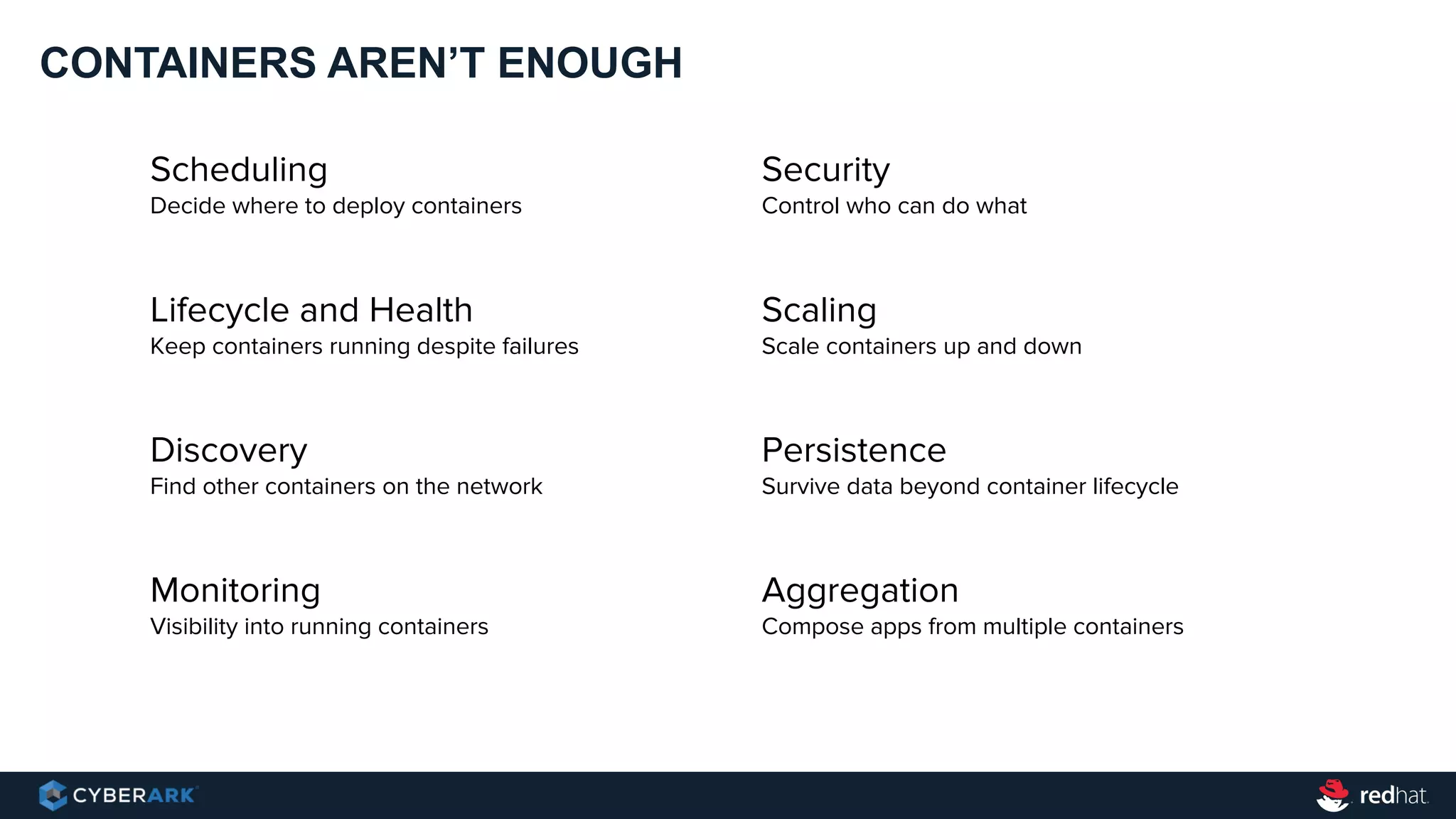
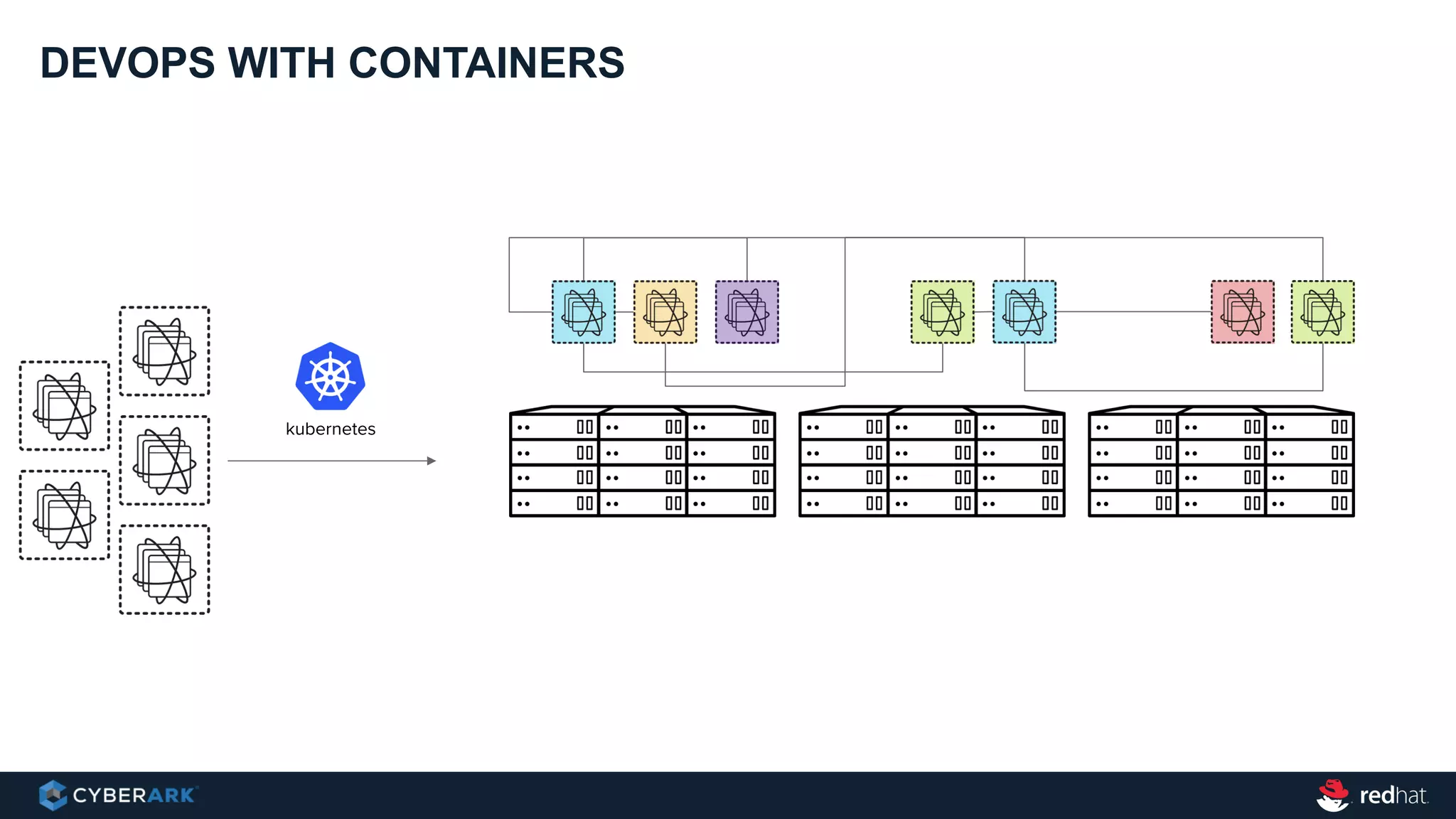
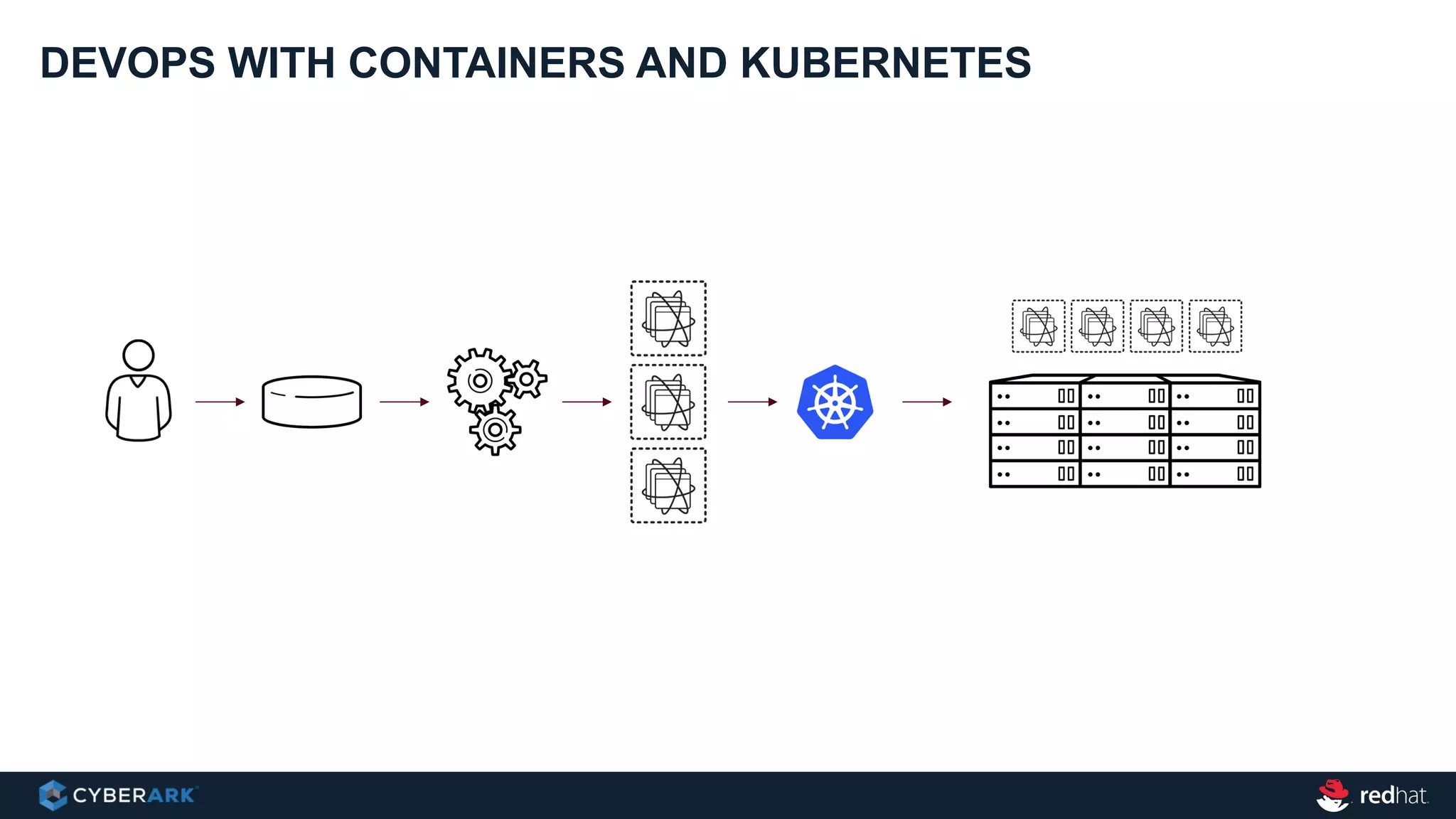
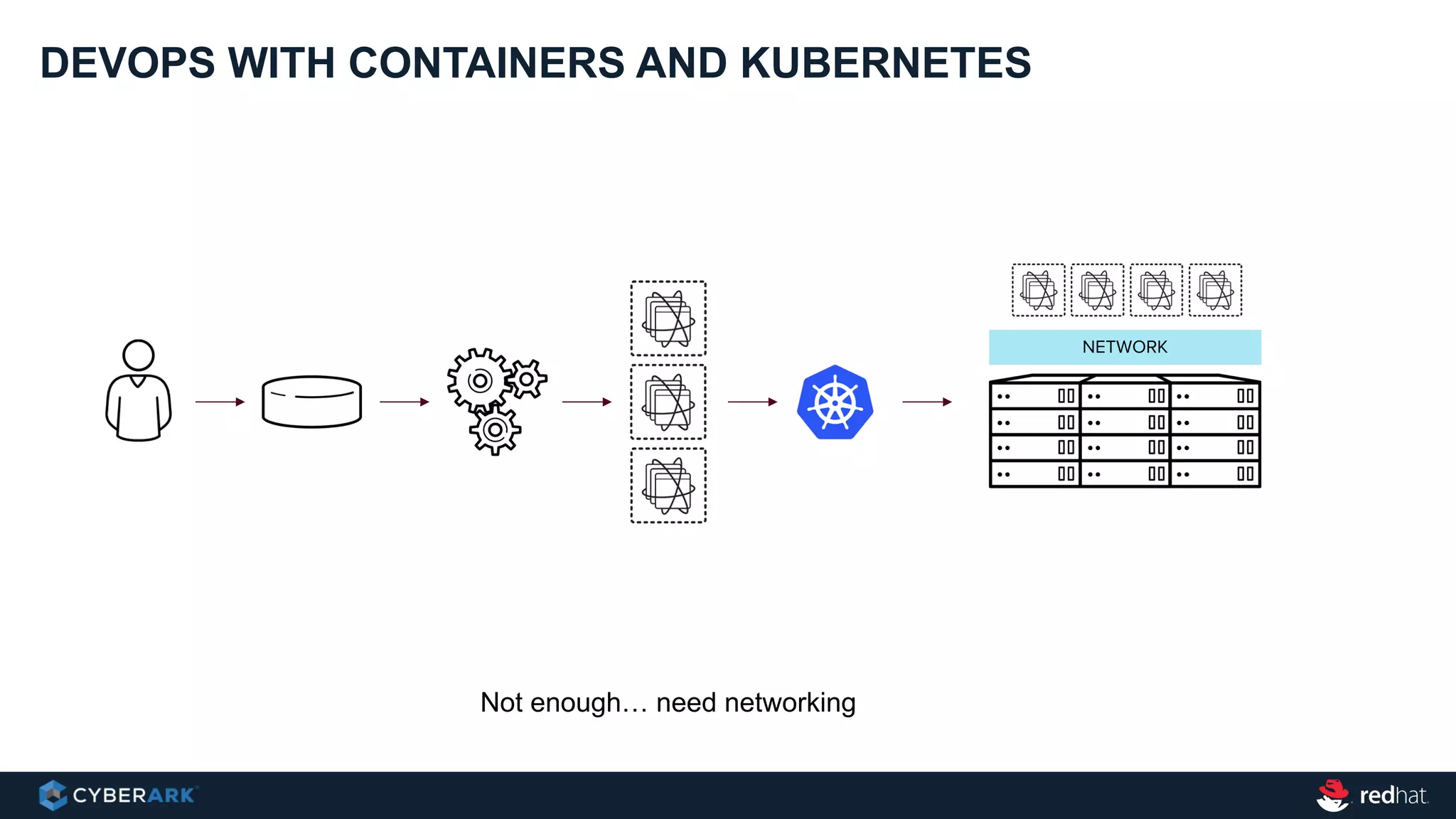
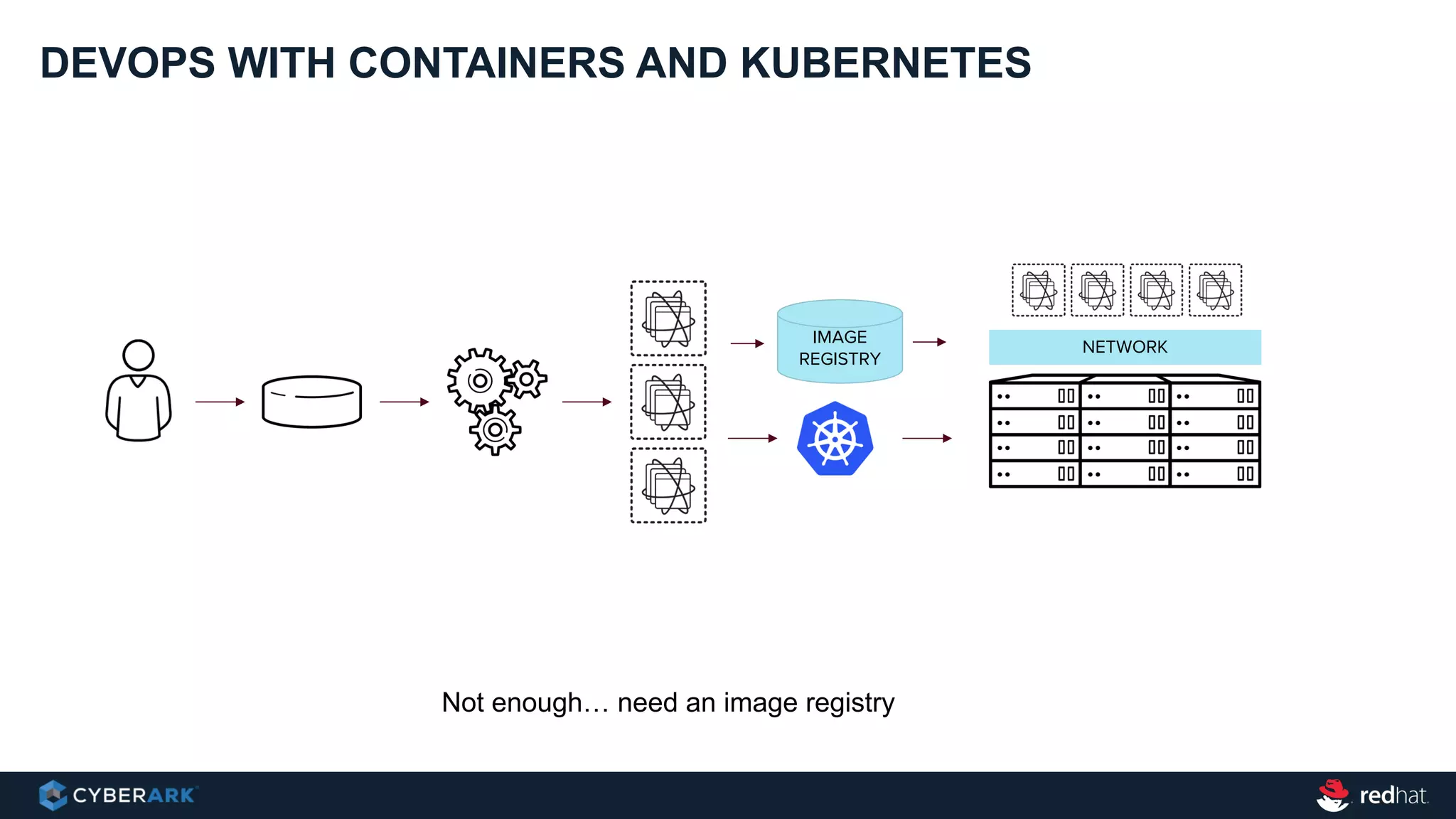
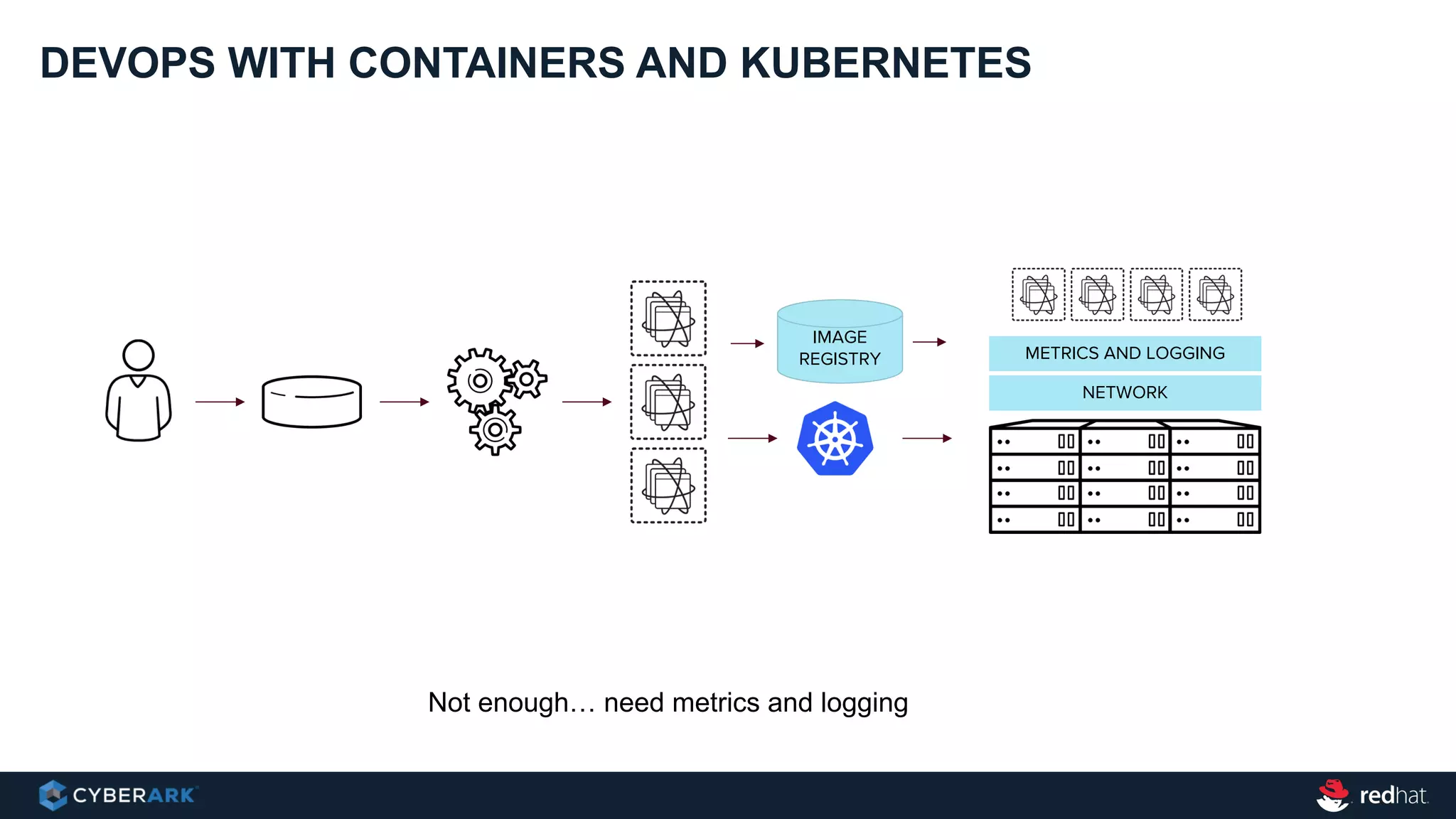
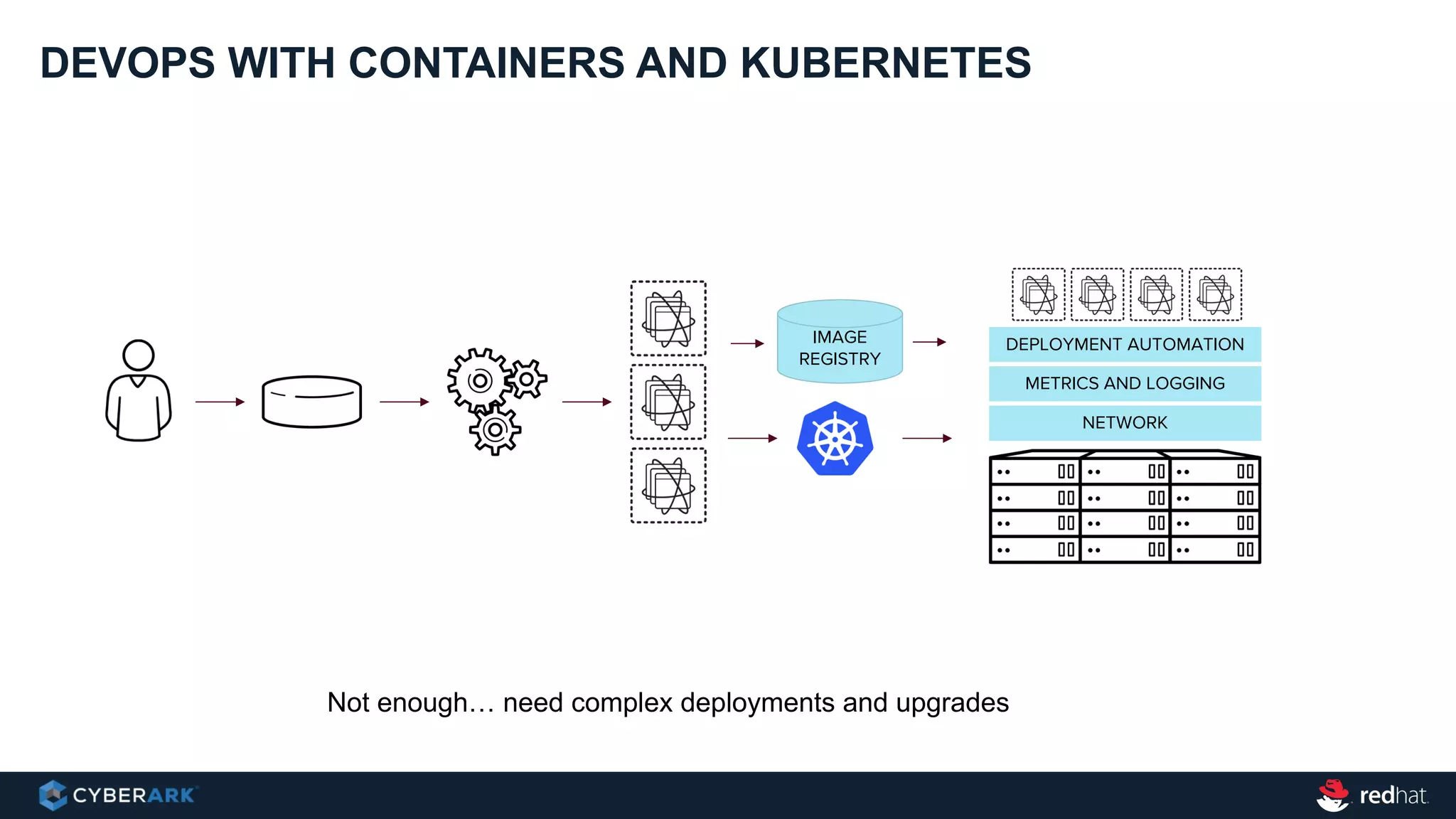
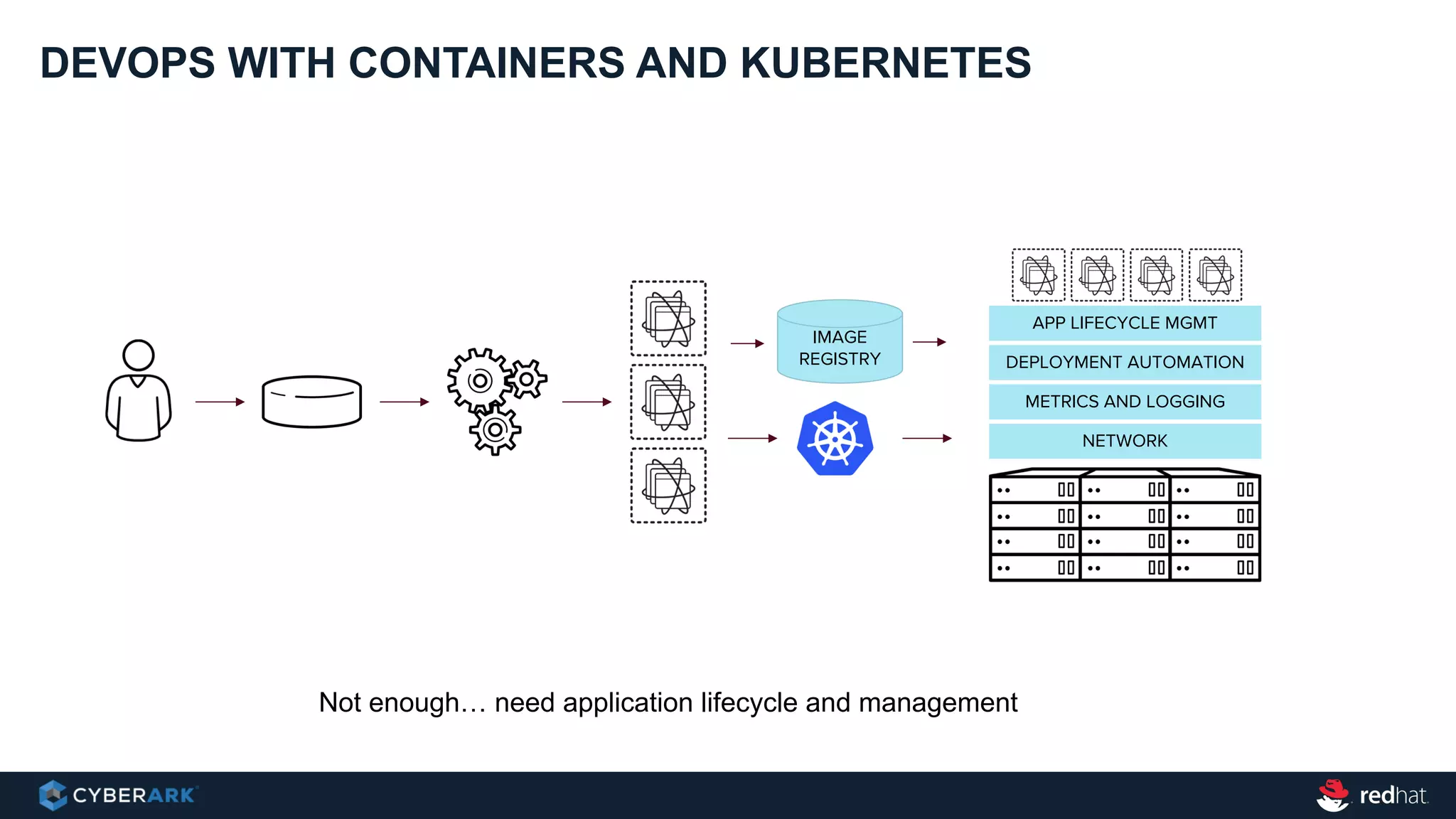
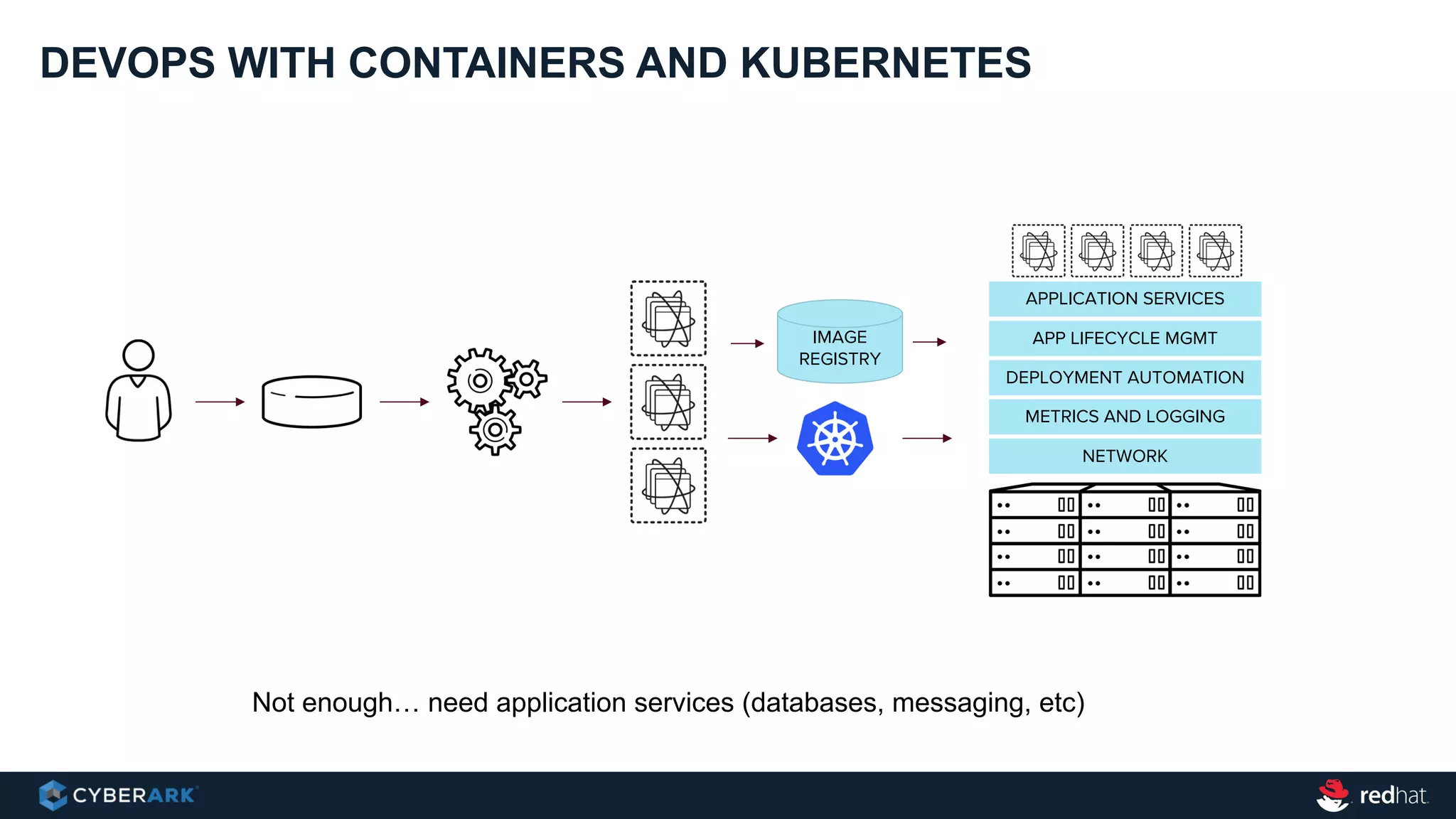
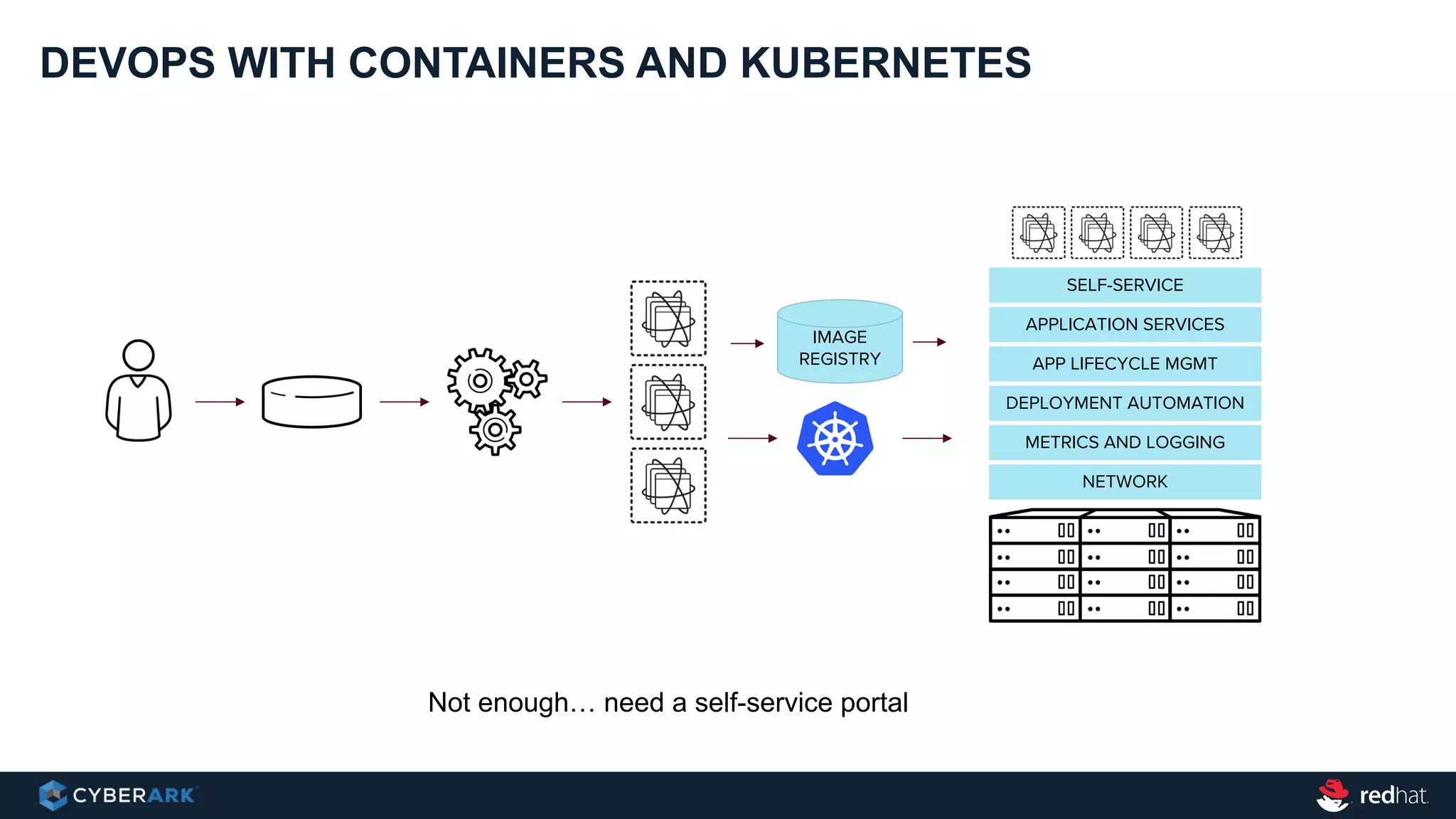
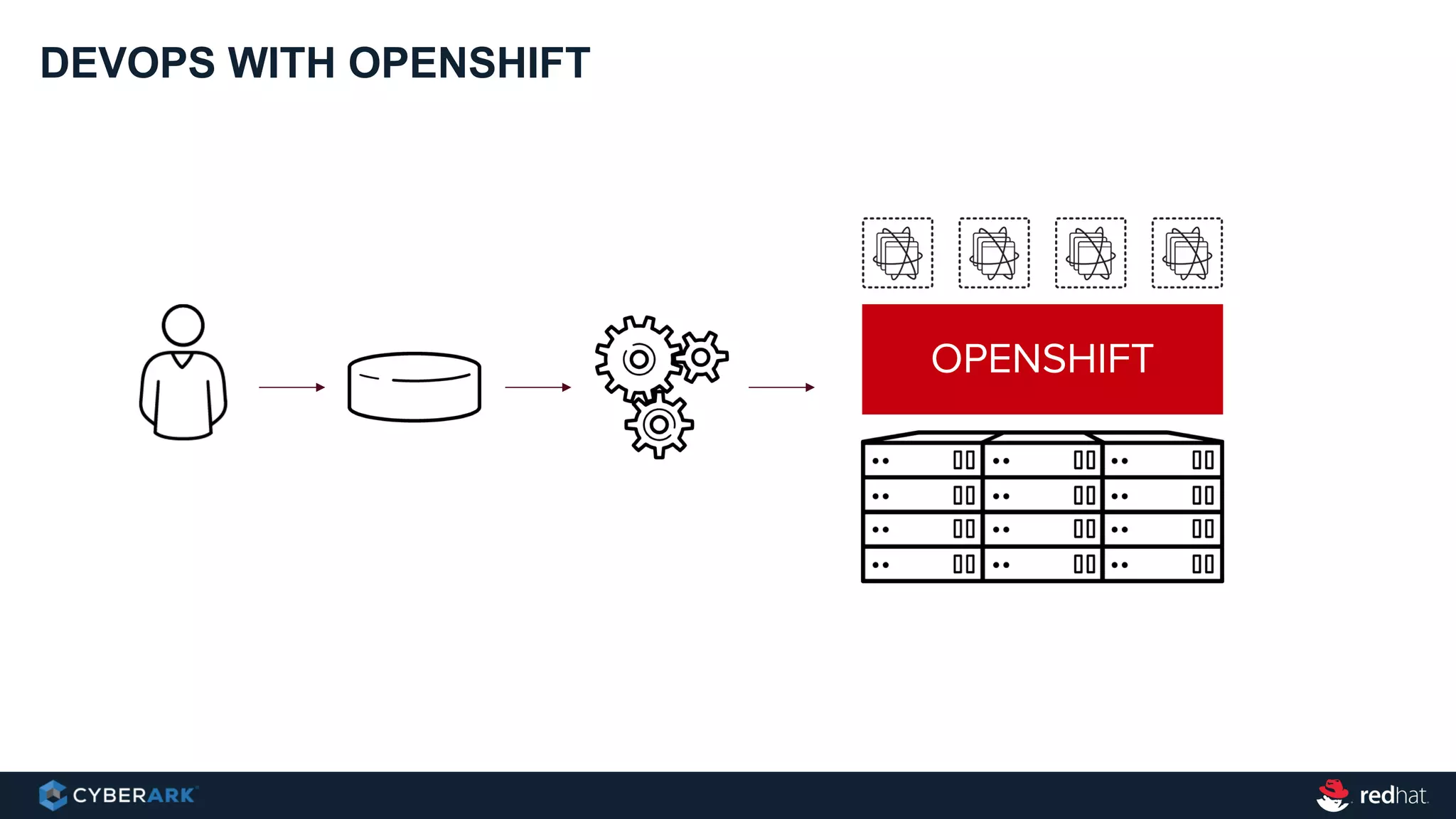
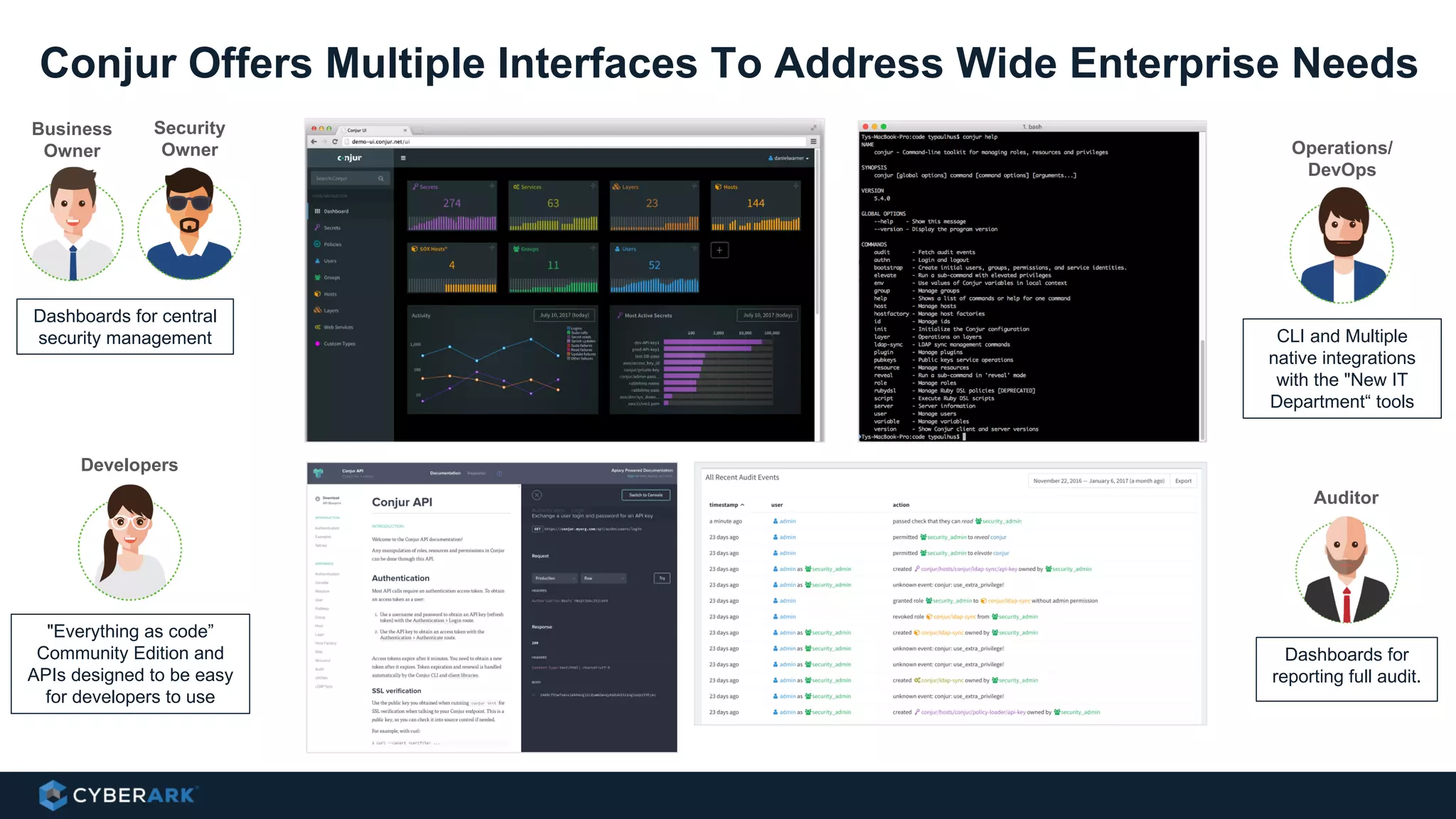
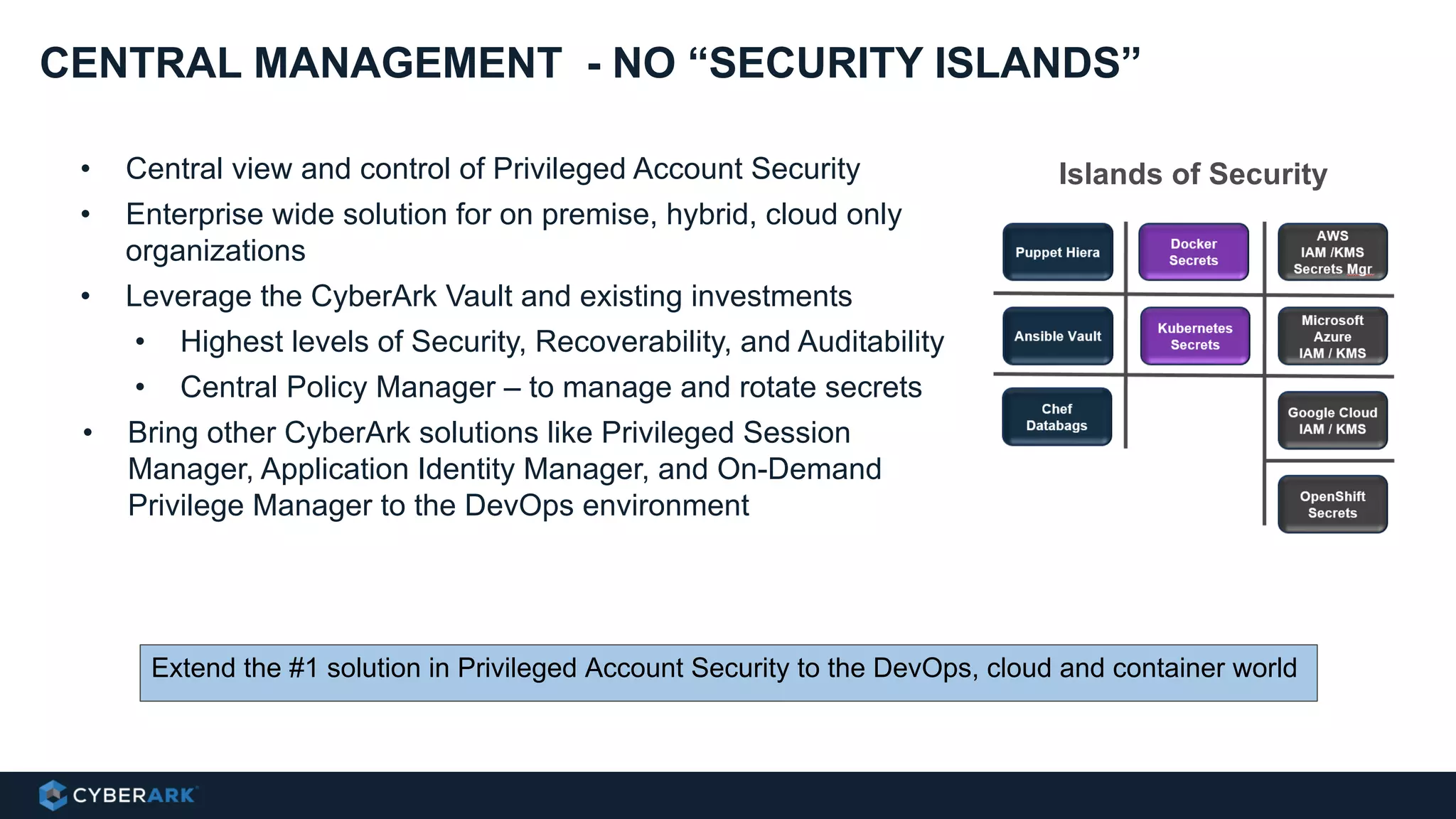
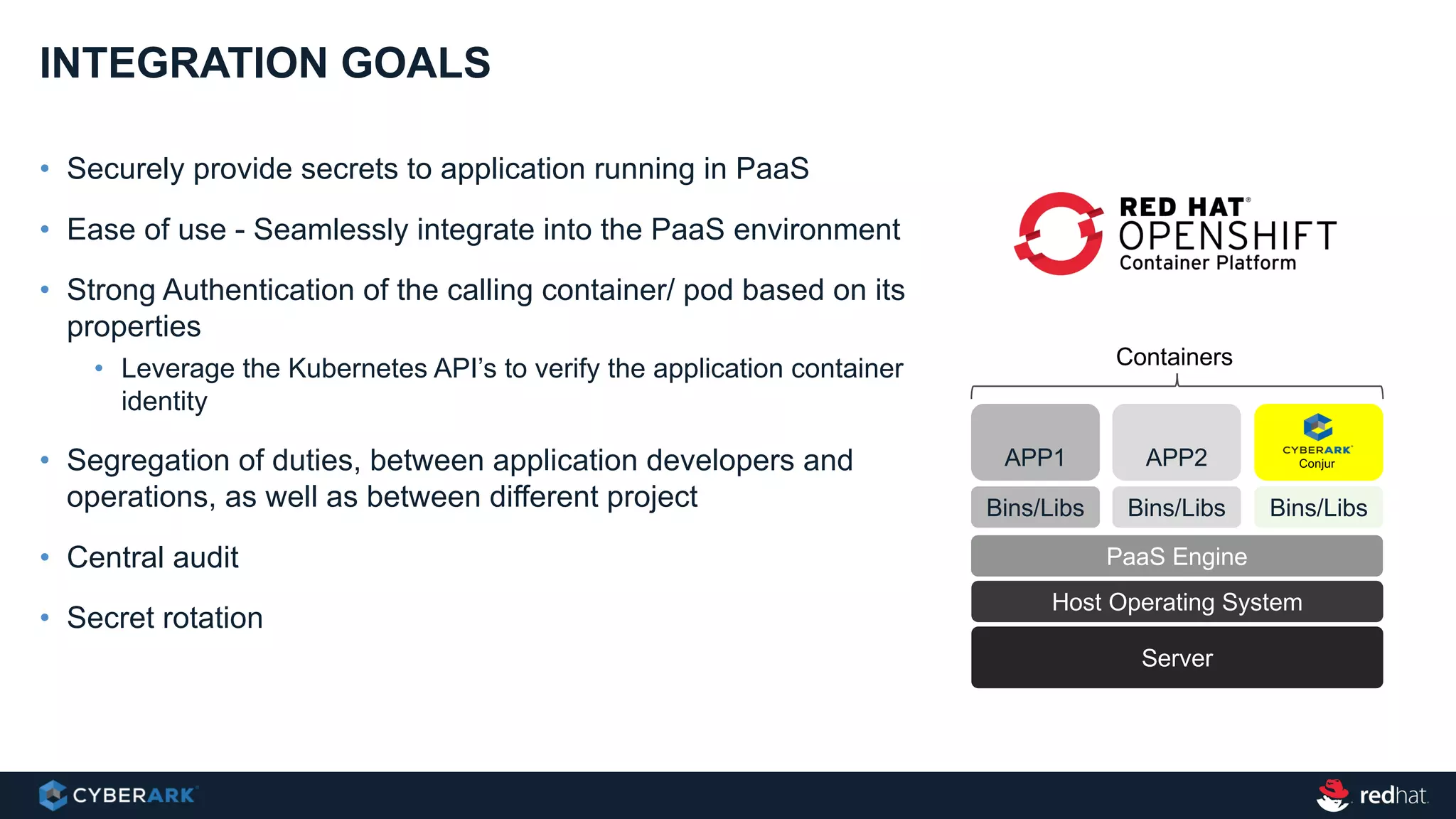
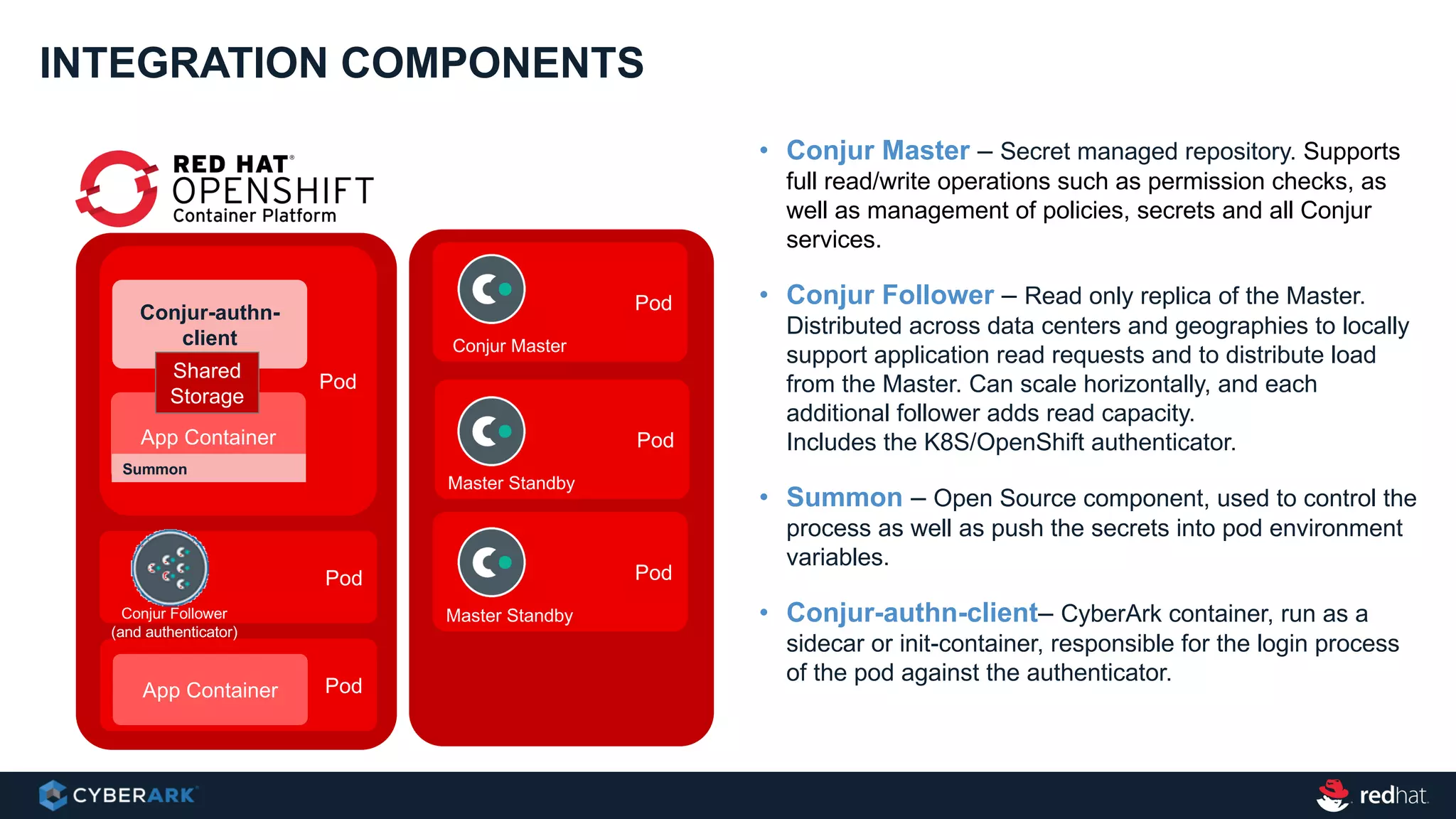
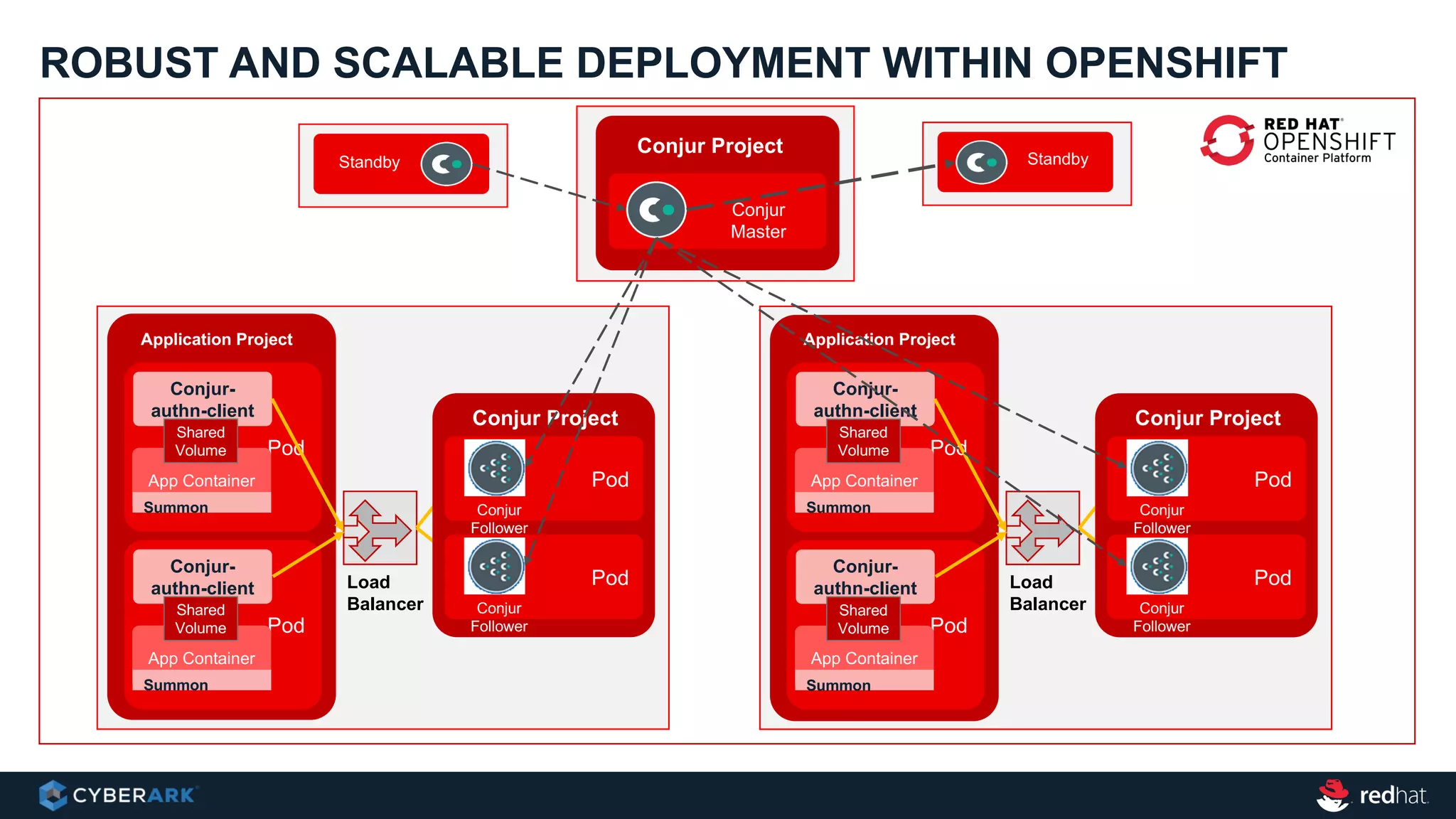
This document provides an overview of a webinar on integrating OpenShift and Conjur for DevOps. It discusses containers and Kubernetes, and how they are not enough on their own for DevOps without additional components like networking, image registries, metrics/logging, deployment automation, application lifecycles, services, and self-service portals. It then outlines how OpenShift addresses these needs and how Conjur can integrate to provide secrets management and access control when using OpenShift for DevOps. The integration goals, components, deployment within OpenShift, and detailed flow are described to securely provide secrets to applications in a scalable and robust manner.



![OPENSHIFT – CONJUR DETAILED FLOW
1. Create a policy for each pod/ application
2. Load the policy into Conjur Master
3. When pod starts, Conjur-authn-client goes up
and creates a CSR
4. Conjur-authn-client calls the Follower with pod
details and CSR
5. Follower verifies pod exist against Kubernetes
API
6. If exist, signs the request and writes it out of
band to the Conjur-authn-client
7. Conjur-authn-client calls Follower - follower
authenticates against Conjur policies and returns
a encrypted token
8. The Conjur-authn-client decrypts the token and
writes it in the pod shared memory
9. Summon uses the token to fetch the secrets
from Conjur and writes the retrieved secrets to
the environment variables.
Init Container
Pod
Summon
App Container
Conjur-authn-
client
Shared
Volume
Pod
Conjur Master
Application Project Conjur Project
Pod
Conjur Follower
(and authenticator)
Init Container
Pod
Conjur-authn-
client
Pod
Conjur Follower
(and authenticator)
Load
Balancer
App policy:
- !policy
id: allowed_apps
annotations:
description: Apps and services in cluster.
body:
- !layer
- &apps
- !host [namespace]/service_account/[sa-name]
- !grant
role: !layer
members: *apps
ü
Summon
App Container
Shared
Volume](https://image.slidesharecdn.com/redhatwebinar6-180627182248/75/Centralize-and-Simplify-Secrets-Management-for-Red-Hat-OpenShift-Container-Environments-with-the-CyberArk-Conjur-Enterprise-Integration-27-2048.jpg)