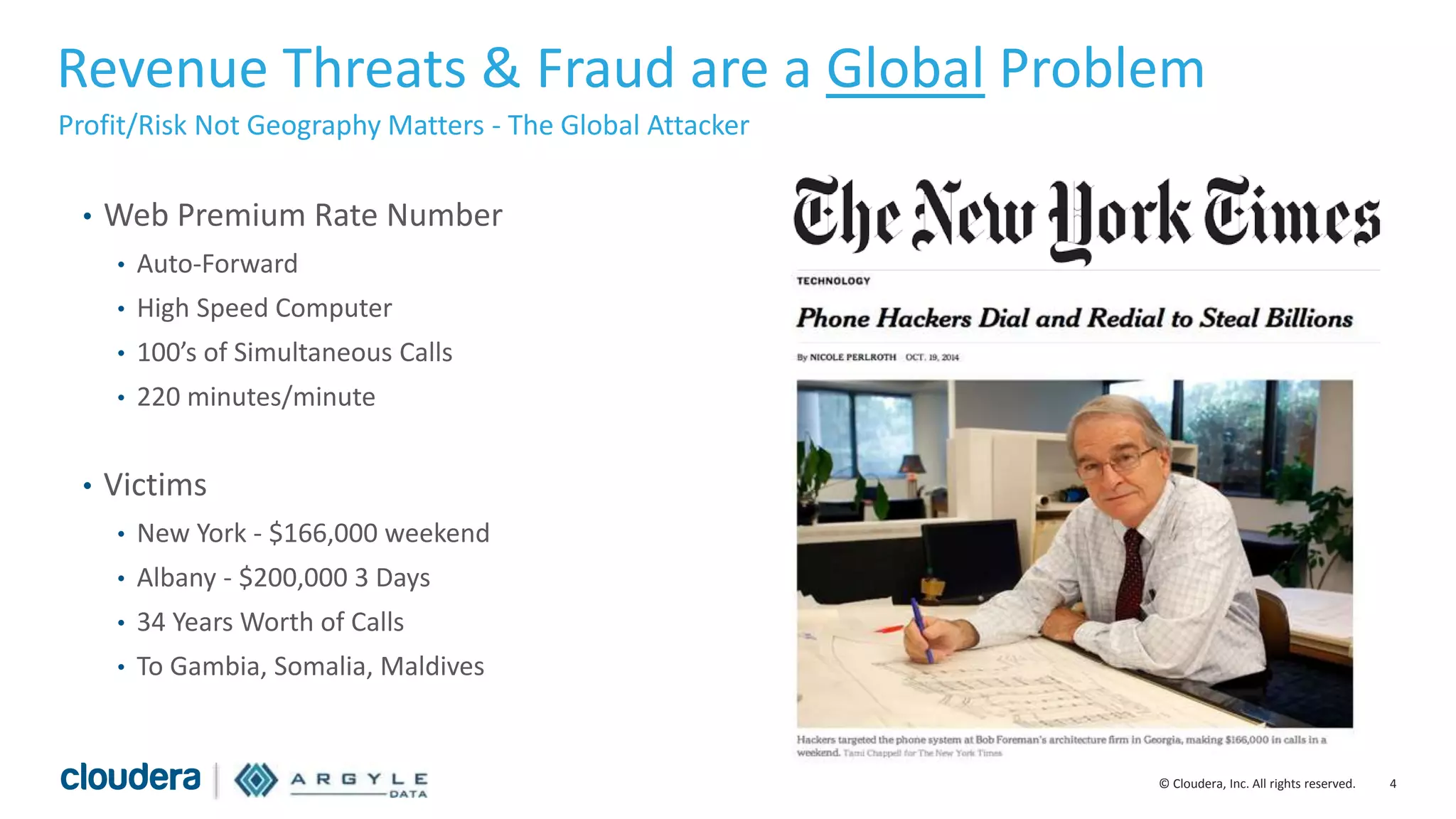
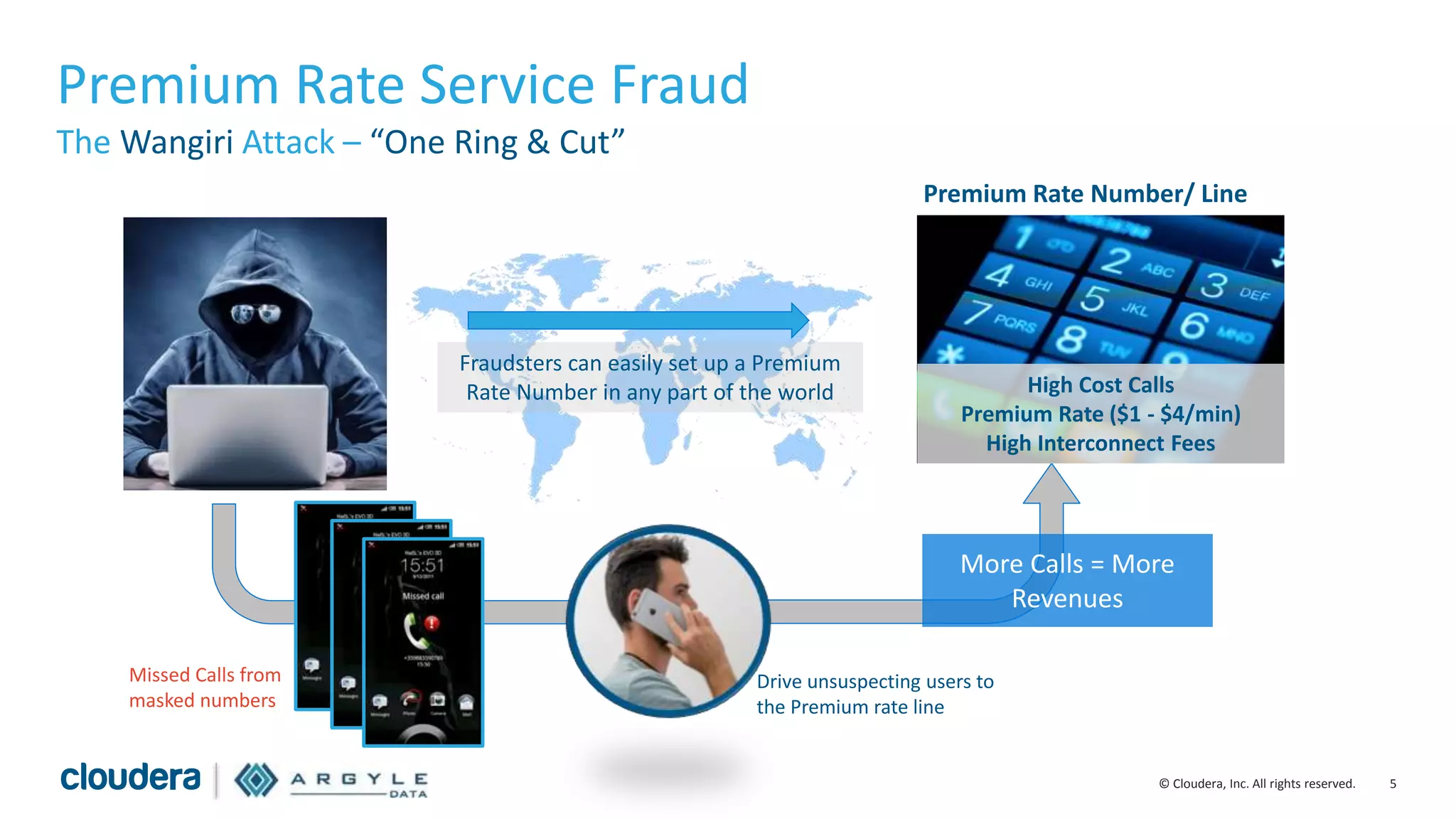
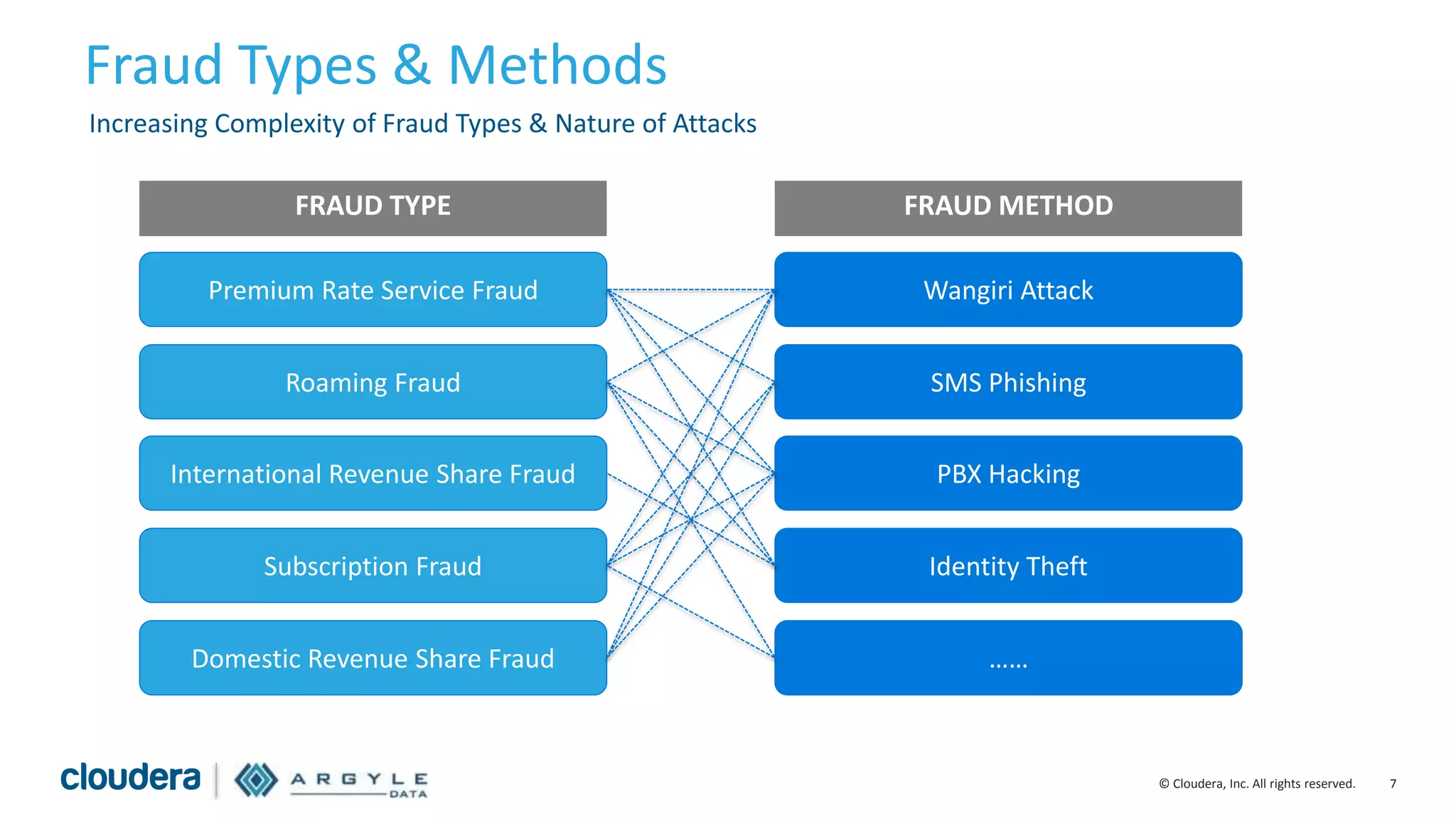
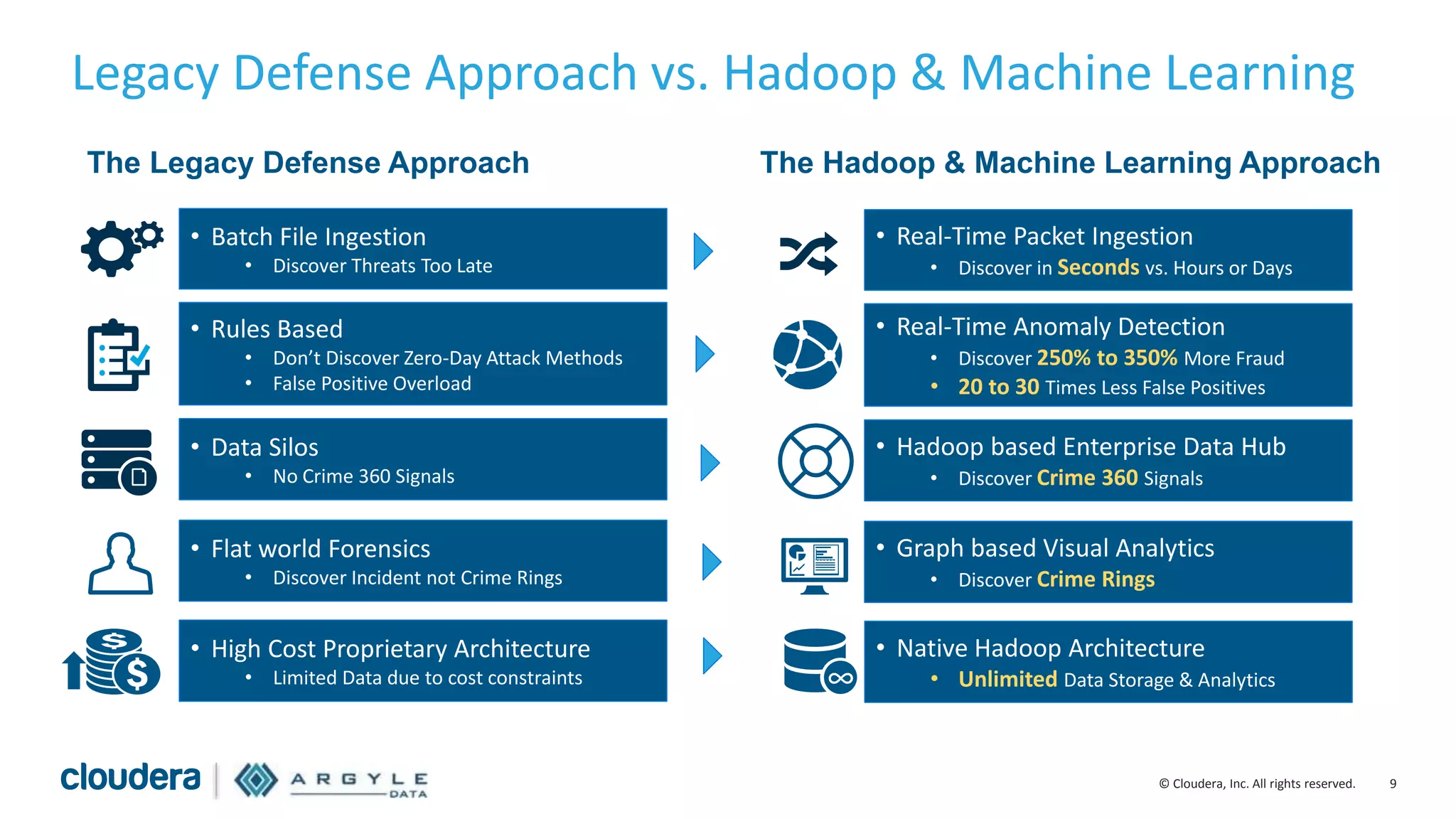
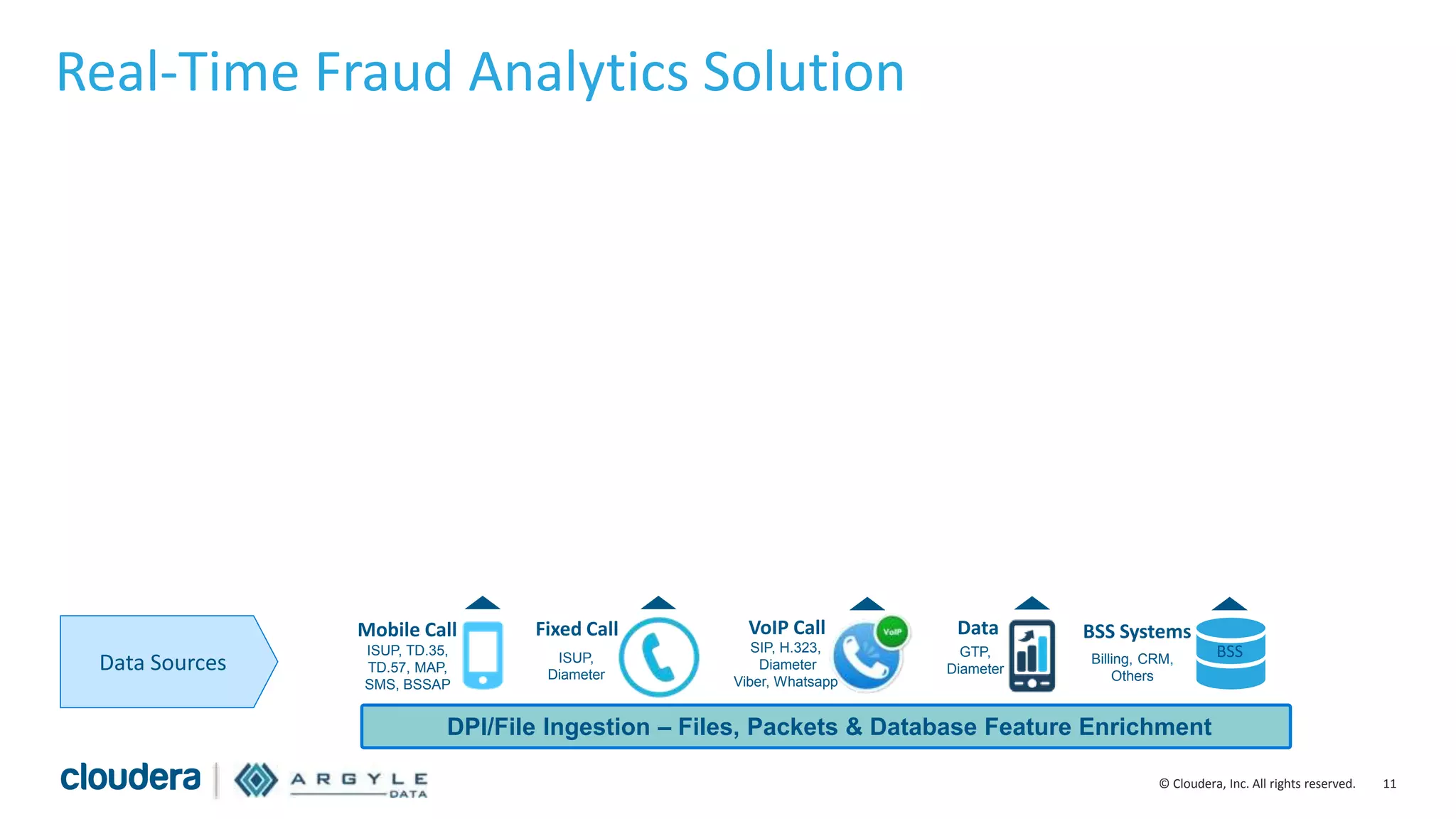
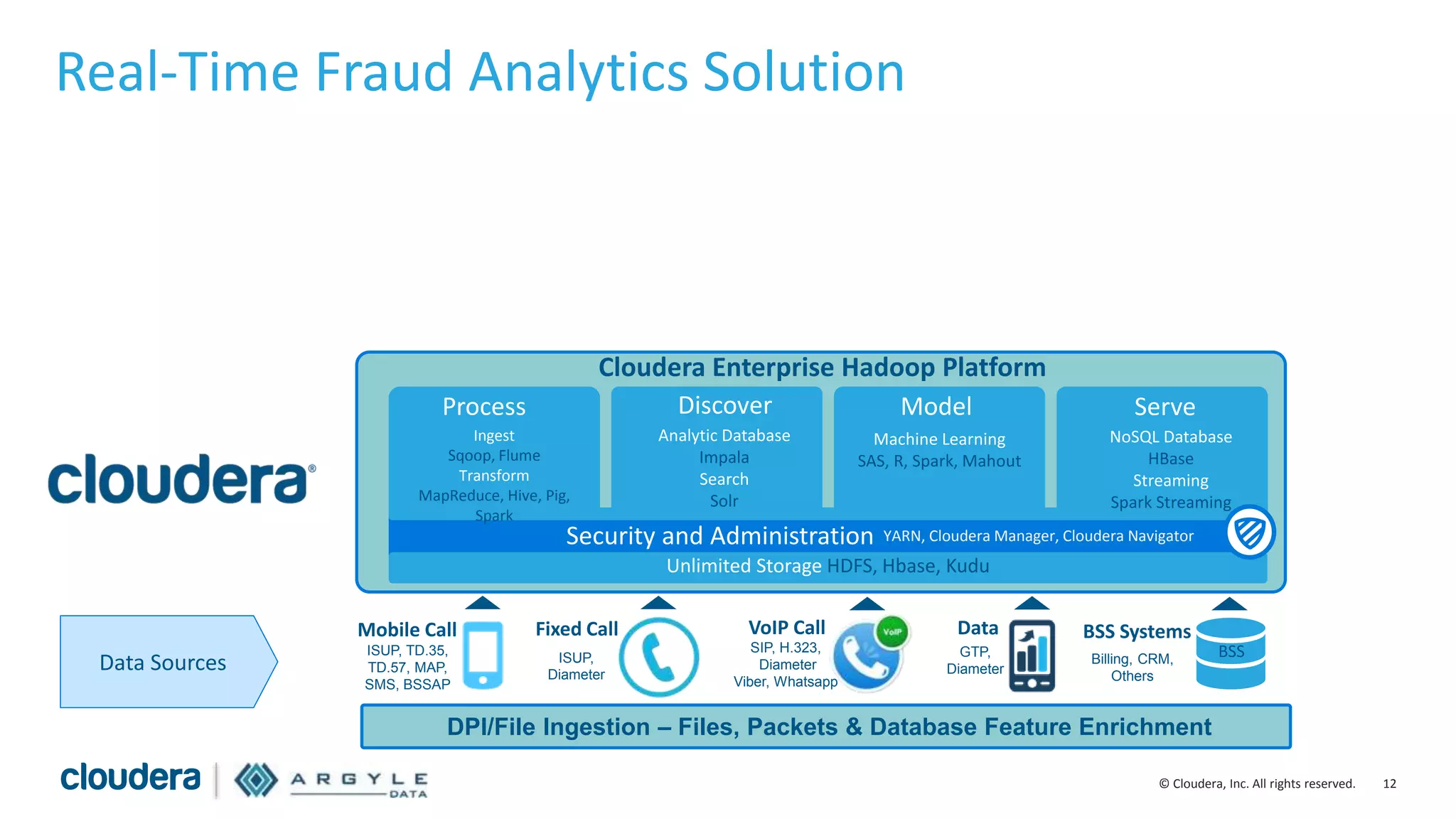
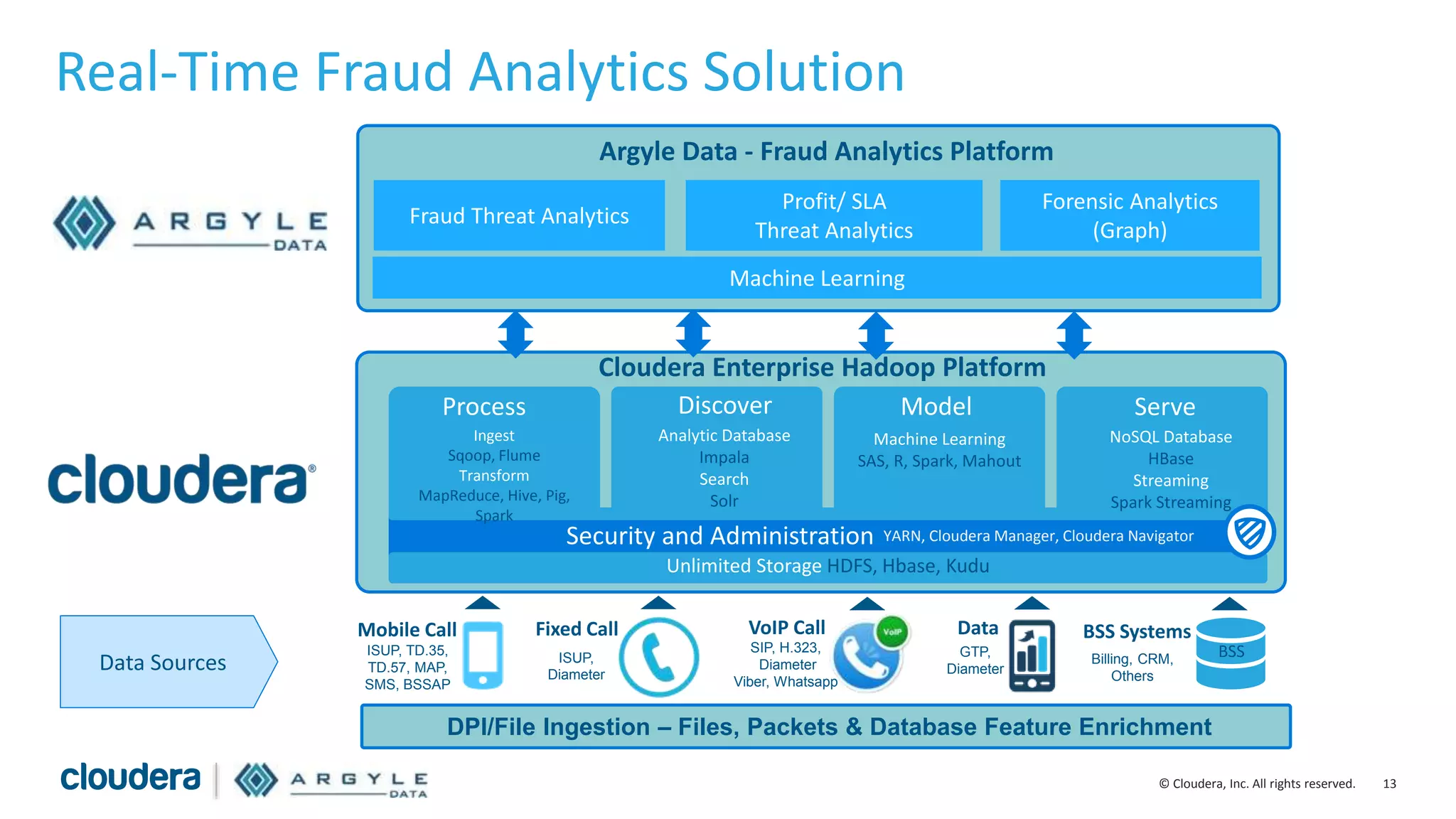
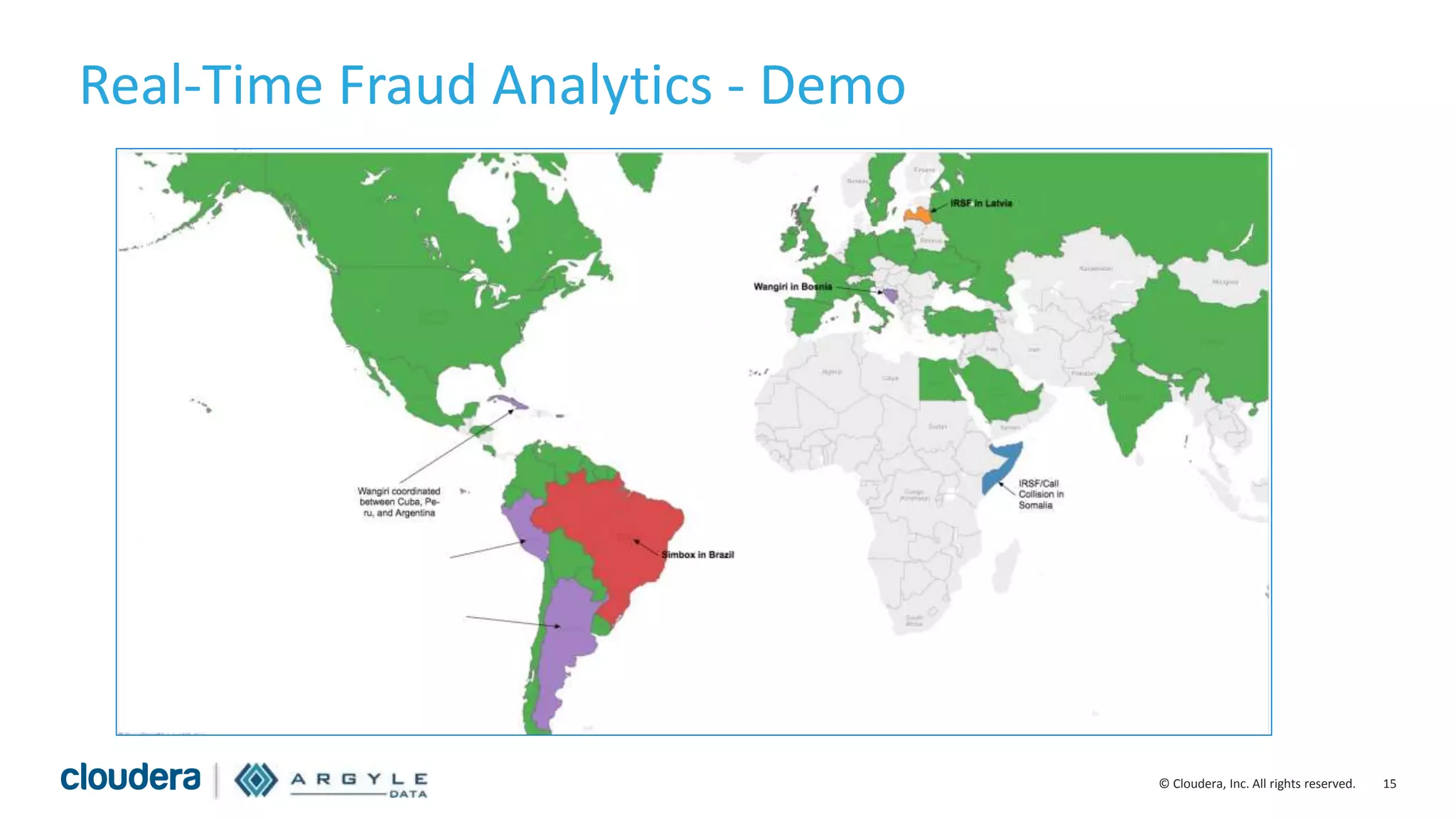
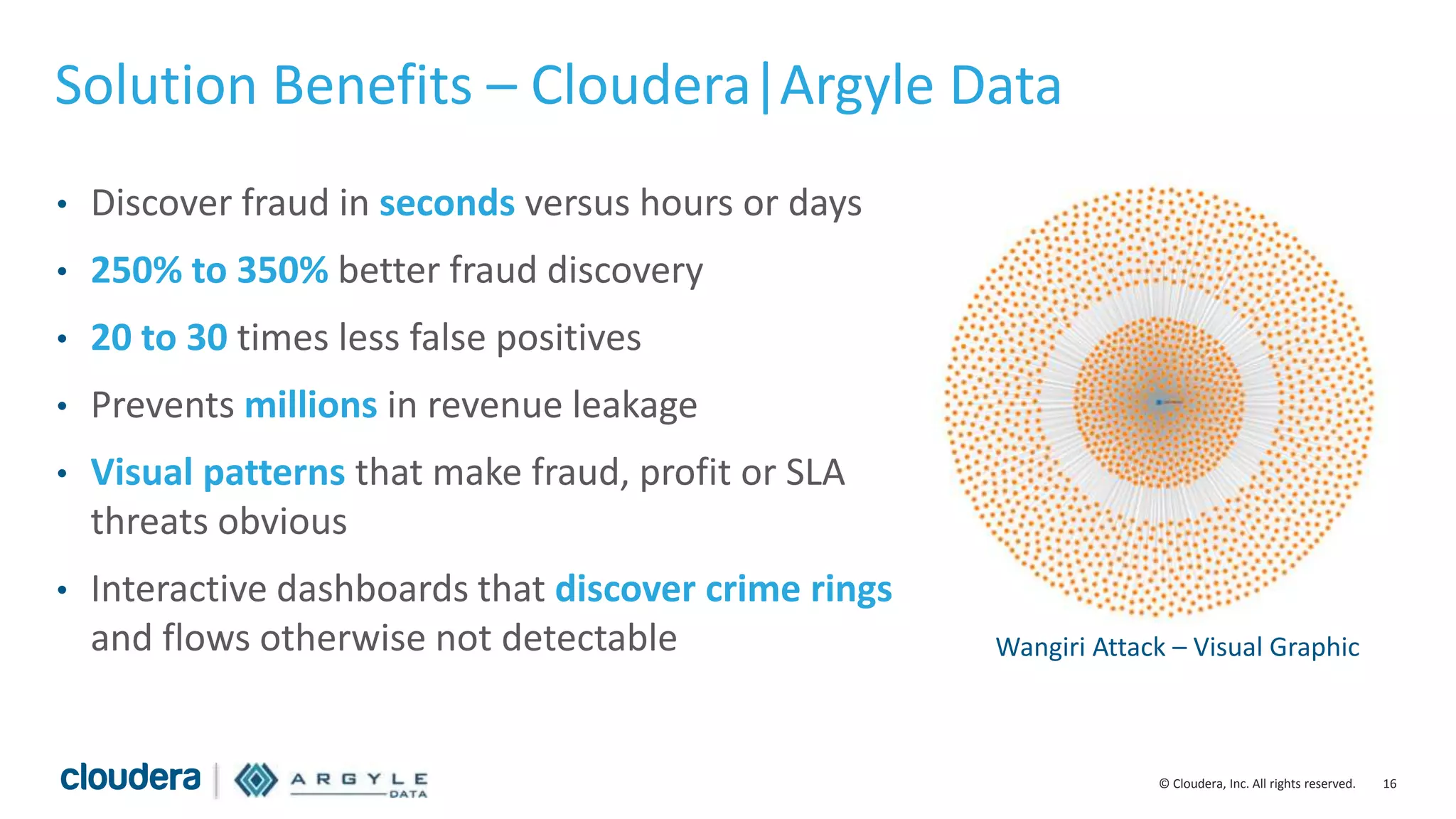
The document discusses the use of Apache Hadoop for real-time fraud analytics in communication service providers, highlighting the significant financial losses due to various types of fraud, such as premium rate service and roaming fraud. It contrasts traditional legacy systems with a Hadoop-based approach, emphasizing faster detection and improved accuracy in identifying fraud. The presentation outlines the solution benefits provided by Cloudera and Argyle Data, including enhanced fraud discovery and reduced false positives.