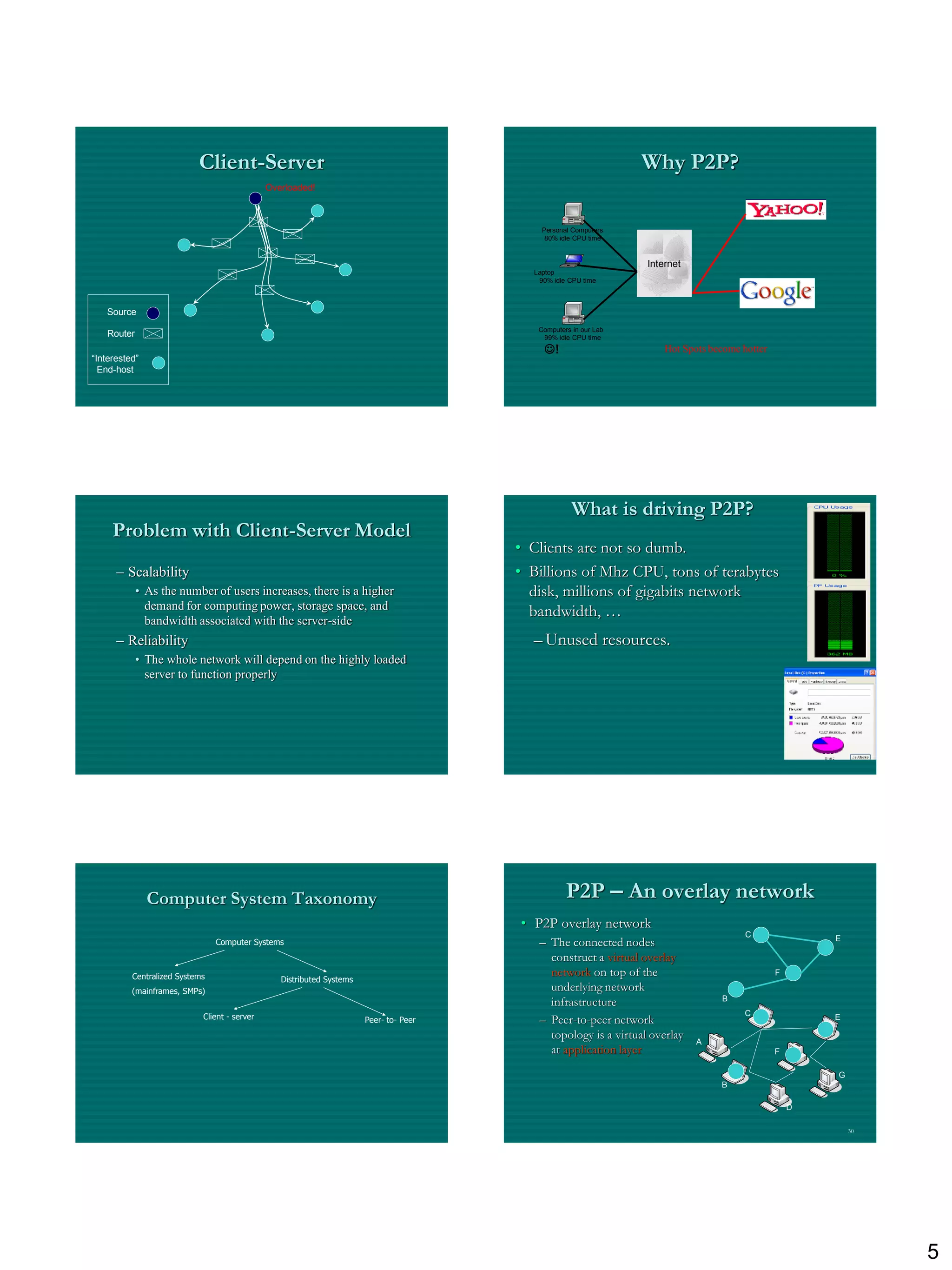
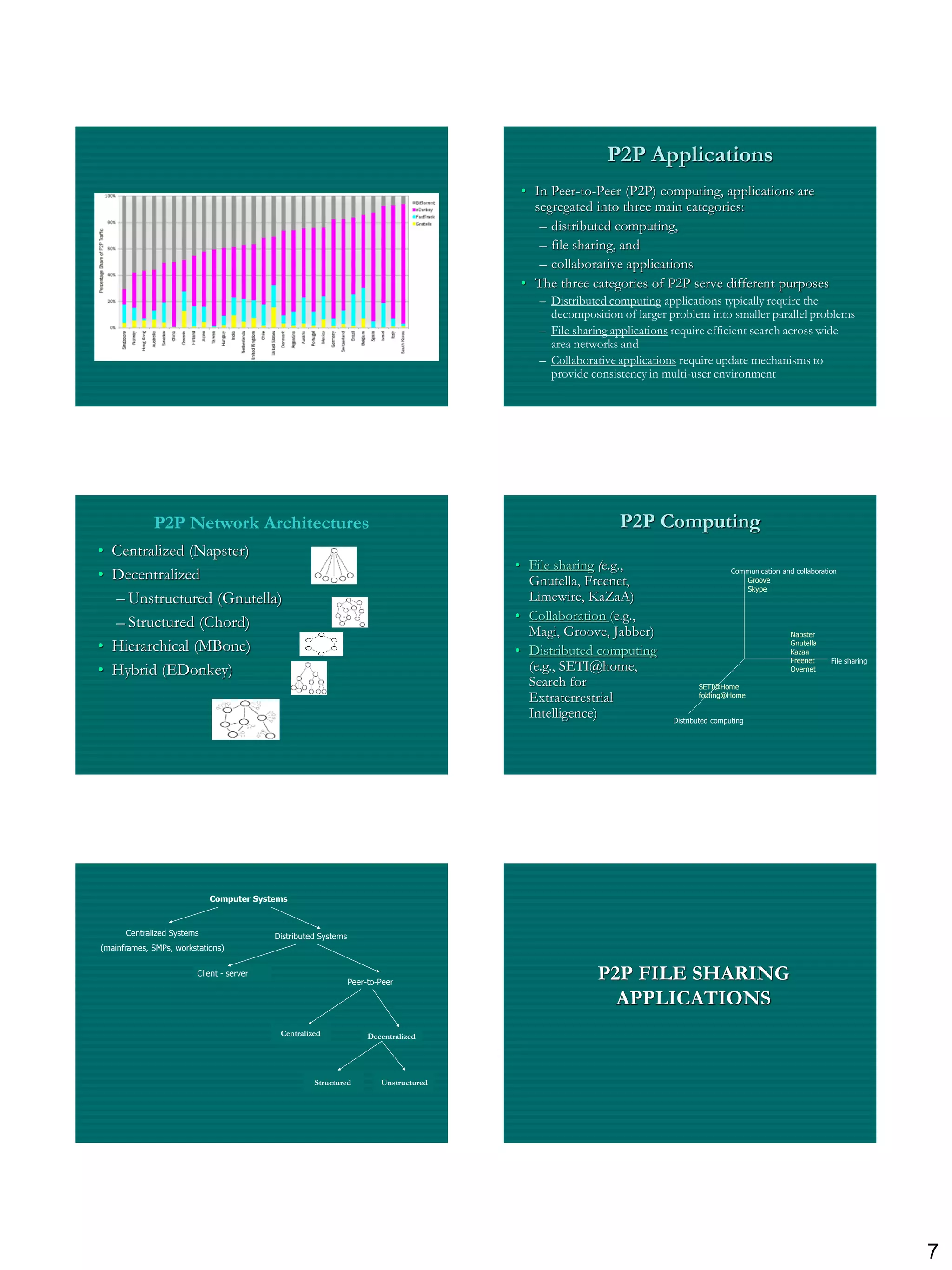
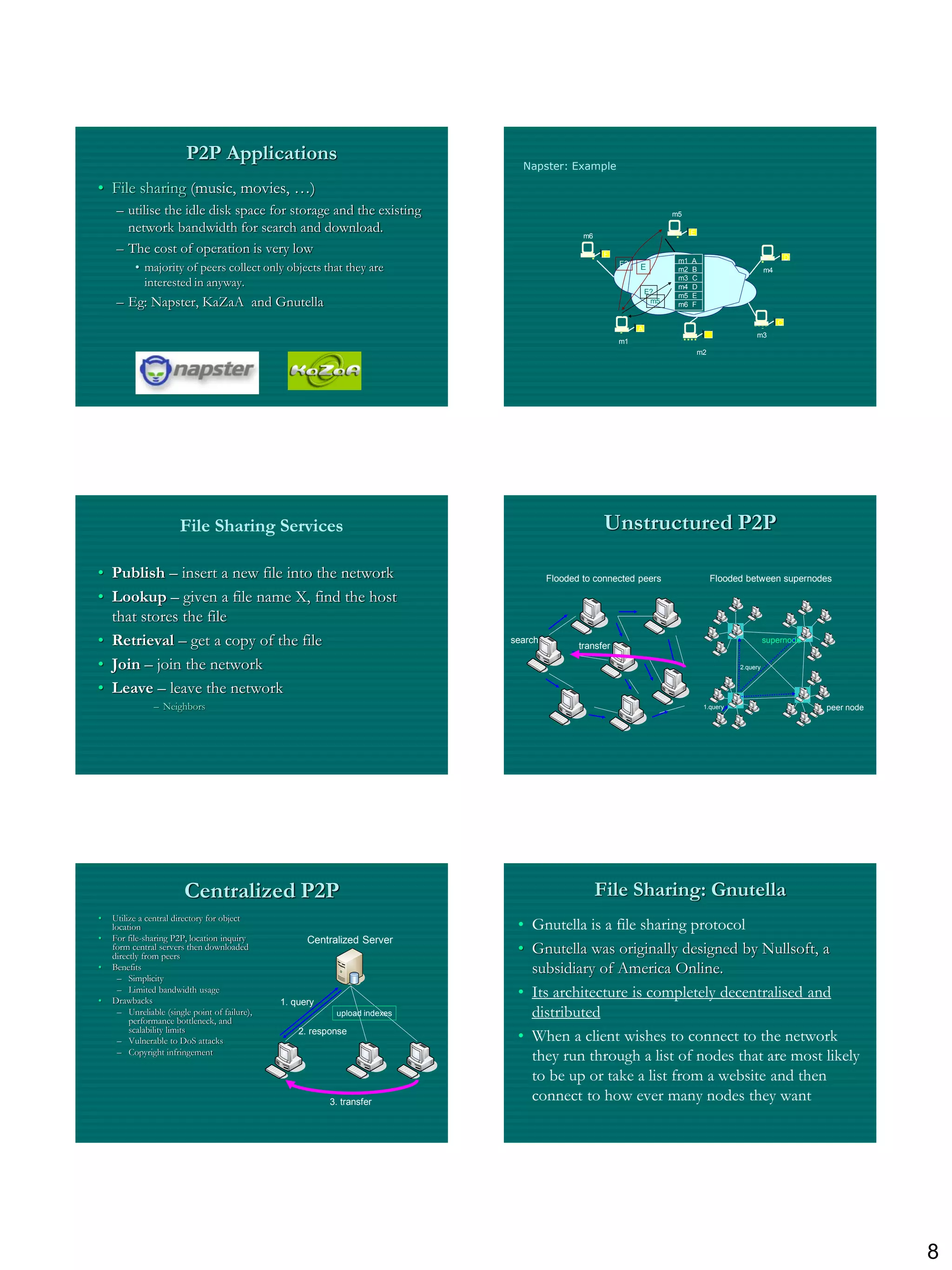
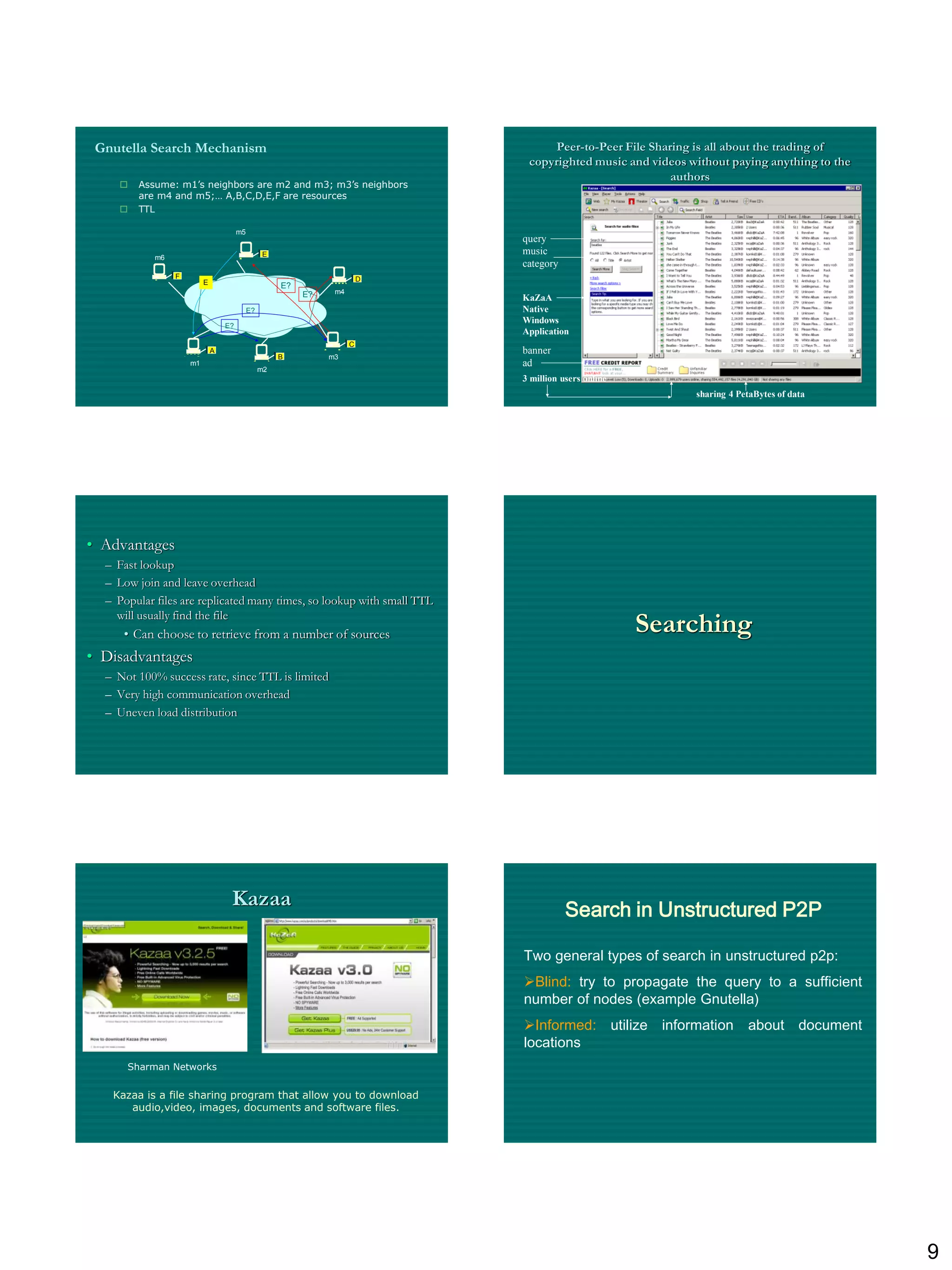
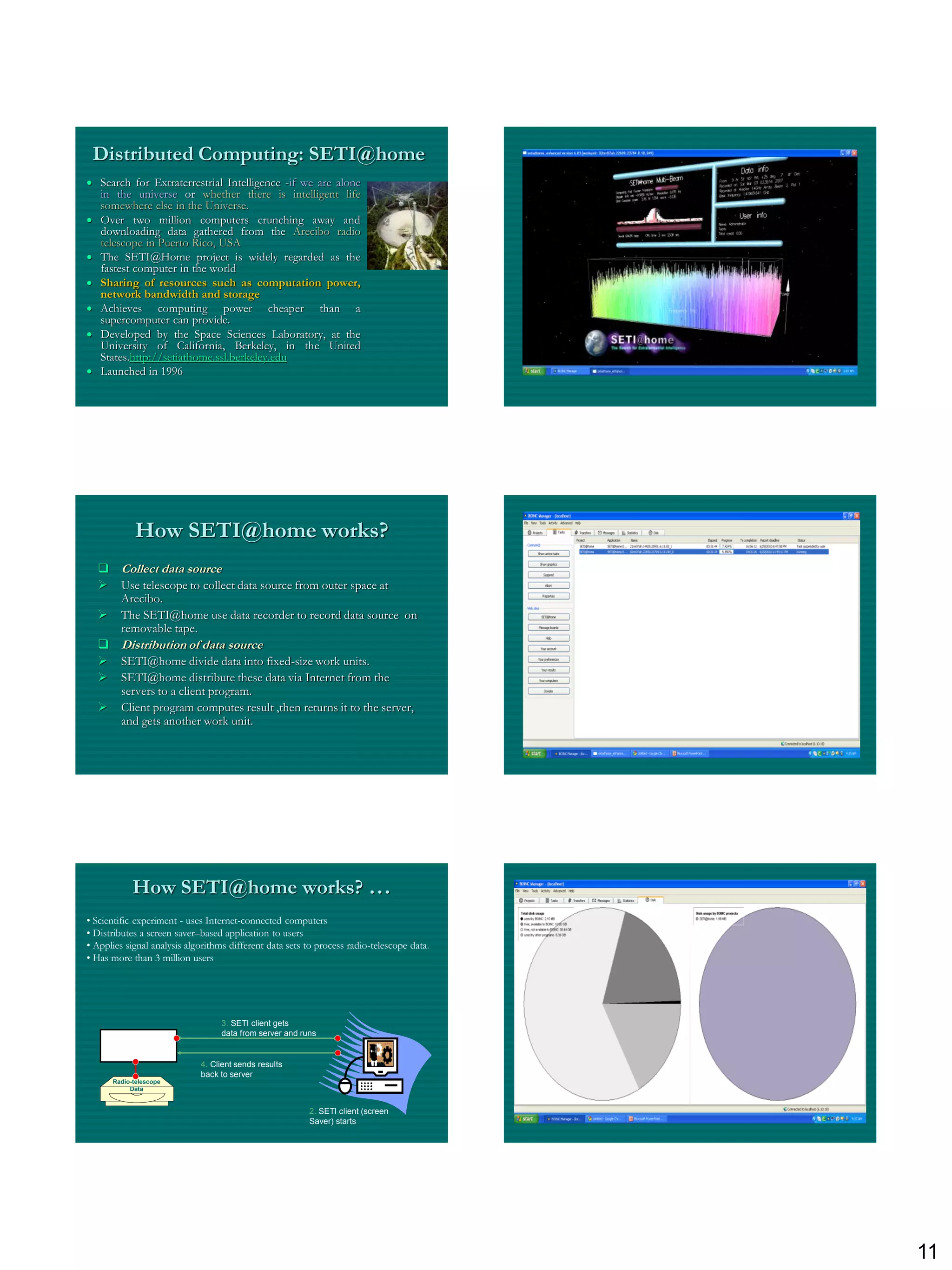
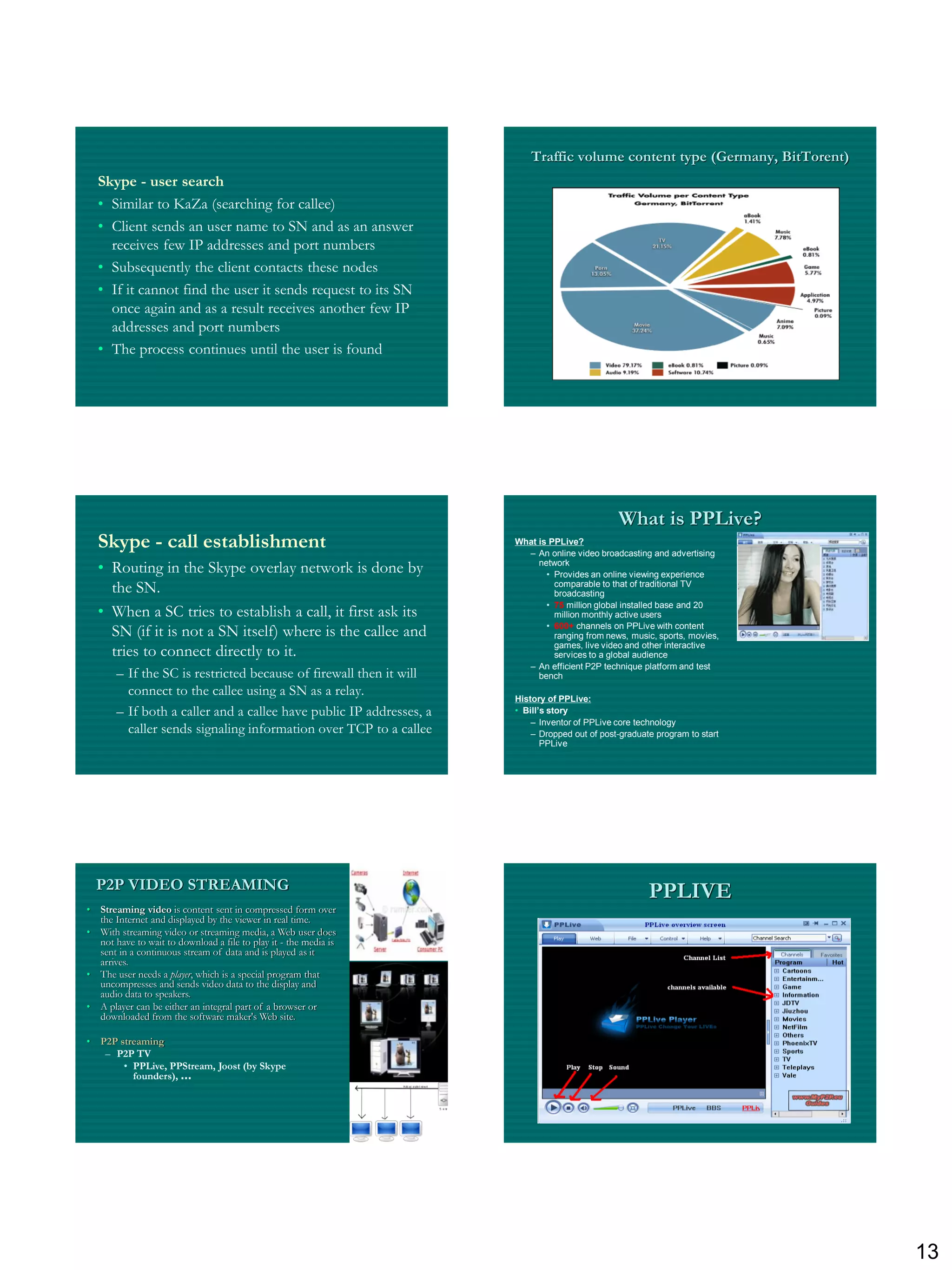
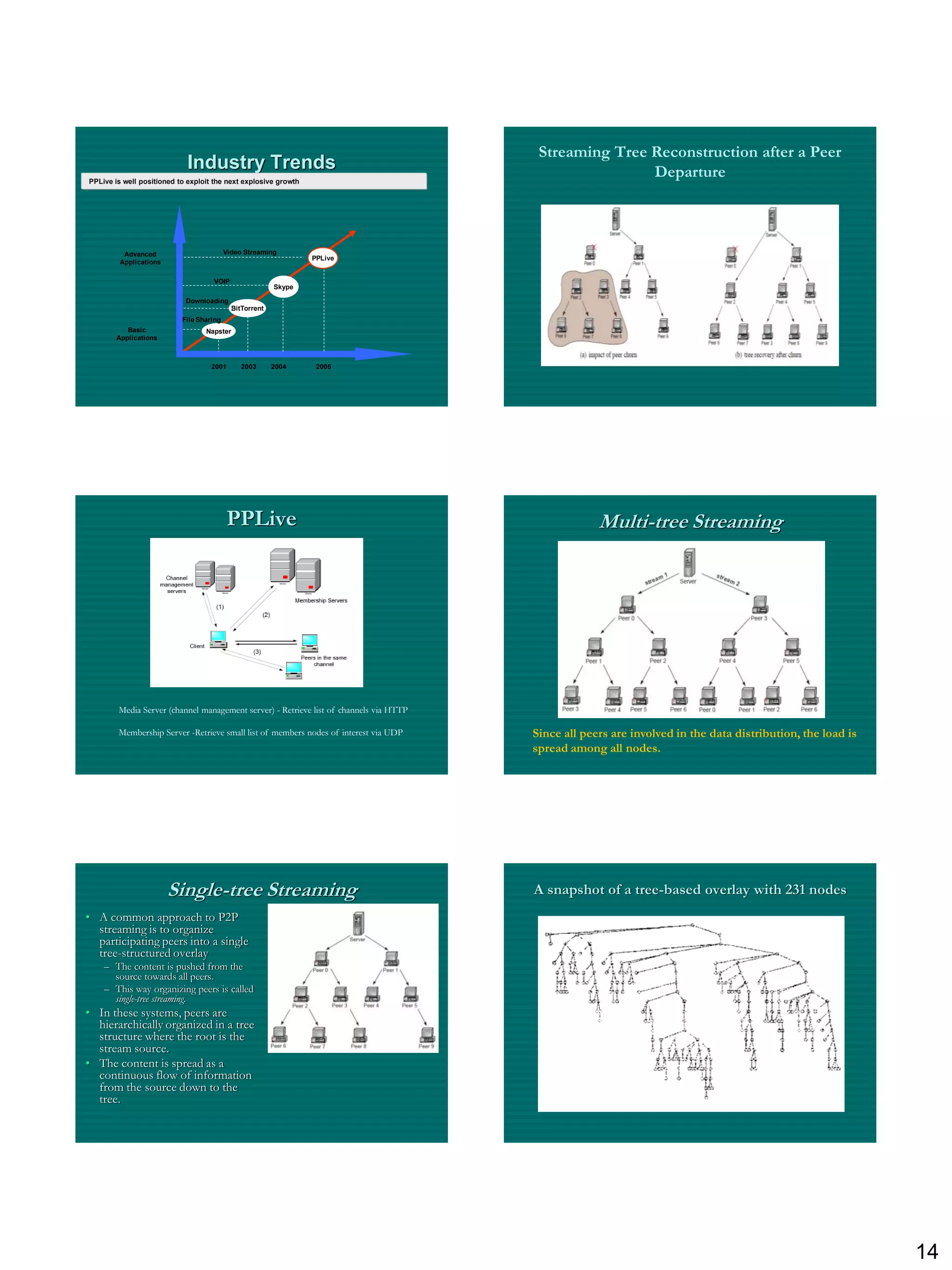
The document discusses three ways to improve computer performance: working harder with faster hardware, working smarter with optimized algorithms, and getting help from multiple linked computers. It then provides examples of centralized versus distributed systems and defines peer-to-peer (P2P) computing as using distributed algorithms across networked computers. Finally, it introduces the concept of middleware enabling coordination between distributed applications across different locations and platforms.






![Overall Architecture
Web Server Tracker
Bit Torrent
•Created by Brahm Cohen in 2001
C
A
Peer
Peer [Seed]
B
[Leech]
Downloader Peer
“US” [Leech]
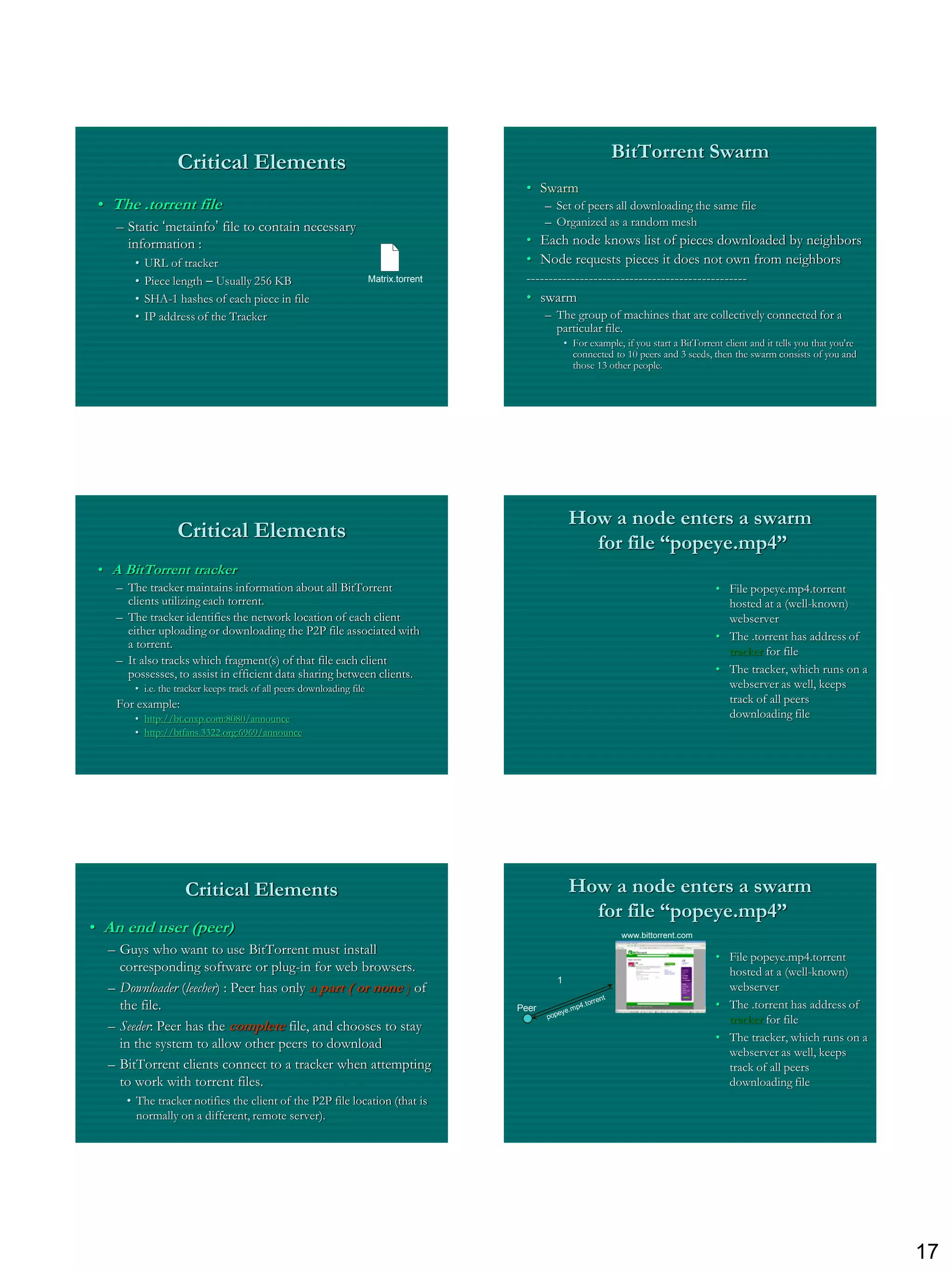
What is BitTorrent?
Overall Architecture
• A peer-to-peer file transfer protocol
Tracker
• Extremely popular today Web Server
• “Pull-based” “swarming” approach
• Each file split into smaller pieces
• Nodes request desired pieces from
neighbors
• As opposed to parents pushing data
C
that they receive A
• Pieces not downloaded in sequential Peer
order Peer [Seed]
B
• Encourages contribution by all nodes [Leech]
Downloader Peer
“US” [Leech]
Overall Architecture Overall Architecture
Web Server Tracker Web Server Tracker
C C
A A
Peer Peer
Peer [Seed] Peer [Seed]
B B
[Leech] [Leech]
Downloader Peer Downloader Peer
“US” [Leech] “US” [Leech]
15](https://image.slidesharecdn.com/academicstaffcollege-keralauniversity-p2p-oct122011-111025022413-phpapp02/75/Research-Issues-in-P2P-Netwroks-15-2048.jpg)
![Overall Architecture BitTorrent Lingo
Web Server Tracker
Seeder = a peer that provides the complete file.
Initial seeder = a peer that provides the initial copy.
Leecher
Initial seeder
One who is downloading
C
A
Peer
Peer [Seed] Leecher
B
[Leech]
Downloader Peer
Seeder
“US” [Leech]
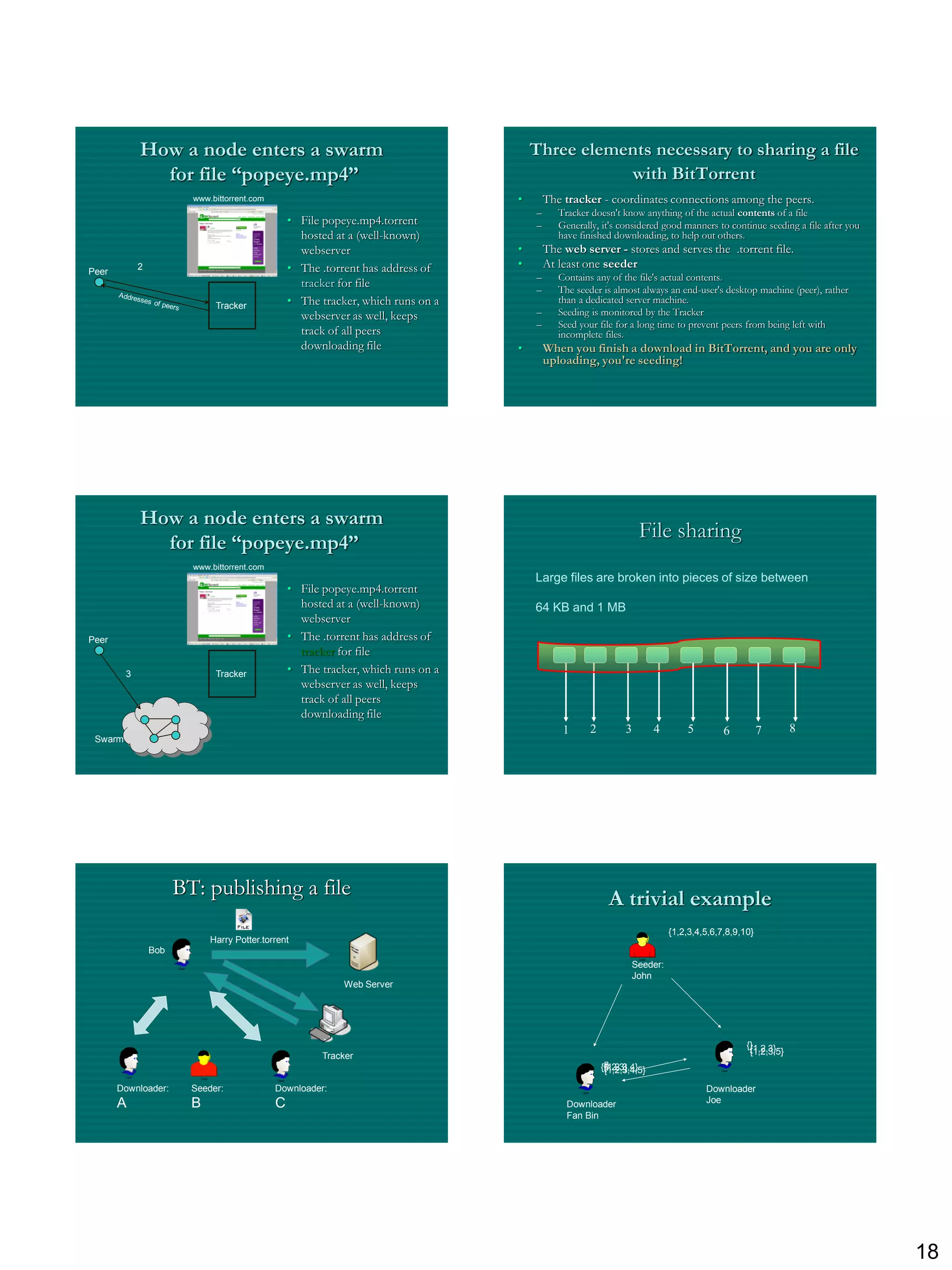
Overall Architecture BitTorrent Basics
Web Server Tracker
• Files are broken into pieces.
– Users each download different pieces from the
original uploader (seed).
– Users exchange the pieces with their peers to obtain
the ones they are missing.
A
C
• This process is organized by a centralized server
Peer called the Tracker.
Peer [Seed]
B
[Leech]
Downloader Peer
“US” [Leech]
Overall Architecture Critical Elements
Web Server Tracker
• A web server
– stores and serves the .torrent file.
– For example:
• http://bt.btchina.net Web Server
• http://bt.ydy.com/
C
A
Peer The Lord of Ring.torrent
Peer [Seed]
B
[Leech]
Troy.torrent
Downloader Peer
“US” [Leech]
16](https://image.slidesharecdn.com/academicstaffcollege-keralauniversity-p2p-oct122011-111025022413-phpapp02/75/Research-Issues-in-P2P-Netwroks-16-2048.jpg)