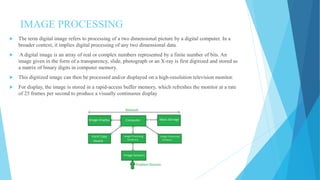
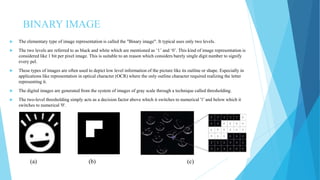
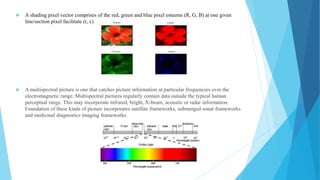
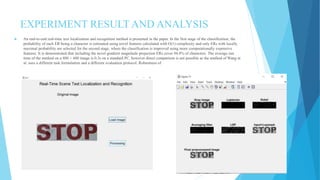
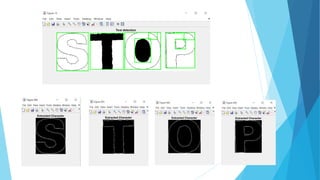
The document summarizes a student project on real-time scene text localization and recognition. It includes an introduction describing the challenges of natural scene text detection compared to well-formatted documents. It also describes previous work on text localization and recognition methods, the proposed image processing and MATLAB software used in the project, experimental results and analysis, and conclusions. The project aims to develop a new video scene text detection method using image enhancement and a Bayesian classifier to classify text pixels without prior image knowledge.


![INTRODUCTION
Scene text recognition (STR) has become an increasing hot research field in computer vision recently, as manifested
by the prosperity of recent ”robust reading” competitions ICDAR [1] in every two years, along with the workshop
about Camera Based Document Analysis and Recognition (CBDAR).
With an extensive demand for the information identification, STR technology has a large-scale applications in
automatically logistics distribution, geographical positioning, license plate recognition, and driverless applications.
Text detection [2] is a common task in image analysis, while text recognition [3] is a more advanced task for it not
only should localize the text spatially which belongs to object detection, but also recognize the text, i.e., text spotting
[4].
Compared to the traditional well-formatted document text detection and recognition, natural text detection and
recognition is a challenging topic in the visual detection task due to multilingual, text sizes, font tilt, blurring,
background interference, handwriting, various angles and so on, as shown](https://image.slidesharecdn.com/real-timescenetextlocalizationandrecognitionppt-221217122512-92e00354/85/REAL-TIME-SCENE-TEXT-LOCALIZATION-AND-RECOGNITION-ppt-pptx-3-320.jpg)
![Previous Work
Numerous methods which focus solely on text localization in real-world images have been published [6, 2, 7, 17].
The method of Epstein et al. in [5] converts an input image to a greyscale space and uses Canny detector [1] to find
edges.
Pairs of parallel edges are then used to calculate stroke width for each pixel and pixels with similar stroke width are
grouped together into characters. The method is sensitive to noise and blurry images because it is dependent on a
successful edge detection and it provides only single segmentation for each character which not necessarily might
be the best one for an OCR module. A similar edge based approach with different connected component algorithm
is presented in [24].
A good overview of the methods and their performance can be also found in ICDAR Robust Reading competition
results [10, 9, 20]. Only a few methods that perform both text localization and recognition have been published. The
method of Wang Figure 2.
Text localization and recognition overview.
(a) Source 2MPx image.
(b) Intensity channel extracted.
(c) ERs selected in ON by the first stage of the sequential classifier.
(d) ERs selected by the second stage of the classifier.
(e) Text lines found by region grouping.
(f) Only ERs in text lines selected and text recognized by an OCR module.
(g) Number of ERs at the end of each stage and its duration.](https://image.slidesharecdn.com/real-timescenetextlocalizationandrecognitionppt-221217122512-92e00354/85/REAL-TIME-SCENE-TEXT-LOCALIZATION-AND-RECOGNITION-ppt-pptx-4-320.jpg)
![RGB IMAGE
An RGB color image is an M*N*3 array of color pixels where each color pixel is triplet
corresponding to the red, green and blue components of an RGB image, at a specific spatial location.
An RGB image may be viewed as “stack” of three gray scale images that when fed in to the red,
green and blue inputs of a color monitor Produce a color image on the screen.
Convention the three images forming an RGB color image are referred to as the red, green and blue
components images.
The data class of the components images determines their range of values. If an RGB image is of class
double the range of values is [0, 1]
A normal grey scale image has 8 bit color depth = 256 grey scales.
A true color image has 24 bit color depth = 8 x 8 x 8 bits = 256 x 256 x 256 colors = ~16 million
colors](https://image.slidesharecdn.com/real-timescenetextlocalizationandrecognitionppt-221217122512-92e00354/85/REAL-TIME-SCENE-TEXT-LOCALIZATION-AND-RECOGNITION-ppt-pptx-6-320.jpg)




![EXISTING METHOD
The method is able to cope with noisy data, but its generality is limited as a lexicon of words (which
contains at most 500 words in their experiments) has to be supplied for each individual image.
Methods presented in [14, 15] detect characters as Maximally Stable Extremal Regions (MSERs) [11]
and perform text recognition using the segmentation obtained by the MSER detector. An MSER is an
particular case of
Extremal Region whose size remains virtually unchanged over a range of thresholds. The methods
perform well but have problems on blurry images or characters with low contrast. According to the
description provided by the ICDAR 2011 Robust Reading competition organizers [20] the winning
method is based on MSER detection, but the method](https://image.slidesharecdn.com/real-timescenetextlocalizationandrecognitionppt-221217122512-92e00354/85/REAL-TIME-SCENE-TEXT-LOCALIZATION-AND-RECOGNITION-ppt-pptx-14-320.jpg)



![REFERENCES
[1] J. Canny. A computational approach to edge detection. IEEE Transactions on Pattern Analysis and Machine
Intelligence, 8:679–698, 1986.
[2] X. Chen and A. L. Yuille. Detecting and reading text in natural scenes. CVPR, 2:366–373, 2004.
[3] H. Cheng, X. Jiang, Y. Sun, and J. Wang. Colour image segmentation: advances and prospects. Pattern Recognition,
34(12):2259 – 2281, 2001.
[4] N. Cristianini and J. Shawe Taylor. An introduction to Support Vector Machines. Cambridge University Press,
March 2000.
[5] B. Epshtein, E. O fek, and Y. Wexler. Detecting text in natural scenes with stroke width transform. In CVPR 2010,
pages 2963 –2970.
[6] L. Jung- Jin, P.-H. Lee, S.-W. Lee, A. Yuille, and C. Koch. Ada boost for text detection in natural scene. In ICDAR
2011, pages 429–434, 2011.
[7] R. Li enhart and A. Wernicke. Localizing and segmenting text in images and videos. Circuits and Systems for
Video Technology, 12(4):256 –268, 2002.
[8] H. Liu and X. Ding. Handwritten character recognition using gradient feature and quadratic classifier with multiple
discrimination schemes. In ICDAR 2005, pages 19 – 23 Vol. 1.](https://image.slidesharecdn.com/real-timescenetextlocalizationandrecognitionppt-221217122512-92e00354/85/REAL-TIME-SCENE-TEXT-LOCALIZATION-AND-RECOGNITION-ppt-pptx-20-320.jpg)
