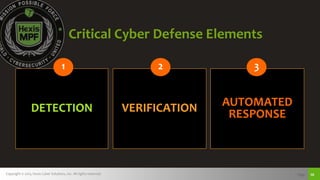
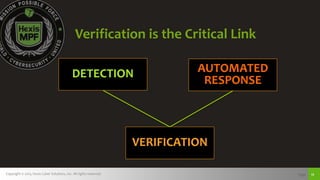
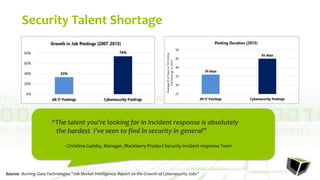
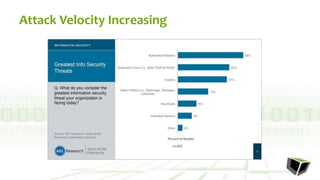
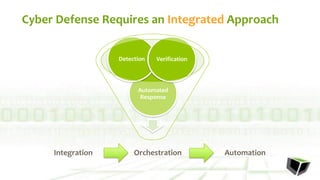
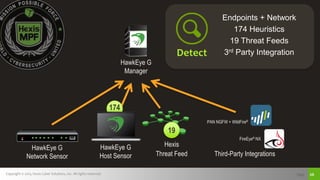
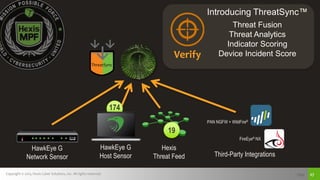
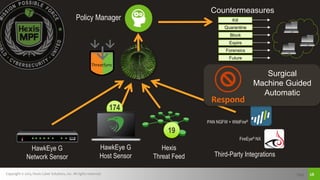
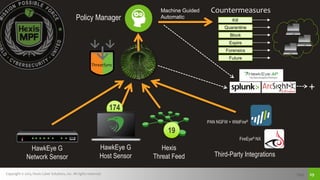
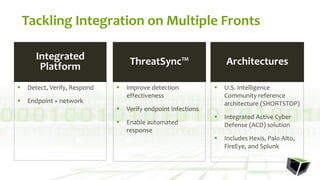
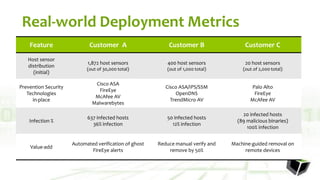
The document discusses challenges with detecting, verifying, and responding to cyber threats. It notes that despite security investments, organizations still experience difficulties keeping up with threats due to a lack of skilled personnel, ineffective prevention tools, and too many alerts to review. It introduces HawkEye G as an integrated platform that uses endpoint detection, network monitoring, and third-party integrations to detect threats, verifies them using correlation techniques, and enables automated and machine-guided responses to threats. Key benefits include reducing time spent on manual verification of alerts and enabling remote response capabilities. Case studies show HawkEye G reducing time spent on verification by 50% and enabling full removal of infections across endpoints.