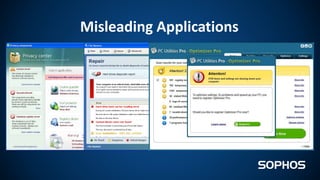
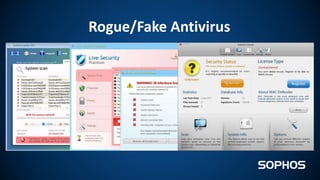
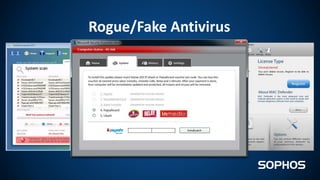
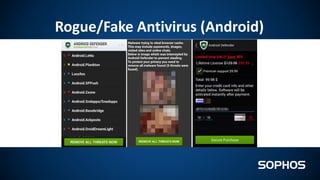
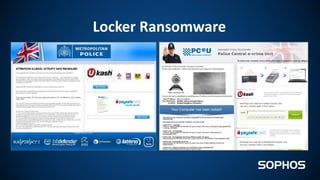
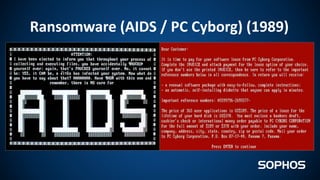
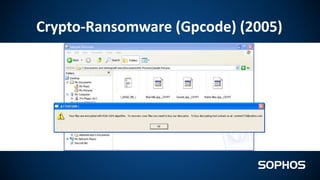
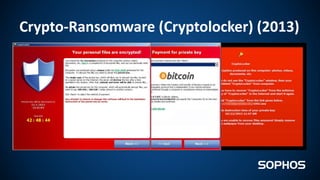
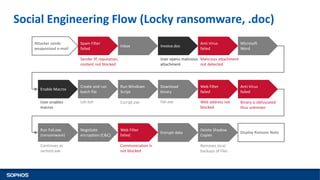
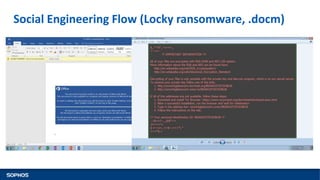
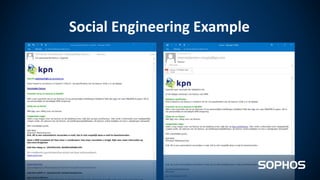
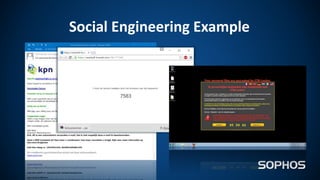
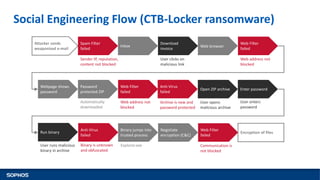
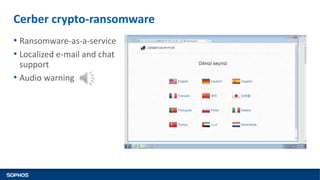
This document summarizes how ransomware works and has evolved over time. It discusses the results of a recent UK poll showing that 60% of victims had backups but 65% still paid ransoms averaging £540. It then outlines the evolution of ransomware from misleading applications in 2008-2014 to crypto-ransomware beginning in 2013. The document analyzes the social engineering techniques used by ransomware like Locky and CTB-Locker and how they evade filters and antivirus. It compares spam emails to exploit kits and discusses new evasion tricks being used. The document advocates for layered security approaches and outlines minimum protections organizations should implement.