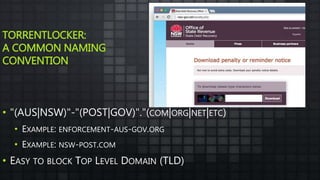
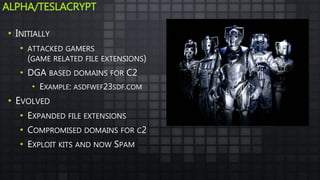
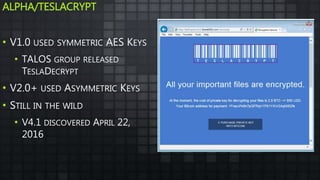
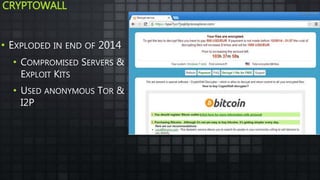
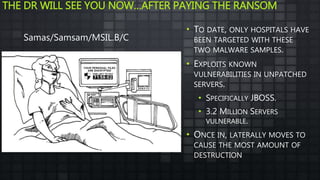
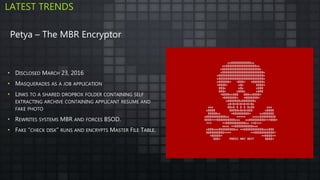
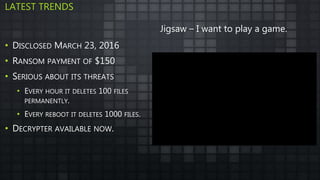
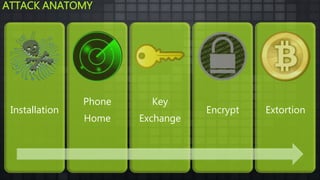
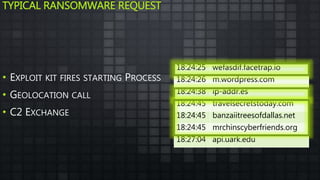
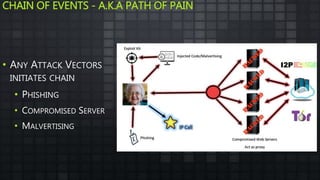
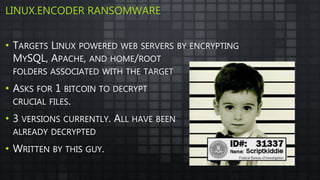
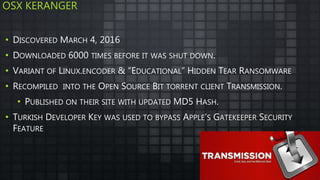
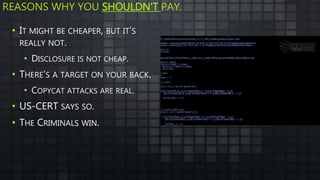
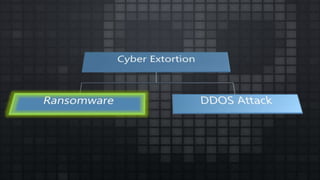
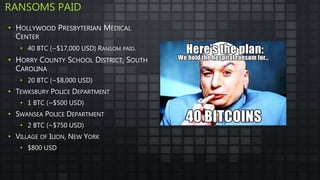
The document provides an overview and analysis of ransomware, including its history, technical details, trends, and mitigation techniques. It discusses how ransomware has evolved from early variants like AIDS to modern cryptoware like CryptoLocker and Locky. The document also analyzes the infection process, command and control infrastructure, and outlines strategies organizations can take to help prevent and recover from ransomware attacks, such as backups, patching, and isolation of critical systems.













![CRYPTOLOCKER
• STARTED TO APPEAR AROUND
SEPTEMBER 2013
• DELIVERED MAINLY THOUGH
THE GAMOVERZEUS (GOZ) P2P
BOTNET
• USED DOMAIN GENERATED
ALGORYTHMS (DGA)
• PRODUCE THOUSANDS OF
DOMAINS
• ONLY 1 OR 2 WERE REAL
Example: Faoefijawjfaslekf9ejaklja[.]ru
Bitcoin Price](https://image.slidesharecdn.com/ransomwaredha-160505053139/85/Ransomware-History-Analysis-Mitigation-16-320.jpg)