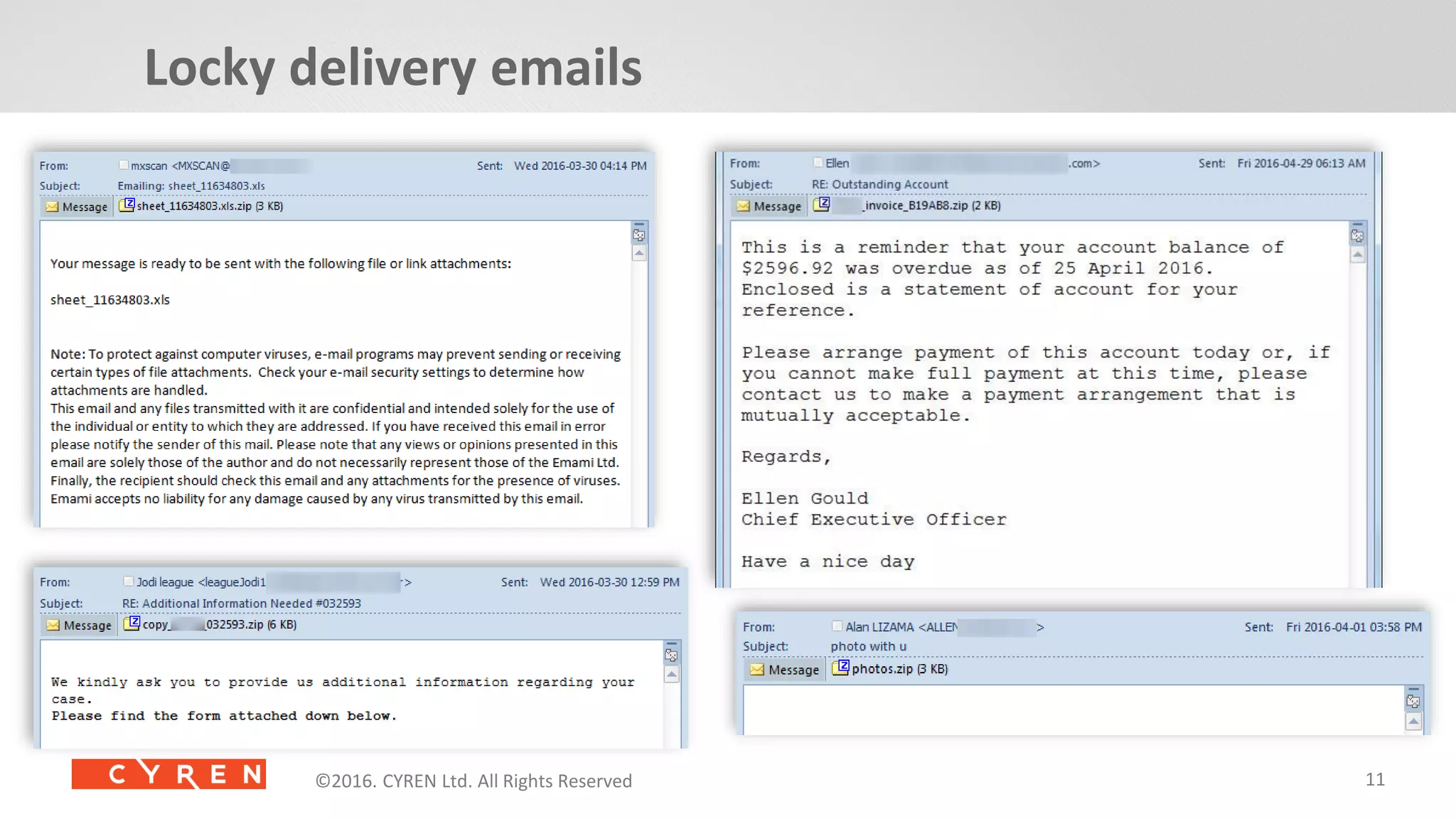
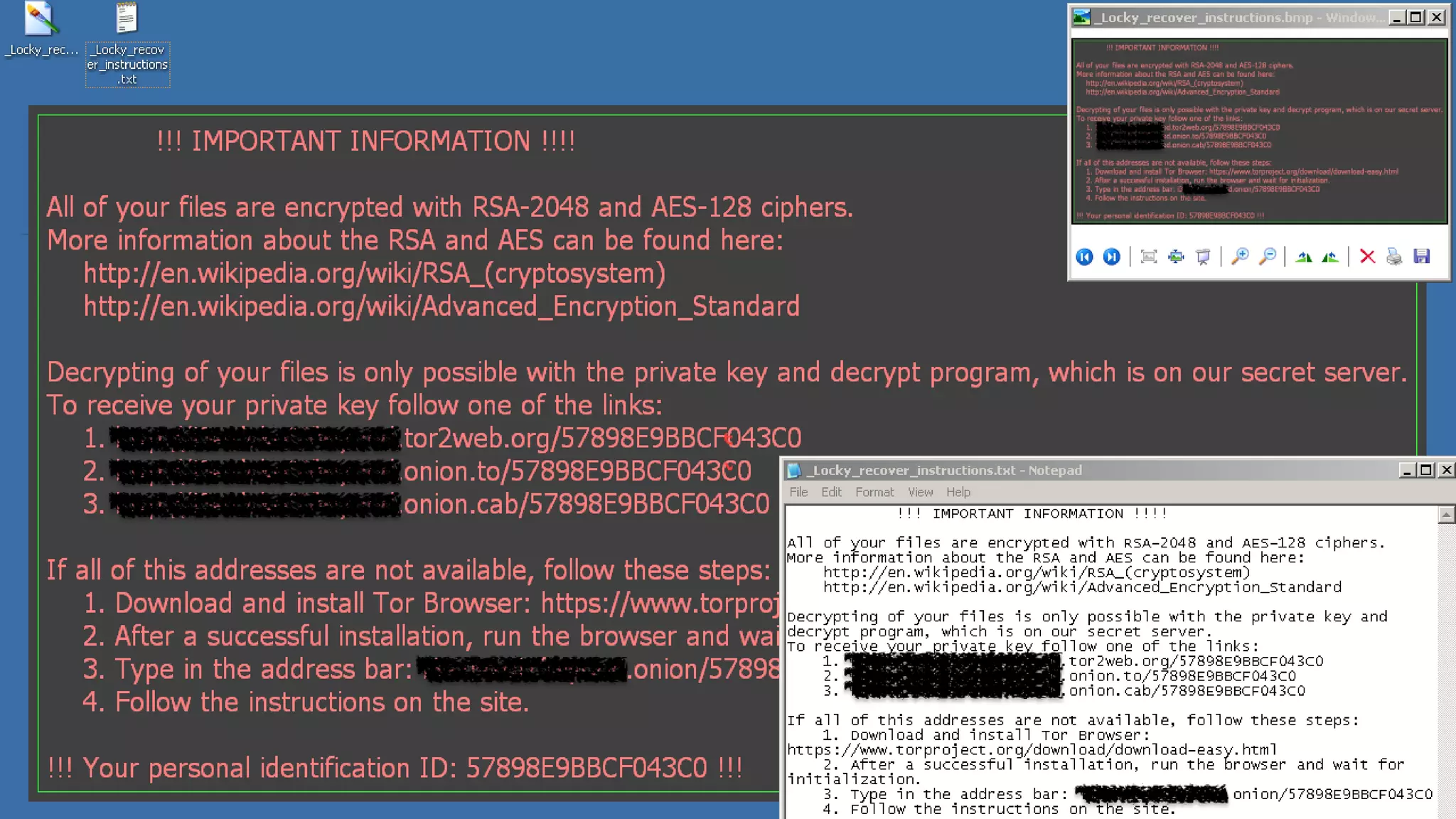
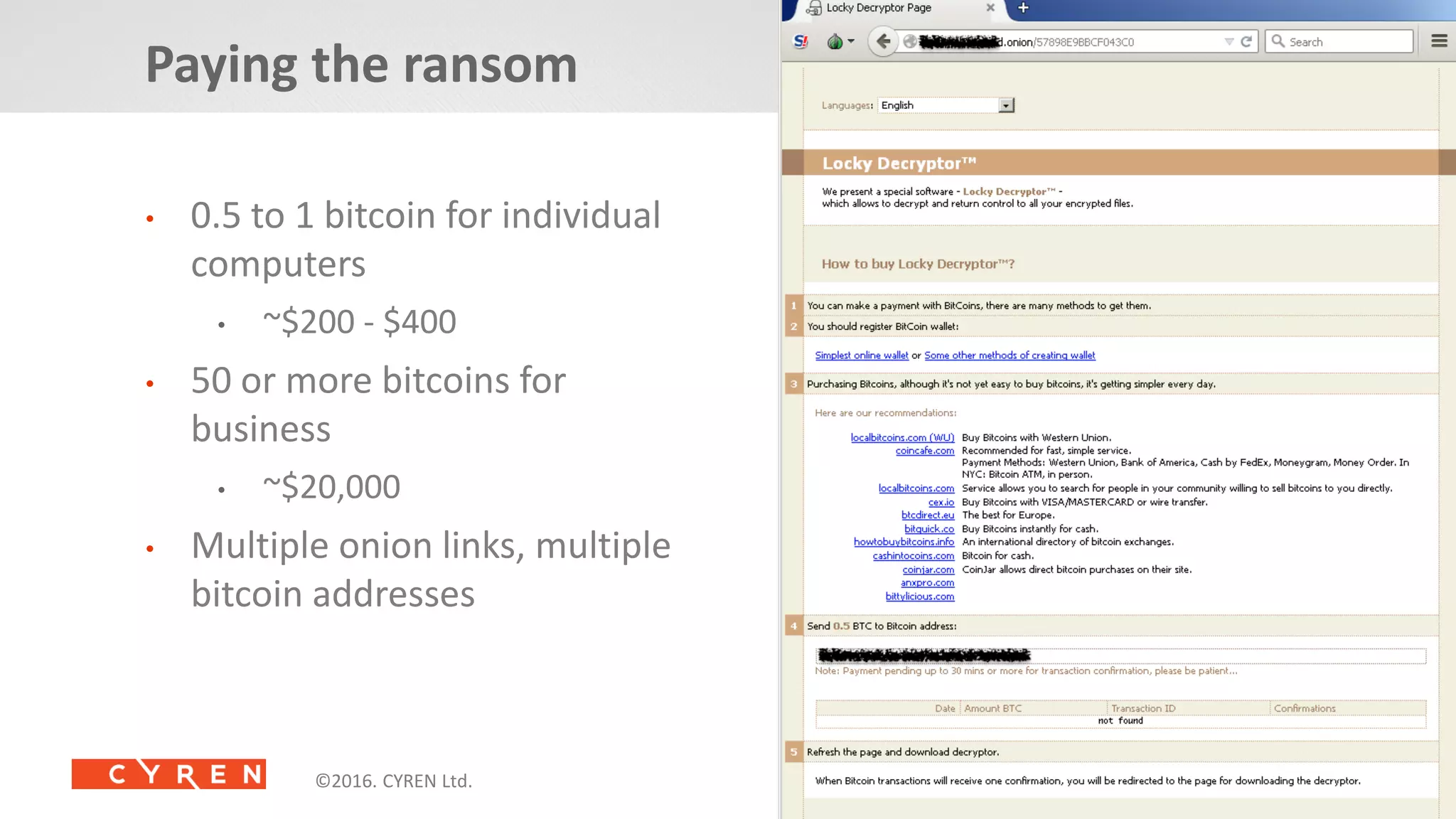
The document provides an in-depth analysis of ransomware, particularly focusing on various types such as Locky, Petya, and Jigsaw, highlighting their operation mechanisms and prevalence in Q1 2016. It discusses the rise of ransomware attacks, including delivery methods and payment demands, while also emphasizing the importance of prevention and detection strategies for individuals and organizations. Additionally, it presents Cyren's security solutions aimed at combating these cyber threats.