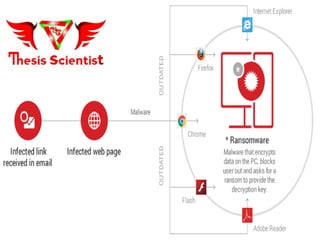
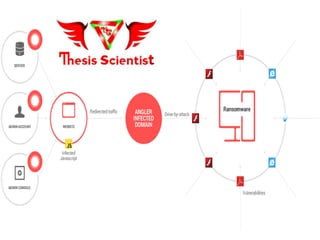
Ransomware has increasingly become a significant threat over the past two years, with two main types: encryptors that block system files for ransom and locker versions that infect the master boot record. Businesses are primary targets due to potential financial gain, complex systems, and vulnerabilities that cybercriminals can exploit. Common infection methods include spam emails, software exploits, and malicious website redirects.