Qubes os presentation_to_clug_20150727
•
2 likes•2,102 views
Presented to a technical Linux-using audience who know what a CVE is.
Report
Share
Report
Share
Download to read offline
Recommended
Ch 9: Embedded Operating Systems: The Hidden Threat

Slides for a college course at City College San Francisco. Based on "Hands-On Ethical Hacking and Network Defense, Third Edition" by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 9781285454610.
Instructor: Sam Bowne
Class website: https://samsclass.info/123/123_S17.shtml
Tails os

Tails is an operating system like Windows or Mac OS, but one specially designed to preserve your anonymity and privacy
Tails or The Amnesic Incognito Live System is a security-focused Debian-based Linux distribution aimed at preservingprivacy and anonymity
All its outgoing connections are forced to go through Tor,[4] and direct (non-anonymous) connections are blocked
The system is designed to be booted as a live DVD or live USB, and will leave no trace (digital footprint) on the machine unless explicitly told to do so. The Tor Project has provided most of the financial support for its development
it is the latest operating system,
Two Factor Authentication: Easy Setup, Major Impact

Presented in the Admin Theater at the Salesforce World Tour NYC on December 15, 2016.
Malicious file upload attacks - a case study

Example of Remote Code Execution using a Web application software.
Web Application Security 101

+ Background & Basics of Web App Security, The HTTP Protocol, Web.
+ Application Insecurities, OWASP Top 10 Vulnerabilities (XSS, SQL Injection, CSRF, etc.)
+ Web App Security Tools (Scanners, Fuzzers, etc), Remediation of Web App
+ Vulnerabilities, Web Application Audits and Risk Assessment.
Web Application Security 101 was conducted by:
Vaibhav Gupta, Vishal Ashtana, Sandeep Singh from Null.
Recommended
Ch 9: Embedded Operating Systems: The Hidden Threat

Slides for a college course at City College San Francisco. Based on "Hands-On Ethical Hacking and Network Defense, Third Edition" by Michael T. Simpson, Kent Backman, and James Corley -- ISBN: 9781285454610.
Instructor: Sam Bowne
Class website: https://samsclass.info/123/123_S17.shtml
Tails os

Tails is an operating system like Windows or Mac OS, but one specially designed to preserve your anonymity and privacy
Tails or The Amnesic Incognito Live System is a security-focused Debian-based Linux distribution aimed at preservingprivacy and anonymity
All its outgoing connections are forced to go through Tor,[4] and direct (non-anonymous) connections are blocked
The system is designed to be booted as a live DVD or live USB, and will leave no trace (digital footprint) on the machine unless explicitly told to do so. The Tor Project has provided most of the financial support for its development
it is the latest operating system,
Two Factor Authentication: Easy Setup, Major Impact

Presented in the Admin Theater at the Salesforce World Tour NYC on December 15, 2016.
Malicious file upload attacks - a case study

Example of Remote Code Execution using a Web application software.
Web Application Security 101

+ Background & Basics of Web App Security, The HTTP Protocol, Web.
+ Application Insecurities, OWASP Top 10 Vulnerabilities (XSS, SQL Injection, CSRF, etc.)
+ Web App Security Tools (Scanners, Fuzzers, etc), Remediation of Web App
+ Vulnerabilities, Web Application Audits and Risk Assessment.
Web Application Security 101 was conducted by:
Vaibhav Gupta, Vishal Ashtana, Sandeep Singh from Null.
Topics in network security

VPN, Malware Analysis, Digital Forensics, Penetration Testing, Firewalls etc.
Management file and directory in linux

In many ways, directories are treated like files. They can be created, deleted, moved and copied from Nautilus or from a shell prompt, using commands similar to those for files.
Creating Directories
You must have write permissions in a directory in order to create a new sub-directory. Most users have these permissions in their home directory (and its sub-directories) and the /tmp/ directory.
To create a new directory with Nautilus, navigate to the location of your new directory. Right-click in a blank portion of the window and select Create Folder. A new folder icon appears with the highlighted text untitled folder. Type a name for your folder and press [Enter].
To create a new directory using a shell prompt, use the command mkdir. Enter: mkdir <directory-name>, replacing <directory-name> with the intended title of the new directory.
Deleting Directories
To delete a directory from Nautilus, right click on it and choose Move to Trash, or click and drag the icon to the Trash on the Desktop.
To delete an empty directory from a shell prompt, enter the command rmdir. To delete a directory that may not be empty (and consequently everything inside that directory), enter the command rm -rf <directory>. Refer to Section 4.5.5 Delete files with rm for more information regarding the rm command.
Dot Directories
Applications create "dot" directories as well as dot files. Dot files are a single hidden configuration file — a dot directory is a hidden directory of configuration and other files required by the application. The non-configuration files in these directories are generally user-specific, and will be available only to the user who installed them.
Firewall and Types of firewall

In this PPT you can learn a firewall and types which help you a lot and you can able to understand. So, that you must read at once I sure that you are understand
Thank you!!!
I
Top 10 Web Application vulnerabilities

A walkthrough of web application defense strategies, based around the Open Web Application Security Project's top 10 list. Presented to the Classic City Developers Meetup in August 2017.
The Hacker's Guide to Kubernetes

Do you want to see live Kubernetes hacking? Come to see interactive demos where your newly registered accounts in a k8s application are hijacked.
This talk guides you through various security risk of Kubernetes, focusing on OWASP Kubernetes Top 10 list. In live demos, you will find out how to exploit a range of vulnerabilities or misconfigurations in your k8s clusters, attacking containers, pods, network, or k8s components, leading to an ultimate compromise of user accounts in an exemplary web application.
You will learn about common mistakes and vulnerabilities along with the best practices for hardening your Kubernetes systems.
Core Java Slides

A complete guide to java core edition comprising of 175 slides written in a lucid, simple manner.Useful for students as well as professionals.
I Heart Stuxnet

or: How I Learned To Stop Worrying And Love The Worm
Video: http://vimeo.com/17364186
More Related Content
What's hot
Topics in network security

VPN, Malware Analysis, Digital Forensics, Penetration Testing, Firewalls etc.
Management file and directory in linux

In many ways, directories are treated like files. They can be created, deleted, moved and copied from Nautilus or from a shell prompt, using commands similar to those for files.
Creating Directories
You must have write permissions in a directory in order to create a new sub-directory. Most users have these permissions in their home directory (and its sub-directories) and the /tmp/ directory.
To create a new directory with Nautilus, navigate to the location of your new directory. Right-click in a blank portion of the window and select Create Folder. A new folder icon appears with the highlighted text untitled folder. Type a name for your folder and press [Enter].
To create a new directory using a shell prompt, use the command mkdir. Enter: mkdir <directory-name>, replacing <directory-name> with the intended title of the new directory.
Deleting Directories
To delete a directory from Nautilus, right click on it and choose Move to Trash, or click and drag the icon to the Trash on the Desktop.
To delete an empty directory from a shell prompt, enter the command rmdir. To delete a directory that may not be empty (and consequently everything inside that directory), enter the command rm -rf <directory>. Refer to Section 4.5.5 Delete files with rm for more information regarding the rm command.
Dot Directories
Applications create "dot" directories as well as dot files. Dot files are a single hidden configuration file — a dot directory is a hidden directory of configuration and other files required by the application. The non-configuration files in these directories are generally user-specific, and will be available only to the user who installed them.
Firewall and Types of firewall

In this PPT you can learn a firewall and types which help you a lot and you can able to understand. So, that you must read at once I sure that you are understand
Thank you!!!
I
Top 10 Web Application vulnerabilities

A walkthrough of web application defense strategies, based around the Open Web Application Security Project's top 10 list. Presented to the Classic City Developers Meetup in August 2017.
The Hacker's Guide to Kubernetes

Do you want to see live Kubernetes hacking? Come to see interactive demos where your newly registered accounts in a k8s application are hijacked.
This talk guides you through various security risk of Kubernetes, focusing on OWASP Kubernetes Top 10 list. In live demos, you will find out how to exploit a range of vulnerabilities or misconfigurations in your k8s clusters, attacking containers, pods, network, or k8s components, leading to an ultimate compromise of user accounts in an exemplary web application.
You will learn about common mistakes and vulnerabilities along with the best practices for hardening your Kubernetes systems.
Core Java Slides

A complete guide to java core edition comprising of 175 slides written in a lucid, simple manner.Useful for students as well as professionals.
I Heart Stuxnet

or: How I Learned To Stop Worrying And Love The Worm
Video: http://vimeo.com/17364186
What's hot (20)
Similar to Qubes os presentation_to_clug_20150727
Practical Introduction To Linux

For people who want to start out with #opensource , #openstack, #cloud , #bigdata Linux is the foundational skill. Consider this a beginner guide to linux , understand why it is important , what is the landscape and how easy it is to learn it.
The learning cheat sheet can be utilized from http://linoxide.com/guide/linux-command-shelf.html
PDF version attached as well .
Making Clouds: Turning OpenNebula into a Product

What does it takes to bring innovations like private clouds to small and medium enterprises? In the course of this talk we will present our experience in creating a self-service toolkit for creating a complete virtualization and cloud platform based on OpenNebula, as well as our experience gathered in tens of installations of all sizes. From scalable storage (with benchmarks!) to autonomic optimization, we will present what in our view is needed to bring private clouds to everyone, what components and additions we created to better solve our customers’ problems (from replacing industrial control systems to medium scale virtual desktop infrastructures), and why OpenNebula has been chosen over other competing cloud toolkits.
OpenNebulaConf 2013 - Making Clouds: Turning OpenNebula into a Product by Car...

What does it takes to bring innovations like private clouds to small and medium enterprises? In the course of this talk we will present our experience in creating a self-service toolkit for creating a complete virtualization and cloud platform based on OpenNebula, as well as our experience gathered in tens of installations of all sizes. From scalable storage (with benchmarks!) to autonomic optimization, we will present what in our view is needed to bring private clouds to everyone, what components and additions we created to better solve our customers’ problems (from replacing industrial control systems to medium scale virtual desktop infrastructures), and why OpenNebula has been chosen over other competing cloud toolkits.
Bio:
Carlo Daffara the Technical director of Cloudweavers, and formerly head of research and development at Conecta, a consulting firm specializing in open source systems and distributed computing; Italian member of the European Working Group on Libre Software and co-coordinator of the working group on SMEs of the EU ICT task force on competitiveness. Since 1999, works as evaluator for IST programme submissions in the field of component-based software engineering, GRIDs and international cooperation. Coordinator of the open source platforms technical area of the IEEE technical committee on scalable computing, co-chair of the SIENA EU cloud initiative roadmap editorial board and part of the editorial review board of the International Journal of Open Source Software & Processes (IJOSSP).
Making clouds: turning opennebula into a product

A summary of our experiences and why we choose OpenNebula over competing open source cloud stacks for our CloudWeavers product.
Linux 开源操作系统发展新趋势

A guest lecture at National University of Defense Technology (NUDT) in 2016 to postgraduate students in China about emerging technologies in the Linux operating system.
Docker and containers : Disrupting the virtual machine(VM)

Talks briefly about Dockers and Containers, evolution and benefits.
Dev and Blind - Attacking the weakest Link in IT Security

The developer is an easy and valuable target for malicious minds. The reasons for that are numerous and hard to come by. This talk delivers examples, proof, discussion and awkward moments in a pretty special way.
Everybody hates developers – especially web developers. And why not? The cracks and crevices of their APIs and implementations are the reason that vulnerabilities in web applications are still a widespread issue – and will continue to be in the foreseeable future.
Bashing and blaming them for their wrongdoings is fun – boy, they are stupid in their mistakes! But has anyone ever dared to have an open on stage battle with an actual developer?
And who of the developers dares to face their collective nemesis – the attacker? Can there be life where matter and anti-matter collide? We will know about this soon – because this is what this talk is going to be about. Developer versus attacker – vulnerability versus defense. Be prepared for swearing, violence and people leaving the stage prematurely in tears.
The Ultimate List of Opensource Software for #docker #decentralized #selfhost...

A list and description for interesting open source software for
#docker #decentralized #selfhosted #privacy #security
It has a description and an indicative image for each one.
Node js presentation

NodeJS Presentation presented to Asset Technology Group employees. It's accompanied with a plenty of example source code (Link to be added later).
Docker - Demo on PHP Application deployment 

Docker is an open-source project to easily create lightweight, portable, self-sufficient containers from any application. The same container that a developer builds and tests on a laptop can run at scale, in production, on VMs, bare metal, OpenStack clusters, public clouds and more.
In this demo, I will show how to build a Apache image from a Dockerfile and deploy a PHP application which is present in an external folder using custom configuration files.
Portable OS & Portable Application

Introducing to Portable Operating Systems and Portable Applications.
Operating system Definition Structures

What is an operating System Structure?
We want a clear structure to let us apply an operating system to our particular needs because operating systems have complex structures. It is easier to create an operating system in pieces, much as we break down larger issues into smaller, more manageable subproblems. Every segment is also a part of the operating system. Operating system structure can be thought of as the strategy for connecting and incorporating various operating system components within the kernel. Operating systems are implemented using many types of structures, as will be discussed below:
SIMPLE STRUCTURE
It is the most straightforward operating system structure, but it lacks definition and is only appropriate for usage with tiny and restricted systems. Since the interfaces and degrees of functionality in this structure are clearly defined, programs are able to access I/O routines, which may result in unauthorized access to I/O procedures.
Dockers zero to hero

présentation de l'utilisation de Docker, du niveau 0 "je joue avec sur mon poste" au niveau Docker Hero "je tourne en prod".
Ce talk fait suite à l'intro de @dgageot et ne comporte donc pas l'intro "c'est quoi Docker ?".
Similar to Qubes os presentation_to_clug_20150727 (20)
OpenNebulaConf 2013 - Making Clouds: Turning OpenNebula into a Product by Car...

OpenNebulaConf 2013 - Making Clouds: Turning OpenNebula into a Product by Car...
Machine Learning , Analytics & Cyber Security the Next Level Threat Analytics...

Machine Learning , Analytics & Cyber Security the Next Level Threat Analytics...
Docker and containers : Disrupting the virtual machine(VM)

Docker and containers : Disrupting the virtual machine(VM)
Dev and Blind - Attacking the weakest Link in IT Security

Dev and Blind - Attacking the weakest Link in IT Security
The Ultimate List of Opensource Software for #docker #decentralized #selfhost...

The Ultimate List of Opensource Software for #docker #decentralized #selfhost...
Recently uploaded
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designer, Beats by Dr Dre
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

The IoT and OT threat landscape report has been prepared by the Threat Research Team at Sectrio using data from Sectrio, cyber threat intelligence farming facilities spread across over 85 cities around the world. In addition, Sectrio also runs AI-based advanced threat and payload engagement facilities that serve as sinks to attract and engage sophisticated threat actors, and newer malware including new variants and latent threats that are at an earlier stage of development.
The latest edition of the OT/ICS and IoT security Threat Landscape Report 2024 also covers:
State of global ICS asset and network exposure
Sectoral targets and attacks as well as the cost of ransom
Global APT activity, AI usage, actor and tactic profiles, and implications
Rise in volumes of AI-powered cyberattacks
Major cyber events in 2024
Malware and malicious payload trends
Cyberattack types and targets
Vulnerability exploit attempts on CVEs
Attacks on counties – USA
Expansion of bot farms – how, where, and why
In-depth analysis of the cyber threat landscape across North America, South America, Europe, APAC, and the Middle East
Why are attacks on smart factories rising?
Cyber risk predictions
Axis of attacks – Europe
Systemic attacks in the Middle East
Download the full report from here:
https://sectrio.com/resources/ot-threat-landscape-reports/sectrio-releases-ot-ics-and-iot-security-threat-landscape-report-2024/
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Sidekick Solutions uses Bonterra Impact Management (fka Social Solutions Apricot) and automation solutions to integrate data for business workflows.
We believe integration and automation are essential to user experience and the promise of efficient work through technology. Automation is the critical ingredient to realizing that full vision. We develop integration products and services for Bonterra Case Management software to support the deployment of automations for a variety of use cases.
This video focuses on the notifications, alerts, and approval requests using Slack for Bonterra Impact Management. The solutions covered in this webinar can also be deployed for Microsoft Teams.
Interested in deploying notification automations for Bonterra Impact Management? Contact us at sales@sidekicksolutionsllc.com to discuss next steps.
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scalable Platform by VP of Product, The New York Times
Essentials of Automations: Optimizing FME Workflows with Parameters

Are you looking to streamline your workflows and boost your projects’ efficiency? Do you find yourself searching for ways to add flexibility and control over your FME workflows? If so, you’re in the right place.
Join us for an insightful dive into the world of FME parameters, a critical element in optimizing workflow efficiency. This webinar marks the beginning of our three-part “Essentials of Automation” series. This first webinar is designed to equip you with the knowledge and skills to utilize parameters effectively: enhancing the flexibility, maintainability, and user control of your FME projects.
Here’s what you’ll gain:
- Essentials of FME Parameters: Understand the pivotal role of parameters, including Reader/Writer, Transformer, User, and FME Flow categories. Discover how they are the key to unlocking automation and optimization within your workflows.
- Practical Applications in FME Form: Delve into key user parameter types including choice, connections, and file URLs. Allow users to control how a workflow runs, making your workflows more reusable. Learn to import values and deliver the best user experience for your workflows while enhancing accuracy.
- Optimization Strategies in FME Flow: Explore the creation and strategic deployment of parameters in FME Flow, including the use of deployment and geometry parameters, to maximize workflow efficiency.
- Pro Tips for Success: Gain insights on parameterizing connections and leveraging new features like Conditional Visibility for clarity and simplicity.
We’ll wrap up with a glimpse into future webinars, followed by a Q&A session to address your specific questions surrounding this topic.
Don’t miss this opportunity to elevate your FME expertise and drive your projects to new heights of efficiency.
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI)
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head of Product, Amazon Games
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Have you ever wanted a Ruby client API to communicate with your web service? Smithy is a protocol-agnostic language for defining services and SDKs. Smithy Ruby is an implementation of Smithy that generates a Ruby SDK using a Smithy model. In this talk, we will explore Smithy and Smithy Ruby to learn how to generate custom feature-rich SDKs that can communicate with any web service, such as a Rails JSON API.
Connector Corner: Automate dynamic content and events by pushing a button

Here is something new! In our next Connector Corner webinar, we will demonstrate how you can use a single workflow to:
Create a campaign using Mailchimp with merge tags/fields
Send an interactive Slack channel message (using buttons)
Have the message received by managers and peers along with a test email for review
But there’s more:
In a second workflow supporting the same use case, you’ll see:
Your campaign sent to target colleagues for approval
If the “Approve” button is clicked, a Jira/Zendesk ticket is created for the marketing design team
But—if the “Reject” button is pushed, colleagues will be alerted via Slack message
Join us to learn more about this new, human-in-the-loop capability, brought to you by Integration Service connectors.
And...
Speakers:
Akshay Agnihotri, Product Manager
Charlie Greenberg, Host
AI for Every Business: Unlocking Your Product's Universal Potential by VP of ...

AI for Every Business: Unlocking Your Product's Universal Potential by VP of Product, Slack
Recently uploaded (20)
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
Designing Great Products: The Power of Design and Leadership by Chief Designe...

Designing Great Products: The Power of Design and Leadership by Chief Designe...
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

State of ICS and IoT Cyber Threat Landscape Report 2024 preview
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...

From Siloed Products to Connected Ecosystem: Building a Sustainable and Scala...
Essentials of Automations: Optimizing FME Workflows with Parameters

Essentials of Automations: Optimizing FME Workflows with Parameters
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
Generating a custom Ruby SDK for your web service or Rails API using Smithy

Generating a custom Ruby SDK for your web service or Rails API using Smithy
Connector Corner: Automate dynamic content and events by pushing a button

Connector Corner: Automate dynamic content and events by pushing a button
AI for Every Business: Unlocking Your Product's Universal Potential by VP of ...

AI for Every Business: Unlocking Your Product's Universal Potential by VP of ...
Qubes os presentation_to_clug_20150727
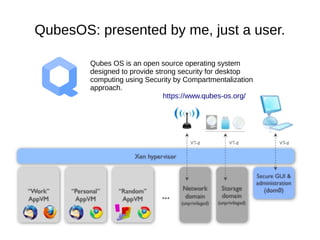
- 1. QubesOS: presented by me, just a user. Qubes OS is an open source operating system designed to provide strong security for desktop computing using Security by Compartmentalization approach. https://www.qubes-os.org/
- 2. Qubes OS is an open source operating system designed to provide strong security for desktop computing using Security by Compartmentalization approach. https://www.qubes-os.org/ Talk contains bias, errors, grudges, revisionist tendencies, misunderstandings and the seeds of its own destruction
- 3. What QubesOS is ● Not a Linux distro - though it runs Fedora on dom0 (admin) domain – Debian, Arch Linux and other TemplateVMs available ● Not a Hypervisor - though it boots Xen – QubesOS R3 (still in development) design abstracts VMM to more easily allow non-Xen implementations – KVM, LXC, Microsoft App- V (one or more of these appear to have been dead-ends) – NICTA has hosted some efforts to port Qubes to seL4, inter-VM communications services apparently done ● Often described as a Xen distro, but has lots of components in domU guests to facilitate the Qubes mission...
- 4. The problem: The endpoint PC ● Most security – especially in Linux – is intended for servers... ● … static. Deterministic lifecycle, predictable observable behaviours, management processes, audit logging, measurable/designable/configurable exposure to 3rd-parties ● Security policy is tractable and definable: network in/egress whitelisting, SELinux, AppArmor, setfacl, etc. ● Configuration management: puppet/chef/salt/ansible/etc ● Extra kernel hardening possible, Eg. TrustedGrub, Grsec, locking down loadable kernel modules, etc. ● Some of this is vaguely achievable in corporate SOEs, but.. ● … without all this bling that breaks client PCs, our operating systems only have process-level isolation to fall back on
- 5. The problem: The endpoint PC
- 6. Process isolation solves nothing Mac, Linux & Windows provide user apps APIs for: ● Capturing keystrokes regardless of which app is in focus – MacOS: addGlobalMonitorForEventsMatchingMask:NSKeyDownMask, Windows: LowLevelKeyboardProc/SetWindowsHookEx, Linux: xev EDIT 2016-02-04 – MacOS requires user intervention to grant permissions to NSKeyDown, thanks https://twitter.com/co60ca ● Screenshotting the desktop, including other applications ● Snooping clipboard contents (password managers!) ● Outbound internet access (sometimes, even inbound!) ● Filesystem access as the logged-in human user (home dir!) ● Accessing devices, services, sometimes IPC of other apps All our MMUs/protected memory, ACLs, ring0/kernel vs ring3/user space means nothing - who needs privilege escalation or authentication bypass when you've got “isolation” like this!
- 7. Process isolation solves nothing
- 8. “So what? I'll just be careful” ● It's true, on Linux we usually install packages from trusted sources. Package managers verify signatures with PGP. ● On Windows, AppLocker allows configuration to only install and run signed software from trusted publishers. ● On MacOS, GateKeeper allows configuration to only install and run signed software from the App Store or Apple approved publishers. ● Yet it's easy to bypass in just a few clicks. ● Studies show human brains are not suited to rationally navigating security warnings; the whole concept is flawed. ● “Antivirus is dead” - crypting services make evasion child's play. ASD lists it at #22 out of 35 top targeted cyber intrusion mitigations! ● Malware needs only one opportunity, so you must never slip up.
- 9. “So what? I'll just be careful”
- 10. “I'm not a target and I know what I'm doing” ● Are you really immune to drive-by remote code execution? – CVE-2015-5119 flash exploit even escapes Google Chrome's sandbox, on all platforms including Linux – Adobe Acrobat Reader has had 62 CVEs scoring 10.0 (maximum) so far this year (55 involving code exec) – Don't be fooled by lack of researcher activity and CVEs on evince and friends. The two on evince are both remote code exec. ● Do you know how quick & easy it is for phishers to build or clone trojaned versions of sites with enticing content? ● Are you sure you don't work in an industry targeted by state- sponsored1 hackers? 1: Jose Pagliery Ex-NSA director: China has hacked 'every major corporation' in U.S., March 2015 http://money.cnn.com/2015/03/13/technology/security/chinese-hack-us/
- 11. Solution: VMs for isolation – enforcing fewer, smaller interfaces Source: Joanna Rutkowska Software compartmentalization vs. physical separation(Or why Qubes OS is more than just a random collection of Vms), 2014. Available from: <http://www.invisiblethingslab.com/resources/2014/Software_compartmentalization_vs_physical_separation.pdf> [2015-07-22]
- 12. Demo ● Qubes manager – Dom0 has no networking, no apps, no data (show /proc/net/dev) – Shared free memory – Config (create new USB VM) – “Global” vs AppVM copy-paste; show xev/xeyes; window decorations ● Net/firewall/proxy VMs/whonix – xl device pass-through ● Disposable VMs ● Template VMs – Non-persistent rootfs vs persistent storage ● USB storage VM – Demonstrate rubber ducky ● PDF reader/converter in DisposableVM ● Mention GPG