The document details the process of securing Prometheus exporters using HashiCorp Vault, providing installation instructions for both Prometheus and Node Exporter. It covers secret management, configuring PKI, and automating certificate lifecycle management. The setup emphasizes security practices for scraping metrics with Vault-issued certificates and includes examples of configuration files and commands.



![Prometheus Config
global:
scrape_interval: 15s
evaluation_interval: 15s
scrape_configs:
- job_name: "node_exporter"
static_configs:
- targets: ["node.pki.vagrant:9100"]](https://image.slidesharecdn.com/speuhc-220217122305/75/Securing-Prometheus-exporters-using-HashiCorp-Vault-5-2048.jpg)

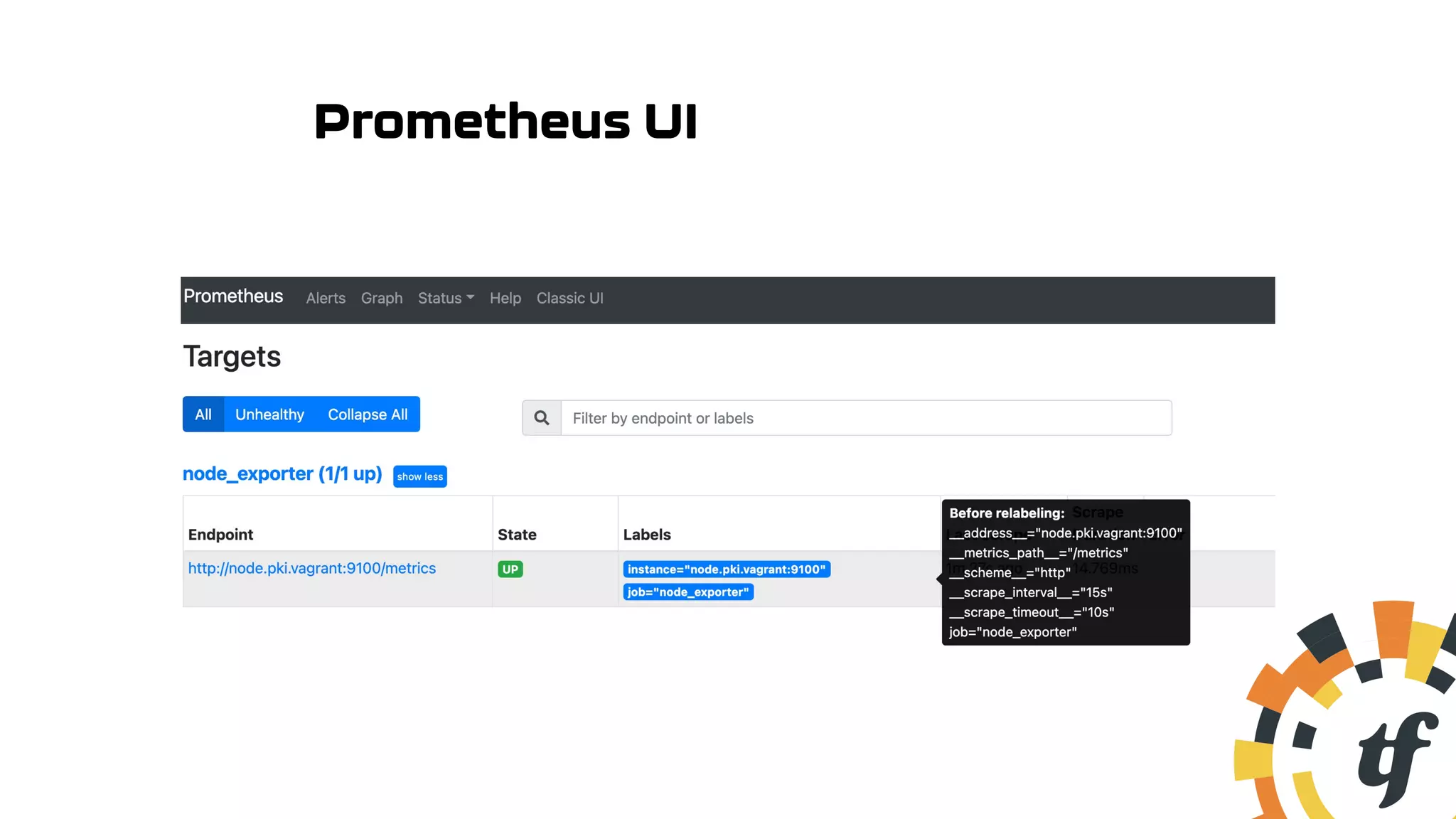


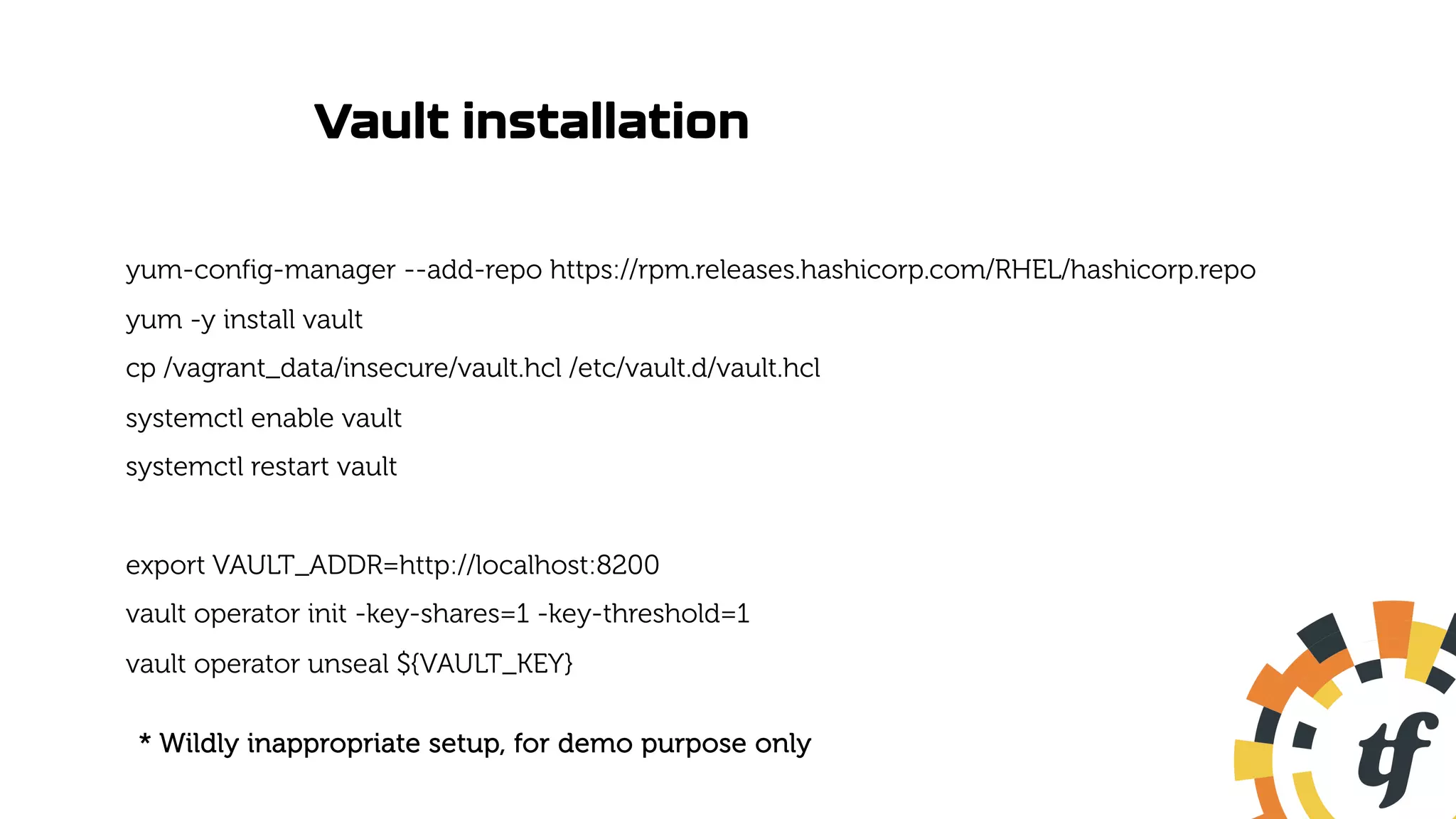

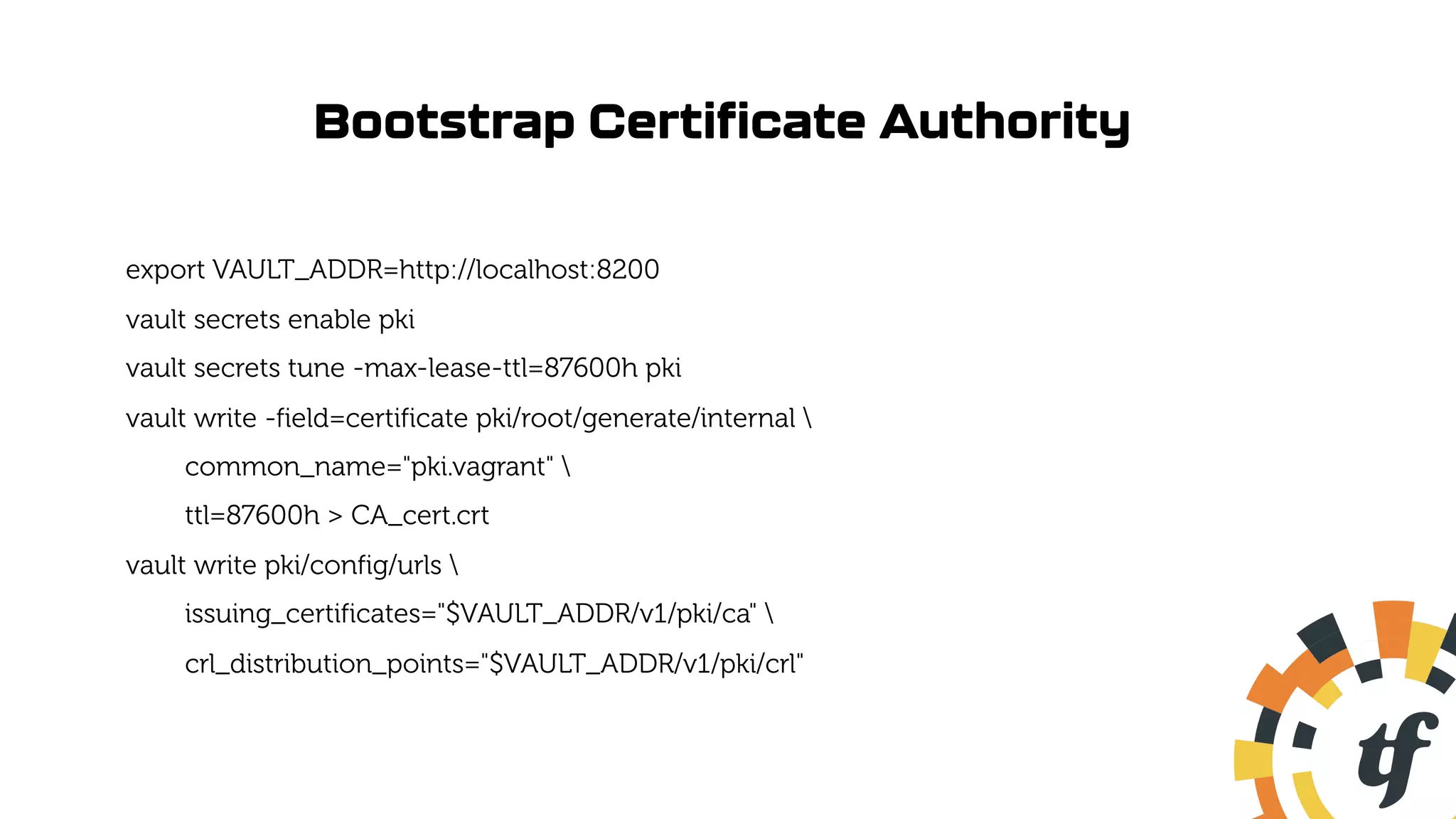


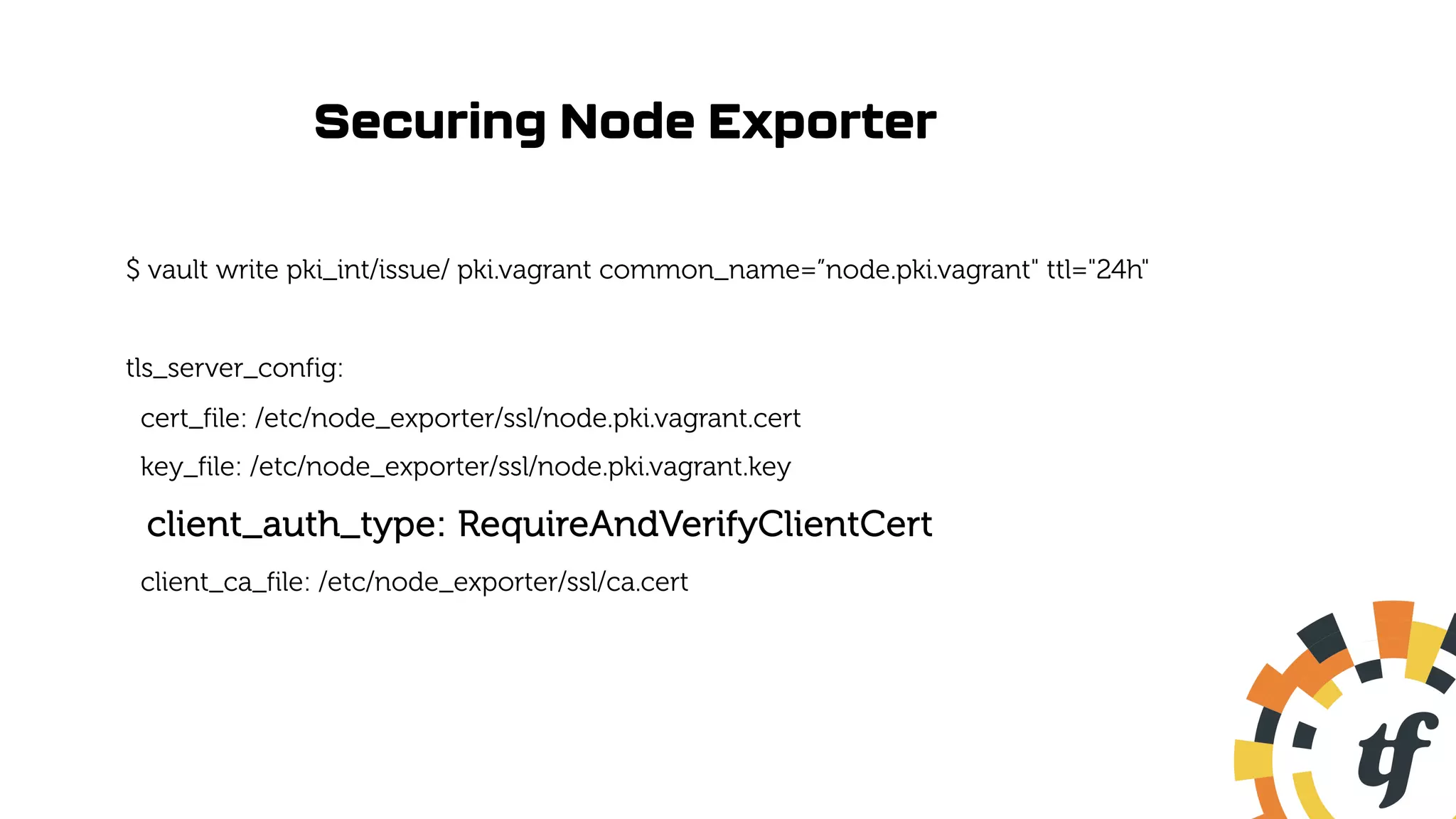
![Update Prometheus Connection
global:
scrape_interval: 15s
evaluation_interval: 15s
scrape_configs:
- job_name: "tls"
scheme: https
static_configs: - targets: [”node.pki.vagrant:9100"]
tls_config:
cert_file: /etc/prometheus/ssl/prometheus.pki.vagrant.cert
key_file: /etc/prometheus/ssl/prometheus.pki.vagrant.key
ca_file: /etc/prometheus/ssl/ca.cert](https://image.slidesharecdn.com/speuhc-220217122305/75/Securing-Prometheus-exporters-using-HashiCorp-Vault-18-2048.jpg)
![Vault PKI Approle
vault auth enable approle
vault policy write pki_policy /vagrant_data/tls/pki_policy.hcl
path "pki_int*" { capabilities = ["create", "read", "update", "delete", "list", "sudo"]}
* Wildly insecure config, for demo purpose only](https://image.slidesharecdn.com/speuhc-220217122305/75/Securing-Prometheus-exporters-using-HashiCorp-Vault-20-2048.jpg)
![Vault Agent Service
[Unit]
Description="Vault Agent to serve Tokens"
Wants=network-online.target
After=network-online.target
[Service]
Type=simple
WorkingDirectory=/etc/vault.d
ExecStart=/usr/bin/vault agent -config=/etc/vault.d/certs.hcl
[Install]
WantedBy=multi-user.target](https://image.slidesharecdn.com/speuhc-220217122305/75/Securing-Prometheus-exporters-using-HashiCorp-Vault-23-2048.jpg)