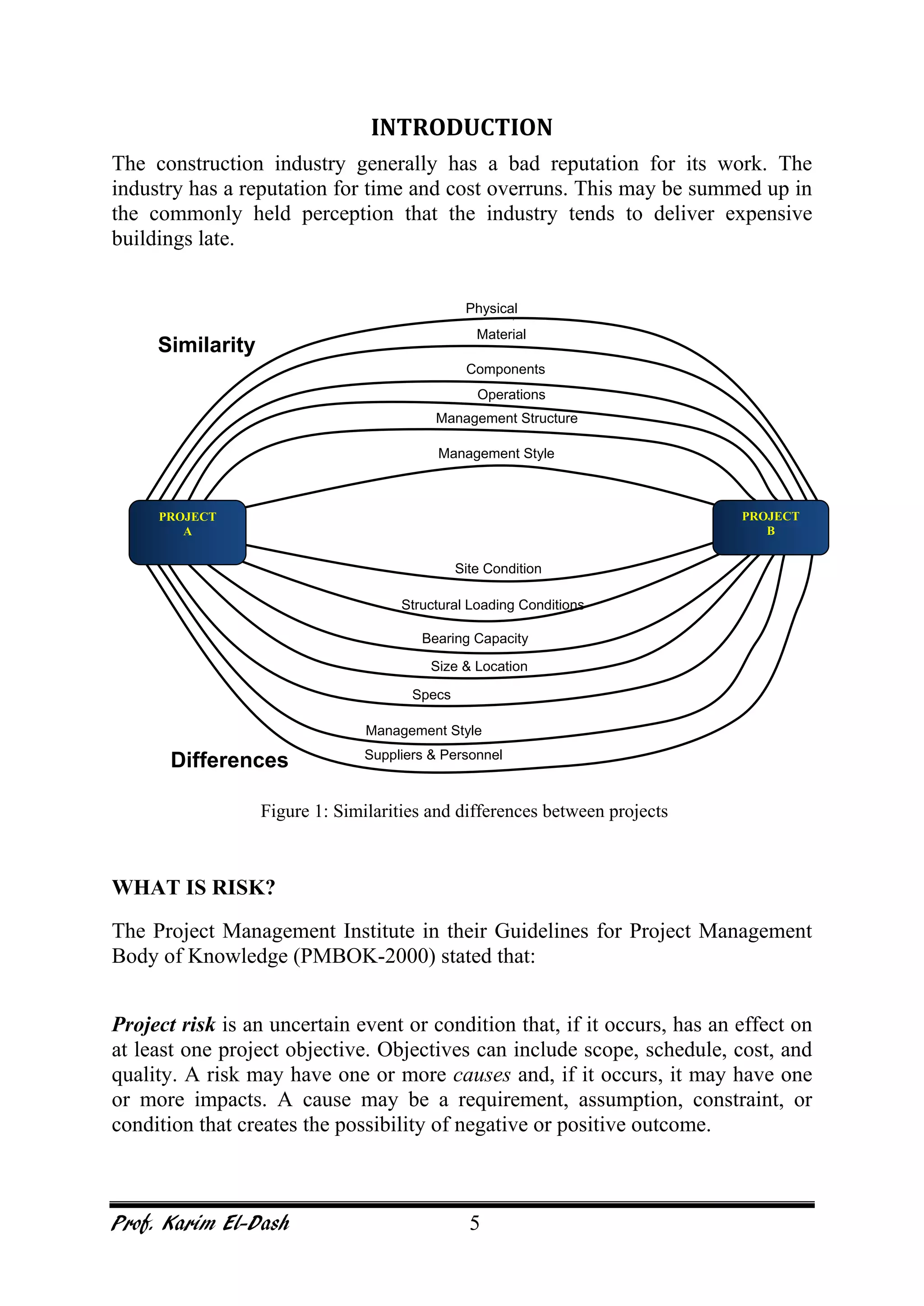
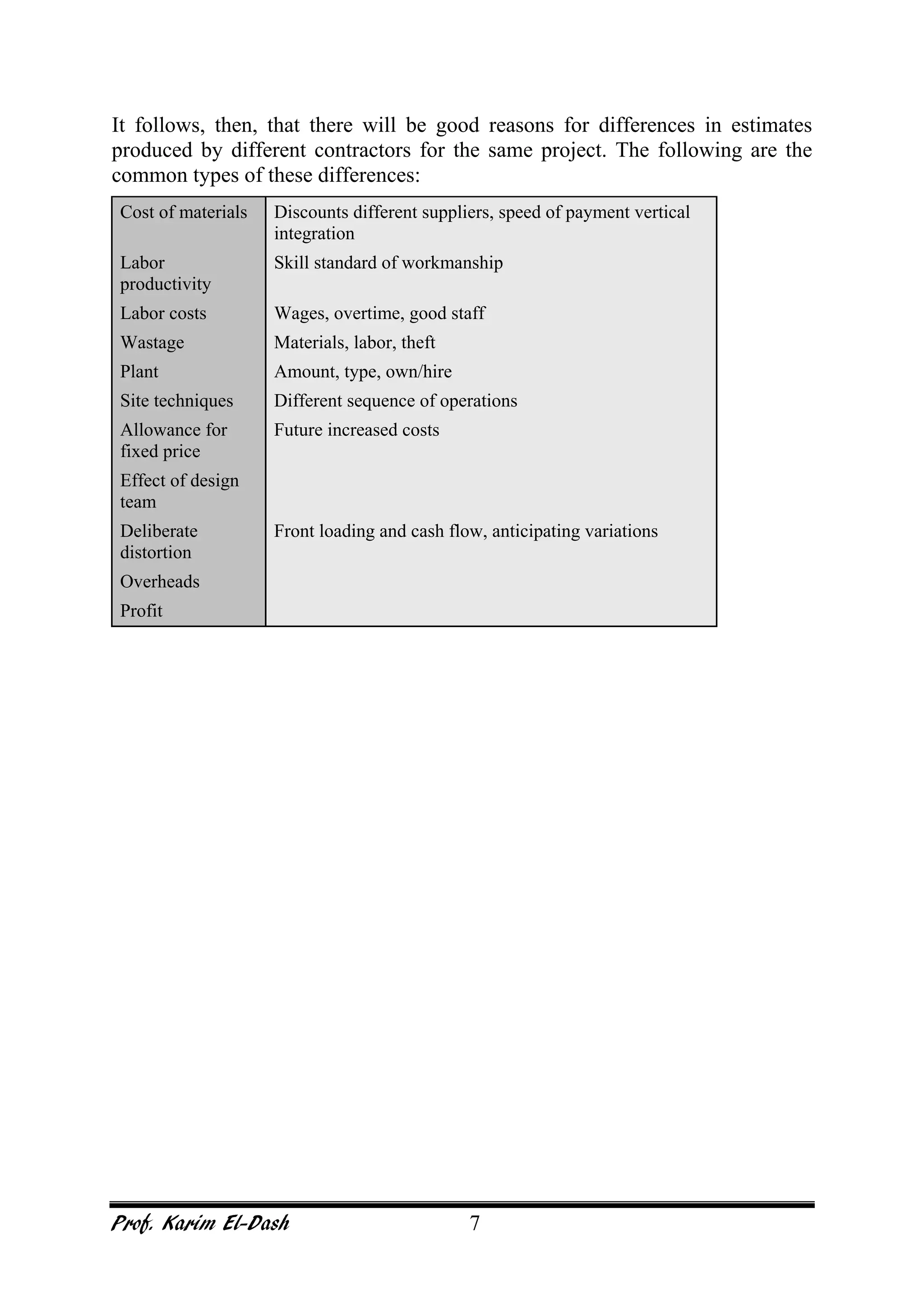
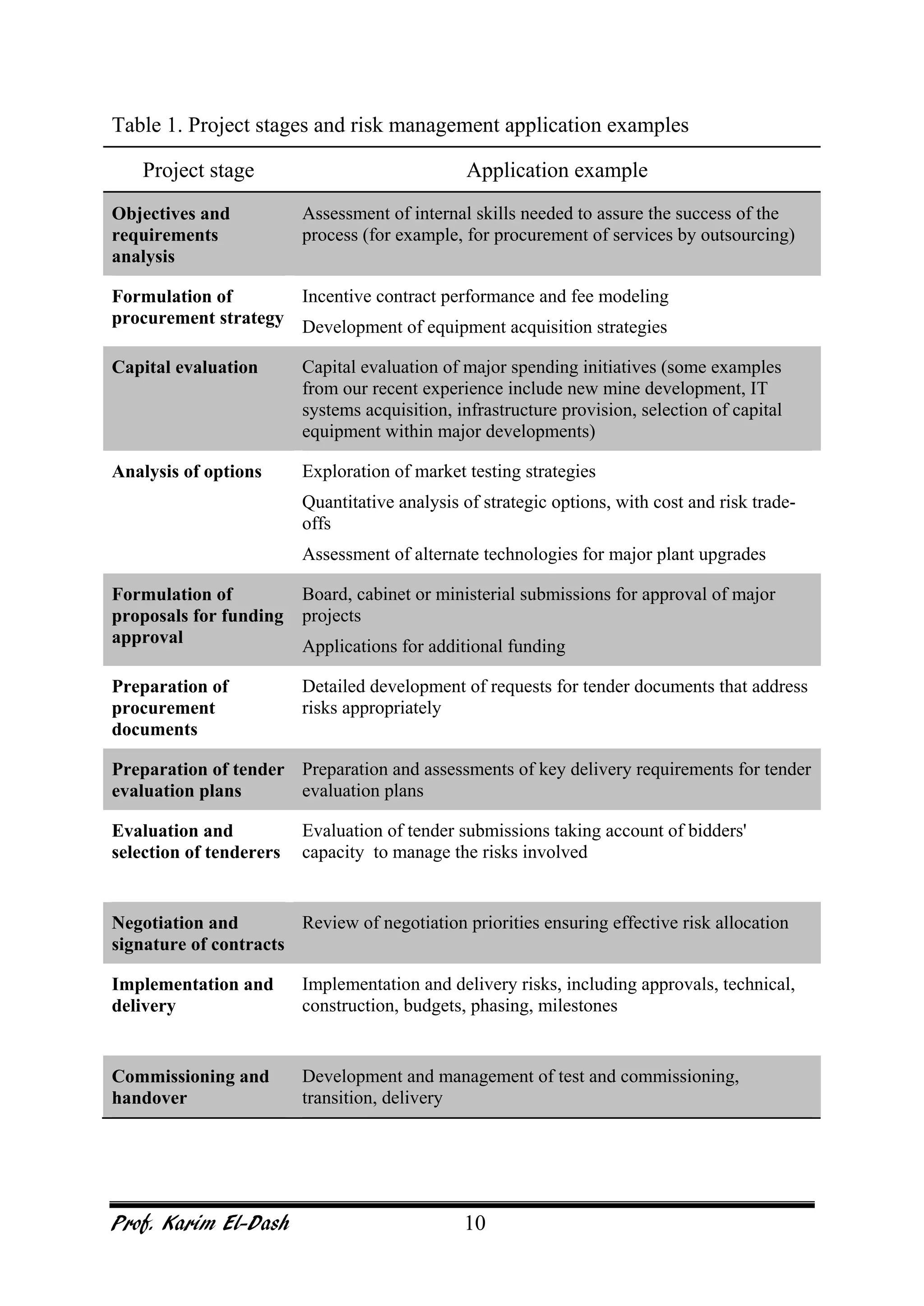
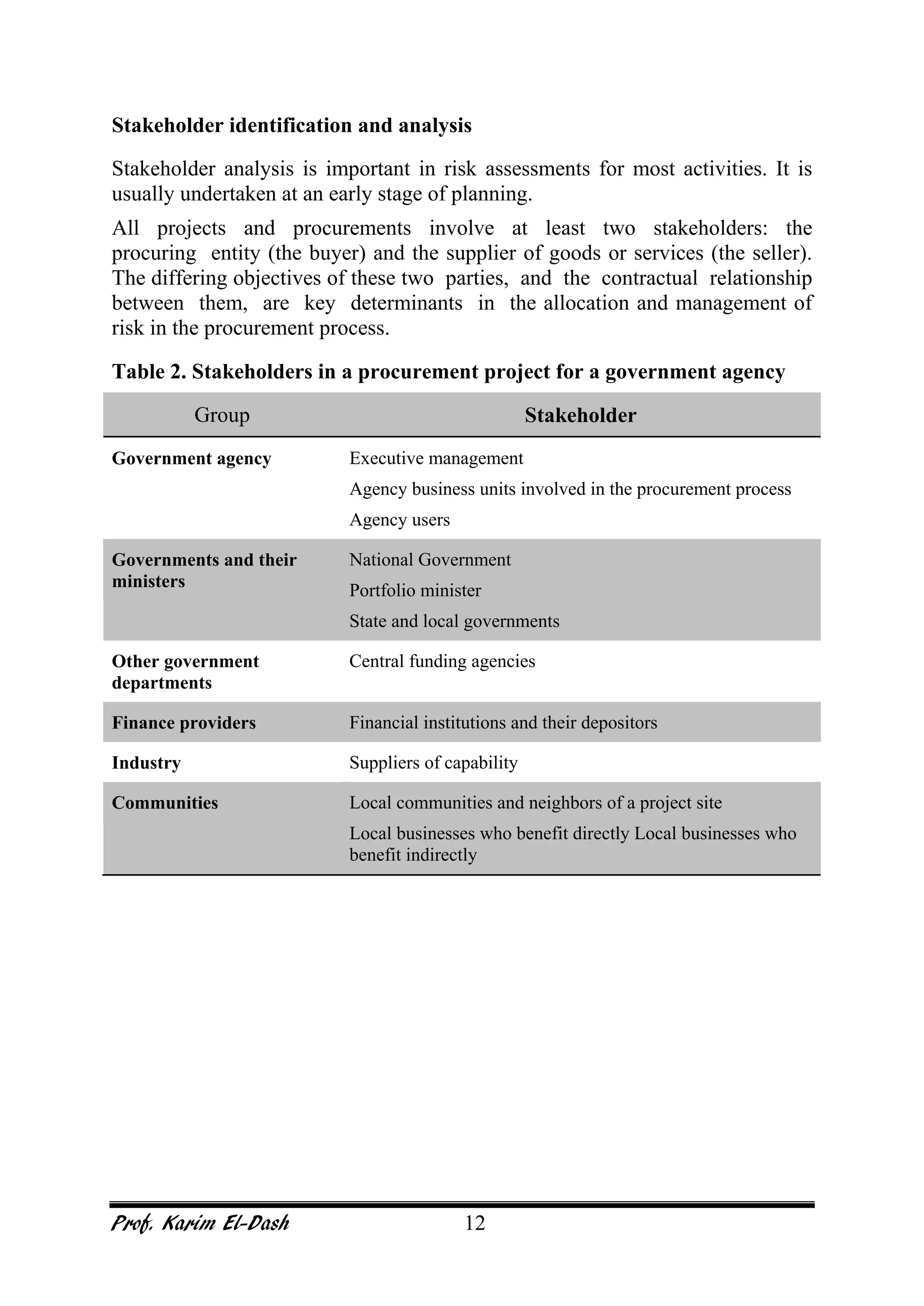
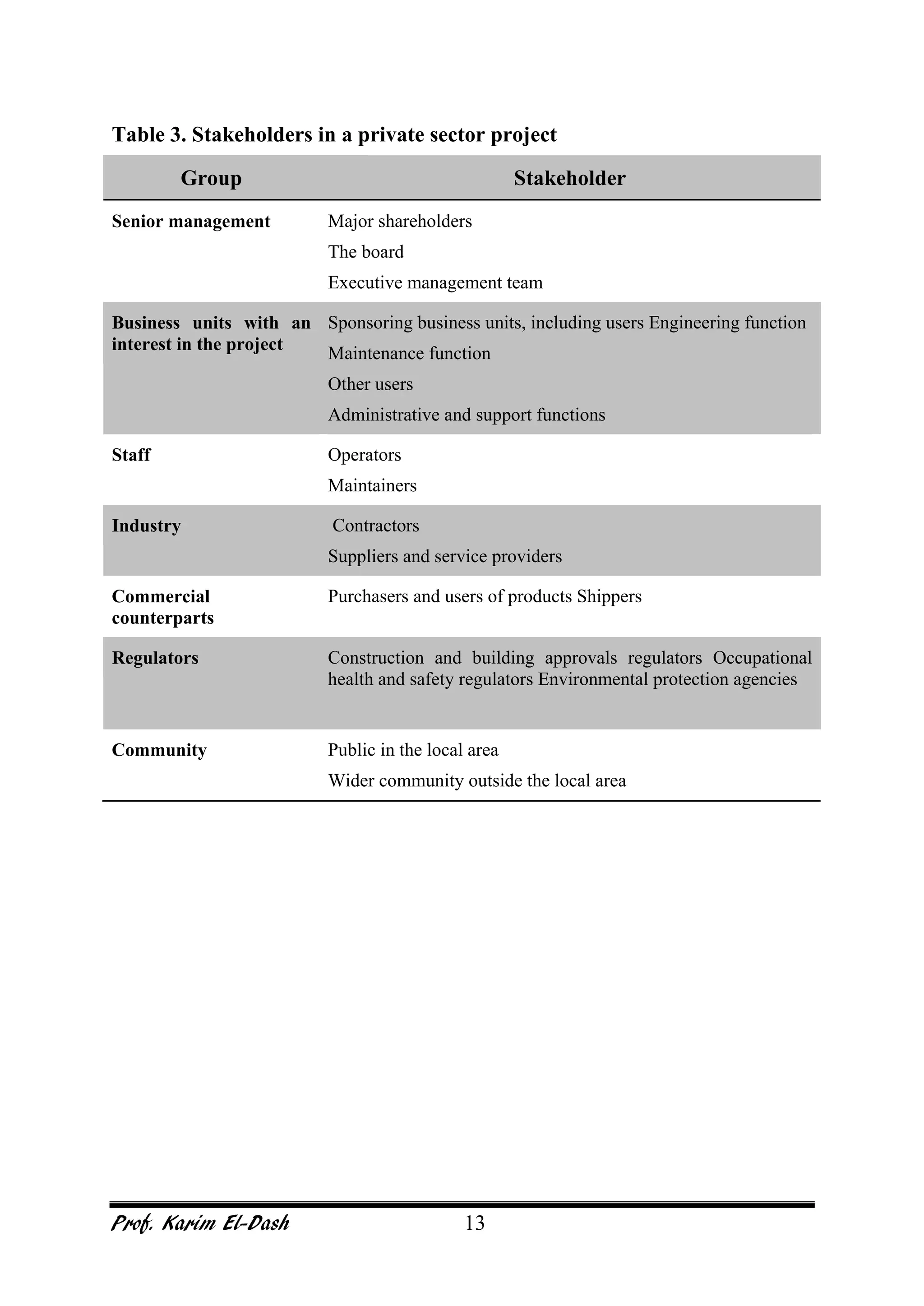
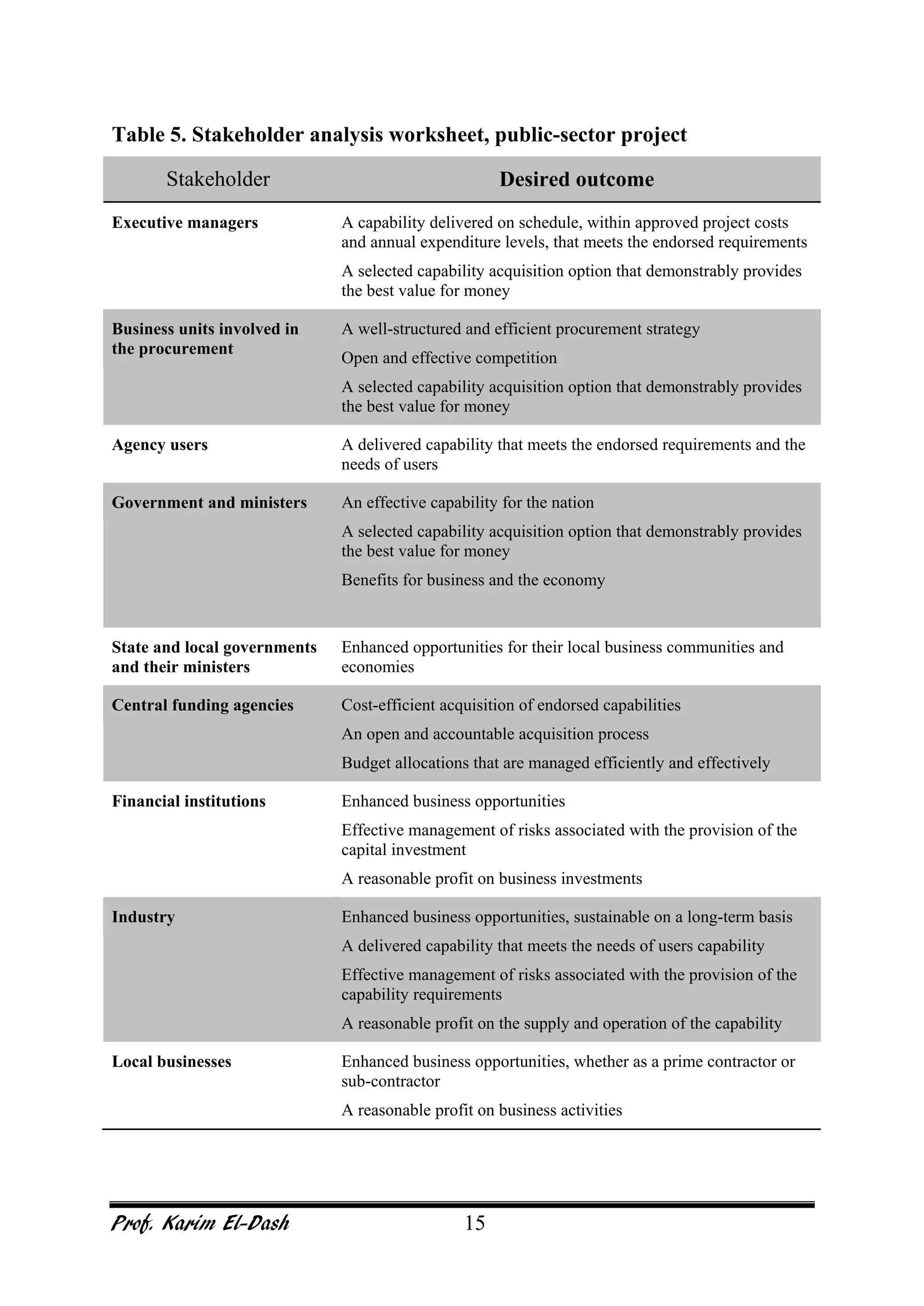
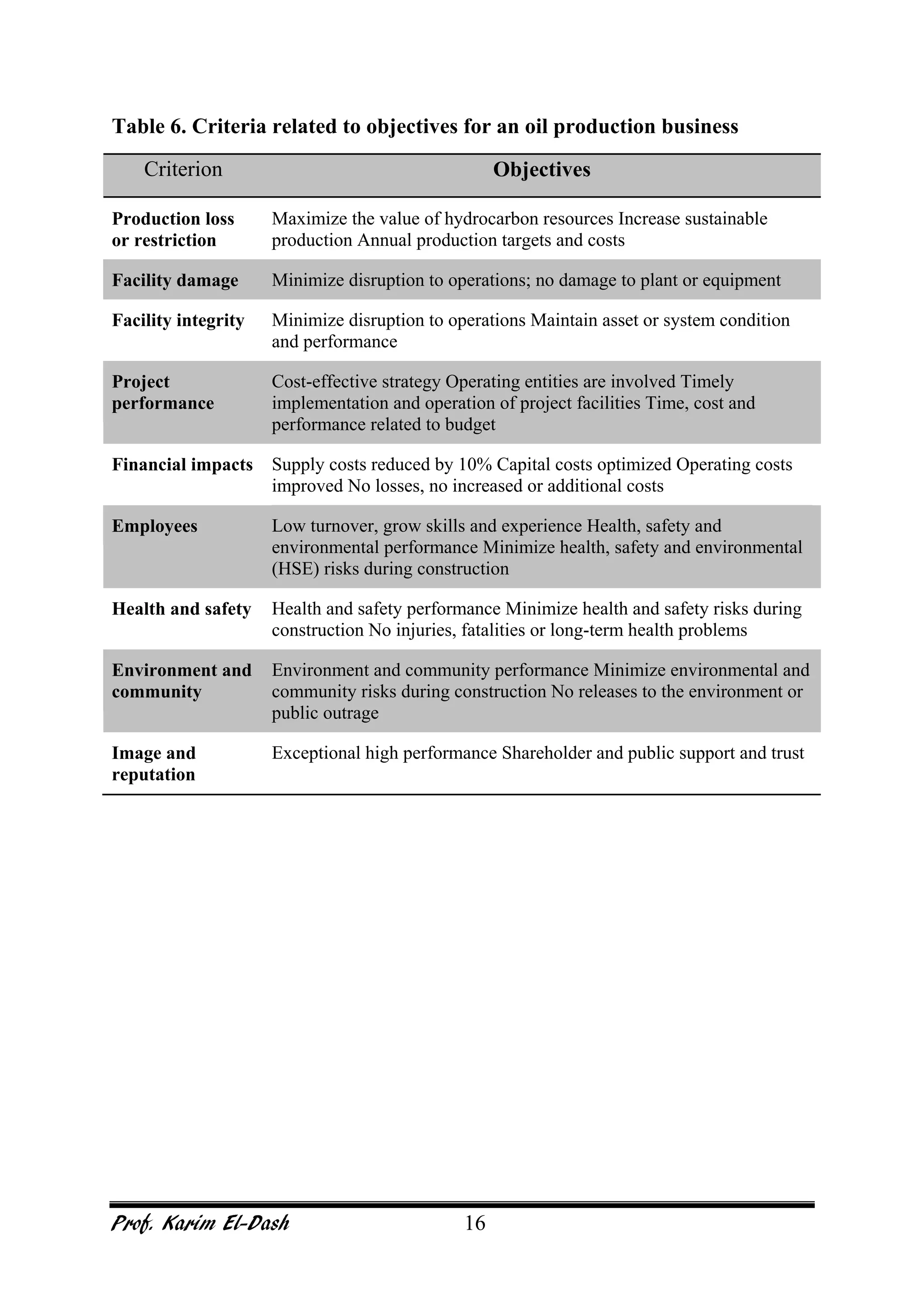
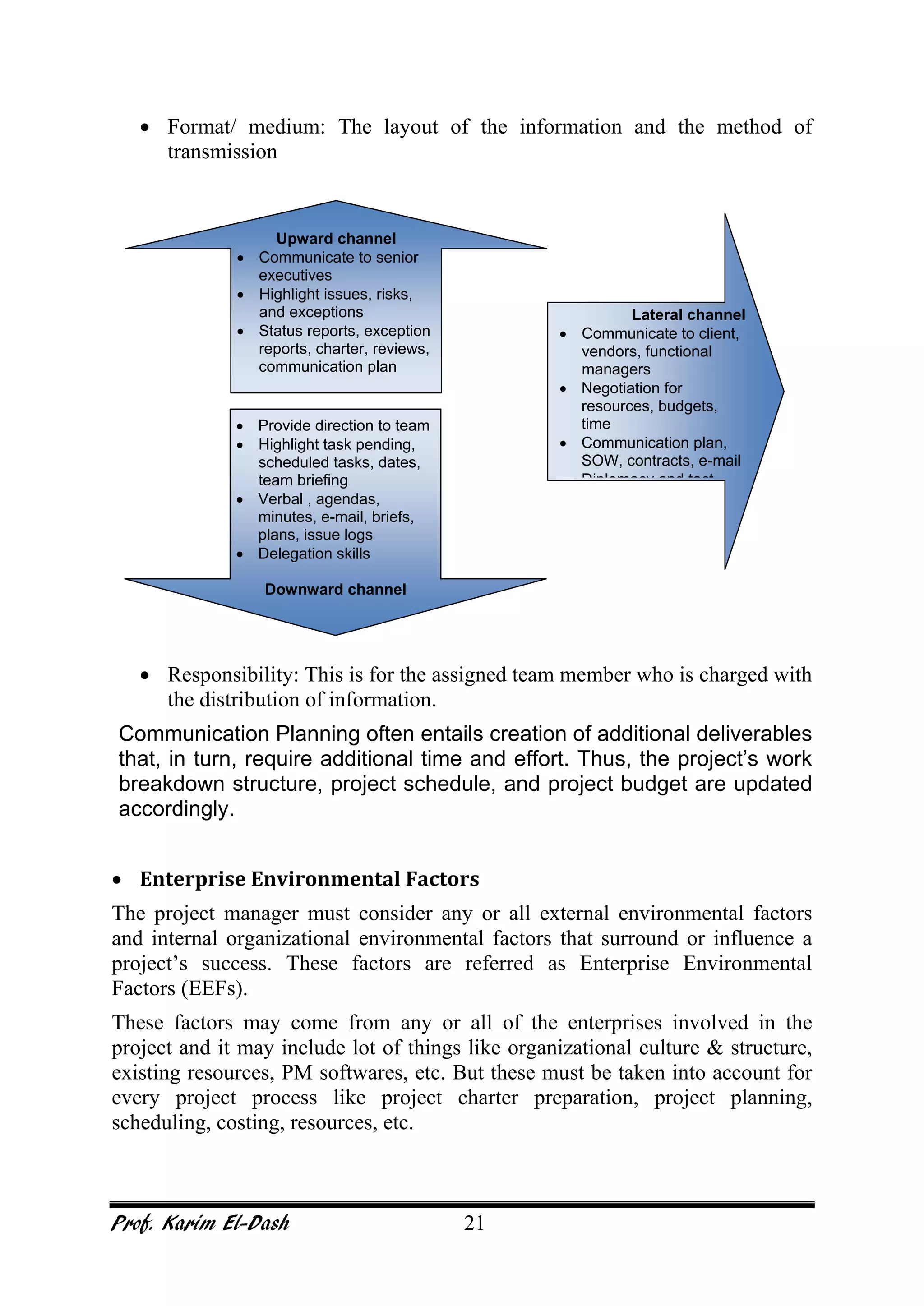
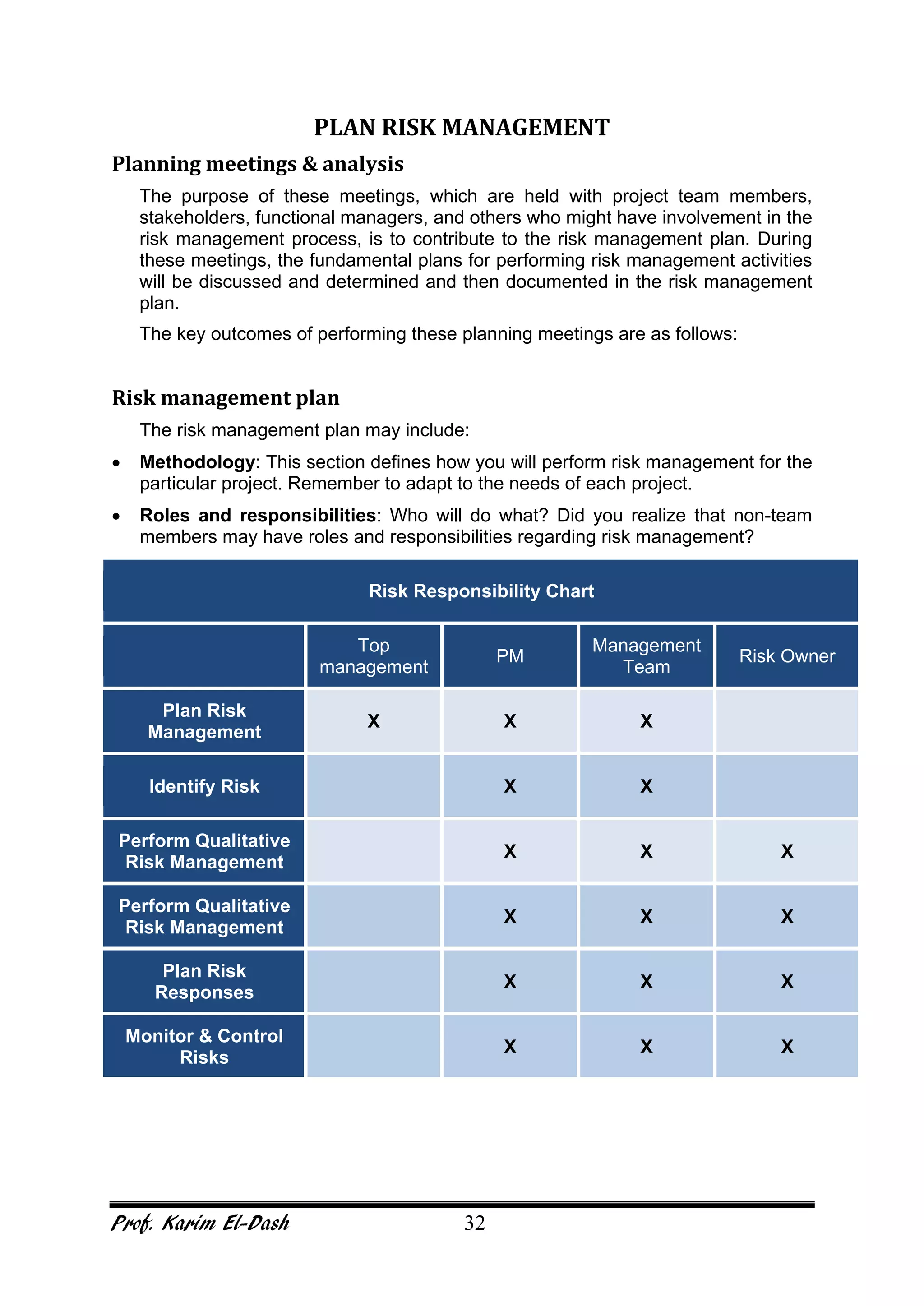
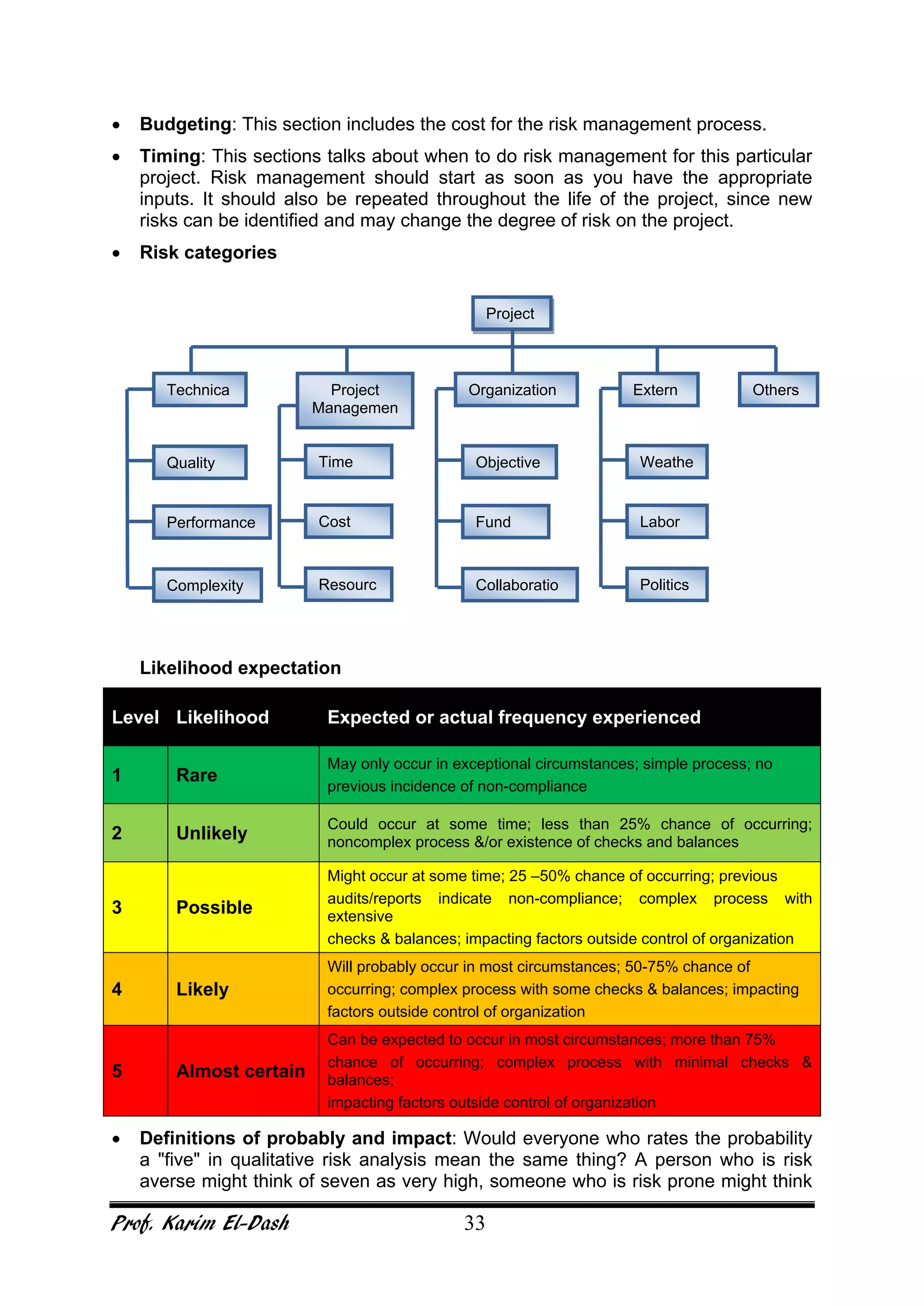
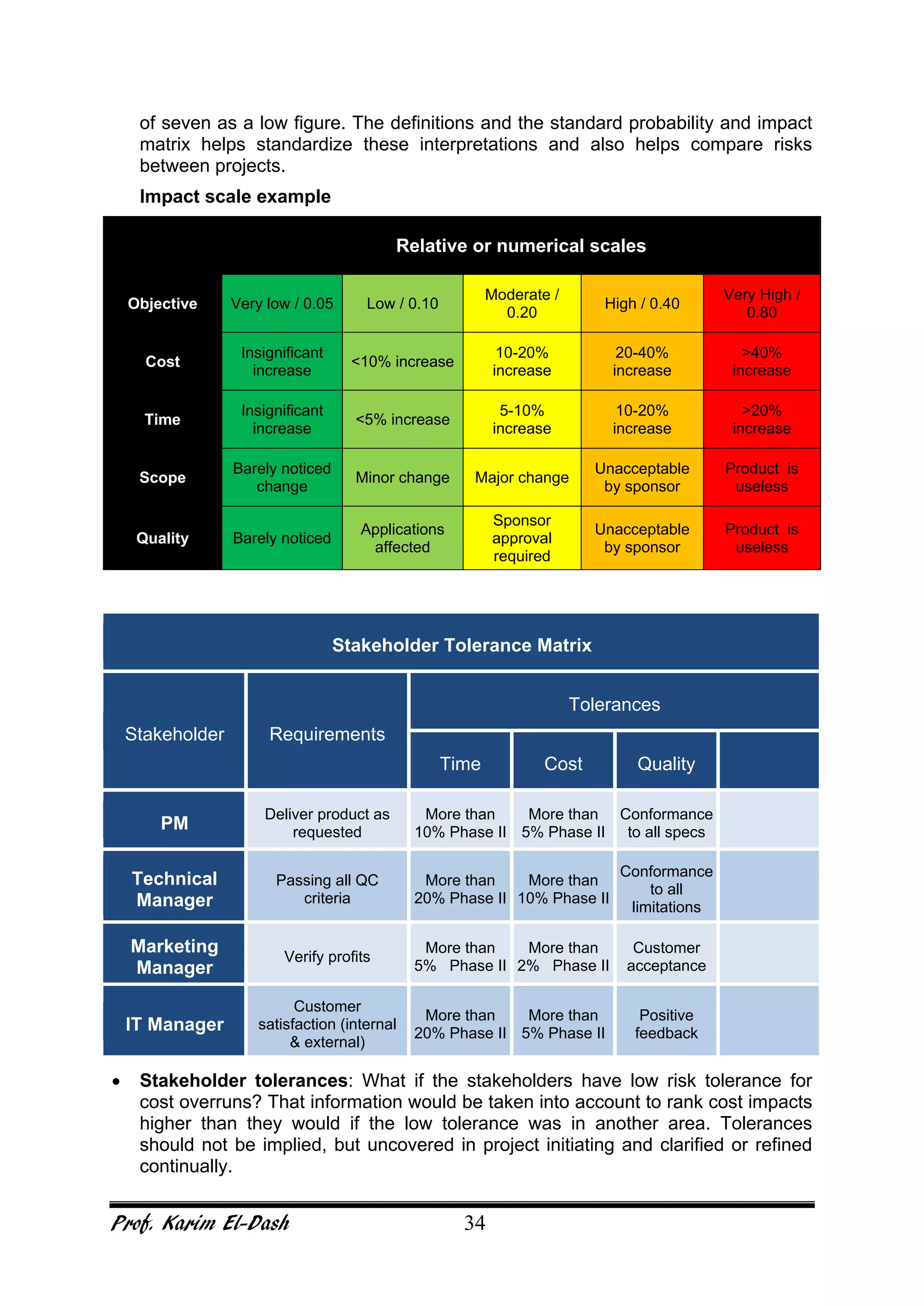
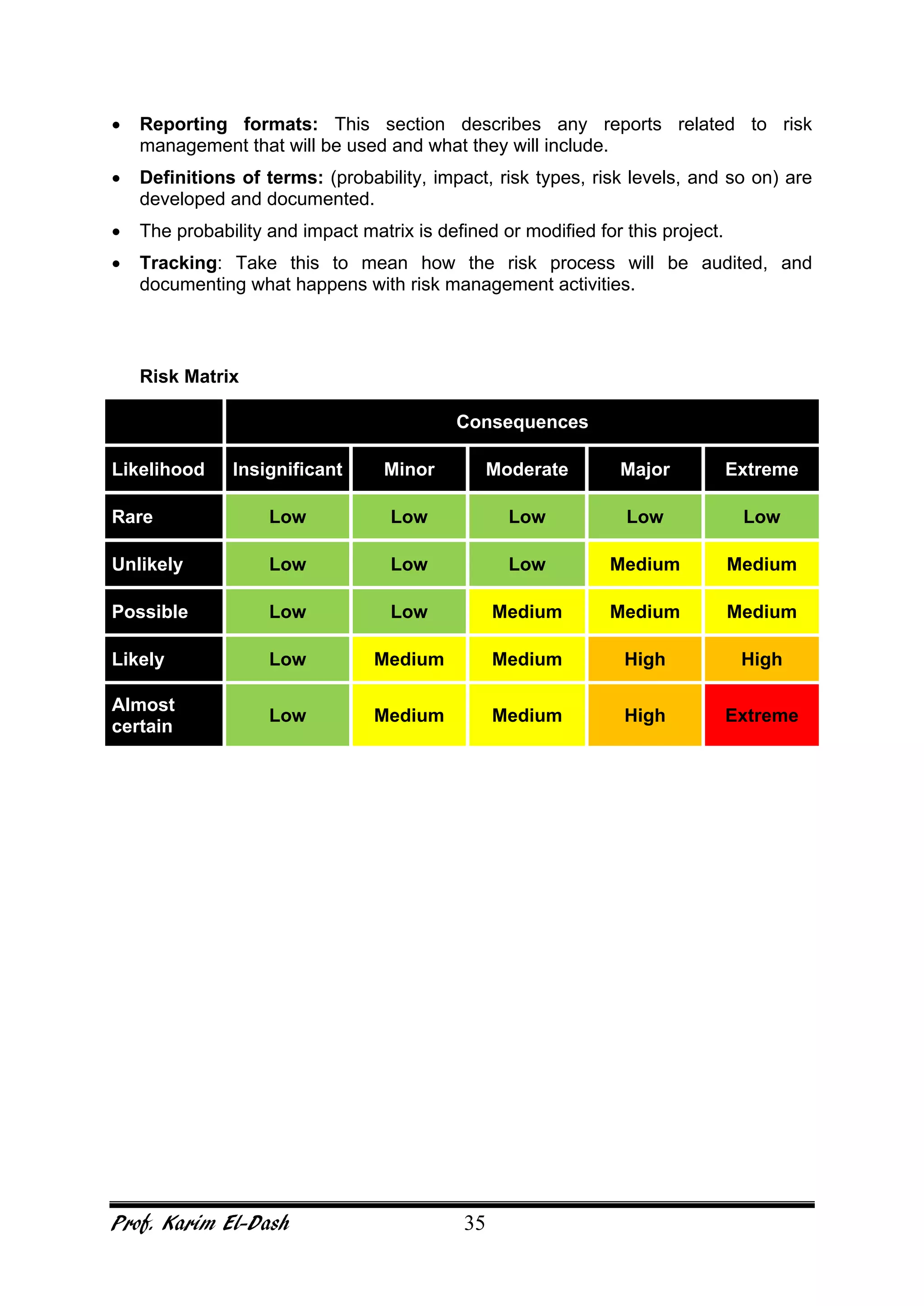
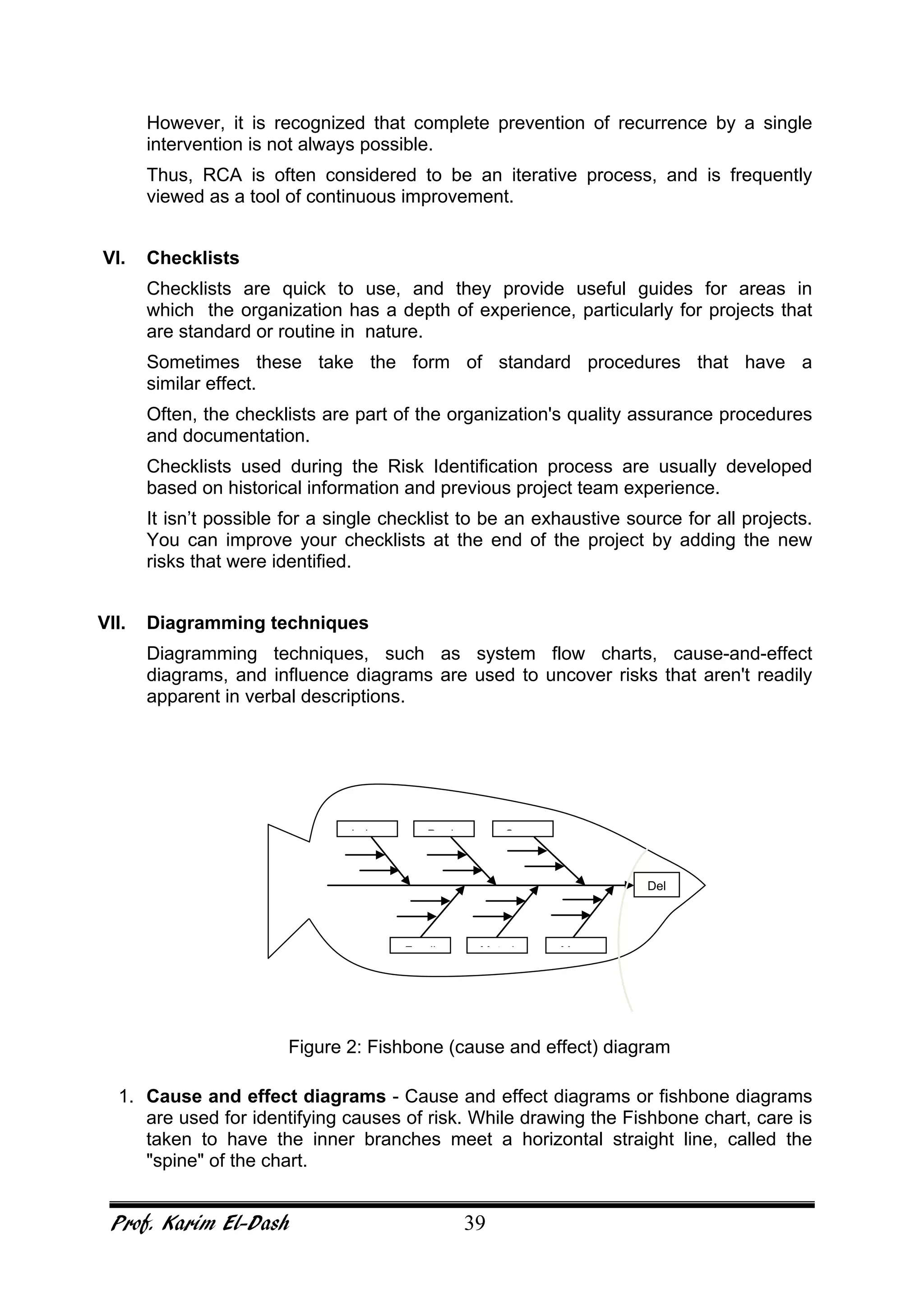
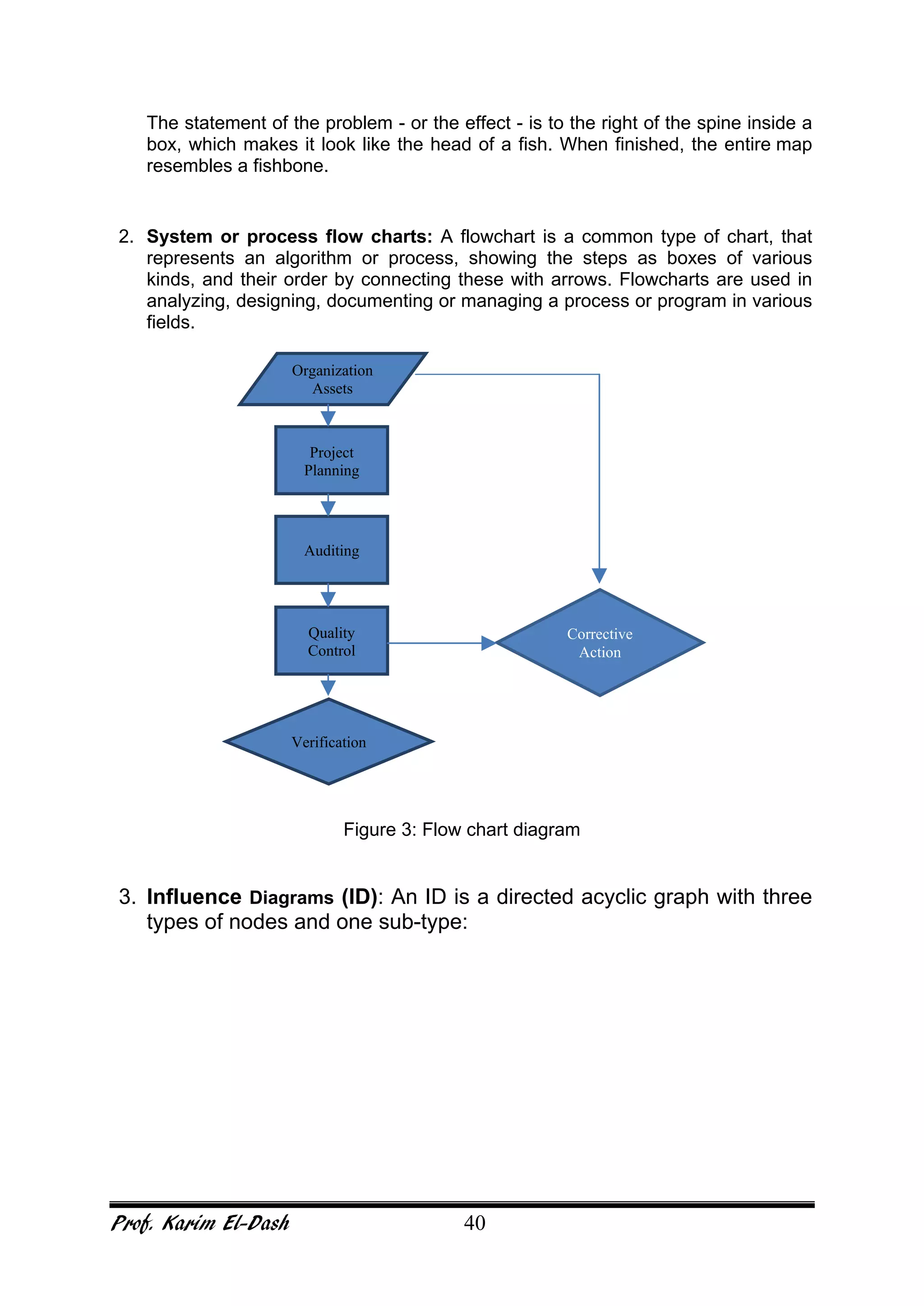
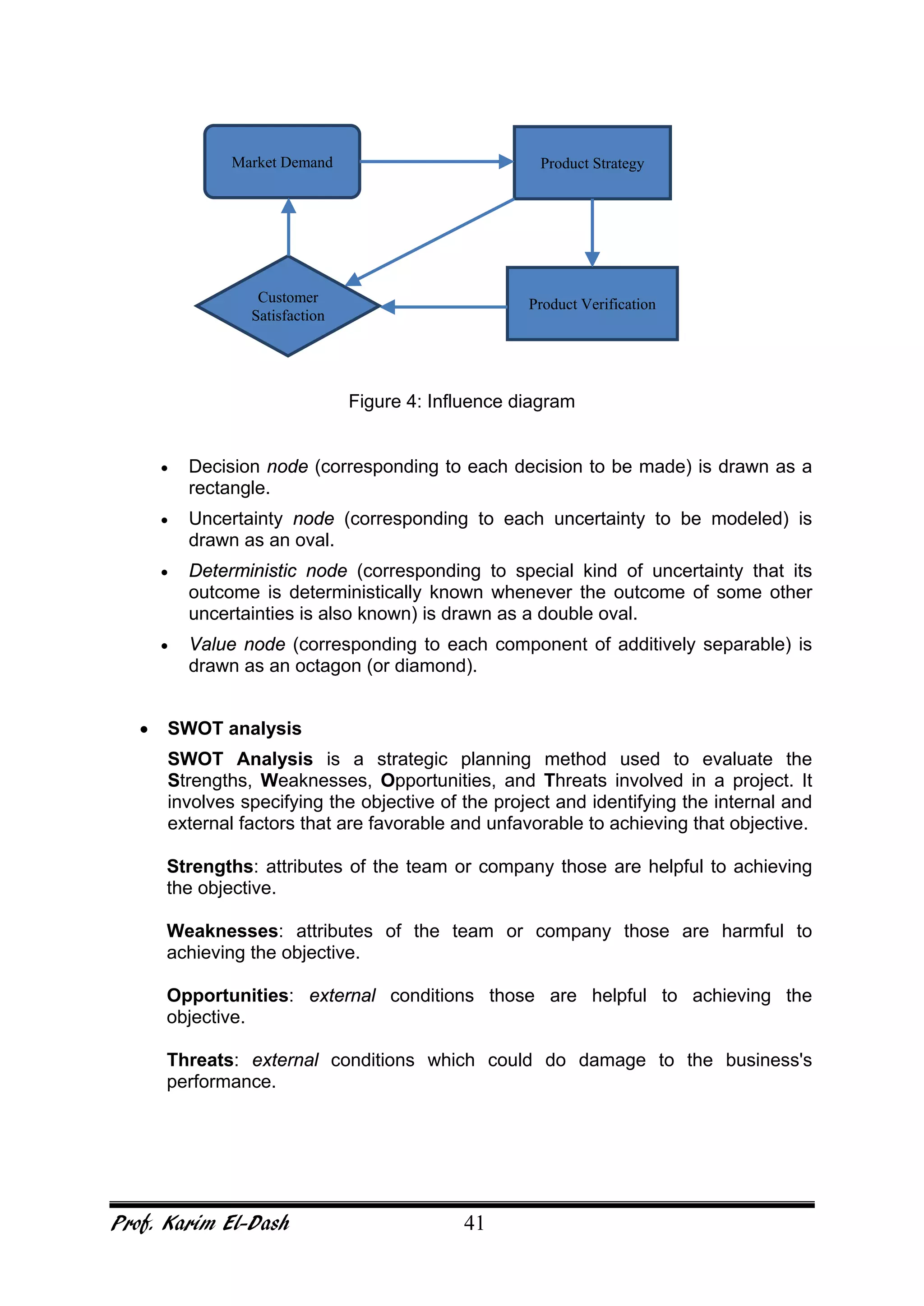
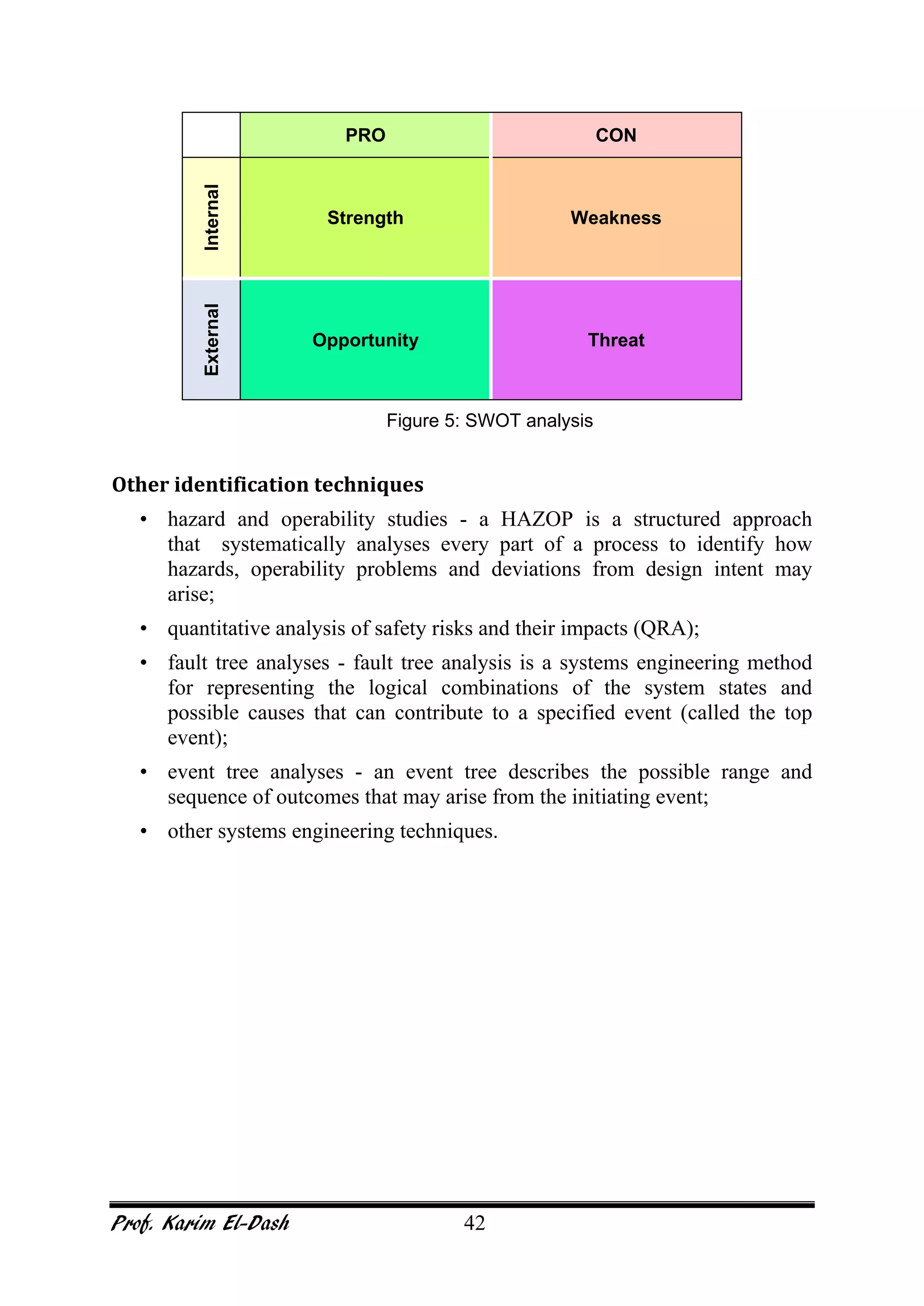
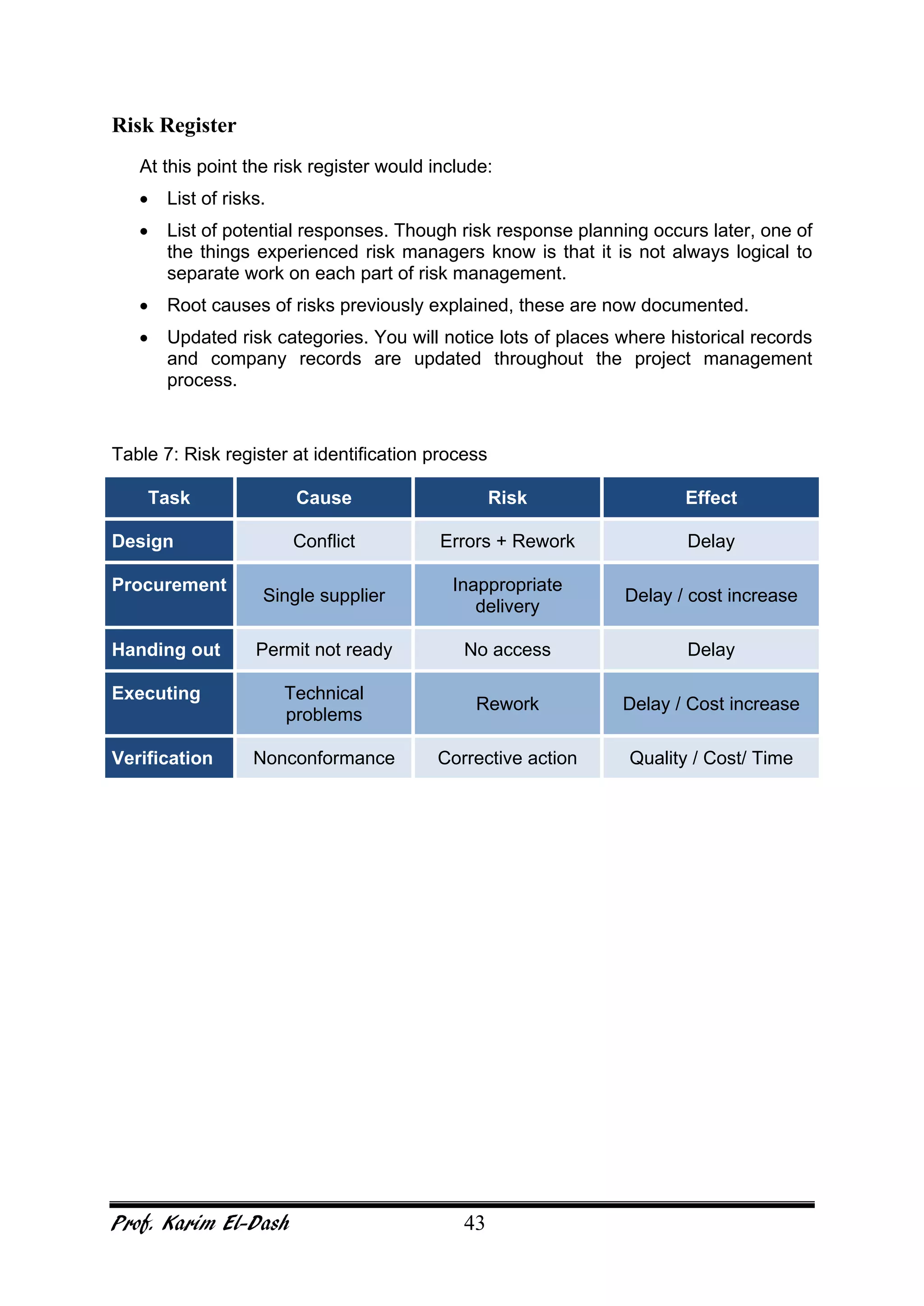
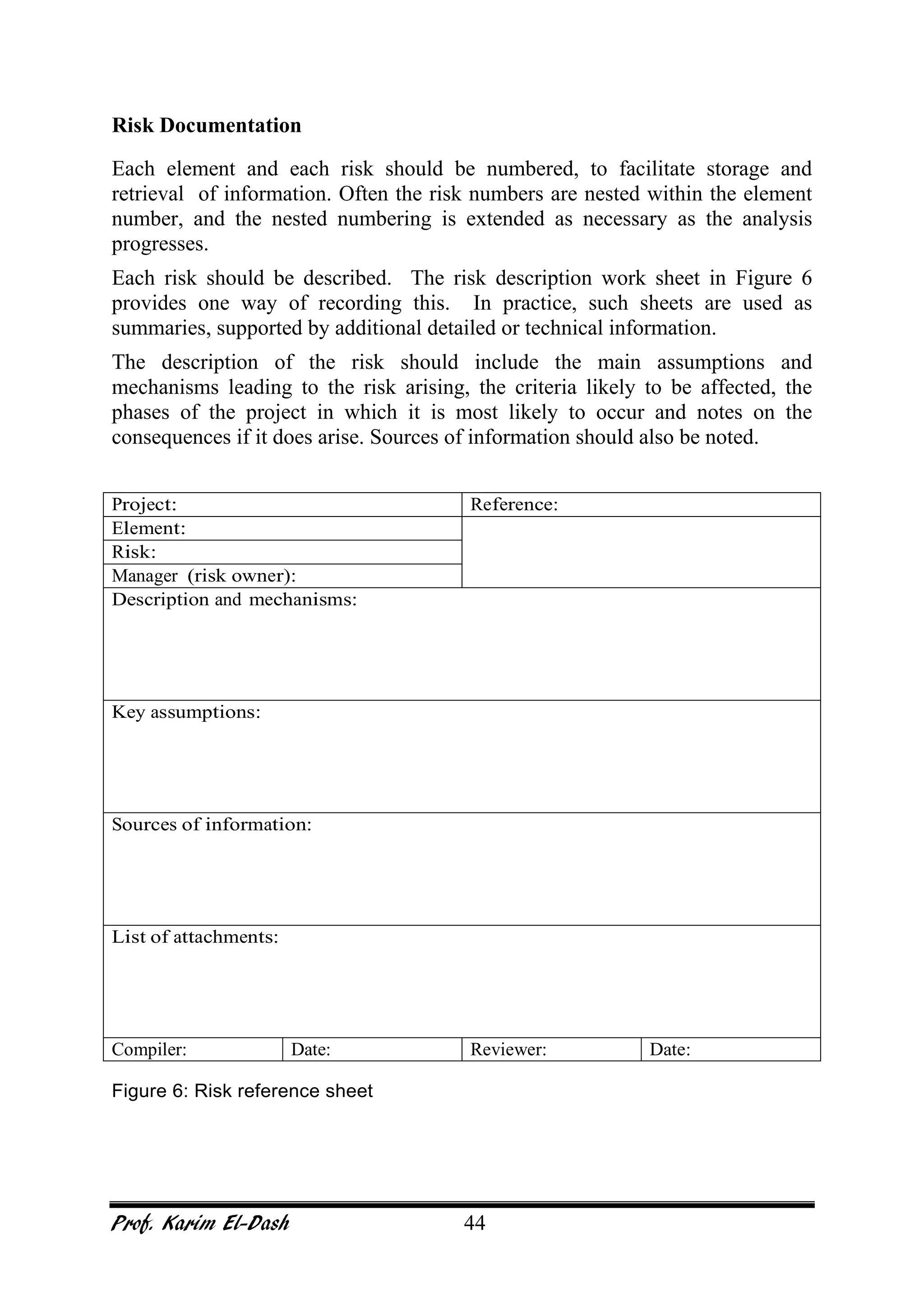
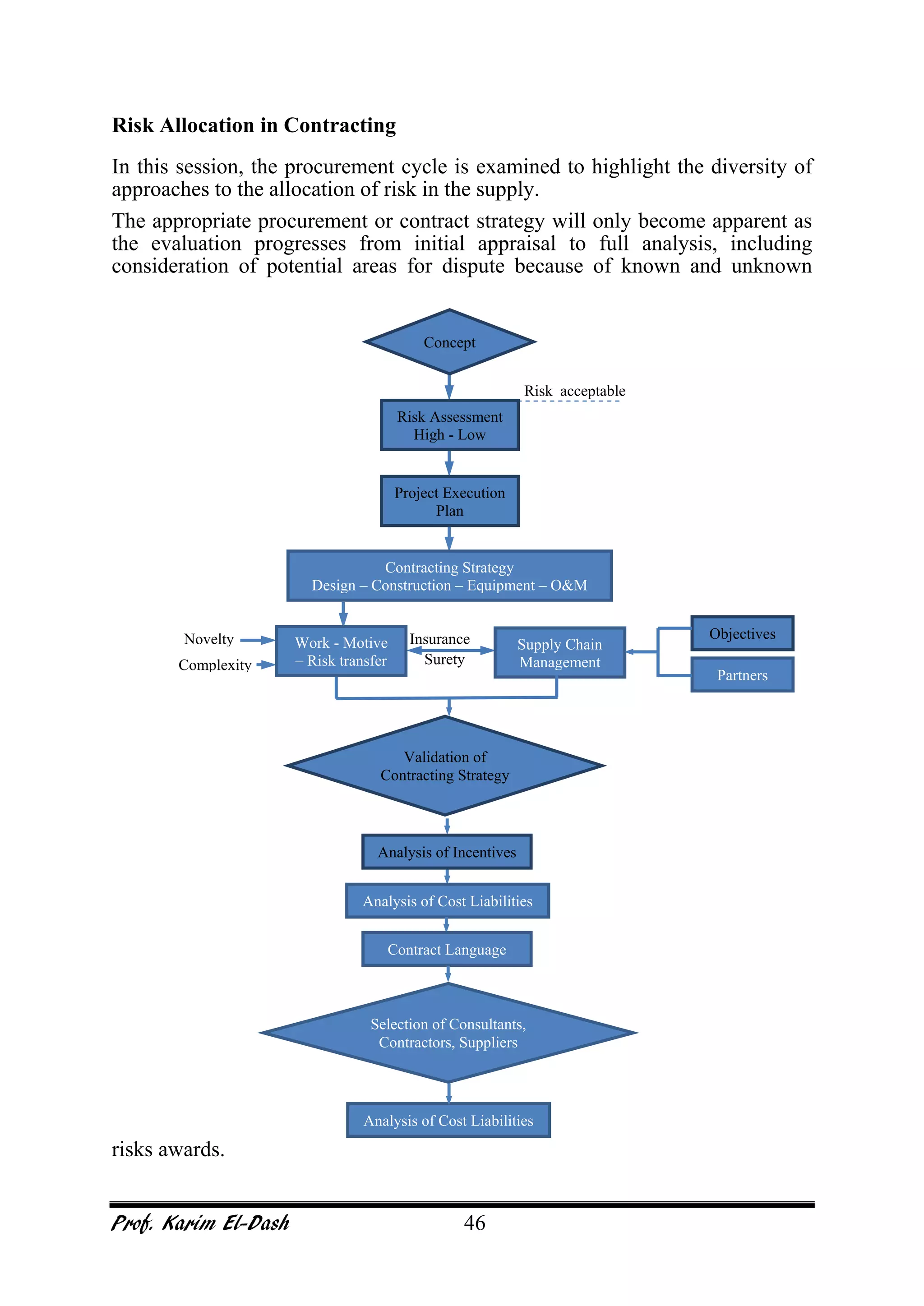
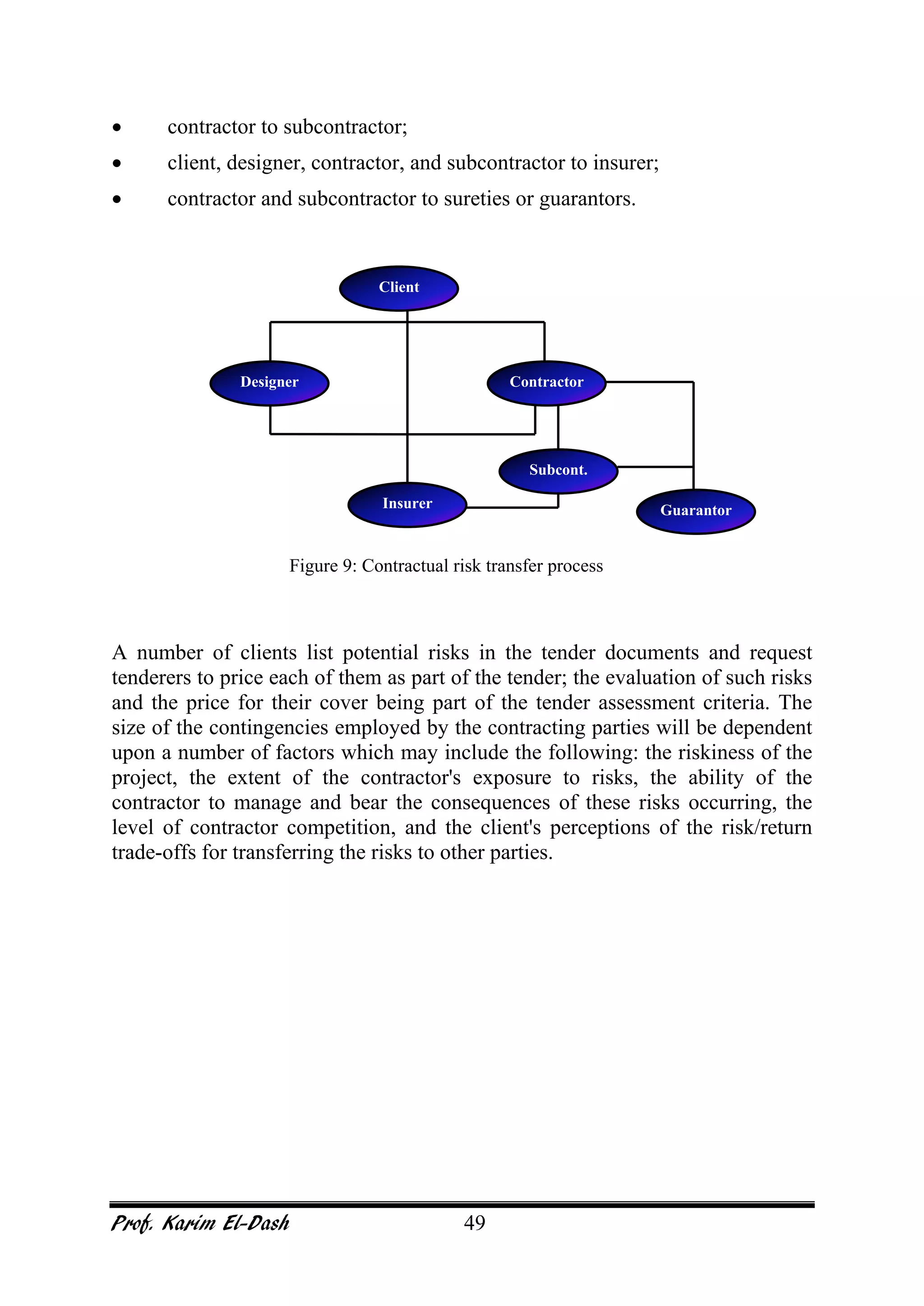
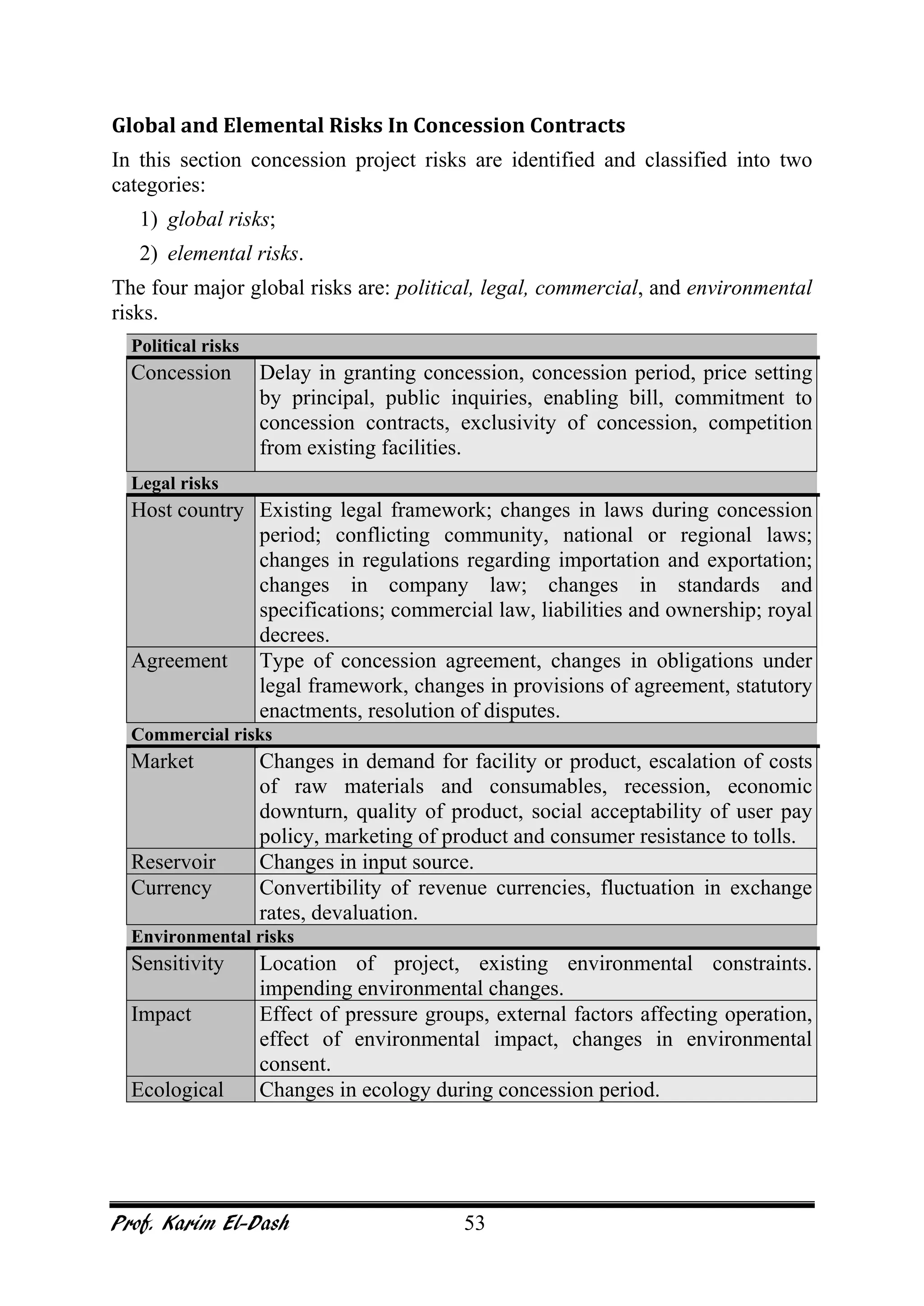
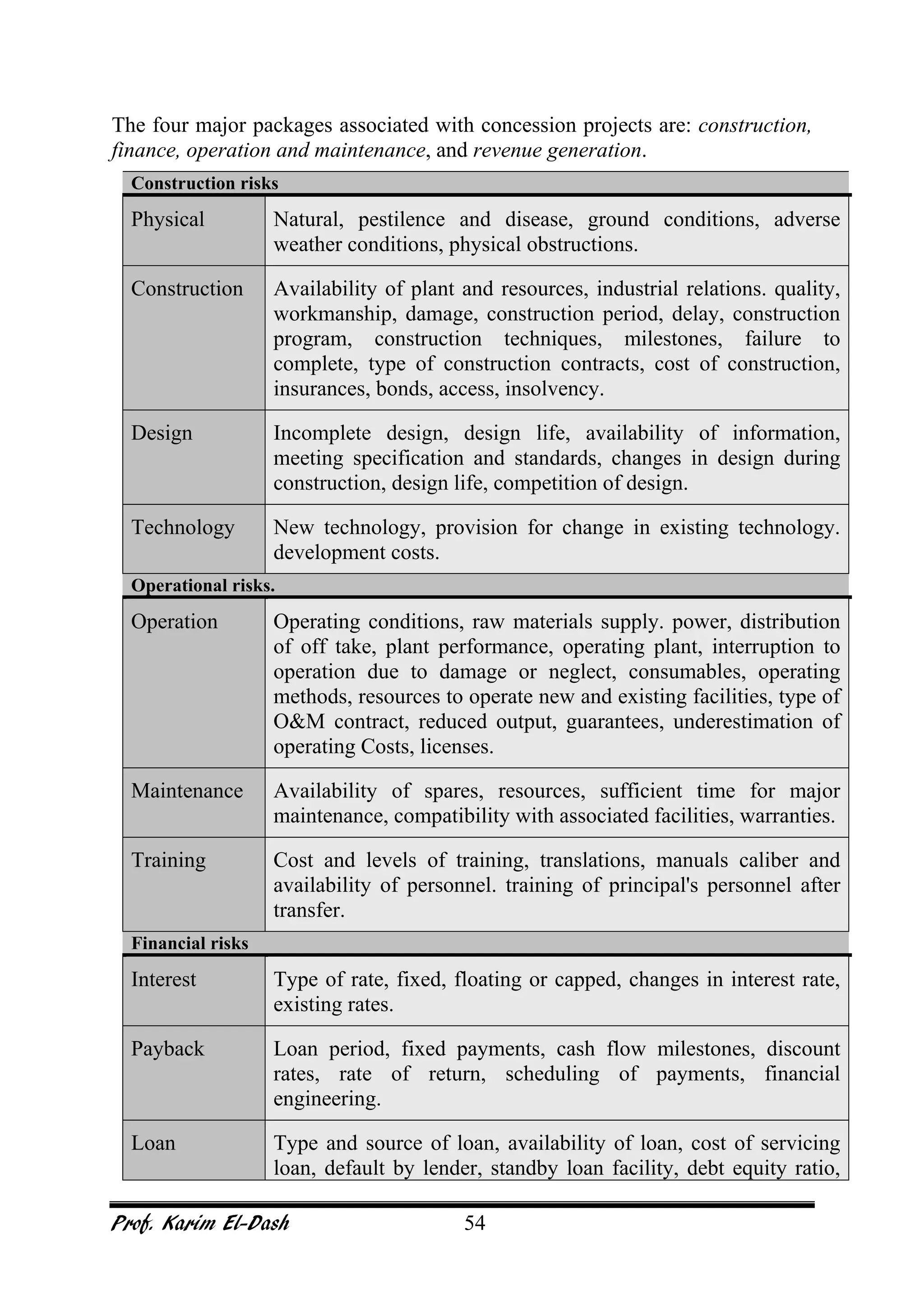
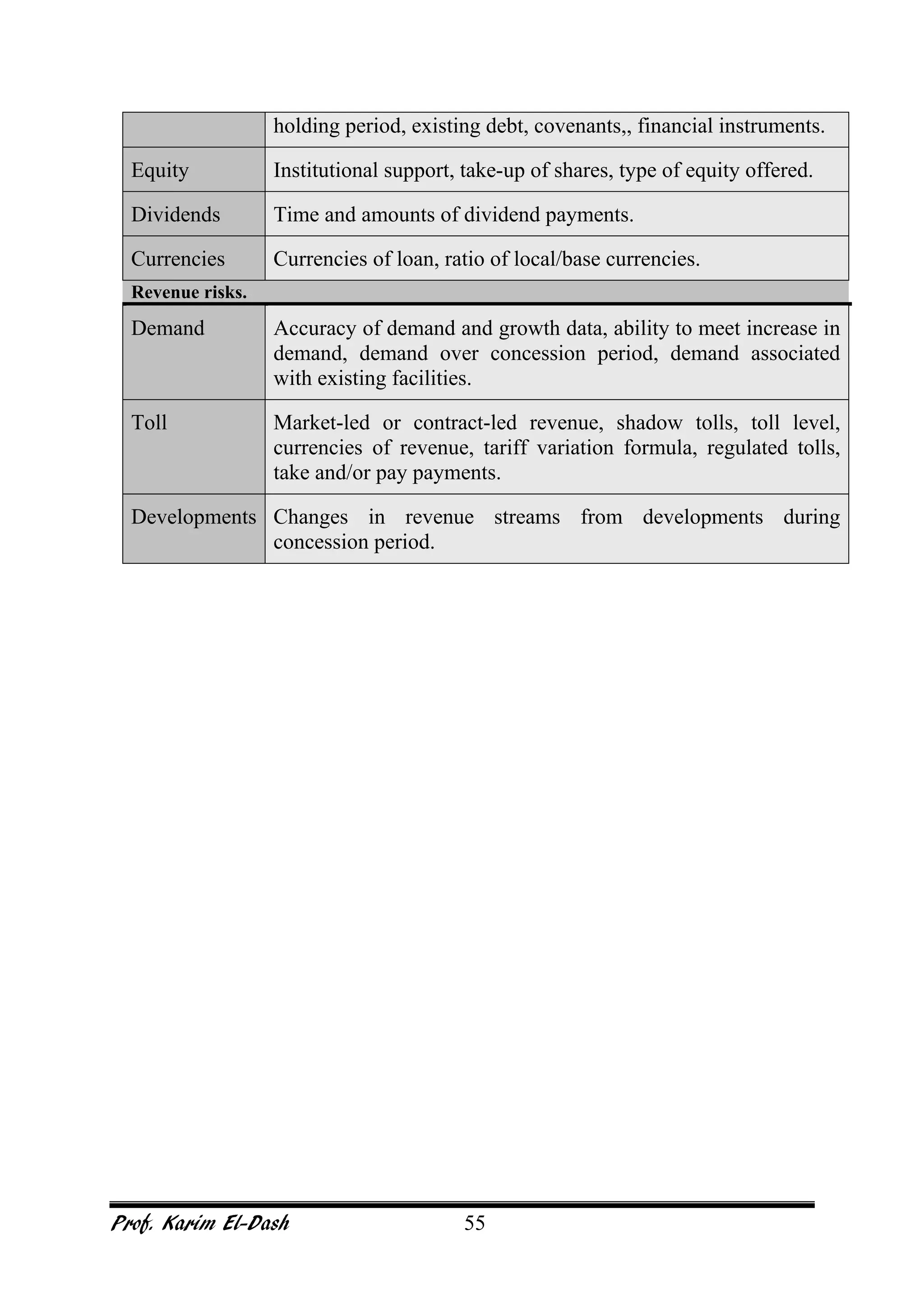
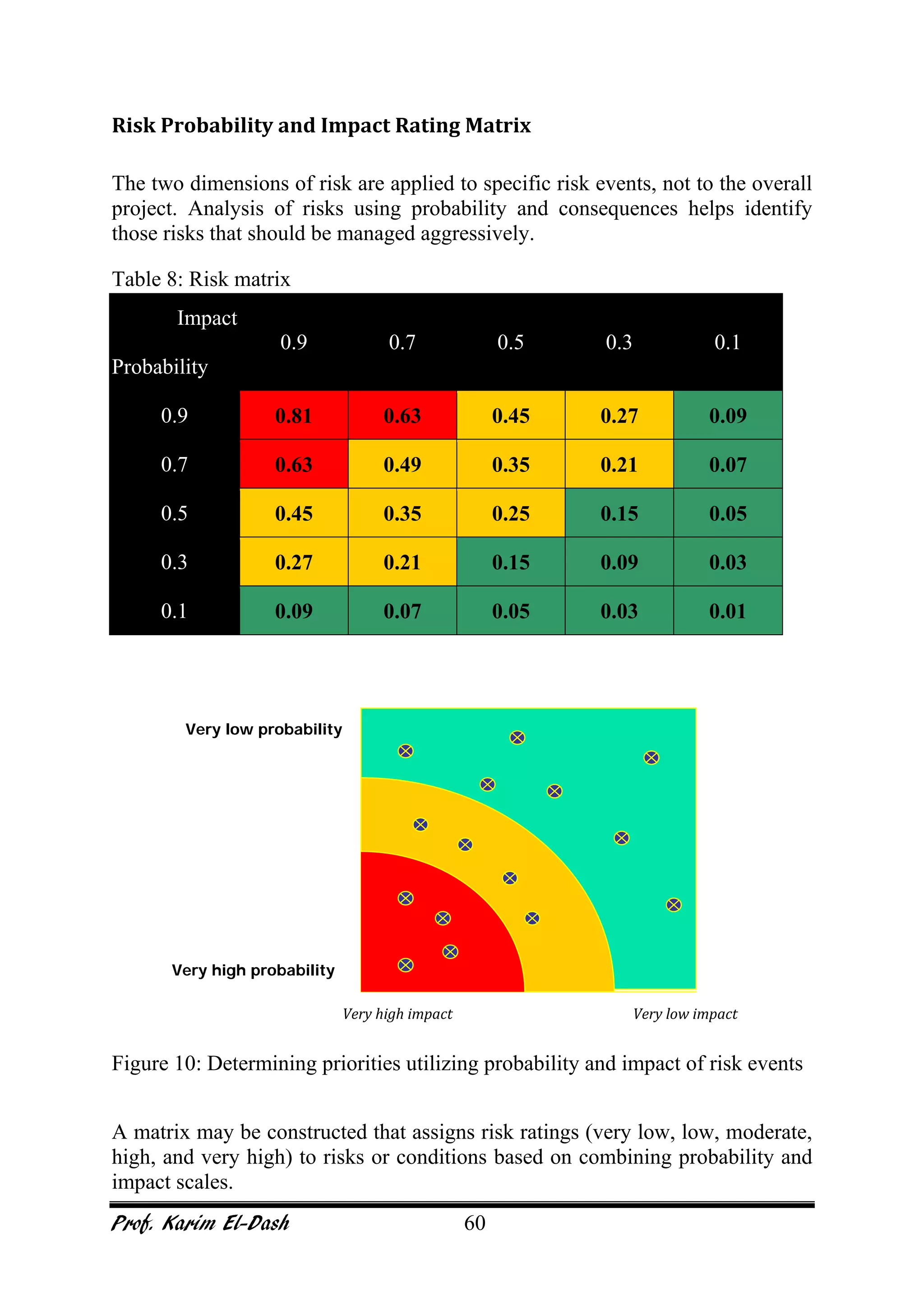
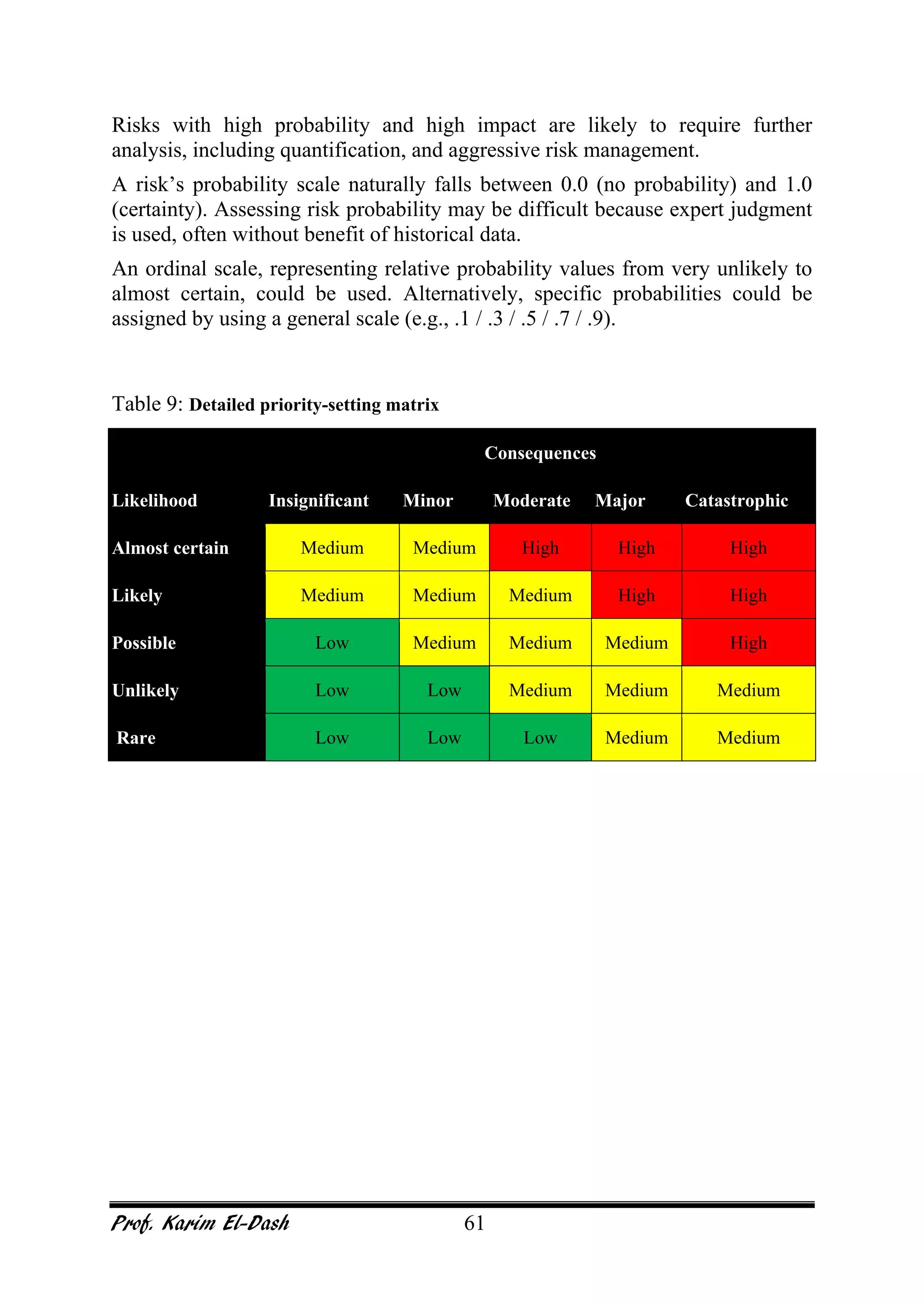
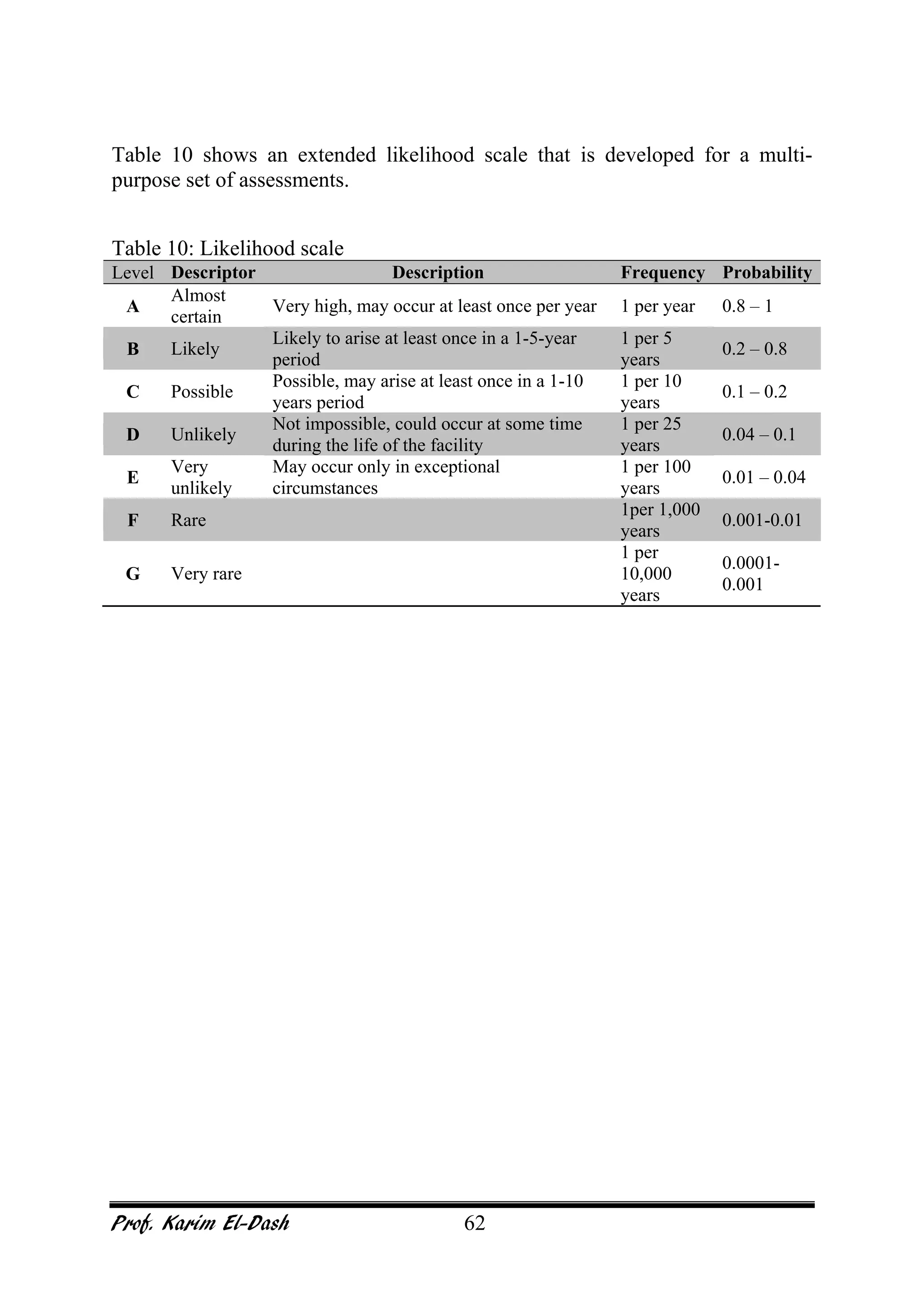
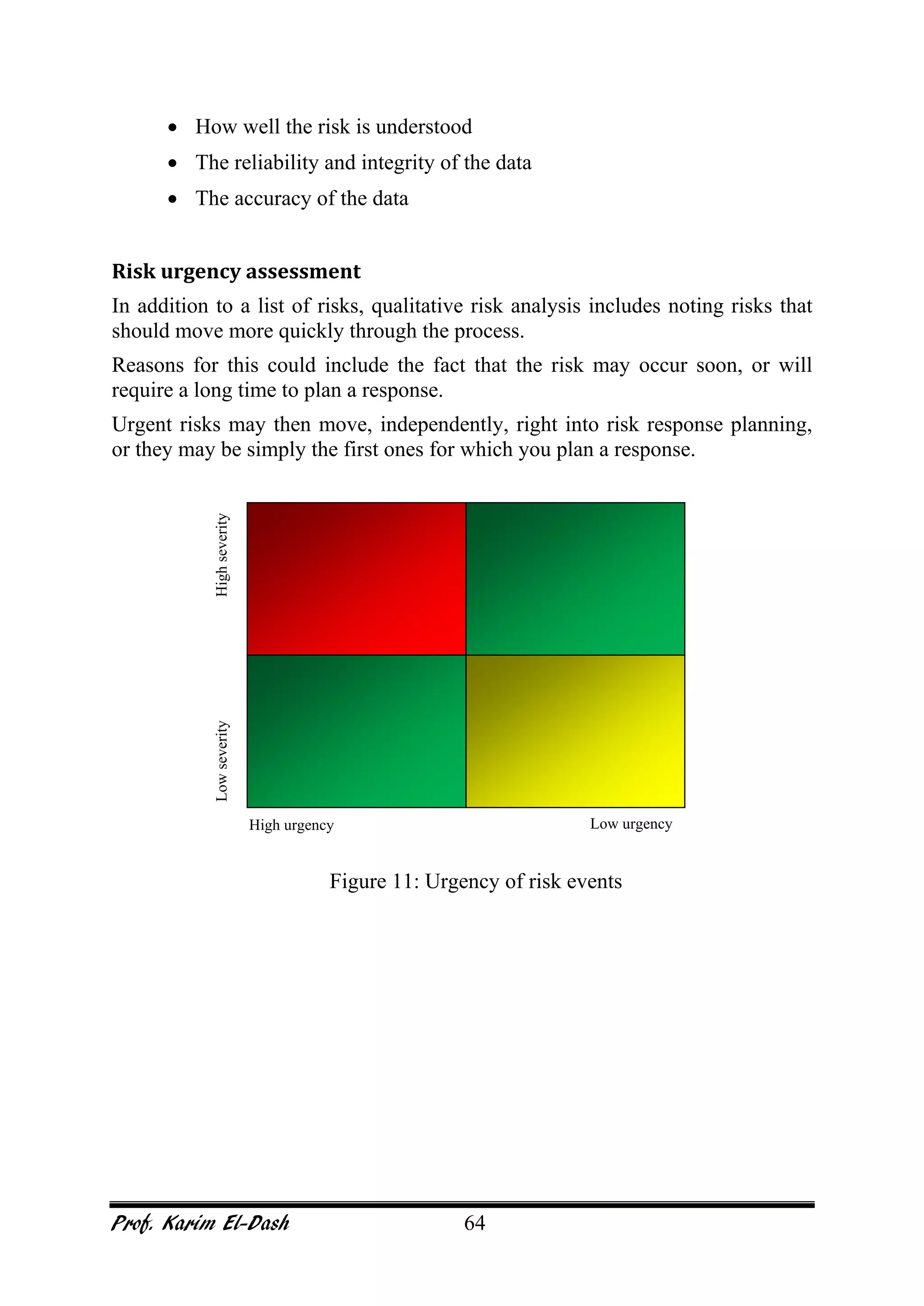
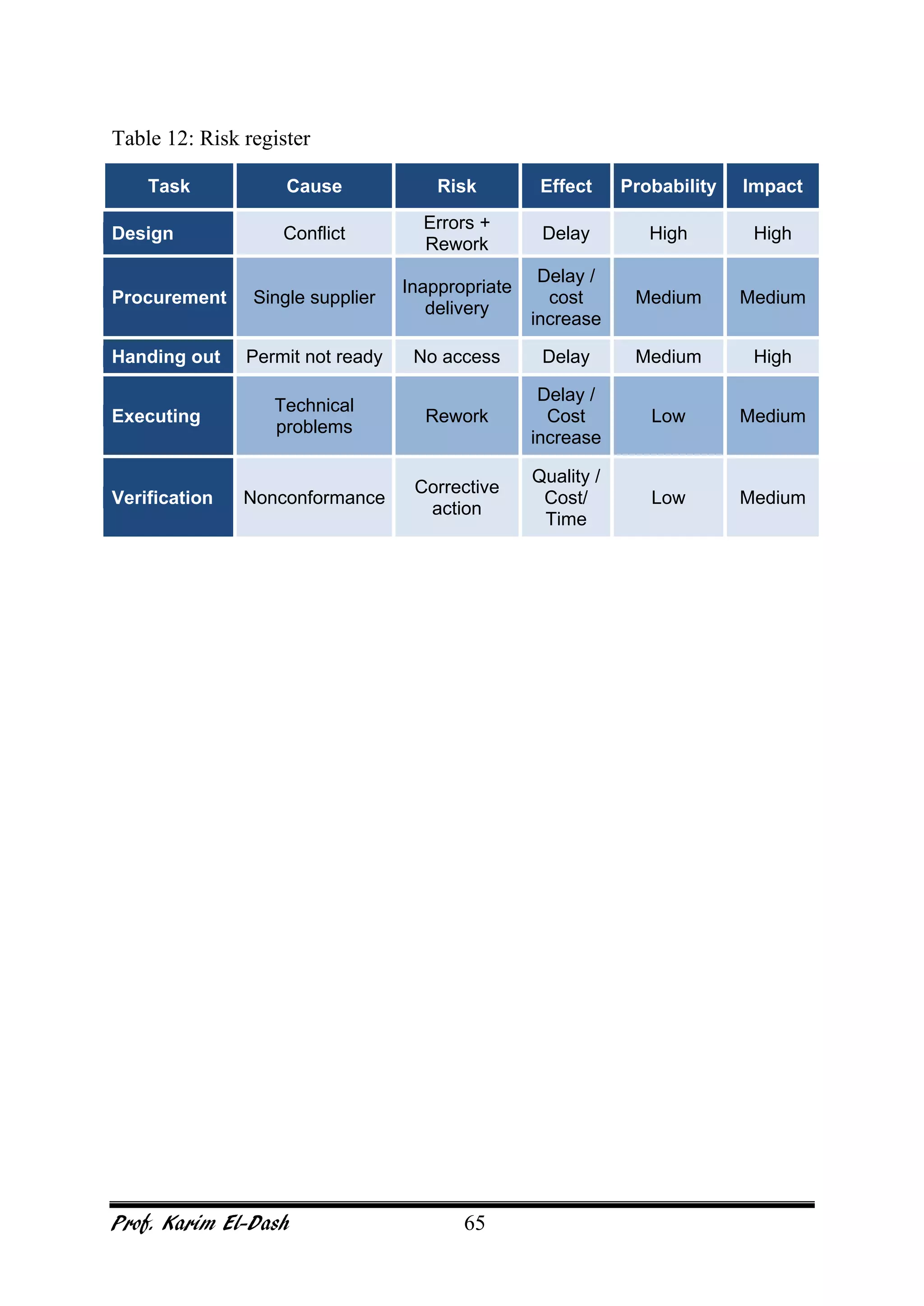
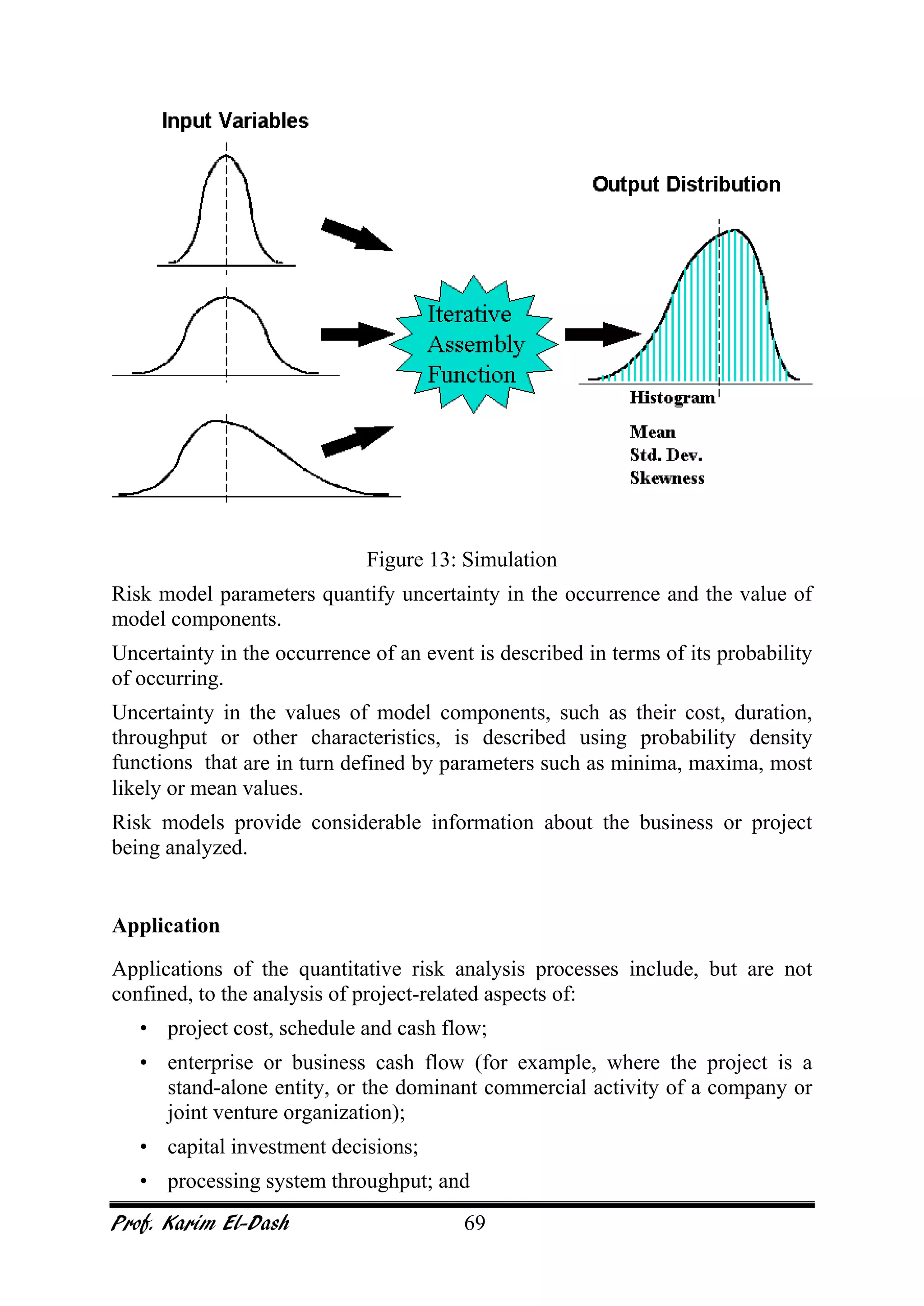
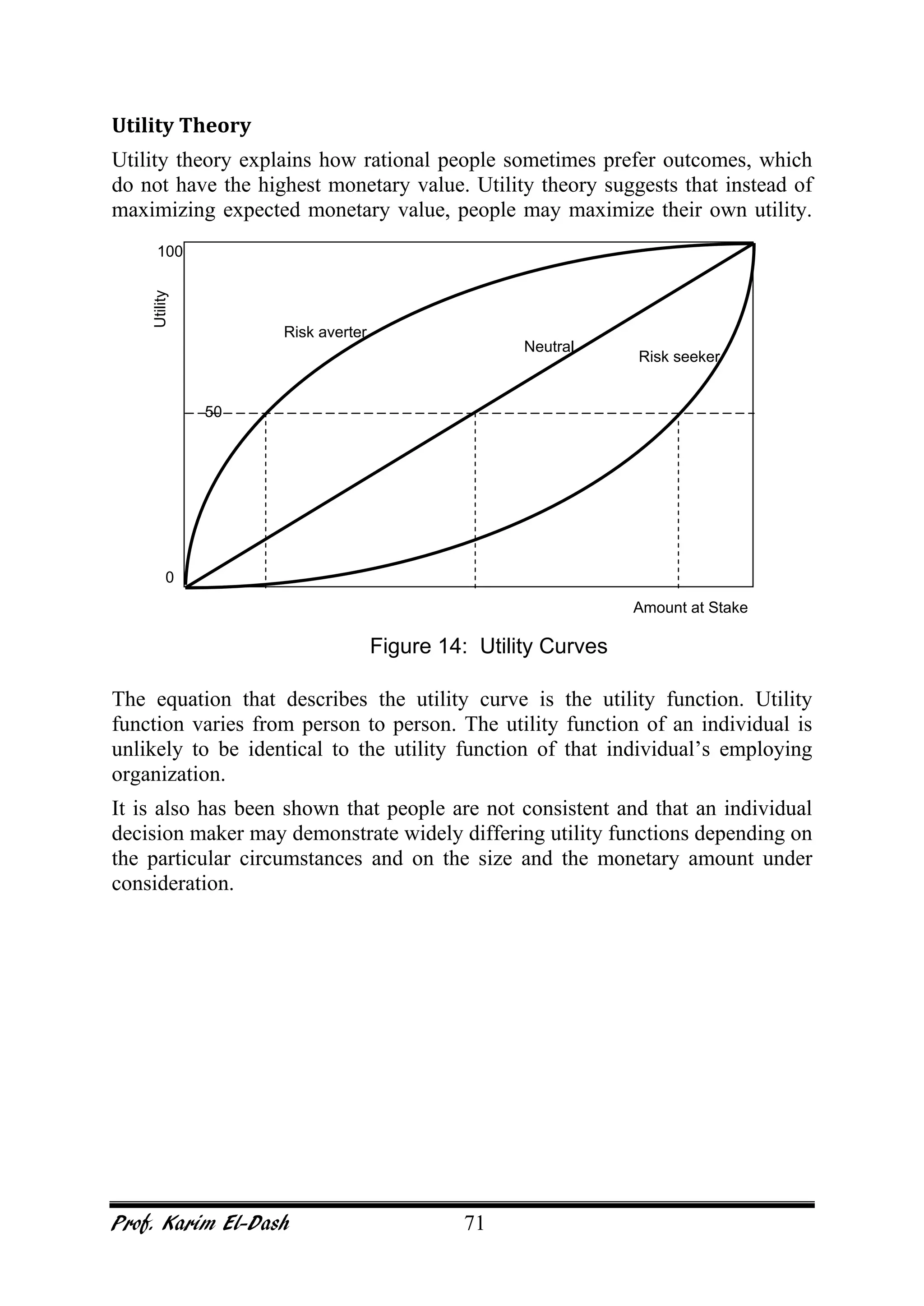
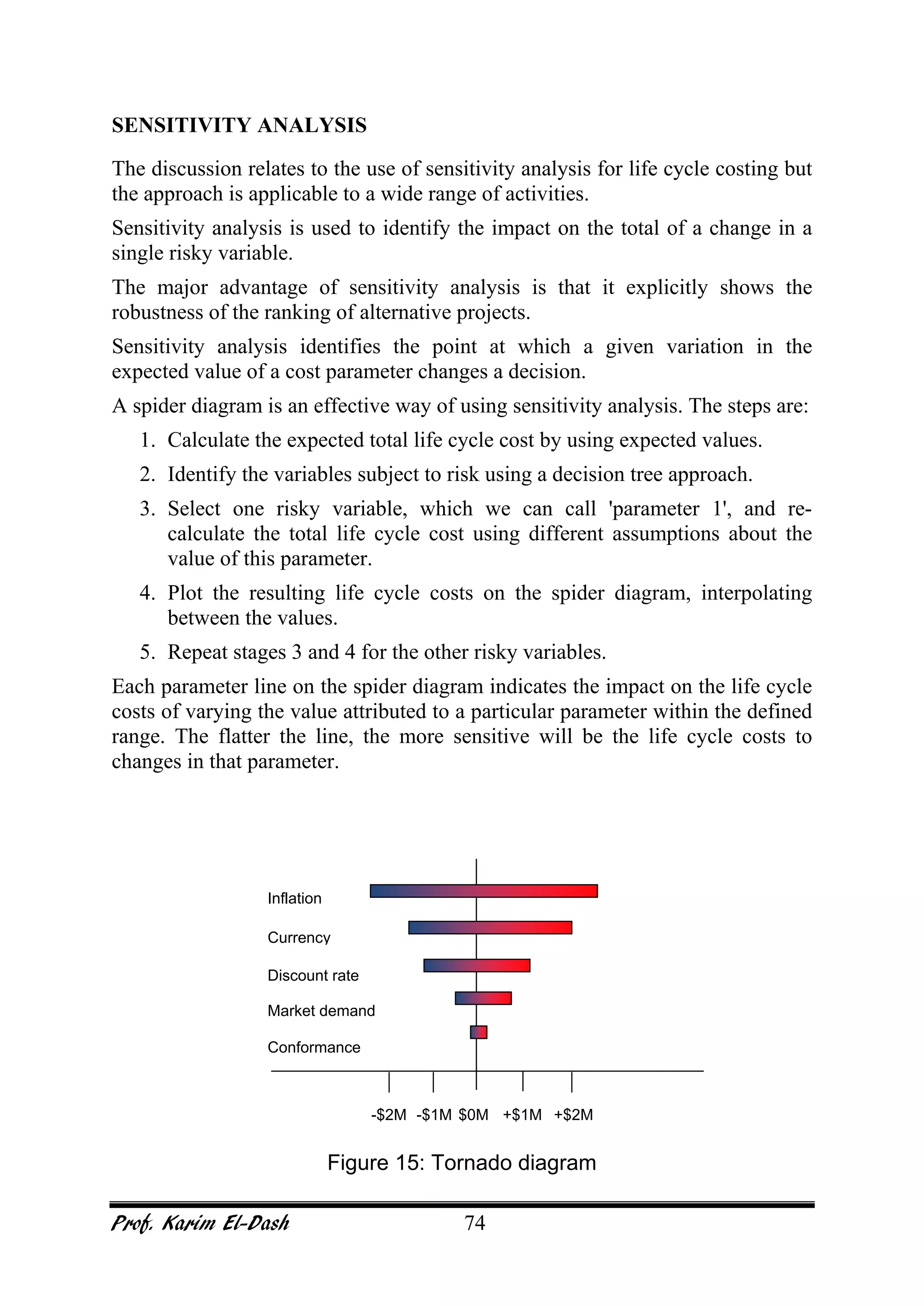
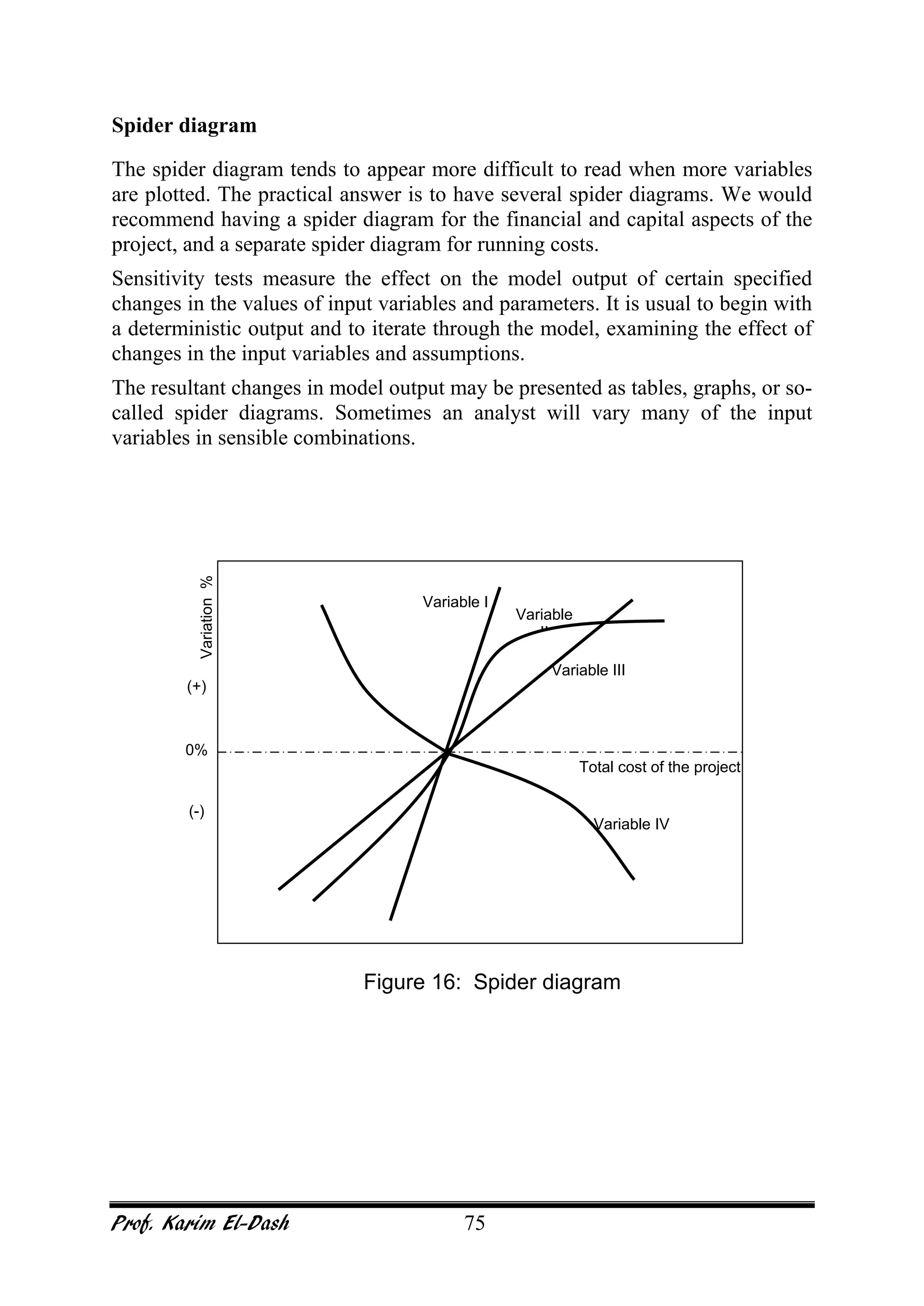
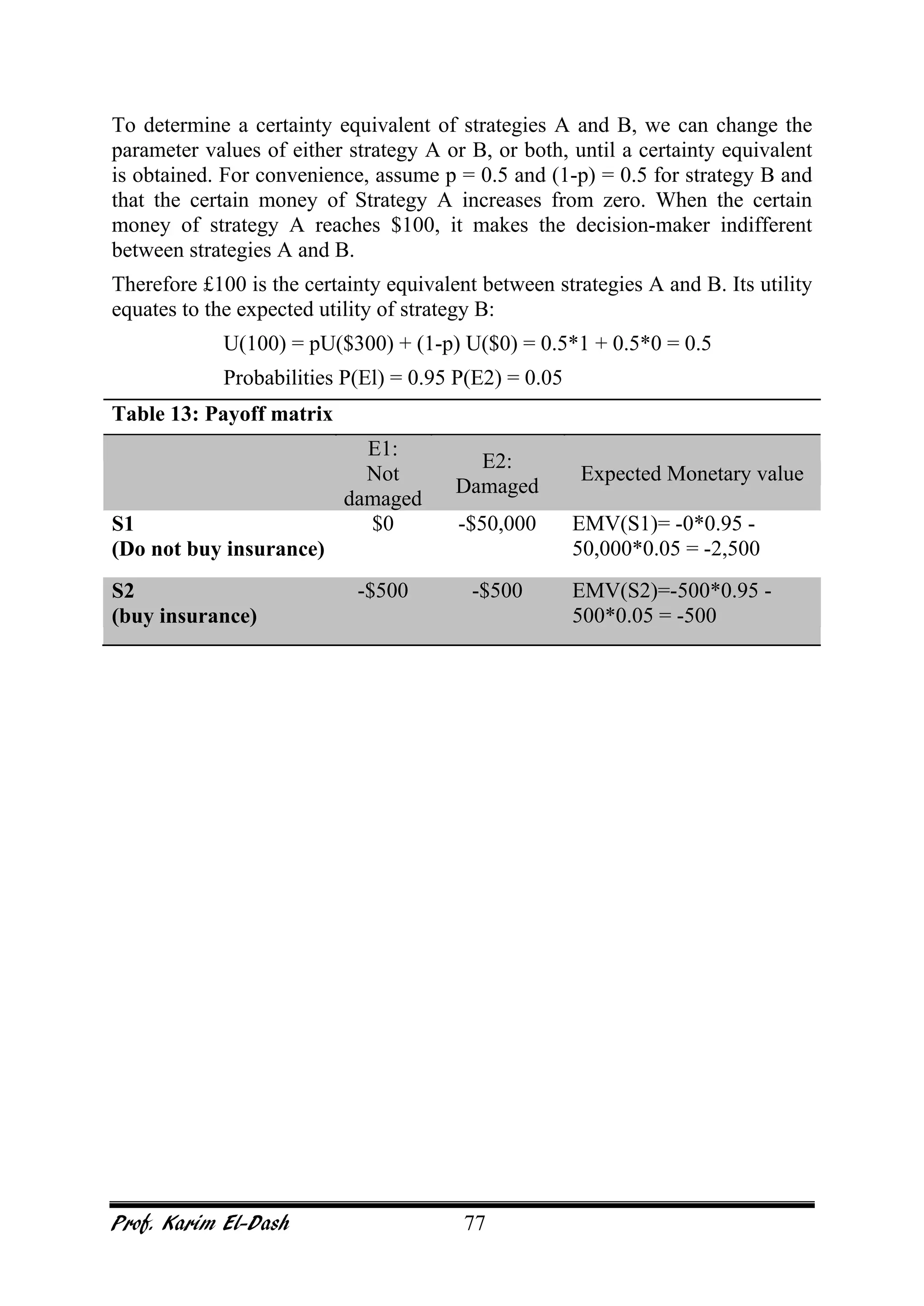
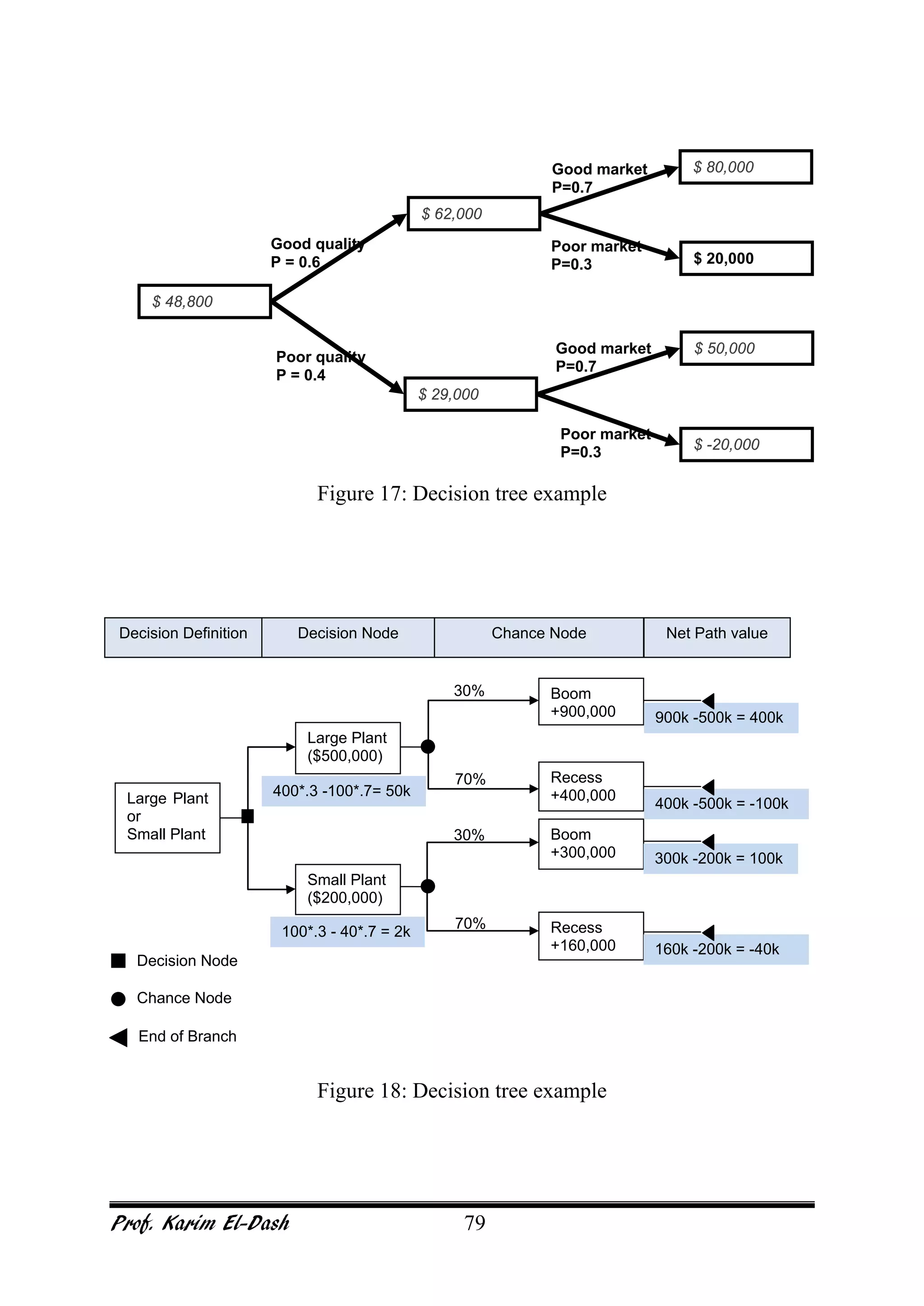
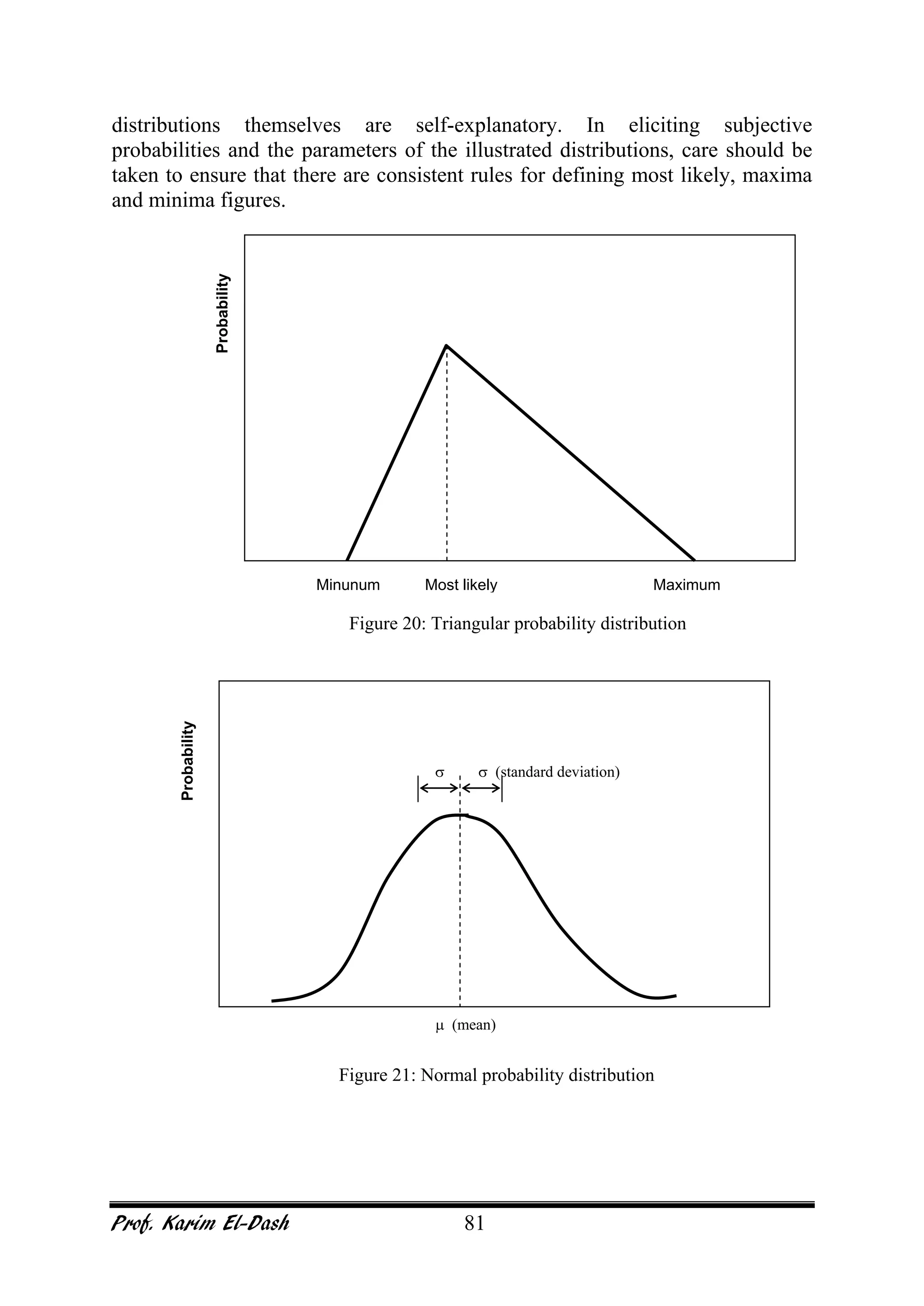
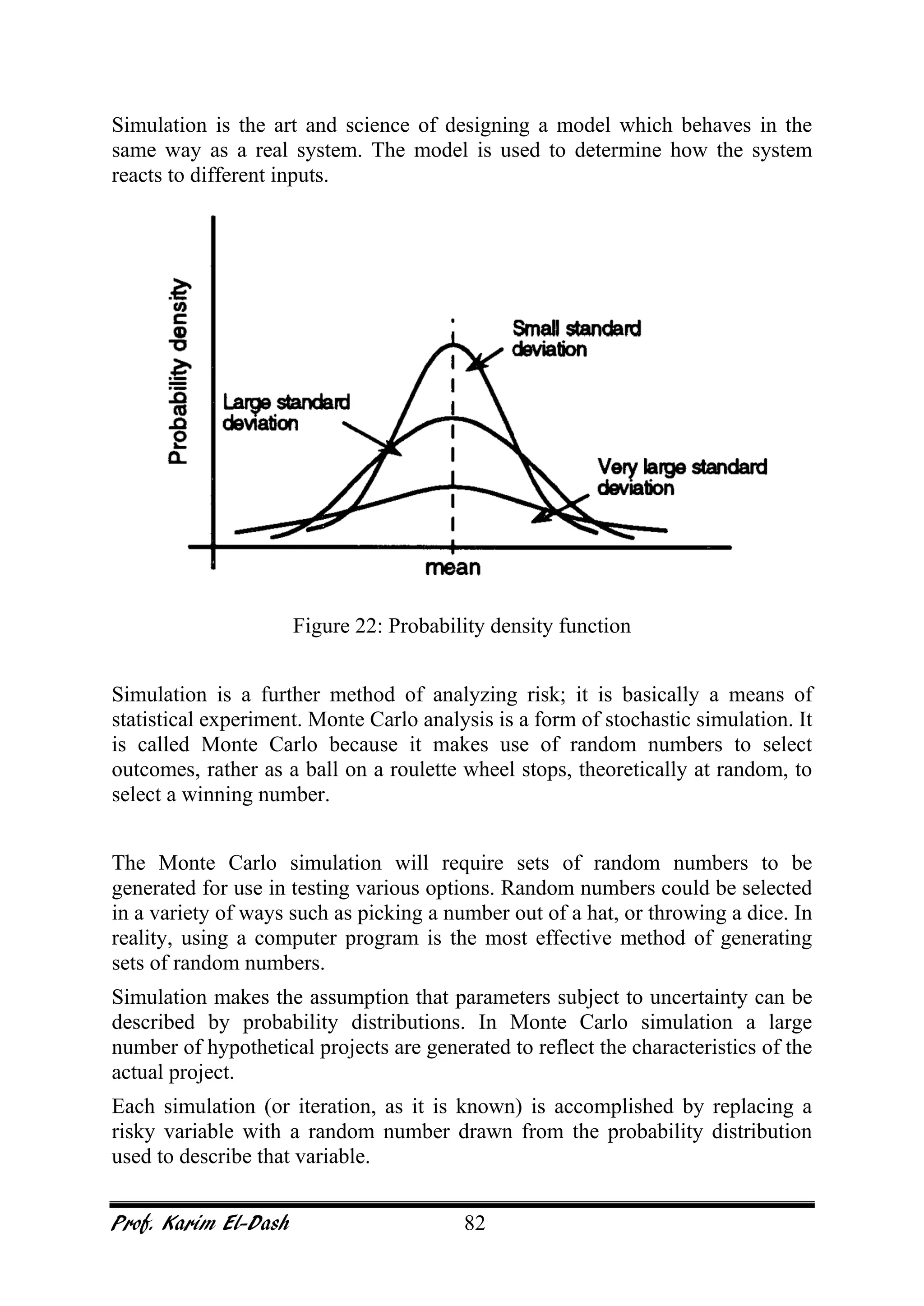
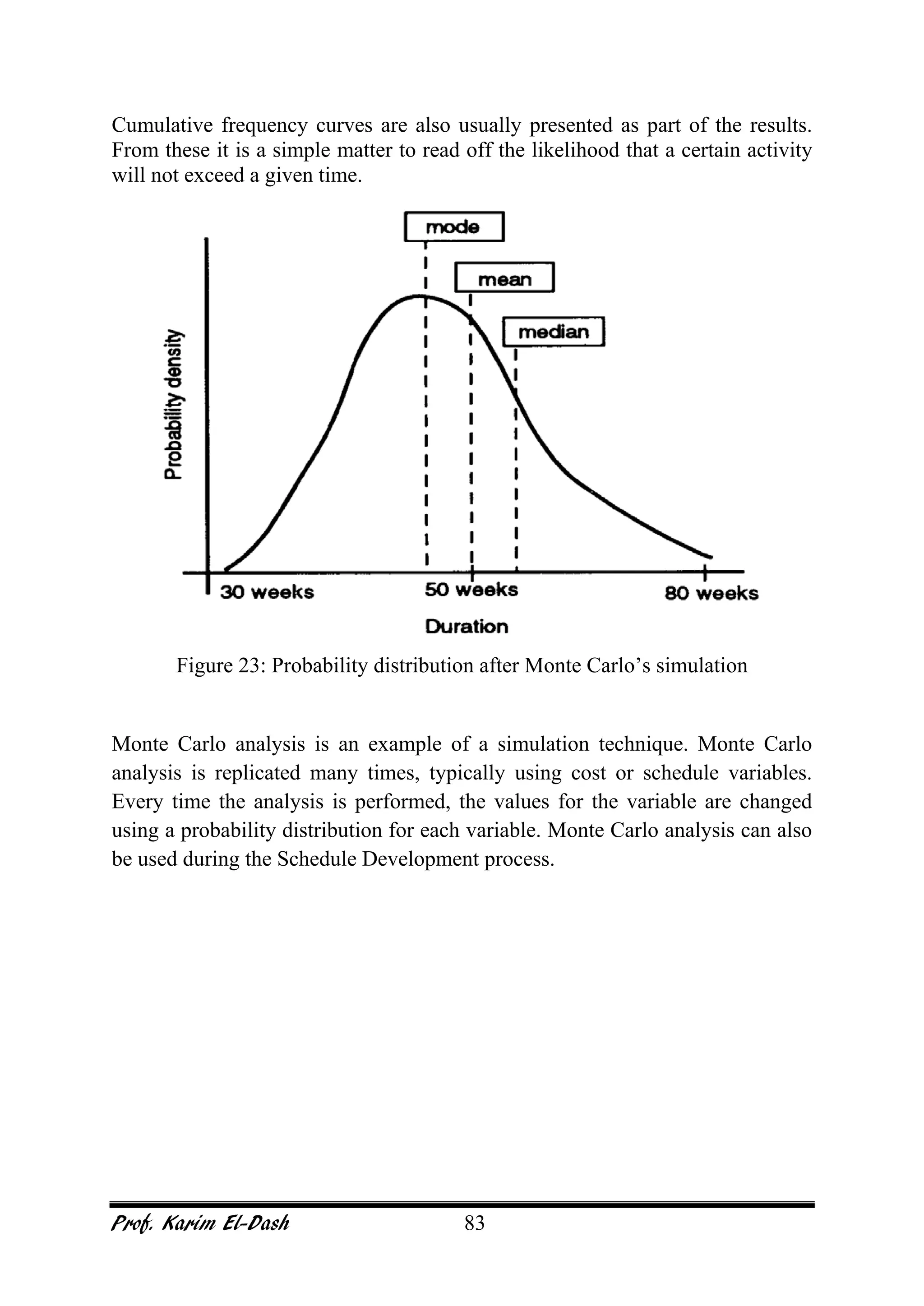
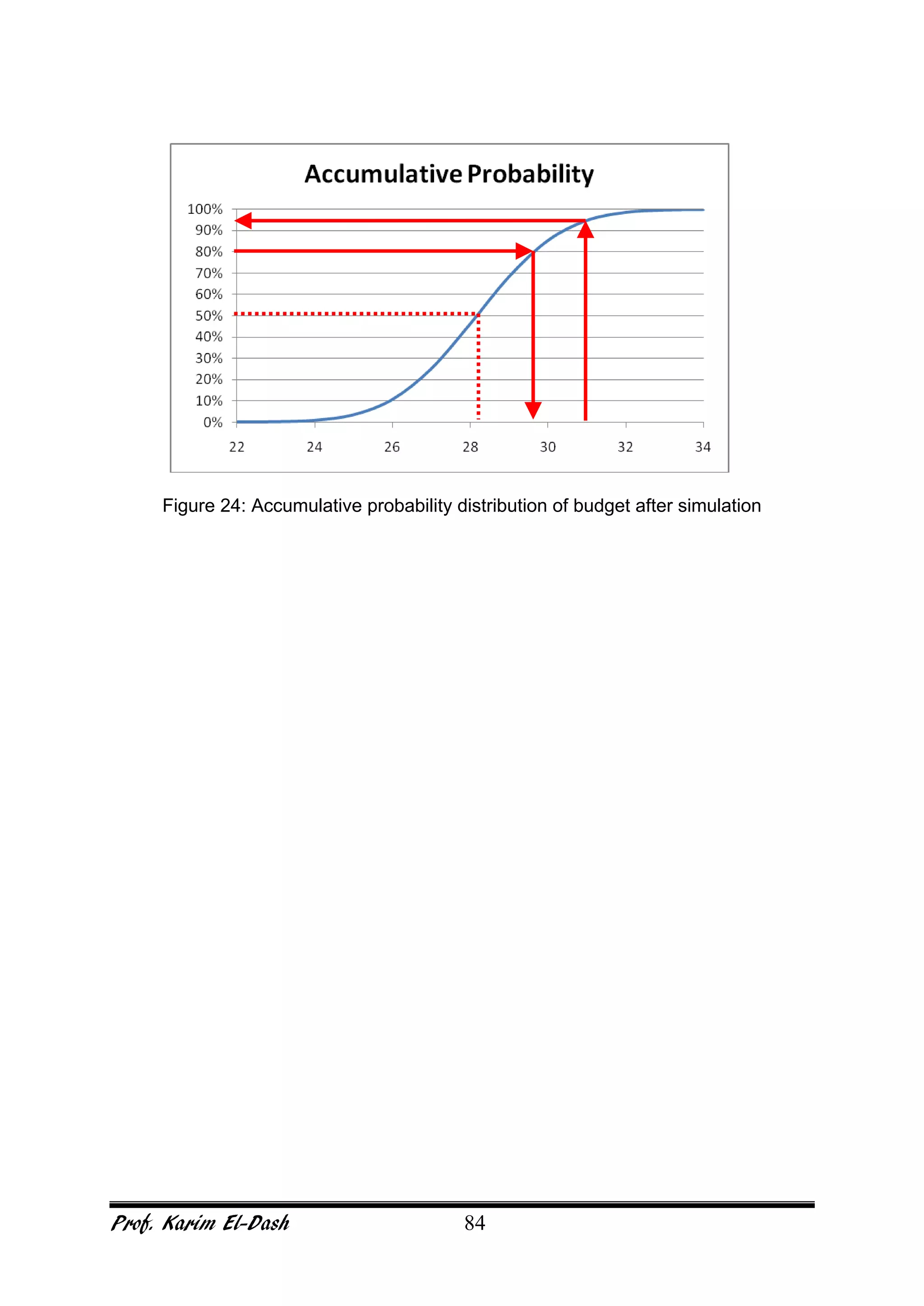
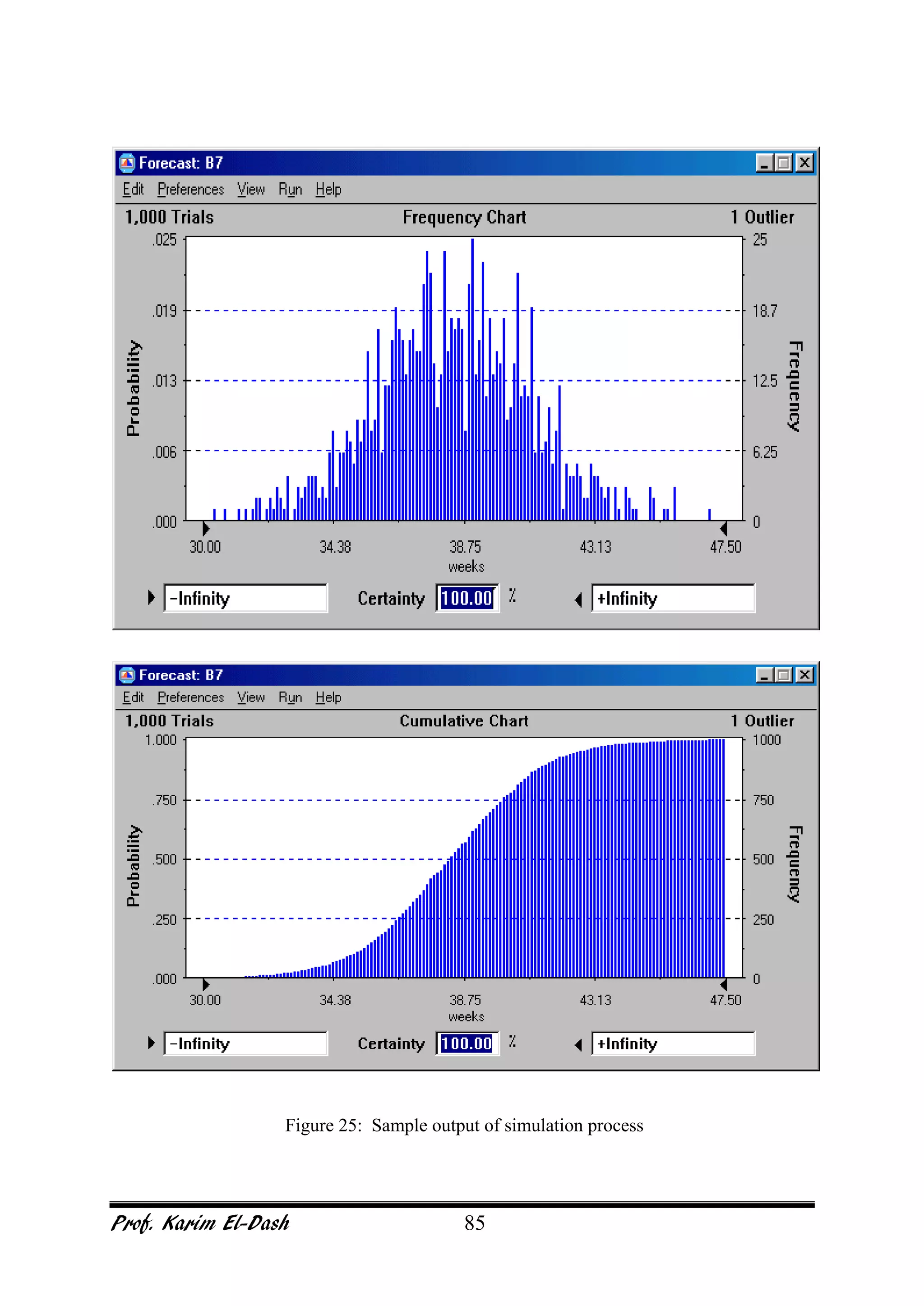
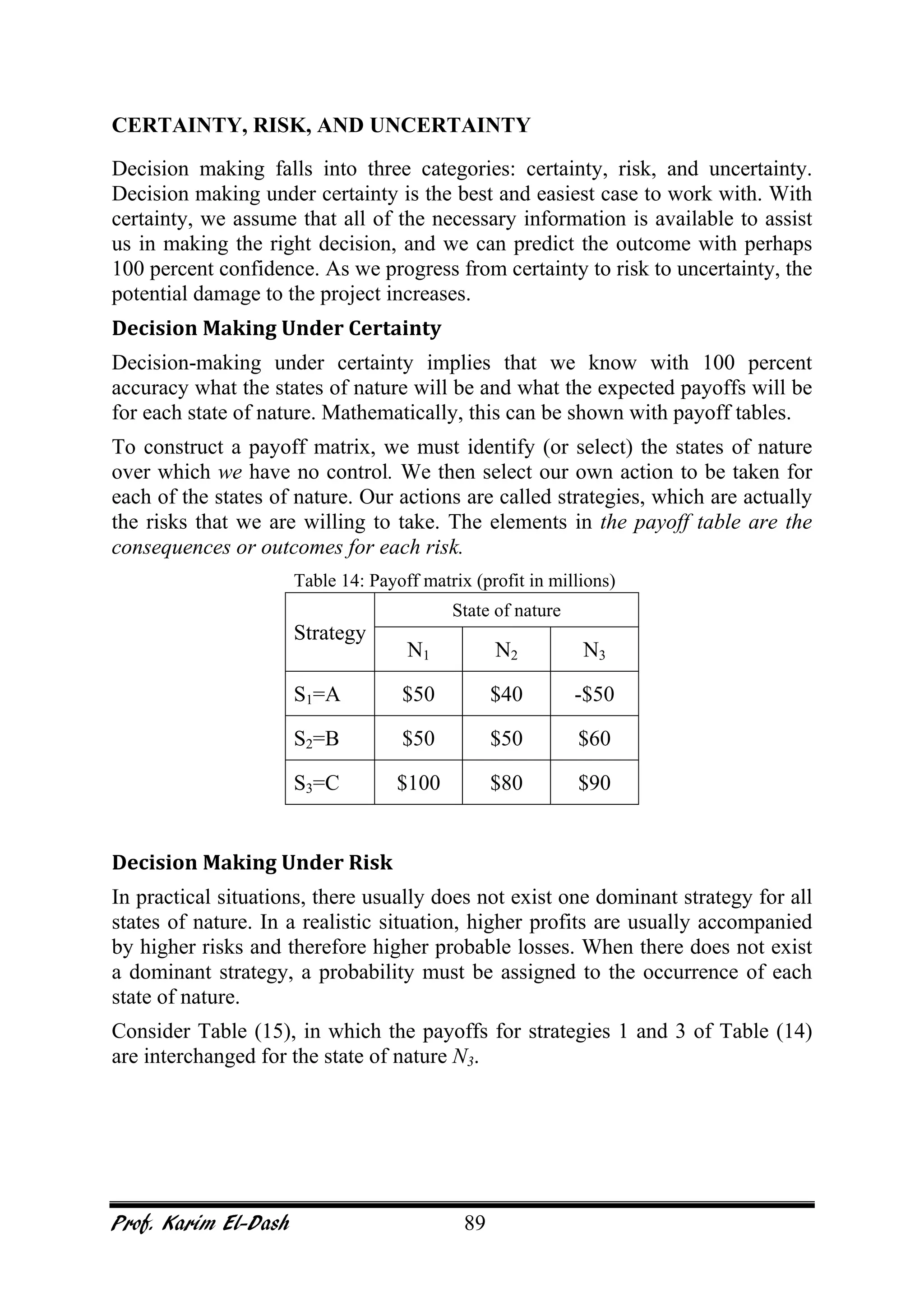
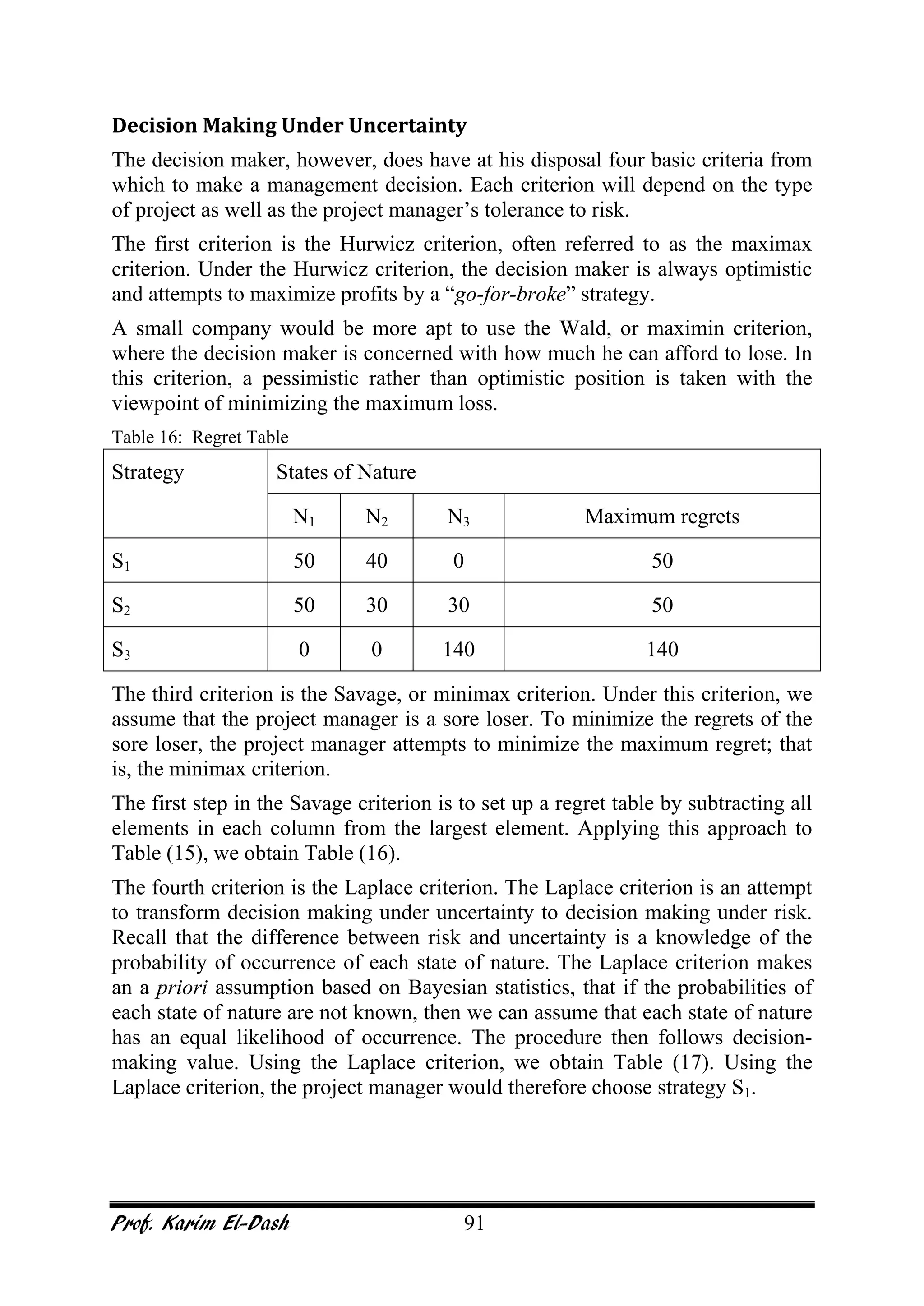
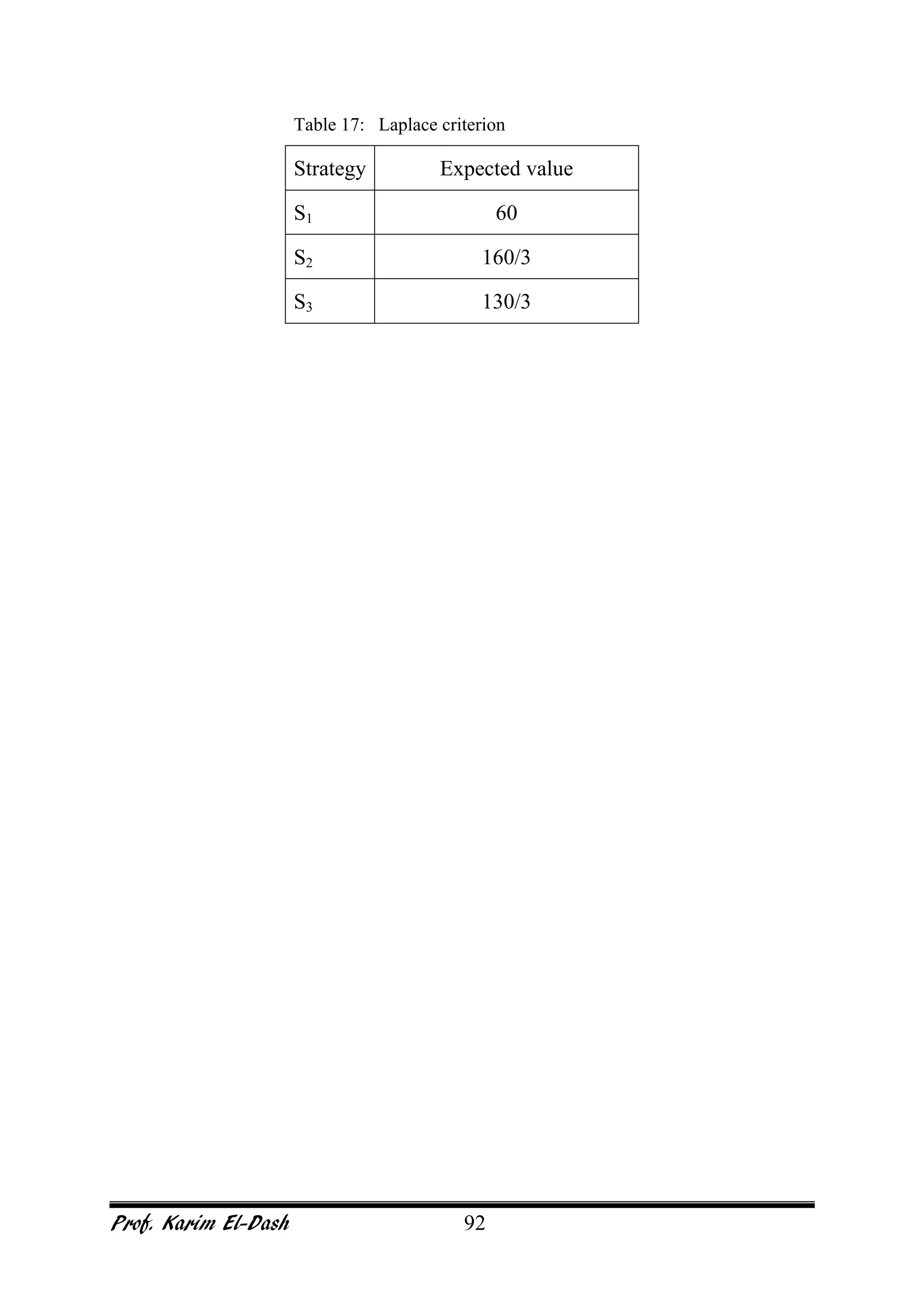
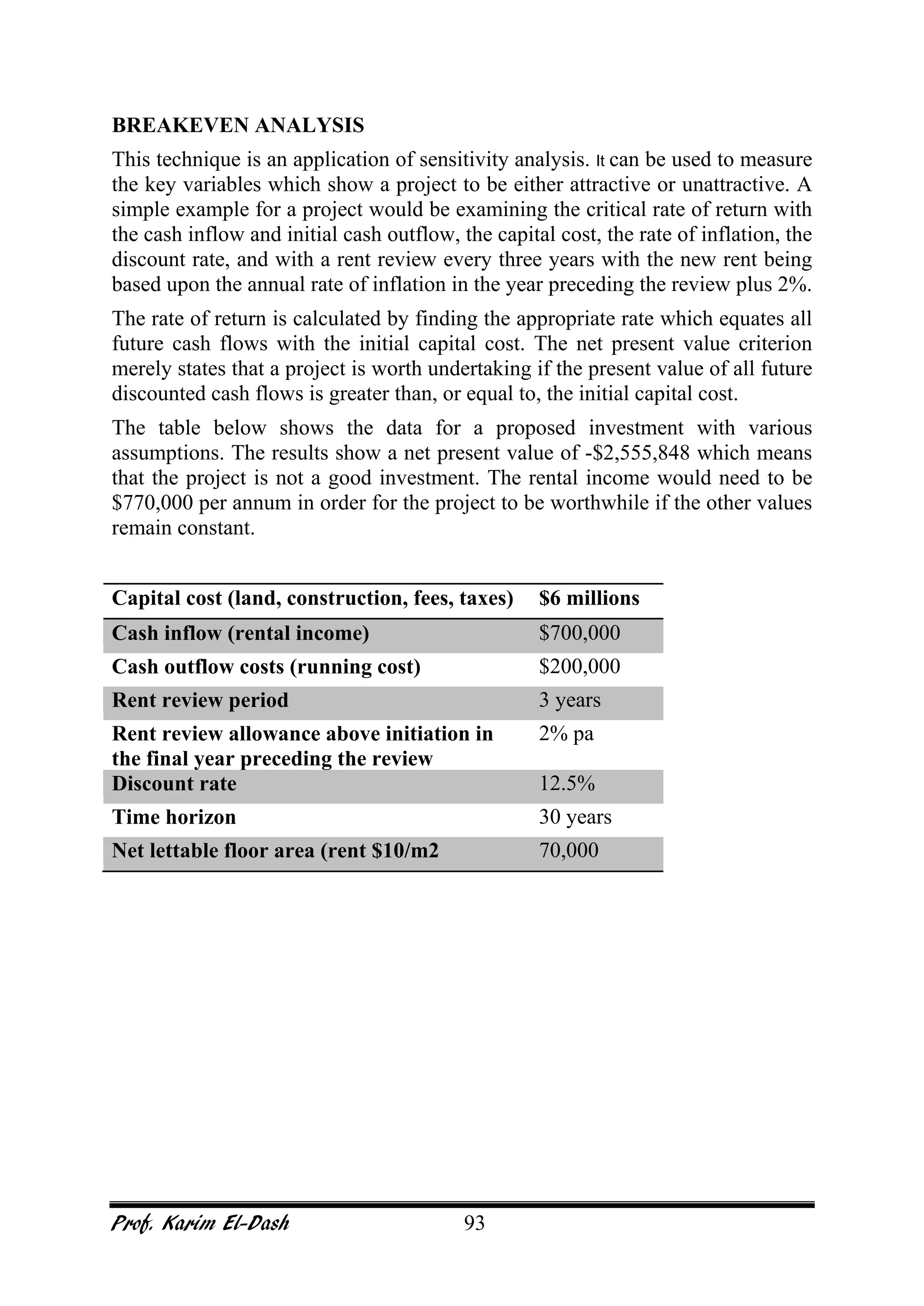
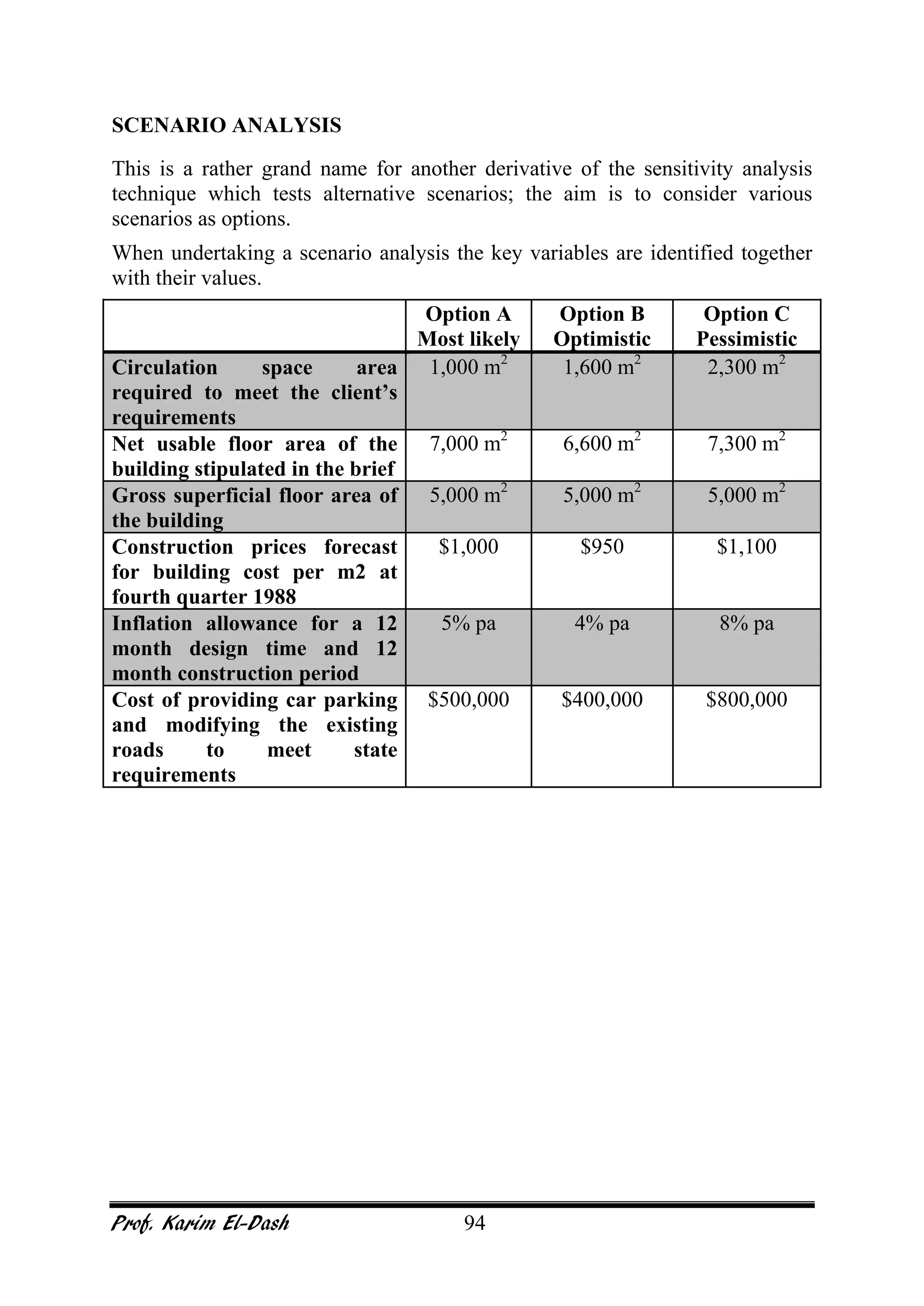
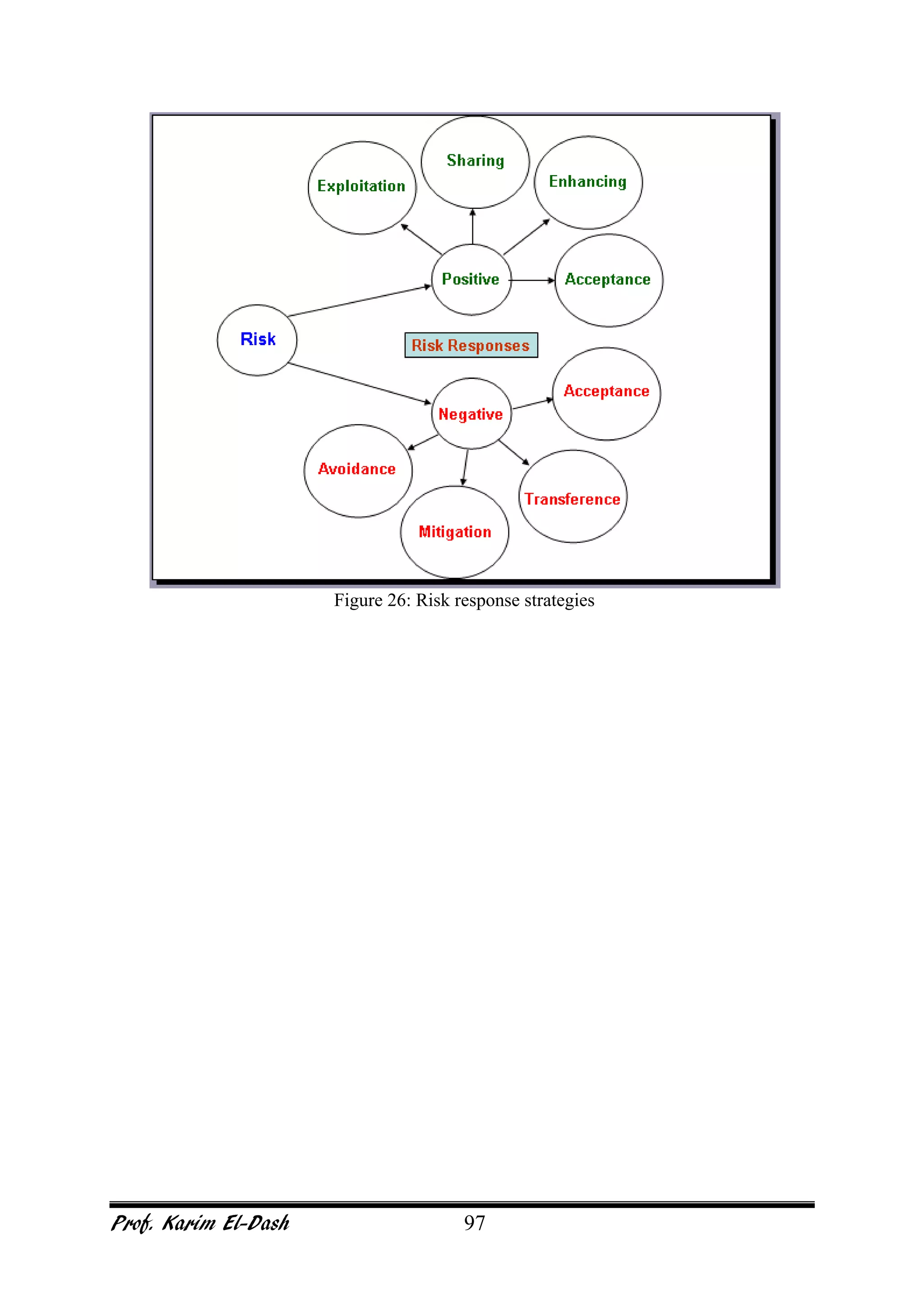
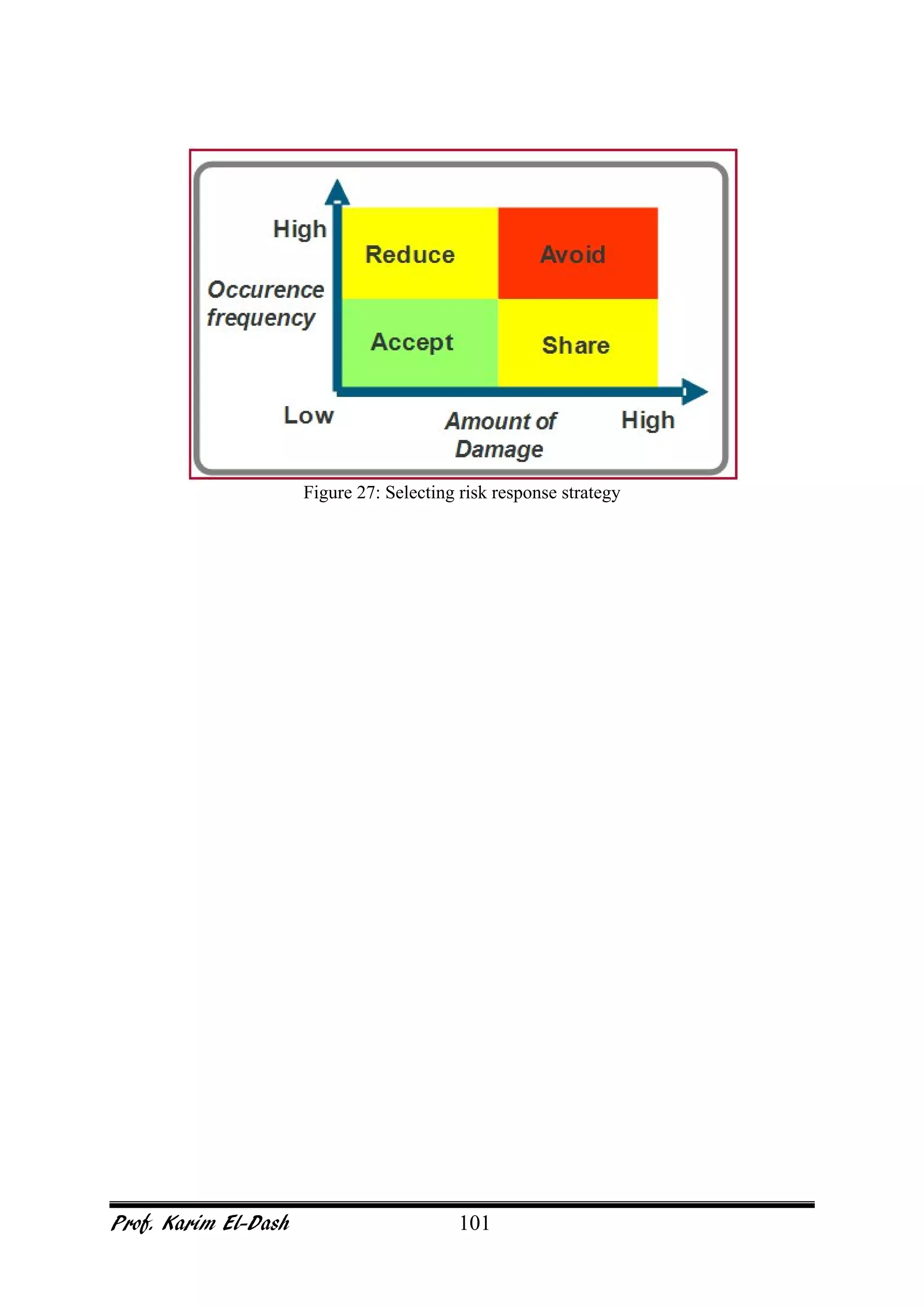
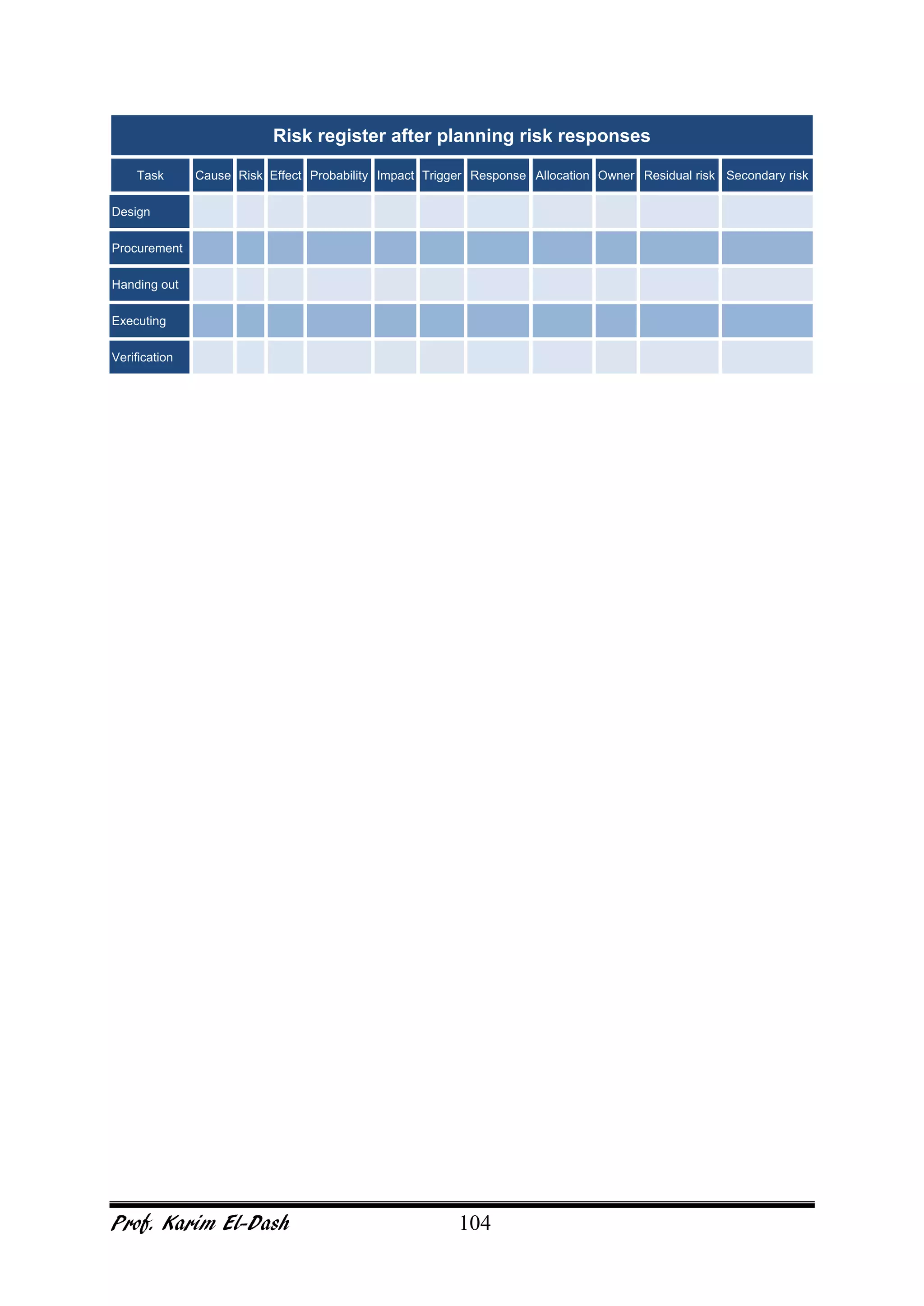
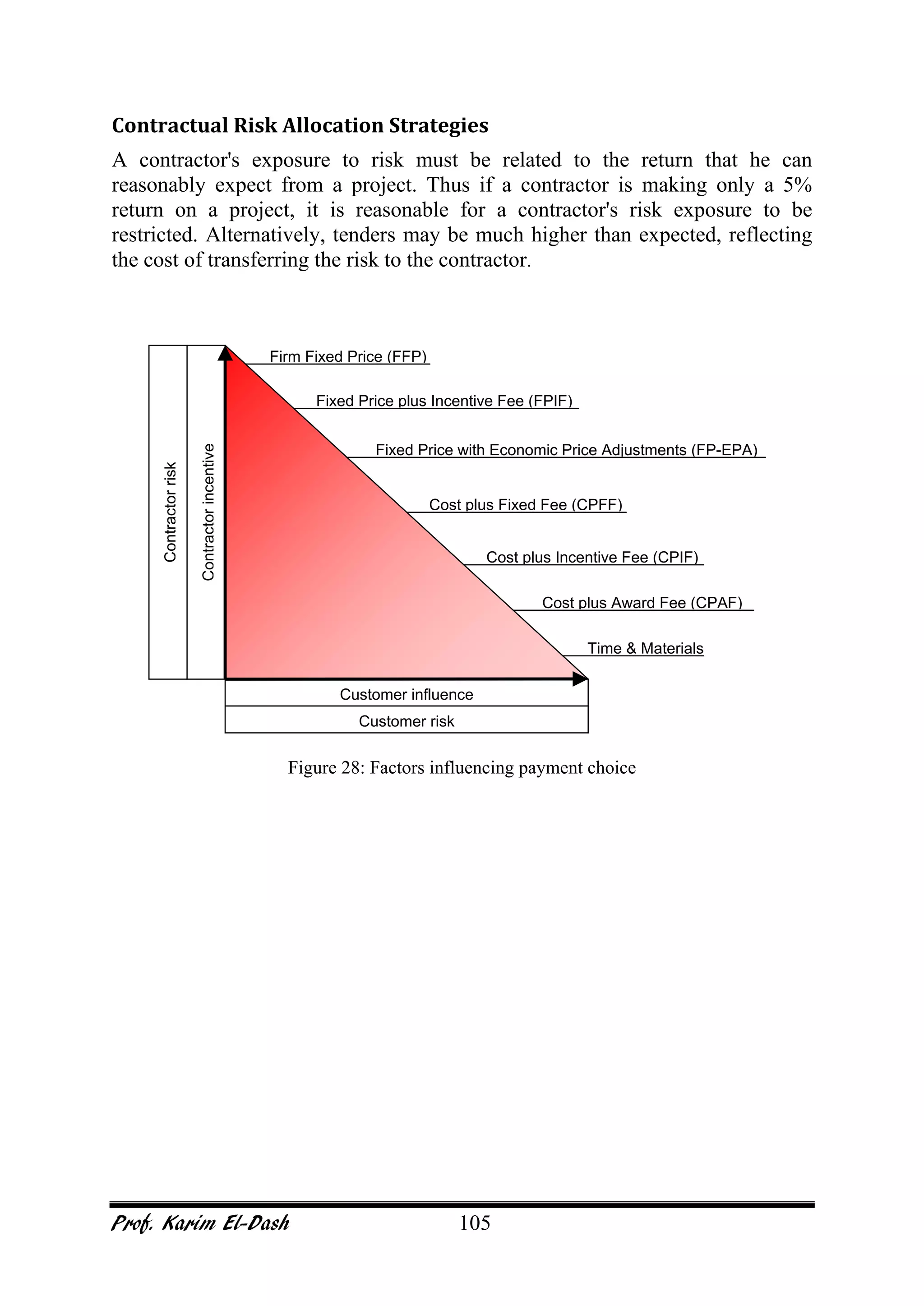
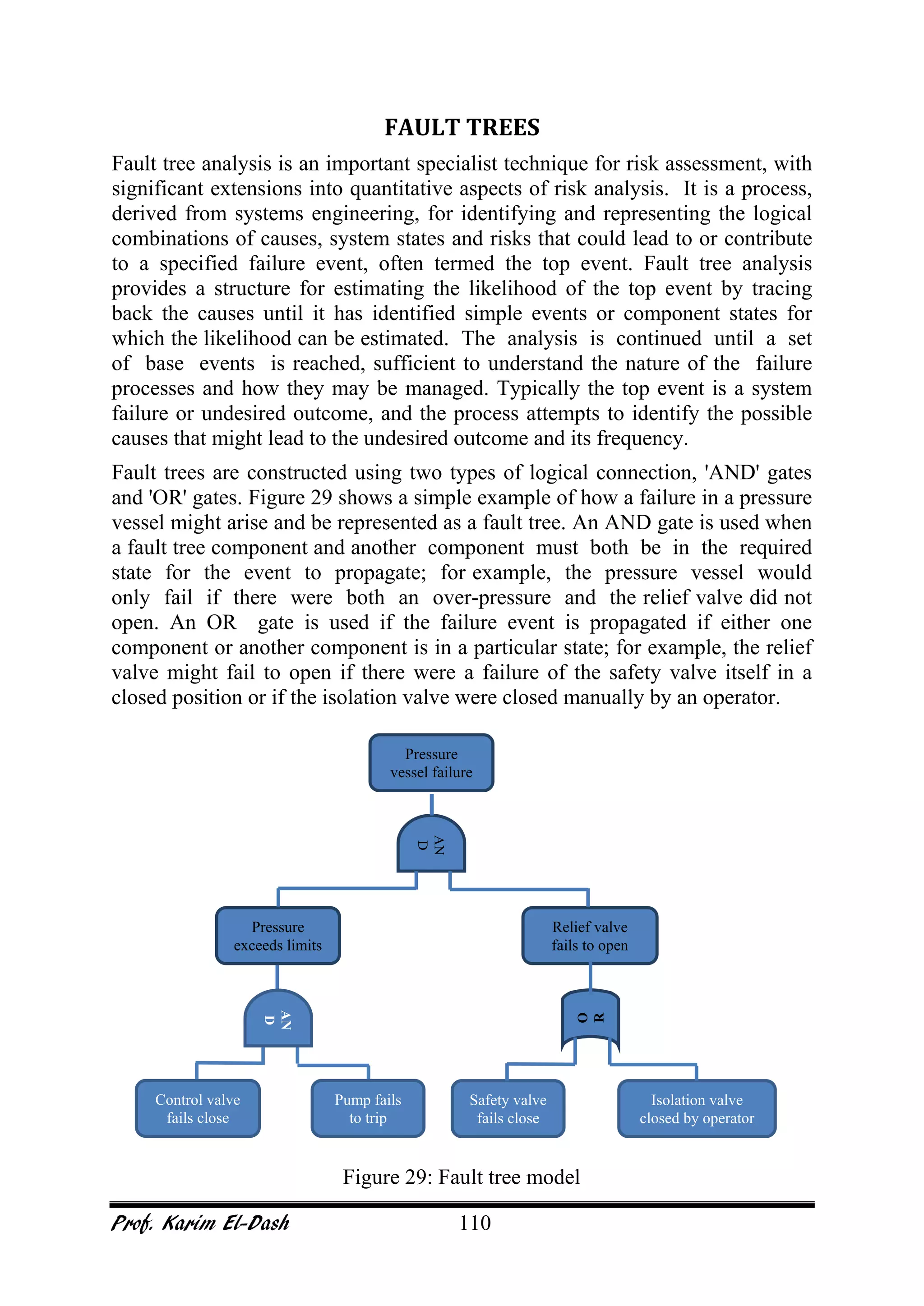
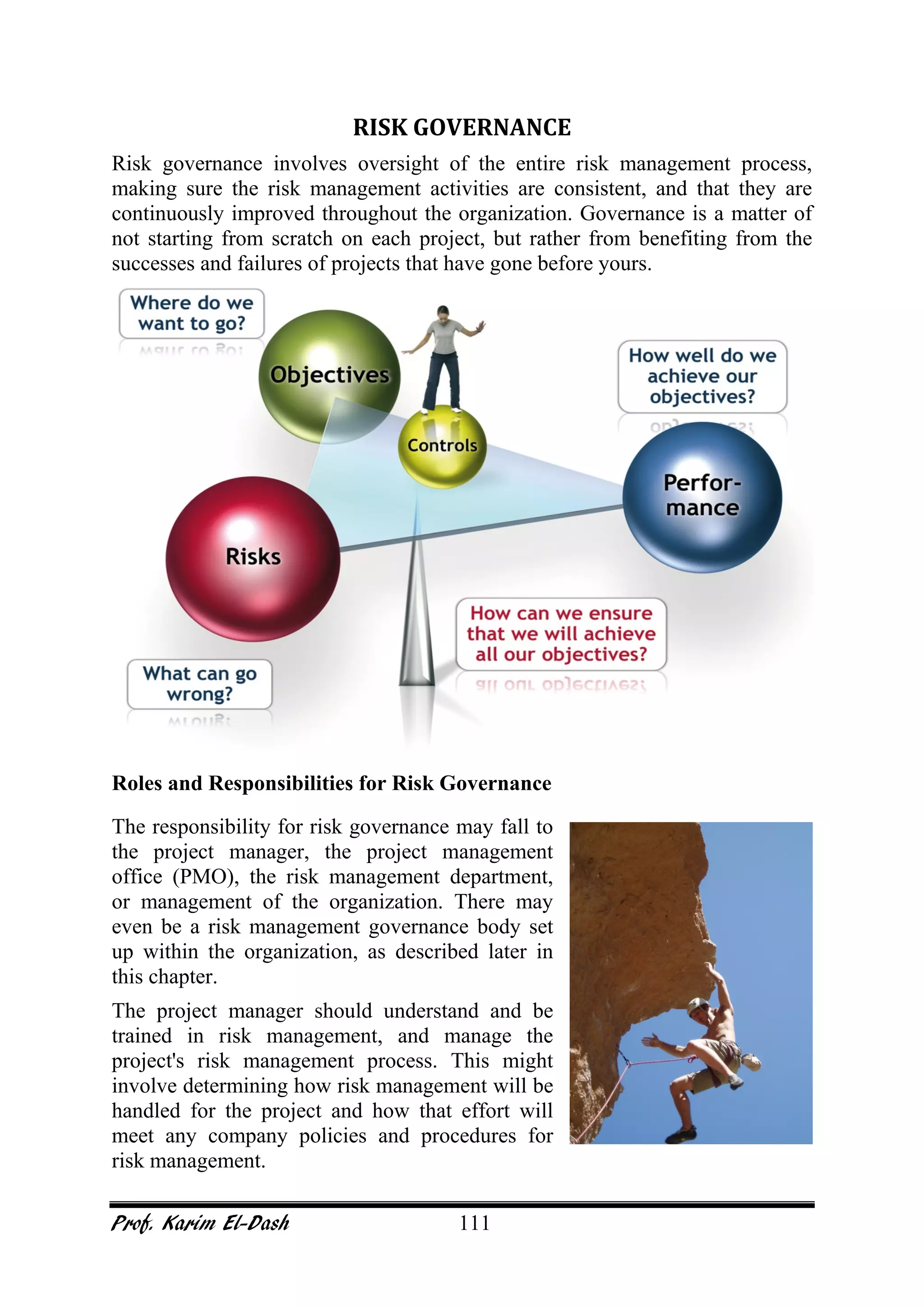
This document provides an overview of project risk management. It discusses key concepts such as defining risk, when risk management is used, and the risk management framework. It also covers topics like stakeholder identification and analysis, qualitative and quantitative risk analysis techniques, developing risk responses, and establishing governance around risk. The document is a comprehensive guide to understanding and implementing project risk management.