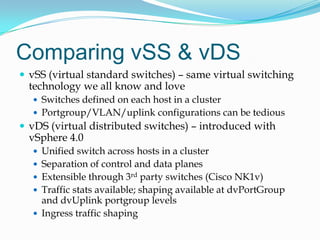
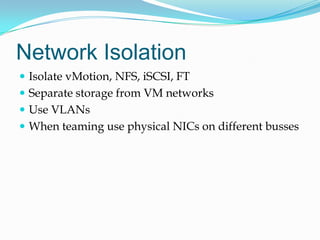
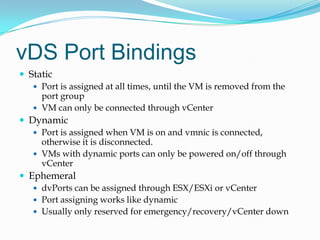
This document summarizes key points from a presentation on objectives 2.1 through 2.4 of the VCAP blueprint for implementing and managing complex virtual networks. It covers topics like VLAN, PVLAN, and vSwitch configuration, uplink teaming, network isolation, vDS port bindings, and migrating from vSS to vDS. Recommended resources are also provided.