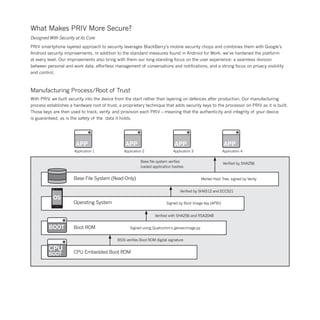
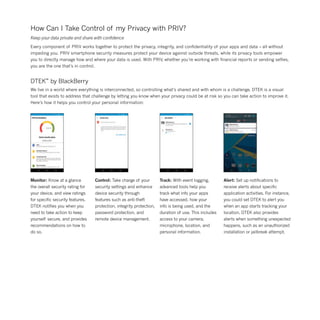
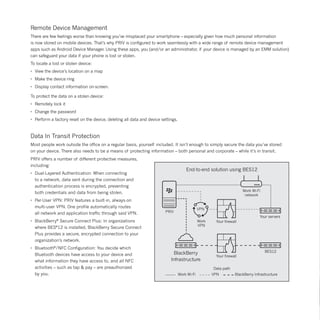
The document highlights the security features of the Priv smartphone by Blackberry, emphasizing its ability to safeguard user data and privacy against various mobile threats. It combines Blackberry's renowned security with Android's flexibility, offering advanced privacy controls, secure boot processes, and effective data encryption. With features like real-time monitoring through DTEK, users can manage their privacy, ensuring that their personal information remains protected and under their control.