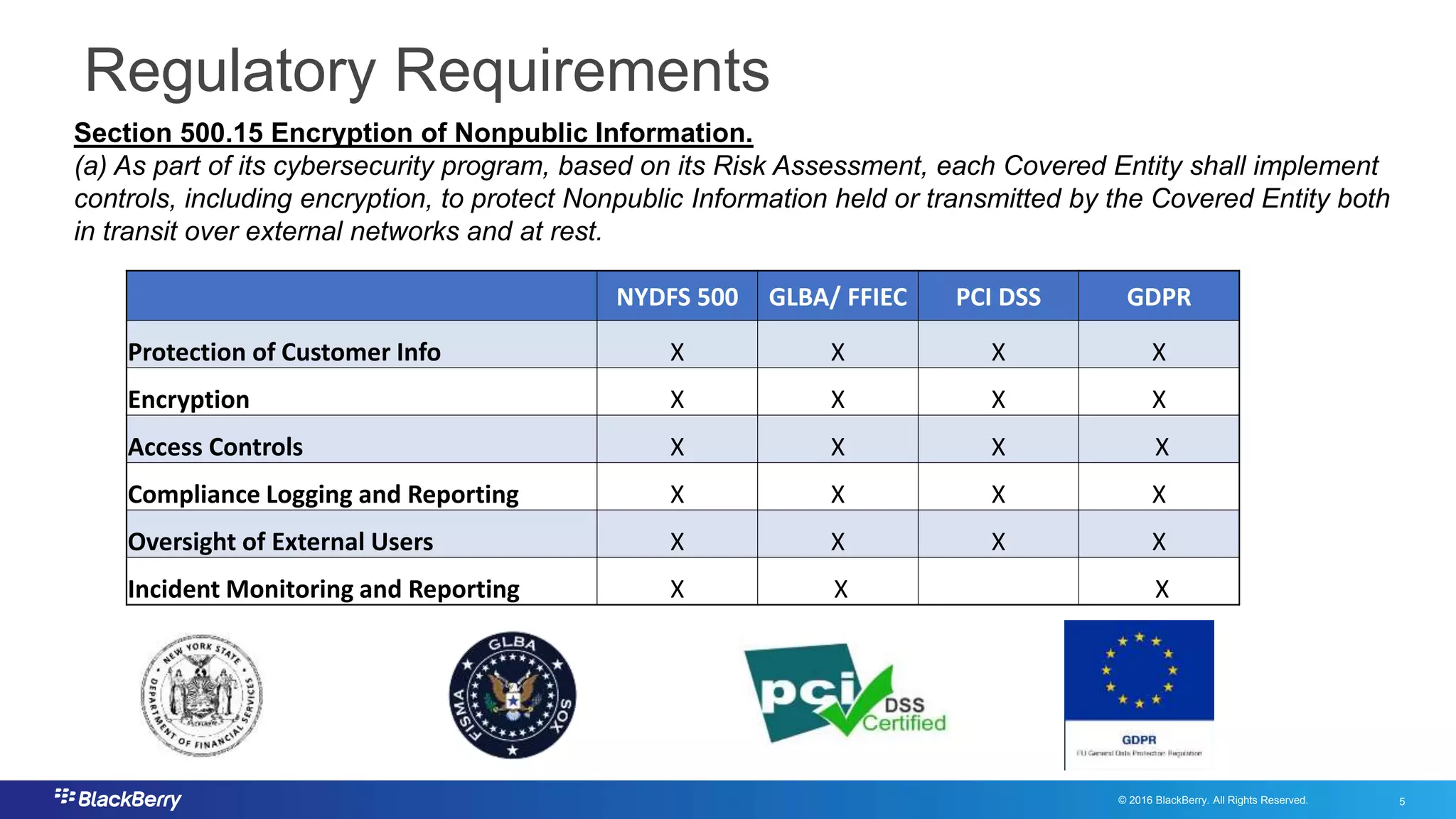
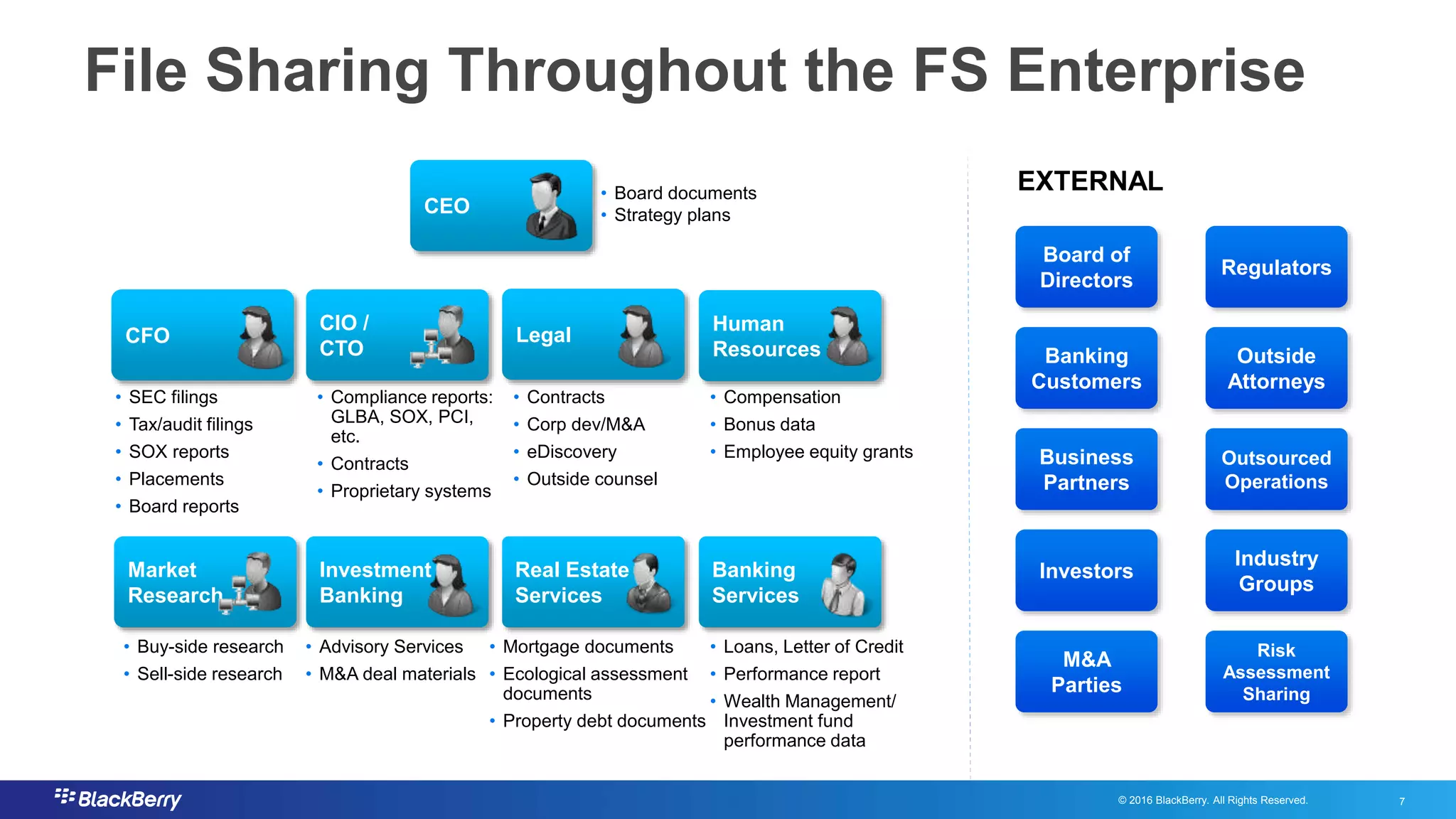
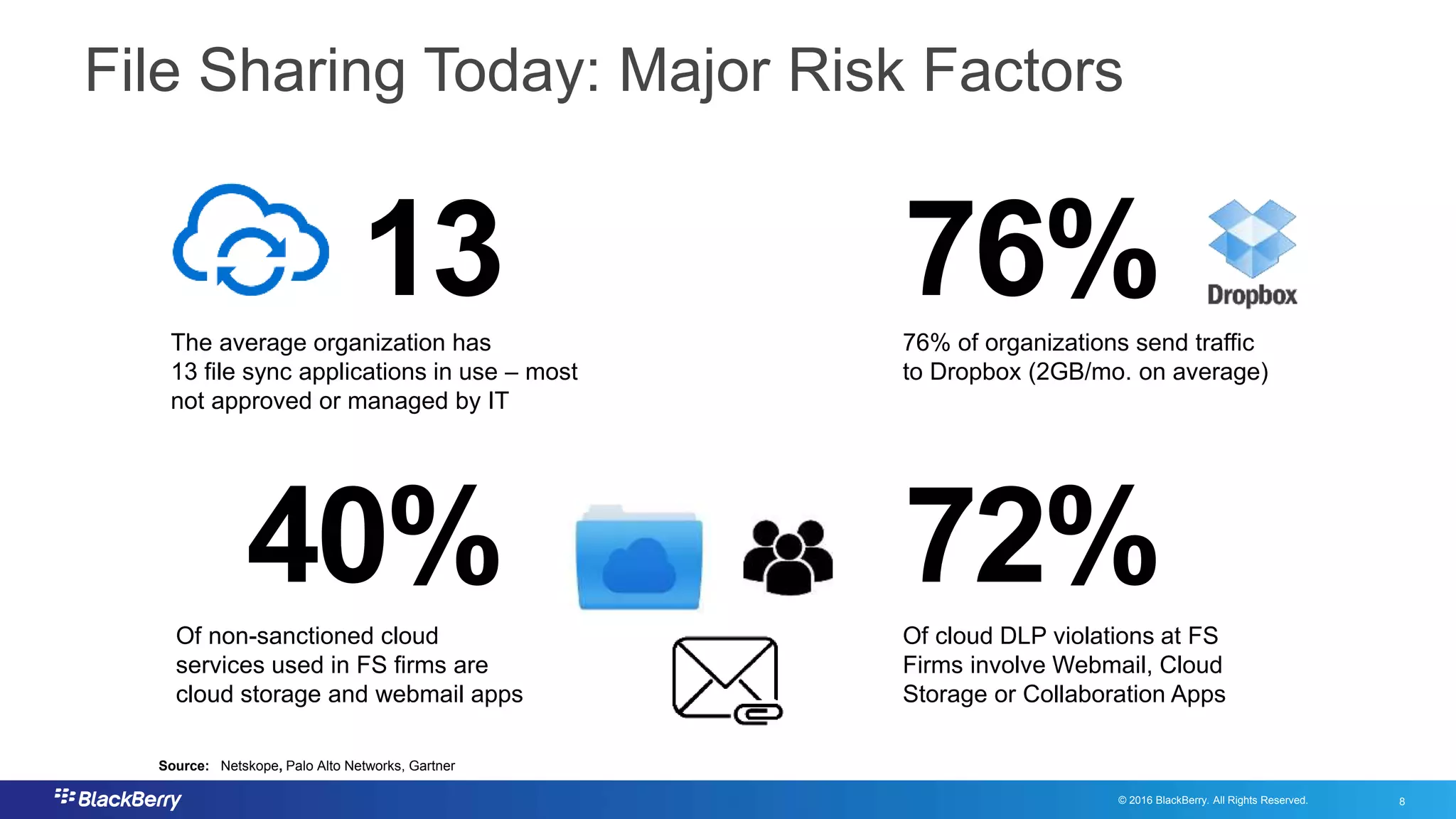
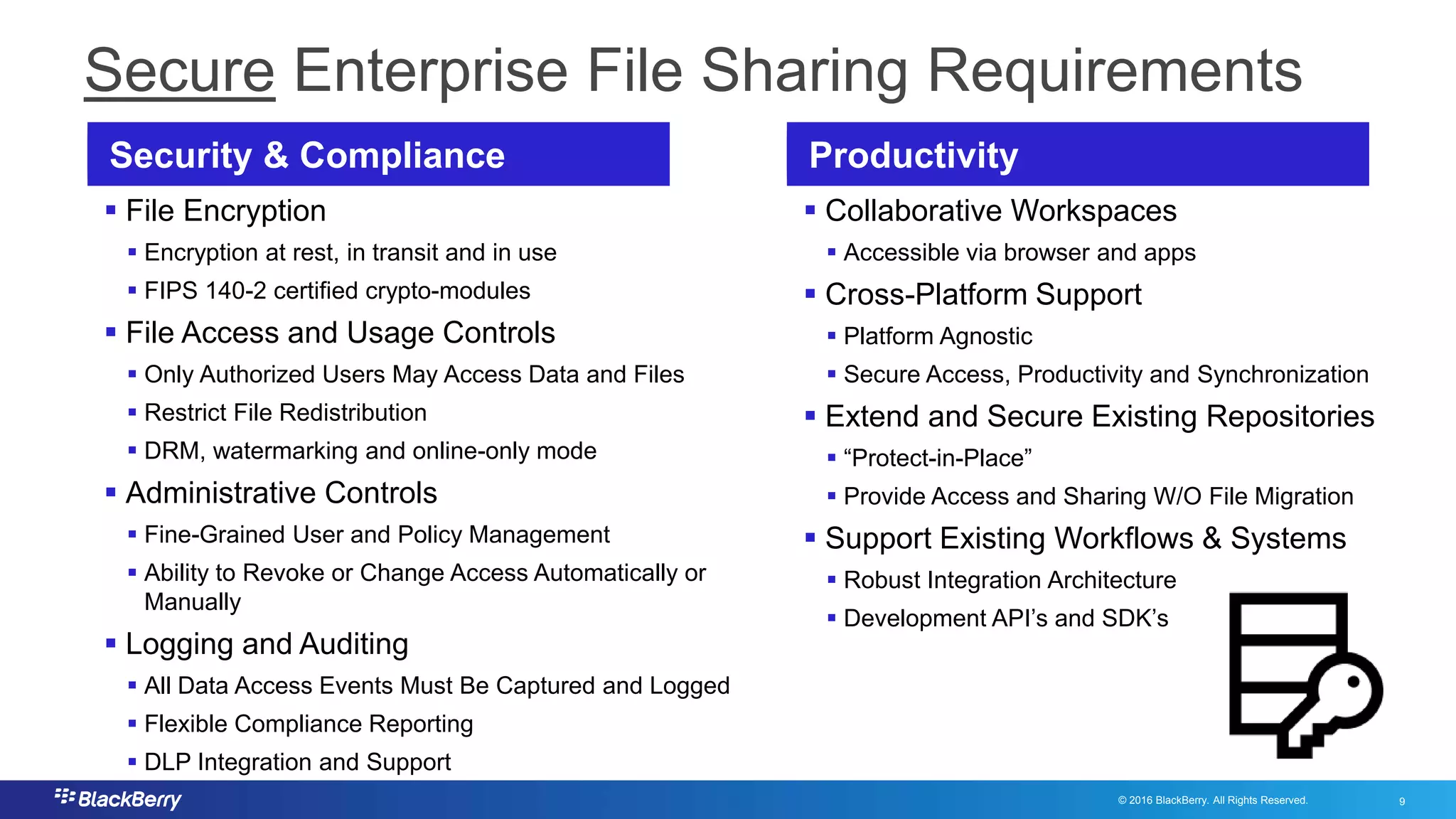
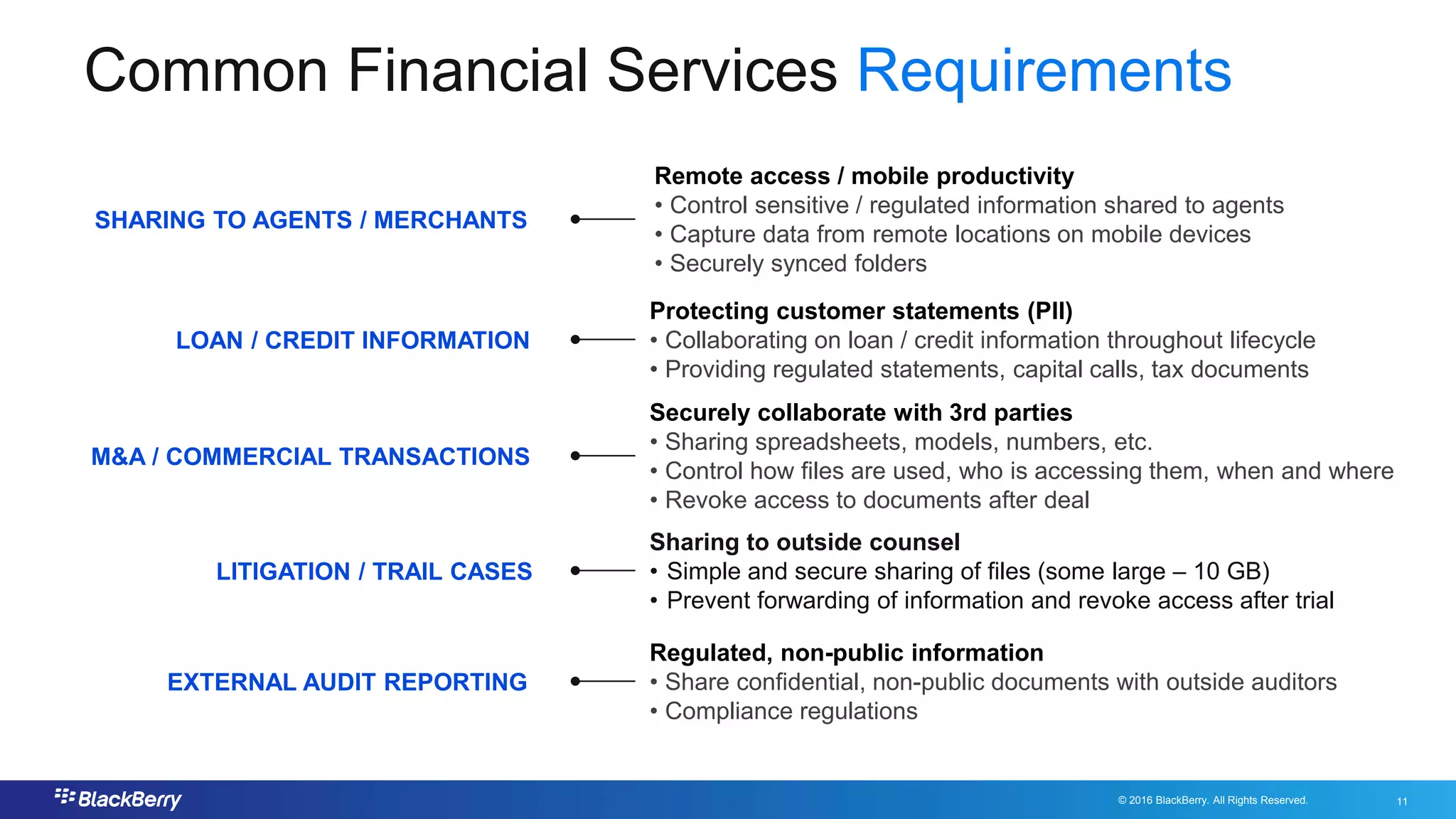
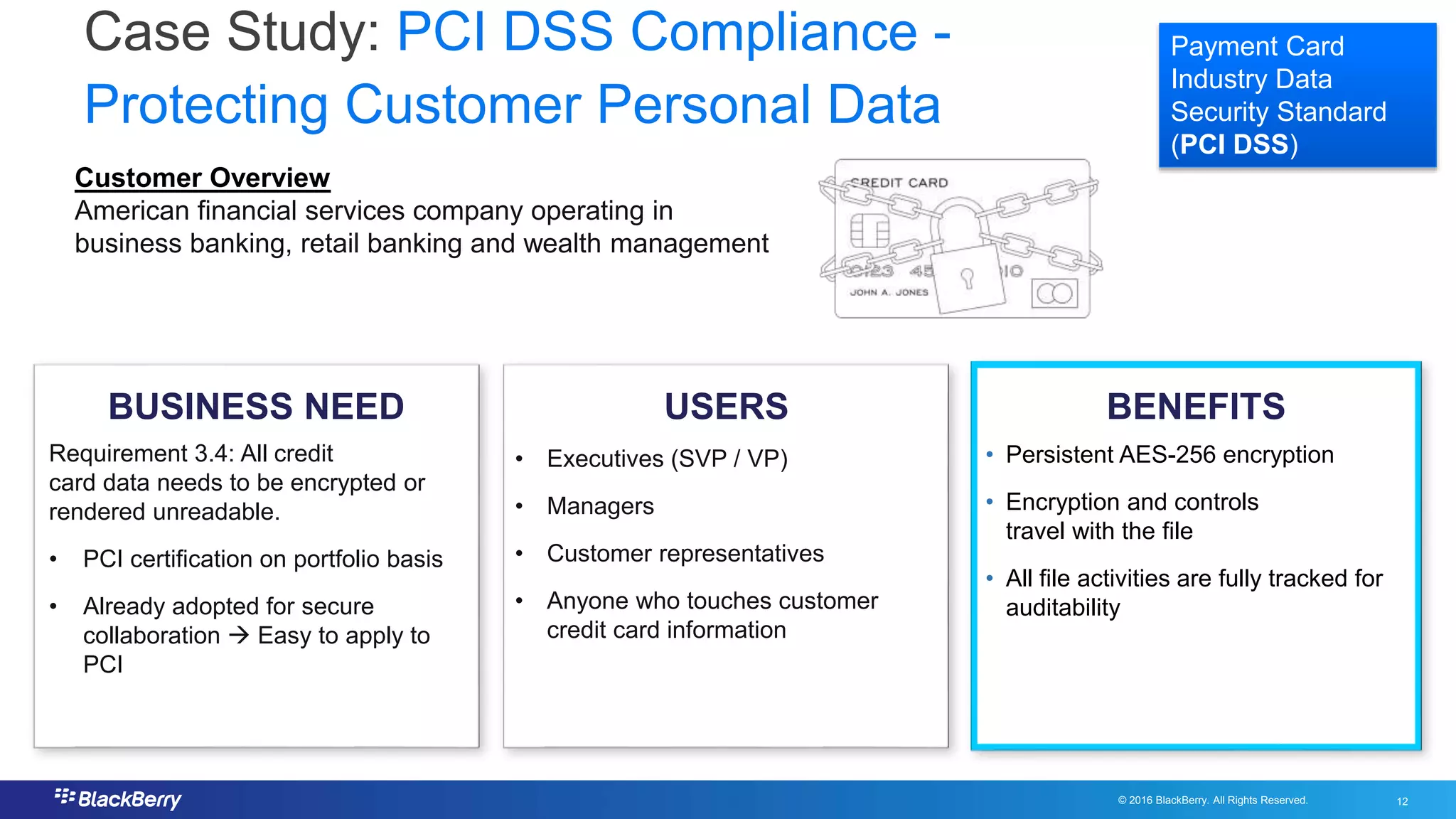
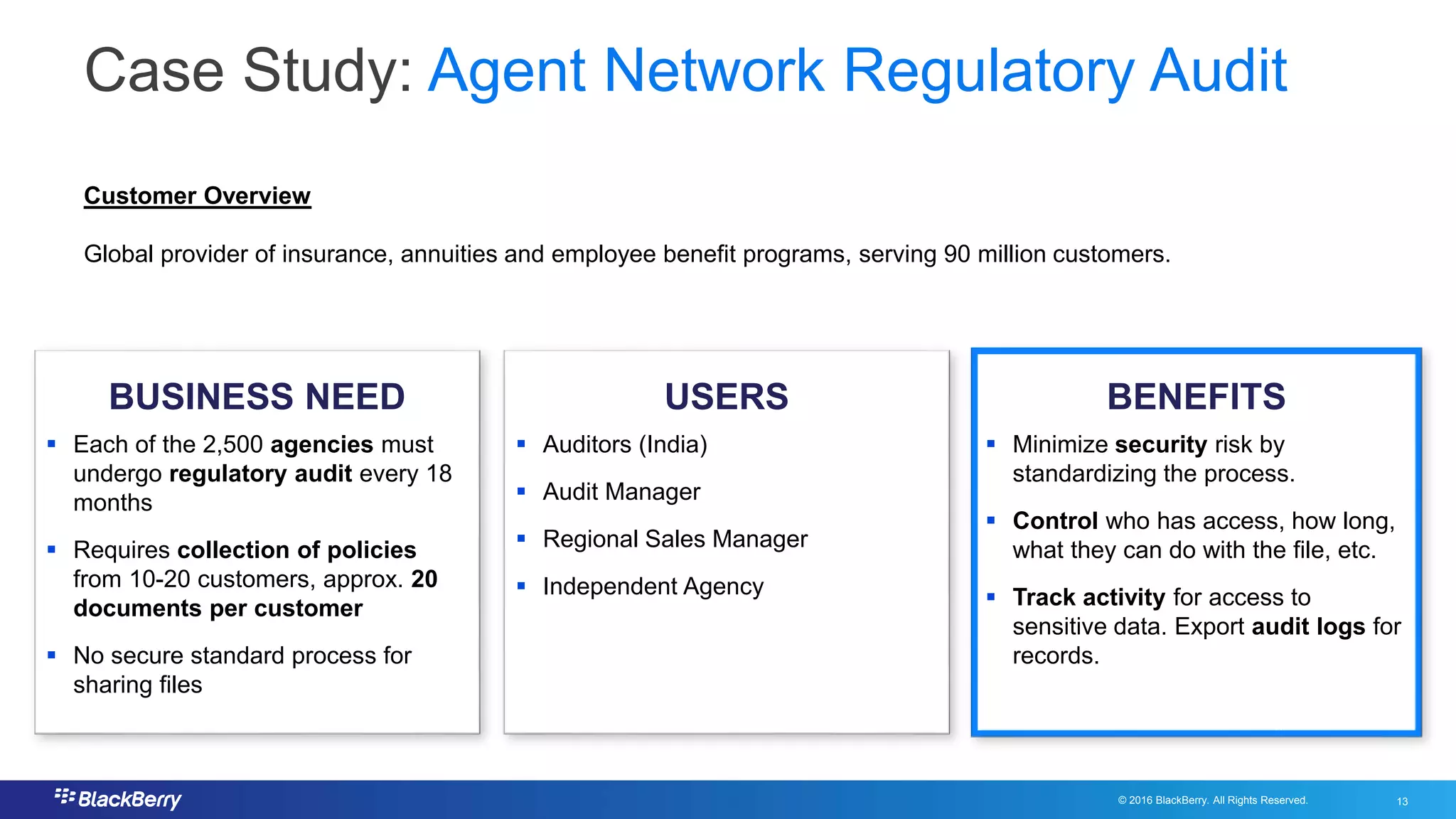
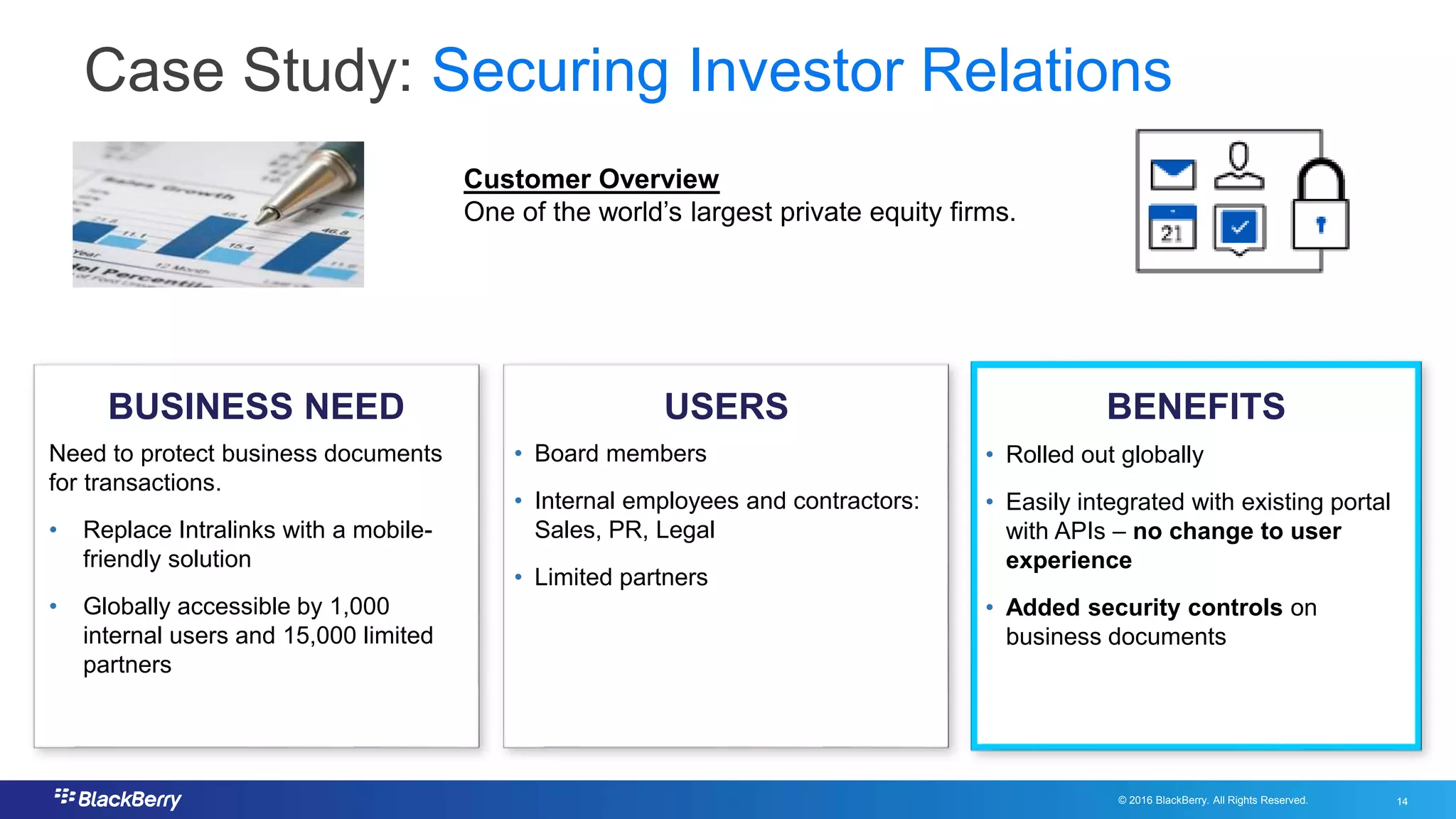
The document addresses secure file sharing needs and regulatory compliance in financial services, emphasizing the importance of data security, encryption, and user management. It outlines file-sharing use cases, best practices, and case studies illustrating how financial institutions can mitigate risks while ensuring productivity. Key highlights include various regulatory requirements and security standards that firms must adhere to for protecting customer data and facilitating secure collaboration.