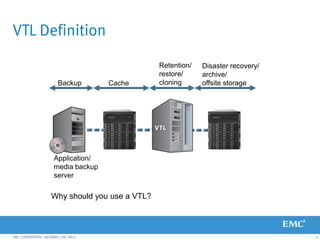
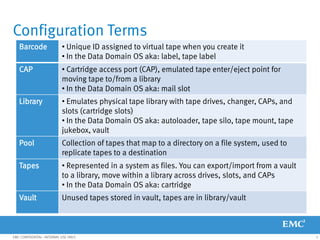
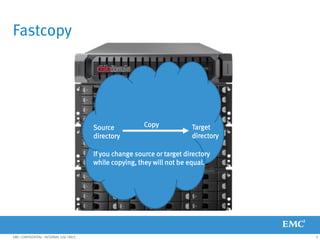
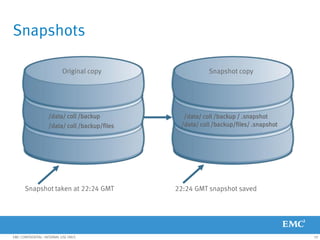
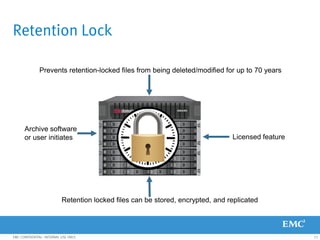
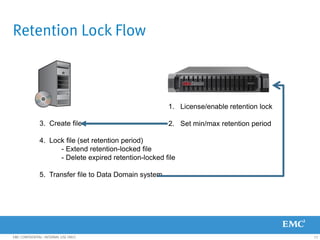
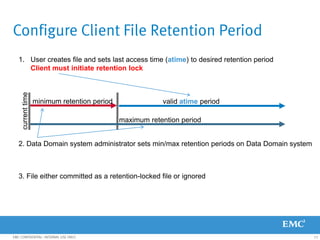
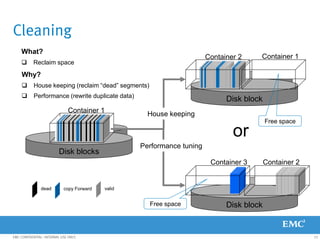
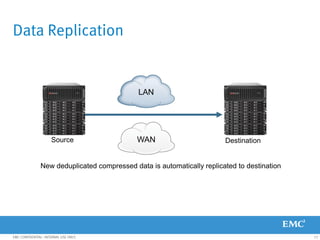
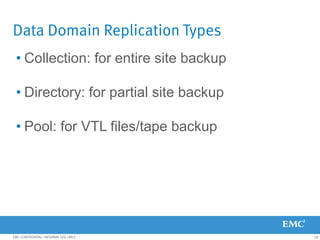
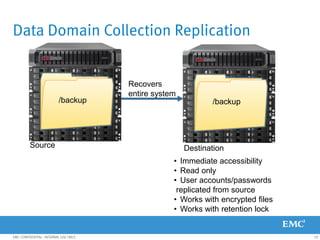
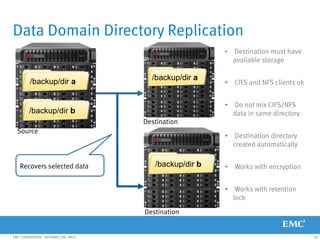
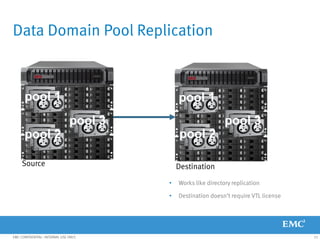
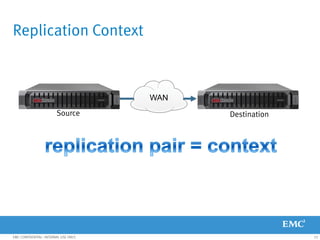
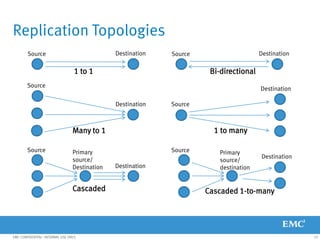
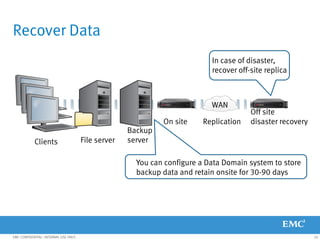
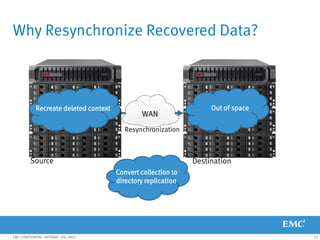
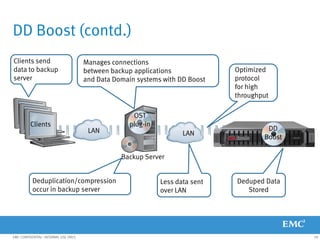
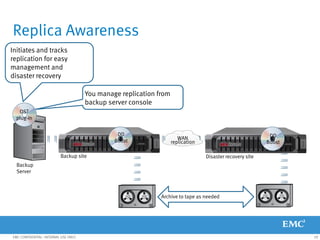
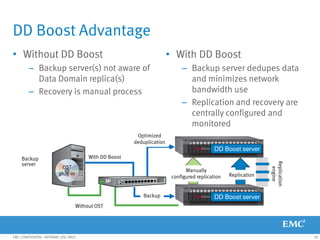
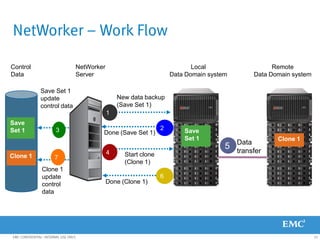
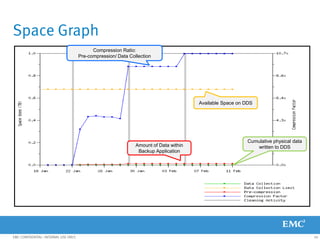
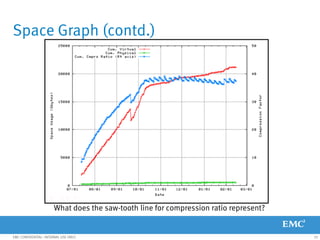
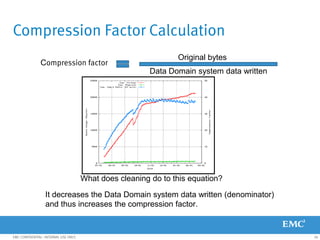
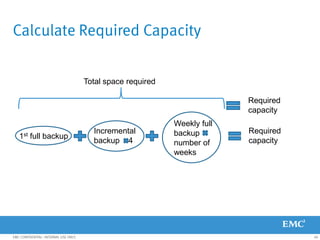
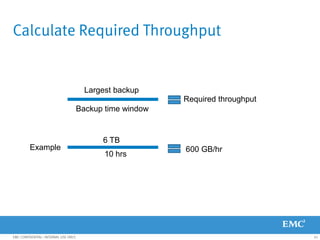
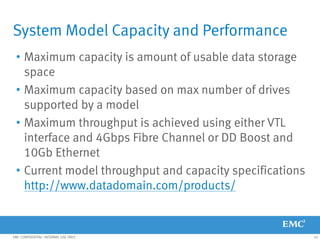
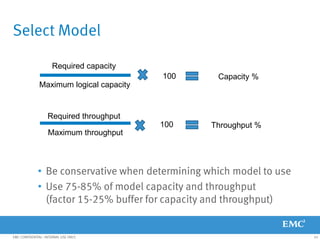
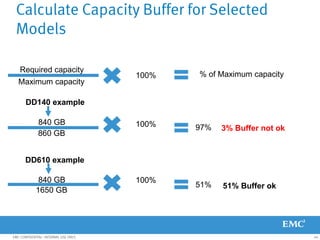
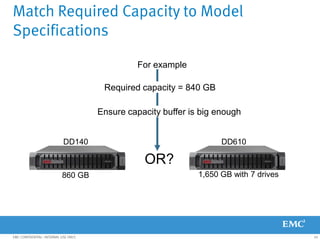
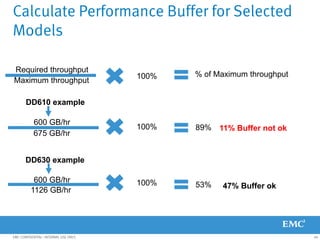
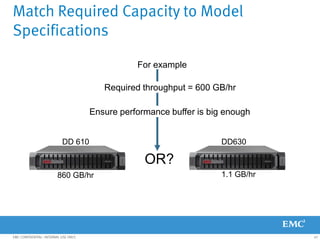
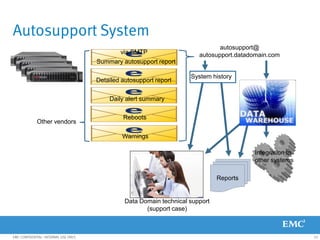
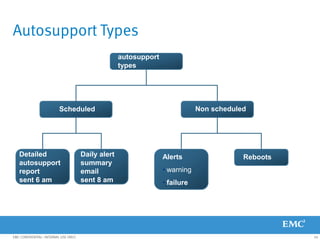
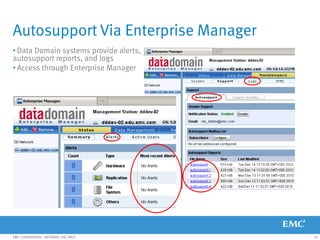
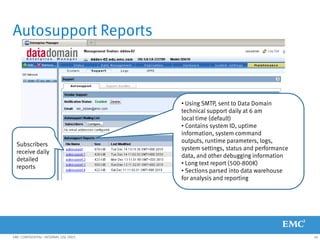
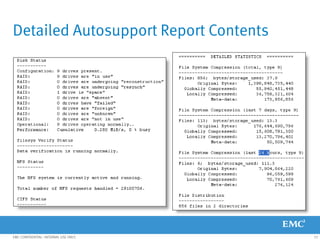
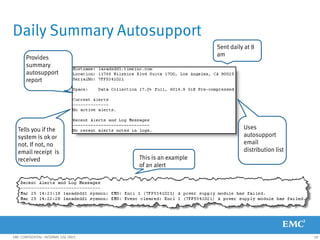
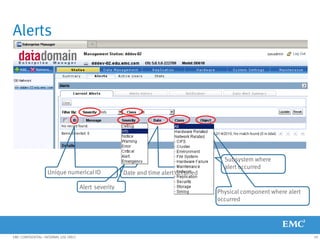
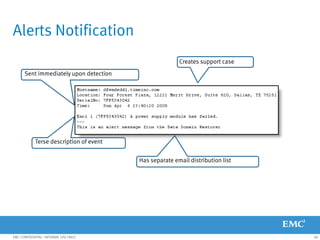
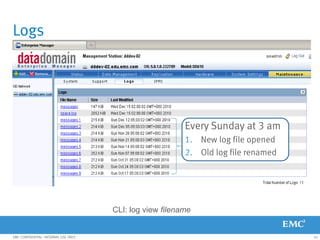
This document provides an overview of Data Domain advanced features and functions for Velocity Partner Accreditation. It covers topics such as virtual tape library (VTL) planning, snapshots, replication, recovery, DD Boost integration, capacity and throughput planning, and system monitoring tools. The document contains lessons and explanations on these topics to help partners learn about and describe Data Domain's data protection solutions.