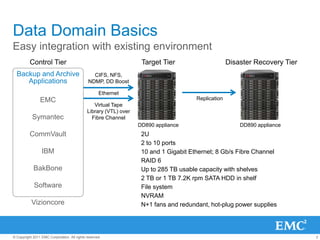
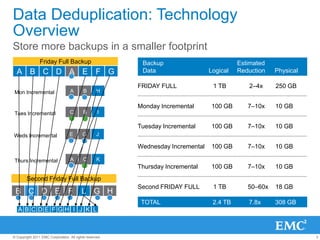
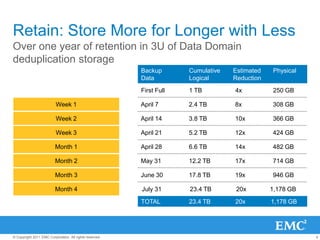
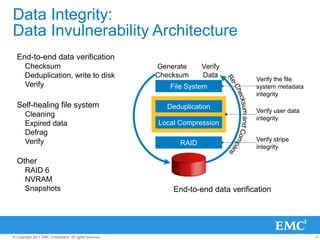
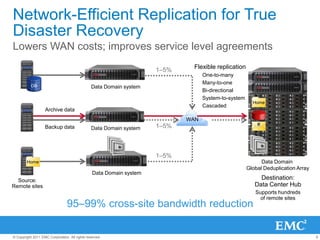
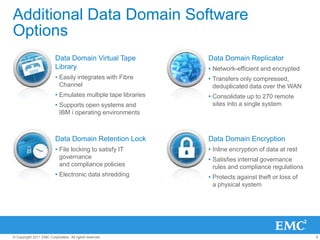
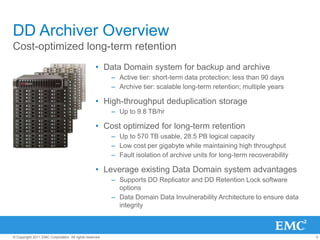
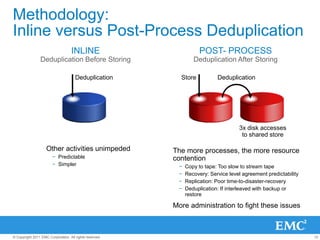
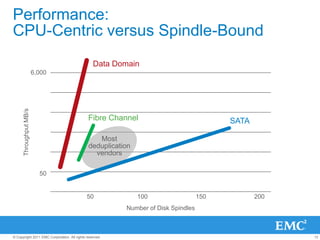
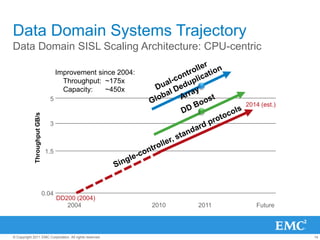
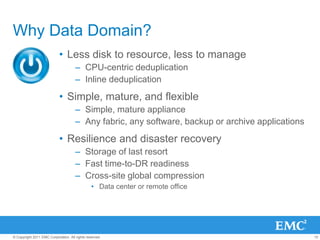
The document provides an overview of data deduplication technology, highlighting its integration with existing environments and its role in disaster recovery and backup applications. It discusses various appliances and their specifications, including performance metrics, data integrity processes, and software options to enhance backup operations. Additionally, it emphasizes the benefits of reduced storage footprint, cost efficiency, and compliance management.