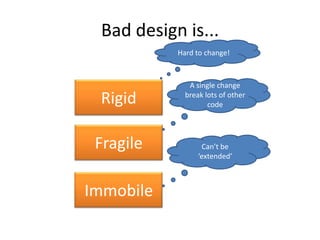
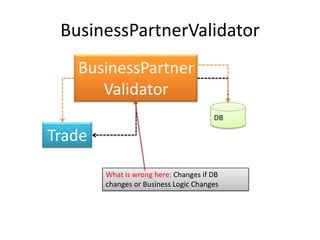
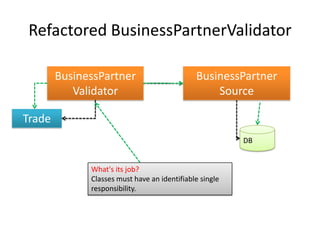
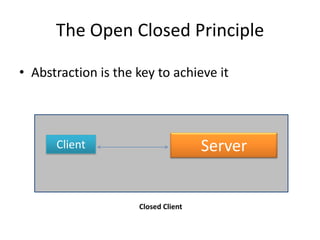
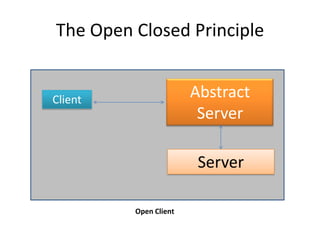
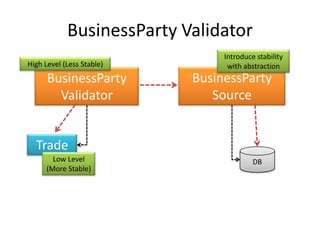
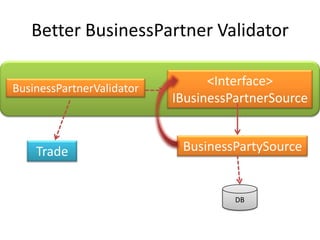
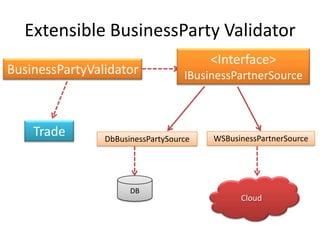
This document discusses principles for practical enterprise application development. It introduces enterprise architecture and design, then discusses principles like the single responsibility principle, open/closed principle, and dependency inversion principle. Bad design is described as being hard to change and fragile. Good design principles emphasize modularity, loose coupling, and applying principles like abstraction to achieve open/closed and dependency inversion. The document demonstrates applying these principles through examples and promises a demo.